Certificateless Proxy Re-Encryption Scheme for the Internet of Medical Things
Abstract
1. Introduction
- We design a secure data sharing framework for IoMT using the CL-PRE mechanism that eliminates the key-escrow problem inherent in identity-based cryptosystems and avoids the complex certificate management of traditional PKI.
- The proposed scheme supports a flexible user revocation without incurring extra computational cost. This property is essential for managing user access rights in dynamic IoMT systems.
- The proposed CL-PRE scheme appeals to resource-constrained IoMT devices, as the encryption cost is specifically optimized.
- We formally prove that our scheme achieves indistinguishability against adaptive chosen-identity and chosen-ciphertext attacks (IND-PrID-CCA) under the Decisional Bilinear Diffie–Hellman (DBDH) assumption.
2. Related Works
2.1. Revocation Mechanism in PRE
2.2. Post-Quantum Secure PRE
3. Proposed CL-PRE System for IoMT
3.1. Preliminaries
- Bilinear PairingAssume that the notations of G1 and GT denote two multiplicative groups. The order of both groups is a prime p. The symbol g represents a generator of G1. We can express a bilinear pairing as e: G1 × G1 → GT, satisfying the characteristics outlined below:
- Bilinearity: Given u, v ∈ Zp, the value e(gu, gv) equals e(g, g)uv.
- Non-degeneracy: The value e(g, g) does not equal 1 for some generator g ∈ G1.
- Computability: There is an efficient algorithm to calculate the value e(X, Y) for all X, Y ∈ G1.
- Decisional Bilinear Diffie–Hellman (DBDH) ProblemTo determine whether W ∈ GT equals the value e(g, g)abc from a given tuple (g, ga, gb, gc, W).
- Decisional Bilinear Diffie–Hellman (DBDH) AssumptionThe advantage is negligible for any probabilistic attacker to solve a given DBDH instance in polynomial time.
3.2. System Party
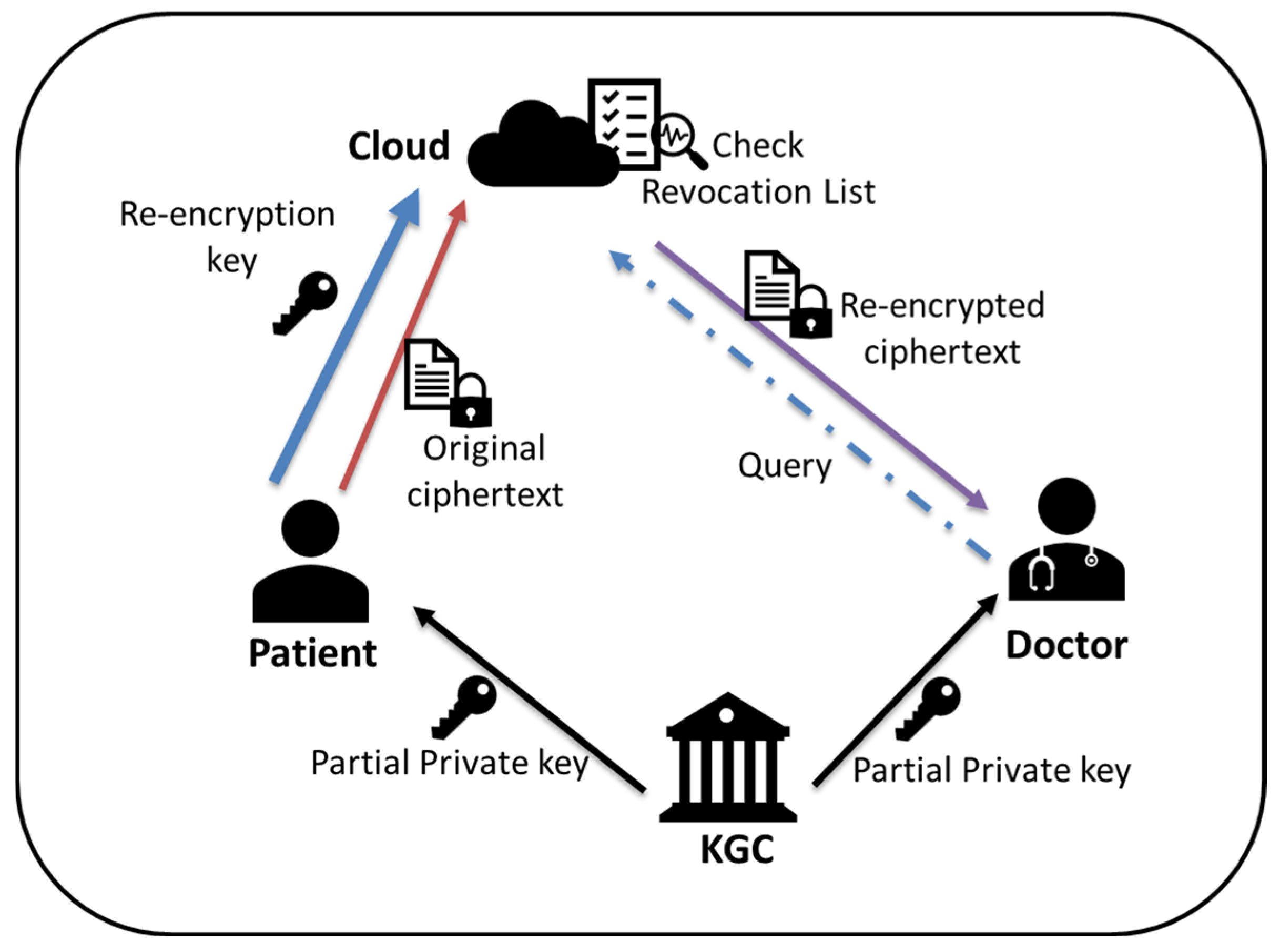
- Key Generator Center (KGC): The KGC is in charge of creating system’s public parameters and issuing the partial private key for all system parties. However, the KGC will be unable to learn the genuine private key of any user due to the secret value chosen by the user themselves.
