1. Introduction
In today’s hyperconnected world, the security of digital systems and the protection of user data pose increasing challenges for individuals, organizations, and governments alike. As societies increasingly rely on cloud computing, artificial intelligence (AI), mobile applications, and the Internet of Things (IoT), the scale and complexity of cyber threats continue to grow, with cybercriminals adopting ever more sophisticated attack strategies [
1]. Any successful cyberattack can compromise sensitive information, including clients’ personal data, as institutions across various sectors collect and process large volumes of such data.
Cybersecurity encompasses measures and strategies designed to safeguard digital systems, networks, and data against unauthorized access, cyberattacks, and other malicious activities [
2]. It is widely recognized as a key mechanism for data protection in cyberspace [
3]. From a security perspective, data protection refers to the process of safeguarding critical data from corruption, compromise, or loss, while also ensuring the ability to restore it, while from the privacy perspective, it pertains to the rules and safeguards established under various laws and regulations governing the collection, storage, use, and disclosure of personal data about individuals [
4]. The evolution of these legal frameworks has been shaped by technological advances and the increasing value of data in the digital economy [
5].
Although the academic community has responded to these challenges by actively increasing research in the field of cybersecurity and user data protection, this field remains fragmented across various disciplines, such as computer science [
6], law [
7], behavioral sciences [
8], and public policy studies [
9]. Consequently, gaining a comprehensive understanding of the field and identifying research trends has become increasingly challenging.
Existing reviews often focus on specific aspects, such us practical approaches and recommendations to enhance cybersecurity in healthcare [
10], digital policy and governance frameworks for electronic health records (EHR) systems [
9], global healthcare data privacy frameworks [
11], machine learning-driven security solutions for the Internet of Things (IoT) [
6], and the role of artificial intelligence (AI) in enhancing cybersecurity and ensuring legal compliance in clinical trials [
12], without integrating them into a broader perspective. As a result, different paradigms coexist: some emphasize technological safeguards and automation through AI-driven threat detection, while others highlight sociotechnical systems, accountability, and regulatory approaches.
Even so, the exponential growth of scientific output from year to year makes it increasingly challenging for researchers to obtain a comprehensive and balanced understanding of the field through traditional literature reviews alone. Classic reviews, while valuable for in-depth exploration of specific themes, are inherently limited in scope and often struggle to keep pace with the volume and diversity of new publications. In this context, bibliometric analysis provides a systematic, data-driven approach that not only enables the mapping of large bodies of literature but also highlights structural patterns, research frontiers, and emerging trends that would be difficult to capture otherwise.
Existing bibliometric studies in cybersecurity and data protection have predominantly focused on delimited subfields. For instance, research on cybersecurity in healthcare delivery [
13] noted that nontechnological variables—such as human–based and organizational aspects, strategy, and management—are understudied. Based on their bibliometric analysis in financial cybersecurity, Koibichuk et al. [
14] offer practical recommendations for managers of financial institutions, banks, and enterprises to effectively organize and enhance cybersecurity measures. Lavanya et al. [
15] analyzed scientific production on cybersecurity in the banking industry, identifying four clusters: cybersecurity, network security, cybercrime and fraud, while noting that future research could explore other industries. Research in education [
16] indicates a shift in educational research toward integrating AI with cybersecurity and data protection to enable safe personalized learning. However, significant gaps remain in real-time threat detection, AI ethics, and privacy in education. On the other hand, few authors have studied cybersecurity in tourism, with little investigation into mechanisms and measures to enhance it [
17].
Other bibliometric studies focused on narrow topics. For instance, Nobanee et al. [
18] provided a comprehensive evaluation of the research on cybercrime and cybersecurity risks, while Lawelai et al. [
19] examined cybersecurity threats and protection strategies in smart city infrastructures, highlighting major risks associated with AI and IoT integration, including intrusions, data theft, and privacy breaches. They recommended security-by-design policies and proactive risk assessments to mitigate vulnerabilities. Other studies explored machine learning applications in cybersecurity, such as threat intelligence and infrastructure monitoring, emphasizing the need for continued innovation supported by international collaboration [
20]. Another line of research investigated the adoption of blockchain technology in healthcare, revealing key applications in health data sharing, clinical trials, pharmaceuticals, big data, AI, and 5G medical devices, while also noting challenges related to scalability, storage capacity, interoperability, and standardization [
21]. Studies on consumer online data protection and consumer privacy concentrate more on policy and legal aspects [
22]. Research directions have shifted from fundamental legal aspects to more complex issues, such as big data and children’s data privacy, highlighting how legislation adapts to technological advancements and societal changes [
5]. Bibliometric research on government data breaches highlights ransomware as a major cybersecurity challenge, underscoring the need for stronger legal frameworks and robust cyber risk management [
23].
These studies provide important insights and map specific areas of knowledge, but a comprehensive bibliometric overview integrating cybersecurity and data protection across sectors and topics is still missing. We found only one bibliometric analysis of big data and cybersecurity [
24], but it does not examine issues related to sensitive personal data. The relevance of this topic is further underscored by the widespread tendency of consumers to consent to data use without carefully reviewing terms and conditions.
Given this context, the aim of the present study is to fill that gap by providing an integrated bibliometric analysis of publications indexed in the Web of Science database to map the structure and evolution of research in cybersecurity and data protection and to identify the cutting-edge breakthroughs and trends in the field. By analyzing publication trends, keyword co-occurrence, and thematic clusters, this work identifies the principal research directions and the emerging topics at the frontier of the field. The identified trends will subsequently be discussed and contextualized to enhance their understanding. By clarifying the intellectual structure of the field, this study contributes to a more integrated understanding of current knowledge and helps guide future research agendas.
Specifically, this study addresses three research questions:
RQ1: What are the main publication trends, the most influential articles, and the leading authors and countries contributing to the field of cybersecurity and data protection?
RQ2: What are the primary research directions in the field of cybersecurity and data protection?
RQ3: Which emerging topics and terms are shaping current developments in cybersecurity and user data protection research?
By answering these research questions, this study not only advances academic understanding but also provides practical insights for policymakers, industry practitioners, and researchers, enabling informed decision making and guiding future research priorities in an era of rapidly evolving digital threats.
