A Personal Privacy-Ensured User Authentication Scheme
Abstract
1. Introduction
- Anonymity: The control unit/the third party cannot retrieve who the user is, even after the user is authenticated by it successfully.
- Untraceability: No control unit or attacker can trace specific user by the transmitted authentication data.
- Mutual authentication: Any two communication parties can authenticate each other to ensure that the involved communication parties are legal.
- Security: In order to provide essential security, the proposed scheme must resist common attacks.
2. Application Scenarios of the Proposed Personal Privacy-Ensured User Authentication Scheme
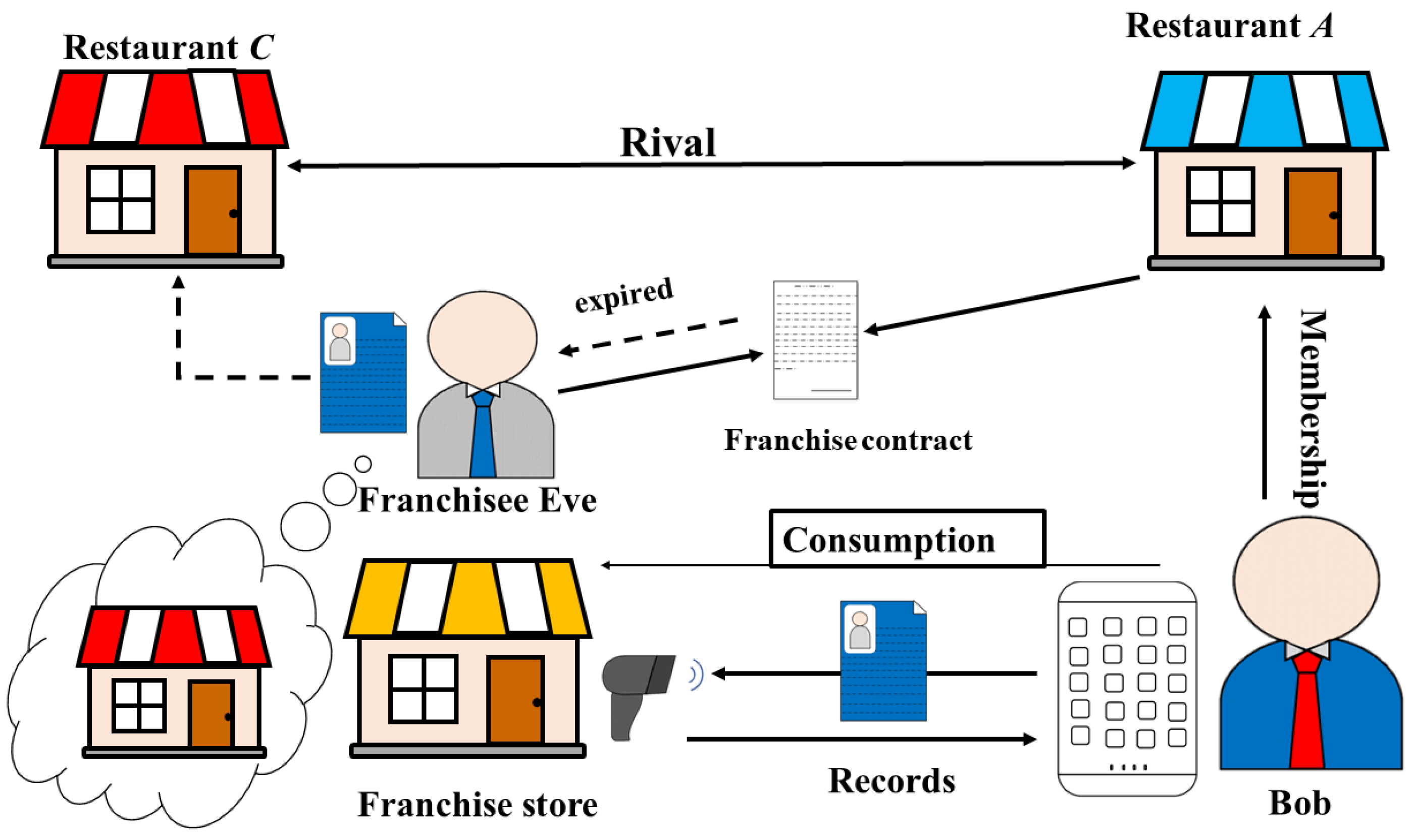
2.1. Scenario 1—Applications for Franchising
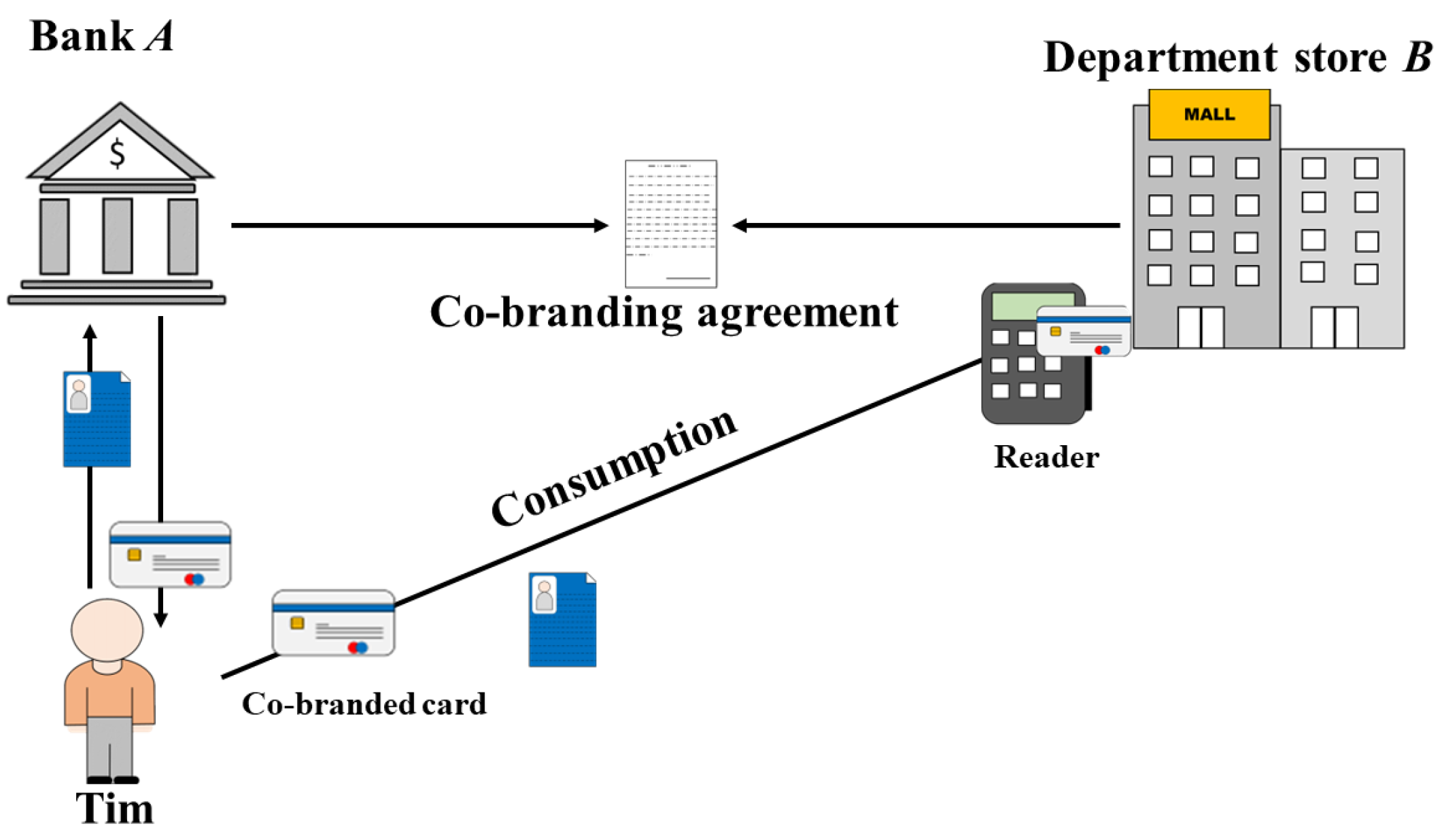
2.2. Scenario 2—Applications for Co-Branding
3. The Proposed User Authentication Scheme Ensuring Personal Privacy
3.1. Initialization Phase
3.1.1. Initialization of the Authentication Unit
- Step 1.