- Data Owner (DO): A data owner is a patient who produces their health data via all kinds of wearable IoMT devices. These IoMT devices will encrypt sensed data with the data owner’s public key and then transmit the ciphertext to the cloud. If someone requests the encrypted health data in the cloud, the data owner/patient can authorize a re-encryption key to the cloud for performing ciphertext transformation.
- Data User (DU): A data user is an institution or medical staff who attempt to access the encrypted health data stored in the cloud. If access request is granted, they will receive the re-encrypted ciphertext that is decryptable by their own private keys.
- Cloud Server (CS): The CS is viewed as a semi-trusted proxy responsible for storing the encrypted health data as well as maintaining the obtained re-encryption keys authorized by the data owner. It also performs ciphertext re-encryption process without learning the content of health data.
3.3. Algorithm Definitions
- Setup: The KGC utilizes a security parameter l as its input to generate a master secret key (Msk) and initializes the system public parameters (PP).
- PPKeyGen: The KGC utilizes PP and Msk to produce a partial private key (du) for the user IDu.
- Set-Secret-Value: Each user IDu determines a secret value (ssu) for themselves.
- Set-Private-Key: Each user IDu sets their full private key (sku).
- Set-Public-Key: Each user IDu sets their full public key (pku).
- Encryption: The DO creates a ciphertext (CT) by taking the inputs of PP, a plaintext (M), an identity (IDo), a symmetric key (K), and a secret value (sso).
- Query: The DU creates a query token W by taking the input of an identity (IDu) and a random number.
- ReKeyGen: The DO creates a re-encryption key (Rk) by taking the inputs of PP, an identity (IDu), a query token (W), the public key (pku) of IDu, and a secret value (sso) of the DO.
- Re-encryption: The CS generates a re-encrypted ciphertext (CT’) by taking the inputs of a re-encryption key and a ciphertext (CT).
- Decryption: The DU recovers the original plaintext (M) by taking the inputs of a transformed ciphertext (CT’), a token seed together with a private key (sku). Similarly, the DO can also recover the original plaintext (M) by taking the inputs of a ciphertext (CT) and a private key (sko).
- Revocation: The KGC creates a renewed revocation list (RVL) by taking the input of a revoked identity IDru.
3.4. Security Model
- Initialization: At first, performs the Setup algorithm to obtain PP as well as the Msk. The former is given to 𝒜.
- Phase 1: 𝒜 is permitted to adaptively make the following queries:
- PPKeyGen Queries: 𝒜 submits an identity IDu to who returns the corresponding partial private key du.
- Full Private Key Queries: 𝒜 submits an identity IDu to who returns the corresponding full partial private key sku.
- Public Key Queries: 𝒜 submits an identity IDu to who returns the corresponding full public key pku.
- Replace Public Key Queries: 𝒜 submits an identity IDu and a public key pk’u1 to who replaces the corresponding public key pku1 with pk’u1. Note that after the public key of IDu has been replaced, 𝒜 cannot query the corresponding full private key.
- Re-encryption Key Queries: 𝒜 submits two legitimate identities (IDo, IDu) to who outputs a related transformation key Rk.
- Decryption Queries: 𝒜 submits a re-encrypted ciphertext CT’ to who returns either a plaintext M or an error symbol ⊥.
- Challenge: 𝒜 submits a chosen identity ID*, two plaintexts (M0*, M1*) of equal lengths to who creates a challenge ciphertext CT* by internally generating a symmetric key K*, flipping a coin λ ∈ {0, 1}, and encrypting Mλ* using K* under ID*. The challenge ciphertext is then given to 𝒜. This challenge is valid only under the condition that ID* was not the subject of any PPKeyGen, Full Private Key, or Re-encryption Key queries during Phase 1.
- Phase 2: 𝒜 makes new queries as those stated in Phase 1 under the constraints below:
- A PPKeyGen query for ID* is disallowed.
- A Full Private Key query for ID* is disallowed.
- A Re-encryption key query with respect to ID* would be disallowed.
- A Decryption query with respect to (ID*, CT*) is disallowed.
- The maximum query times for PPKeyGen, Full Private Key, Public Key, Replace Public Key, Re-encryption Key, and Decryption queries are bounded by qpsk, qsk, qpk, qrpk, qrek, and qd.
- Guess: After Phase 2 ends, 𝒜 guesses a bit λ’. As long as λ’ = λ, 𝒜 succeeds in the game. We therefore express the advantage of 𝒜 as Adv(𝒜) = |Pr[λ’ = λ] − 1/2|.