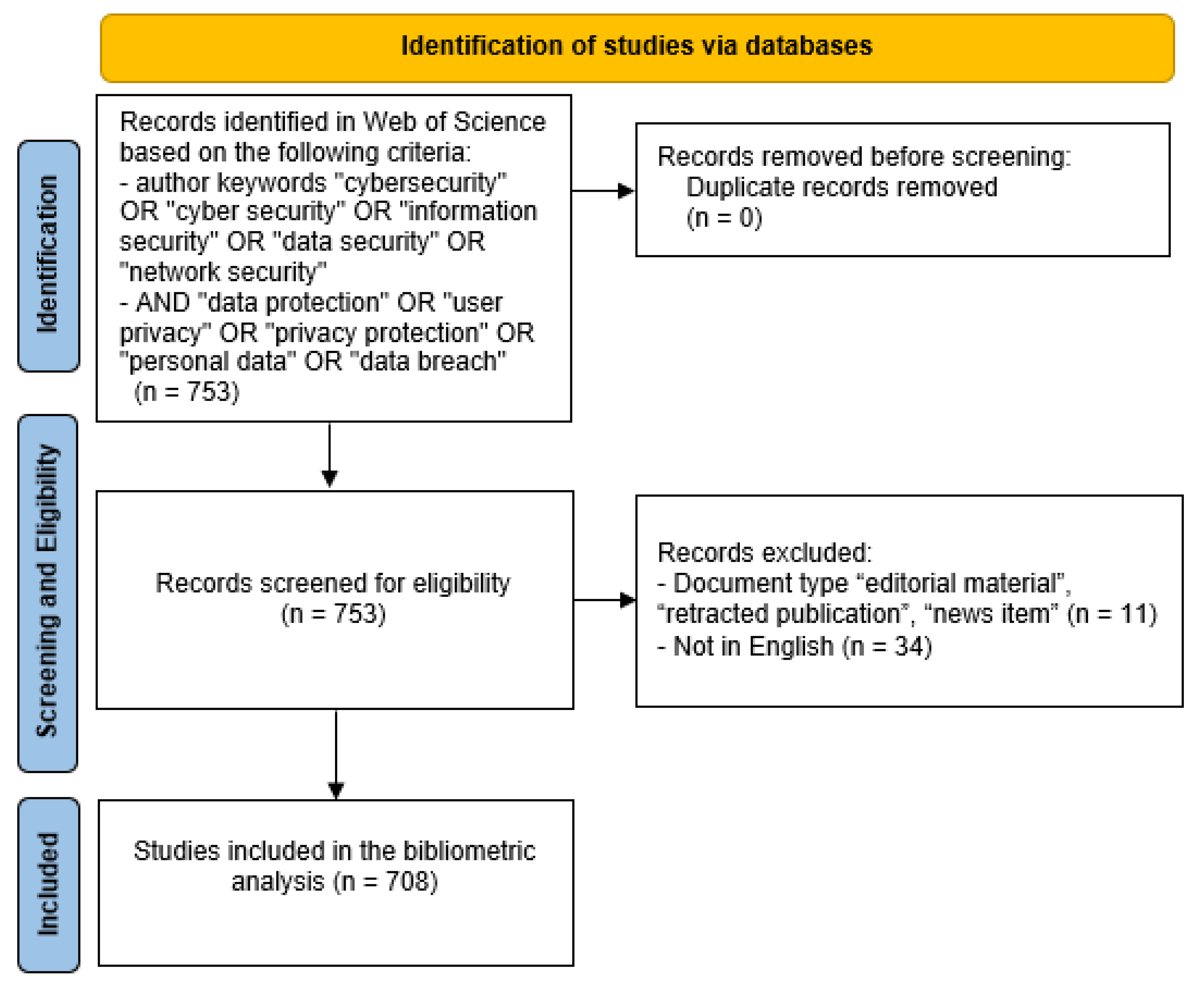
3. Results
To address the research questions of the study, the Results section is structured in three parts. First, we provide an overview of publication trends, the most influential articles, and the leading authors and countries in the field (RQ1). Next, we explore the main research directions through a co-occurrence analysis of keywords (RQ2). Finally, the analysis focuses on the relationships between emerging terms within different clusters, providing insights into the evolution of cybersecurity and data protection research (RQ3).
RQ1: What are the main publication trends, the most influential articles, and the leading authors and countries contributing to the field of cybersecurity and data protection?
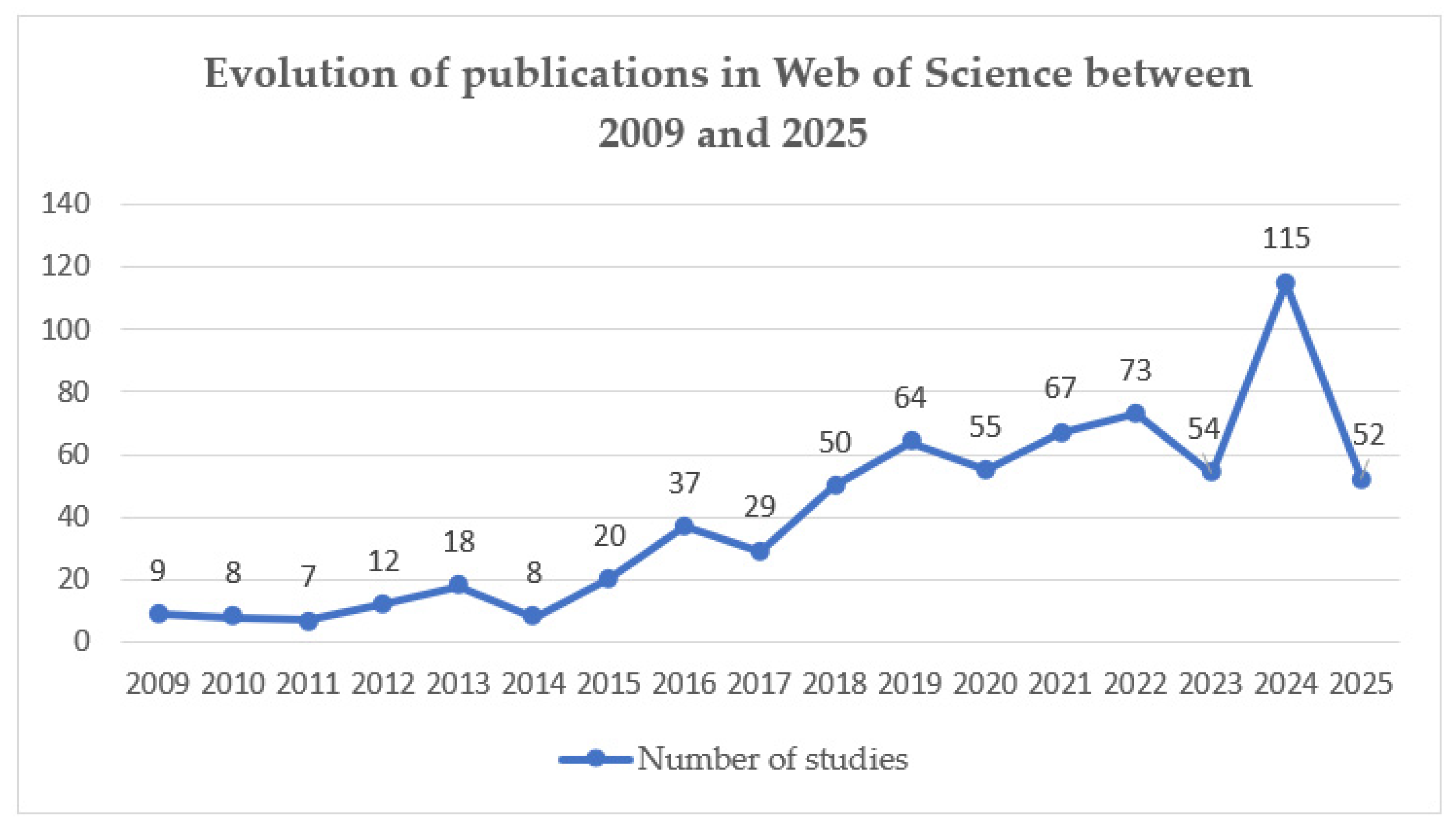
As illustrated in
Figure 2, there is a general upward trend in academic interest in topics related to cybersecurity and user data protection. Although the first publication in this field appeared in 1998, the topic attracted limited attention from researchers until 2009, with only one to four studies published per year. Data from 1998 to 2008 are omitted from the figure due to very low publication counts (1–4 per year), which do not significantly contribute to trend visualization. After 2009, the number of publications increased steadily, despite minor fluctuations likely influenced by technological developments and shifting research priorities. After a significant decline in 2023, interest increased sharply in 2024, reaching 115 publications—the highest number recorded during the entire period. It is likely that a similar or even higher number of publications will be recorded by the end of 2025.
