Bluetooth Protocol for Opportunistic Sensor Data Collection on IoT Telemetry Applications
Abstract
1. Introduction
- A new communication protocol leveraging Bluetooth, specifically tailored for IoT scenarios involving heterogeneous devices. The protocol supports low-latency communication and transmits more information per beacon, improving efficiency in dense deployments.
- The proposed protocol offers dynamic configurability, allowing adjustments to key parameters such as beacon advertisement intervals and transmission power levels to suit specific operational requirements.
- A real-world IoT network was deployed, comprising mobile, power-constrained sensor nodes communicating with distributed BLE bridges. These bridges operate collaboratively to ensure continuous data collection and transmission to an Edge Computing System, regardless of node location within indoor or outdoor environments.
- The protocol was rigorously tested and validated under varying conditions (e.g., distances, obstructions, and parameter settings), demonstrating significant data rate improvements through reduced beacon transmission intervals.
2. Background
2.1. Opportunistic Edge Computing Systems
2.2. Bluetooth Low Energy Communication Basics
- Connection establishment. One of the devices has to take the role of advertiser and the other one, the role of scanner. The advertiser sends advertising packets so that a scanner can discover them and establish communication between both.
- Data exchange. During data exchange, one device acts as the master (i.e., the initiation of the communication), while the other becomes the slave (responding to requests). This dynamic role assignment ensures efficient communications and power management, along with lower latency times.
2.2.1. Connection-Based Communications
2.2.2. Advertisement-Based Communications
2.3. BLE Beacons
- iBeacon: developed by Apple, iBeacon is widely used for indoor positioning systems. It utilizes fixed-position devices distributed throughout a location, such as in a building, to help navigate areas where GPS signals may be unavailable or unreliable, like inside ships or large buildings. In [67] the use of iBeacon for indoor navigation in environments with poor GPS reception was explored, showing its effectiveness in improving location-based services in complex indoor scenarios.
- Altbeacon [68]: authored by Radius Networks, AltBeacon aims to create an open and competitive market for proximity beacon implementations. It is often used in research and commercial applications to measure distances between beacons and devices. For instance, in [69] researchers demonstrated how AltBeacon could be used to determine the distance to a beacon node using a smartphone.
- Eddystone: developed by Google and now open source, Eddystone serves multiple use cases across various industries, including industrial, marketing and healthcare. Eddystone supports four different frame types: URL, UID, EID and TLM. For example, Eddystone-TLM is ideal for transmitting telemetry data, making it suitable for wearables that monitor user and environmental parameters despite supporting limited payloads. For instance, the authors of [70] analyzed the security and privacy of the existing Eddystone-EID protocol, emphasizing its utility in secure data transmission.
2.4. Custom Beaconing Protocols
3. Design and Implementation of the Proposed Bluetooth Opportunistic Protocol
3.1. Communications Architecture
- IoT Mobile Devices. They are microcontroller-based devices connected to sensors. Such mobile devices broadcast sensor parameter values via BLE, compressing the transmitted data to allow for sending up to three parameters per frame. After transmitting the information, the device enters low-power mode, thus extending battery autonomy. These devices are configured with a predefined transmission power level and advertisement interval. To modify these settings, a firmware update is required.
- IoT Static Devices. They are similar to IoT Mobile Devices, but they remain at a fixed position and include sensors that read parameters from the environment, like temperature, noise level or air quality. These devices are not battery-dependent, as they do not need to be mobile. The parameters are also broadcast via BLE.
- BLE Bridges. These devices serve as mere data receivers, so they do not embed sensors. Their primary function is to capture all the data transmitted by IoT devices. Strategically positioned at fixed locations, these bridges relay the information to Single Board Computer (SBC) devices capable of processing or presenting it to end users. The distribution of these devices across a given area ensures that the transmitters do not lose coverage even when they move out of the range of a specific bridge. As a beacon communication, there is no need for a bonding process between the bridge and an IoT device. Therefore, a bridge can receive a beacon from an IoT device that it has never detected before. Every bridge device is configured with a transmission power level and it stores information about beacon frame types, as previously explained in Section 2.4. A detailed description of the Bridge layer internal design, including message structure, framing, segmentation and reassembly is provided in [5]. Such an article provides a comprehensive overview of the Bridge architecture and its role in enabling end-to-end interoperability in the IoT use cases considered. It also goes into detail about how the Bridge handles the data translation process and various issues, such as describing how BLE advertisements relate to libp2p messages, integrity checks, segmentation logic, and how clients are requested to deliver the data to them.
- Cloud. Once the bridges have received the information and decompressed it, it can be transferred to the Cloud, which is a powerful computing system capable of managing all the information and making it accessible and understandable to the end user. For this latter purpose, a Cloud usually makes use of a Data Base Management System (DBMS) and executes a remote web application, so that the end user does not need to run a specific app on his/her own device.
- Blockchain or Distributed Ledger Technologies (DLTs). It is also possible to store data on a blockchain/DLT in scenarios where the information is sensitive, particularly in industrial contexts where traceability information can be critical [73]. In a system that utilizes a decentralized network of SBCs, like the proposed architecture, the integration of blockchain offers significant advantages, including transparency, decentralization, data authenticity, data security and operational efficiency thanks to the use of smart contracts [74].
3.2. Bluetooth-Based Opportunistic Protocol
- IoT devices can receive new beacons from the same transmitter at a maximum rate (e.g., in the proposed protocol, one beacon every second from each transmitter).
- The length of a beacon frame is limited, so it is not possible to send all the collected information in a single beacon frame.
- The first limitation is related to the beacon frame format: for Eddystone beacon frames, 8 bytes are used for general Eddystone data like UUID or length; 14 bytes are dedicated to some telemetry data like battery or temperature and 6 bytes are not used. Therefore, there is only a small amount of bytes available for sensing sensor values and such bytes are not flexible.
- The second limitation is associated with the bridge, since it is only able to scan for beacons within a certain time window. During such a time, the bridge can only obtain one single beacon from a specific IoT device within range, and this window has a minimum time of 1 s, so if, for example, a device requires five different beacons to communicate all its parameters, the total reading time would be at least 5 s for every device.
- Every beacon will make use of the last 6 bytes that are not used by traditional Eddystone-TLM beacons.
- Since it is not necessary to utilize the bytes originally designated for temperature, the two available bytes are used to identify the “frame type”. This frame type serves to specify the parameters contained within the last six bytes of the frame. For example, frame type 1 indicates that the last 6 bytes contain data for temperature, humidity or pressure. Note that having 2 bytes for frame types means that there will be 65,536 different types available, which are shared by all devices and all their parameters.
- The structure of an Eddystone-TLM frame, shown in Figure 3 has a total of 20 bytes, 14 of them dedicated for Type, Version, Battery, Temperature, PDU Count and time. Thus, the proposed protocol makes use of the last 6 bytes for custom parameters, while still maintaining the structure from the original Eddystone-TLM definition. However, in situations where even more data need to be transmitted and when the parameters from the dedicated bytes are not useful, there is the possibility of using more bytes, taking them from the original structure, leading to being able to use 14 more bytes. The proposed frame for Eddystone-TLM ADV Data is shown in Figure 4, illustrating how the “Temperature” bytes are replaced by “Frame ID” bytes, while the previously unused bytes are utilized for additional parameters.
