Cyberattack Detection and Classification of Power Converters in Islanded Microgrids Using Deep Learning Approaches
Abstract
1. Introduction
| Paper Reference | Detection Type | Accuracy (%) | Model Type |
|---|---|---|---|
| Koduru et al. [22] | Denial-of-Service (DoS) attack | 98.00 | Deep Neural Network (DNN) |
| Koduru et al. [22] | False Data Injection (FDI) attack | 90.00 | Deep Neural Network (DNN) |
| Hybrid ML Approach in DC Microgrids [23] | False Data Injection (FDI) attack | >96.5 | Long Short-Term Memory (LSTM) |
| Hybrid ML Approach in DC Microgrids [23] | False Data Injection (FDI) attack | >96.0 | Logistic Regression |
| Dehghani et al. [24] | FDI on control signals, communication networks | >97 | Wavelet transform + Deep auto-encoder |
| Ye et al. [25] | FDI into smart metering and central controller unit | 97.00 | Modified prediction interval-based LSTM |
| Hakim and Karegar [26] | FDI into substation measurements and sensors | 95.53 | Cross wavelet transform + SVM |
| Mohiuddin et al. [27] | FDI into output voltage and power measurements | 91.00 | Deep learning using rectified linear unit |
2. Islanded Microgrid
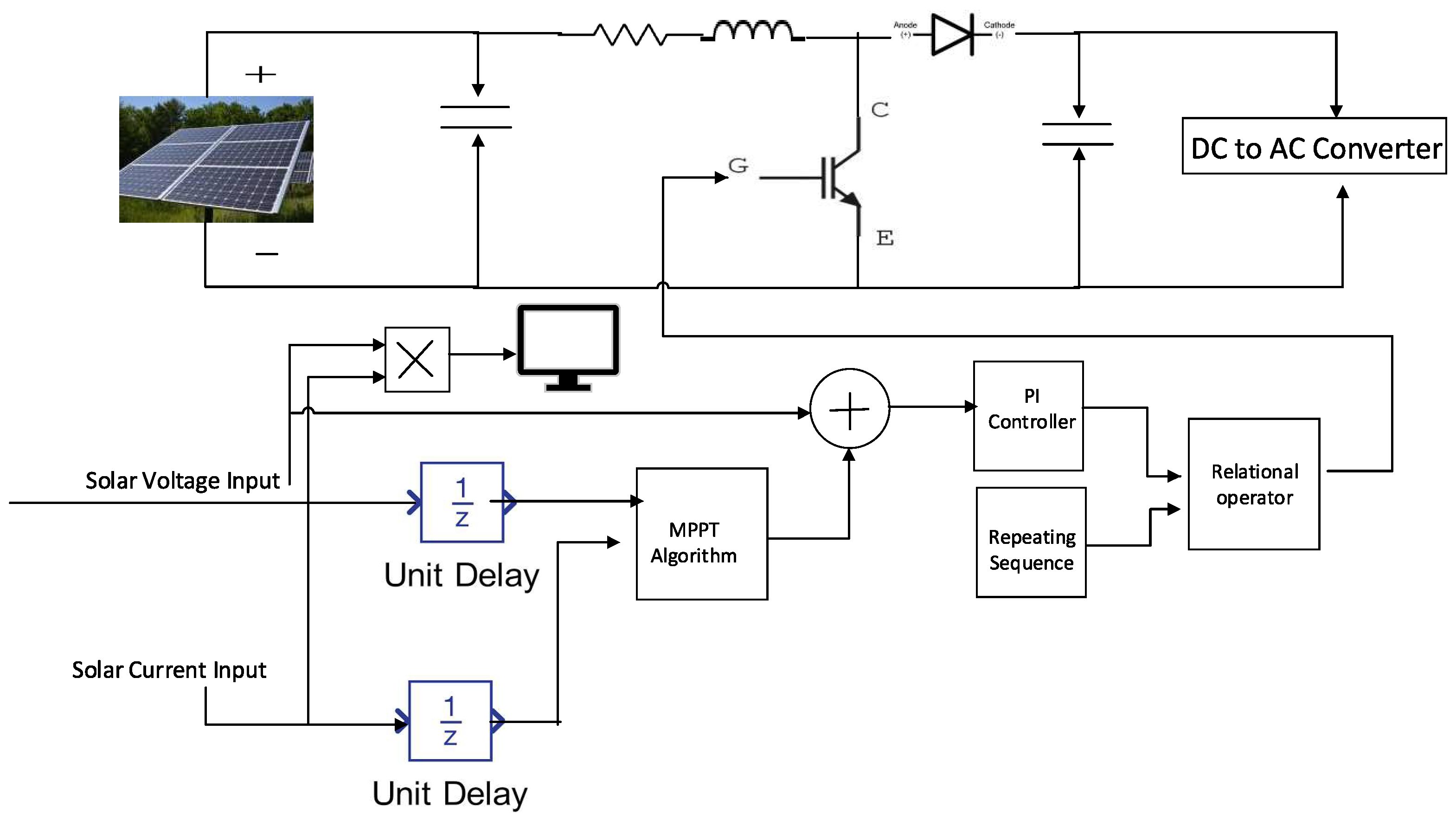
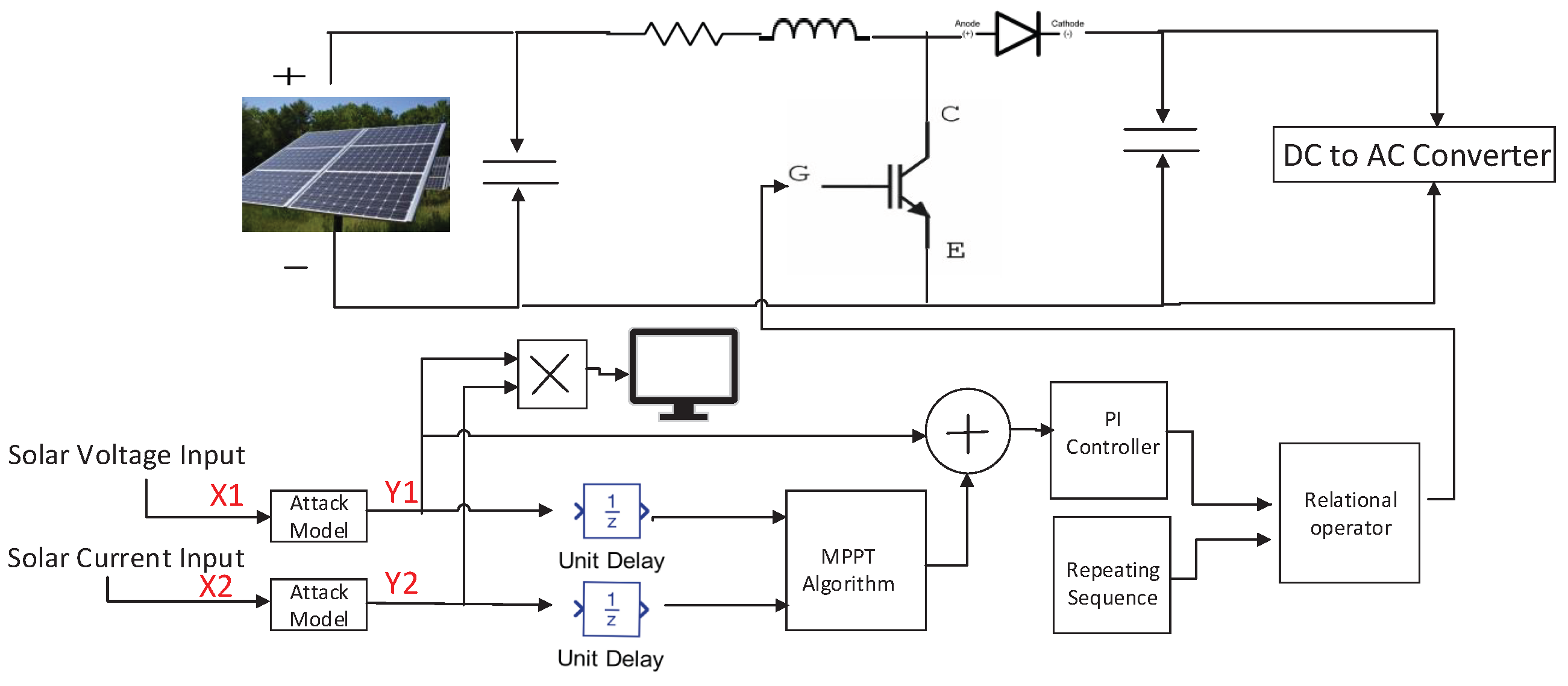
