1. Introduction
In modern cryptographic systems and secure communication frameworks, the random number generator (RNG) serves as a fundamental module, widely utilized in key generation, authentication challenges, initialization vectors, and large prime number construction. The quality of its output directly impacts the overall security of the system. Among various RNG types, the pseudorandom number generator (PRNG) is extensively adopted in security-sensitive scenarios due to its advantages such as high generation speeds, simple implementation, and low resource consumption. It is particularly suitable for embedded devices, low-power chips, and applications where the security requirements are not extremely stringent. Although PRNGs cannot theoretically achieve the unpredictability of physical randomness sources, they remain the mainstream choice for entropy source modules in information security chips, owing to their controllability and widespread applicability. As such, PRNGs constitute a crucial component in many lightweight security architectures.
However, with the continuous evolution of security threats—especially in practical attacks targeting embedded hardware and cryptographic chips—PRNGs now face risks that extend beyond algorithm-level security [
1,
2,
3]. Fault injection attacks (FIAs), as a practical and targeted physical attack method, are emerging as a critical threat to PRNG security [
4,
5]. By precisely manipulating environmental parameters such as the voltage, electromagnetic field, or temperature, attackers can disturb the operational state of the chip without damaging its packaging [
6], resulting in abnormal behaviors such as register flips, timing violations, or erroneous logic paths within the circuitry [
7]. For instance, electromagnetic fault injection may induce transient voltages in the target chip through localized electromagnetic pulses, potentially flipping logic states [
8]; similarly, single-event effects (SEEs) caused by high-energy particles may result in logic bit flips within storage cells [
9,
10,
11]. Such disturbances can disrupt the pseudorandom number generation process and even indirectly expose internal seeds or intermediate key values, significantly undermining the system’s security [
12]. In the domain of SEE-based fault injection, various technical approaches have been explored. Cheng et al. [
13] proposed a software-based fault injection method using random forest algorithms to predict instruction vulnerability, aiming to improve the injection efficiency through machine learning. However, this approach primarily focuses on optimizing faults in data and control flows from a single-dimensional perspective, without adequately addressing the time cost in large-scale IC simulations. Liao introduced a mixed-signal simulation methodology that combines SPICE-level accuracy with gate-level simulation speeds. Nevertheless, the analysis of the data validity and logic gate state correlation remains insufficient, particularly when addressing ineffective faults in storage modules and combinational logic [
9].
The Counter Mode Deterministic Random Bit Generator (CTR-DRBG), a standardized PRNG architecture based on the Advanced Encryption Standard (AES) algorithm, is widely adopted in information security systems and automotive-grade chips due to its robust security and implementation feasibility. It employs a counter mode combined with symmetric encryption for state updates and integrates entropy feedback mechanisms to enhance unpredictability, making it one of the most commonly used high-quality RNG modules in the industry. However, research has indicated that AES-like encryption architectures may be susceptible to key leakage under fault injection conditions [
14]. Given the CTR-DRBG’s complex data paths, feedback structure, and state dependencies, such physical disturbances may induce significant systemic vulnerabilities through cascading failures.
Existing research typically employs techniques such as FPGA reconfiguration and scan-chain injection for the simulation of SEEs [
15,
16,
17,
18], while electromagnetic fault injection relies on dedicated hardware platforms to introduce transient disturbances [
7]. In parallel, countermeasures against side-channel attacks have advanced significantly, with growing attention paid to enhancing the side-channel resistance of FPGA-based cryptographic systems and automotive-grade chips. Nevertheless, protection mechanisms against fault injection attacks remain comparatively underexplored [
19,
20,
21,
22]. Most studies focus on the impact of single fault types, lacking comprehensive evaluation under multidimensional perturbations such as temperature, electromagnetic interference, and voltage fluctuations.
This study investigates the robustness of the CTR-DRBG under multidimensional fault injection scenarios, focusing on three representative physical attack vectors: temperature variation, electromagnetic disturbance, and voltage fluctuation. A highly controllable FPGA-based experimental platform is developed to emulate real-world operating environments and fault conditions. To address the challenges of low success rates and poor repeatability in physical fault injection experiments, a bit-flip fault simulation mechanism at the RTL level is introduced. Faults are injected during the logic synthesis phase, enabling the controlled analysis of the fault sensitivity and error propagation paths across system modules [
9]. Through the comparative analysis of the output random sequences before and after fault injection, the study identifies potential vulnerabilities and structurally sensitive regions within the CTR-DRBG under multidimensional disturbances. The findings validate the combined impacts of different fault types on the output consistency, feedback loop stability, and randomness quality. These results provide quantifiable experimental data and an analytical framework to support the fault-tolerant design and security assessment of automotive-grade chips and high-assurance cryptographic modules.
To contextualize our framework, it is important to highlight both its strengths and limitations relative to existing approaches. Traditional EMFI/glitch benches provide realistic disturbances but generally suffer from low repeatability and limited spatial precision, while FPGA SEU/SEE simulation platforms (e.g., RTL SEU injection frameworks or radiation-based testbeds) offer controllability and statistical coverage but do not capture the complex noise interactions present in real environments.
The proposed combined “physical + RTL bit flip” framework complements these existing practices by bridging realism and controllability. The RTL simulation component enables precise and repeatable injections at specific registers and clock cycles, facilitating sensitivity analysis and fault-propagation tracing with minimal experimental overhead. In contrast, the physical injection component, although less controllable, directly reflects the impact of real-world disturbances. By cross-verifying persistent deviations across both domains, the framework enhances the explanatory power and robustness evaluation.
2. CTR-DRBG Based on the AES Encryption Algorithm
Before conducting fault injection experiments, it is essential to establish a reliable and standard-compliant pseudorandom number generation architecture. This section introduces the internal design of the CTR-DRBG based on the AES encryption algorithm and outlines the statistical testing method used to evaluate its output randomness. These two aspects provide the necessary foundation for the subsequent robustness analysis under physical disturbances.
2.1. CTR-DRBG
AES is a symmetric encryption algorithm officially released by the U.S. National Institute of Standards and Technology (NIST) in 2001. It is widely applied in communication, finance, defense, and other fields. Due to its efficiency, security, and implementability, AES has become one of the most widely adopted encryption algorithms. AES supports key lengths of 128, 192, and 256 bits. Among them, AES-128 is commonly used in embedded systems and hardware encryption modules due to its balanced trade-off between security and resource consumption.
The CTR-DRBG is a pseudorandom number generation mechanism specified by NIST in the SP 800-90A standard [
23]. It is widely adopted in cryptographic modules, encrypted communication, and embedded security systems. Based on symmetric encryption, the algorithm employs a counter mode to process the key and initial seed, thereby generating pseudorandom bit sequences with high entropy and unpredictability.