3.3. Data Processing
4. Experiments
4.1. Experiment Design
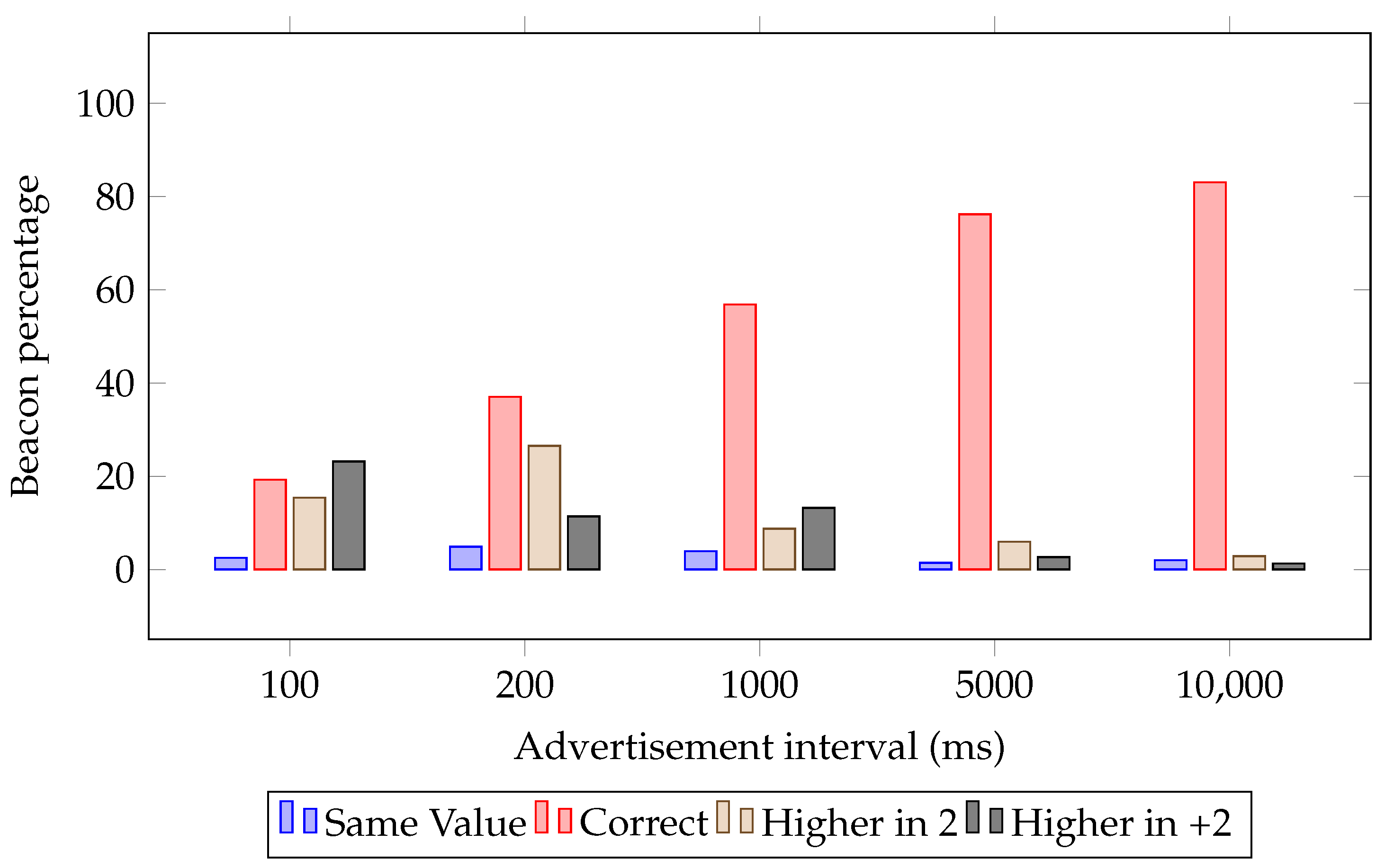
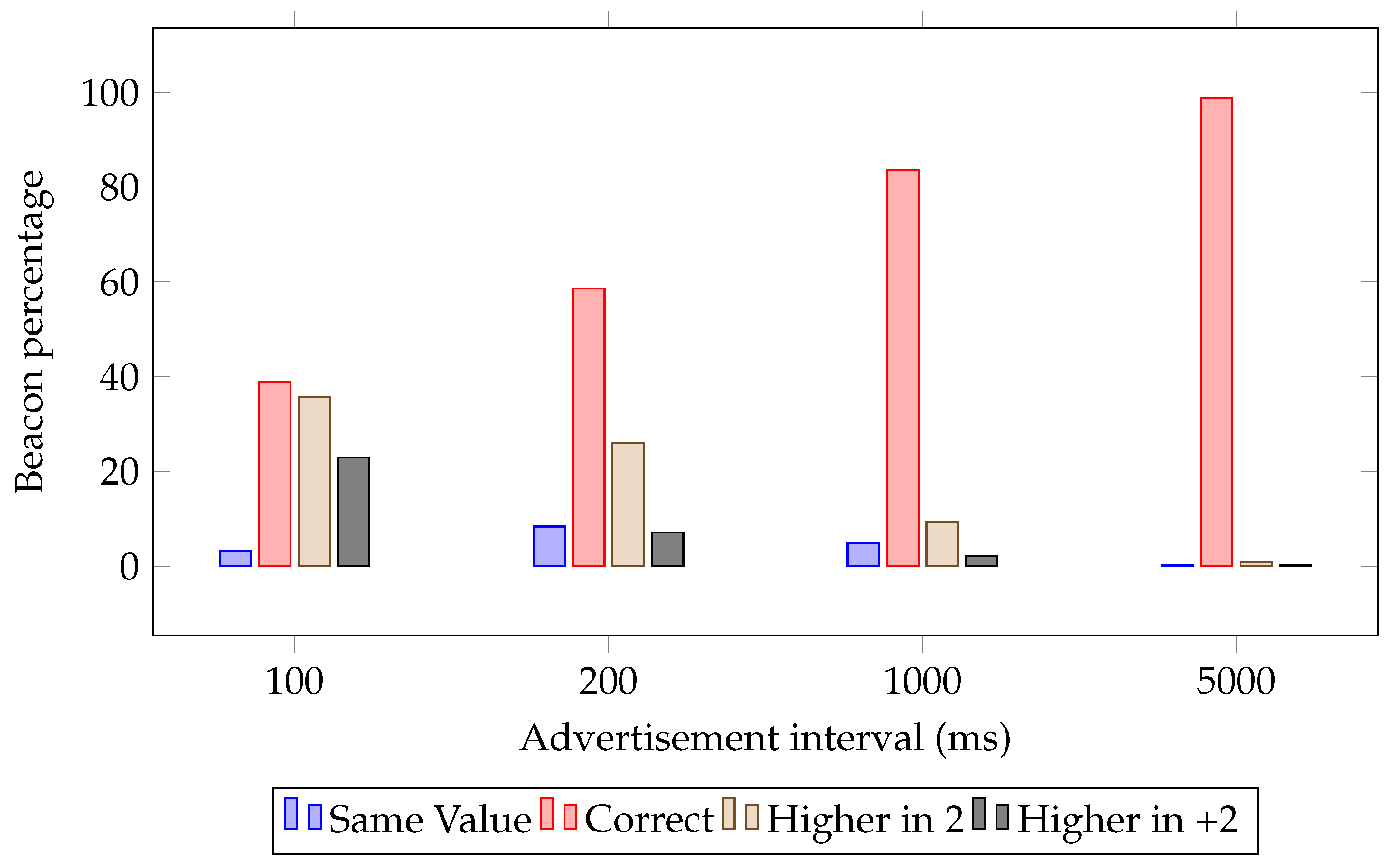
4.1.1. Advertisement Interval Distribution
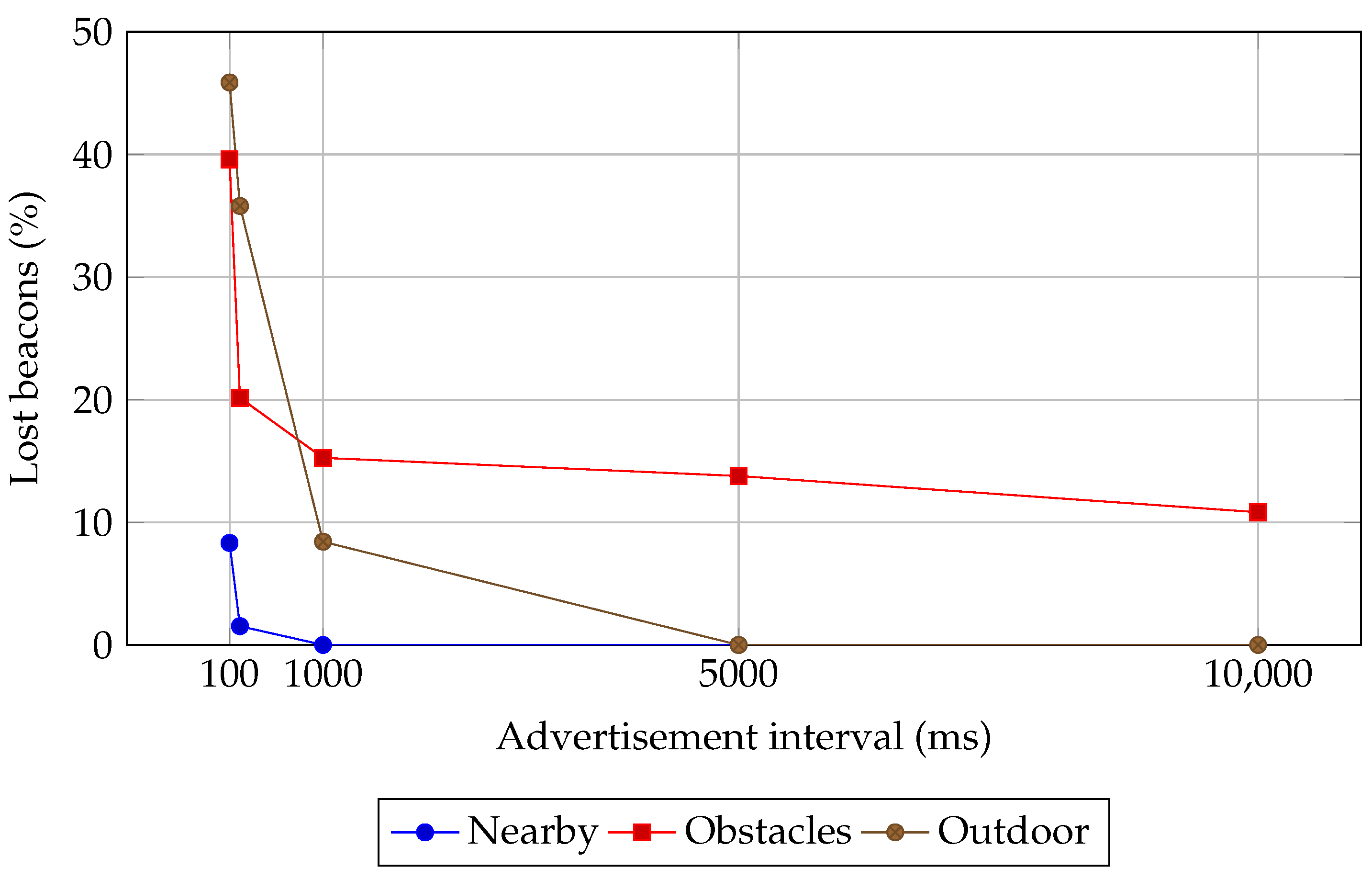
4.1.2. Lost Beacons
4.1.3. Test Scenarios
- Nearby scenario. All IoT devices surrounded the bridge device at approximately 10 cm of distance and no obstacles. As it can be imagined, this is an ideal scenario that can be considered as a reference when assessing the results obtained in other, more complex scenarios. All devices are located on a flat wooden surface. The ceiling is 1.8 m above, and all surrounding surfaces are flat. There is no presence of humans, machinery, or vehicles in this scenario.
