A Lightweight Mutual Authentication Mechanism for Applications Utilizing Low-Power IoT Devices
Abstract
1. Introduction
2. Related Work
- Reliance on computationally intensive cryptographic operations (such as ECC), which may not be feasible for LP-IoT devices.
- High communication overhead, making it unsuitable for bandwidth-constrained networks.
- Limited scalability in dynamic IoT environments, where frequent device additions and removals can introduce security and performance concerns.
- Some mechanisms, despite being lightweight, still requiring iterative computations or modular arithmetic, making them impractical for ultra-low-power IoT devices.
3. Proposed Mechanism
3.1. System Introduction
3.2. The Lightweight Mutual Authentication Mechanism
3.2.1. Registration Phase
3.2.2. Mutual Authentication Phase
3.2.3. Data Transmission Phase
3.2.4. Device Purge Phase
4. Analyses and Discussion
4.1. Adversarial Model
4.1.1. Adversary Capabilities
- Eavesdropping: The adversary can passively intercept communications between and the servers (AS, DCS).
- Replay: The adversary may resend previously captured messages in an attempt to bypass authentication.
- Message Injection/Modification: The adversary may inject or alter transmitted messages to impersonate a device or server.
- Active Initiation: The adversary may actively send fabricated authentication requests to the AS or DCS.
- Limited Compromise: The adversary may obtain local information from a single compromised , such as its or partial stored values.
4.1.2. Adversary Limitations
- The adversary cannot reverse the on-way hash function.
- The adversary cannot derive the global secret parameters or system master secrets held securely by the AS.
- The initialization process is assumed to be performed in a trusted environment, ensuring each is securely provisioned with its and .
4.1.3. Adversary Goals
- Forge a legitimate or AS to gain unauthorized access.
- Replay outdated messages to trick the system into accepting invalid credentials.
- Intercept or alter transmitted data without detection.
- Escalate a local compromise of one device into a broader system breach.
4.2. Resistance Against Common Attacks
- Eavesdropping Attack/Passive AttackThe eavesdropping attack focuses on collecting data in a network environment, which may result in sensitive data leakage. Our proposed mechanism involves encrypting messages and data using XOR and a hash function during transmission. When a malicious attacker sniffs network packets, all the information is encrypted and cannot be decrypted effectively. This confirms that our proposed mechanism is effective in defending against eavesdropping attacks.
- Dictionary and Exhaustive AttackDictionary and exhaustive attacks focus on systematically guessing or enumerating passcodes. These attacks are particularly effective when secret numbers lack sufficient complexity. To mitigate such risks, our proposed mechanism combines the LP-IoT device’s ID with the secret number using an XOR operation, followed by encryption and hashing processes before transmission. This layered approach effectively prevents attackers from successfully performing dictionary and exhaustive attacks.
- Credential Stuffing AttackThe credential stuffing attack is a malicious attack where a malicious attacker utilizes a leaked valid password list to try to log in as an authorized user. Our proposed mechanism does not directly use a secret number; instead, it encrypts the secret number using the XOR of the LP-IoT device’s ID and transmits it after the hashing process. This confirms that our proposed mechanism is effective in defending against credential stuffing attacks.
- Forgery Attack/Impersonation AttackA forgery attack focuses on forging the mandatory infrastructure, trying to mislead both sides into believing they are communicating with a valid device. Our proposed mechanism is designed for LP-IoT and performs mutual authentication to verify both sides are trustworthy before data transmission. This confirms that our proposed mechanism is effective in defending against forgery attacks.
- Replay AttackThe replay attack is a malicious attacker sniffing the valid credentials and resending the credentials to cheat the authentication mechanism as a valid user. Our proposed mechanism is attaching a timestamp in each transmission, and the AS also asks all the servers to check whether the is in a reasonable time period. This confirms that our proposed mechanism is effective in defending against replay attacks. The overhead for verifying freshness is only a single hash computation (0.12 ms in Table 3), which is negligible for LP-IoT devices.