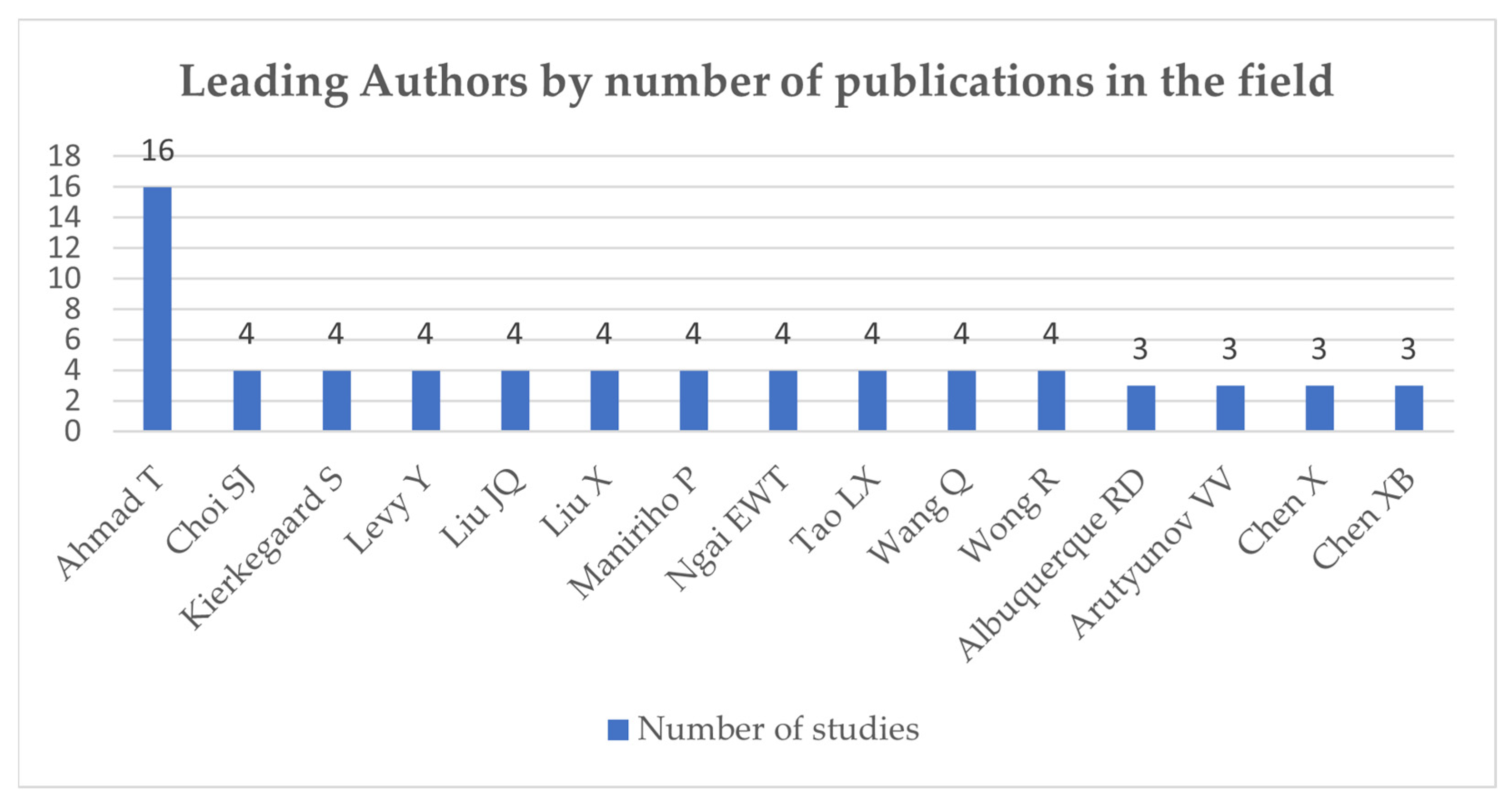
The papers included in our dataset were written by 2132 authors. The most productive author in the field of cybersecurity and data protection is, by far, Ahmad Tohari, with a total of 16 publications. He stands out significantly from the rest of the contributors, indicating a sustained and focused research activity in this area. He is followed by ten authors, each having published four papers, as can be seen in
Figure 3. The rest of the contributors have authored three or fewer publications. Such a pattern suggests that, although the field is attracting increasing academic interest, it still lacks a broad base of consistently high-output contributors, likely due to its relative novelty and the gradual consolidation of research efforts.
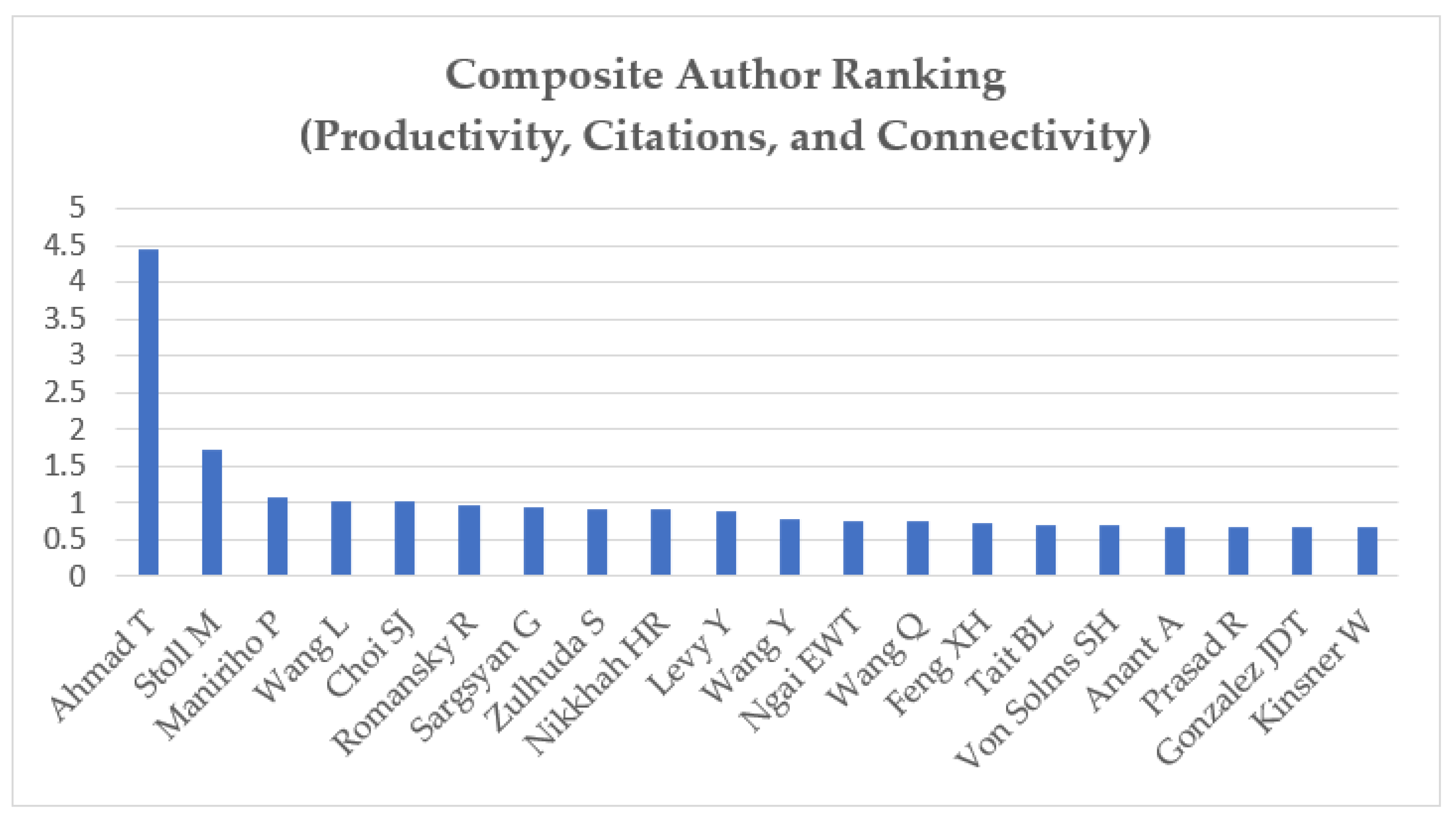
To identify the most influential scholars in the field, we calculated a composite influence score using the bibliometrix R-tool [
26], which integrates three normalized indicators: productivity (
P), citations (
C), and network connectivity (
L). The formula is
Productivity was measured using fractional counting, assigning each author only a fraction of a publication proportional to the total number of co-authors in order to avoid overestimating output in multi-authored papers. Citations were measured as field and year-normalized citations, obtained by dividing each paper’s citations by the average number of citations of publications from the same year and Web of Science category. Self-citations were excluded to more accurately capture recognition from the broader scientific community, which constituted 1.45% of total citations. We assigned a slightly higher weight to connectivity (normalized total link strength in the co-authorship network), as influence in science often arises not only from individual output but also from collaboration and scholarly embeddedness, suggesting they are a hub of activity and a key part of the flow of ideas [
27]. The analysis of the composite ranking score reveals that Ahmad Tohari (4.436) stands out as the most influential scholar in the field, displaying strength across all three dimensions. For the other top authors shown in
Figure 4, the differences in scores are relatively small, with their impact deriving either from network centrality or from the citations. These minor differences suggest that the field is still in an early stage of development. Overall, this approach provides a more balanced perspective compared to using publications or citations alone, as it captures multiple dimensions of scholarly influence.