- Initialization: At first, performs the Setup algorithm to obtain PP and the Msk and then gives both to 𝒜.
- Phase 1: The adversary 𝒜 is permitted to adaptively ask the following queries:
- Full Private Key Queries: 𝒜 submits an identity IDu to who returns the corresponding full partial private key sku.
- Public Key Queries: 𝒜 submits an identity IDu to who returns the corresponding full public key pku.
- Re-encryption Key Queries: 𝒜 submits two legitimate identities (IDo, IDu) to who outputs the related transformation key Rk.
- Decryption Queries: 𝒜 submits a re-encrypted ciphertext CT’ to who outputs either a plaintext M or an error symbol ⊥.
- Challenge: 𝒜 sends a chosen identity ID*, two plaintexts (M0*, M1*) of equal lengths to who creates a challenge ciphertext CT* by internally generating a symmetric key K*, flipping a coin λ ∈ {0, 1}, and encrypting Mλ* using K* under ID*. The challenge ciphertext is then given to 𝒜. This challenge is valid only under the condition that ID* was not the subject of any Full Private Key or Re-encryption Key queries during Phase 1.
- Phase 2: The adversary 𝒜 makes new queries as those stated in Phase 1 under the constraints below:
- A Full Private Key query for ID* is disallowed.
- A Re-encryption Key query with respect to ID* is disallowed.
- A Decryption query with respect to (ID*, CT*) is disallowed.
- The maximum query times for Full Private Key, Public Key, Re-encryption Key, and Decryption queries will be bounded by qsk, qpk, qrek, and qd.
- Guess: After Phase 2 ends, 𝒜 guesses a bit λ’. As long as λ’ = λ, 𝒜 succeeds in the game. We therefore express the advantage of 𝒜 as Adv(𝒜) = |Pr[λ’ = λ] − 1/2|.
3.5. Construction
- Setup(1ζ) → (PP, Msk)Taking the security parameter l as an input, the KGC chooses α ∈ R Zp to be the Msk and produces PP = (e, G1, GT, g, H1~2, Mpk, SE, SD) as follows. Here, PP stands for the set of all system-wide public parameters, which includes the Master Public Key (Mpk) as one of its components.
- (1)
- Two multiplicative groups are separately expressed as G1 and GT. Each of them has prime order p and let g be a generator of G1. A symmetric bilinear pairing could be written as e: G1 × G1 → GT.
- (2)
- Two collision-resistant cryptographic hash functions are denoted as H1 and H2. The former accepts variable-length inputs and maps the result to an element in G1 while the latter also maps the result to an element in G1 but only accepts an element from GT.
- (3)
- The master public key Mpk is derived as N = gα.
- (4)
- A symmetric encryption and decryption functions are denoted as SE and SD, respectively.
- PPKeyGen(PP, Msk, IDu) → (du)A user can request his partial private key by the following processes with the KGC:
- (1)
- A user transmits his identity IDu to the KGC.
- (2)
- The KGC calculates du = H1(IDu || IDKGC)α and sends du back to IDu.
- (3)
- The correctness of generated partial private key could be verified if
e(du, g) = e(H1(IDu || IDKGC), N) - Set-Secret-Value(PP, IDu) → (ssu)A user IDu designates his secret value as ssu ∈ R Zp.
- Set-Private-Key(PP, IDu, du, ssu) → (sku)A user IDu sets sku = (du, ssu) as his/her full private key.
- Set-Public-Key(PP, IDu, ssu) → (pku)A user IDu first calculates Yu = gssu and then sets pku = (Yu, H1(IDu || IDKGC)) as his/her full public key.
- Encryption(PP, IDo, K, M, sso) → (CT)To create a ciphertext CT = (CT1, CT2) for the data M composed of (M1, M2, …, Mn), the DO, with identity IDo, uses PP, a symmetric key K, along with his secret value sso to perform the following processes. The DO first selects h ∈ Zp and derivesEO, 1 = K · e(N, H1(IDo || IDKGC)hsso)EO, 2 = ghCT1 = (EO, 1, EO, 2)CT2 = (SE(K, M1)…, SE(K, Mn))Here, the ciphertext CT = (CT1, CT2), an associated file index FM, and the identity IDo are delivered to the CS for storage.
- Query(PP, IDu, FM) → (W)To retrieve the ciphertext for a given file index FM, the DU, with identity IDu, first chooses a query number v ∈ Zp and then derivesV = gvThe query token W = (V, IDu, FM) will be sent to the CS who will check whether IDu is in the revocation list RVL. If it does, the CS will reject the request. Otherwise, the CS forwards the token W to the DO. The component V (derived from the user’s secret v) serves a dual purpose: it is first used by the data owner (DO) in the ReKeyGen algorithm to generate the re-encryption key, and the corresponding secret v is later required by the data user (DU) to perform the final decryption.
- ReKeyGen(PP, W, sko) → (Rk)The DO first chooses z, r ∈ Zp and then calculatesRk1 = NzRk2 = (do)sso · Rk1/H2(e(N, H1(IDu || IDKGC)VrYu))= ((do)sso · Nz)/H2(e(N, H1(IDu || IDKGC)gvrYu))Rk3 = e(gr, N)Here, the ciphertext transformation key Rk composed of Rk1, Rk2, and Rk3 will be forwarded to the CS.