- Man-in-the-Middle AttackIn a man-in-the-middle attack, an attacker intercepts and potentially alters communication between the device and the server. To defend against this, our mechanism uses mutual authentication combined with timestamp-based hash masking. Even if communication is intercepted, the attacker cannot decrypt or modify the data without being detected, as each message’s integrity is verified using cryptographic hash functions and the inclusion of fresh timestamps. Since each authentication round generates new hash values bound to the current timestamp, the attacker cannot reuse old messages or maintain prolonged exposure.
4.3. Cryptographic Security
- Data Freshness and Hash-based ProtectionThe authentication server (AS) does not distribute long-term session keys; instead, it relies on lightweight hash functions combined with timestamps to ensure data freshness. Even if a past message is intercepted, the bound timestamp and hash values prevent it from being reused in future sessions, thereby achieving forward protection against replay and forgery attempts.
- Low Computational OverheadThe mechanism avoids computationally expensive operations, such as public-key cryptography, and instead relies on lightweight hashing and XOR operations. This makes it feasible for LP-IoT devices with limited processing power.As shown in Table 3, each masking step requires only one XOR and one hash operation, with combined latency below 0.15 ms, which is significantly lighter compared to RSA- or ECC-based protocols that require tens to hundreds of milliseconds per operation.
- Resistance to Side-Channel AttacksThe mechanism is designed to mitigate the risks of side-channel attacks by minimizing the exposure of cryptographic computations to an external observer. Since the mechanism utilizes XOR and a hash function rather than complex modular arithmetic, it reduces the likelihood of timing attacks and power analysis attacks. Furthermore, the authentication process incorporates randomized elements, ensuring that each execution path varies slightly, making pattern analysis more difficult for adversaries.
4.4. Device and Communication Security
- Mutual AuthenticationUnlike traditional IoT authentication mechanisms that only verify client-side legitimacy, our mechanism ensures that both the LP-IoT device and the authentication server authenticate each other before any data transmission occurs. The proposed lightweight authentication mechanism for low-power IoT devices demonstrably upholds the property of mutual authentication by ensuring that both the device and the Authentication Server (AS) verify each other’s legitimacy before any data exchange occurs. In the mutual authentication phase, the first generates authentication values (, ) derived from its unique ID, secret number, and time-sensitive parameters, which the DCS verifies for validity and timeliness. This prevents replay attacks and confirms the device’s authenticity. Subsequently, the DCS responds with its own authentication token (, ), computed using shared secret components and a fresh timestamp, which the validates through cryptographic checks. This bidirectional verification process, coupled with the use of lightweight hash and XOR operations, ensures that neither party proceeds without confirming the trustworthiness of the other.In contrast, schemes using ECC incur approximately 15–20 ms per scalar multiplication, which is more than two orders of magnitude heavier than our approach.
- Minimal Local SecretsThe LP-IoT device stores only minimal security information (such as its device ID and a hashed value tied to its secret number). All authentication values are generated dynamically for each session using lightweight hash and XOR operations with fresh timestamps, eliminating the need for long-term session keys and further reducing the risk of key compromise.
4.5. Functional Analysis
- Suitability for LP-IoT DevicesThe proposed mechanism executes all complex calculations on the server side during the registration phase. The LP-IoT devices only store mandatory information generated by AS, which significantly reduces their computational loading. In the authentication phase, the devices execute only XOR operations, which is a simple logical function that requires minimal computational resources and power. This design aligns with the limited processing power and energy constraints of LP-IoT devices, ensuring efficient performance without overloading hardware.
- Lightweight Storage RequirementsOur proposed mechanism requires minimal storage on LP-IoT devices. Only essential credentials, such as device IDs and hashed secret keys, are stored locally, reducing memory usage. This is particularly advantageous compared to mechanisms like ECC-based protocols, which require complex key management and large storage capacities.
- Flexibility Across IoT ApplicationsUnlike protocols designed for specific industries (e.g., healthcare or smart grids), our mechanism is highly adaptable to various LP-IoT applications, including automobile insurance, supply chain management, and environmental monitoring. Its generic design ensures ease of integration into diverse IoT environments without significant architectural modifications.
- Reduced Communication OverheadOur proposed mechanism minimizes the number of communication steps during the authentication phase, thereby significantly reducing bandwidth consumption. This is particularly beneficial in LP-IoT environments where devices often operate under low-bandwidth or intermittent network conditions.