- S first chooses and assigns a unique identification number AIDi to Ai. Then S randomly generates a temporary identification number and sets = .
- Step 2.
- S randomly generates a secret key shared between S and Ai.
- Step 3.
- S stores (AIDi, , , ) in its database for Ai and stores (AIDi, , , ) in Ai’s memory. If Mode 2 is applied to generating NA, S will also store p and g in Ai’s memory; otherwise, if Mode 1 is adopted to generate NA, only (AIDi, , , ) are stored in Ai’s memory.
- Step 4.
- S issues the initialized Ai to Ui securely.
3.1.2. Initialization of the Control Unit
- Step 1.
- S first chooses and assigns a unique identification number RIDj to Rj. Then S randomly generates the secret key shared between S and Rj.
- Step 2.
- S stores (RIDj, ) in its database for Rj and stores (RIDj, ) in Rj’s memory. If Mode 2 is applied to generating NR, S will also store p and g in Rj’s memory; otherwise, if Mode 1 is adopted to generate NR, only (RIDj, ) are stored in Rj’s memory.
3.2. Authentication Phase
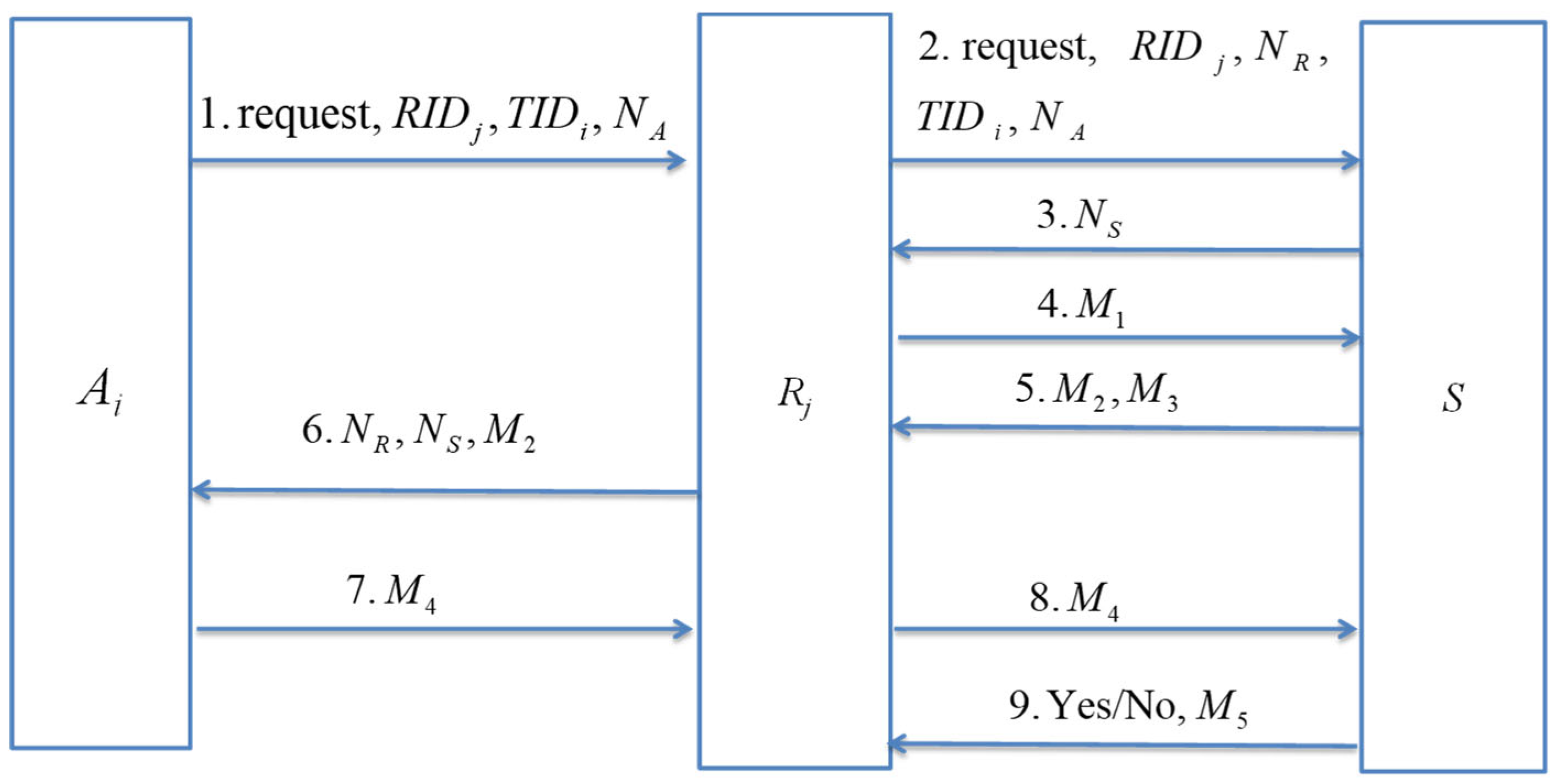
3.2.1. Synchronous Authentication Subphase
- Step 1.
- The authentication unit Ai generates the authentication parameter NA and sends {request, RIDj, , NA} to Rj.
- Step 2.
- When Rj receives {request, RIDj, , NA}, Rj generates the authentication parameter NR and sends {request, RIDj, NR, , NA} to S.
- Step 3.
- When S receives {request, RIDj, NR, , NA}, it generates the authentication parameter NS and sends NS back to Rj
- Step 4.
- When NS is received, Rj computes M1 = H(NA||NR||NS||) and sends M1 to S.
- Step 5.
