1. Introduction
Millimeter-wave (mmWave) technology is a cornerstone of sixth-generation (6G) communication and future networks, offering advantageous characteristics such as high data rates, low latency, and receiver diversity [
1]. The short wavelength of mmWave facilitates the integration of large antenna arrays into compact receiver form factors, leading to the development of mmWave Single-Input Multiple-Output (SIMO) systems. These systems represent a key enabling technology for a wide range of applications, including the Internet of Things (IoT) [
2]. Compared to Multiple-Input Multiple-Output (MIMO) systems equipped with multiple antennas at both the transmitter and receiver ends, the SIMO architecture offers a more cost-effective and practical solution for many millimeter-wave applications, particularly in the IoT domain. This preference stems primarily from the fact that transmitting devices in IoT applications—such as sensors, wearables, or terminals—typically face extremely stringent constraints on size, cost, and power consumption. Integrating the multi-antenna arrays and corresponding RF chains required for MIMO systems onto these devices is often technically and economically infeasible. SIMO systems ingeniously address this challenge by shifting the system complexity to the receiver. The transmitter can maintain a minimalist design with a single antenna, thereby minimizing power consumption and hardware costs. The receiver, typically subject to less stringent constraints, can instead be configured with a large-scale multiple-output antenna array. This enables high receiver diversity gains, effectively countering the path loss and fading inherent in millimeter-wave channels, and ensuring reliable communication and signal quality. Therefore, the millimeter-wave SIMO system architecture discussed in this paper represents a critical and practical choice in balancing performance, cost, and power consumption constraints. However, the broadcast nature of wireless channels renders mmWave SIMO systems susceptible to spoofing attacks, where an illicit transmitter impersonates a legitimate entity to deceive the receiver, thereby gaining unauthorized access to execute further malicious activities. To mitigate this threat, device authentication has become a critical defense mechanism. Unlike higher-layer authentication schemes based on cryptography, physical layer authentication (PLA) verifies a transmitter’s identity by leveraging intrinsic physical layer characteristics, such as channel features and hardware fingerprints. PLA offers notable advantages, including high security, low complexity, and strong compatibility [
3,
4,
5,
6], making it a vital supplement to conventional cryptographic methods.
PLA is broadly categorized into hardware fingerprinting-based and channel-based authentication, distinguished by the exploited physical layer features [
7]. Regarding hardware fingerprinting, Hou et al. [
8] proposes a hypothesis-based authentication scheme that utilizes the time-varying carrier frequency offset (CFO) in dynamic environments. In the domain of channel-based authentication, Xiao et al. [
6] utilized multiple landmarks to enhance transmitter resolution via received signal strength indicator (RSSI) features, subsequently proposing a logistic regression-based authentication scheme. Exploiting the sparse characteristics of the mmWave MIMO channel, the work in [
9] extracts virtual angle of arrival (AoA) features from the virtual channel and formulates a binary hypothesis test to validate the transmitter.
While existing mechanism enhance wireless security, PLA in the context of mmWave SIMO systems remains underexplored. Such systems exhibit unique physical layer characteristics not present in conventional networks, particularly the multipath time delay features within the channel, which are highly suitable for identity validation. Accordingly, this paper introduces a novel PLA scheme for mmWave SIMO systems that leverages these distinctive delay characteristics. In particular, we first develop an efficient method to estimate and extract the requisite multipath time delay features. Subsequently, employing principles from statistical signal processing and hypothesis testing, we derive closed-form expressions for the key performance metrics of false alarm and detection probabilities. Finally, the practical effectiveness and robustness of the proposed authentication framework are validated through comprehensive simulations under a range of estimation conditions.
The rest of this paper is organized as follows. The system model and problem formulation are introduced in
Section 2.
Section 3 presents the proposed PLA scheme. The false alarm and detection probabilities are derived in
Section 4.
Section 5 provides the simulation results, and
Section 6 concludes the paper.