2.1. Solar PV with Solar Inverter
2.1.1. DC–DC Boost Converter and Inverter Control Equations
- Steady-State Output Voltage
- Load and Inductor Currents
- Inductor Current Ripple
- Output Voltage Ripple
2.1.2. DC–AC Converter System Parameters
- Inverter inductance L and resistance R (AC-side filter)
- DC-link voltage (from the boost converter)
- AC-side voltages and currents
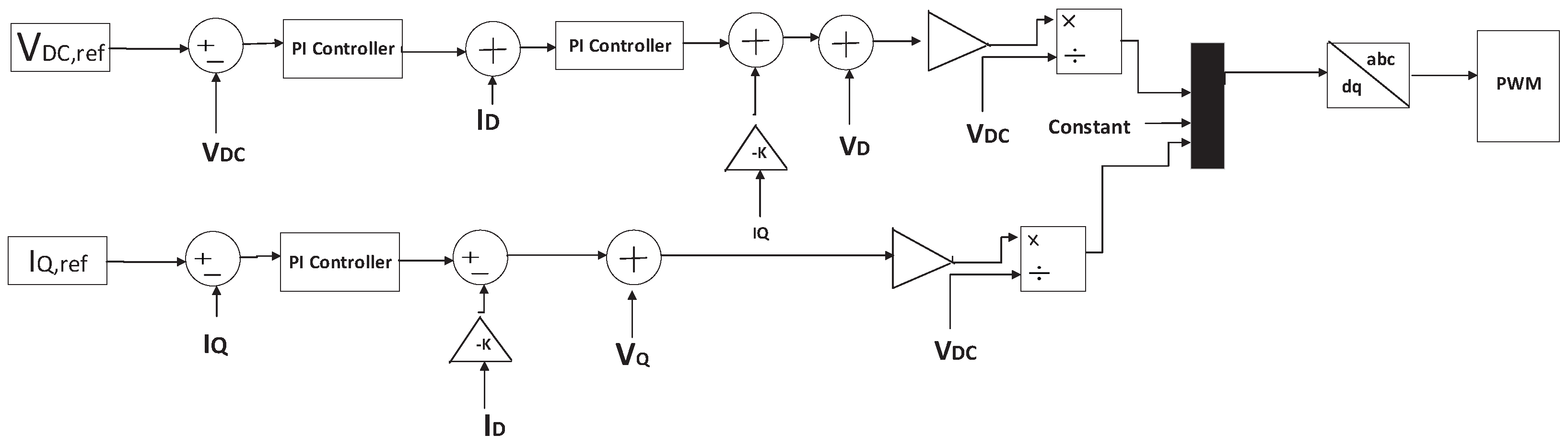
- Reference Currents
- Outer DC-Voltage PI Controller
- Current PI Controllers
- Voltage Commands with Decoupling
- PWM Generation
2.1.3. EMI Filter Design: − () Branch
- Series inductor : Acts as a line choke, blocking high-frequency harmonics.
- Shunt capacitor C: Diverts high-frequency components to ground.
- Parallel inductor : Forms a resonant LC tank with C, high impedance at fundamental frequency, enhancing filtering near resonance.
- Series Inductor Impedance
- Parallel LC Tank Impedance
- Total Input Impedance
- Component Selection
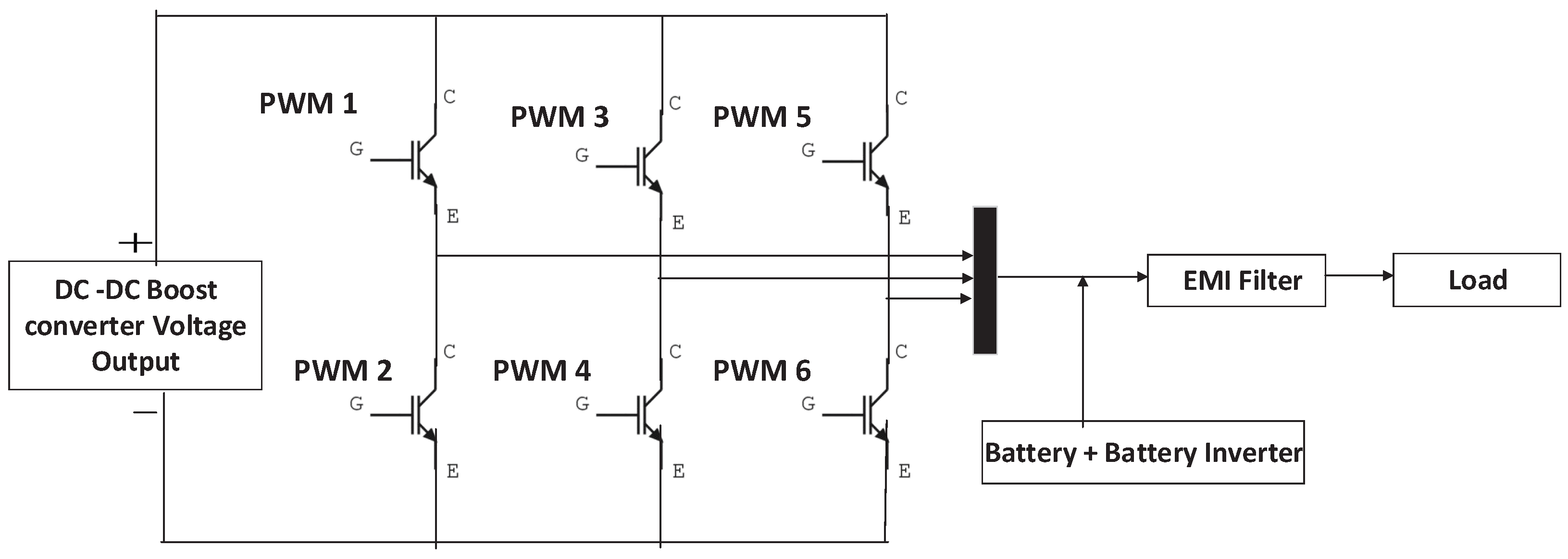
2.2. Battery Bank with Battery Inverter
3. Cyberattacks in Microgrid
3.1. Attacks on Data Integrity
- If , this attack manipulates the real measurement by
- If , this attack replaces the real measurement by
- If , there is no attack in the controller.