- After S receives M1, S uses RIDj as the index to get stored in its database to compute H(NA||NR||NS||) and checks whether the computation result is equal to the received M1. If they are not equal, S will determine that Rj is not a legal control unit, and the authentication phase will be terminated immediately; otherwise, S will determine that Rj is legal, and this subphase will proceed. S uses as the index to find the corresponding data in its database. If no matched item is found, synchronous authentication subphase will be terminated immediately, and asynchronous authentication subphase will be performed instead. Otherwise, it denotes that stored in the database of S and that stored in Ai’s memory are consistent, and the last authentication iteration is completely successful. Then S gets (AIDi, , , ) from its database, computes M2 = H(RIDj||AIDi||NA||NR||NS||) and M3 = H(RIDj||M1||) and sends {M2, M3} to Rj.
- Step 6.
- When Rj receives {M2, M3}, Rj computes H(RIDj||M1||) and checks whether the computation result is equal to M3 or not. If they are not equal, Rj determines that S is not legal and terminates the authentication phase; otherwise, Rj sends {NR, NS, M2} to Ai.
- Step 7.
- When Ai receives {NR, NS, M2}, Ai uses its identification number AIDi and secret key to compute H(RIDj||AIDi||NA||NR||NS||) and checks whether the computation result is equal to the received M2. If they are not equal, Ai determines other parties are illegal and terminates the authentication phase immediately; otherwise, Ai determines that S and Rj are legal and computes M4 =H(AIDi ||M2||). and stored in its memory are updated to H(NA||NS||||AIDi) and , respectively. At last, Ai sends {M4} to Rj.