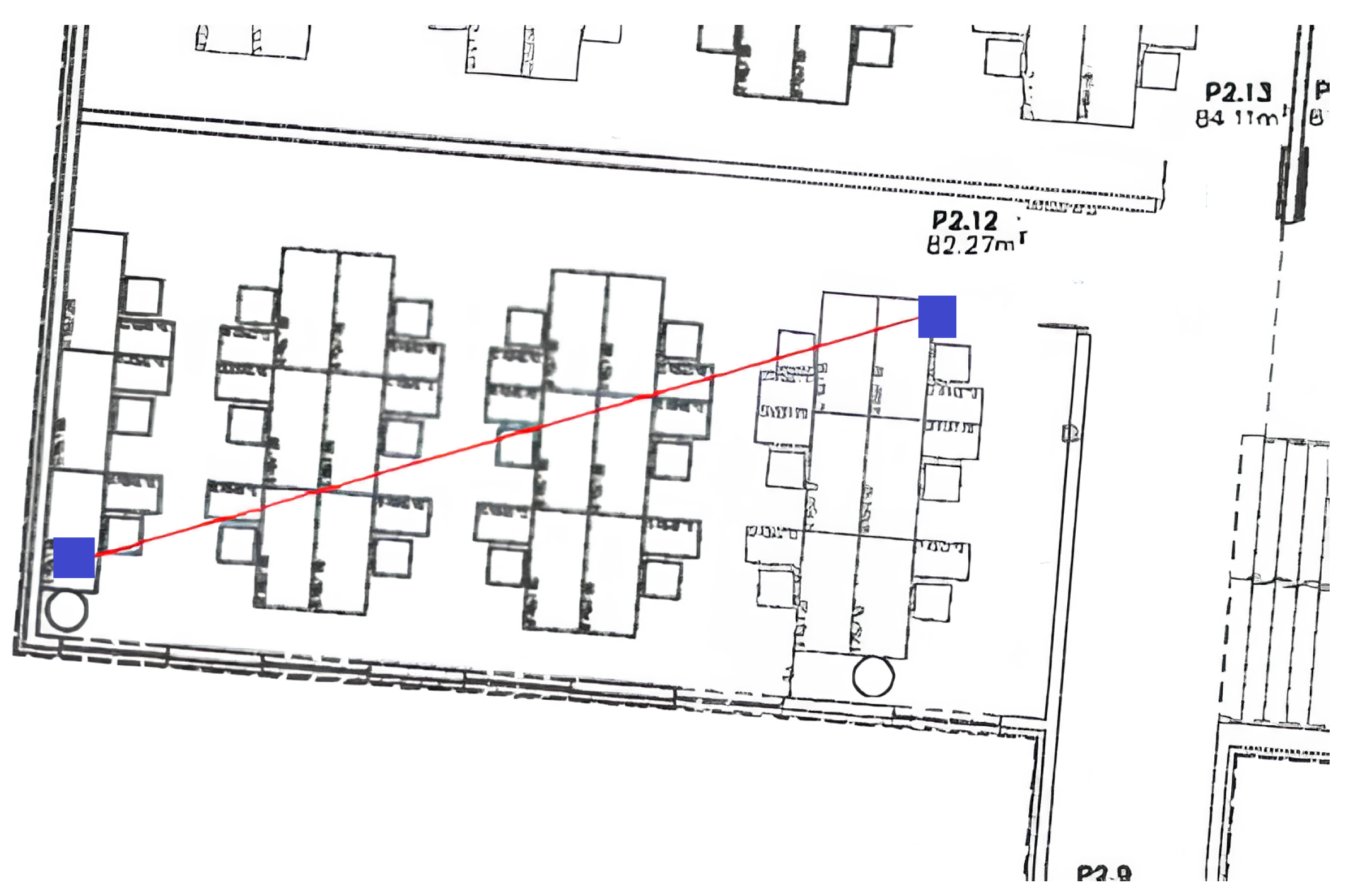
- Home with obstacles. This is an indoor scenario within a building, where the bridge and the IoT devices were separated by two concrete walls, some wooden furniture, one metal pillar and two closed wooden doors; every obstacle has right angles and a flat surface. The IoT devices were close to each other, while the distance between these devices and the bridge was around 10 m. This setup represents a challenging Non Line of Sigth (NLoS) scenario, characterized by thick obstacles that introduce signal interference and reflections. The IoT devices and bridge were located on an elevated surface at a height of roughly 1 m. Figure 6 shows a blueprint of this scenario.