To address RQ1 regarding the most influential publications in the field,
Table 1 presents the ten most cited papers from our dataset. This overview not only identifies the key articles that have shaped the research landscape of cybersecurity and data protection but also highlights the diversity of research domains (healthcare, smart cities, finance, and cloud infrastructure) where similar concerns emerge. The most cited paper, by Seh et al. [
28], addresses the growing threat of data breaches in the healthcare sector, identifying hacking and IT-related incidents as the most common causes, followed by unauthorized internal disclosures. Hussien et al. [
21] suggest blockchain as a solution to security gaps in telemedicine and e-health systems.
On the other hand, Yang, Xiong, and Ren [
29] focus on cloud storage security, highlighting encryption and access control as its foundational elements but noting persistent challenges. Braun et al. [
30] expand the discussion to smart cities, identifying five core security challenges: preserving privacy in high-dimensional data, securing expansive attack surfaces, ensuring trustworthy data sharing, effectively leveraging artificial intelligence, and preventing cascading failures across interconnected systems.
Several studies emphasize the human and social dimensions of cybersecurity. Hinds et al. [
31] explore public attitudes following the Cambridge Analytica scandal, revealing a surprising apathy among users, possibly due to limited understanding of algorithmic data processing or “crisis fatigue.” Sen and Borle [
32] apply criminological theories to organizational breaches, arguing that misdirected IT security investments may even heighten risks.
There is also growing interest in newer areas like the metaverse [
33], where privacy threats are significantly more complex and multi-layered due to its immersive and expansive nature. Other contributions focus on technical innovation, such as Qiu et al. [
34], who propose a user-centric, proactive data protection framework for mobile cloud environments, and Xu et al. [
35], who use stochastic process modeling to better understand and forecast hacking incidents over time. In parallel, Papadogiannaki and Ioannidis [
36] analyze emerging solutions for encrypted traffic analysis, as well as countermeasures designed to protect user privacy, highlighting the technical possibilities and limitations.
Table 1.
Top 10 most influential papers.
Table 1.
Top 10 most influential papers.
| Authors | Article Title | Citations | Year |
|---|
| Seh et al. [28] | Healthcare Data Breaches: Insights and Implications | 228 | 2020 |
| Yang, Xiong, and Ren [29] | Data Security and Privacy Protection for Cloud Storage: A Survey | 219 | 2020 |
| Braun et al. [30] | Security and privacy challenges in smart cities | 199 | 2018 |
| Sen and Borle [32] | Estimating the Contextual Risk of Data Breach: An Empirical Approach | 146 | 2015 |
| Huang, Li, and Cai [33] | Security and Privacy in Metaverse: A Comprehensive Survey | 127 | 2023 |
| Papadogiannaki and Ioannidis [36] | A Survey on Encrypted Network Traffic Analysis Applications, Techniques, and Countermeasures | 120 | 2021 |
| Hussien et al. [21] | Blockchain technology in the healthcare industry: Trends and opportunities | 115 | 2021 |
| Qiu et al. [34] | Proactive user-centric secure data scheme using attribute-based semantic access controls for mobile clouds in financial industry | 109 | 2018 |
| Hinds et al. [31] | “It wouldn’t happen to me”: Privacy concerns and perspectives following the Cambridge Analytica scandal | 102 | 2020 |
| Xu et al. [35] | Modeling and Predicting Cyber Hacking Breaches | 83 | 2018 |
Authors from 90 countries contributed to the papers included in the database analyzed. As illustrated in
Figure 5, the People’s Republic of China and the United States are leading contributors to research in the field of cybersecurity and data protection, with 165 and 136 publications, respectively. They are followed at a distance by the United Kingdom (41 publications), India (37), and Germany (31). Notably, among the top 15 contributing countries, Saudi Arabia stands out for having the most recent publications. This suggests a significant and growing national investment in cybersecurity research, which has enabled the country to quickly rise into the top 10 globally.
Figure 6 illustrates the collaborations between countries in cybersecurity and data protection research. Although a high level of international collaboration is evident, there are 23 countries that do not engage in international cooperation within this domain. It is observed that some groups of countries collaborate frequently among themselves, whereas others, such as the United Kingdom, the People’s Republic of China, and the USA, maintain collaborations with a significantly larger number of countries.
RQ2: What are the primary research directions in the field of cybersecurity and data protection?
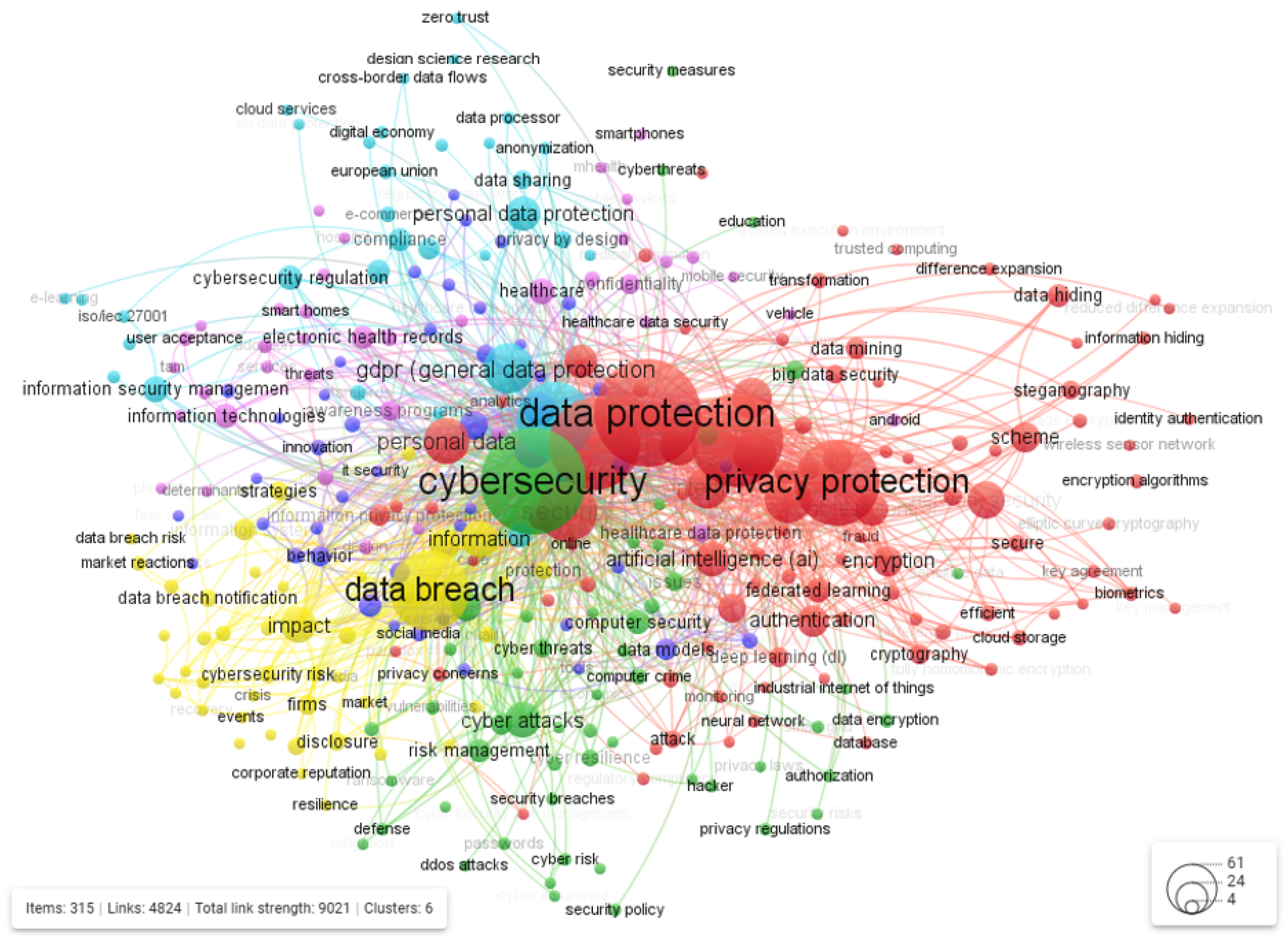
To identify the central research themes within cybersecurity and data protection, we performed a keyword co-occurrence analysis. This method enables the visualization of dominant topics based on terms extracted from titles, abstracts, and author-defined keywords. The resulting thematic map (
Figure 7) reveals six distinct research directions, with a total of 4824 connections among keywords. Numerous links exist not only within individual clusters but also across them, indicating that many of the analyzed publications address interdisciplinary or overlapping topics. In the following sections, each thematic cluster is examined in detail, outlining the key research directions it represents.