- Step 8.
- Rj forwards {M4} to S.
- Step 9.
- When S receives {M4}, it computes H(AIDi ||M2||) and checks whether the computation result is equal to the received M4. If they are not equal, it denotes that Ai is not authenticated successfully, and S computes M5 = H(“No”||NR||NS||) and sends {No, M5} to Rj; otherwise, it denotes that Ai is authenticated successfully by S, and S computes M5 = H(“Yes”||NR||NS||), sends {Yes, M5} to Rj, and updates and stored in its database to H(NA||NS||||AIDi) and , respectively.
- Step 10.
- When Rj receives the reply, Rj computes H(“No”||NR||NS||) or H(“Yes”||NR||NS||) and compares the computation result with the received M5. If they are equal, it denotes that the response is indeed sent by S, and Rj will provide Ai with the desired service or deny the request.
3.2.2. Asynchronous Authentication Subphase
- Step 1.
- The authentication unit Ai generates the authentication parameter NA and sends {request, RIDj, , NA} to Rj.
- Step 2.
- When Rj receives {request, RIDj, , NA}, Rj generates the authentication parameter NR and sends {request, RIDj, NR, , NA}to S.
- Step 3.
- When S receives {request, RIDj, NR, , NA}, it generates the authentication parameter NS and sends NS back to Rj.
- Step 4.
- When NS is received, Rj computes M1 = H(NA||NR||NS||) and sends M1 to S.
- Step 5.
- After S receives M1, S uses RIDj as the index to get stored in its database to compute H(NA||NR||NS||) and checks whether the computation result is equal to the received M1. If they are not equal, S will determine that Rj is not a legal control unit, and the authentication phase will be terminated immediately; otherwise, S will determine that Rj is legal, and this subphase will proceed. S uses as the index to find the corresponding data in its database. If no matched item is found, S sends a reply to ask Rj to inform Ai that no information related to exists and asks Ai to execute the asynchronous authentication subphase. Otherwise, matched (AIDi, , , ) are found in its database, S computes M2 = H(RIDj||AIDi||NA||NR||NS||) and M3 = H(RIDj||M1||) and sends {M2, M3} to Rj.
- Step 6.
- When Rj receives {M2, M3}, Rj computes H(RIDj||M1||) and checks whether the computation result is equal to M3. If they are not equal, Rj determines that S is not legal and terminates the authentication phase; otherwise, Rj sends {NR, NS, M2} to Ai.
- Step 7.
- When Ai receives {NR, NS, M2}, Ai uses its identification number AIDi and secret key to compute H(RIDj||AIDi||NA||NR||NS||) and checks whether the computation result is equal to the received M2. If they are not equal, Ai determines that other parties are illegal and terminates the authentication phase immediately; otherwise, Ai determines that S and Rj are legal and computes M4 = H(AIDi||M2||). stored in its memory is updated to H(NA||NS||||AIDi). At last, Ai sends {M4} to Rj. Note that stored in Ai’s memory does not need to be updated in the asynchronous authentication subphase.
- Step 8.
- Rj forwards {M4} to S.
- Step 9.
- When S receives {M4}, it computes H(AIDi||M2||) and checks whether the computation result is equal to the received M4. If they are not equal, it denotes that Ai is not authenticated successfully, and S computes M5 = H(“No”||NR||NS||) and sends {No, M5} to Rj; otherwise, it denotes that Ai is authenticated successfully by S, and S computes M5 = H(“Yes”||NR||NS||), sends {Yes, M5} to Rj, and updates and stored in its database to H(NA||NS||||AIDi) and , respectively. Note that stored in Ai’s memory after updating, stored in the database of S before updating, and sent with the authentication request are the same.