- Building with obstacles. This is an indoor office scenario, where the bridge and the IoT devices were separated by many desktops and electronic devices. There was only one transmitter and one receiver. The IoT devices and bridge were located inside a drawer to make communications even more difficult, thus simulating the existence of additional obstacles. Additional obstacles in the environment included people and IT equipment (PCs, routers, monitors). Drawers and other furnishings were primarily made of wood. Most of the obstacles have right angles and flat surfaces. The devices were positioned approximately 2 m below the ceiling. Figure 7 shows a blueprint of this scenario.
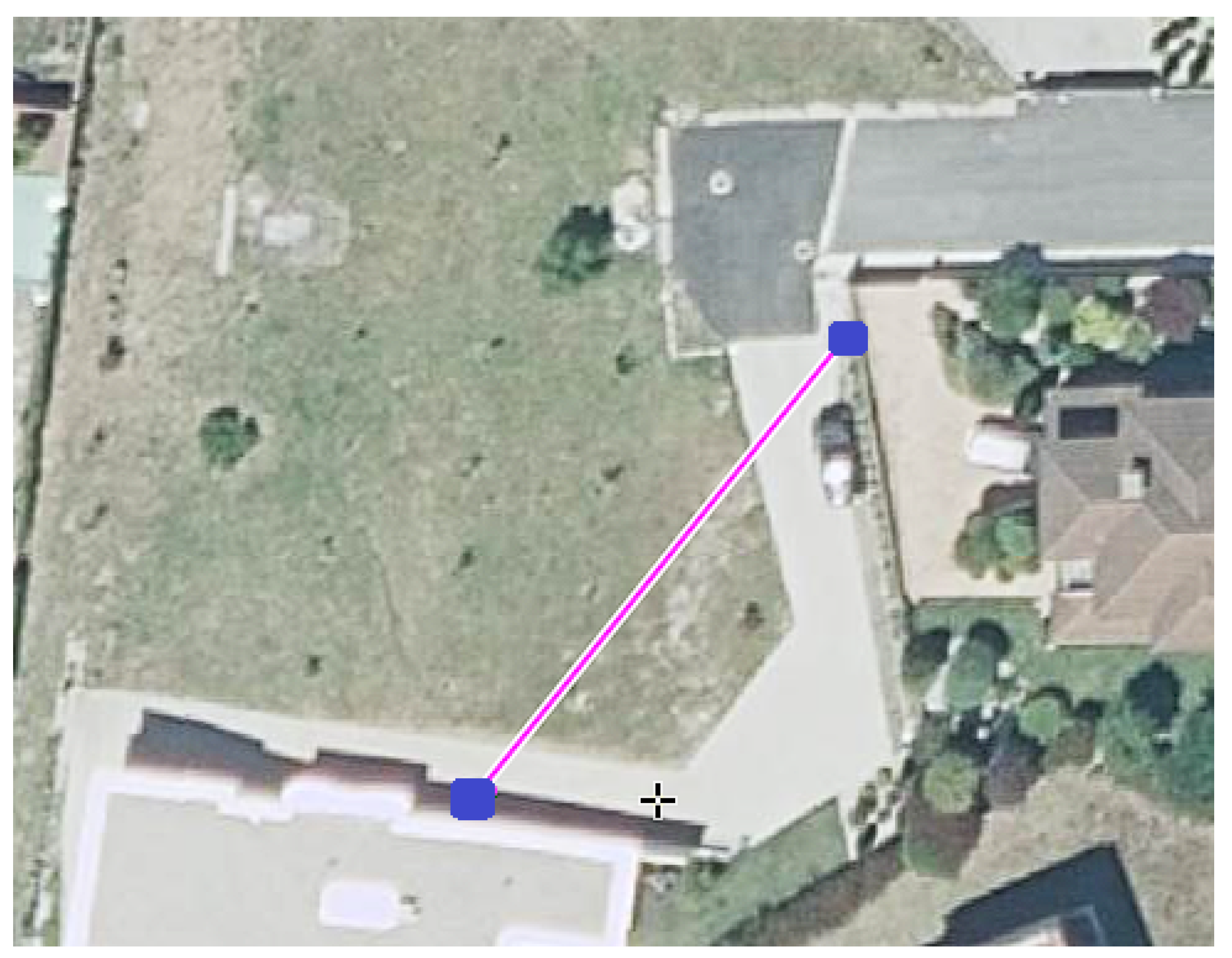
- Outdoor scenario. All IoT devices were positioned in the same location, at a height of approximately 25 cm, and they were separated from the bridge by 25 m (the bridge was at a height of roughly 1 m). The ground that separates the bridge and the IoT devices was slightly inclined, but there was a Line of Sight (LoS) between the transmitters and the receiver. There were no physical barriers or obstructions between the devices, and the density of electronic devices is minimized to reduce the risk of interference. Also, there are no people, vehicles, or obstacles between devices. As an outdoor scenario, there was no ceiling. Each device, at the opposite path from the other device, had a rock wall that may absorb part of the signal, but also create reflections that generate multiple paths; this may lead to overlapping, producing constructive or destructive interferences. This scenario aims to measure the performance of the proposed protocol over long distances in an environment with minimal obstacles and reduced reflection sources. Figure 8 shows a satellite view of this scenario.
- Industrial scenario. Some tests were performed in an industrial workshop with the presence of heavy machinery and metal objects. Specifically, the place where the tests were carried out was the facilities of Navantia in Ferrol (Spain). Navantia is one of the ten largest shipbuilders in the world. Actually, the goal of this set of experiments was to evaluate the performance of the proposed protocol to locate objects used by industrial operators for their shipbuilding tasks and also track some parameters from a vast set of objects, being scalable and power efficient. Figure 9 and Figure 10 show the location of the devices and distance between them, while Figure 11, shows a blueprint with the different positions of the devices and distance between them. This is a NLoS scenario. The devices were located at a 1–1.5 m height, and the ceiling is at approximately 10 m distance. Different distances and obstacle densities were tested. During the tests, industrial operators, electronic devices, and machinery were moving between both IoT devices, as in a regular working day in the workshop. This scenario is very demanding due to the high presence of metal obstacles, which notably reduces the quality of the signal received. As there were a vast amount of obstacles, the surface of the environment is not flat, causing more interferences, different reflections and multipath.
4.1.4. Configurable Parameters
4.2. Experimental Results
4.2.1. Advertisement Interval Distribution
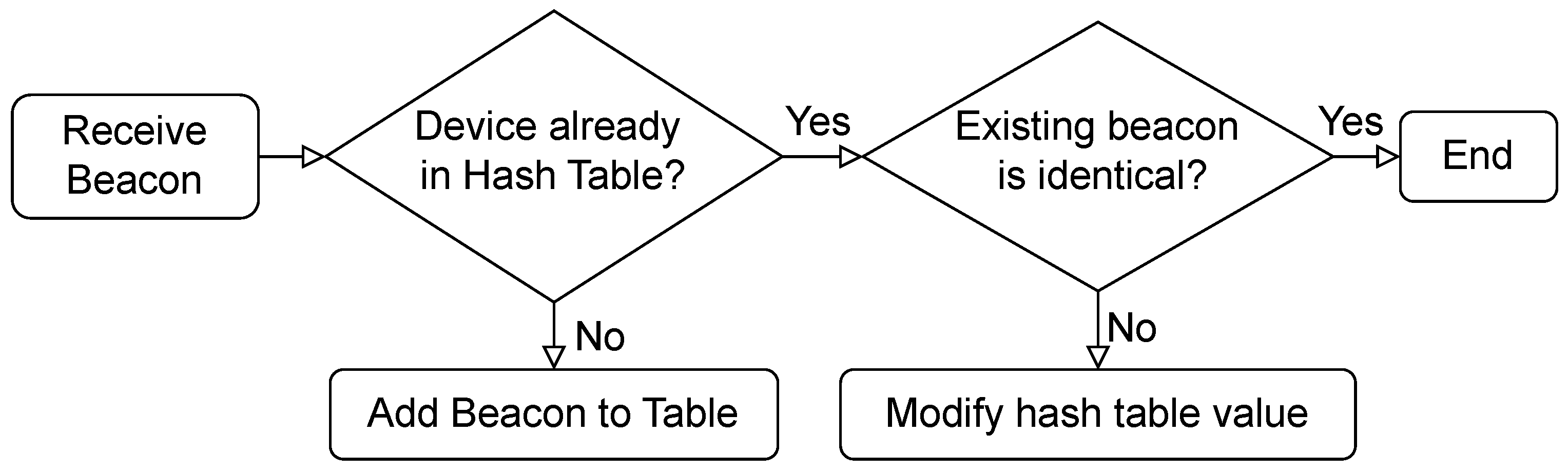
- Same value. When the received value was identical to the previous one, this would mean the receiver was not able to receive the current beacon but did receive a beacon before the sender updated the counter value. By default, it is not possible for a bridge to receive the same beacon from the same sender more than once, but in this case, this is possible because the bridge forgets the last beacon received in order to increase the frequency of receiving them. In addition, the hash table mentioned in Section 3.3 was not used for these tests, as the aim of the test is to measure how often these situations occur. It must be noted that sending a beacon is not something that happens instantly, as happens with GATT communications; the beacon is continuously emitted during the advertisement interval.