5. Simulation Results and Analysis
In this section, we conduct a series of numerical simulations to validate our theoretical derivations and evaluate the performance of the proposed PLA mechanism under various conditions. The simulation methodology is designed to model the authentication scenario described in
Section 2.1. The time intervals between multipath delays,
, are modeled as exponential random variables, and their evolution between two consecutive frames (at time
and
t) is characterized using the first-order Gauss–Markov process. The channel for the illegitimate user, Eve, is generated independently using the same statistical model, but with a different variance for its delay components, as defined by the parameter
. To generate the performance metrics, we first simulate the reception of an authenticated frame from Alice at
to store the reference fingerprint
. Subsequently, we simulate a new frame at time
t from an unknown transmitter X.
In the simulations, the system performance is evaluated under varying conditions. The SNR is defined as
, where
denotes the average signal energy per symbol, and
represents the variance of the additive white Gaussian noise. Regarding the receiver configuration, the base station Bob employs a hybrid uniform cylindrical array (UCyA) as described in the system model. The specific geometry parameters for the UCyA used in our experiments are set as follows: the number of vertical layers is
, and the number of antennas per circular array is
, resulting in a total of
receiving antennas. The radius of each circular array is set to
r, and the vertical spacing between adjacent layers is
h. The variance ratio of multipath delay components is denoted by
, and is controlled by fixing
while adjusting
,
M represents the number of propagation paths,
D is the number of subcarriers,
is the frequency of each subcarrier,
W is the system bandwidth, and
represents the autocorrelation coefficient of adjacent multipath delay components.
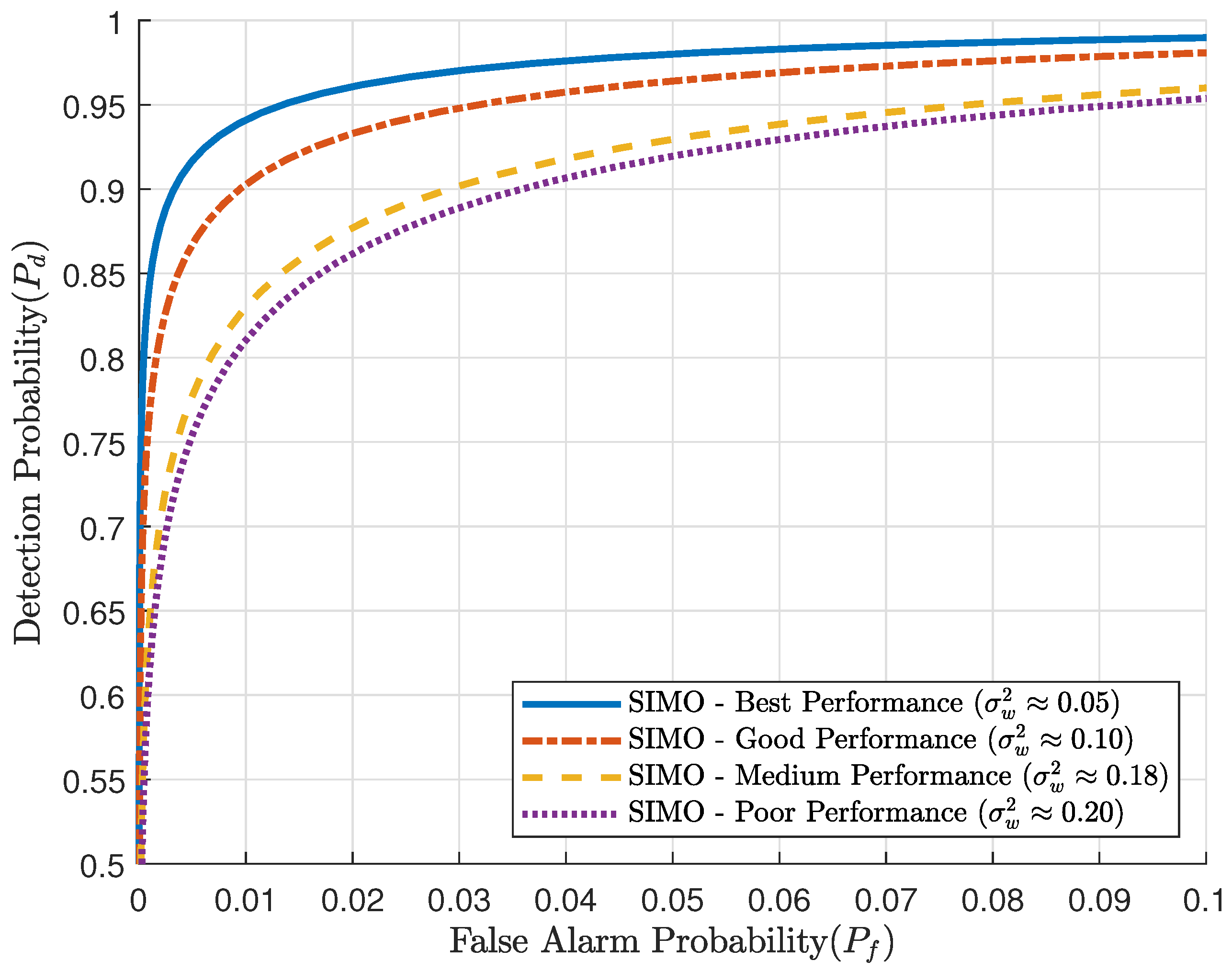
