ScaL2Chain: Towards a Scalable Protocol for Multi-Chain Decentralized Applications
Abstract
1. Introduction
- 1.
- High Performance: Transaction processing should demonstrate high throughput and low latency.
- 2.
- High Confidentiality: Detailed information regarding transactions between DApps should remain confidential.
- 3.
- High Reliability: Each DApp interaction must guarantee that transactions are processed correctly and in the intended order.
- 1.
- We propose ScaL2Chain, a novel scalable protocol designed to facilitate efficient state sharing and interaction among multi-chain DApps. ScaL2Chain can execute cross-chain transfers conditionally, efficiently, securely, and trustlessly, thereby addressing the performance bottlenecks of existing multi-chain DApp solutions.
- 2.
- We design the cross-chain transaction processing flow of the transmission integration constraint synergy (TICS) workflow to ensure efficient and trustless transaction execution in a multi-chain environment. This process optimizes the state update mechanism, safeguarding both transaction confidentiality and execution correctness, thereby effectively preventing potential malicious activities.
- 3.
- We conduct extensive experiments to evaluate the performance of ScaL2Chain. Our evaluation compares ScaL2Chain against three baseline systems across key parameters including the DApp count (4-64), cross-application transaction ratio (0–100%), and node failure rate (0–30%). The results indicate that ScaL2Chain’s throughput in a non-task environment improves by 7.9 to 8.4 times compared to baseline schemes, while, in permissioned environments, it increases by 1.9 to 35.8 times.
2. Background
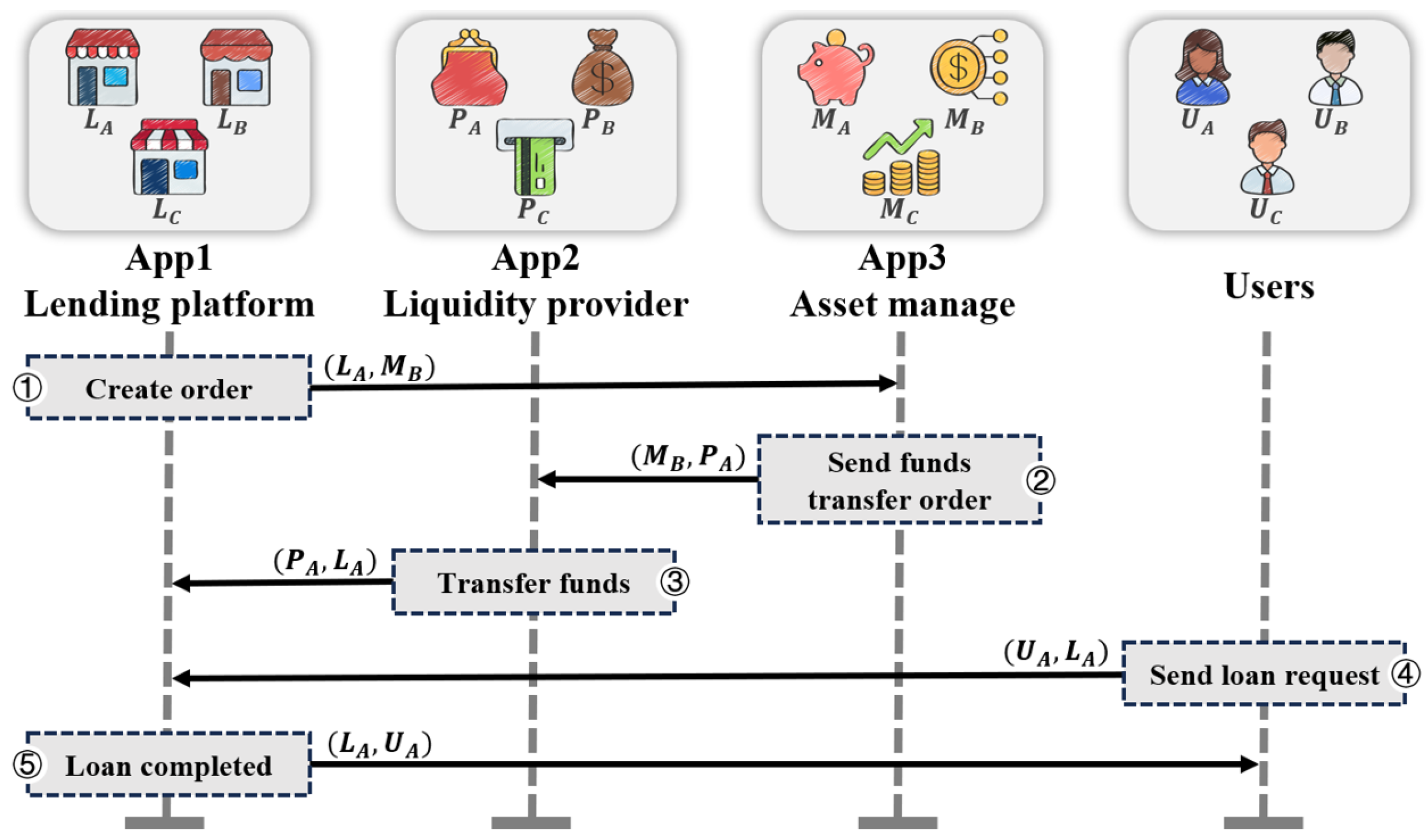
2.1. Motivation Example
2.2. Payment Channel Layer-2 Blockchain Scaling
3. Related Works
3.1. Scalability of Decentralized Applications
- Advanced BFT engines. Permissioned ledgers such as Hyperledger Fabric [30] and Quorum [31] use crash-fault or Byzantine fault tolerance (BFT) mechanisms instead of PoW. These systems implement protocols like Raft [32], PBFT [33], and IBFT [29], achieving several hundred transactions per second (TPS). However, each replica re-executes every transaction, and global ordering becomes a bottleneck with multiple DApps on the same chain. Research has streamlined Byzantine consensus: Tendermint [34], HotStuff [35], and SBFT [36] reduce message rounds or achieve linear commits, but the throughput is still limited because each validator duplicates state storage and execution. Hybrids on Steroids [37] encapsulates consensus logic within Intel software guard extensions (SGX) to reduce the latency while maintaining deterministic replay requirements.