- Correct value. The received value was exactly one unit higher than the previous value received from that sender.
- Value higher than 2 units. One intermediate beacon was lost, or the transmitter ended its sending interval before expected.
- Value higher in more than 2 units. Between the transmissions of two beacons, more than one beacon was lost.
4.2.2. Impact of Transmission Power Level and Advertisement Interval for Different IoT Nodes
5. Key Findings
- The communication protocol presented in this article is designed for IoT telemetry systems that require low consumption. Compared with the original Eddystone-TLM standard, this protocol reduces many limitations, such as the restriction to a single beacon per second per device and the maximum payload per frame. The protocol is designed to be customizable using different frame types for heterogeneous devices, while still maintaining compatibility with the standard Eddystone-TLM beacon.
- The performed experiments allowed for validating the use of the protocol in the selected evaluation scenarios. For instance, in the nearby scenario, more than 90% of the emitted data were received for a 100 ms advertisement interval, meaning an effective data rate of 9 received beacons per second for each device, in contrast to the maximum of only one when using the Eddystone-TLM standard. For a 25 m distance, data loss was approximately 36% for a 200 ms advertisement interval, still granting a higher effective data rate than the original protocol.
- Some of the evaluated IoT nodes proved to offer clearly better results, like when using Bluetooth 5 hardware and an external antenna with +21 dBm, which led to almost 90% data reception for a 100 m distance (when using the same advertisement interval). Such IoT nodes were also effective for scenarios with a high presence of metal obstacles, where increasing the advertisement interval is not enough for receiving more than 90% of the emitted data. For instance, in the industrial scenario, the previously mentioned hardware obtained roughly 80% of the data received at a 42 m distance with a 200 ms advertisement interval (i.e., four beacons were actually received beacons per second). These results can be further enhanced by the ability to transmit up to three parameters per beacon when employing data compression techniques.
- The effectiveness of the proposed protocol is demonstrated for diverse contexts, including industry environments, indoor and outdoor scenarios. For instance, the results from the previous section show that beacon loss is minimal in scenarios with short distances and few obstacles.
- Ideal conditions are not always present in real-world deployments. To keep a high bandwidth under challenging conditions, there are different strategies. The first one involves utilizing the latest hardware, equipped with Bluetooth 5.0 or newer, which leads to lower power consumption and reduces data loss. When the objective is to maximize bandwidth, reducing the advertisement interval has proven effective, as it allows for the emission of updated data with the lowest latency. In long-distance scenarios, increasing the advertisement interval can help reduce beacon loss. However, this approach may be insufficient in environments with thick obstacles and rough surfaces that significantly cause signal attenuation. In such cases, increasing the transmission power level is an effective solution. Finally, in harsh environments where long-distance communications must occur in the presence of obstacles, using external antennas can significantly enhance performance.
- The experimental tests validated the functionality of the proposed protocol, demonstrating notable improvements in data rate achieved by reducing beacon transmission intervals. Specifically, the results indicate that newer hardware utilizing Bluetooth 5 not only offers broader coverage compared with earlier versions but also provides lower power consumption. Moreover, the proposed protocol can take advantage of increasing the transmission power level to increase data reception at the cost of more energy consumption. Furthermore, the use of an external antenna can significantly extend the operating range of the proposed protocol. While this extended range may not be necessary in all scenarios, using a single device for receiving data from all the transmitters deployed in a large area reduces the number of receiver devices needed. Deploying more receivers in the same area can also provide fine-grained information about the location of the devices.
- It is worth noting that the presented experiments evaluated performance in each environment using packet loss as the primary metric, without relying on empirical models, as several existing studies have already explored that approach. For instance, a relevant study about BLE 5 and how distances affect its range for indoor environments is found in [75], where authors measure the Received Signal Strength Indicator (RSSI) for different positions inside a building. A more in-depth analysis is performed in [76] for RSSI and how transmission power affects connectivity for the previous BLE version 4. On Low-Power Wide-Area Network (LPWAN) communications, the studies [77,78] use empirical models and equations for measuring the signal strength at different scenarios. These models cannot apply to this study, as they are designed for >1 km distances, while the performed experiments took place on <100 m scenarios.
- With respect to future work, it is worth noting that this article is not focused on providing an in-depth analysis of the energy consumption of the proposed protocol and architecture. Therefore, a natural extension of this research would be to compare the power usage of the proposed protocol against the standard Eddystone-TLM when running on identical devices. In addition, it would be valuable to quantify the additional energy cost associated with techniques such as increasing transmission power or utilizing larger antennas.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Demandsage. How Many IoT Devices Are There (2025–2030). Available online: https://www.demandsage.com/number-of-iot-devices/ (accessed on 8 July 2025).
- Hernández-Rojas, D.; Fernández-Caramés, T.; Fraga-Lamas, P.; Escudero, C. A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things. Sensors 2018, 18, 2052. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Barros, D.; Lopes, S.I.; Fernández-Caramés, T.M. Mist and Edge Computing Cyber-Physical Human-Centered Systems for Industry 5.0: A Cost-Effective IoT Thermal Imaging Safety System. Sensors 2022, 22, 8500. [Google Scholar] [CrossRef] [PubMed]
- Niebla-Montero, A.; Froiz-Míguez, I.; Fraga-Lamas, P.; Fernández-Caramés, T.M. Practical Latency Analysis of a Bluetooth 5 Decentralized IoT Opportunistic Edge Computing System for Low-Cost SBCs. Sensors 2022, 22, 8360. [Google Scholar] [CrossRef] [PubMed]
- Niebla-Montero, A.; Froiz-Míguez, I.; Fraga-Lamas, P.; Fernández-Caramés, T.M. Design, Implementation and Practical Evaluation of an Opportunistic Communications Protocol Based on Bluetooth Mesh and libp2p. Sensors 2025, 25, 1190. [Google Scholar] [CrossRef]
- Ayele, E.D.; Meratnia, N.; Havinga, P.J. Towards a New Opportunistic IoT Network Architecture for Wildlife Monitoring System. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Huang, X.; Yu, R.; Liu, J.; Shu, L. Parked Vehicle Edge Computing: Exploiting Opportunistic Resources for Distributed Mobile Applications. IEEE Access 2018, 6, 66649–66663. [Google Scholar] [CrossRef]
- Max-Onakpoya, E.; Madamori, S.; Baker, C.E. Utilizing Opportunistic Social Networks for Remote Patient Monitoring in Rural Areas. In Proceedings of the 1st ACM International Workshop on Technology Enablers and Innovative Applications for Smart Cities and Communities, New York, NY, USA, 13–14 November 2019; TESCA’19. pp. 46–49. [Google Scholar] [CrossRef]
- Silva, R.; Silva, J.S.; Boavida, F. Opportunistic fog computing: Feasibility assessment and architectural proposal. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 510–516. [Google Scholar] [CrossRef]
- Mohamed, N.; Al-Jaroodi, J.; Jawhar, I.; Noura, H.; Mahmoud, S. UAVFog: A UAV-based fog computing for Internet of Things. In Proceedings of the 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), San Francisco, CA, USA, 4–8 August 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Chamarajnagar, R.; Ashok, A. Opportunistic Mobile IoT with Blockchain Based Collaboration. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 10–12 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. Design of a Fog Computing, Blockchain and IoT-Based Continuous Glucose Monitoring System for Crowdsourcing mHealth. Proceedings 2019, 4, 37. [Google Scholar] [CrossRef]
- Bluetooth. Bluetooth 5.4 Specification. Available online: https://www.bluetooth.com/bluetooth-resources/bluetooth-core-specification-version-5-4-technical-overview/ (accessed on 15 July 2025).