Figure 2 illustrates the ROC curves of the proposed PLA scheme under varying conditions of multipath delay estimation error variance. The experimental setup is fixed with the following parameters:
,
,
,
, and
. In the plot, the horizontal axis represents the probability of false alarm (
), and the vertical axis represents the probability of detection (
). Each curve corresponds to a specific value of
, namely 0.05, 0.10, 0.15, and 0.20.
We first evaluate the impact of the multipath delay estimation error variance,
. This parameter quantifies the accuracy of the feature extraction process itself. A lower
signifies a more precise estimation of the channel’s multipath delay features, which serve as the basis for the authentication decision. As this is a crucial parameter for the system’s performance, our first analysis is dedicated to isolating its effect. To clearly demonstrate this, the simulation process for
Figure 2 treats
as an independent variable. We directly vary its value to model different levels of estimation quality, from “Best Performance” to “Poor Performance”. It is important to note that in a practical, real-world system,
would be a dependent variable; its value would be determined by other factors, most notably the SNR of the received signal. This relationship will be explored in the subsequent analysis for
Figure 3.
It is clearly observable from the figure that
has a direct and significant impact on the performance of the authentication system. A lower value
indicates a more accurate estimation of the multipath delay features. As shown in
Figure 2, the ROC curve corresponding to the smallest
is closest to the top left corner. This signifies that for a given false alarm probability
, the detection probability
is maximized; conversely, for a given
,
is minimized, which represents the optimal authentication performance. Although the figure directly illustrates the effect of
, according to signal processing theory, the estimation error variance
is typically inversely proportional to the SNR of the received signal. Consequently, a lower
corresponds to a higher SNR, and vice versa. Therefore, the plot also implicitly demonstrates that higher SNR yields better performance.
