1. Introduction
The exponential increase in internet usage and the surge in connected devices have led to a dramatic rise in wireless data traffic demand. Particularly, the advancement of IoT (Internet of Things) and the progression toward 5G and 6G networks have intensified the need for wireless technologies with higher speeds and greater capacity. In response, global research efforts are accelerating toward the realization of beyond 5G and 6G systems, targeting data transmission rates surpassing 100 Gbit/s [
1]. Among the emerging candidates, terahertz (THz) technology stands out as a promising solution for ultra-high-speed, short-range wireless communication due to its capacity for transmitting massive data volumes.
In the case of electrical approaches, THz generation has been pursued using III–V compound semiconductor devices. For instance, InP-based heterojunction bipolar transistors (HBTs), high electron mobility transistors (HEMTs), and GaAs-based Schottky diodes have demonstrated output powers in the range of 0.1 to 1 mW at room temperature [
2,
3,
4,
5,
6]. Nevertheless, these electronic approaches face intrinsic limitations in terms of bandwidth, output power, and noise performance. To overcome these obstacles, photomixing technology has attracted significant attention.
Photomixing utilizes a high-speed photodiode such as the uni-traveling carrier photodiode (UTC-PD) to generate THz signals by beating two optical carriers of different frequencies inside a semiconductor material [
7,
8,
9]. This technique enables precise control over the frequency, phase, and output power of the generated THz waves by simply adjusting the properties of the input lasers. Additionally, its compatibility with existing optical fiber infrastructure makes photomixing a compelling option for future wide-scale implementation.
Wireless communication is inherently vulnerable to eavesdropping due to its open medium. Conventional cryptography can mitigate this risk but remains threatened by advances in quantum computing [
10,
11,
12,
13,
14]. As a complementary approach, physical layer security (PLS) leverages channel characteristics, particularly in highly directive millimeter-wave and THz bands, to enhance confidentiality [
15,
16,
17,
18,
19].
In our previous work, we proposed a physical-layer encrypted wireless communication scheme employing beam steering and coherent detection in the THz band and demonstrated a proof-of-concept for data decryption based on logical operations between THz beams [
20]. However, these studies were limited to configurations in which two THz signals were combined on a single chip or within a waveguide, and did not evaluate performance under spatial wireless transmission conditions.
In this study, we investigate the characteristics of physical-layer encrypted communication based on logical AND operations using a setup in which THz signals are transmitted from two spatially separated points and received simultaneously [
21]. An experimental environment was constructed to emulate a dual-base-station configuration with sufficient separation between transmitters, and the impact on communication quality and reception area was evaluated. The results confirm that the proposed logical-operation-based encryption scheme remains effective even in spatially distributed wireless scenarios.
The key contributions and novelties of this work are summarized as follows:
Proposal of an analog-domain physical-layer encryption scheme based on logical AND operations between dual terahertz (THz) beams.
Implementation using photomixing with UTC-PDs, enabling the generation of two spatially separated THz carriers carrying distinct data streams.
Experimental demonstration of decryption via coherent detection, validating that the original bit stream can be recovered only when both THz beams overlap and are phase-aligned.
Evaluation of system performance, including bit error rate (BER) measurements up to 1.5 Gbit/s and comparison with simulation, confirming the feasibility of the proposed scheme.
Verification of spatial selectivity, through experiments and simulations that show successful decryption is confined to a narrow overlap region, enhancing the inherent security.
2. Related Works
As briefly noted in the introduction, wireless communication remains fundamentally vulnerable to eavesdropping, and traditional cryptographic schemes face increasing challenges from brute-force methods and quantum computing [
10,
11,
12]. In this section, we provide a more comprehensive review of related works, covering the evolution from conventional cryptography to post-quantum cryptography (PQC), and exploring the emergence of physical layer security (PLS) techniques in millimeter-wave and terahertz systems.
In response to these threats, the research community has explored post-quantum cryptography (PQC), which aims to design cryptographic algorithms resistant to quantum attacks. PQC schemes, such as lattice-based or code-based cryptography, promise enhanced resilience and are being standardized by organizations such as NIST. However, while PQC provides strong theoretical guarantees, its practical implementation raises new challenges. Hardware implementations, whether based on FPGA or ASIC platforms, often remain susceptible to side-channel attacks that exploit leakage through timing, power consumption, or electromagnetic emissions [
13,
14]. As a result, there is a growing interest in complementary security mechanisms that can strengthen system resilience beyond traditional cryptographic layers.
One such approach is Physical Layer Security (PLS), which leverages the inherent characteristics of wireless channels to enhance confidentiality. Rooted in Wyner’s wiretap channel model, PLS establishes secrecy by exploiting differences in channel conditions between the legitimate receiver and potential eavesdroppers. Compared with cryptographic methods, PLS offers significantly lower computational complexity and can be integrated into existing systems without excessive overhead [
15]. This makes it especially attractive for resource-constrained scenarios such as Internet of Things (IoT) deployments and wireless sensor networks (WSNs).
PLS has been particularly effective in high-frequency bands such as millimeter-wave and terahertz (THz) systems. In these regimes, strong directivity reduces the spatial footprint of transmissions, inherently limiting signal leakage and improving secrecy. For example, hybrid beamforming techniques in multi-user multiple-input multiple-output (MIMO) systems have demonstrated significant resistance to eavesdropping by steering beams precisely toward intended receivers while suppressing side lobes [
16]. Other researchers have explored quantum noise–based masking, which injects random noise into the transmitted signal, thereby confusing potential eavesdroppers while enabling legitimate receivers to recover the original data [
17]. Similarly, highly directive antenna technologies, including leaky-wave antennas and vortex beams, have been investigated to confine the spatial region of secure communication. These approaches have shown promise in simulation and experimental studies [
18,
19]. A comparative summary of these techniques is presented in
Table 1.