Cluster 1 (Red): Technical innovations in data protection and cryptographic security
The first cluster consists of 99 terms and can be named generically "Technical innovations in data protection and cryptographic security”. The term “data protection”, prominently featured with 244 occurrences, underscores its central importance in the network, connecting a wide range of concepts, such as “information security”, “data security”, “personal data”, “blockchain”, “authentication”, and “artificial intelligence (ai)”. This research direction focuses on the development and application of advanced technologies to secure data and ensure privacy protection, particularly through cryptographic methods (e.g., homomorphic encryption and attribute-based encryption), AI-driven threat detection, blockchain, IoT security, and privacy-preserving machine learning. It highlights a technical foundation for protecting data confidentiality, ensuring secure authentication for controlled access.
Within this cluster, the concepts of “data hiding”, “steganography”, and “image steganography” are closely related, emphasizing the importance of concealing information to maintain data security and data protection. These methods employ specific schemes, such as difference expansion or optimized variants like reduced difference expansion, to embed data into pixel structures with minimal distortion. The connections of the word “network security”, with 29 occurrences, emphasize the authentication mechanisms designed to verify identities and prevent attacks. Modern approaches integrate machine learning to detect threats more efficiently and improve defensive strategies. Core technologies, including cryptography and key agreement protocols, ensure secure communication, while advanced methods like elliptic curve cryptography enhance both security and efficiency. Additional safeguards, such as biometrics for identity verification and robust encryption algorithms to protect sensitive information, create a comprehensive framework for resilient and efficient cybersecurity.
The connections of the concept “blockchain”, appearing 48 times, with “smart contracts”, “federated learning”, “encryption”, “cryptography”, and “information security”, form the technological foundation for data protection and privacy preservation. These approaches enable secure and verifiable authentication while supporting recognition systems and the IoT, where sensitive data are constantly exchanged. Advanced computational approaches like deep learning and machine learning enhance the analysis and data mining capabilities, allowing intelligent insights without compromising security or privacy. These interrelated concepts create a cohesive framework for safeguarding information, ensuring privacy, and enabling secure, efficient, and intelligent data-driven applications.
Cluster 2 (Green): Cyber risk management and economic impact of security threats
The second cluster comprises 53 terms and focuses on the identification, assessment, and mitigation of cyber threats—including malware, phishing, ransomware, and DDoS attacks—while also addressing the economic implications of cybersecurity incidents, such as breach costs, cyber insurance, and the impact on small- and medium-sized enterprises. It encompasses the implementation of security policies and cyber risk management frameworks that aim to minimize potential losses and ensure organizational resilience.
The term “cybersecurity”, with 234 occurrences, is the most prominent and demonstrates strong interconnections across nearly all other terms in the cluster, reflecting its central role in integrating technical, managerial, and economic dimensions of cyber risk. The second most frequent term, “cyber attacks” (27 occurrences), is linked to related concepts within the cluster, including “defense”, “mitigation”, “reliability”, “cyber threats”, and “risk”. At the same time, it also bridges to terms in other clusters, such as “resilience”, “data breach”, “awareness programs”, “data protection”, and “deep learning”, highlighting that managing attacks requires not only defensive measures but also broader strategies involving technology, human factors, and advanced analytics.
Cluster 3 (Dark blue): Organizational behavior, security culture, and strategic governance
The third cluster has 47 keywords and explores how human factors, organizational culture, and targeted awareness and training initiatives influence the effectiveness of cybersecurity measures. It encompasses topics such as security policy compliance, board-level governance, trust, information security awareness, as well as the integration of digital transformation and strategic security management within organizational processes.
Within this cluster, the most prominent term, “challenges”, appearing 28 times, is strongly connected with concepts such as governance, systems, smart cities, trends, and frameworks, while also bridging to terms in other clusters. This highlights the multifaceted obstacles organizations face in maintaining effective security practices in dynamic technological and social environments. Meanwhile, the most interconnected term within the cluster is “behavior”, which links closely with “deterrence”, “policy compliance”, “fear appeals”, “organizations”, “social media”, “countermeasures”, “information security awareness”, “information security culture”, “systems”, “frameworks”, “knowledge”, and “training”. These connections emphasize the centrality of human behavior in shaping security outcomes, showing that organizational practices, cultural norms, and knowledge dissemination are all critical to fostering a resilient security culture.
Cluster 4 (Yellow): Corporate impact, disclosure, and market response to cybersecurity incidents
The fourth thematic group comprises 44 items and examines how firms respond to cybersecurity incidents (e.g., data breaches) in terms of disclosure, recovery strategies, and corporate communication. It investigates the effects on corporate reputation, financial performance, stock market reactions, and legal responsibilities, often using event studies to quantify the impact of such incidents.
Within this cluster, the term “data breach”, appearing 137 times, is the most prominent and highly interconnected. The term “information” (30 occurrences) connects with several key concepts within this cluster, including “cybersecurity risk”, “social responsibility”, “corporate disclosure”, “announcements”, “market”, “data breach”, and “quality”, underscoring its central role in shaping corporate communication and transparency strategies. Meanwhile, the term “impact” (28 occurrences) shows the strongest internal connectivity, linking to concepts such as “information systems”, “corporate social responsibility”, “compensation”, “investment”, “event study”, “recovery”, “crisis”, “firms”, “reputation”, “market”, “performance”, “strategies”, and “data breach”. These connections emphasize the multidimensional effects of cybersecurity incidents on both operational and strategic levels, reflecting how organizations manage risks, communicate with stakeholders, and implement measures to preserve reputation and market stability. This cluster highlights the critical role of effective disclosure, recovery, and information management in mitigating the negative consequences of security incidents.
Cluster 5 (Purple): Secure adoption of digital health and mobile technologies
Cluster 5 includes 39 terms and focuses on research into user acceptance; technology adoption models; and privacy concerns related to mobile devices, smart technologies, and digital health systems. It underscores the importance of secure design principles and policy frameworks for platforms such as electronic health records (EHRs), mHealth applications, and smart home systems, particularly in healthcare and mobile contexts where sensitive personal data are involved.
Within this cluster, the most interconnected term is “information technologies”, which links closely with “technology acceptance”, “user acceptance”, “technology acceptance model”, and “adoption”, reflecting the central role of technological integration and user readiness in the successful deployment of secure digital solutions. The second highly connected term, “electronic health records”, is associated with “adoption”, “interoperability”, “information management”, and “digital health”, highlighting both the operational and strategic challenges of managing sensitive health information securely across systems. Both of these core terms also connect with concepts from other clusters related to cybersecurity and data protection, illustrating that the secure adoption of digital health technologies cannot be separated from broader security and privacy considerations.
Cluster 6 (Light Blue): Regulatory compliance, international standards, and cross-border data governance
The smallest thematic group is the sixth (Light Blue) and includes 33 terms. This cluster addresses the legal and regulatory frameworks guiding cybersecurity and data protection, focusing on compliance with GDPR [
37]; ISO/IEC 27001 [
38]; and national or international laws; as well as issues such as data anonymization, cross-border data flows, cloud services, privacy by design, and human rights in the digital age.