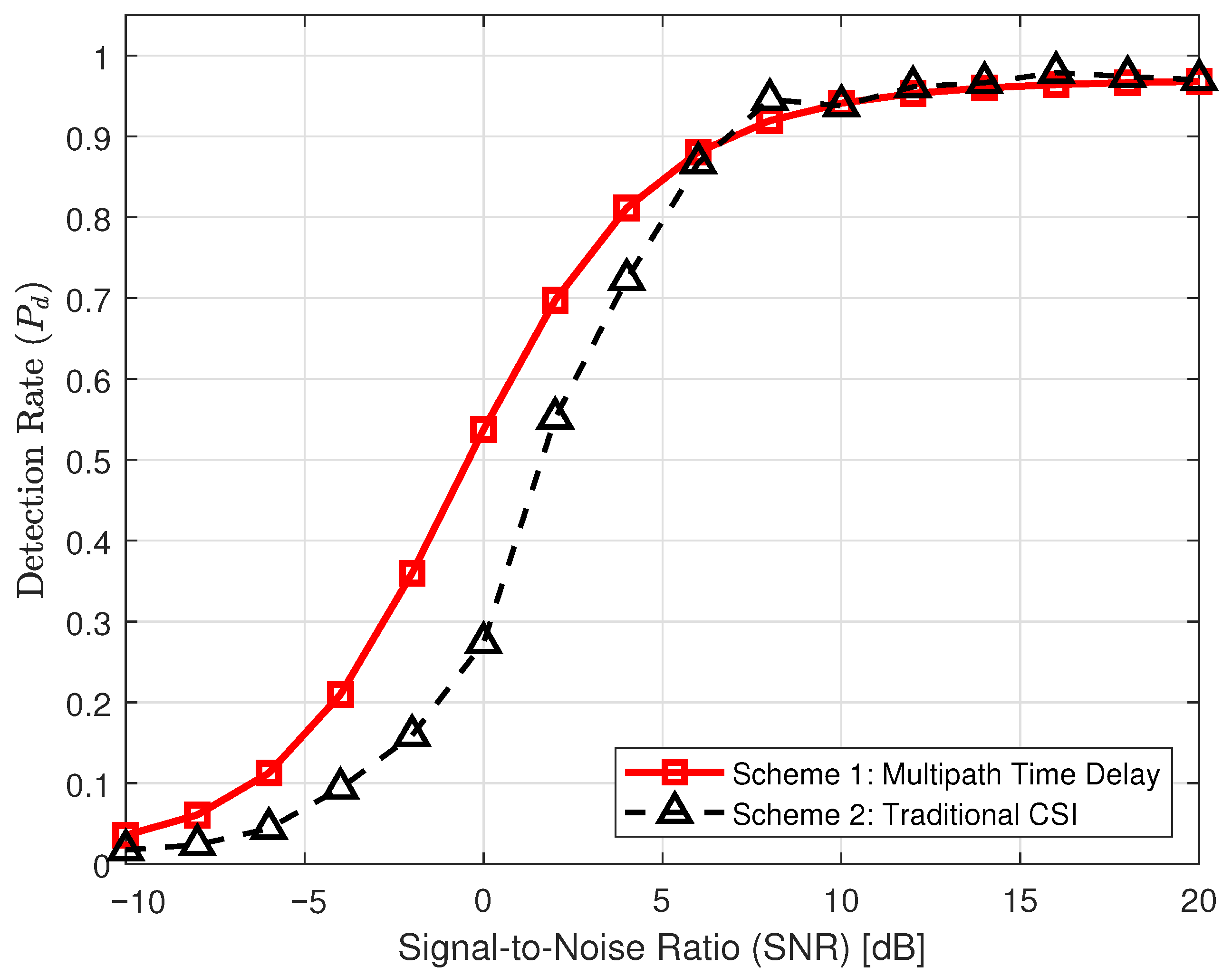
Figure 3 compares the detection performance of the traditional authentication scheme based on CSI in [
21,
22] with the authentication proposed based on multipath delay features in this paper, respectively. It illustrates the evolution of
as a function of the SNR, given a fixed false alarm rate of
. As anticipated, the detection performance for both mechanisms improves monotonically with increasing SNR. This trend validates the theoretical expectation that higher signal quality minimizes noise interference, thereby enabling more accurate channel estimation and enhancing the distinctiveness of legitimate users. Notably, the proposed Scheme 1 (Multipath Time Delay) demonstrates superior robustness in low-SNR regimes compared to Scheme 2 (Traditional CSI). As shown in the plot, between −10 dB and 5 dB, Scheme 1 maintains a significant performance lead. For instance, at 0 dB, the multipath-based scheme achieves a
of approximately 0.55, whereas the traditional CSI scheme reaches only 0.28. This advantage is attributed to the fine-grained nature of multipath delay features, specifically their differential and time-evolutionary characteristics, which are less sensitive to noise than the macroscopic holistic CSI correlations. Conversely, in high-SNR conditions (>10 dB), the performance of both methods converges and saturates near unity (
), implying that both methods can effectively identify illegitimate users when the SNR is sufficiently high. This indicates that while traditional CSI is effective when signal quality is pristine, the proposed multipath delay approach offers a critical advantage in challenging, noise-limited environments.