Despite these advances, existing PLS methods face practical challenges. Many techniques rely heavily on precise beam alignment and synchronization, which can be difficult to maintain in dynamic wireless environments. Signal scattering, multipath fading, and environmental fluctuations may degrade secrecy performance, making real-world deployment complex. Moreover, the trade-offs between secrecy capacity, hardware complexity, and energy consumption remain unresolved, especially in mobile and large-scale networks.
In the context of terahertz communications, recent works have emphasized photonic-assisted approaches for secure and high-speed wireless links. Photomixing, in which two optical tones are combined in a high-speed photodiode such as a UTC-PD, has emerged as a key enabling technology. Its compatibility with optical fiber infrastructure and ability to generate high-frequency carriers make it attractive for beyond-5G and 6G systems. Several studies have demonstrated THz wireless links exceeding 100 Gbit/s over short distances, highlighting the feasibility of photonic methods for next-generation communication. Importantly, photonic-based THz systems can also support novel security schemes in the analog domain, where encryption is achieved through signal mixing, masking, or logical operations.
The concept of employing logical operations for secure communication has been discussed in both optical and wireless contexts. By dividing an original data stream into multiple sub-streams and applying bitwise operations such as XOR or AND, researchers have shown that information can be concealed unless all sub-streams are simultaneously available. When combined with directional THz beams, this strategy offers inherent spatial selectivity, restricting the possibility of interception to confined regions where multiple beams overlap. This feature aligns well with the high directivity of UTC-PD-based THz transmitters, making logical-operation-based security schemes particularly relevant.
Beyond technical mechanisms, it is also essential to consider the application domains where these approaches are viable. Terrestrial WSNs provide a natural use case, as they typically rely on short-range, line-of-sight communication, where precise beam alignment is feasible. In such networks, PLS techniques can complement cryptographic methods to safeguard sensitive data. By contrast, underwater WSNs suffer from severe attenuation of THz waves due to absorption by water molecules, making them unsuitable for THz-based PLS. Similarly, underground networks face challenges from soil permittivity and scattering, which hinder THz propagation. Therefore, the most promising application domain for logical-operation-based encryption in THz systems lies in terrestrial networks, especially in urban or indoor environments where spatial confinement and infrastructure support are available.
Another important research direction involves integrating PLS with existing wireless infrastructures. For example, hybrid systems that combine PLS with PQC could provide multi-layered protection, defending against both physical-layer attacks and computational threats. Similarly, the coexistence of PLS with reconfigurable intelligent surfaces (RIS) has been proposed to dynamically control wireless propagation environments, further enhancing security. In THz systems, RIS could be used to steer or reshape beams, creating controlled secure zones in dynamic scenarios.