- Step 10.
- When Rj receives the reply, Rj computes H(“No”||NR||NS||) or H(“Yes”||NR||NS||) and compares the computation result with the received M5. If they are equal, it denotes that the response is indeed sent by S, and Rj will provide Ai with the desired service or deny the request.
4. Property Analysis
4.1. Anonymity
4.2. Untraceability
4.3. Mutual Authentication
4.4. Security
4.4.1. Resistance to Desynchronization Attack
4.4.2. Resistance to Replay Attack
4.4.3. Resistance to Impersonation Attack
4.4.4. Resistance to Offline Secret Key Guessing Attack
5. Further Discussions
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lamport, L. Password Authentication with Insecure Communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Wang, D.; Ma, C.G. Cryptanalysis of a Remote User Authentication Scheme for Mobile Client–Server Environment Based on ECC. Inf. Fusion 2013, 14, 498–503. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A Novel User Authentication and Key Agreement Scheme for Heterogeneous Ad Hoc Wireless Sensor Networks, Based on the Internet of Things Notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an Anonymity-preserving Three-factor Authenticated Key Exchange Protocol for Wireless Sensor Networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Chen, S.; Yang, L.; Zhao, C.; Varadarajan, V.; Wang, K. Double-blockchain Assisted Secure and Anonymous Data Aggregation for Fog-enabled Smart Grid. Engineering 2022, 8, 159–169. [Google Scholar] [CrossRef]
- Wu, Y.; Feng, T.; Su, C.; Liu, C. MSAUPL: A Multi-Server Authentication and Key Agreement Protocol for Industrial IoT Based on User Privacy Level. J. Inf. Secur. Appl. 2025, 89, 103991. [Google Scholar] [CrossRef]
- Mehta, P.J.; Parne, B.L.; Patel, S.J. P3AKA: A PUF Based Privacy Preserving Authentication and Key Agreement Framework for Secure Communication in Vehicle to Grid Network. Veh. Commun. 2025, 54, 100925. [Google Scholar] [CrossRef]
- Ibrahim, S.J.; Beitollahi, H. PPA6-IoV: A Six-Step Privacy-Preserving Authentication Protocol for the Internet of Vehicles. IEEE Access 2024, 12, 168120–168134. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A Realistic Lightweight Authentication Protocol Preserving Strong Anonymity for Securing RFID System. Comput. Secur. 2015, 55, 271–280. [Google Scholar] [CrossRef]
- Erguler, I. A Potential Weakness in RFID-based Internet-of-things Systems. Pervasive Mob. Comput. 2015, 20, 115–126. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An Efficient User Authentication and Key Agreement Scheme for Heterogeneous Wireless Sensor Network Tailored for the Internet of Things Environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.K.R. A Three-factor Anonymous Authentication Scheme for Wireless Sensor Networks in Internet of Things Environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Lo, N.W.; Tsai, J.L. An Efficient Conditional Privacy-Preserving Authentication Scheme for Vehicular Sensor Networks Without Pairings. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1319–1328. [Google Scholar] [CrossRef]
- Zeng, S.; Zhang, H.; Hao, F.; Li, H. Deniable-Based Privacy-Preserving Authentication Against Location Leakage in Edge Computing. IEEE Syst. J. 2022, 16, 1729–1738. [Google Scholar] [CrossRef]
- Chang, Y.F.; Tai, W.L.; Hou, P.L.; Lai, K.Y. A Secure Three-Factor Anonymous User Authentication Scheme for Internet of Things Environments. Symmetry 2021, 13, 1121. [Google Scholar] [CrossRef]