- Re-encryption(PP, IDu, Rk, CT) → CT′To re-encrypt the ciphertext CT for DU, the CS uses the authorized re-encryption key Rk to computeE′O, 1 = EO, 1 · e(Rk1, EO, 2)= K · e(Nsso, H1(IDo || IDKGC)h)e(Nz, gh)E′O, 2 = EO, 2 = ghE′O, 3 = Rk2 = ((do)sso · Nz)/H2(e(N, H1(IDu || IDKGC)gvrYu))E′O, 4 = Rk3 = e(gr, N)CT′1 = (E′O, 1, E′O, 2, E′O, 3, E′O, 4)Finally, the CS sends the re-encrypted ciphertext CT’ = (CT’1, CT2) to the DU.
- Decryption(CT, sku) → (M = M1, M2, …, Mn)If the DO wants to decrypt their own ciphertext CT, they can use their partial private key do to recover the symmetric key K asand then decrypt {Mi = SD(K, SE(K, Mi))}i = 1, …, n.For the DU to decrypt a requested ciphertext CT’, they first use their full private key sku = (du, ssu) and the previously selected query number v to compute= (do)sso · Nz= (H1(IDo || IDKGC)α)sso · Nzand then decrypt {Mi = SD(K, SE(K, Mi))}i = 1, …, n. The correctness for the derivation of the symmetric key K can be confirmed as follows:
- Revocation(IDru) → RVL
4. Security Proof and Comparison
4.1. Security Proof
- Initialization: By performing the Setup(1l) algorithm, first sets Mpk to be N = ga, which implicitly defines the Msk to be the integer a that does not know. Then, sends PP = (e, G1, GT, g, p, H2, Mpk, SE, SD) to 𝒜.
- Phase 1: responds the queries 𝒜 made below:
- H1 Oracles: To respond to an H1(IDu || IDKGC) query, the challenger searches the stored H1-list for previous records. If no matched entry exists, tosses a coin cc with Pr[cc = 1] = π. When cc equals 0, derives the return value Oh1 = , in which h1 ∈R Zp. Otherwise, sets Oh1 = . The entry (IDu, cc, h1, Oh1) is also added to the H1-list.
- PPKeyGen Queries: To respond to a PPKeyGen query of IDi, the challenger first makes an H1(IDi || IDKGC) query and then aborts as long as cc equals 0. Otherwise, derives the return value di =
- Full Private Key Queries: To respond to a Full Private Key query of IDi, the challenger first makes an H1(IDi || IDKGC) query and then aborts as long as cc equals 0. Otherwise, obtains the secret value ssi by the Set-Secret-Value(PP, IDi) algorithm and sets the return value ski = (, ssi).
- Public Key Queries: To respond to a Public Key query of IDi, the challenger obtains Oh1 and the secret value ssi by H1(IDi || IDKGC) oracle and the Set-Secret-Value(PP, IDi) algorithm, respectively. Then and sets the return value pki = (Oh1, Yi = gssi).
- Replace Public Key Queries: To respond to a Replace Public Key query of (IDi, Yi, Yi’), in which the Full Private Key query of IDi has never been made, the challenger replaces the associated public key Yi with Yi’.
- Re-encryption Key Query: To respond to a Re-encryption Key query of (IDo, IDu, FM), in which IDu ∉ RVL, first makes an H1(IDo || IDKGC) query and might abort if cc equals 0. If not, obtains the secret value sso by the Set-Secret-Value(PP, IDo) algorithm and derives full private key sko = (, sso). Next, calculates the token W by performing the Query(PP, IDu, FM) algorithm and finally derives the returned ciphertext transformation key Rk composed of (Rk1, Rk2, Rk3) with the algorithm of ReKeyGen(PP, W, sko).
- Decryption Query: To respond to a Decryption query of (IDu, CT’), in which IDu ∉ RVL, first makes an H1(IDu || IDKGC) query and might abort if cc equals 0. If not, obtains the secret value ssu by the Set-Secret-Value(PP, IDu) algorithm and derives full private key sku = (, ssu). Next, outputs the result of Decryption(CT’, sku) process.
- Challenge: 𝒜 submits a chosen identity, say ID*, two plaintexts (M0*, M1*) of equal lengths to who creates a challenge ciphertext CT* = (EO, 1*, EO, 2*, CT2*) by internally generating a symmetric key K*, flipping a coin λ ∈ {0, 1}, and encrypting Mλ* using K* under ID* as follows. The challenge ciphertext is then given to 𝒜.
- Without loss of generality, it is assumed that the H1(ID* || IDKGC) oracle has been made by 𝒜. In this case, whenever the value cc* equals 1, the challenger directly aborts.
- Otherwise, the associated value h1 could be fetched from the H1-list. Then sets the secret value of ID* to be ss* ∈R Zp and computes
- 3.
- Here, the challenge ciphertext CT* = (EO, 1*, EO, 2*, CT2*) is given to 𝒜.
- Phase 2: 𝒜 makes new queries as those described in previous phase under the limits outlined in Definition 1.