- FDI Case 1:
- FDI Case 2:
- FDI Case 3:
3.2. Attacks on Data Availability
3.3. Attacks on Data Confidentiality
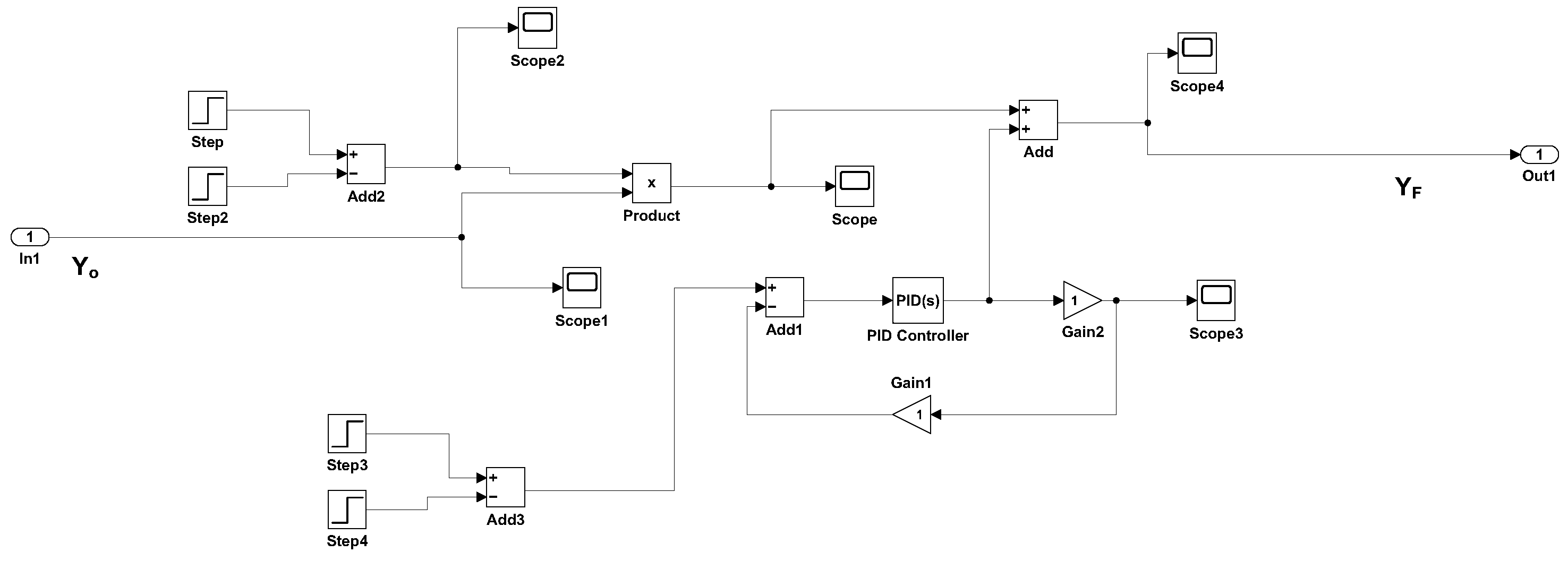
3.4. Cyberattack Model Design
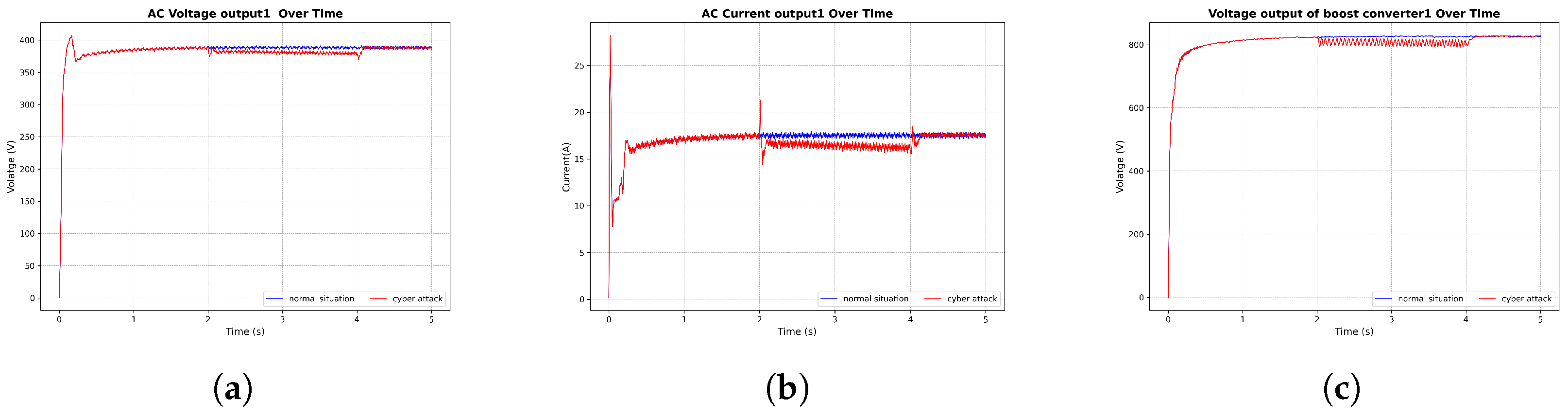
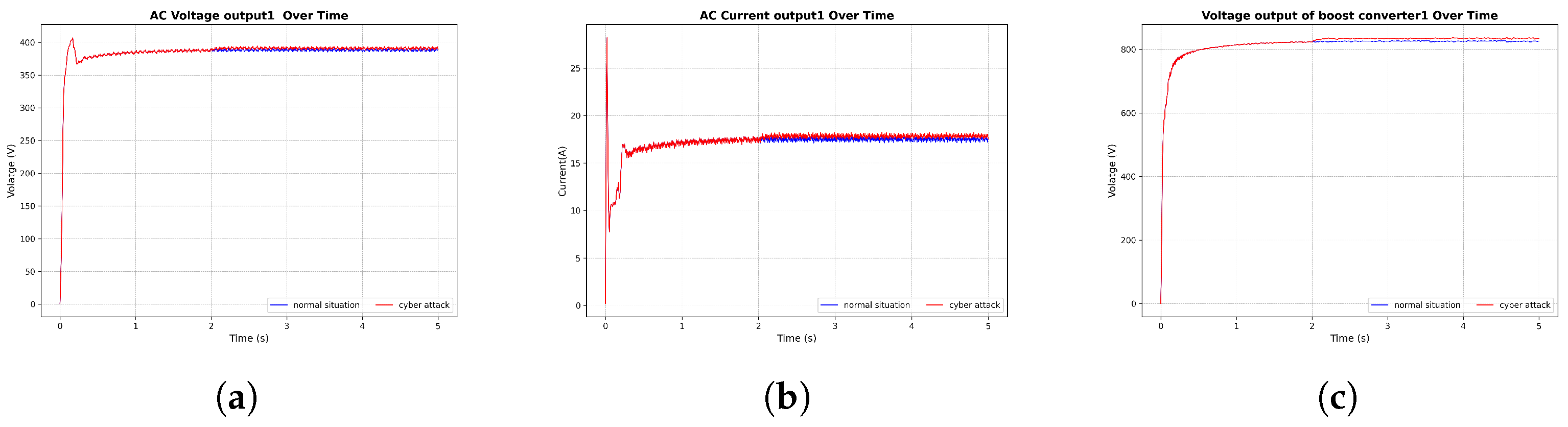
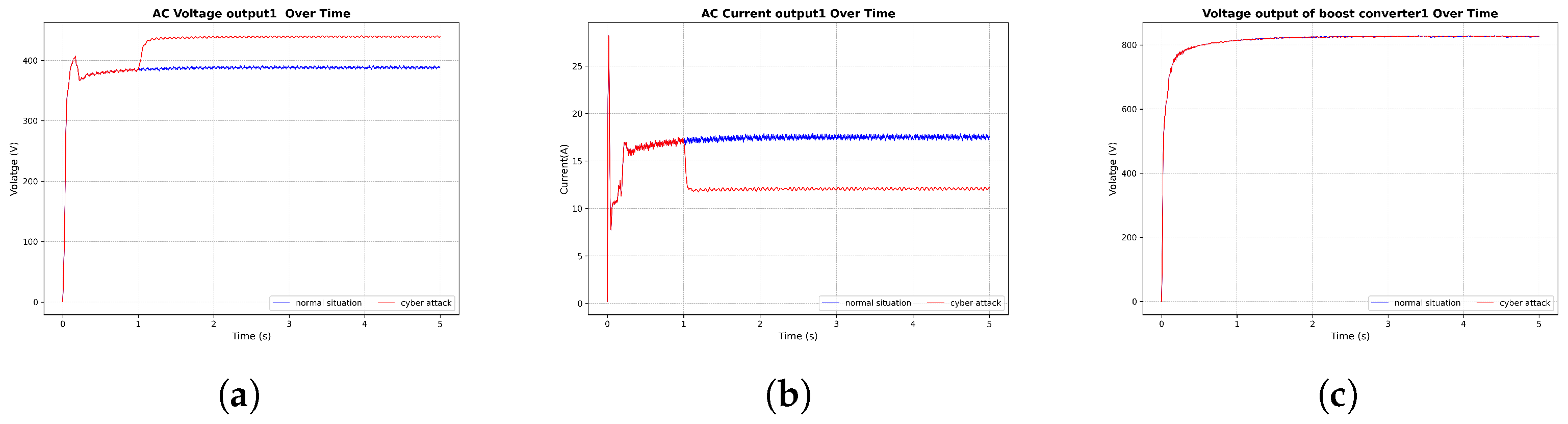
3.5. Cyberattack Results
4. Experiment and Evaluation
4.1. Data Pre-Processing
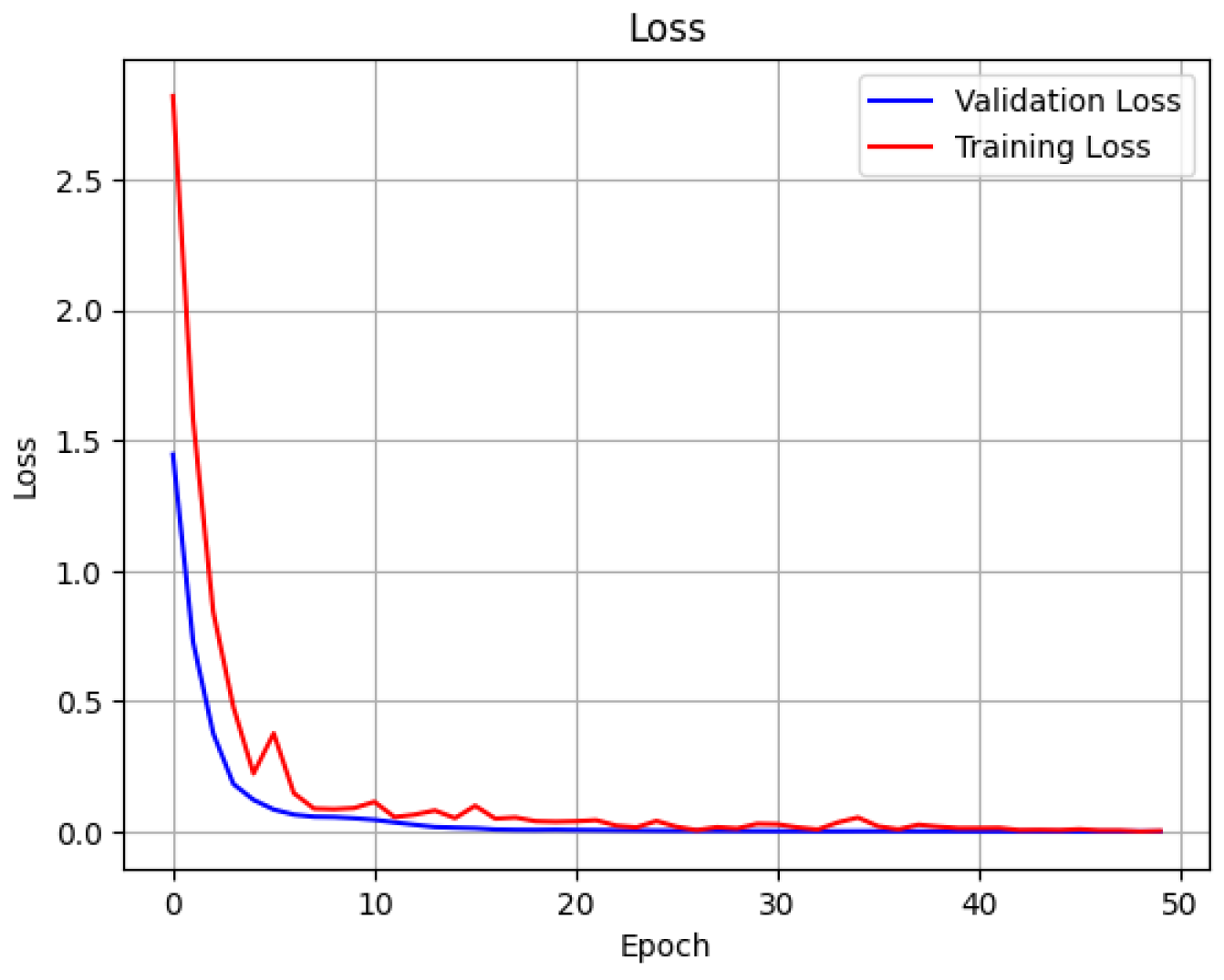
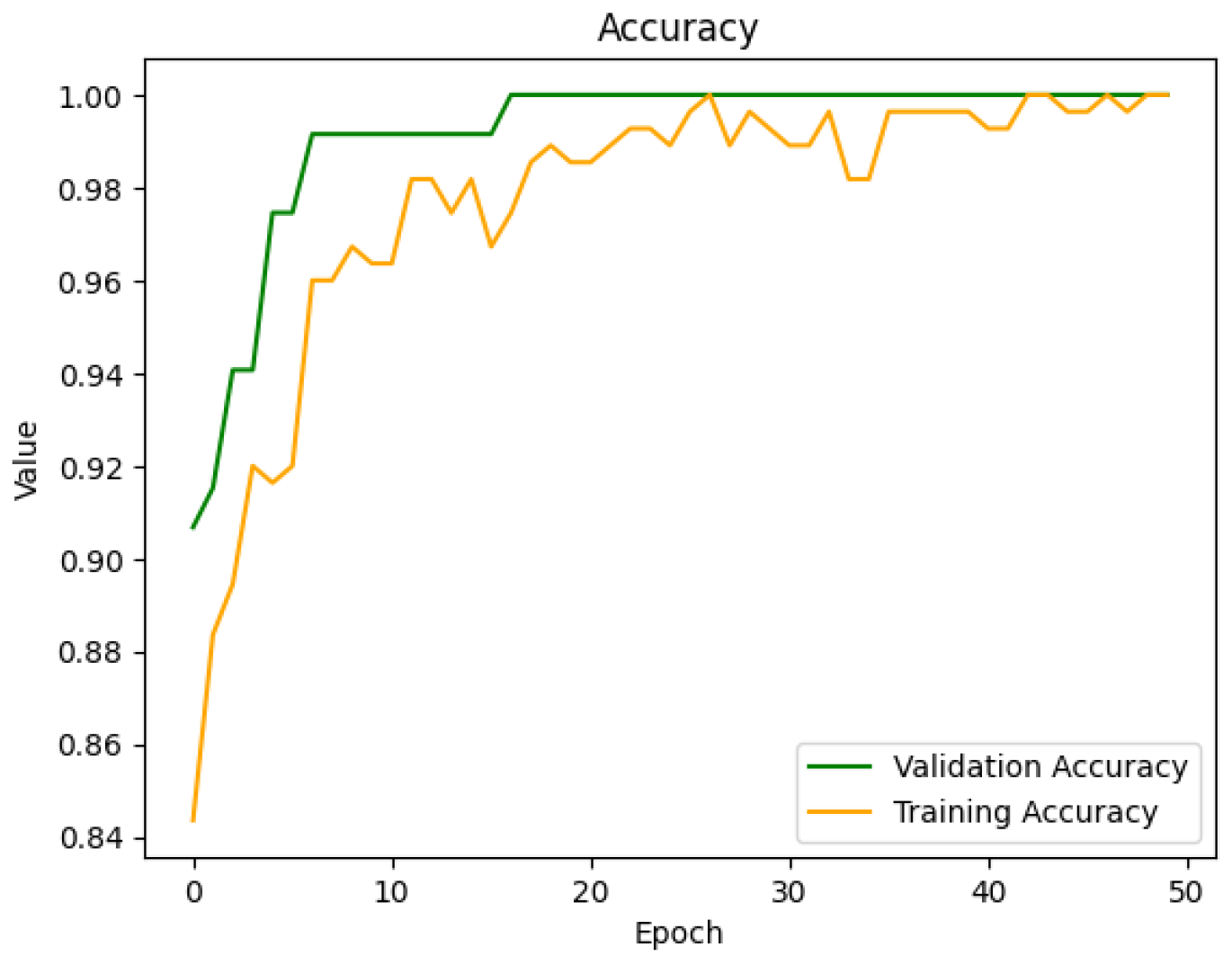
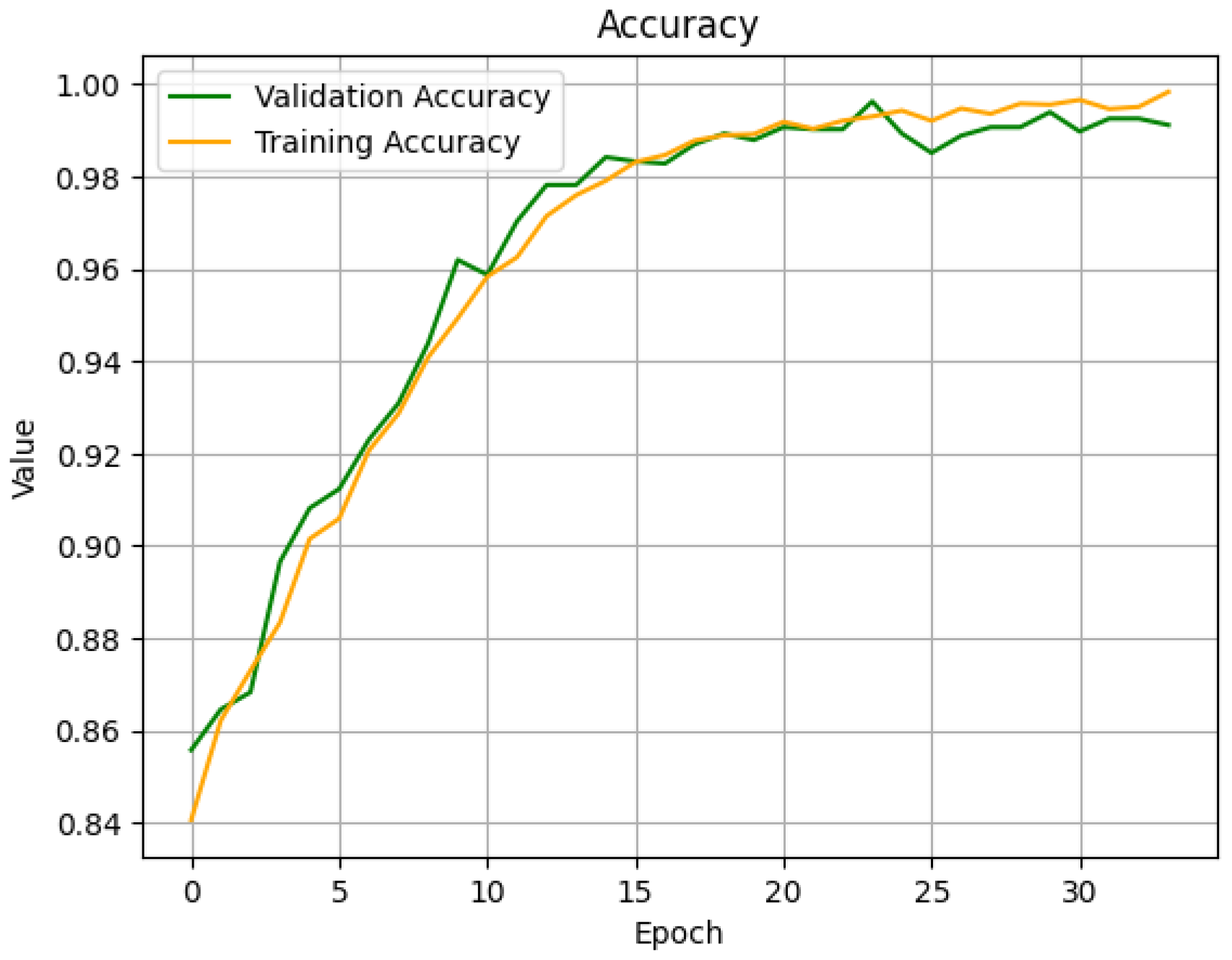
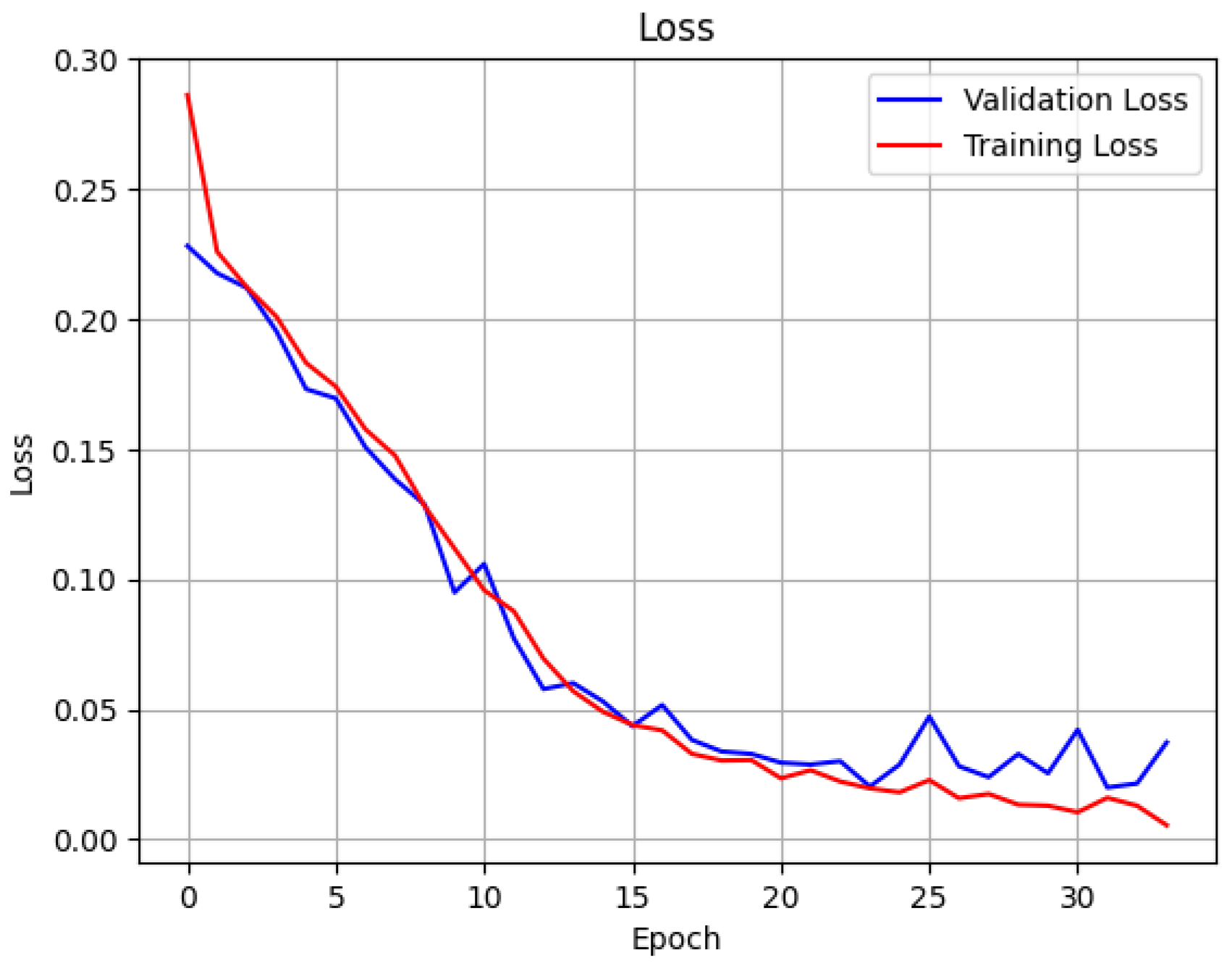
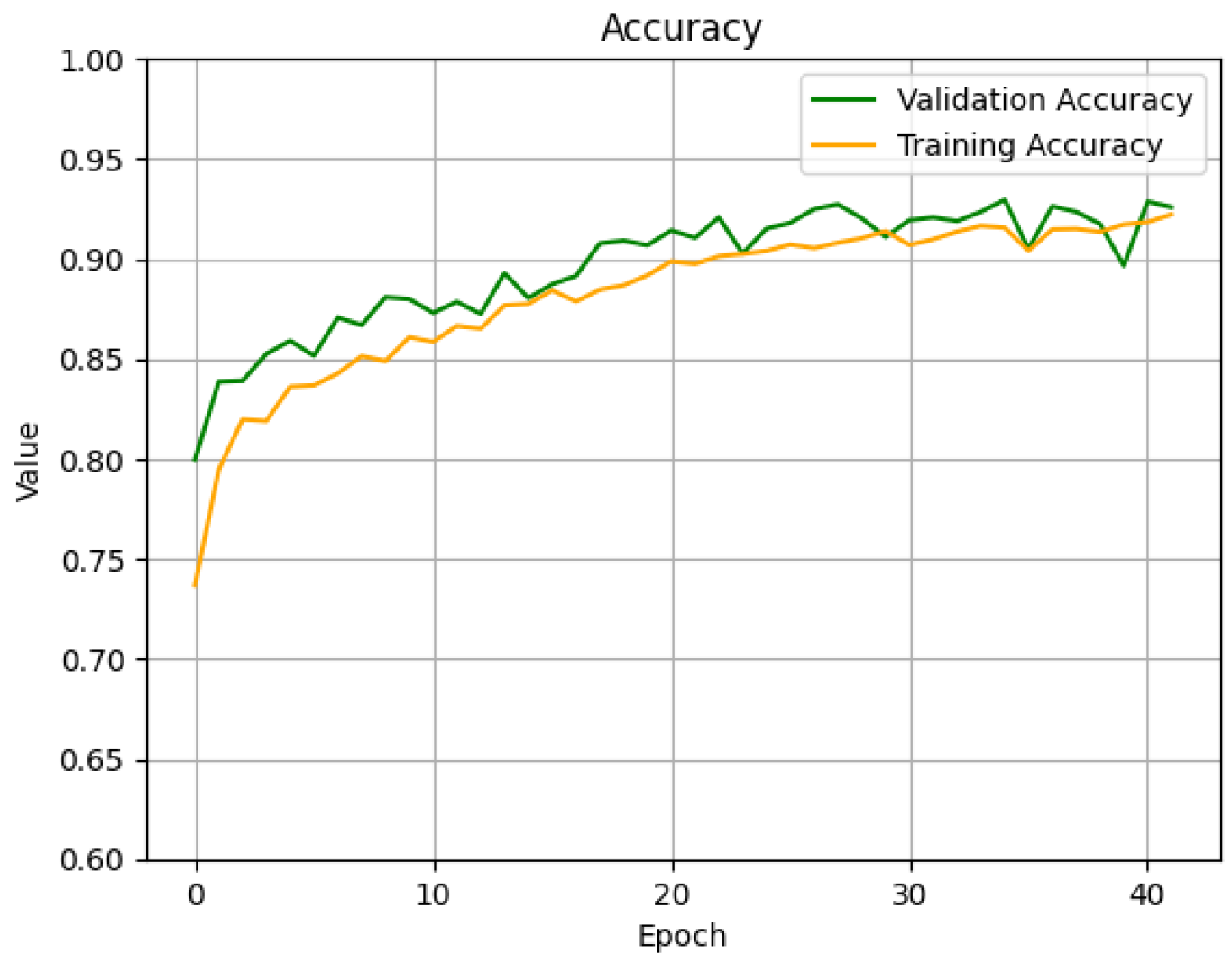
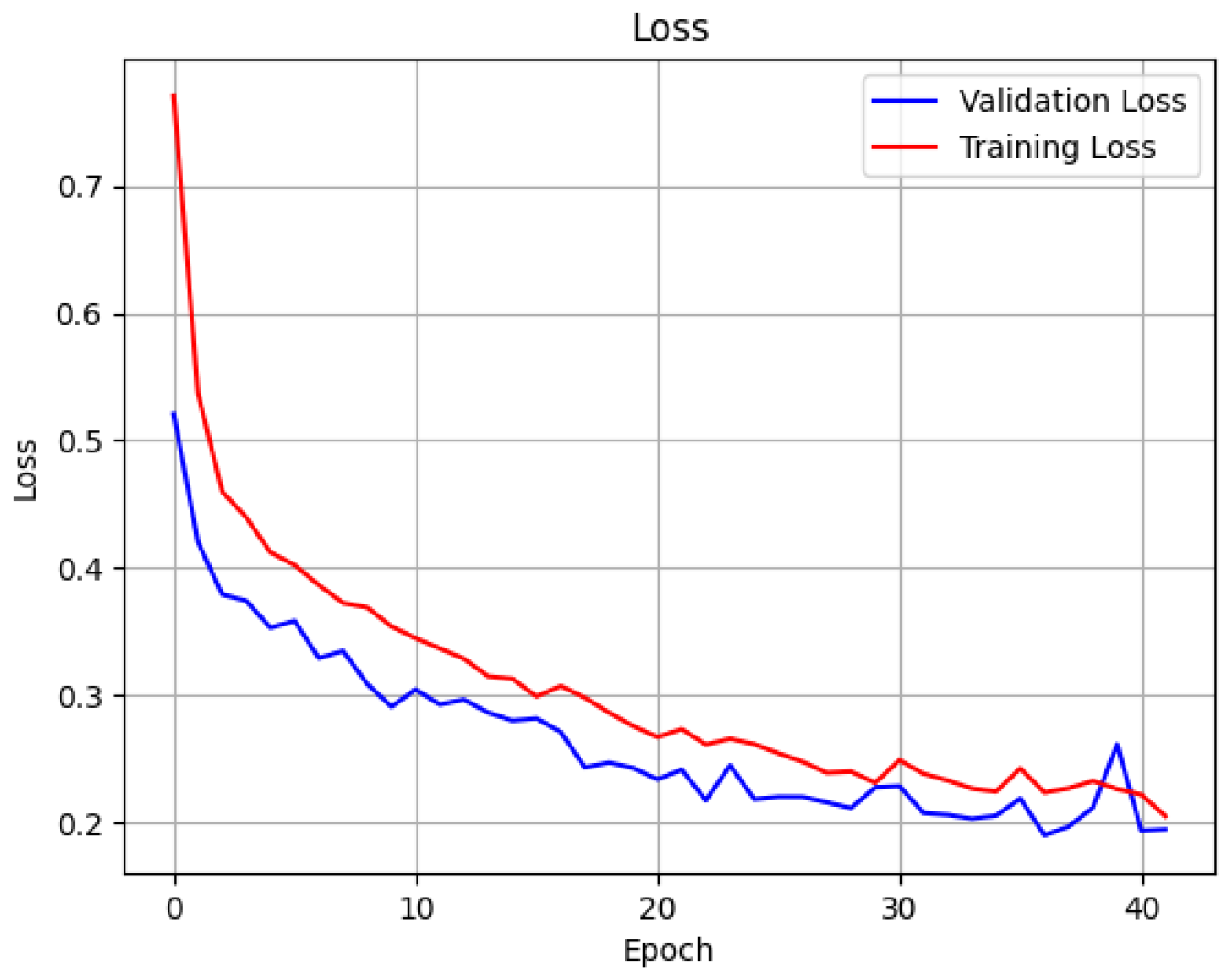
4.2. FNN Model for Detection
4.3. LSTM Model for Detection
4.4. FNN Model for Classification
4.5. LSTM Model for Classification
4.6. Final Combined Model
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AC | Alternating Current |
| ANN | Artificial Neural Networks |
| BMS | Battery Management System |