Despite the significant progress in the literature, there are still clear research gaps. First, the tolerance of PLS methods to phase noise, jitter, and misalignment in practical THz systems remains underexplored. Second, comparative analyses between different security schemes—such as beamforming secrecy, noise masking, and logical operations—are limited, making it difficult to evaluate their relative advantages. Third, the scalability of photonic-based PLS to large networks, where multiple transmitters and receivers must be coordinated, presents both a technical and architectural challenge. Finally, energy efficiency is an increasingly important consideration, as schemes that exploit multiple beams or high-power photonic devices inherently consume more power.
Motivated by these challenges, our work builds on prior studies of THz PLS and photonic-based communication to propose a novel scheme in which logical AND operations are realized directly in the analog domain. By transmitting two THz beams carrying complementary data streams and recovering the original data only when both beams overlap and are phase-aligned, the proposed method enhances security while maintaining hardware simplicity. This approach not only addresses some of the shortcomings of prior methods but also opens a new research direction for scalable, spatially selective, and low-complexity physical-layer security in high-frequency wireless networks.
3. The Concept of Employing Logical Operations
3.1. Configuration of the Proposed System
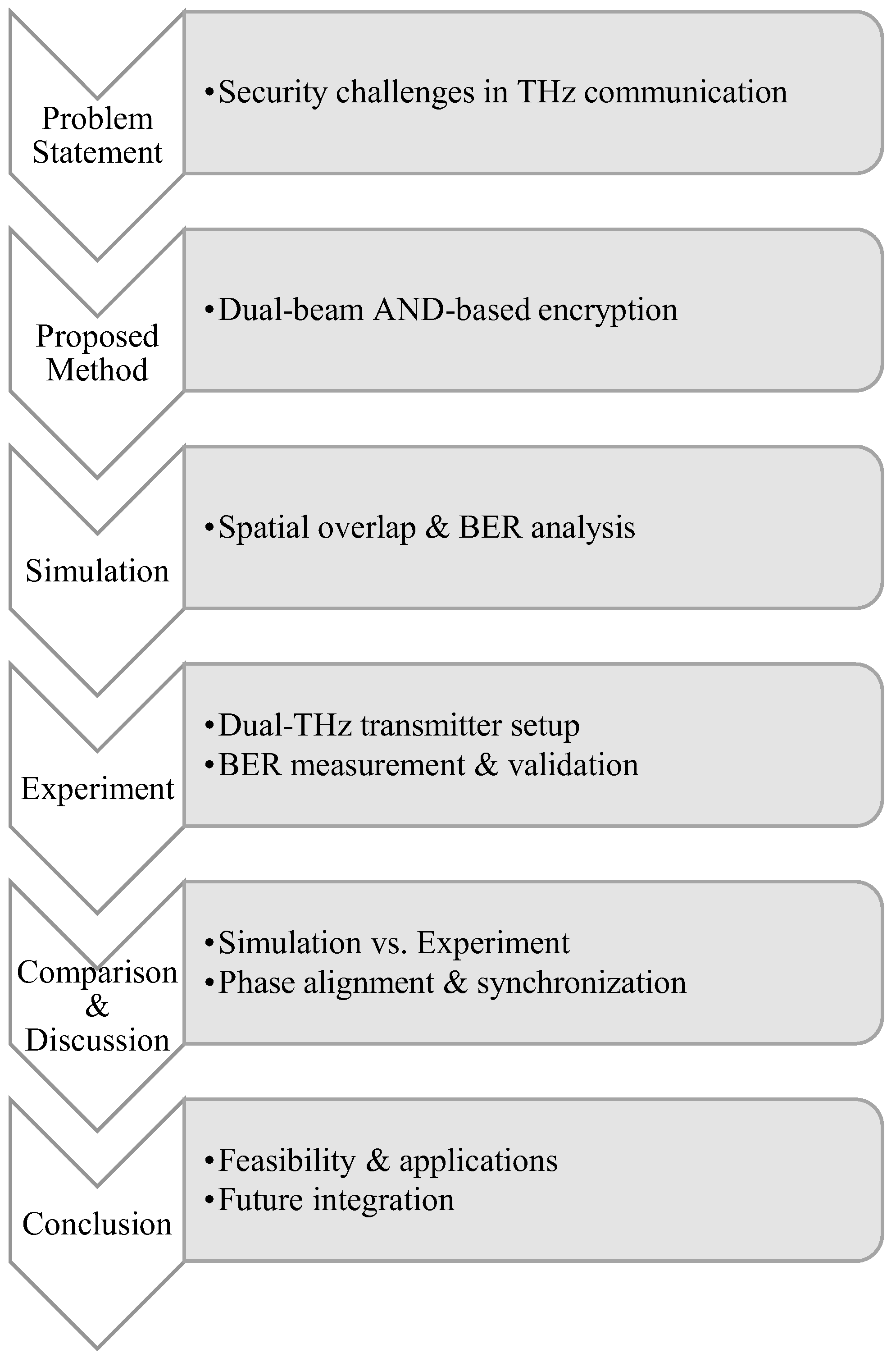
To provide a clear overview of our study,
Figure 1 illustrates the research flow of the proposed terahertz (THz) physical-layer encryption scheme. The flow chart highlights the major steps, starting from the identification of security challenges in THz communication, through the proposal of a dual-beam AND-based encryption method, simulation analysis, and experimental validation, and finally concluding with comparative discussion and key findings. This diagram allows readers to follow how the different components of the work are interconnected and how each stage contributes to demonstrating the feasibility of the proposed approach.
Figure 2 illustrates a proof-of-concept configuration corresponding to our short-range laboratory experiment. For practical deployment, the schematic would require adaptation to larger coverage scenarios by incorporating higher-power transmitters, directive antennas, or beam steering technologies. The physically secured wireless transmission system proposed in this study consists of an encryption module, two optical transmission paths, two THz transmitters, and a decryption module, as depicted in
Figure 2. In the encryption process, the original data are divided into two distinct sequences, labeled Data1 and Data2. For example, Data2 may represent a randomly generated binary sequence, while Data1 is obtained by performing a bitwise logical AND operation between the original data and Data2. At the receiver, the original data can be retrieved by applying the same logical AND operation to the received sequences. While this method does not provide unconditional security as in the one-time pad scheme, it enhances resistance to interception by increasing the computational difficulty of reconstructing the plaintext from a single data stream.
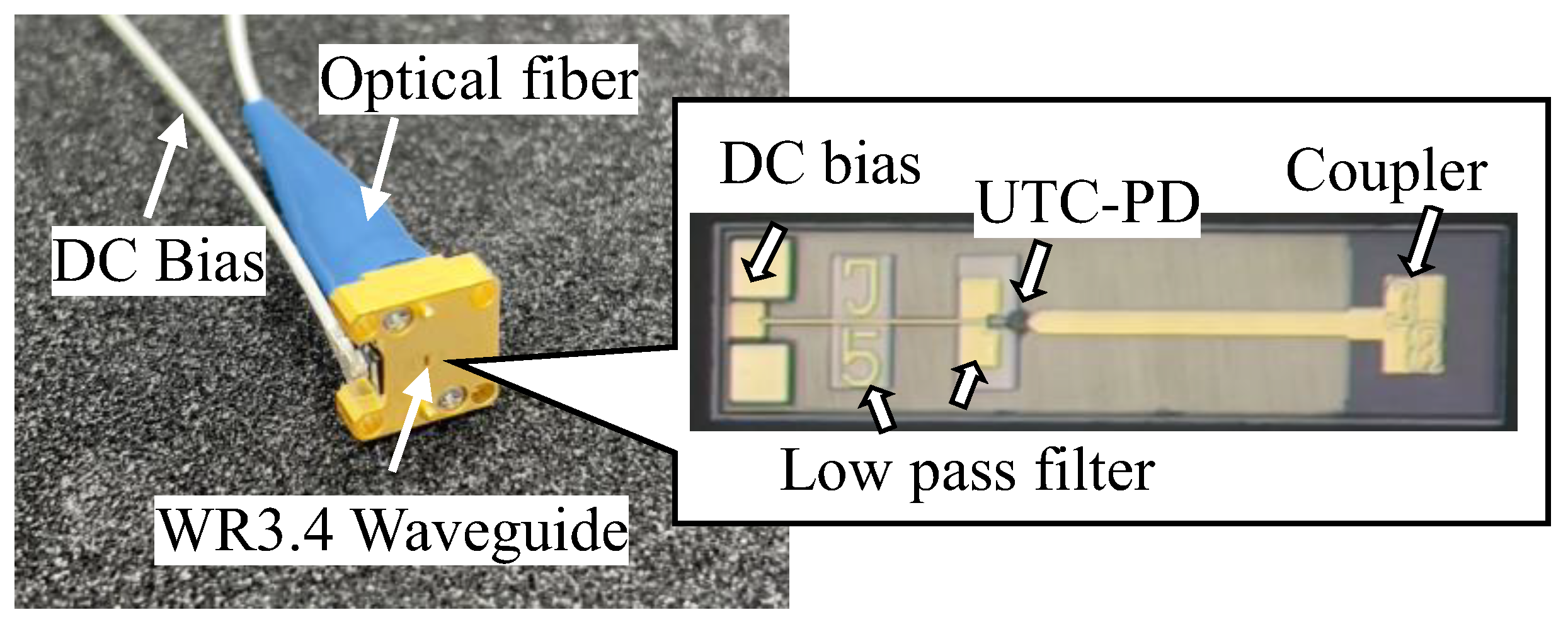
Each data sequence is modulated onto a two-tone optical signal via electro-optic modulators, with the frequency spacing between the tones corresponding to the desired THz carrier frequency. These optical signals are transmitted over separate optical fiber links to two geographically separated THz transmitters, Tx1 and Tx2. At each transmitter, the two-tone optical signal is converted into a THz wave by irradiating it onto the UTC-PD. The generated THz beams (THz1 and THz2) are radiated toward the designated location using horn antennas integrated with the UTC-PD modules.