- Scalability in a dynamic IoT environmentThe proposed mechanism is designed for operation in dynamic IoT settings, where the number of devices may frequently fluctuate. The registration phase has been designed to accommodate these changes, allowing the system to maintain its efficiency and security even in highly variable environments. This scalability ensures long-term usability across diverse IoT deployments.
- Enhanced Energy EfficiencyThe mechanism limits calculations on the LP-IoT device to XOR and hash functions. According to Table 3 [13], these operations require minimal computation time compared to other cryptographic methods. This ensures the mechanism is both fast and resource-efficient, meeting the performance requirements of LP-IoT devices while maintaining robust security.The performance evaluation demonstrates that our mechanism consumes only 1.56 ms per authentication cycle (as derived from Table 3). This value is substantially lower than other schemes that require more than 30 ms on average.
- Strong Security with Minimal Resource ConsumptionDespite its lightweight design, the mechanism provides robust security guarantees against common attack vectors, including reply attacks, impersonation attacks, and man-in-the-middle attacks. This balance between security and efficiency distinguishes our mechanism from traditional IoT security protocols.
4.6. Computation Time Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Grag, A.; Demirezen, E.M. Hsing Kenneth Cheng. Financial Sustainabilitiy of IoT Platforms: The Role of Quality and Security. Prod. Oper. Manag. 2024, 2, 412–431. [Google Scholar] [CrossRef]
- Manral, J. IoT enabled Insurance Ecosystem—Possibilities Challenges and Risks. arXiv 2015, arXiv:1510.03146. [Google Scholar]
- Elicegui, I.; Carrasco, J.; Escribano, C.P.; Gato, J.; Becerra, A.; Politis, A. Usage-Based Automotive Insurance. In Big Data and Artificial Intelligence in Digital Finance: Increasing Personalization and Trust in Digital Finance Using Big Data and AI; Springer International Publishing: Cham, Switzerland, 2022; pp. 295–311. [Google Scholar]
- Tyagi, S.K.S.; Boyang, Q. An Intelligent Internet-of-Things-Aided Financial Crisis Prediction Model in FinTech. IEEE Internet Things 2023, 10, 2183–2193. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Yang, K.; Blaauw, D.; Sylvester, D. Hardware Designs for Security in Ultra-Low-Power IoT Systems: An Overview and Survey. IEEE Micro 2017, 37, 72–89. [Google Scholar] [CrossRef]
- Sasi, T.; Lashkari, A.H.; Lu, R.; Xiong, P.; Iqbal, S. A Comprehensive Survey on IoT Attacks: Taxonomy, Detection Mechanism and Challenges. J. Inf. Intell. 2024, 2, 455–513. [Google Scholar] [CrossRef]
- Allioui, H.; Mourdi, Y. Exploring the Full Potentials of IoT for Better Financial Growth and Stability: A Comprehensive survey. Sensors 2023, 23, 8015. [Google Scholar] [CrossRef] [PubMed]
- New York State Department of Financial Services. 23 NYCRR-Part 500 Cybersecurity Requirements for Financial Services Companies. 2017. Available online: https://www.dfs.ny.gov/system/files/documents/2023/12/rf23_nycrr_part_500_amend02_20231101.pdf (accessed on 17 November 2024).
- Hong Kong Monetary Authority. Cybersecurity Fortification Initiative. 2016. Available online: https://www.hkma.gov.hk/eng/key-functions/international-financial-centre/fintech/research-and-applications/cybersecurity-fortification-initiative-cfi/ (accessed on 17 November 2024).
- Monetary Authority of Singapore. Cyber Hygiene Notice. 2018. Available online: https://www.mas.gov.sg/regulation/cyber-security (accessed on 17 November 2024).
- Cook, J.; Rehman, S.U.; Khan, A. Security and Privacy for Low Power IoT Devices on 5G and Beyond Networks: Challenges and Future Directions. IEEE Access 2023, 11, 39295–39317. [Google Scholar] [CrossRef]
- Kumar, D.; Shen, K.; Case, B.; Garg, D.; Alperovich, G.; Kuznetsov, D.; Gupta, R.; Durumeric, Z. All Things Considered: An Analysis of IoT Devices on Home Networks. 2019. Available online: https://www.usenix.org/conference/usenixsecurity19/presentation/kumar-deepak (accessed on 20 September 2025).