- Guess: After Phase 2 ends, 𝒜 guesses a bit λ’. Provided that λ’ = λ, outputs 1 implying that Q equals e(g, g)abc. If Q ≠ e(g, g)abc, outputs 0.
- Analysis: Based on the ciphertext CT* properly simulated in the challenge phase, it will be valid if only Q equals e (g, g)abc. In this case, the adversary 𝒜 owns an assumed advantage to break our scheme, meaning that Adv(𝒜) = | Pr[λ’ = λ] | ≥ ε. On the contrary, as long as Q is inequivalent to e (g, g)abc, the formed ciphertext CT* will be invalid, which denotes that 𝒜 owns no better advantage, and we get | Pr[λ’ = λ] | = . To obtain a reliable estimation, we use Pr[¬AT] to stand for the probability that will not abort during the entire game. We can thus describe the success advantage for to solve the given DBDH instance as
- Initialization: By performing the Setup(1l) algorithm, first sets Mpk to be N = gα, which defines the Msk to be the integer α chosen by . Then, sends PP = (e, G1, GT, g, p, H2, Mpk, SE, SD) and the Msk α to 𝒜.
- Phase 1: responds the queries 𝒜 made below:
- H1Oracles: To respond an H1(IDu || IDKGC) query, the challenger searches the stored H1-list for previous records. If no matched entry exists, tosses a coin cc with Pr[cc = 1] = π. When cc equals 0, derives the return value Oh1 = , in which h1 ∈R Zp. Otherwise, sets Oh1 = The entry (IDu, cc, h1, Oh1) is also added to the H1-list.
- Full Private Key Queries: To respond a Full Private Key query of IDi, the challenger first makes an H1(IDi || IDKGC) query and then aborts as long as cc equals 0. Otherwise, obtains the secret value ssi by the Set-Secret-Value(PP, IDi) algorithm and sets the return value ski = (, ssi).
- Public Key Queries: To respond a Public Key query of IDi, the challenger obtains Oh1 and the secret value ssi by H1(IDi || IDKGC) oracle and the Set-Secret-Value(PP, IDi) algorithm, respectively. Then and sets the return value pki = (Oh1, Yi = gssi).
- Re-encryption Key Query: To respond a Re-encryption Key query of (IDo, IDu, FM), in which IDu ∉ RVL, first makes an H1(IDo || IDKGC) query and might abort if cc equals 0. If not, obtains the secret value sso by the Set-Secret-Value(PP, IDo) algorithm and derives full private key sko = (, sso). Next, calculates the token W by performing the Query(PP, IDu, FM) algorithm and finally derives the returned ciphertext transformation key Rk composed of (Rk1, Rk2, Rk3) with the algorithm of ReKeyGen(PP, W, sko).
- Decryption Query: To respond a Decryption query of (IDu, CT’), in which IDu ∉ RVL, first makes an H1(IDu || IDKGC) query and might abort if cc equals 0. If not, obtains the secret value ssu by the Set-Secret-Value(PP, IDu) algorithm and derives full private key sku = (, ssu). Next, outputs the result of Decryption(CT’, sku) process.
- Challenge: 𝒜 submits a chosen identity, say ID*, two plaintexts (M0*, M1*) of equal lengths to who create a challenge ciphertext CT* = (EO, 1*, EO, 2*, CT2*) by internally generating a symmetric key K*, flipping a coin λ ∈ {0, 1}, and encrypting Mλ* using K* under ID* as follows. The challenge ciphertext is then given to 𝒜.
- Without loss of generality, it is assumed that the H1(ID* || IDKGC) oracle has been made by 𝒜. In this case, whenever the value cc* equals 1, the challenger directly aborts.
- Otherwise, the associated value h1 could be fetched from the H1-list. Then sets the public key Y* of ID* to be ga, which implicitly defines the secret value ss* to be a and then computes
- 3.
- Here, the challenge ciphertext CT* = (EO, 1*, EO, 2*, CT2*) is given to 𝒜.
- Phase 2: 𝒜 makes new queries as those described previous phase under the limits outlined in Definition 2.
- Guess: After Phase 2 ends, 𝒜 guesses a bit λ’. Provided that λ’ = λ, outputs 1 implying that Q equals e(g, g)abc. If Q ≠ e(g, g)abc, outputs 0.