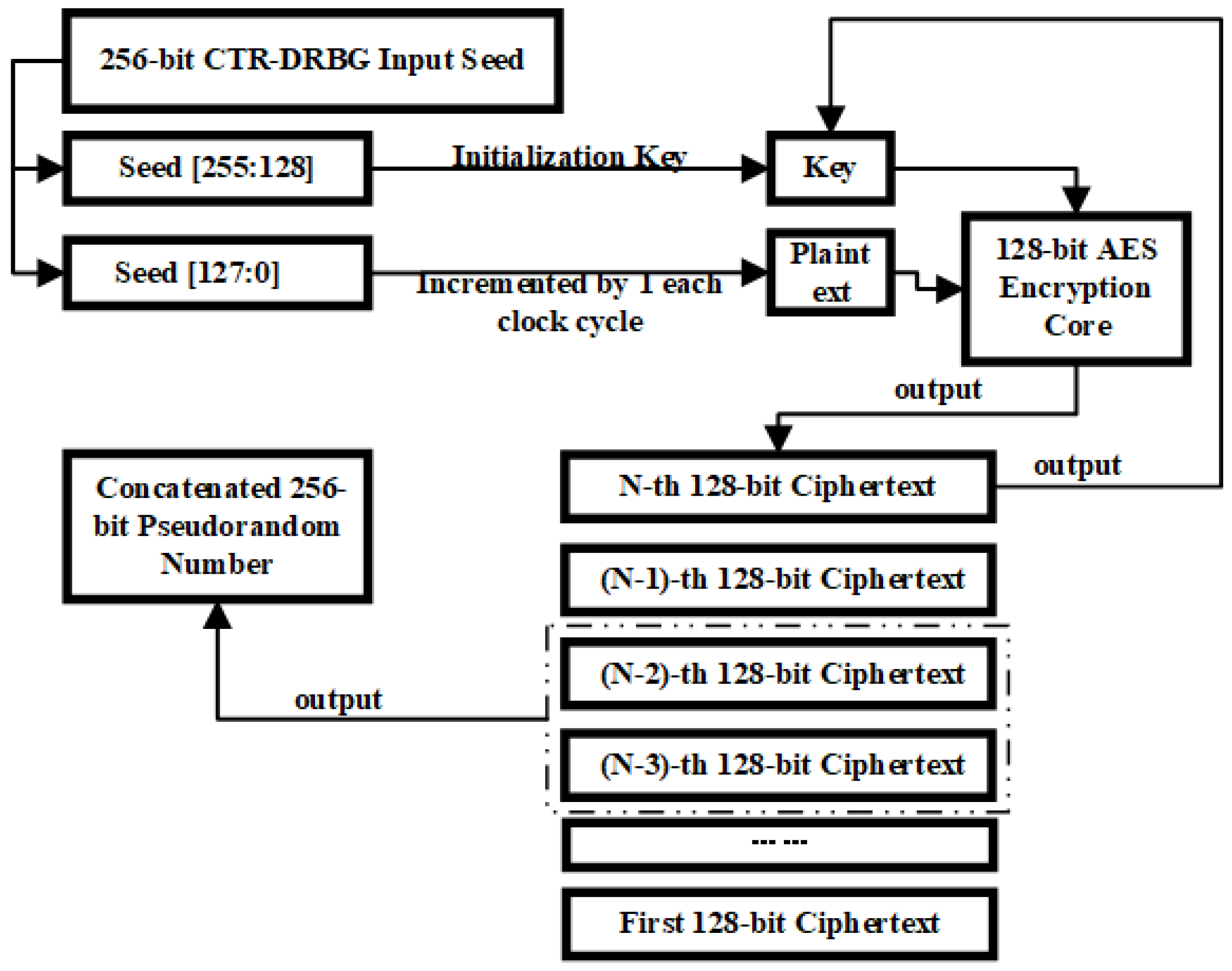
The CTR-DRBG operates by encrypting a monotonically increasing counter value using a block cipher, outputting the encrypted result as the pseudorandom sequence. A seed update mechanism is incorporated to maintain output randomness and security. As shown in
Figure 1, the CTR-DRBG in this design adopts AES-128 as its core encryption engine. The 256-bit input seed is divided into two parts: the upper 128 bits serve as the AES encryption key, and the lower 128 bits act as the initial counter value. During random number generation, the current counter is encrypted by the AES module to produce a random output, and the counter is incremented after each operation to continuously generate random bit blocks.
To enhance the complexity of the output patterns, a feedback mechanism is introduced. The generated output is used to update the encryption parameters for the next round, ensuring that both the encryption key and plaintext inputs to the AES module evolve dynamically during the generation process. Two consecutive 128-bit outputs are concatenated to form a single 256-bit pseudorandom number output.
2.2. NIST SP 800-22 Randomness Standard
To evaluate the statistical randomness of the output sequences generated by the design, the NIST SP 800-22 standard—developed by the U.S. National Institute of Standards and Technology [
24]—is adopted. This test suite provides a systematic and quantitative approach to evaluating the randomness of sequences used in cryptographic systems, ensuring that the output meets essential requirements for unpredictability and uniform distribution.
The NIST SP 800-22 suite includes 15 statistical tests, as summarized in
Table 1, each designed to assess a specific characteristic of a random sequence, such as the bit frequency, run distribution, block frequency, autocorrelation, and compressibility. Representative tests include the frequency test, block frequency test, runs test, longest run of ones test, discrete Fourier transform test, and linear complexity test. These tests analyze the distribution and behavioral patterns of the generated pseudorandom sequences from multiple dimensions, aiming to detect potential biases or structural defects.
It should be noted that the NIST SP 800-22 test suite only provides statistical evaluations of the output sequences generated by the random number generator. Passing these tests demonstrates that the output exhibits desirable randomness properties, such as unpredictability and a uniform distribution, but does not guarantee full compliance with the CTR-DRBG algorithmic specification defined in NIST SP 800-90A. Furthermore, SP 800-22 does not address entropy source characterization or health testing, which are covered by NIST SP 800-90B and SP 800-90C.
In this work, the SP 800-22 suite is used solely to assess the statistical quality of the generated sequences. Algorithmic conformance to CTR-DRBG and entropy source health are outside the scope of this study.
3. Fault Injection Testing Framework
In typical embedded application scenarios such as automotive electronics, industrial control systems, and IoT terminals, devices often operate in complex and uncontrollable external physical environments. The primary sources of interference in these settings include electromagnetic radiation, power supply fluctuations, and extreme temperature conditions. Among them, electromagnetic interference is prevalent in power systems, high-frequency wireless communication environments, and engine operation contexts, and it can easily affect sensitive nodes within the chip. Voltage fluctuations may result from unstable power supplies, abrupt load changes, or defects in power system design and are common causes of failure in embedded systems. Temperature variation—particularly during low-temperature cold starts or high-temperature, high-load operation—can directly impact the electrical characteristics and timing reliability of semiconductor devices.
Accordingly, this study selects these three representative environmental disturbance sources—electromagnetic interference, voltage fluctuation, and temperature variation—as the basis for fault injection. These sources not only possess strong practical relevance but also closely reflect the real-world fault scenarios that secure chips may encounter when operating under complex environmental conditions.
3.1. Single-Dimensional Fault Injection Mechanisms and Test Platforms
3.1.1. Electromagnetic Fault Injection
Electromagnetic (EM) fault injection is a non-contact attack technique based on electromagnetic induction. Its fundamental principle involves generating transient or continuous electromagnetic fields near the target chip to induce abnormal voltages or currents within the circuit [
25,
26,
27], thereby disrupting normal functions or triggering erroneous behavior. Currently, EM injection is mainly implemented in two forms: transient electromagnetic pulse injection and electromagnetic harmonic radiation.