At the receiver, the two incoming THz waves are mixed to generate a heterodyne signal. By extracting the envelope of this signal, the original data can be recovered through a logical AND operation between Data1 and Data2. Details of the decryption mechanism are presented in the subsequent section.
Successful recovery of the original data requires the simultaneous reception of both THz1 and THz2 signals. This implies that accurate decryption is possible only within a confined spatial region where the two THz beams overlap. Owing to the high directivity of THz waves radiated from UTC-PD modules equipped with horn antennas, the area in which both beams can be received is inherently limited. Furthermore, proper data reconstruction demands not only spatial overlap of the beams but also precise phase alignment between the two data sequences. If the phase offset exceeds one bit period, the decryption process may yield incorrect results. Furthermore, both transmission paths must employ identical modulation formats to ensure successful recovery of the original bit stream. This requirement was satisfied in our experiments by adopting OOK modulation. In practical deployment, additional synchronization mechanisms, such as low-rate pilot training, could further ensure coherent operation, although such procedures were not implemented in the present study.
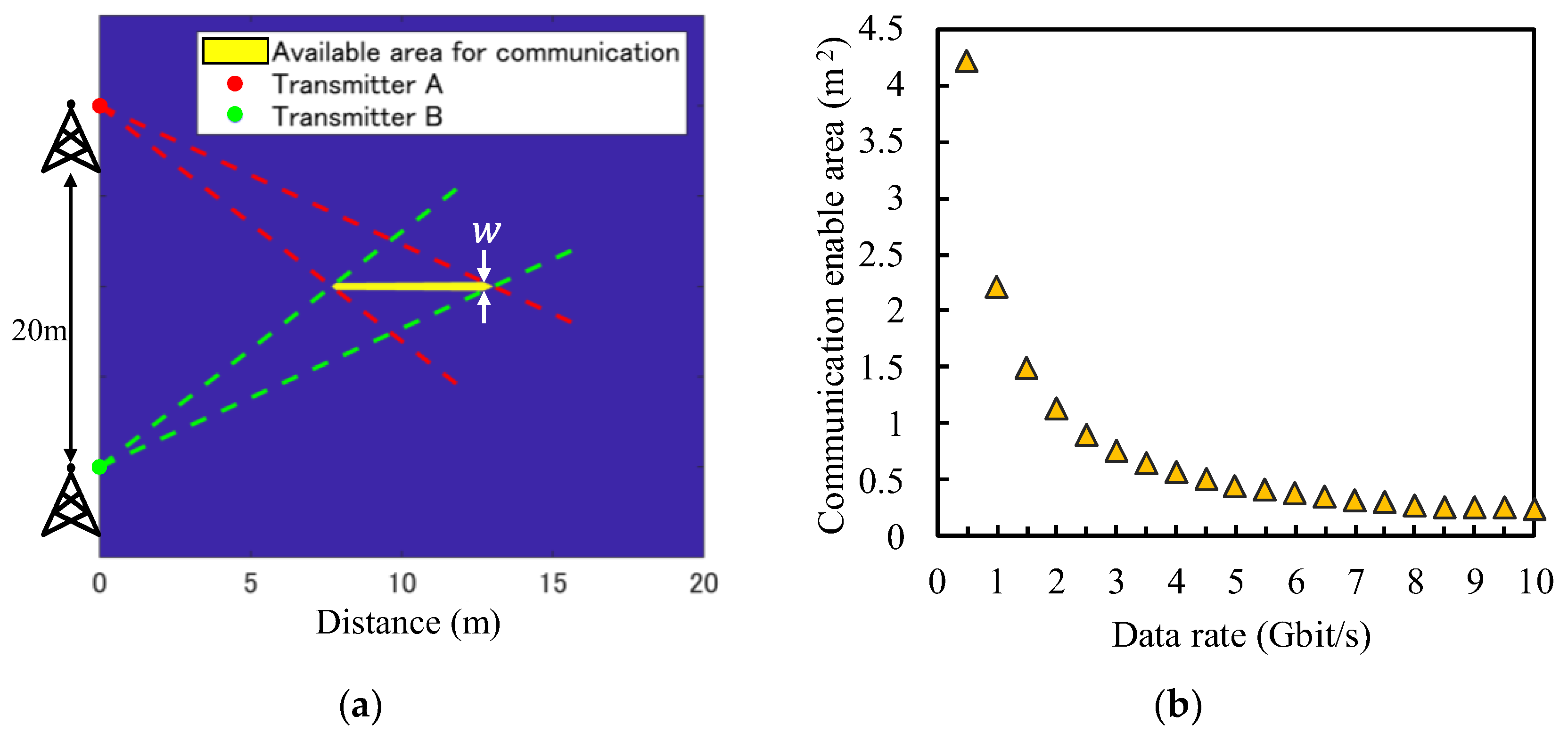
Figure 3a shows the simulated communication area of the system when the distance between the two transmitters is 20 m, the THz beamwidth is 15 degrees, and the bit rate is set to 1 Gbit/s. Here, the communication area is defined by the spatial region where the beams of both THz waves overlap, and their data phases coincide. Although it appears as a narrow line in the figure, its actual width (
W) is approximately 0.045 m, resulting in a finite area of 2.2168 m
2. This indicates that communication is possible within this very narrow region, thereby enabling highly secure wireless communication. The relationship between the bit rate and the resulting communication range is illustrated in
Figure 3b. As shown in
Figure 3b, the bit rate and the communication range are inversely related, and wireless communication with a high bit rate can be performed with higher security. When the bit rate is set to 10 Gbit/s, the communication range is limited to 0.244 m
2.