- Sharding and cross-application architectures. OmniLedger-style shards [38] partition states horizontally to increase the aggregate TPS, but cross-shard transactions require two-phase protocols and still serialize through shard roots, creating bottlenecks. CAPER [39] and MultiChain [40] enable each DApp to operate its own consensus while a higher-level protocol manages inter-application transfers, adding complexity and latency. SlimChain [41] separates execution from ordering by maintaining only digests on-chain, but its single Merkle accumulator becomes a contention point when multiple proposers attempt concurrent updates.
3.2. Scalable Blockchain Protocol
- Payment and state channel networks. The Lightning Network [13] and its duplex extension [22], along with the Raiden Network for ERC-20 tokens [42], allows participants to exchange signed updates off-chain, settling only opening and closing states on Layer 1. These networks provide sub-second latency and low fees but have limited transaction logic and require participants to stay online throughout the routing process.
- Commit-chain architectures. Commit chains evolve architectures through Khalil et al.’s model [43], placing an untrusted operator between users and Layer 1. This operator periodically submits the Merkle roots of the off-chain ledger to Layer 1, allowing users to submit fraud proofs when necessary. This design removes the “always online” requirement of payment channels, but it exposes transaction contents to the operator, raising privacy concerns.
- Rollup systems. Rollups are an advanced Layer-2 paradigm with two main types. Optimistic rollups batch transactions and rely on fraud-proof challenge windows, causing finality delays of minutes to days. Notable examples include the Plasma [44] and Optimistic rollup prototypes [45]. Zero-knowledge rollups (ZK-rollups) use succinct ZKPs instead of fraud proofs; zkSync [46] and similar designs [21] achieve faster finality but incur high computational costs for proof generation. Both approaches use a single global Merkle root, which can create contention when multiple DApps operate.
- TEE-assisted Layer 2. Some systems combine Layer-2 processing with trusted execution environments (TEEs). Teechain [47] shows how TEEs can secure multi-hop payment channels, while Hybrids on Steroids [37] uses SGX to speed up BFT consensus. SlimChain [41] executes contracts within SGX proposers while using stateless Layer-1 validators. These methods offer advantages but may expose plaintext transactions or still serialize state updates through a single root hash, limiting scalability in concurrent applications.