Transient EM pulse injection typically involves applying high-amplitude, narrow-width voltage pulses across the coil of an EM probe, generating a strong transient electromagnetic field. This field causes abrupt changes in voltage or current at critical internal nodes of the chip, potentially leading to logic errors. In contrast, harmonic EM injection couples a sinusoidal interference signal into sensitive signal lines of the chip and fine-tunes the frequency to achieve subtle behavioral disturbances. Compared with transient pulses, harmonic injection introduces smoother voltage disturbances, making it less likely to be detected by voltage monitors or protective circuits. It offers higher concealment and controllability and can be performed without decapsulating the chip, enabling precise disturbances to specific regions. As a result, it has become a key focus in current fault injection research.
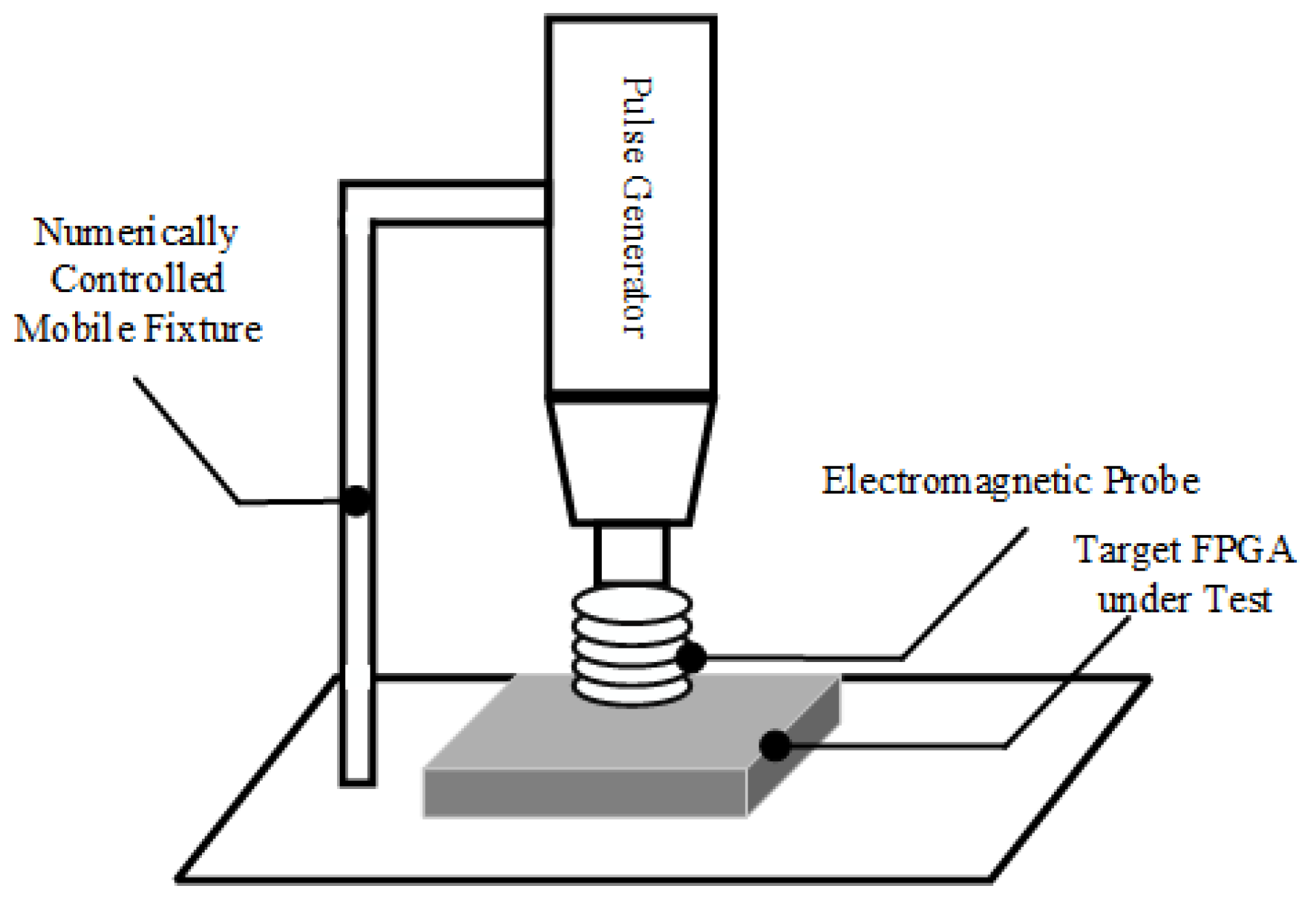
The EM injection experiments in this study are conducted using a platform capable of up to five injection attempts with a maximum field strength of 5 V/m. As shown in
Figure 2, the EM fault injection setup targets a PRNG implemented on an FPGA. The method employs a dedicated EM probe to apply localized high-frequency electromagnetic signals to the logic configuration area of the FPGA board, interfering with the internal cryptographic logic or data paths. This setup provides high injection precision and significant attack effectiveness.
3.1.2. Voltage Fault Injection
Voltage glitch injection is an attack technique that disrupts the normal operation of a chip by manipulating its supply voltage. This method introduces brief, precisely timed voltage fluctuations—typically lasting on the nanosecond or even picosecond scale—which alter the biasing conditions of transistor circuits within the chip [
28]. These disturbances may cause logic errors or computation faults, potentially bypassing security mechanisms or leaking sensitive data.
Effective voltage glitching requires precise timing control. Attackers must first identify the critical operation window of the target device and then inject a voltage glitch at the exact moment. Due to process variations in semiconductor manufacturing, the effectiveness and repeatability of glitch attacks can vary. To counteract such threats, multilayered protection strategies are adopted: at the physical level, voltage monitors, glitch detectors, and power filtering networks are used; at the architectural level, redundancy and error detection are introduced; and, at the system level, randomized execution timings increase the attack complexity.