- Analysis: Based on the ciphertext CT* properly simulated in the challenge phase, it will be valid if only Q equals e(g, g)abc. In this case, the adversary 𝒜 owns an assumed advantage to break our scheme, meaning that Adv(𝒜) = |Pr[λ’ = λ] | ≥ ε. On the contrary, as long as Q is inequivalent to e(g, g)abc, the formed ciphertext CT* will be invalid, which denotes that 𝒜 owns no better advantage, and we get |Pr[λ’ = λ]| = . To obtain a reliable estimation, we use Pr[¬AT] to stand for the probability that will not abort during the entire game. We can thus describe the success advantage for to solve the given DBDH instance as
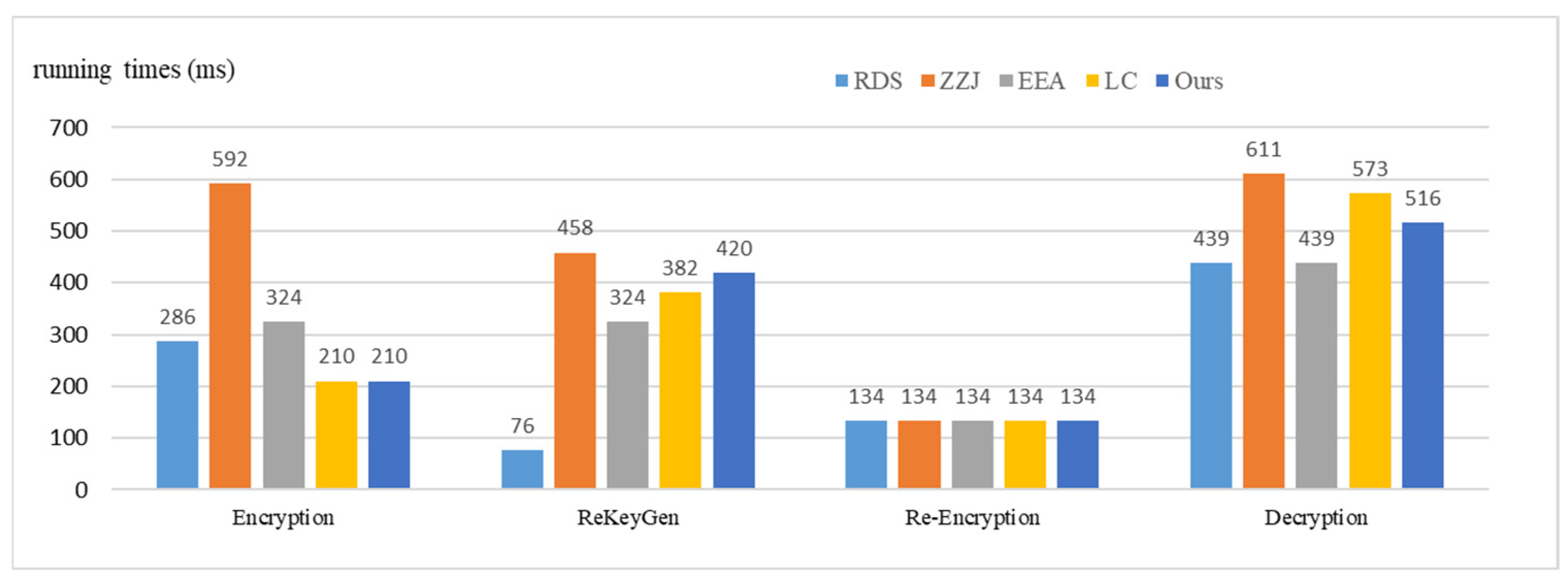
4.2. Comparison
- (1)
- Implementation Language: C.
- (2)
- Pairing Type: MNT224 curve (a Type 3 pairing).
- (3)
- Security Level: 96-bit.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Chaudhary, S.; Johari, R.; Bhatia, R.; Gupta, K.; Bhatnagar, A. CRAIoT: Concept, review and application(s) of IoT. In Proceedings of the 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Ghaziabad, India, 30 October 2019; pp. 1–4. [Google Scholar]
- Joseph, V.C.; Ahn, S.H.; Kim, J.; Lee, K.H.; Kim, D.H. Intelligent healthcare systems: Re-defining personal healthcare solutions. In Proceedings of the 7th International Conference on Advanced Communication Technology (ICACT 2005), PyeongChang, Republic of Korea, 21–23 February 2005; pp. 424–427. [Google Scholar]
- Luo, Z.; Ou, D.; Lin, T.; Lin, X. Research on wireless dynamic magnetic resonance charging technology for autonomous vehicles. In Proceedings of the 4th International Conference on Electronic Information Engineering and Computer Technology (EIECT), Shenzhen, China, 15–17 November 2024; pp. 774–777. [Google Scholar]
- Park, D.H.; Bang, H.C.; Pyo, C.S.; Kang, S.J. Semantic open IoT service platform technology. In Proceedings of the IEEE World Forum on Internet of Things (WF-IoT), Seoul, Republic of Korea, 6–8 March 2014; pp. 85–88. [Google Scholar]
- Santosa, I.; Supangkat, S.H.; Arman, A.A. People-centric smart city services measurement using Garuda smart city framework. In Proceedings of the Mediterranean Smart Cities Conference (MSCC), Tangier, Morocco, 25–27 September 2024; pp. 1–5. [Google Scholar]
- Villanueva-Miranda, I.; Nazeran, H.; Martinek, R. A semantic interoperability approach to heterogeneous Internet of Medical Things (IoMT) platforms. In Proceedings of the IEEE 20th International Conference on e-Health Networking, Applications and Services (Healthcom), Ostrava, Czech Republic, 17–20 September 2018; pp. 1–5. [Google Scholar]
- Hwata, C.; Armando, E.J.; Gatera, O.; Rushingabigwi, G.; Twizere, C.; Mtonga, K. Real-time monitoring and prediction of electromagnetic compatibility over Internet of medical things using Kalman filter algorithm. In Proceedings of the 17th International Conference on Signal Processing and Communication System (ICSPCS), Gold Coast, Australia, 9–11 December 2024; pp. 1–4. [Google Scholar]
- Harvey, P.; Toutsop, O.; Kornegay, K.; Alale, E.; Reaves, D. Security and privacy of medical Internet of Things devices for smart homes. In Proceedings of the 7th International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Paris, France, 14–16 December 2020; pp. 1–6. [Google Scholar]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. 2006, 9, 1–30. [Google Scholar] [CrossRef]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; pp. 127–144. [Google Scholar]
- Chen, B.; He, D.; Kumar, N.; Wang, H.; Choo, K.K.R. A blockchain-based proxy re-encryption with equality test for vehicular communication systems. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2048–2059. [Google Scholar] [CrossRef]
- Chow, S.S.; Weng, J.; Yang, Y.; Deng, R.H. Efficient unidirectional proxy re-encryption. In Proceedings of the International Conference on Cryptology in Africa, Stellenbosch, South Africa, 3–6 May 2010; pp. 316–332. [Google Scholar]