3.2. Decryption Based on Coherent Detection
Two spatially overlapping THz beams, THz1 and THz2, are considered. The electric fields of the two terahertz waves are expressed as follows, where their amplitudes are denoted by
and
, their frequencies by
and
and their phases by
and
respectively.
When the two THz waves are input into the diode mixer and coherently detected, the output signal
is obtained as follows.
Equation (3) indicates that when two THz waves are coherently detected, the output current becomes proportional to the product of their amplitudes. In other words, the detected signal is strong only when both input waves are present at the same time. Since each wave is modulated by an independent binary sequence using on–off keying (OOK), the multiplication process naturally yields an AND operation: the output is nonzero only when both input bits are ‘1’. The carrier phase difference appears in the intermediate frequency term, but after envelope detection it does not affect the logical result.
Figure 4 shows the schematic of the result of coherent detection between THz1 and THz2 when they are intensity-modulated with different data sequences, 11100011 and 11000110, respectively. When both THz waves are received at the same location and coherently mixed by a photoconductive receiver, the coherently detected signal reflects the instantaneous product of the two input intensities. Therefore, the coherently detected signal appears only when both THz1 and THz2 are simultaneously active (i.e., both data bits are ‘1’). This naturally realizes a bitwise AND operation in the analog domain. The coherently detected signal is then down-converted to baseband using an envelope detector, resulting in a time-domain signal that represents the logical AND of the original data sequences. In this way, both signal mixing (down-conversion) and decryption (logical AND) are performed simultaneously and passively in the physical layer.
This configuration enables a simple receiver architecture without the need for active decryption circuitry or prior knowledge of individual data sequences. Moreover, due to the spatial selectivity of coherent detection with directional THz beams, decryption is only possible within the limited spatial region where both beams overlap, providing an inherent spatial security mechanism. Furthermore, it should be noted that the adoption of UTC-PD photomixing and the self-heterodyne coherent detection scheme is not arbitrary but technically motivated. UTC-PDs allow arbitrary and precise carrier frequency generation by simply adjusting the optical tone spacing, and they are inherently compatible with existing optical communication systems, enabling seamless conversion from fiber to THz. On the receiver side, unlike conventional coherent receivers that require a separate local oscillator, our scheme performs self-heterodyne detection by directly combining the two incident THz beams at the mixer. This approach simplifies the receiver hardware, while the resulting IF amplitude follows the product relation described in Equation (3), naturally yielding an analog-domain AND operation that contributes to the security property of the system.
In this study, on–off keying (OOK) was employed as the modulation format owing to its simplicity and compatibility with the proposed analog-domain multiplication scheme. OOK facilitates a clear demonstration of the logical AND operation, since the product of two binary amplitude-modulated signals naturally yields the intended bitwise result. Although advanced modulation schemes such as QPSK or QAM could potentially improve spectral efficiency, they would also require additional circuitry for carrier recovery and symbol synchronization, thereby complicating the proof-of-concept demonstration. Accordingly, OOK is considered an appropriate and representative choice for verifying the fundamental feasibility of the proposed dual-beam encryption system.
5. Demonstration of Decoding Functions Based on AND Operations
Figure 8 illustrates the temporal waveforms of the transmitted 500 Mbit/s THz signals from UTC-PD 1 (I) and UTC-PD 2 (II), along with the heterodyne-detected waveform obtained at the receiver (III). It can be clearly observed that the detected signal in trace (III) only appears during the time intervals where both signals (I) and (II) are simultaneously nonzero. This behavior directly reflects the logical AND relationship between the two input data streams.
Importantly, this result validates not only the principle of AND-based encryption and decryption at the physical layer, but also the robustness of coherent detection in selectively reconstructing the intended signal. The absence of detectable output when either of the two THz inputs is low confirms that a single data stream alone does not reveal any meaningful information—an essential property for maintaining data confidentiality. Furthermore, the sharp transitions and well-defined bit intervals in the waveform of trace (III) suggest that the system preserves data integrity even at a bit rate of 500 Mbit/s. This behavior also underscores the security enhancement of our scheme: since each stream individually appears as a random-like sequence, no useful information can be extracted without access to both beams. Hence, confidentiality is inherently reinforced at the physical layer.
This experimental result supports the feasibility of implementing secure wireless communication through logical operations in the analog domain, without requiring complex post-processing. It also highlights the potential for scalability to higher data rates, provided that precise phase synchronization and beam alignment are maintained. Beyond the laboratory setup in
Figure 5, the proposed scheme could be adapted to practical environments such as indoor small-cell or backhaul links, where precise alignment is feasible and infrastructure support is available. This adaptability highlights its relevance to future short-range secure THz deployments.