- Lazzaro, S.; De Angelis, V.; Mandalari, A.M.; Buccafurri, F. A black-box assessment of authentication and reliability in consumer IoT devices. Pervasive Mob. Comput. 2025, 110, 102045. [Google Scholar] [CrossRef]
- Zhao, J.; Hu, H.; Huang, F.; Guo, Y.; Liao, L. Authentication Technology in Internet of Things and Privacy Security Issues in Typical Application Scenarios. Electronics 2023, 12, 1812. [Google Scholar] [CrossRef]
- Thakare, A.; Kim, Y.-G. Secure and Efficient Authentication Mechanism in IoT Environments. Appl. Sci. 2021, 11, 1260. [Google Scholar] [CrossRef]
- Peivandizadeh, A.; Molavi, B. Compatible Authentication and Key Agreement Protocol for Low Power and Lossy Network in Iot Environment. SSRN. 2023. Available online: https://www.researchsquare.com/article/rs-2085426/v1 (accessed on 18 October 2025).
- Wang, C.; Wang, D.; Duan, Y.; Tao, X. Secure and Lightweight User Authentication Mechanism for Cloud-Assisted Internet of Things. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2961–2976. [Google Scholar] [CrossRef]
- Das, S.; Singh, M.P.; Namasudra, S. A Lightweight Authentication and Key Agreement protocol for IoT-Based Smart Healthcare System. World Conf. Commun. Comput. 2023, 1–5. [Google Scholar]
- Li, X.; Zao, H.; Xu, J.; Zhu, G.; Deng, W. APDPFL: Anti-Poisoning Attack Decentralized Privacy Enhanced Federated Learning Scheme for Flight Operation Data Sharing. IEEE Trans. Wirel. Commun. 2024, 23, 19098–19109. [Google Scholar] [CrossRef]
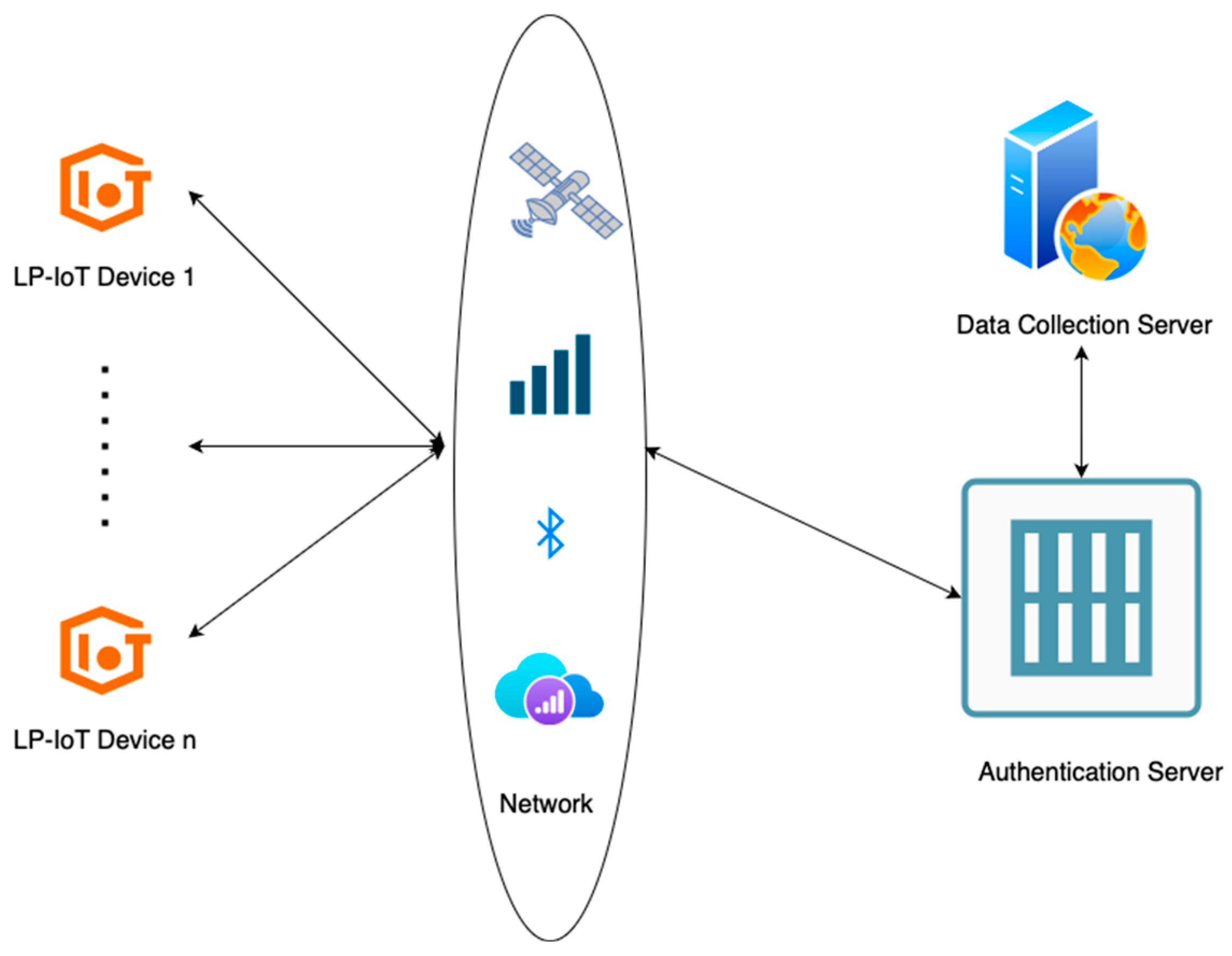
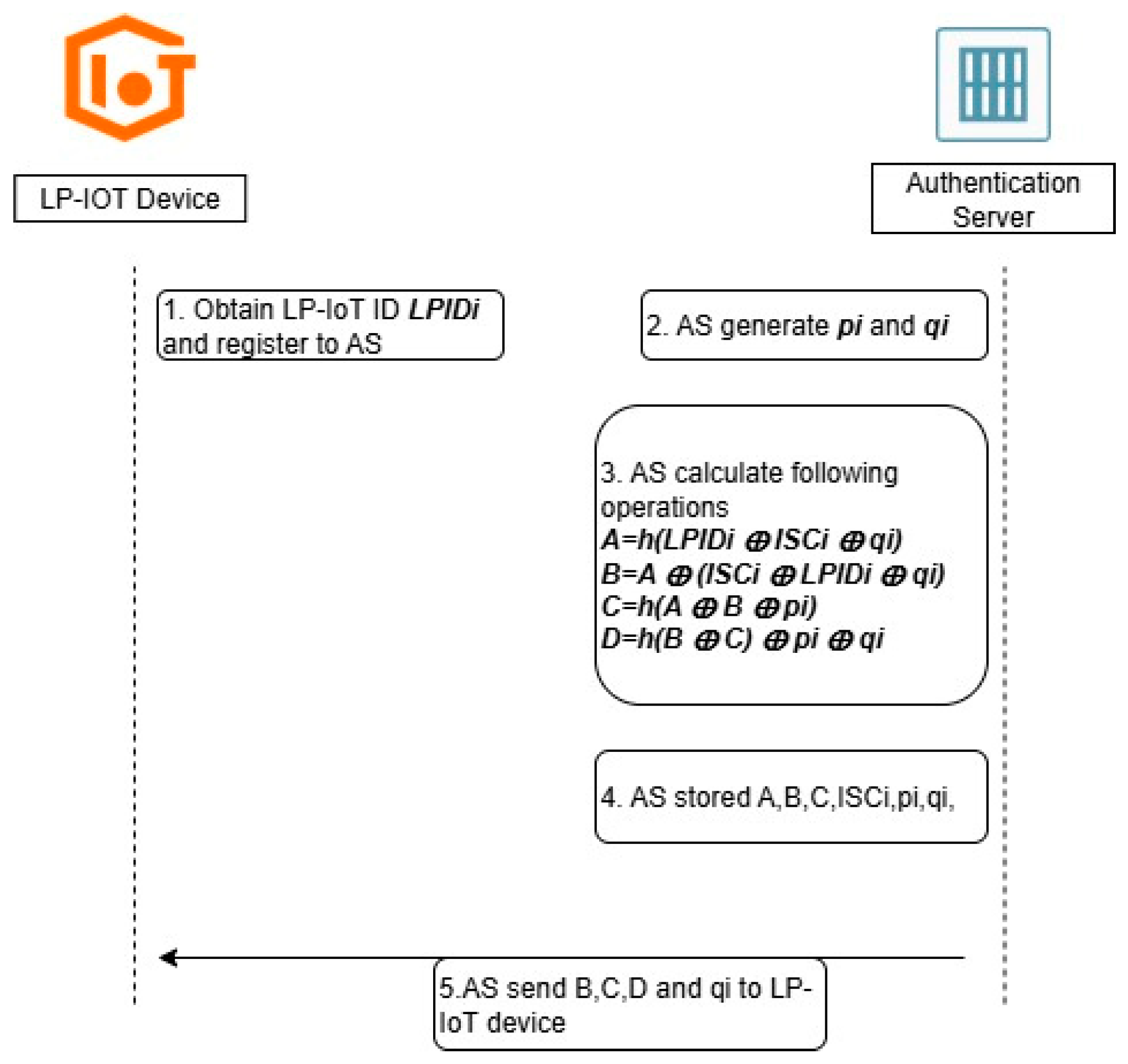
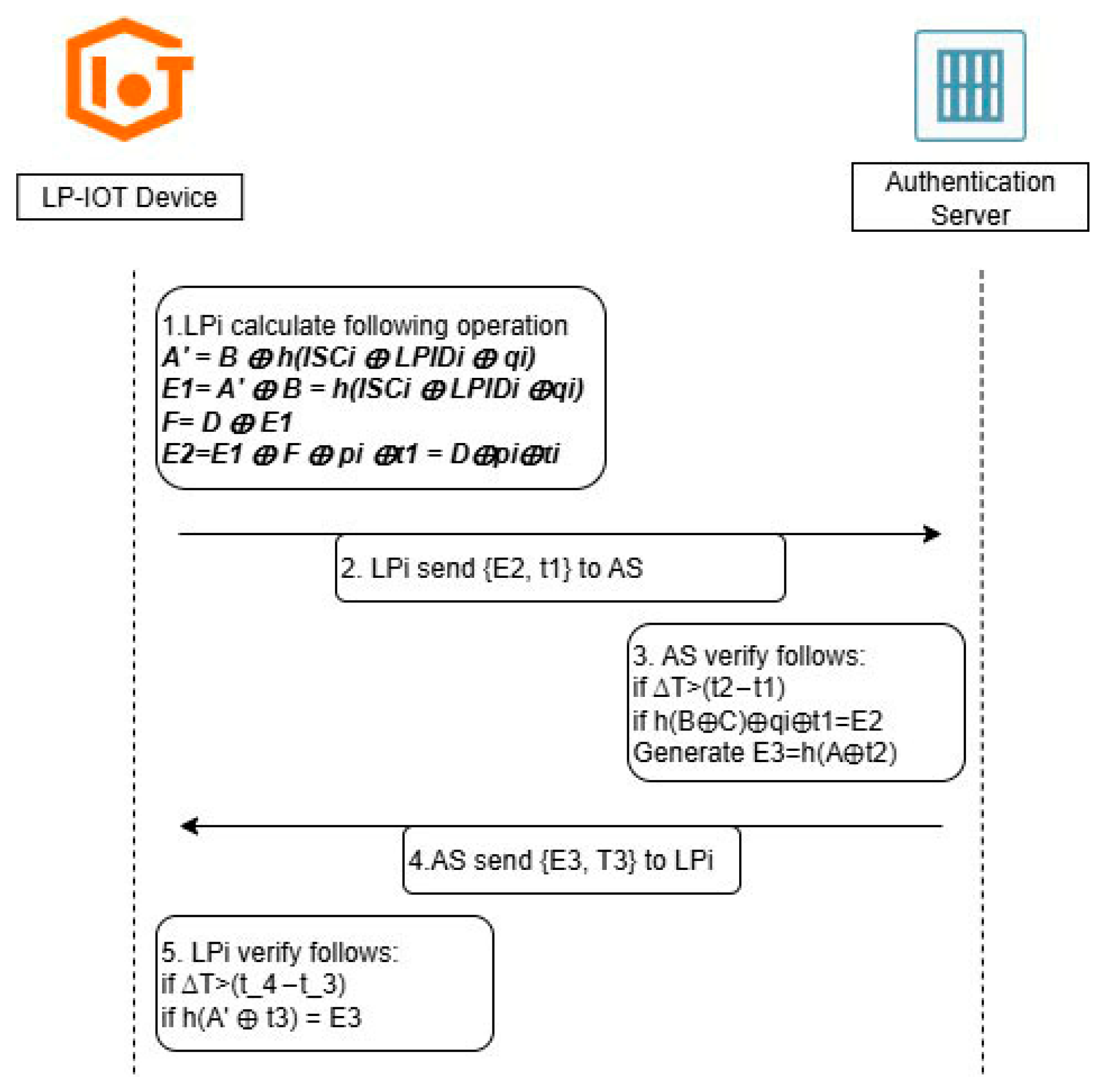
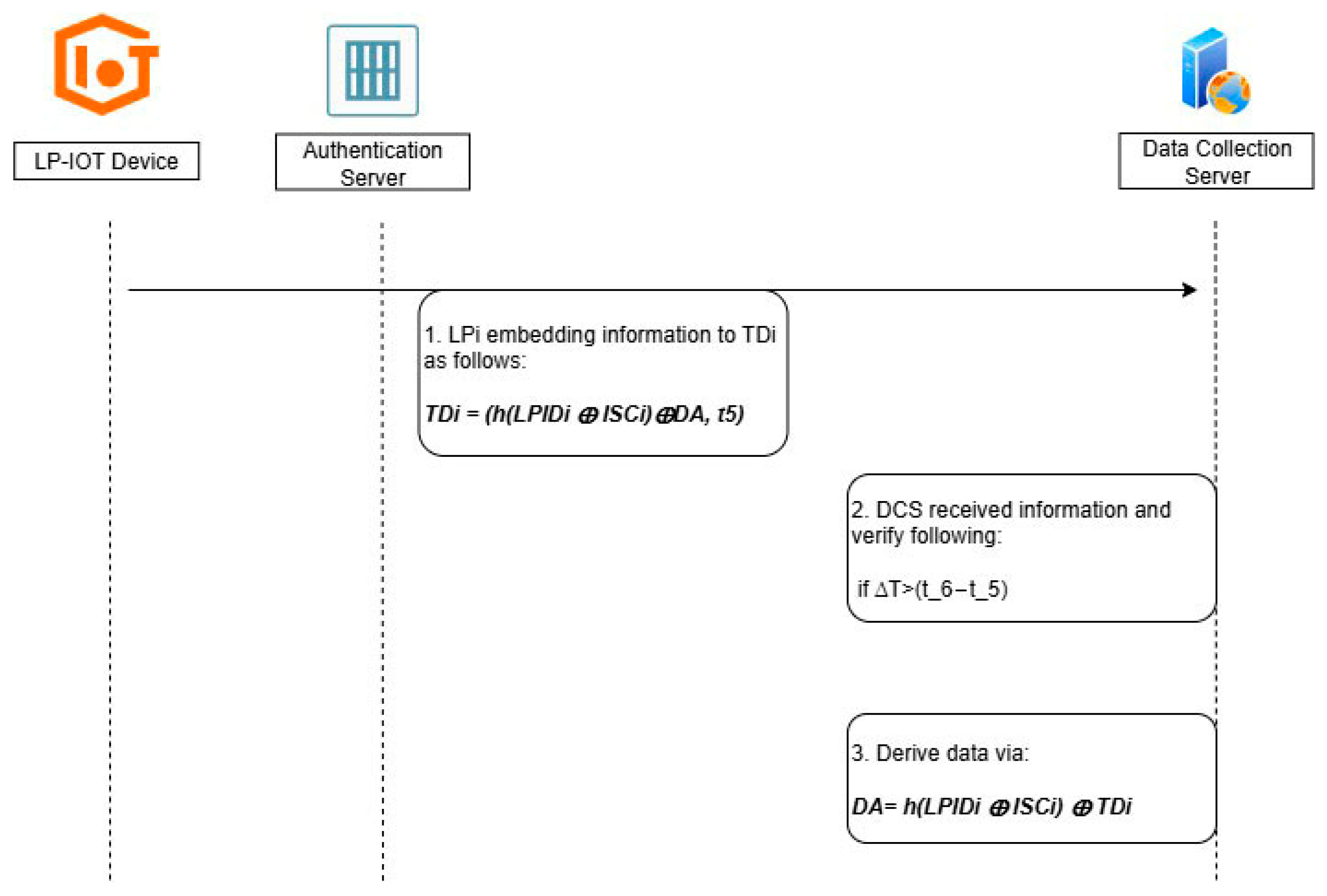
| Device/Server | Description |
|---|---|