| DC | Direct Current |
| DNN | Deep Neural Networks |
| DoS | Denial of Service |
| EMI | Electromagnetic Interference |
| FDI | False Data Injection |
| FNN | Feedforward Neural Network |
| IoT | Internet of Things |
| LSTM | Long Short-Term Memory |
| MPPT | Maximum Power Point Tracking |
| SCADA | Supervisory Control and Data Acquisition |
| SOC | State of Charge |
| SVM | Support Vector Machines |
| UoM | University of Moratuwa |
| VSI | Voltage Source Inverter |
References
- Wang, Y.; Deng, C.; Liu, Y.; Wei, Z. A Cyber-Resilient Control Approach for Islanded Microgrids under Hybrid Attacks. Int. J. Electr. Power Energy Syst. 2023, 147, 108889. [Google Scholar] [CrossRef]
- Canaan, B.; Colicchio, B.; Abdeslam, D.O. Microgrid Cyber-Security: Review and Challenges toward Resilience. Appl. Sci. 2020, 10, 5649. [Google Scholar] [CrossRef]
- Zhang, J.; Ye, J.; Guo, L.; Li, F.; Song, W. Vulnerability Assessments for Power-Electronics-Based Smart Grids. In Proceedings of the 2020 IEEE Energy Conversion Congress and Exposition (ECCE), Detroit, MI, USA, 11–15 October 2020; pp. 1702–1707. [Google Scholar] [CrossRef]
- Mohee, A. Cyber War: The Hidden Side of the Russian-Ukrainian Crisis. SocArXiv 2022. [Google Scholar] [CrossRef]
- Stănculescu, M.; Deleanu, S.; Andrei, P.C.; Andrei, H. A Case Study of an Industrial Power Plant under Cyberattack: Simulation and Analysis. Energies 2021, 14, 2568. [Google Scholar] [CrossRef]
- Beg, O.A.; Khan, A.A.; Rehman, W.U.; Hassan, A. A Review of AI-Based Cyber-Attack Detection and Mitigation in Microgrids. Energies 2023, 16, 7644. [Google Scholar] [CrossRef]
- Wang, H.; Wei, Q.; Xie, Y. Research on Cascading Failures of Power Grid. In Advances in Technology and Engineering; IOS Press: Amsterdam, The Netherland, 2022. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.R.; Liang, H.; Ahrabi, R. Cyber-Security of Smart Microgrids: A Survey. Energies 2020, 14, 27. [Google Scholar] [CrossRef]