- Han, G.; Li, L.; Qin, B.; Zheng, D. Pairing-free proxy re-encryption scheme with equality test for data security of IoT. J. King Saud Univ. Comput. Inf. Sci. 2024, 36, 102105. [Google Scholar] [CrossRef]
- Zheng, R.; Jin, H.; Zhang, Q.; Liu, Y.; Chu, P. Heterogeneous medical data share and integration on grid. In Proceedings of the International Conference on BioMedical Engineering and Informatics, Sanya, China, 27–30 May 2008; pp. 905–909. [Google Scholar]
- Liu, A.; Du, X.; Wang, N.; Qiao, R.; Ning, Y.; Zhang, L. Medical health data sharing scheme based on blockchain and attribute-based encryption. In Proceedings of the 4th International Conference on Information Communication and Signal Processing (ICICSP), Beijing, China, 20–22 August 2021; pp. 553–559. [Google Scholar]
- Muthukumar, K.A.; Nandhini, M. Modified secret sharing algorithm for secured medical data sharing in cloud environment. In Proceedings of the 2nd International Conference on Science Technology Engineering and Management (ICONSTEM), Chennai, India, 17–18 March 2016; pp. 67–71. [Google Scholar]
- Wang, L.; Wang, L.; Mambo, M.; Okamoto, E. New identity-based proxy re-encryption schemes to prevent collusion attacks. In Proceedings of the Pairing-Based Cryptography—Pairing 2010, Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6487, pp. 595–609. [Google Scholar]
- Seo, J.W.; Yum, D.H.; Lee, P.J. Proxy-invisible CCA-secure type-based proxy re-encryption without random oracles. Theor. Comput. Sci. 2013, 491, 83–93. [Google Scholar] [CrossRef]
- Zeng, P.; Choo, K.K.R. A new kind of conditional proxy re-encryption for secure cloud storage. IEEE Access 2018, 6, 70017–70024. [Google Scholar] [CrossRef]
- Liang, K.; Susilo, W.; Liu, J.K.; Wong, D.S. Efficient and fully CCA secure conditional proxy re-encryption from hierarchical identity-based encryption. Comput. J. 2015, 58, 2778–2792. [Google Scholar] [CrossRef]
- Qiu, J.; Hwang, G.H.; Lee, H. Efficient conditional proxy re-encryption with chosen-ciphertext security. In Proceedings of the 9th Asia Joint Conference on Information Security (AsiaJCIS), Wuhu, China, 9–10 September 2014; pp. 104–110. [Google Scholar]
- Zhou, D.; Chen, K.; Liu, S.; Zheng, D. Identity-based conditional proxy re-encryption. Chin. J. Electron. 2013, 22, 61–66. [Google Scholar]
- Mo, L.; Yao, G. Multi-use conditional proxy re-encryption. In Proceedings of the International Conference on Information Science and Cloud Computing Companion (ISCC-C), Guangzhou, China, 7–8 December 2013; pp. 246–251. [Google Scholar]
- Zhang, J.; Bai, W.; Wang, X. Identity-based data storage scheme with anonymous key generation in fog computing. Soft Comput. 2020, 24, 5561–5571. [Google Scholar] [CrossRef]
- Lin, H.Y.; Tsai, T.T.; Ting, P.Y.; Chen, C.C. An improved ID-based data storage scheme for fog-enabled IoT environments. Sensors 2022, 22, 4223. [Google Scholar] [CrossRef] [PubMed]
- Lin, H.Y.; Chen, P.R. Revocable and fog-enabled proxy re-encryption scheme for IoT environments. Sensors 2024, 24, 6290. [Google Scholar] [CrossRef] [PubMed]
- Zhou, Y.; Zhao, L.; Jin, Y.; Li, F. Backdoor-resistant identity-based proxy re-encryption for cloud-assisted wireless body area networks. Inf. Sci. 2022, 604, 80–96. [Google Scholar] [CrossRef]
- Ren, C.; Dong, X.; Shen, J.; Cao, Z.; Zhou, Y. CLAP-PRE: Certificateless autonomous path proxy re-encryption for data sharing in the cloud. Appl. Sci. 2022, 12, 4353. [Google Scholar] [CrossRef]
- Eltayieb, N.; Elhabob, R.; Abdelgader, A.M.S.; Liao, Y.; Li, F.; Zhou, S. Certificateless proxy re-encryption with cryptographic reverse firewalls for secure cloud data sharing. Future Gener. Comput. Syst. 2025, 162, 107478. [Google Scholar] [CrossRef]
- Yao, S.; Dayot, R.V.J.; Kim, H.J.; Ra, I.H. A Novel Revocable and Identity-Based Conditional Proxy Re-Encryption Scheme with Ciphertext Evolution for Secure Cloud Data Sharing. IEEE Access 2021, 9, 42801–42816. [Google Scholar] [CrossRef]