Figure 9 shows the measured bit error rate (BER) as a function of received photocurrent for three different transmission rates: 500 Mbit/s, 1 Gbit/s, and 1.5 Gbit/s. For all data rates, the system achieved BERs below the hard-decision forward error correction (HD-FEC) threshold, indicating the feasibility of logical-AND-based secure transmission at gigabit-level rates. A minimum BER of 3.13 × 10
−10 was observed at 6.65 mA for the 500 Mbit/s signal, whereas higher bit rates, such as 1.5 Gbit/s, required significantly more received power (8.55 mA) to achieve a BER of 4.67 × 10
−9.
One important factor contributing to the BER degradation at higher bit rates is the limited bandwidth of the envelope detector used in this study. Specifically, the detector has a 3-dB bandwidth of 500 MHz, which is sufficient for resolving the 500 Mbit/s signal but becomes increasingly inadequate for accurately detecting faster signals. At 1.5 Gbit/s, the signal contains frequency components beyond the detector’s passband, leading to signal distortion, reduced amplitude fidelity, and timing jitter in the recovered waveform. This bandwidth limitation effectively acts as a low-pass filter, distorting the envelope shape of high-speed heterodyne signals and increasing inter-symbol interference (ISI), which ultimately contributes to higher BERs.
Therefore, while the experimental results validate the principle and feasibility of physical-layer encryption via logical AND operations, they also highlight the importance of component-level bandwidth in determining system performance. In future implementations targeting higher bit rates, increasing the bandwidth of the envelope detector—or replacing it with a high-speed digital demodulation technique—would be essential to preserve signal integrity. Additionally, optimizing the signal-to-noise ratio through enhanced UTC-PD power output and low-noise receiver design could further mitigate BER degradation at high data rates.
Figure 10 highlights, in yellow, the region estimated to be available for communication at 500 Mbit/s, based on the antenna radiation patterns and FMBD receiver characteristics. The simulation estimated the available communication area at 500 Mbit/s to be approximately 6.360 cm
2.
Table 2 summarizes the parameters employed in simulation evaluations. The simulation parameters include carrier frequency, antenna gains, and beam geometry. These parameters are values obtained experimentally. In the simulation, transmitters A and B were placed at positions corresponding to the experimental setup, and signal reception was evaluated at angles of ±10 degrees relative to the receiver. The analysis also considered the bit misalignment caused by the difference in propagation distance between the two transmitters.
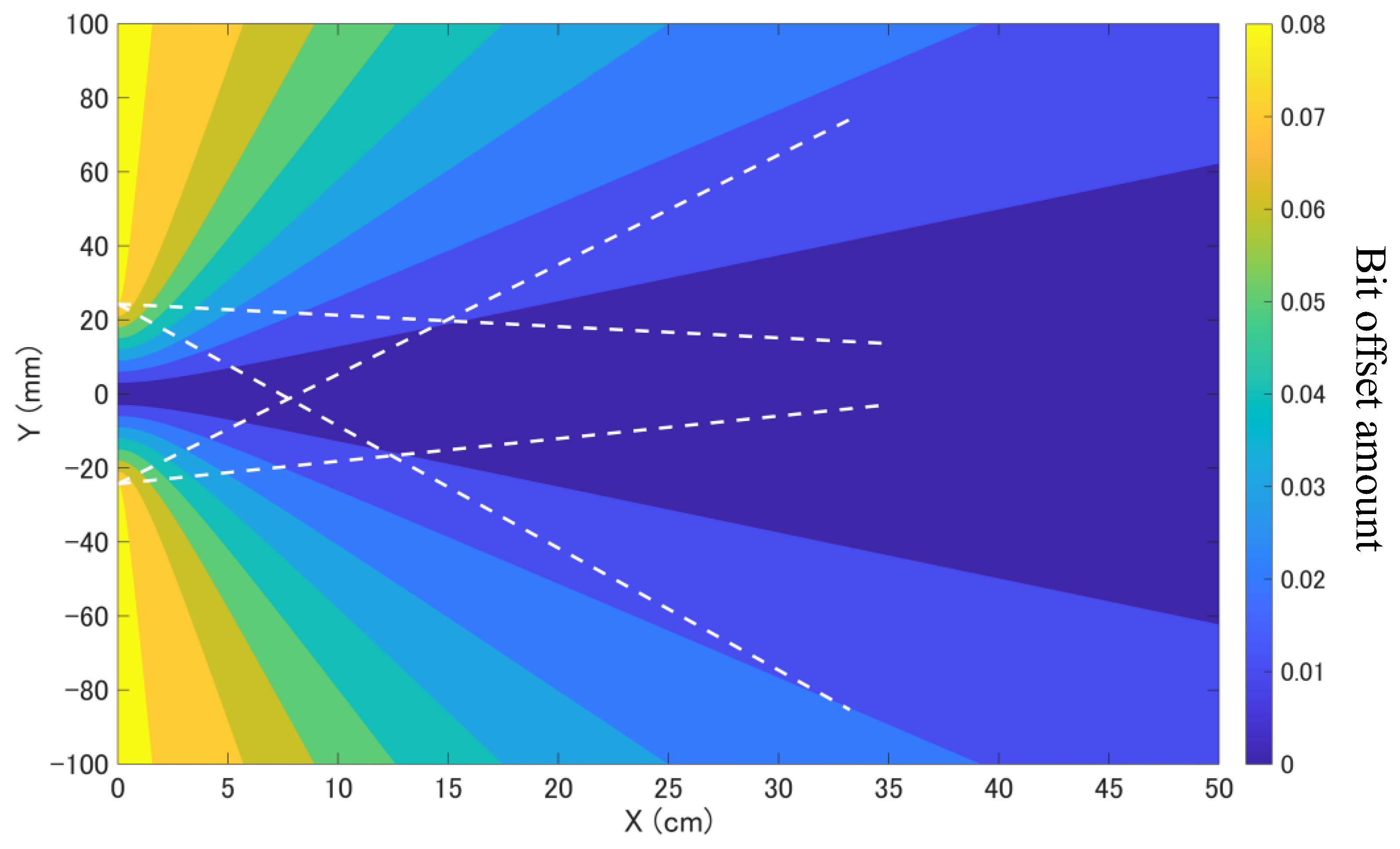
Figure 11 presents the spatial distribution of bit offset using a colour map. As shown, under the experimental conditions employed, no bit offset was observed. This implies that the secure communication range in this simulation is not solely determined by the occurrence of bit offset, but also strongly depends on the received power. Accordingly, by regulating the transmitted power, it is possible to further enhance the security level, in addition to the control achieved through bit offset.