- Shamshad, S.; Rana, M.; Mahmood, K.; Khan, M.K.; Obaidat, M.S. On the Security of A Secure Anonymous Identity-Based Scheme in New Authentication Architecture for Mobile Edge Computing. Wirel. Pers. Commun. 2022, 124, 283–292. [Google Scholar] [CrossRef]
- Chang, Y.F.; Tai, W.L.; Fung, K.H. Offline User Authentication Ensuring Non-repudiation and Anonymity. Sensors 2022, 22, 9673. [Google Scholar] [CrossRef]
- Chang, Y.F.; Tai, W.L.; Lin, C.H. A Feasible Solution for eHealth with an Anonymous Patient Monitoring System and a Privacy-ensured Telecare Medical Information System. J. Inf. Sci. Eng. 2024, 40, 1211–1226. [Google Scholar]
- Huang, Y.; Xu, G.; Wang, Q.; Song, X.; Wang, X. Efficient and Privacy-Preserving Authentication for Federated Learning in Industrial Internet of Things Data Sharing Application. IEEE Internet Things J. 2025, 12, 11652–11663. [Google Scholar] [CrossRef]
- Liu, P.; He, Q.; Chen, Y.; Jiang, S.; Zhao, B.; Wang, X. A Lightweight Authentication and Privacy-Preserving Aggregation for Blockchain-Enabled Federated Learning in VANETs. IEEE Trans. Consum. Electron. 2025, 71, 1274–1287. [Google Scholar] [CrossRef]
- Seifelnasr, M.; AlTawy, R.; Youssef, A. A Conditional Privacy-Preserving Protocol for Cross-Domain Communications in VANET. IEEE Trans. Intell. Transp. Syst. 2025, 26, 5251–5263. [Google Scholar] [CrossRef]
- Yu, L.; Wu, W.; Mei, L. A Lightweight Cross-Layer Mutual Authentication With Key Agreement Protocol for IIoT. IEEE Internet Things J. 2025, 12, 7051–7066. [Google Scholar] [CrossRef]
| Notations | Definitions |
|---|---|
| S | backend server |
| Ui | i-th user |
| Ai | Ui’s authentication unit |
| Rj | j-th control unit |
| AIDi | permanent identification number of Ai |
| temporary identification number of the last successful authentication iteration of Ai | |
| temporary identification number for the next authentication iteration of Ai | |
| TIDi | transmitted in synchronous/asynchronous authentication subphase |
| RIDj | identification number of Rj |
| secret key shared between S and Rj | |
| secret key shared between S and Ai | |
| P | large prime number |
| g | primitive root modulo p |
| NA | random number generated by Ai in the authentication phase |
| NR | random number generated by Rj in the authentication phase |
| NS | random number generated by S in the authentication phase |
| H(.) | one-way hash function |
| || | connection operator |
| Input (bits) | SHA-256 (μs) | SHA-512 (μs) | SHA3-256 (μs) | SHA3-512 (μs) |
|---|---|---|---|---|
| 1024 | 1.33 | 1.61 | 1.35 | 1.38 |
| 2048 | 1.51 | 1.62 | 1.37 | 1.96 |
| 4096 | 1.86 | 1.98 | 2.24 | 3.54 |
| 5120 | 2.10 | 1.90 | 2.67 | 4.23 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chang, Y.-F.; Tai, W.-L.; Chang, T.-Y. A Personal Privacy-Ensured User Authentication Scheme. Electronics 2025, 14, 3072. https://doi.org/10.3390/electronics14153072
Chang Y-F, Tai W-L, Chang T-Y. A Personal Privacy-Ensured User Authentication Scheme. Electronics. 2025; 14(15):3072. https://doi.org/10.3390/electronics14153072
Chicago/Turabian StyleChang, Ya-Fen, Wei-Liang Tai, and Ting-Yu Chang. 2025. "A Personal Privacy-Ensured User Authentication Scheme" Electronics 14, no. 15: 3072. https://doi.org/10.3390/electronics14153072
APA StyleChang, Y.-F., Tai, W.-L., & Chang, T.-Y. (2025). A Personal Privacy-Ensured User Authentication Scheme. Electronics, 14(15), 3072. https://doi.org/10.3390/electronics14153072