| is the ith device used in the default deployment environment. | |
| DCS | . |
| AS | The Authentication Server is responsible for registering the LP-IoT device and sending the generated secret key. |
| Symbol | Description |
|---|---|
| LP-IoT device ID | |
| LP-IoT device | |
| Two distinct large prime numbers | |
| A predefined, reasonable length of time for the party that receives a message with a timestamp to ensure the freshness of the received message. | |
| The transferred data from the LP-IoT device i | |
| Hash function | |
| XOR operation |
| Operation | Notation | Computation Time (ms) |
|---|---|---|
| One-way hash function | 0.00032 | |
| ECC point multiplication | 0.0171 | |
| ECC point addition | 0.0044 | |
| Symmetric encryption/decryption | 0.0056 | |
| Modular exponentiation operation | 0.0192 | |
| Modular multiplication operation | 0.00088 | |
| Chebyshev chaotic map operation | 0.0171 | |
| Operation based on the Chinese Remainder Theorem | 0.00704 | |
| Signature generation for the elliptic curve digital signature | 0.02182 | |
| Verification for the elliptic curve digital signature | 0.03892 | |
| Message authentication code | 0.00032 |
| Authentication Solution | Applied Operations | Approximate Computation Time (ms) |
|---|---|---|
| Zhao et al. [15] | Chebyshev chaotic mapping | 0.0171 |
| Thakare et al. [16] | ECC point multiplication + Hash + XOR | 0.01742 |
| Peivandizadeh et al. [17] | ECC point multiplication | 0.0171 |
| Zhou et al. [18] | Cloud-assisted ECC + Hash + XOR | 0.00032 (with cloud computing ability) |
| Das et al. [19] | Hash + XOR (Session Key) | 0.00032 |
| Ours | XOR + Hash | 0.00032 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lo, N.-W.; Huang, J.-J.; Yang, T.-C. A Lightweight Mutual Authentication Mechanism for Applications Utilizing Low-Power IoT Devices. Electronics 2025, 14, 4178. https://doi.org/10.3390/electronics14214178
Lo N-W, Huang J-J, Yang T-C. A Lightweight Mutual Authentication Mechanism for Applications Utilizing Low-Power IoT Devices. Electronics. 2025; 14(21):4178. https://doi.org/10.3390/electronics14214178
Chicago/Turabian StyleLo, Nai-Wei, Jheng-Jia Huang, and Ta-Chih Yang. 2025. "A Lightweight Mutual Authentication Mechanism for Applications Utilizing Low-Power IoT Devices" Electronics 14, no. 21: 4178. https://doi.org/10.3390/electronics14214178
APA StyleLo, N.-W., Huang, J.-J., & Yang, T.-C. (2025). A Lightweight Mutual Authentication Mechanism for Applications Utilizing Low-Power IoT Devices. Electronics, 14(21), 4178. https://doi.org/10.3390/electronics14214178