- Wang, B.; Sun, Q.; Wang, R.; Dong, C. Vulnerability Analysis of Secondary Control System When Microgrid Suffering from Sequential Denial-of-Service Attacks. IET Energy Syst. Integr. 2021, 4, 12026. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, M.; Song, K.; Li, T.; Zhang, N. An Optimal DoS Attack Strategy Disturbing the Distributed Economic Dispatch of Microgrid. J. Electr. Comput. Eng. 2021, 2021, 5539829. [Google Scholar] [CrossRef]
- Wang, B.; Sun, Q.; Han, R.R.; Ma, D. Consensus-Based Secondary Frequency Control under Denial-of-Service Attacks of Distributed Generations for Microgrids. J. Frankl. Inst. 2019, 358, 2343–2364. [Google Scholar] [CrossRef]
- Zhang, J.; Ye, J.; Guo, L. Model-Based Cyber-Attack Detection for Voltage Source Converters in Island Microgrids. In Proceedings of the IEEE Energy Conversion Congress and Exposition (ECCE), Vancouver, BC, Canada, 10–14 October 2021; pp. 1413–1418. [Google Scholar]
- Hussien, A. Classification of Cybersecurity Attacks Using Machine Learning: A Comparative Study of Random Forest, Logistic Regression, and Neural Networks. 2025. Available online: https://www.researchgate.net/publication/391234103_Classification_of_Cybersecurity_Attacks_Using_Machine_Learning_A_Comparative_Study_of_Random_Forest_Logistic_Regression_and_Neural_Networks (accessed on 1 March 2025).
- Avci, İ.; Koca, M. Cybersecurity Attack Detection Model, Using Machine Learning Techniques. Acta Polytech. Hung. 2023, 20, 29–44. [Google Scholar] [CrossRef]
- Doris, L.; Shad, R. Cyber Attack Prediction Using Machine Learning Algorithms. J. Cybersecur. 2024. Available online: https://www.researchgate.net/publication/385444981_CYBER_ATTACK_PREDICTION_USING_MACHINE_LEARNING_ALGORITHMS (accessed on 1 March 2025).