The most frequently occurring term, “privacy” (127 occurrences), is a central element of the analysis, showing extensive interconnections not only within this cluster but also across all other clusters, underscoring its foundational role in modern data governance and cybersecurity. The term “GDPR- General Data Protection Regulation” (53 occurrences) is strongly linked with “standards”, “governance”, “information security management”, “ISO 27001”, “personal data security”, “compliance”, “data protection regulation”, “European Union”, “personal data protection”, “privacy by design”, and “design science research”. These connections highlight the GDPR’s dual role as both a legal requirement and a strategic driver for aligning organizational practices with internationally recognized standards and governance models. The strong association with ISO 27001 and information security management reflects how GDPR compliance is operationalized through structured security frameworks, while links to privacy by design emphasize the need to embed privacy safeguards into technology development from the outset. Its connection with design science research suggests that GDPR is not only a regulatory constraint but also a catalyst for innovation in security architecture, policy design, and privacy-preserving technologies. Overall, the interlinkages demonstrate that GDPR serves as a bridge between legal mandates, technical standards, and organizational governance, ensuring cohesive and accountable approaches to data protection across jurisdictions.
A particularly close interconnection exists between cybersecurity regulation and data protection regulation, illustrating why these two areas must be studied together, especially in the context of the rapidly expanding digital economy. This relationship highlights that effective governance in the digital age requires harmonizing security and privacy requirements within a unified legal and regulatory framework, enabling trust, interoperability, and the protection of fundamental rights in an increasingly interconnected world.
Together, these six research directions offer a comprehensive and structured understanding of the cybersecurity and data protection literature. They provide valuable insights that enable researchers, policymakers, and practitioners to prioritize security interventions, design effective regulatory frameworks, and develop integrated strategies to address the growing complexity of cyber threats in an increasingly digital and globally connected environment.
RQ3: Which emerging topics and terms are shaping current developments in cybersecurity and user data protection research?
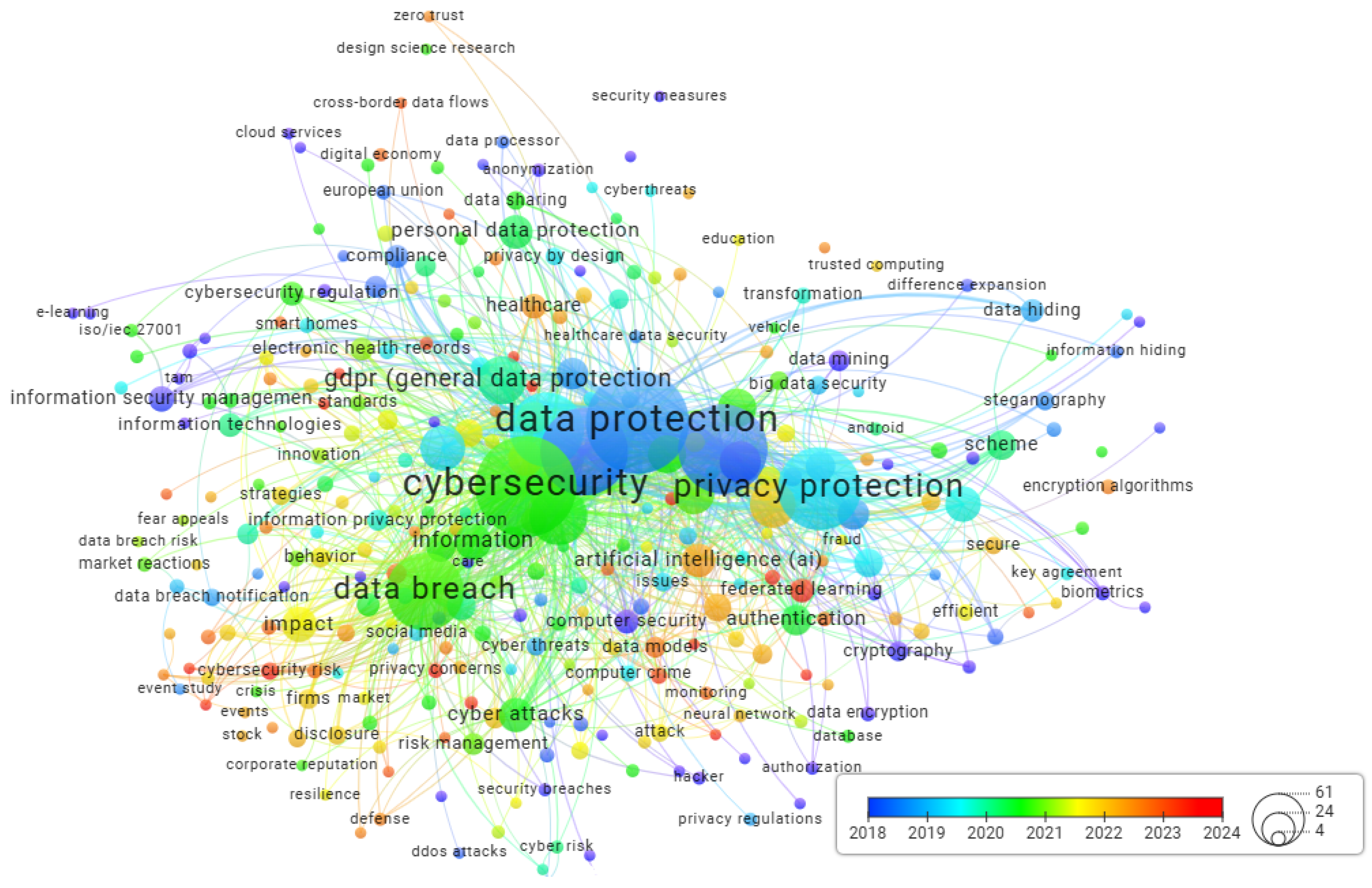
To uncover emerging trends in cybersecurity and user data protection research, we utilized a semantic map with overlay visualization created by VOSviewer, which is based on the average publication year (
Figure 8). Terms displayed in red and darker orange correspond to more recent studies and are thus considered indicative of emerging topics.
Recent research related to technical innovations in data protection and cryptographic security highlights the integration of advanced machine learning and privacy-preserving technologies to enhance cybersecurity. Key emerging concepts included in this cluster are “artificial intelligence (AI)”, “machine learning (ML)”, “federated learning”, “homomorphic encryption”, “encryption algorithms”, “recognition”, “trusted execution environments”, “privacy preservation”, “privacy concerns”, “differential privacy”, “lightweight” “AI ethics”, and “smart contracts”. These concepts reflect a multi-layered approach to data security and privacy, combining decentralized systems, blockchain technologies, federated learning, and advanced encryption methods. Privacy-preserving AI, edge-based processing, and ethical frameworks are increasingly prioritized alongside technical innovations, highlighting a shift toward holistic, scalable, and robust solutions that protect sensitive data and ensure trust across IoT, smart cities, healthcare, and industrial environments.
In the “Cyber risk management and economic impact of security threats” thematic group, only four emerging terms were identified: “reliability”, “ransomware”, “defense”, and “mitigation”. The term reliability is directly connected to defense, mitigation, algorithm, and analytics, indicating that dependable systems are built on both technological robustness and the ability to anticipate and counter cyber threats. These interconnections suggest that effective cyber risk management requires a multidimensional approach—one that combines resilient security architectures, precise economic risk assessment, advanced analytical capabilities, and adaptive defense mechanisms capable of evolving alongside emerging threats. Among these terms, ransomware is likely the most prevalent type of cyberattack today, reflecting its escalating occurrence and severe financial and operational consequences.
Modern cybersecurity resilience depends not only on advanced technologies but also on organizational behavior and the cultivation of a strong security culture. In the third cluster, the emerging terms identified include “security investments”, “trends” related to “city”, “governance” and “data governance”, “policy compliance”, “training”, “knowledge”, “data models”, and “predictive models”. These emerging concepts reflect evolving approaches in organizational behavior, security culture, and strategic governance, showing that effective cyber resilience requires an integrated perspective combining human factors, technological innovation, regulatory compliance, and data-driven decision-making. The interconnections among these terms suggest that investment in security, continuous training, and the use of predictive and data-driven models collectively enhance policy compliance and governance practices, thereby strengthening overall organizational resilience.