- Worapaluk, K.; Fugkeaw, S. An Efficiently Revocable Cloud-based Access Control Using Proxy Re-encryption and Blockchain. In Proceedings of the 20th International Joint Conference on Computer Science and Software Engineering (JCSSE), Bangkok, Thailand, 28–30 June 2023. [Google Scholar]
- Liang, Y.; Tian, B.; Hao, Y.; Wu, K. Multi-user Search on the Encrypted Network: A Lattice-based Proxy Re-encryption with Keyword Search. In Proceedings of the 2023 8th International Conference on Communication, Image and Signal Processing (CCISP), Chengdu, China, 15–17 December 2023; pp. 97–101. [Google Scholar]
- Zhang, K.; Liu, Y.; Wang, L.; Li, L. Identity-Based Proxy Re-Encryption Based on LWE with Short Parameters. In Proceedings of the 2023 International Conference on Mobile Internet, Cloud Computing and Information Security (MICCIS), Nanjing, China, 27–29 October 2023; pp. 118–124. [Google Scholar]
- Zhu, F.; Yi, X.; Abuadbba, A.; Khalil, I.; Nepal, S.; Huang, X. Cost-effective authenticated data redaction with privacy protection in IoT. IEEE Internet Things J. 2021, 8, 11678–11689. [Google Scholar] [CrossRef]
| Symbol | Description |
|---|---|
| l | security parameter |
| PP | system-wide public parameters |
| p | large prime |
| G1, GT | multiplicative group |
| g | generator |
| e | bilinear pairing |
| H1, H2 | one-way hash function |
| α | Msk |
| N (= gα) | Mpk |
| SE, SD | symmetric encryption and decryption functions |
| di | partial private key of IDi |
| ssi | secret value of IDi |
| ski | full private key of IDi |
| Yi (= gssi) | partial public key of IDi |
| pki | full public key of IDi |
| K | symmetric key |
| M = (M1, M2, …, Mn) | message |
| CT = (CT1, CT2) | ciphertext |
| CT1 = (EO, 1, EO, 2) | partial ciphertext |
| EO, 1, EO, 2 | partial ciphertext components |
| FM | File index of message M |
| v | secret query number |
| V | query token component |
| W | query token |
| h, z, r | random numbers |
| Rk = (Rk1, Rk2, Rk3) | re-encryption key |
| CT′ = (CT′1, CT2) | re-encrypted ciphertext |
| CT′1 = (E′O, 1, E′O, 2, E′O, 3, E′O, 4) | re-encrypted partial ciphertext |
| E′O, 1, E′O, 2, E′O, 3, E′O, 4 | re-encrypted partial ciphertext components |
| X | intermediate decryption value |
| RVL | revocation list |
| RDS | ZZJ | EEA | LC | Ours | |
|---|---|---|---|---|---|
| Encryption | B + 4M | 3B + 3M + 2E | B + 4M + E | B + 2M | B + 2M |
| ReKeyGen | 2M | 2B + 3M + 2E | B + 5M | 2B + 3M | 2B + 4M |
| Re-encryption | B | B | B | B | B |
| Decryption | 3B + M | 4B + 2M | 3B + M | 4B + E | 3B + 2M + E |
| Ciphertext Size | >>4096 bits | ≈2048 bits | ≈3072 bits | ≈2048 bits | ≈2048 bits |
| Re-encryption Key Size | >>4096 bits | ≈3072 bits | ≈3072 bits | ≈3072 bits | ≈3072 bits |
| Re-encrypted Ciphertext Size | >>4096 bits | ≈4096 bits | ≈4096 bits | ≈4096 bits | ≈4096 bits |
| Certificateless | √ | × | √ | × | √ |
| Revocation | × | × | √ | √ | √ |
| Security Level | CPA | CPA | CPA | CPA | CCA |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, H.-Y.; Yeh, C.-W.; Chen, C.-S. Certificateless Proxy Re-Encryption Scheme for the Internet of Medical Things. Electronics 2025, 14, 4654. https://doi.org/10.3390/electronics14234654
Lin H-Y, Yeh C-W, Chen C-S. Certificateless Proxy Re-Encryption Scheme for the Internet of Medical Things. Electronics. 2025; 14(23):4654. https://doi.org/10.3390/electronics14234654
Chicago/Turabian StyleLin, Han-Yu, Ching-Wei Yeh, and Chi-Shiu Chen. 2025. "Certificateless Proxy Re-Encryption Scheme for the Internet of Medical Things" Electronics 14, no. 23: 4654. https://doi.org/10.3390/electronics14234654
APA StyleLin, H.-Y., Yeh, C.-W., & Chen, C.-S. (2025). Certificateless Proxy Re-Encryption Scheme for the Internet of Medical Things. Electronics, 14(23), 4654. https://doi.org/10.3390/electronics14234654