To further evaluate the robustness of the proposed methodology, we investigated the impact of key system variables on the authentication performance. First, regarding the correlation coefficient , which models the temporal stability of the channel, our analysis indicates that a higher significantly improves performance. As approaches 1, the legitimate channel becomes more correlated over time, reducing the variance of the test statistic Z under hypothesis . Consequently, this lowers the False Alarm Probability () for a fixed threshold. Second, the system bandwidth W plays a critical role in the resolution of multipath delay estimation. An increase in bandwidth results in finer time-domain resolution. This enhanced resolution reduces the estimation error variance , thereby shifting the ROC curves toward the optimal upper-left corner. However, it is worth noting that increasing bandwidth imposes higher requirements on the hardware sampling rate and processing complexity. Third, the number of multipath components M contributes to the diversity of the fingerprint. As M increases, the degrees of freedom in the chi-square distribution of the test statistic increase. Theoretical analysis suggests that a larger M provides more distinctive features, improving the distinguishability between the legitimate user and the spoofer, provided that the additional paths can be accurately estimated. Moreover, in our proposed scheme, the antenna geometry indirectly, yet critically, influences the ROC curves through the channel estimation accuracy. The delay estimation algorithm relies on the effective SNR after beamforming. Specifically, the total number of antenna elements determines the array gain. A larger array provides higher array gain, which effectively suppresses the noise variance in the signal subspace. Therefore, while the geometric parameters () primarily determine the manifold structure for the Angle of Arrival resolution, the quantity of antennas is the dominant geometric factor enhancing the multipath delay authentication performance by minimizing estimation errors.
6. Conclusions
This paper addresses the issue of identity spoofing attacks in mmWave SIMO systems by proposing a PLA mechanism based on multipath delay fingerprint features. By constructing a channel model, designing an efficient feature extraction method, and establishing an authentication framework founded on hypothesis testing theory, the proposed scheme achieves effective differentiation between legitimate and spoofing devices. Furthermore, theoretical expressions for the false alarm rate and detection rate are derived to characterize the authentication performance. The efficacy of the scheme is systematically evaluated through simulations under various SNR and channel estimation error conditions. The results demonstrate that the proposed solution exhibits strong robustness and practicality while maintaining low communication overhead, thereby significantly enhancing the security of mmWave SIMO communication systems.
While the proposed scheme demonstrates strong robustness, it is important to discuss its limitations. Firstly, as noted in
Section 2.1, our methodology assumes the absence of signal collisions, where the receiver discards collided frames. Developing a mechanism to authenticate reliably in the presence of such spoofing-by-collision attacks remains a significant challenge. Secondly, regarding mobility, our current work models the channel variation between two consecutive frames using a first-order Gauss–Markov process. This is effective for low-to-moderate mobility scenarios. However, in high-mobility environments, the channel may decorrelate significantly within a single transmission frame, not just between frames. This rapid intra-frame variation could degrade the accuracy of the channel feature estimation and subsequently increase the false alarm rate, as the reference fingerprint stored at time
would become rapidly outdated. Analyzing and mitigating the impact of such high-speed movement is a critical limitation of the current study.
Future research will proceed in several directions to address these limitations. Firstly, we will investigate authentication mechanisms robust to signal collisions. Secondly, we will explicitly analyze the impact of high-mobility scenarios and develop more adaptive online mechanisms that can track rapid intra-frame channel variations, potentially by shortening the observation window or employing predictive tracking filters. Finally, we will explore multi-modal authentication that integrates diverse physical layer features to improve the overall identification accuracy.