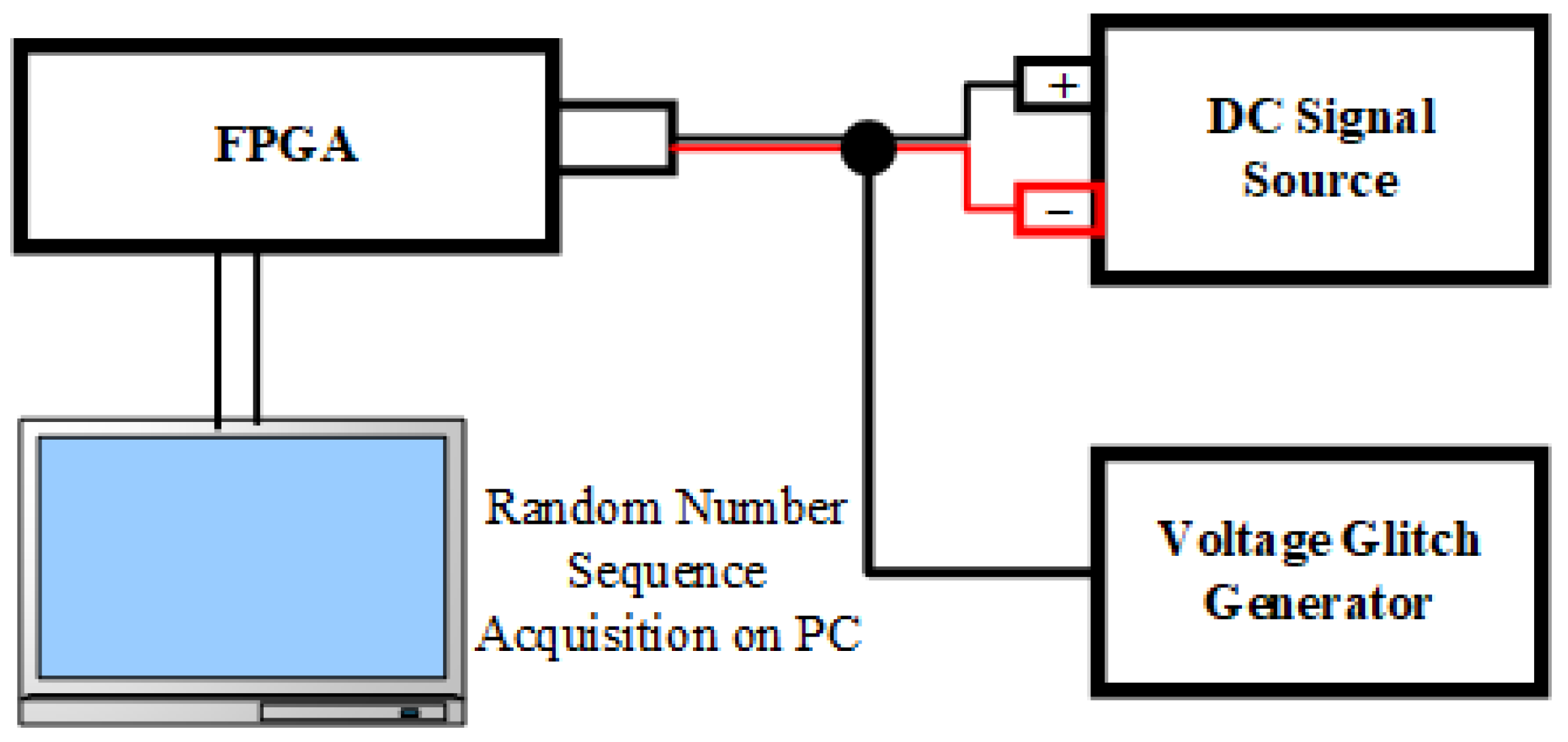
In practical experiments, voltage glitch injection is typically achieved by modifying the supply voltage or superimposing glitches on the power supply pins. These perturbations can violate the setup and hold time requirements in flip-flops, leading to data corruption. An insufficient voltage can also increase the logic delay and slow register transitions, which may result in incorrect values being latched. The fault injection platform used in this study, shown in
Figure 3, provides a controlled power supply and configurable voltage glitches. The standard supply voltage is 3.3 V for normal FPGA operation, while the glitch parameters include the glitch count (<5) and amplitude (−5 V to 5 V).
3.1.3. Temperature Fault Injection
Temperature fault injection is a physical attack technique that induces computational or logical errors by altering the ambient temperature of a chip or electronic device. Semiconductor components are highly sensitive to temperature variations, and attackers can exploit this characteristic to interfere with system operation, compromise cryptographic processes, bypass authentication, or extract sensitive data [
29].
Temperature changes can significantly affect transistors’ electrical properties—for example, high temperatures increase the leakage current, while low temperatures may introduce abnormal signal delays. These effects can impair the stability of logic gates and memory elements such as registers and SRAM. Additionally, temperature-induced disturbances may affect clock synchronization, leading to timing errors such as instruction skips or repeated executions. In extreme cases, temperature changes can also trigger power supply fluctuations, further exacerbating the internal logic instability. Collectively, these phenomena pose significant threats to system security and reliability.
In this study, temperature fault injection is conducted using a programmable thermal chamber, as illustrated in
Figure 4. The chamber simulates external thermal environments with a configurable temperature range of −40 °C to 100 °C, enabling the controlled testing of device behavior under extreme conditions.
3.2. Multidimensional Combined Fault Injection
In practical attack scenarios, single-dimensional physical perturbations often struggle to compromise secure modules equipped with basic protection mechanisms [
30]. To comprehensively evaluate the robustness of the CTR-DRBG under compound disturbance conditions, this study designs and implements multidimensional fault injection experiments involving pairwise combinations of three techniques—voltage glitching, electromagnetic interference, and temperature variation—as well as the simultaneous injection of all three.
The experiments are conducted on a controllable and repeatable FPGA-based platform. A synchronized multisource disturbance environment, as illustrated in
Figure 5, is constructed using a programmable voltage source, a high-frequency EM injection probe, and a temperature-controlled thermal chamber. Specifically, for two-dimensional combined injections, the configurations include Voltage + EM, Voltage + Temperature, and EM + Temperature. In each case, the fault intensity of individual sources is appropriately reduced compared to single-dimensional injection to avoid hardware damage. For three-dimensional injections, precise timing control is applied to align the fault injection windows, ensuring that all three disturbances converge during critical moments such as seed updating and output generation, thereby forming a compound interference peak.
During the experiments, the output pseudorandom sequences generated by the CTR-DRBG are captured in real time and compared against prerecorded reference sequences to determine whether the fault has introduced persistent disruptions to the core cryptographic logic. To ensure a thorough evaluation, each combined fault injection configuration is executed for at least five rounds, with all output variations recorded for analysis.
3.3. Fault Injection Success Determination Mechanism Based on Output Sequences
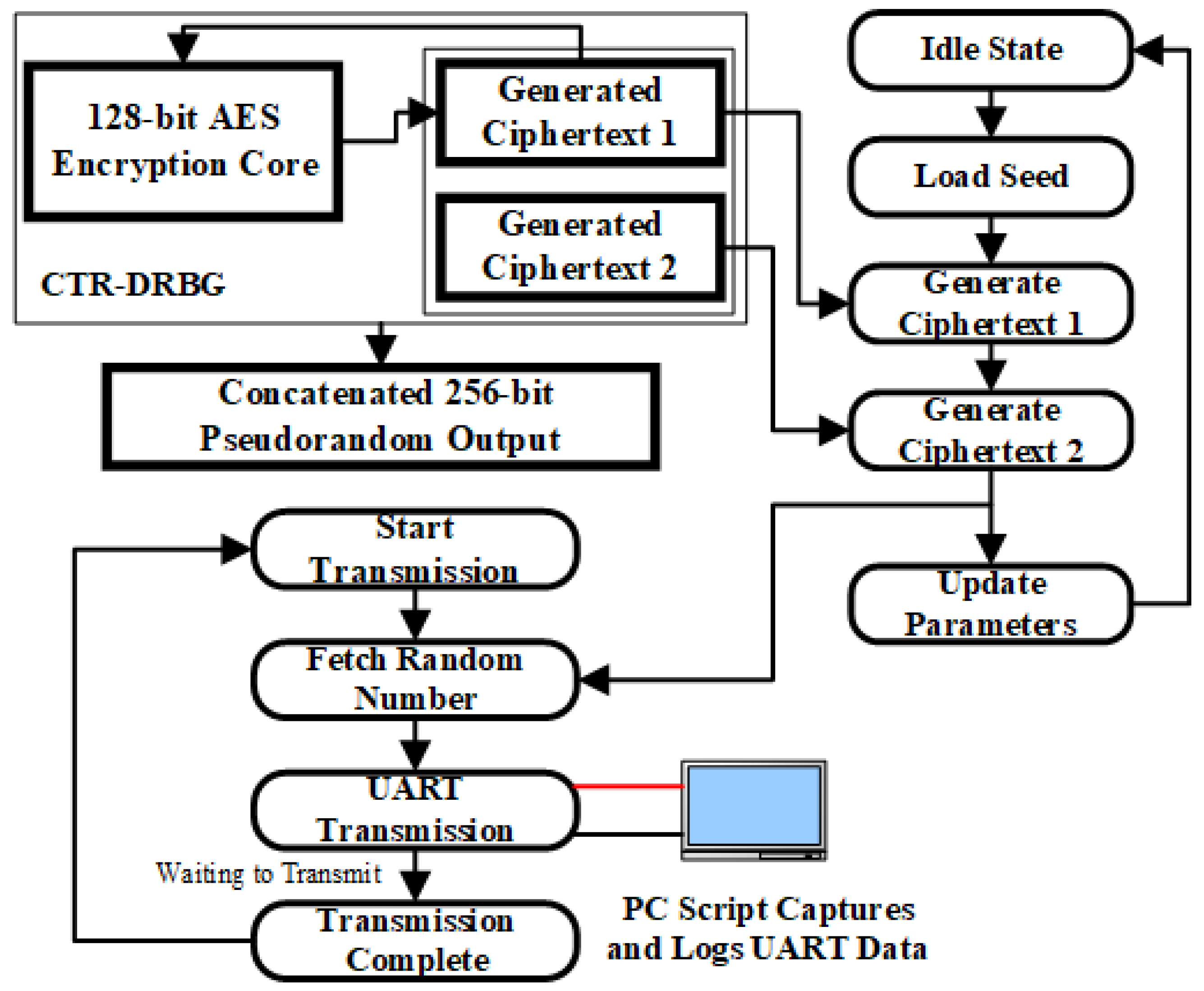
As illustrated in
Figure 6, a universal asynchronous receiver/transmitter (UART) communication module is integrated into the system to monitor the output of the CTR-DRBG during the experiments. This module transmits the 256-bit random number generated in each round to the PC in real time. The PC collects and stores the output sequences to facilitate offline analysis after each experimental session.