The thematic cluster named “Corporate impact, disclosure, and market response to cybersecurity incidents” highlights emerging terms, such as “compensation”, “recovery”, “corporate disclosure”, “context”, “cybersecurity risk”, “identity”, “social responsibility”, “stock”, and “security breach”, reflecting evolving priorities in cybersecurity management from a corporate reputation perspective. This thematic group demonstrates that companies are increasingly treating cybersecurity not merely as a technical or compliance issue but as a strategic imperative with direct implications for reputation, investor trust, and social responsibility. The interconnections among these terms suggest that disclosure practices, compensation policies, and risk management strategies are actively linked to strengthen resilience, maintain stakeholder confidence, and mitigate the market impact of security breaches.
The emerging terms related to the “Secure adoption of digital health and mobile technologies” reveal an intriguing intersection of “healthcare”; “adoption”; “information management”; and “services” with “higher education”, “awareness programs”, “integrity”, and “sustainability”. In recent years, the adoption of digital health and mobile technologies has accelerated, driven by advancements in cloud computing, mobile applications, and emerging technologies such as blockchain. Alongside these benefits, significant security and privacy challenges have emerged, highlighting the need for integrated technical and policy solutions to ensure secure and sustainable adoption. The inclusion of higher education and cybersecurity awareness in this cluster underscores that even the most advanced technological safeguards are ineffective without informed and conscientious users. Consequently, the secure adoption of digital health and mobile technologies requires a holistic approach that combines robust technical measures, such as encryption and access controls, with strong regulatory frameworks, organizational readiness, and continuous user education. By addressing both technological and human factors, stakeholders can promote trustworthy, resilient, and sustainable digital health ecosystems.
The last thematic cluster highlights a dynamic and rapidly evolving landscape shaped by legal, technological, and economic transformations at the intersection of cybersecurity, data protection, and international digital governance. Three key emerging terms, “cross-border data flows,” “zero trust,” and “digital economy”, exemplify crucial trends reflecting both challenges and innovations in this domain. The cluster underscores a multifaceted regulatory environment where the development of coherent and inclusive frameworks for cross-border data flows is crucial to balance local values with global interoperability. Zero trust security models offer a practical technological approach to address modern cybersecurity threats while ensuring regulatory compliance. At the same time, laws and standards must continuously evolve to keep pace with the rapid growth of the digital economy, reinforcing the need for integrated strategies that align technological, legal, and economic dimensions.
4. Discussion
The research patterns reveal a field that has expanded substantially since 2009, with notable growth after 2023. This growth coincides with rising regulatory pressure, the expansion of artificial intelligence, and the escalation of large-scale incidents, drivers that help explain both the volume and the breadth of topics captured in the co-occurrence map. Authorship is still relatively dispersed: a single prolific author dominates output within a narrow subdomain (data hiding), whereas citations are distributed across multiple topical pillars (healthcare breaches, cloud security, smart cities, and mobile/cloud protection). The geographic distribution, led by China and the United States, with fast-growing contributions from several countries, suggests increasing capacity worldwide, as well as uneven participation and collaboration.
The semantic map resulting from the keyword co-occurrence analysis reveals six research directions within cybersecurity and data protection. The overlay visualization clarifies how the field’s frontier is shifting within each of these directions. Semantic analysis of the cluster on technical innovations in data protection and cryptographic security shows that privacy-preserving AI (federated learning, differential privacy, and homomorphic encryption) and trustworthy execution environments are central. The rise of cyberattacks, such as phishing, unauthorized network exploitation, malware, and website intrusions, underscores the limits of traditional defenses. In this context, data encryption remains one of the most effective strategies to prevent the misuse or unauthorized disclosure of stolen or leaked information [
39], with a hybrid method combining the Advanced Encryption Standard (AES) and Standard Encryption Module 2 (SEM2) algorithms, enhancing both security and speed [
40]. At the same time, the emerging terms “machine learning (ML)” and “federated learning (FL)” highlighted in the semantic map reflect their growing role in addressing intrusions, anomaly detection, and trust management across healthcare, smart cities, and industrial IoT [
6], with FL enabling decentralized model training that preserves privacy and enhances network efficiency [
41]. Examples include cost-efficient edge FL for intelligent transport [
42], secure FL for open government data [
36], FL approach based on homomorphic assessment (Fed-HA) for robust gradient evaluation [
43], FL approaches combining local and global differential privacy (LDP and GDP) [
44], and FL with convolutional neural networks used to address privacy concerns for the intelligent home monitoring systems [
45]. All these studies illustrate a clear trend: integrating privacy, security, and AI performance in a holistic manner.
Blockchain is also gaining traction as a basis for frameworks for securing critical infrastructures and protecting data. Examples include advanced metering infrastructure in smart grids [
46], credit card fraud detection combining FL and blockchain [
47], IoT access control with zero-knowledge proofs and trusted execution environments [
48], and lattice-based anti-quantum linkable ring signature schemes for Industrial Internet of Things [
49]. These solutions leverage decentralization, immutability, and smart contracts to enhance trust, reduce economic risks, and protect data confidentiality. Complementary methods, such as dynamic data obfuscation [
50] and an AI-powered automatic sensitive image search system for detecting sensitive personal data leaks online [
51], support proactive privacy breach prevention, while integrating technological innovation with ethical and regulatory frameworks highlights the need to balance AI utility with data protection [
52]. In the big data context, techniques such as differential privacy, k-anonymity, T-closeness, and L-diversity [
53] remain essential, complementing both traditional encryption and federated/blockchain mechanisms.
Overall, trends in the first cluster highlight a clear convergence: modern cybersecurity and data protection can no longer rely on isolated measures. Instead, combining advanced cryptography, explainable AI, federated learning, blockchain, and ethical/regulatory frameworks forms an integrated approach to prevent attacks, protect privacy, and ensure data integrity in complex, distributed ecosystems.
The emerging terms from the second thematic group—cyber risk management and economic impact of security threats—reflect a shift from isolated, reactive responses to an integrated strategy that anticipates and mitigates threats before they materialize. This aligns with recent research stressing proactive approaches: Dutta et al. [
54] argue that 5G security should be embedded from the design phase and integrated across all components of the end-to-end architecture, while offensive security strategies help identify hidden vulnerabilities. The prominence of the term "ransomware” reflects its growing prevalence and severe economic impact, particularly in healthcare [
55]. Studies emphasize the need for investment in advanced technologies such as zero trust architectures, solid organizational strategies, and user-friendly measures to combat evolving cyber threats while minimizing workflow disruptions [
10]. On the other hand, cloud computing and IoT health data introduce new vulnerabilities, prompting solutions such as the security reputation model (SCNN-DGT), which combines S-AlexNet convolutional neural networks and dynamic game theory for accurate classification, security assessment, and incentive strategies [
56]. In next-generation networks, hybrid approaches combining quantum-resistant algorithms, elliptic curve cryptography, and multifactor authentication can secure IoT, autonomous vehicles, and smart cities while maintaining low latency and scalability [
57]. In industrial control systems, methods such as Symmetric Analog Licence Transfer (SALT) integrate analog key transfers with symmetric encryption to offer cost-effective, scalable protection [
58], while edge AI models with embedded licenses improve resistance to tampering by over 29% with minimal performance loss [
59].
Economic considerations are central to cyber risk management. Algarni et al. [
60] present models that estimate both the likelihood and cost of data breaches, emphasizing that defense strategies must balance the cost of preventive measures against potential losses. Accurate cost assessment also informs cyber insurance policies, which have become increasingly essential as traditional coverage often excludes cyber threats [
61]. Overall, the literature supports a multidimensional view of cyber risk management, as evidenced by the semantic cluster analysis, where advanced analytics, proactive defenses, economic assessments, and adaptive strategies converge to address the complexity and financial impact of cyber threats.
Research trends in the third cluster show that cybersecurity resilience extends beyond technical solutions, relying heavily on organizational behavior, security culture, and governance practices. Evidence shows that organizations with stronger prevention, detection, and recovery controls suffer less severe cyberattacks, but simply having cybersecurity roles or frameworks does not reduce breach impact. Interestingly, stronger organizational responses were associated with higher breach severity but did not influence fines, penalties, or investigations [
62]. In sectors with privileged access to sensitive data, such as healthcare, organizational information security culture (ISC) shapes security outcomes by influencing both social norms and individual attitudes, pointing to the value of targeted training and awareness programs [
63]. Gamified e-learning systems boost self-efficacy and compliance behaviors [
64], while workplace monitoring (dataveillance) improves accountability but can raise privacy concerns that may reduce compliance intentions [
65].