- Yaakop, M.B.; Abd Malik, I.A.; bin Suboh, Z.; Ramli, A.F.; Abu, M.A. Bluetooth 5.0 throughput comparison for internet of thing usability a survey. In Proceedings of the 2017 International Conference on Engineering Technology and Technopreneurship (ICE2T), Kuala Lumpur, Malaysia, 18–20 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Enriko, I.K.A.; Gustiyana, F.N. Wi-Fi HaLow: Literature Review About Potential Use of Technology in Agriculture and Smart Cities in Indonesia. In Proceedings of the 2024 International Conference on Green Energy, Computing and Sustainable Technology (GECOST), Miri Sarawak, Malaysia, 17–19 January 2024; pp. 277–281. [Google Scholar] [CrossRef]
- Webpage, T.G.O. Thread Group Official Webpage. Available online: https://www.threadgroup.org (accessed on 4 July 2025).
- Tupas Castro, C.M.; Sharma, A.; Sampath Kumar, D.; Abidi, K.; Kim, N. The implementation of Thread Network for a Smart Factory. In Proceedings of the 2022 IEEE Symposium Series on Computational Intelligence (SSCI), Singapore, 4–7 December 2022; pp. 253–260. [Google Scholar] [CrossRef]
- Jaisinghani, D.; Rehman, T.U.; Mulkey, R.; Berns, A. IoT in the Air: Thread-Enabled Flying IoT Network for Indoor Environments. In Proceedings of the 2023 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Atlanta, GA, USA, 13–17 March 2023; pp. 142–147. [Google Scholar] [CrossRef]
- IQRF Alliance. Available online: https://www.iqrfalliance.org/index.php (accessed on 4 July 2025).
- Bouzidi, M.; Gupta, N.; Dalveren, Y.; Mohamed, M.; Alaya Cheikh, F.; Derawi, M. Indoor Propagation Analysis of IQRF Technology for Smart Building Applications. Electronics 2022, 11, 3972. [Google Scholar] [CrossRef]
- Gkagkas, G.; Vergados, D.J.; Michalas, A. The advantage of the 5G network for enhancing the Internet of Things. In Proceedings of the 2021 6th South-East Europe Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM), Preveza, Greece, 24–26 September 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Petrenko, A.S.; Petrenko, S.A.; Makoveichuk, K.A.; Chetyrbok, P.V. The IIoT/IoT device control model based on narrow-band IoT (NB-IoT). In Proceedings of the 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow and St. Petersburg, Russia, 29 January–1 February 2018; pp. 950–953. [Google Scholar] [CrossRef]
- Insteon Official Webpage. Available online: https://www.insteon.com (accessed on 4 July 2025).
- EnOcean Alliance. Available online: https://enocean-alliance.org (accessed on 4 July 2025).
- X10. Available online: https://www.x10.com/pages/allaboutx10 (accessed on 4 July 2025).
- Wi-Sun Official Webpage. Available online: https://wi-sun.org/ (accessed on 4 July 2025).
- Scaramella, G.; Heck, G.C.; Lippmann Junior, L.; Hexsel, R.A.; Santana, T.; Gomes, V.B. Enabling LoRaWAN Communication Over Wi-SUN Smart Grid Networks. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 4842–4847. [Google Scholar] [CrossRef]
- Extended Coverage-GSM-Internet of Things (EC-GSM-IoT). Available online: https://www.gsma.com/solutions-and-impact/technologies/internet-of-things/extended-coverage-gsm-internet-of-things-ec-gsm-iot/ (accessed on 4 July 2025).
- Weber, B.; Korb, M.; Tschopp, D.; Altorfer, S.; Rogin, J.; Kröll, H.; Huang, Q. A SAW-less RF-SoC for cellular IoT supporting EC-GSM-IoT -121.7 dBm sensitivity through EGPRS2A 592 kbps throughput. In Proceedings of the ESSCIRC 2017—43rd IEEE European Solid State Circuits Conference, Leuven, Belgium, 11–14 September 2017; pp. 340–343. [Google Scholar] [CrossRef]
- Ingenu Official Webpage. Available online: https://www.ingenu.com/technology/rpma/ (accessed on 4 July 2025).
- Nashiruddin, M.I.; Winalisa, S.; Nugraha, M.A. Random Phase Multiple Access Network for Public Internet of Things in Batam Island. In Proceedings of the 2021 8th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), Semarang, Indonesia, 20–21 October 2021; pp. 311–316. [Google Scholar] [CrossRef]
- Waviot Official Webpage. NB-Fi Specification. Available online: https://waviot.com/technology/nb-fi-specification/ (accessed on 4 July 2025).
- Bankov, D.; Levchenko, P.; Lyakhov, A.; Khorov, E. On the Limits and Best Practice for NB-Fi: A New LPWAN Technology. IEEE Internet Things J. 2023, 10, 12352–12365. [Google Scholar] [CrossRef]
- Mioty Alliance Official Webpage. Available online: https://mioty-alliance.com/ (accessed on 4 July 2025).
- Mandal, D.; Banerjee, S. Surface Acoustic Wave (SAW) Sensors: Physics, Materials, and Applications. Sensors 2022, 22, 820. [Google Scholar] [CrossRef]
- Shah, S.; Koley, S.; Malandra, F. Experimental End-To-End Delay Analysis of LTE Cat-M with High-Rate Synchrophasor Communications. IEEE Internet Things J. 2023, 10, 19839–19848. [Google Scholar] [CrossRef]
- Wize Alliance. Technical Documents. 2024. Available online: https://www.wize-alliance.com/Downloads/Technical (accessed on 4 July 2025).
- Niebla-Montero, A.; Froiz-Míguez, I.; Fraga-Lamas, P.; Fernández-Caramés, T.M. Practical Evaluation of Wize and Bluetooth 5 Assisted RFID for an Opportunistic Vehicular Scenario. In Proceedings of the 2024 IEEE International Conference on RFID (RFID), Cambridge, MA, USA, 4–6 June 2024; pp. 101–106. [Google Scholar] [CrossRef]
- Arnaud, A.; Costa, G. Ultra low-cost sensors using RFID standards for data collection, for IoT systems in food production and logistics. In Proceedings of the 2020 IEEE 11th Latin American Symposium on Circuits & Systems (LASCAS), San Jose, Costa Rica, 25–28 February 2020; pp. 1–4. [Google Scholar] [CrossRef]
- NFC Forum. Specifications. 2024. Available online: https://nfc-forum.org/ (accessed on 4 July 2025).