To ensure the accuracy of the fault injection results, it is essential to distinguish faults that affect the core CTR-DRBG module from those that impact only the data transmission process (i.e., UART), thereby avoiding misjudgments. For this purpose, multiple groups of output sequences were collected under fault-free conditions as reference data for subsequent comparison.
If a specific sequence generated during fault injection begins to show persistent deviation from the reference and all subsequent outputs consistently differ, it can be concluded that the fault has affected the internal logic of the CTR-DRBG. This determination is based on the feedback structure adopted in the CTR-DRBG design, where the current output participates in the next round of encryption. As a result, once an error occurs, its impact propagates continuously.
In contrast, if an output mismatch is followed by a return to alignment with the reference sequence, the deviation is attributed to transient disturbances during UART transmission. Such cases are excluded from the statistics of effective fault injections into the CTR-DRBG.
4. Software-Level Fault Injection During the Compilation Phase
To systematically evaluate the resilience of the CTR-DRBG against logical disturbances at the software level, this section proposes an embedded RTL-based fault injection method using bit-flip models. By introducing internal perturbations into the AES encryption core and applying randomized triggering combined with reference sequence comparisons, the robustness and fault propagation behavior of the system are assessed. The method provides effective support for hardware security evaluation through multilocation and multiround fine-grained simulation experiments.
4.1. Fault Model Construction Method
Bit-flip fault injection is a commonly used approach to emulate hardware anomalies. Its fundamental principle involves flipping specific bits—typically via XOR operations—in critical registers or intermediate variables at designated moments during system execution, thereby simulating logic errors caused by hardware disturbances such as electromagnetic interference, radiation, or voltage spikes. In this work, fault injection logic is embedded at the RTL level into the designed CTR-DRBG module to simulate bit-flip faults and observe the output variations within a co-simulation environment. This approach offers high repeatability, fine-grained interference control, and precise fault localization, making it a powerful technique for the analysis of fault propagation paths and identification of sensitive modules. Single-bit-flip injection is adopted in this study. Two distinct fault injection strategies targeting the AES encryption core—one of the most critical components of the CTR-DRBG system—are designed and implemented to investigate the impacts of different fault locations on the output random numbers.
4.2. RTL Fault Embedding and Testing Process
Targeting the AES-128 encryption core within the CTR-DRBG module, a lightweight RTL fault injection mechanism is embedded into the register logic without altering the original data paths or timing constraints [
31]. Specifically, a 32-bit fault counter is introduced, which increments over time and works in conjunction with SystemVerilog’s urandom_range to randomly determine the fault injection time during each simulation run.
Furthermore, XOR operations are inserted before the write paths of plaintext registers, key registers, and round key registers. The bit positions to be flipped are dynamically selected using urandom, with the current implementation flipping one randomly chosen bit out of 128. To verify the effectiveness, six sets of different initial seeds are used, and random number sequences are outputted under both fault-enabled and fault-disabled conditions for comparison. If the output begins to deviate from the reference sequence starting from the fault-triggered round and continues to diverge, the RTL random fault is considered to have successfully disrupted the core encryption logic. This “controlled randomness with result equivalence” strategy allows the simulated bit-flip faults to replicate the functional impact of real-world disturbances such as electromagnetic interference and voltage fluctuations. It also enables high-precision, repeatable validation for subsequent fault path tracing and hardware security assessment.
5. Experimental Evaluation and Analysis
This work evaluates the robustness and stability of the CTR-DRBG under fault injection from two perspectives. First, it investigates the system’s output stability under various physical environmental disturbances, including both single and combined fault sources. Second, it analyzes the system’s internal sensitivity to microlevel perturbations through RTL bit-flip simulations. The combined results offer a comprehensive view of the CTR-DRBG’s behavioral characteristics and security boundaries in multifault injection scenarios.
5.1. Analysis of Physical Environment Fault Injection Results
5.1.1. Single-Dimensional Fault Injection Experiments
In the electromagnetic fault injection experiments, the testbench was configured to inject five EM pulses after system startup and stabilization. As shown in
Figure 7, only when the electromagnetic intensity was set to 3.3 V/m did the random number output deviate from the expected sequence. This deviation began from the 1253rd 256-bit output, indicating that the CTR-DRBG logic was successfully affected by the EM disturbance.