- Hajira, A.B.; Gokulraj, S. Cyber Attacks Classification Using Supervised Machine Learning Techniques. J. Sens. IoT Health Sci. 2025, 3, 57–67. [Google Scholar] [CrossRef]
- Anwar, A.; Mahmood, A.N.; Pickering, M. Modeling and Performance Evaluation of Stealthy False Data Injection Attacks on Smart Grid in the Presence of Corrupted Measurements. J. Comput. Syst. Sci. 2017, 83, 58–72. [Google Scholar] [CrossRef]
- Barua, A.; Al Faruque, M.A. Hall Spoofing: A Non-Invasive DoS Attack on Grid-Tied Solar Inverter. In SEC’20: Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Online, 12–14 August 2020; USENIX Association: Berkeley, CA, USA, 2020; pp. 1273–1290. [Google Scholar]
- Li, Q.; Li, F.; Zhang, J.; Ye, J.; Song, W.; Mantooth, A. Data-Driven Cyberattack Detection for Photovoltaic (PV) Systems through Analyzing Micro-PMU Data. In Proceedings of the 2020 IEEE Energy Conversion Congress and Exposition (ECCE), Detroit, MI, USA, 11–15 October 2020; pp. 431–436. [Google Scholar] [CrossRef]
- Mohiuddin, S.M.; Qi, J. Attack Resilient Distributed Control for AC Microgrids with Distributed Robust State Estimation. In Proceedings of the 2021 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 2–5 February 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Van Houdt, G.; Mosquera, C.; Nápoles, G. A Review on the Long Short-Term Memory Model. Artif. Intell. Rev. 2020, 53, 5929–5955. [Google Scholar] [CrossRef]
- Koduru, S.; Machina, V.S.P.; Madichetty, S. Cyber Attacks in Cyber-Physical Microgrid Systems: A Comprehensive Review. Energies 2023, 16, 4573. [Google Scholar] [CrossRef]
- Souri, N.; Mehrizi-Sani, A. Hybrid Machine Learning Approach for Cyberattack Mitigation in DC Microgrids. In Proceedings of the IECON 2024—50th Annual Conference of the IEEE Industrial Electronics Society, Chicago, IL, USA, 3–6 November 2024. [Google Scholar] [CrossRef]
- Dehghani, M.; Kavousi-Fard, A.; Dabbaghjamanesh, M.; Avatefipour, O. Deep learning based method for false data injection attack detection in AC smart islands. IET Gener. Transm. Distrib. 2020, 14, 5756–5765. [Google Scholar] [CrossRef]
- Ye, Z.; Yang, H.; Zheng, M. Using modified prediction interval-based machine learning model to mitigate data attack in microgrid. Int. J. Elec. Power Energy Syst. 2021, 129, 106847. [Google Scholar] [CrossRef]
- Hakim, M.S.S.; Karegar, H.K. Detection of False Data Injection Attacks Using Cross Wavelet Transform and Machine Learning. In Proceedings of the 2021 11th Smart Grid Conference (SGC), Tabriz, Iran, 7–9 December 2021. [Google Scholar]
- Mohiuddin, S.M.; Qi, J.; Fung, S.; Huang, Y.; Tang, Y. Deep learning based multi-label attack detection for distributed control of AC microgrids. In Proceedings of the 2021 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aachen, Germany, 25–28 October 2021. [Google Scholar] [CrossRef]








| Parameter | PV Array for 100 kW | PV Array for 50 kW | PV Array for 200 kW |
|---|---|---|---|
| Parallel strings | 24 | 8 | 36 |
| Series-connected modules per string | 11 | 16 | 14 |
| Maximum Power (W) | 400.32 | 400.32 | 400.32 |
| Cells per module () | 80 | 80 | 80 |
| Open circuit voltage (V) | 49.8 | 49.8 | 49.8 |
| Short-circuit current (A) | 10.61 | 10.61 | 10.61 |
| Voltage at maximum power point (V) | 41.7 | 41.7 | 41.7 |
| Current at maximum power point (A) | 9.6 | 9.6 | 9.6 |
| Temperature coefficient of (%/°C) | |||
| Temperature coefficient of (%/°C) | 0.09 | 0.09 | 0.09 |
| Light-generated current (A) | 10.6354 | 10.6354 | 10.6354 |
| Diode saturation current (A) | |||
| Diode ideality factor | 1.0088 | 1.0088 | 1.0088 |
| Shunt resistance () | 77.1038 | 77.1038 | 77.1038 |
| Series resistance () | 0.18434 | 0.18434 | 0.18434 |
| Hyperparameter | LSTM Class | FNN Class | LSTM Detect | FNN Detect |
|---|---|---|---|---|
| Model Type | Stacked LSTM (6) | Feedforward ANN (4) | Stacked LSTM (4) | Feedforward ANN (3) |
| Layers | 6 LSTM | 4 Dense (128, 64, 64, 32) | 4 LSTM | 3 Dense (128, 64, 32) |
| Units per Layer | 50 | 128, 64, 64, 32 | 50 | 128, 64, 32 |
| Return Sequences | Yes | N/A | Yes | N/A |
| Activation | Default | ReLU | Sigmoid (output) | ReLU |
| Dropout | 0.2 | 0.3 | 0.2 | 0.2 |
| Batch Norm. | Yes | No | No | No |
| L2 Reg. | 0.01 (1st layer) | No | No | No |
| Output Layer | Dense (3, softmax) | Dense (3, softmax) | Dense (1, sigmoid) | Dense (1, sigmoid) |
| Loss | Categorical CE | Categorical CE | Binary CE | Binary CE |
| Optimizer | Adam | Adam | Adam | Adam |
| Epochs | 60 | 60 | 50 | 50 |
| Batch Size | 20 | 20 | 20 | 20 |
| Validation Split | 0.2 | 0.2 | 0.2 | 0.3 |
| Callbacks (EarlyStopping) | val_loss | val_loss & val_mae | val_loss | val_loss |
| Patience | 5 | 15 | 10 | 15 |
| Min Delta |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Eswaran, N.; Sivarajah, J.; Karunakaran, K.; Velmanickam, L.; Kumarawadu, S.; Wanigasekara, C. Cyberattack Detection and Classification of Power Converters in Islanded Microgrids Using Deep Learning Approaches. Electronics 2025, 14, 3409. https://doi.org/10.3390/electronics14173409
Eswaran N, Sivarajah J, Karunakaran K, Velmanickam L, Kumarawadu S, Wanigasekara C. Cyberattack Detection and Classification of Power Converters in Islanded Microgrids Using Deep Learning Approaches. Electronics. 2025; 14(17):3409. https://doi.org/10.3390/electronics14173409
Chicago/Turabian StyleEswaran, Nanthaluxsan, Jalini Sivarajah, Kopikanth Karunakaran, Logeeshan Velmanickam, Sisil Kumarawadu, and Chathura Wanigasekara. 2025. "Cyberattack Detection and Classification of Power Converters in Islanded Microgrids Using Deep Learning Approaches" Electronics 14, no. 17: 3409. https://doi.org/10.3390/electronics14173409
APA StyleEswaran, N., Sivarajah, J., Karunakaran, K., Velmanickam, L., Kumarawadu, S., & Wanigasekara, C. (2025). Cyberattack Detection and Classification of Power Converters in Islanded Microgrids Using Deep Learning Approaches. Electronics, 14(17), 3409. https://doi.org/10.3390/electronics14173409