- Gawade, D.R.; Roy Simorangkir, B.V.B.; Kumar, S.; Pigeon, M.; Belcastro, M.; Rather, N.; Buckley, J.L.; O’Flynn, B. A Battery-less NFC Sensor Transponder for Cattle Health Monitoring. In Proceedings of the 2023 IEEE Applied Sensing Conference (APSCON), Bengaluru, India, 23–25 January 2023; pp. 1–3. [Google Scholar] [CrossRef]
- Bluetooth Technology Website. Specifications. 2024. Available online: https://www.bluetooth.com/specifications/specs/ (accessed on 4 July 2025).
- García-Rivada, P.; Fraga-Lamas, P.; Fernández-Caramés, T. An Intelligent IoT Wearable for Monitoring and Preventing Asthma Attacks. In Proceedings of the VI Congreso XoveTIC: Impulsando el Talento Científico, A Coruña, Spain, 5–6 October 2023; pp. 263–268. [Google Scholar] [CrossRef]
- Fré, G.; Erman, B.; Martino, C.D. Data Shower in Electronics Manufacturing: Measuring Wi-Fi 4, Wi-Fi 6, and 5G SA behavior in production assembly lines. In Proceedings of the 2023 53rd Annual IEEE/IFIP International Conference on Dependable Systems and Networks—Supplemental Volume (DSN-S), Porto, Portugal, 27–30 June 2023; pp. 14–20. [Google Scholar] [CrossRef]
- Stankevich, S.A.; Lubskyi, M.S.; Lysenko, A.R. Long-wave infrared remote sensing data spatial resolution enhancement using modulation transfer function fusion approach. In Proceedings of the 2021 International Conference on Information and Digital Technologies (IDT), Zilina, Slovakia, 22–24 June 2021; pp. 89–94. [Google Scholar] [CrossRef]
- UWB Alliance. UWB Alliance Official Website. 2024. Available online: https://uwballiance.org/ (accessed on 4 July 2025).
- Kopta, V.; Enz, C. Ultra-Low Power FM-UWB Transceivers for IoT; River Publishers: Boca Raton, FL, USA, 2019; pp. i–xxiv. [Google Scholar]
- Connectivity Standards Alliance. ZigBee. 2024. Available online: https://csa-iot.org/all-solutions/zigbee/ (accessed on 4 July 2025).
- Pawaskar, M.; Aneesh, S.; Sharma, D.; Sawale, P.; Sharma, R.; Sharma, A. IoT Enabled Smart Dustbin Using Zigbee Network. In Proceedings of the 2021 International Conference on Advances in Computing, Communication, and Control (ICAC3), Mumbai, India, 3–4 December 2021; pp. 1–4. [Google Scholar] [CrossRef]
- DASH7 Alliance. DASH7 Alliance Official Website. 2024. Available online: https://dash7-alliance.org (accessed on 4 July 2025).
- Ayoub, W.; Nouvel, F.; Samhat, A.E.; Prevotet, J.C.; Mroue, M. Overview and Measurement of Mobility in DASH7. In Proceedings of the 2018 25th International Conference on Telecommunications (ICT), Saint Malo, France, 26–28 June 2018; pp. 532–536. [Google Scholar] [CrossRef]
- Garmin ANT+. Garmin ANT+ in the Gym. 2024. Available online: https://www8.garmin.com/intosports/antplus.html (accessed on 4 July 2025).
- Z-Wave Alliance. Z-Wave Alliance Official Website. 2024. Available online: https://z-wavealliance.org/ (accessed on 4 July 2025).
- Koch, G.; Mahir, S.M.; Chien, S.; Herne, J.; Cheshire, A.; Lee, J.J. No Programming, Configurable Z-Wave Node with Multi-Sensor-Protocol Support. In Proceedings of the 2023 17th International Conference on Ubiquitous Information Management and Communication (IMCOM), Seoul, Republic of Korea, 3–5 January 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Salsabila, M.G.; Murti, M.A.; Fuadi, A.Z. Design of 3 Phase kWh Meter Communication Based on Internet of Things (IoT) Using LoRa. In Proceedings of the 2022 IEEE International Conference on Internet of Things and Intelligence Systems (IoTaIS), Bali, Indonesia, 24–26 November 2022; pp. 93–97. [Google Scholar] [CrossRef]
- Sigfox Official Webpage. Sigfox Official Website. 2024. Available online: https://www.sigfox.com/ (accessed on 4 July 2025).
- Yamazaki, S.; Nakajima, Y. A Sigfox Energy Consumption Model via Field Trial: Case of Smart Agriculture. IEEE Access 2023, 11, 145320–145330. [Google Scholar] [CrossRef]
- Garg, N.; Garg, R. Energy Harvesting in IoT Devices: A Survey. In Proceedings of the 2017 International Conference on Intelligent Sustainable Systems (ICISS), Palladam, India, 7–8 December 2017; pp. 127–131. [Google Scholar] [CrossRef]
- Mohammed, M.A.; Mustafa, F.F.; Mustafa, F.I. Feasibility Study for Using Harvesting Kinetic Energy Footstep in Interior Space. In Proceedings of the 2020 11th International Renewable Energy Congress (IREC), Hammamet, Tunisia, 24–26 March 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Ruan, T.; Chew, Z.J.; Zhu, M. Energy-Aware Approaches for Energy Harvesting Powered Wireless Sensor Nodes. IEEE Sens. J. 2017, 17, 2165–2173. [Google Scholar] [CrossRef]
- Boursianis, A.D.; Papadopoulou, M.; Gotsis, A.G.; Wan, S.; Sarigiannidis, P.; Nikolaidis, S.; Goudos, S.K. Smart Irrigation System for Precision Agriculture—The AREThOU5A IoT Platform. IEEE Sens. J. 2021, 21, 17539–17547. [Google Scholar] [CrossRef]
- Md Jamil, M.N.B.; Omar, M.; Ibrahim, R.; Bingi, K.; Faqih, M. Rectenna System Development Using Harmonic Balance and S-Parameters for an RF Energy Harvester. Sensors 2024, 24, 2843. [Google Scholar] [CrossRef]
- Online UUID Generator Tool. Online UUID Generator Tool. Available online: https://www.uuidgenerator.net/ (accessed on 27 June 2025).
- Bluetooth SIG. List of Officially Adopted Services UUIDs. Available online: https://www.bluetooth.com/specifications/gatt/services (accessed on 27 June 2025).
- Aguilar, S.; Vidal, R.; Gomez, C. Opportunistic Sensor Data Collection with Bluetooth Low Energy. Sensors 2017, 17, 159. [Google Scholar] [CrossRef]
- Hernández-Rojas, D.; Fernández-Caramés, T.; Fraga-Lamas, P.; Escudero, C. Design and Practical Evaluation of a Family of Lightweight Protocols for Heterogeneous Sensing through BLE Beacons in IoT Telemetry Applications. Sensors 2018, 18, 57. [Google Scholar] [CrossRef]
- Volkovich, Z.; Ravve, E.V.; Avros, R. Indoor Navigation in Facilities with Repetitive Structures. Sensors 2024, 24, 2876. [Google Scholar] [CrossRef]
- Altbeacon. Altbeacon Official Website. Available online: https://altbeacon.org/ (accessed on 4 July 2025).