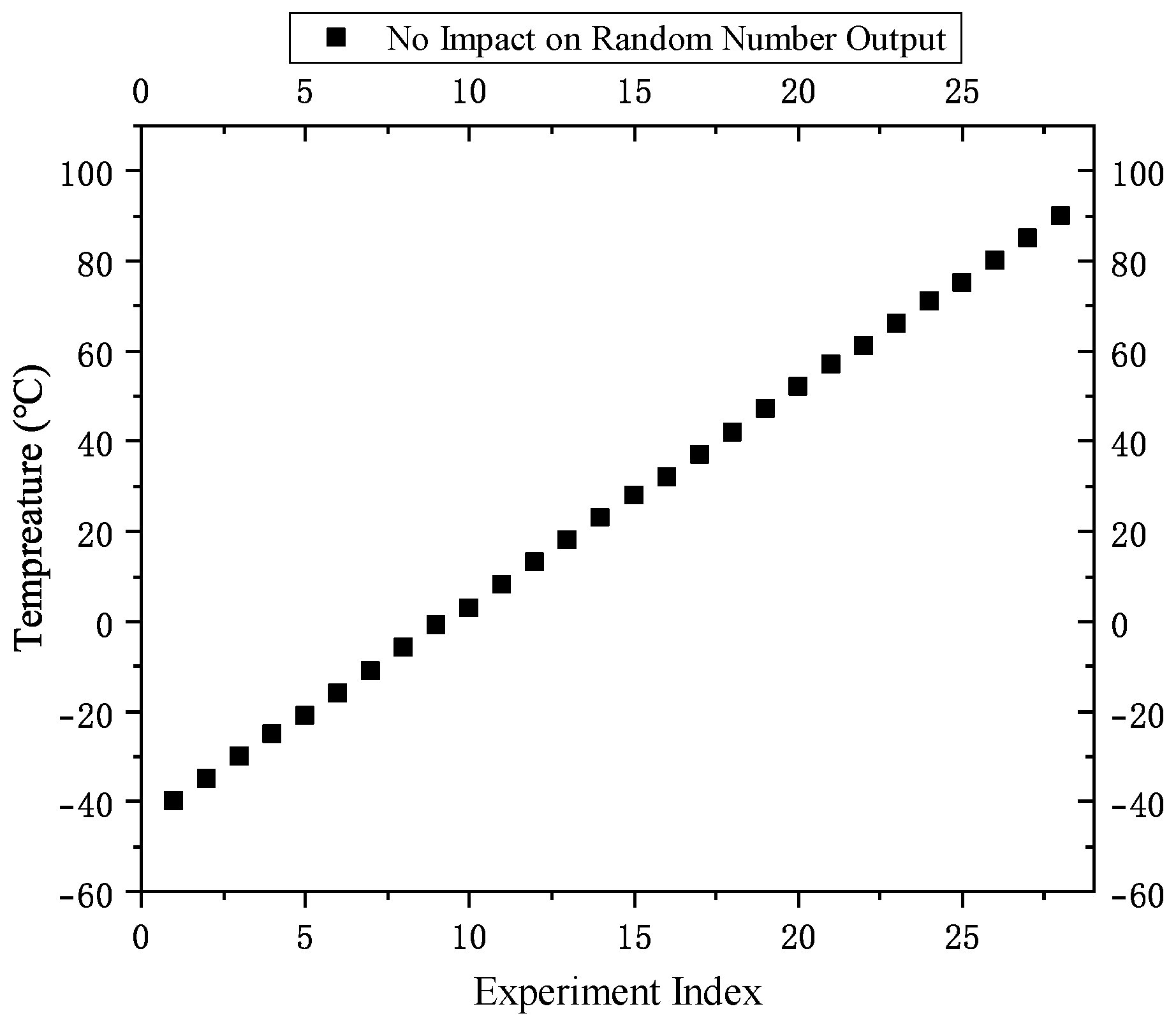
In the temperature disturbance experiments, the temperature range was set to cover typical and extreme fluctuations that the chip might experience during operation. During the experiments, the integrity and consistency of the random number outputs were continuously monitored under various thermal conditions. As illustrated in
Figure 8, no anomalies or deviations were observed throughout the temperature range, suggesting that, under the current test conditions, temperature changes within the controlled range had no substantial impact on the output.
In the voltage glitch injection experiments, three glitches were applied. As shown in
Figure 9, successful random number deviations occurred when the glitch voltages were set to
V and 4.49 V. Specifically, deviations began from the 1253rd and 1267th 256-bit outputs, respectively. This confirms that voltage glitches can, under certain conditions, interfere with the internal logic or register states of the CTR-DRBG and affect the output.
5.1.2. Multidimensional Fault Injection Experiments
Based on three fault sources—temperature, electromagnetic, and voltage glitch—multidimensional joint fault injection experiments were designed and executed. Each case was repeated multiple times to ensure consistency. The results are summarized in
Table 2. In 2D combinations, EM–Temp, EM–Voltage, and Voltage–Temp scenarios were tested.
The findings show that combined faults enhance system disruption. For instance, in the Voltage–Temp combination with a glitch of 4.19 V and temperature at 75 °C, the output started deviating persistently, indicating that joint disturbances can compromise randomness generation. The EM–Voltage combination exhibited stronger attack efficacy, producing more frequent and sustained output deviations than standalone EM or voltage injection. By contrast, the EM–Temp combination only caused a brief anomaly at 3.3 V/m EM strength and 85 °C, showing limited interference under these conditions.
In 3D joint injection scenarios, the system faced simultaneous voltage glitches, EM pulses, and thermal disturbances. These cases showed significantly more instances of sustained output deviation compared to single-source injections. The findings suggest that multisource interference accumulates at key moments—like seed generation and encryption—forming “interference peaks” that break the internal feedback loop, resulting in long-term deviation and loss of determinism.
The combined effect of EM interference and voltage glitches was observed to induce stronger and more persistent deviations compared to other combinations. At the hardware level, this behavior can be explained by their complementary disruption mechanisms. EM interference perturbs the signal integrity of interconnects and combinational paths, while voltage glitches reduce noise margins and delay slack across sequential elements. When both faults occur concurrently, the likelihood of violating the setup and hold constraints in critical registers, such as those storing the AES round keys and the counter state, increases significantly.
In the context of the CTR-DRBG, the corruption of these registers directly impacts the round-key generation and counter increment operations that govern the state update. Once these operations are altered, the deterministic feedback structure of the generator propagates the error, leading to persistent deviations in the output sequence. This mechanism explains why combined EM–voltage injection produces a stronger and more sustained effect than EM–temperature or voltage–temperature combinations. The physical results are consistent with RTL bit-flip simulations, which demonstrate that faults in these key registers trigger long-lasting divergences, confirming the causal relationship between hardware-level timing violations and algorithmic state corruption.
In practice, the absolute number of successful persistent deviations observed in our experiments was small relative to the total number of injection attempts. This limitation prevents the derivation of statistically meaningful confidence intervals or stable intensity–width–phase dependency maps. Such low success rates are consistent with prior reports in the literature, where only a small fraction of injections activated critical faults. Nevertheless, the presence of even a modest number of persistent deviations is sufficient to demonstrate the vulnerability of the CTR-DRBG to environmental disturbances. Future work will expand the number of trials and incorporate synchronized intensity–width–phase sweeps to enable sensitivity mapping and more robust statistical characterization.
5.2. Analysis of Software-Level Bit-Flip Fault Injection
To overcome limitations in the precision and repeatability of physical fault experiments, this study further constructs RTL fault injection models simulating bit-level disturbances to systematically analyze the CTR-DRBG’s internal logic sensitivity and fault propagation behavior.
The Verilog-based CTR-DRBG module introduced control logic in AES core registers, applying single-bit flips to specific bits (e.g., bit 0). The timing was managed via a fault counter, and the fault trigger flag fault-injected ensured precise and repeatable injections. Fault targets included the AES plaintext input register, key register, and round key register—representing key intermediate states. This setup enabled the comprehensive observation of the system’s response to single-bit errors.
To evaluate the impact of bit-flip faults on output behavior, six seeds (Seed1–Seed6) were used. Seed1 and Seed2 served as control groups with no fault injection. The rest enabled RTL injection logic. Several rounds of 256-bit outputs were generated per seed and compared bit-by-bit against their fault-free references.