Governance strategies increasingly rely on advanced methods to secure collaboration and decision making, such as secure multiparty computation (SMPC) protocols to prevent premature information disclosure [
66], and predictive, data-driven models for proactive risk management, such as frameworks for rare breach forecasting [
67] and the multicritics generative adversarial network (GAN) clustering-based intrusion detection system (IDS) model (MCGC-IDS), improving accuracy and adaptability [
68]. By integrating such models into strategic governance processes, organizations can shift from static compliance toward adaptive, risk-informed decision making. At a societal scale, the rise of smart cities enhances efficiency and citizen well-being but requires robust governance structures to protect privacy and ensure inclusivity. Evidence shows that effective cybersecurity and data protection policies can significantly boost citizen participation, with one study reporting a 30% increase over four years [
69]. These findings underscore that security investments, training, governance frameworks, and predictive modeling must work in tandem to strengthen both organizational and civic resilience in the digital age.
The emerging terms in the fourth cluster—corporate impact, disclosure, and market response to cybersecurity incidents—such as compensation, disclosure, recovery, and social responsibility, illustrate that cybersecurity has become a strategic issue for corporations, with direct implications for reputation, investor trust, and market stability. Recent studies reveal the growing challenge of assigning responsibility and compensating for cyber incidents. Attribution often depends on user behavior and context: users who follow security protocols tend to blame negligent actors, while non-compliant users shift blame externally [
8]. In the case of IoT devices, accountability is further complicated by fragmented ownership structures and manufacturers prioritizing cost over security. Nekit et al. [
7] emphasize that sustainable solutions require coordinated regulatory enforcement, certification systems, and industry–society collaboration to strengthen accountability and prevent systemic harm. Transparent communication is equally essential, with organizations mitigating reputational damage by acknowledging responsibility, providing detailed explanations, and offering timely compensation [
70]. Disclosure practices have emerged as a central element of corporate response to cybersecurity incidents: firms expand risk disclosures after severe breaches, while reductions in disclosure trigger negative investor reactions [
71]. Breach context also matters, with public events generating stronger reporting pressure than internal incidents or breaches suffered by industry peers [
72]. These patterns highlight the growing importance of context-sensitive corporate disclosure, which functions both as a market signal and an ethical demonstration of corporate social responsibility.
The financial implications of cybersecurity incidents are significant: breach announcements reduce deposits and stock returns, though banks may offset this with higher lending [
73]. However, long-term trust effects are limited, highlighting tensions between convenience and security in the digital marketplace [
74]. Regulatory frameworks, such as China’s Cybersecurity Law, reduce breach risk by strengthening firms’ cybersecurity culture and systems [
75], while also improving personal data protection, lowering stock crash risk, and encouraging firms to invest in security. These measures further increase firm value and reinforce corporate social responsibility [
76]. This underscores an emerging trend where cybersecurity management is closely linked to financial performance and capital market stability. The shift toward proactive risk management reflects the recognition that prevention is more effective than remediation, supporting the development of privacy-first system architectures [
77], but its effectiveness depends on authentic corporate practices, as strong corporate social performance (CSP) in peripheral areas combined with weaknesses in core areas can backfire, increasing vulnerability by signaling “greenwashing” [
78]. Together, these findings emphasize that cybersecurity management must integrate disclosure, compensation, preventive risk analysis, and authentic social responsibility to maintain resilience and safeguard market trust.
The rapid adoption of digital health and mobile technologies is transforming healthcare delivery but introduces critical security and privacy risks, defining a specific research direction on the secure adoption of digital health and mobile technologies. In cloud-enabled health systems, unauthorized access and breaches make encryption, access controls, and threat detection essential for protecting sensitive data, building user trust, and promoting wider adoption [
79], with multiple encryption strategies proposed to safeguard data integrity [
80]. The growth of mobile health (mHealth) apps highlights the tension between usability and security. An analysis of 30 mHealth apps revealed widespread vulnerabilities, including weak encryption, invalid SSL certificates, and insecure data transmission. Rajput et al. [
81] proposed a security framework focused on confidentiality and integrity, while Looi et al. [
82] advocated stronger legislative oversight of electronic health records. Yet, in practice, many healthcare workers relied on personal devices during the pandemic, prioritizing usability over safety [
83], emphasizing the need for a balanced approach that combines robust security measures with user-centered policies.
Organizational and social factors also shape adoption patterns. In the elderly care sector, blockchain adoption is driven by perceived advantages, corporate social responsibility, top management support, and organizational readiness. Trust in technology and information security enhance the perceived benefits of blockchain, driving adoption, whereas privacy protection is less significant [
84]. Similar patterns occur in consumer behavior, where users often replace smart devices after three years due to privacy and security worries [
85].
Even advanced cybersecurity measures are ineffective without user awareness. Studies show varied cybersecurity awareness among students, with active social media users understanding terms of service better but sharing more personal data to gain certain benefits, while passive users remain cautious [
86]. In Palestinian higher education, mobile cloud adoption faces multiple risks from data loss, breaches, poor backup, and weak institutional safeguards, exacerbated by gaps in user awareness [
87]. Although students have a satisfactory level of awareness, significant improvements are needed [
88]. Therefore, technical safeguards such as encryption and blockchain must be reinforced by regulatory frameworks, organizational readiness, and above all, continuous user education to ensure resilient, trustworthy, and sustainable digital health ecosystems.
The final thematic cluster—regulatory compliance, international standards, and cross-border data governance—captures the complex interplay between law, technology, and economics in shaping cybersecurity and digital governance. Emerging terms reflect the need for frameworks that not only secure digital environments but also ensure global interoperability and regulatory coherence. Cross-border data flows remain critical yet underregulated: Mishra and Kugler [
89] note the absence of a systematic, inclusive framework in international trade agreements, arguing for the integration of community values in regional rule-making, while Chaisse [
90] underscores the fragmentation caused by conflicting domestic laws and the lack of a comprehensive global framework. These gaps are most evident in emerging markets, where culturally sensitive and economically tailored rules are urgently needed.
The zero trust security model marks a significant change in cybersecurity governance, replacing perimeter defenses with continuous verification and strict access controls for every user, device, and resource. Vukotich [
91] recommends its use in healthcare, while Daah et al. [
92] propose a blockchain-integrated zero trust framework for finance, and Al-Ayed [
93] introduces a real-time three-factor authentication approach that incorporates facial biometric verification. These approaches reflect broader compliance trends, converging legal requirements (e.g., GDPR mandates on data protection) with adaptive technological solutions. The digital economy further magnifies regulatory gaps. Botes [
94] shows how South Africa’s current legal frameworks inadequately address risks in digital mental health applications, particularly AI-driven tools, third-party data sharing, and cross-border transfers. Although the EU’s GDPR is a global benchmark [
95], ambiguities and interpretative challenges hinder effective compliance and enforcement [
96]. This research direction underscores the need for integrated strategies where legal modernization, adaptive technologies like zero trust, and international cooperation align to reduce fragmentation and place security and privacy at the core of digital governance.
Our study complements previous bibliometric analyses, which focus on narrow topics, by providing a comprehensive view of the intersection between the cybersecurity and data protection fields. By clarifying the intellectual structure of the domain and identifying research directions and emerging trends, it offers a more integrated understanding of current knowledge and supports future research agendas. The study highlights that effective cybersecurity and data protection require a multidimensional approach, combining technological innovations, human behavior, and organizational governance. In particular, it emphasizes the central role of human factors, organizational culture, and knowledge dissemination in shaping security outcomes, demonstrating that technical measures alone are insufficient without compliance and continuous training. It also underscores the growing relevance of privacy-preserving AI, ethical frameworks, and edge-based processing in emerging research, pointing to an evolution toward holistic and scalable solutions.