- Gowrishankar, S.; Madhu, N.; Basavaraju, T.G. Role of BLE in Proximity Based Automation of IoT: A Practical Approach. In Proceedings of the 2015 IEEE Recent Advances in Intelligent Computational Systems (RAICS), Kerala, India, 10–12 December 2015; pp. 400–405. [Google Scholar] [CrossRef]
- David, L.; Hassidim, A.; Matias, Y.; Yung, M.; Ziv, A. Eddystone-EID: Secure and Private Infrastructural Protocol for BLE Beacons. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3877–3889. [Google Scholar] [CrossRef]
- Padiya, S.D.; Gulhane, V.S. Extended Eddystone-TLM Frame for Sensor Data Broadcasting in the IoT. Prepr. Res. Sq. 2022. [Google Scholar] [CrossRef]
- Gautam, S.; Kumar, S. Analysis of the Maximum Achievable Throughput of Extended Advertisements in BLE. IEEE Internet Things J. 2025, 12, 22168–22186. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Froiz-Míguez, I.; Blanco-Novoa, O.; Fraga-Lamas, P. Enabling the Internet of Mobile Crowdsourcing Health Things: A Mobile Fog Computing, Blockchain and IoT Based Continuous Glucose Monitoring System for Diabetes Mellitus Research and Care. Sensors 2019, 19, 3319. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Rosado da Cruz, A.M.; Lopes, S.I. An Overview of Blockchain for Industry 5.0: Towards Human-Centric, Sustainable and Resilient Applications. IEEE Access 2024, 12, 116162–116201. [Google Scholar] [CrossRef]
- Badihi, B.; Sheikh, M.U.; Ruttik, K.; Jäntti, R. On Performance Evaluation of BLE 5 In Indoor Environment: An Experimental Study. In Proceedings of the 2020 IEEE 31st Annual International Symposium on Personal, Indoor and Mobile Radio Communications, London, UK, 31 August–3 September 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Castillo-Cara, M.; Lovón-Melgarejo, J.; Bravo-Rocca, G.; Orozco-Barbosa, L.; García-Varea, I. An Empirical Study of the Transmission Power Setting for Bluetooth-Based Indoor Localization Mechanisms. Sensors 2017, 17, 1318. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Celaya-Echarri, M.; Lopez-Iturri, P.; Castedo, L.; Azpilicueta, L.; Aguirre, E.; Suárez-Albela, M.; Falcone, F.; Fernández-Caramés, T.M. Design and Experimental Validation of a LoRaWAN Fog Computing Based Architecture for IoT Enabled Smart Campus Applications. Sensors 2019, 19, 3287. [Google Scholar] [CrossRef] [PubMed]
- Akinbolati, A.; Abe, B.T. Investigating the Reliability of Empirical Path Loss Models over Digital Terrestrial UHF Channels in Ikorodu and Akure, Southwestern Nigeria. Telecom 2025, 6, 28. [Google Scholar] [CrossRef]



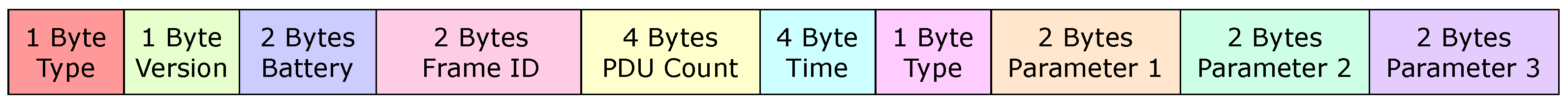





| Technology | Typical Range | Features | Popular Applications |
|---|---|---|---|
| Bluetooth 5.0 [13,14] | 50 m | Low power | Peripherals, wearables, IIoT |
| Wi-Fi HaLow [15] | 50 m | QoS Levels | Smart agriculture, smart cities |
| Thread/Openthread [16,17,18] | 10–30 m | Mesh networking | Home automation, IIoT |
| IQRF [19,20] | 500 m | Reliability, simplicity | Telemetry, smart cities |
| LTE (2G/3G/4G/5G) [21] | 10 km | Wide infrastructure | Mobile communications |
| NB-IoT [22] | 1–10 km | Deep indoor penetration | smart metering, asset tracking |
| Insteon [23] | A building | Power line communication | Home automation, access control |
| EnOcean [24] | 30–300 m | No battery, interoperability | Building automation |
| X10 [25] | A building | Power line communication | Basic lighting, appliance control |
| Wi-Sun [26,27] | 5 km | Robust, secure | FAN, IoT, Smart cities |
| EC-GSM-IoT [28,29] | 10 km | LTE for IoT | Agriculture and environment |
| RPMA [30,31] | 15–80 km | Capacity, security, battery life | Asset tracking, industrial monitoring |
| NB-Fi (Waviot) [32,33] | 10–15 km | Durability | IIoT, M2M |
| MIOTY [34] | 1.5 km–20 km | Robust, scalable | IIoT, smart cities |
| SAW [35] | 10 m | No battery | Aerospace, healthcare |
| LTE-M (LTE-MTC) [36] | 10 km | LTE infrastructure, lower power | Smart metering |
| Wize [37] | 50 km | Harsh environments | Smart metering and smart city |
| LF RFID [38] | 1–5 cm (<10 cm) | Durability, low cost | Smart Industry, security access |
| HF RFID [38] | 30 cm (<1 m) | Durability, low cost | Smart Industry, asset tracking |
| UHF RFID [38,39] | 10 m | Durability, low cost | Smart Industry, toll roads |
| NFC [40,41] | 4–10 cm (<20 cm) | Low cost, no power | Ticketing, payments |
| BLE [42,43] | <50 m | Low cost | Beaconing, GATT |
| Wi-Fi [44] | <100 m | High-speed, ubiquity | LAN, internet access, broadband |
| Infrared (IrDA) [45] | <1 m | Security, high-speed | Remote control, data transfer |
| UWB [46,47] | <10 m | Low power, high-speed data | Radar, video streaming |
| ZigBee [48,49] | <10 m | Mesh network | Smart Home, Industry |
| DASH7 [50,51] | <5 Km | BLAST network technology | Smart industry, military |
| ANT+ [52] | <10 m | Low power | Health, sport monitoring |
| Z-Wave [53,54] | <30 m | Low cost | Smart Home |
| LoRa [55] | >15 m | Long battery life and range | Smart city, M2M |
| SigFox [56,57] | 3–50 Km | Global cellular | Internet of Things, M2M |
| Device | Distance | Adv. Interval | Obstacle Density | Received Beacons |
|---|---|---|---|---|
| ESP32 +9 dBm | 18.3 m | 200 ms | High | 93.72% |
| ESP32 +9 dBm | 18.3 m | 3000 ms | High | 100% |
| ESP32 +9 dBm | 21 m | 3000 ms | Medium | 95.82% |
| ESP32S3 +21 dBm | 27.8 m | 200 ms | Medium | 78.66% |
| ESP32S3 +9 dBm | 27.8 m | 200 ms | Medium | 46.99% |
| ESP32S3 w/external antenna +21 dBm | 42.4 m | 200 ms | High | 80.66% |
| Device | Distance | Antenna | Adv Interval | Received Beacons |
|---|---|---|---|---|
| ESP32 | 48 m | +9 dBm | 3000 ms | 83.73% |
| ESP32S3 | 61 m | +21 dBm | 200 ms | 39.35% |
| ESP32S3 w/antenna | 61 m | +21 dBm | 200 ms | 99.67% |
| ESP32S3 w/antenna | 100 m | +21 dBm | 200 ms | 89.93% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
García-Rivada, P.; Niebla-Montero, Á.; Fraga-Lamas, P.; Fernández-Caramés, T.M. Bluetooth Protocol for Opportunistic Sensor Data Collection on IoT Telemetry Applications. Electronics 2025, 14, 3281. https://doi.org/10.3390/electronics14163281
García-Rivada P, Niebla-Montero Á, Fraga-Lamas P, Fernández-Caramés TM. Bluetooth Protocol for Opportunistic Sensor Data Collection on IoT Telemetry Applications. Electronics. 2025; 14(16):3281. https://doi.org/10.3390/electronics14163281
Chicago/Turabian StyleGarcía-Rivada, Pablo, Ángel Niebla-Montero, Paula Fraga-Lamas, and Tiago M. Fernández-Caramés. 2025. "Bluetooth Protocol for Opportunistic Sensor Data Collection on IoT Telemetry Applications" Electronics 14, no. 16: 3281. https://doi.org/10.3390/electronics14163281
APA StyleGarcía-Rivada, P., Niebla-Montero, Á., Fraga-Lamas, P., & Fernández-Caramés, T. M. (2025). Bluetooth Protocol for Opportunistic Sensor Data Collection on IoT Telemetry Applications. Electronics, 14(16), 3281. https://doi.org/10.3390/electronics14163281