In physical fault injection experiments, the precise fault location within the CTR-DRBG cannot be directly observed because the applied electromagnetic or voltage perturbations affect a broad set of circuit paths. Instead, the persistent deviation of the output sequence serves as a behavioral indicator of internal state corruption. To improve the interpretability, the results were complemented by RTL bit-flip simulations, where specific registers—namely the AES round-key storage and the counter registers—were selectively disturbed. These simulations consistently reproduced the persistent output divergence observed in physical tests.
The convergence of these two perspectives supports the conclusion that the observed deviations in physical experiments are most plausibly attributed to disturbances in these critical registers. In the CTR-DRBG architecture, both the round-key generation and counter update processes are timing-critical operations whose corruption irreversibly alters the feedback state. Once disturbed, the generator can no longer resynchronize with its original deterministic trajectory, resulting in sustained output divergence. By explicitly aligning the experimental outcomes with the simulated register-level disturbances, the analysis establishes a clear and transparent relationship between the conclusion on register sensitivity and the presented data.
As shown in
Table 3, the Seed1 and Seed2 outputs remained consistent, verifying the system stability in the absence of faults. For Seed3–Seed6, sustained output deviations occurred starting from specific rounds, confirming that the injected bit-flip faults in the AES path and state feedback loop had a cumulative impact.
This behavior illustrates the high sensitivity of the CTR-DRBG feedback mechanism to state perturbation. Once a critical register or variable is corrupted, the output cannot self-correct, degrading the determinism and entropy quality.
In conclusion, the RTL simulation validates its ability to accurately emulate real-world physical fault characteristics. Compared to physical injections, software simulation provides higher control granularity and precision, enabling clearer visibility regarding fault propagation.
Furthermore, the results highlight precise fault-sensitive areas and propagation paths. Faults injected into AES-related registers caused immediate and irreversible output deviations—mirroring the sustained “random drift” observed in physical tests—proving the consistency and cross-verifiability between physical and logical injection models.
5.3. Discussion and Cross-Layer Interpretation
The experimental results collectively demonstrate that persistent output deviation constitutes a robust behavioral indicator of internal faults in the CTR-DRBG. In physical fault injection experiments, the precise spatial location of the disturbance cannot be directly observed due to the limited controllability of the external perturbation. Instead, the sustained divergence of the output sequence from its reference is employed as a proxy, reflecting the permanent corruption of internal states. This phenomenon is consistent with the feedback mechanism of the CTR-DRBG, where each output directly participates in the next encryption round. Once an internal register is disturbed, the effect propagates irreversibly, preventing the system from resynchronizing with its original deterministic trajectory.
The RTL bit-flip simulations provide a complementary perspective with higher controllability and repeatability. By directly targeting AES-related registers, the simulations reproduce persistent deviations analogous to those observed in physical experiments. This correspondence, denoted as the “PRNG Bias Point”, establishes a behavioral mapping between uncontrolled physical disturbances and controlled logical perturbations. The finding confirms that both physical and software-level faults, when acting on critical state variables, converge to the same failure mode—loss of output determinism and randomness. Importantly, this mapping allows software-based injections to serve as a diagnostic tool, enabling the precise identification of fault-sensitive regions that cannot be localized through physical experiments alone.
Several limitations must be acknowledged. The number of successful physical fault injections remains small, restricting the statistical power of the conclusions. In addition, the absence of gate-level timing characterization prevents the analysis of temporal fault propagation, and the current platform does not incorporate hardware redundancy mechanisms that may mask or mitigate disturbances. These limitations indicate future research directions: (i) expanding the number of fault injection trials to improve the statistical reliability, (ii) introducing timing-aware models such as static timing analysis (STA) to capture temporal effects, and (iii) integrating redundancy and error detection schemes to evaluate their efficacy in containing persistent deviations.
Taken together, the cross-layer methodology strengthens the causal interpretation of the observed phenomena. Physical fault injections reveal the vulnerability of the CTR-DRBG under realistic disturbance conditions, while RTL simulations reproduce and extend these observations with finer granularity. Their combination not only validates the consistency of fault manifestations across layers but also provides a coherent framework for robustness evaluation under multidimensional fault injection scenarios.
6. Conclusions
For RNGs, stability under physical disturbances is critical to their deployment in security-sensitive systems. However, most existing studies focus on isolated fault mechanisms and lack comprehensive frameworks that capture multisource disturbances or quantify their effects on pseudorandom behavior. To address these limitations, this work constructed a multidimensional fault injection platform targeting the AES-128-based CTR-DRBG, integrating voltage glitches, electromagnetic interference, and temperature variations. A hardware–software co-simulation methodology, combining physical injection and RTL bit-flip modeling, enabled an in-depth analysis of the output divergence, feedback chain stability, and fault propagation characteristics.
In addition, while persistent deviation has proven to be a reliable behavioral indicator of internal faults, the current design lacks on-chip redundancy features to conclusively isolate faults from potential transport-layer artifacts. As future work, the platform will be enhanced with internal redundancy mechanisms, such as lightweight CRC checkers and sampled intermediate states, to validate internal computations in real time. These additions will improve the fidelity of fault localization, ensure that persistent deviations are strictly attributed to the CTR-DRBG core, and further strengthen the robustness of cross-layer fault analysis.
Furthermore, while the current results confirm that the CTR-DRBG is sensitive to multidimensional disturbances, the experimental platform does not allow the precise spatial localization of injected faults. The electromagnetic probe lacks the resolution to target individual registers, and voltage or temperature injections act globally across the device. Combined with the compact hardware footprint of the CTR-DRBG, these factors prevent the construction of a fine-grained sensitivity map at this stage. As future work, the methodology will be extended with more localized fault injection techniques and timing-aware simulations at the gate level. This will enable the derivation of a sensitivity map that relates fault locations, divergence onset, and trigger windows to specific AES operations such as round-key generation and counter updates, thereby offering deeper insight into the mechanisms of fault propagation.
A structured, timing-preserving fault injection model was further introduced at the RTL level, offering the precise and repeatable perturbation of AES core registers. The experimental results revealed the high sensitivity of the CTR-DRBG to both external physical disturbances and internal bit-level faults, with sustained output deviations observed under composite fault scenarios. This platform establishes a reproducible basis for RNG security evaluation and can support future work in machine learning-based fault classification and the development of resilient RNG architectures suitable for automotive and industrial control systems.
Author Contributions
Conceptualization, J.C., J.Z. and R.Z.; Methodology, X.X. (Xianli Xie); Validation, J.Z., R.Z. and X.X. (Xianzhao Xia); Formal analysis, X.X. (Xianli Xie), J.C., J.Z. and X.X. (Xianzhao Xia); Investigation, J.C., J.Z., R.Z. and X.X. (Xianzhao Xia); Resources, X.X. (Xianli Xie) and X.X. (Xianzhao Xia); Data curation, J.C. and J.Z.; Writing—original draft, J.C. and J.Z.; Writing—review & editing, J.C.; Visualization, R.Z.; Supervision, X.X. (Xianli Xie); Project administration, X.X. (Xianli Xie), J.Z. and X.X. (Xianzhao Xia). All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded in part by the National Key R&D Program of China (Grant No. 2023YFB4403000) and the Open Fund of the State Key Laboratory of Intelligent Vehicle Safety Technology (Grant No. IVSTSKL-202408).