From a practical implementation perspective, the computational complexity of the proposed scheme is significantly lower than that of conventional cryptographic protocols such as RSA or PQC. Unlike these methods, which require iterative digital operations, the logical AND operation in our scheme naturally emerges from the analog multiplication of two THz beams, as described in Equation (3). Consequently, decryption is performed passively in the physical layer with constant complexity, O(1) per bit. The hardware overhead is limited to standard THz front-end devices (UTC-PDs, FMBD, and an envelope detector), meaning that the computational burden is negligible compared with software-based cryptographic schemes. Instead, the practical complexity of our system lies mainly in maintaining beam overlap and phase alignment, which introduces synchronization and alignment overhead rather than computational cost.
Next, the simulated BER variation with respect to the receiver position was compared to the experimental results. The simulation evaluated the bit error rate (BER) performance of the proposed dual-transmitter AND-operation scheme under on–off keying (OOK) with direct detection.
First, the system geometry is defined by the transmitter positions (
) and (
), the receiver grid with step size
, and the beam parameters: center directions
and half-power beamwidths,
. The transmitted power is
, and the antenna gains
(converted from dBi) are modeled using a radiation pattern. The free-space path loss is calculated as
where
is the distance from transmitter
to each grid point, and
is the wavelength corresponding to the carrier frequency
GHz.
In this instance, the terahertz waves strike the Si-based FMBD receiver at an oblique angle. Consequently, attenuation due to the angle of incidence must also be taken into account. Additional angular attenuation is applied using an empirical quadratic model, and the medium transmissivity is expressed as
with
the baseline transmissivity and
an experimentally determined exponent.
The received power at each grid point is then
where
is the angular attenuation term, and only points within the beamwidth are considered.
The signal-to-noise ratio (SNR) per branch is obtained as
with
the Boltzmann constant,
, and
GHz.
In direct detection OOK, the bit error rate (BER) for each branch is approximated as follows [
32,
33].
To model the AND operation, the combined BER is given by
If the relative path length difference corresponds to a bit offset exceeding the threshold , the BER is set to unity, i.e., correct decoding is impossible.
Finally, a communication-available region is defined by the condition
where the BER threshold is set to
(HD-FEC limit). Spatial maps of the bit offset, binary availability, BER profiles, and BER versus received power are generated accordingly.
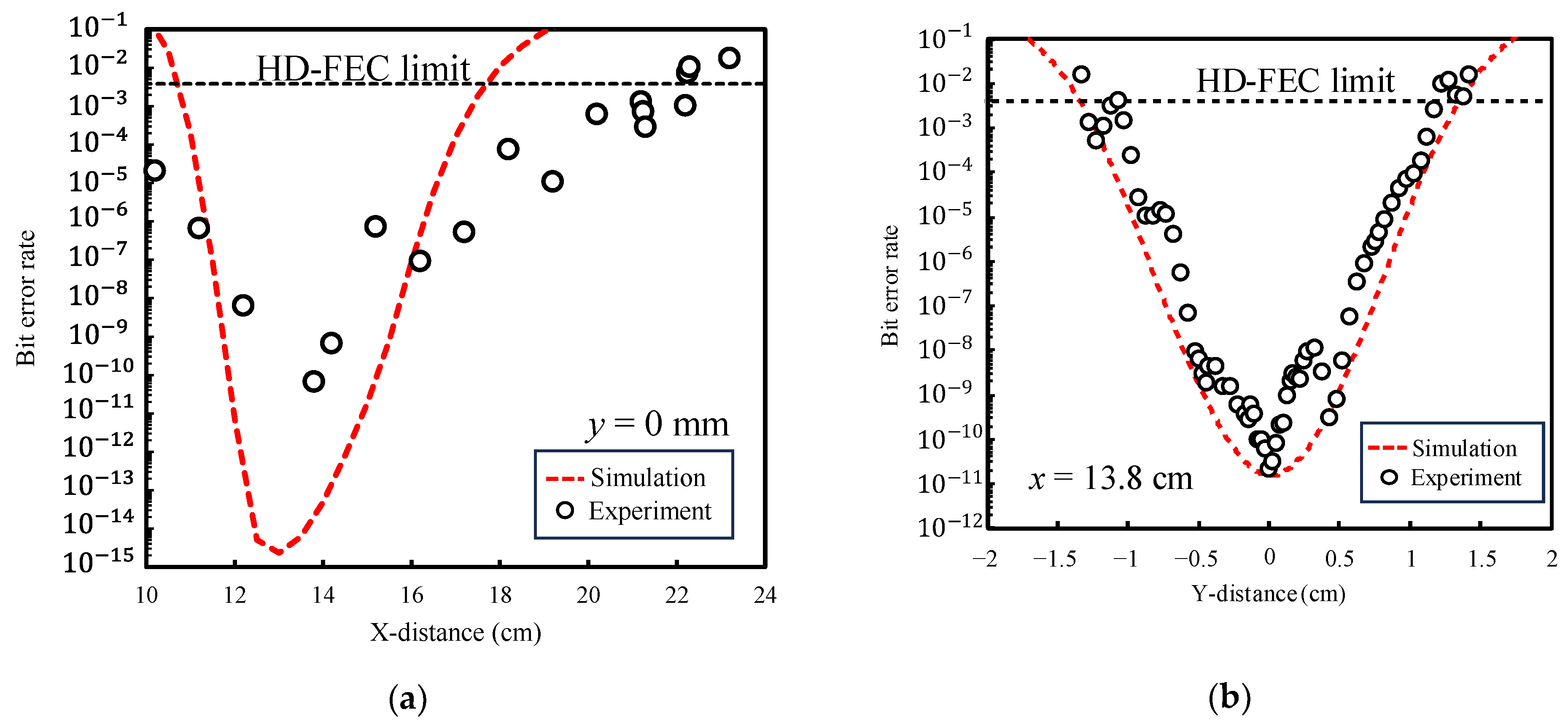
Figure 12a shows that when the FMBD receiver was moved along the x-axis, agreement with the experimental data was not achieved due to insufficient positioning accuracy. In contrast,
Figure 12b demonstrates that when the receiver was moved along the y-axis, the experimental results were in close agreement with the simulated trend. These findings indicate that the simulated communication coverage and BER variation can faithfully reproduce the actual system performance. The prediction accuracy of the simulation was evaluated from
Figure 12b. The proposed model reproduced the experimental BER tendency with an R
2 of 0.84 on a log-scale, while the mean deviation was about 0.91 decades (≈8×). These results indicate that the model captures the overall trend well, although systematic factors such as receiver noise and alignment loss may contribute to the residual discrepancy. Therefore, the model is considered reliable for predicting and optimizing similar secure wireless transmission setups.
From a system design perspective, these results highlight the strong spatial selectivity inherent in the AND-based physical-layer encryption approach. The secure communication zone is clearly defined, contributing to enhanced physical-layer security by naturally restricting the reception area to a well-controlled spatial region. This characteristic is particularly beneficial for applications requiring high confidentiality and targeted wireless transmission.