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
Authors Ruiqing Zhai and Xianzhao Xia were employed by the company CATARC Technology Co., Ltd. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Defense Technical Information Center: Fort Belvoir, VA, USA, 2001. [Google Scholar]
- Ning, B. Research on Fault Model and Countermeasure Effectiveness Evaluation of Clock Glitch Fault Injection Attack. Master’s Thesis, Tianjin University, Tianjin, China, 2022. [Google Scholar]
- Baksi, A.; Bhasin, S.; Breier, J.; Jap, D.; Saha, D. A Survey on Fault Attacks on Symmetric Key Cryptosystems. ACM Comput. Surv. 2022, 55, 86. [Google Scholar] [CrossRef]
- Zhu, X. Research of Fault Injection Technology on Integrated Circuits by Laser. Ph.D. Thesis, School of Astronomy and Space Science, University of Chinese Academy of Sciences, Beijing, China, 2021. [Google Scholar]
- Breier, J.; Hou, X. How Practical Are Fault Injection Attacks, Really? IEEE Access 2022, 10, 113122–113130. [Google Scholar] [CrossRef]
- Shepherd, C.; Markantonakis, K.; Van Heijningen, N.; Aboulkassimi, D.; Gaine, C.; Heckmann, T.; Naccache, D. Physical fault injection and side-channel attacks on mobile devices: A comprehensive analysis. Comput. Secur. 2021, 111, 102471. [Google Scholar] [CrossRef]
- Chu, W.; Ou, Q.; Fu, W.; Wu, T. Overview of Electromagnetic Fault Injection Attacks. Commun. Technol. 2021, 54, 2589–2594. [Google Scholar]
- Wei, X.; Li, X.; Dai, Y. Construction method of reliability prediction model for GPGPU programs based on limited fault injection samples. J. Jilin Univ. (Eng. Technol. Ed.) 2025, Online First, 1–10. [Google Scholar] [CrossRef]
- Liao, J. Research on SEE Fault Injection Method Based on Mixed-simulation. Ph.D. Thesis, Xidian University, Xi’an, China, 2025. [Google Scholar]
- Li, Y.; Zhu, X.; Jiang, H.-L. Fault Model Analysis of SRAM Single Event Upset Induced by Pulsed Laser. J. Cryptologic Res. 2021, 8, 1074–1081. [Google Scholar] [CrossRef]
- Wang, T. Research on Single Event Effects Simulation Fault Injection Methods for SRAM-based. Master’s Thesis, Southwest University of Science and Technology, Mianyang, China, 2025. [Google Scholar]
- Liu, Q.; Tang, H. Study on Effect of ElectroMagnetic Fault Injection Attack on Dynamic Random Access Memory. J. Electron. Inf. Technol. 2021, 43, 2449–2457. [Google Scholar]
- Cheng, Y.; Zhuang, Y.; Cao, Z.-n. Fault Injection for Single Event Upset Simulation Based on Random Forest. J. Chin. Comput. Syst. 2021, 42, 2452–2458. [Google Scholar]
- Wang, X.; Hu, W.; Tan, J. Correlation fault attack on AES. J. Xidian Univ. 2021, 48, 192–199, 208. [Google Scholar]
- Chen, X.; Shi, Y.; Bai, Y. FPGA emulation technology for single event upset. Electron. Packag. 2021, 21, 70–76. [Google Scholar]
- El Amraoui, S.; Douadi, A.; Leveugle, R.; Maistri, P. On the Harmonic Locking of Ring Oscillators under Single ElectroMagnetic Pulsed Fault Injection in FPGAs. J. Electron. Test. 2025, 41, 257–272. [Google Scholar] [CrossRef]
- Wu, J. Research on SRAM-based FPGA Single Event Upset Fault Injection Method. Master’s Thesis, China University of Petroleum (Beijing), Beijing, China, 2023. [Google Scholar]
- Zhao, M. Research of SRAM-based FPGASingle Event Effect Fault Injection System. Master’s Thesis, Hefei University of Technology, Hefei, China, 2021. [Google Scholar]
- Gao, Y.; Zhang, Q.; Ma, H.; He, J.; Zhao, Y. EO-Shield: A Multi-Function Protection Scheme against Side Channel and Focused Ion Beam Attacks. In Proceedings of the 28th Asia and South Pacific Design Automation Conference, ASPDAC ’23, Tokyo, Japan, 16–19 January 2023; pp. 670–675. [Google Scholar]
- Ma, H.; Zhang, Q.; Gao, Y.; He, J.; Zhao, Y.; Jin, Y. PathFinder: Side channel protection through automatic leaky paths identification and obfuscation. In Proceedings of the 59th ACM/IEEE Design Automation Conference, DAC ’22, San Francisco, CA, USA, 10–14 July 2022; pp. 79–84. [Google Scholar]
- He, J.; Ma, H.; Guo, X.; Zhao, Y.; Jin, Y. Design for EM Side-Channel Security through Quantitative Assessment of RTL Implementations. In Proceedings of the 2020 25th Asia and South Pacific Design Automation Conference (ASP-DAC), Beijing, China, 13–16 January 2020; pp. 62–67. [Google Scholar]
- Ma, H.; He, J.; Liu, Y.; Zhao, Y.; Jin, Y. CAD4EM-P: Security-Driven Placement Tools for Electromagnetic Side Channel Protection. In Proceedings of the 2019 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Xi’an, China, 16–17 December 2019; pp. 1–6. [Google Scholar]
- NIST SP 800-90A; Recommendation for Random Number Generation Using Deterministic Random Bit Generators (Revised), NIST Special Publication 800-90A, Revision 1. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015.
- NIST SP 800-22; A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications, NIST Special Publication 800-22, Revision 1a. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010.
- Liu, X. Research on Simulation of Strong Magnetic Pulse Fault Injection in Digital Integrated Circuits. Master’s Thesis, Xidian University, Xi’an, China, 2023. [Google Scholar]
- Elmohr, M.A.; Liao, H.; Gebotys, C.H. EM Fault Injection on ARM and RISC-V. In Proceedings of the 2020 21st International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 25–26 March 2020; pp. 206–212. [Google Scholar]
- Dumont, M.; Lisart, M.; Maurine, P. Modeling and Simulating Electromagnetic Fault Injection. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2021, 40, 680–693. [Google Scholar] [CrossRef]
- Lyakhov, S. Awgsome Fault Injection: In-Depth Analysis of Waveform Generation for Voltage Glitches. Master’s Thesis, Oregon State University, Corvallis, OR, USA, 2023. [Google Scholar]
- Fibich, C.; Horauer, M.; Obermaisser, R. Device- and Temperature Dependency of Systematic Fault Injection Results in Artix-7 and iCE40 FPGAs. In Proceedings of the 2021 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 1–5 February 2021; pp. 1600–1605. [Google Scholar]
- Mao, H.; Cheng, Y.; Hu, H. Multiple Persistent Faults Analysis with Unknown Faults. Netinfo Secur. 2023, 23, 41–49. [Google Scholar]
- Salih, N.K.; Satyanarayana, D.; Alkalbani, A.S.; Gopal, R. A Survey on Software/Hardware Fault Injection Tools and Techniques. In Proceedings of the 2022 IEEE Symposium on Industrial Electronics & Applications (ISIEA), Langkawi Island, Malaysia, 16–17 July 2022; pp. 1–7. [Google Scholar]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).