Moreover, the clear correspondence between experimental observations and simulation results demonstrates the high fidelity of the proposed simulation model. This consistency indicates that the model accurately captures the key physical-layer phenomena—including beam overlap and phase alignment—and can be effectively utilized for system optimization. Such predictive capability is expected to facilitate the design of future secure THz wireless systems, including those incorporating advanced functions such as beam steering, phase control, or spatial diversity techniques to further improve robustness and adaptability.
6. Conclusions
In this work, we have demonstrated a novel physical-layer encryption scheme based on logical AND operations between dual THz beams transmitted from spatially separated transmitter. The system utilizes coherent detection and envelope extraction to recover encrypted data without relying on upper-layer cryptographic protocols. Experimental validation confirmed the feasibility of this approach at data rates up to 1.5 Gbps, with 500 Mbit/s showing particularly low BER values even under modest received power levels. Through spatial BER mapping and comparative simulation analysis, we identified the usable communication area and highlighted the constraints imposed by beam alignment and timing synchronization. While our present experiments did not include explicit synchronization mechanisms, a potential practical solution would be to use staged low-rate training followed by gradual rate escalation before transmitting actual data. Such an approach could mitigate phase noise and environmental misalignment, thereby improving the applicability of the scheme to real-world scenarios. The strong agreement between experimental and simulated results validates the accuracy of our system model, achieving a predictive accuracy of approximately 84%, and confirms its utility in designing future secure THz wireless systems. Overall, this study provides a foundation for scalable, hardware-efficient physical-layer security in next-generation wireless communication, particularly in high-frequency domains such as THz, where beam directivity can be harnessed to restrict access and enhance confidentiality. In addition, the inherently narrow overlap region of the dual beams strongly limits the eavesdropping area, as receivers outside this zone inevitably experience insufficient power or bit misalignment, resulting in BER values close to unity. By adjusting the transmit power in addition to beam overlap constraints, the system can further enhance resistance to interception. Naturally, exploiting two transmission paths introduces additional power consumption compared to a single-link system. However, this overhead is balanced by the significant gain in confidentiality, as eavesdroppers cannot recover data from a single stream. In future implementations, energy-efficient designs such as low-power UTC-PDs or duty-cycled operation could mitigate this trade-off. Moreover, the proposed framework is expected to facilitate the development of more robust and adaptive secure systems through the integration of advanced functionalities such as beam steering, phase control, and spatial diversity techniques in future implementations. Finally, we note that the proposed scheme is well suited for integration with existing wireless infrastructures. Its compatibility with photonic fiber–THz conversion allows straightforward deployment in terrestrial small-cell scenarios. By combining our physical-layer approach with synchronization protocols and higher-layer cryptography, the system can provide multi-layered, practical security in future 6G networks. It should also be emphasized that the present work employed identical modulation formats across both transmission paths to ensure reliable recovery of the original data stream. In practice, however, disparities in channel characteristics—such as path-dependent attenuation, fading, or phase distortion—may arise between the two beams. Under such conditions, enforcing identical modulation on both paths may lead to performance imbalance and reduced decoding efficiency. Future research should therefore explore adaptive mechanisms that mitigate such disparities, for example through dynamic power control, coding redundancy, or channel-specific pre-compensation. Incorporating these techniques would enhance the robustness and scalability of the proposed scheme in realistic wireless environments.