3.3. Multi-Chain Constructions
- Sidechain implementations. Sidechains expand blockchain ecosystems by running parallel chains with bidirectional asset transfer. Liquid [48] is an early Bitcoin sidechain using federated consensus for confidential transactions and fast settlement. Polygon [49] operates a proof of stake (PoS) sidechain for Ethereum, processing EVM-compatible transactions at higher throughput while committing checkpoints to the main network. Gnosis Chain [50] shows how application-specific sidechains can be optimized for certain use cases while inheriting security from the parent chain. Avalanche’s subnet architecture [51] allows customizable sidechains with independent validators. While sidechains enhance throughput, they generally involve security trade-offs as they have fewer validators, raising centralization risks [52].
- Multi-chain network protocols. Multi-chain network protocols create interoperability frameworks for independent blockchains. Cosmos pioneered this with the inter-blockchain communication (IBC) protocol [53], enabling trustless state transfers through standardized messaging and light client verification. Polkadot [54] uses a shared security model where parachains inherit security from a common validator set. Its cross-consensus message (XCM) format [55] standardizes cross-chain communication. Innovations like Chainlink’s cross-chain interoperability protocol (CCIP) [56] and LayerZero [57] enhance trustless communication. These protocols advance an interconnected ecosystem that maintains the unique advantages of individual chains while facilitating seamless cross-chain interactions [11].
4. ScaL2Chain Overview
4.1. Design Goals and Challenges
4.1.1. Scalable Cross-Chain DApp Transaction Protocol
- Design objectives. (1) Achieve scalability through constant computational and storage complexity. (2) Enable cross-chain operations independent of source chain consensus mechanisms. (3) Minimize data storage and relay requirements. (4) Support deployment on blockchain platforms with signature verification capabilities.
- Technical challenges. (1) Different blockchain ecosystems implement various rules and consensus mechanisms. It is essential to develop an innovative cross-chain state transition verification mechanism to ensure the accuracy and consistency of transactions without relying on the consensus of the source chain. (2) There are inherent differences in transaction loads and architectures among different blockchains. Therefore, it is necessary to construct an efficient computational model to reduce the time and space complexity of cross-chain operations. (3) Finding the right balance between the data required for efficiency and security is crucial. We must design a lightweight transaction relay and storage solution to transmit only the minimal necessary cross-chain data. (4) The diverse architectures and consensus algorithms adopted by different blockchains complicate the creation of standardized protocols. (5) Some challenges may be encountered during actual deployment. In interactive verification schemes, all ScaL2Chain states must maintain eventual consistency. The key to achieving this consistency lies in efficiently and securely transmitting and verifying messages to avoid potential security risks. Therefore, a universal cross-chain DApp transaction protocol that is compatible with blockchain platforms supporting basic signature verification is needed.
4.1.2. Secure and Low-Cost Cross-Chain Transaction Verification
- Design objectives. (1) Conduct comprehensive security analysis within the universal composability framework. (2) Implement robust penalty mechanisms to deter malicious behavior. (3) Control transaction costs within twice the standard Ethereum transaction fee. (4) Ensure near-instant transaction finality.
- Technical challenges. (1) In a distributed environment, a range of potential adversarial behaviors and attack vectors exist. Thus, we need to employ methods from the Byzantine adversary model to formally prove the security of the protocol. (2) In a competitive landscape, understanding participants’ motivations and designing effective mechanisms to encourage cooperation are essential in mitigating the risks associated with exploitation and dishonest behavior. We must create multi-layered economic incentive mechanisms to guide participants toward honest behavior. (3) Simplifying the verification process often introduces security vulnerabilities, while overly complex processes may impede scalability and responsiveness. We must optimize the verification process to reduce the computational complexity while maintaining security integrity. (4) Nodes exhibit geographic dispersion and experience inherent communication latency across different networks. Therefore, achieving near-instant finality while minimizing the impact of network latency is essential.
4.2. Current Limitations
4.2.1. Computational and Storage Complexity
4.2.2. Security and Interoperability
4.3. System Overview
4.3.1. ScaL2Chain Protocol
4.3.2. Decentralized Application
4.3.3. Smart Contract
5. Protocol Design
5.1. Naive Construction Workflow
- Channel funding transaction ;
- Proof submission timeout threshold ;
- Dispute resolution timeout threshold ;
- Closure timeout threshold for scenarios with neither proof submission nor dispute initiated;
- Mapping function f transforming DApp token allocation to smart contract balance distribution.
- Submitting an outdated DApp update that predates the establishment of the ScaL2Chain smart contract;
- Submitting commitment transactions representing disparate DApp update stages, such as and , corresponding to the i-th and -th channel updates, respectively.
5.2. TICS Workflow
5.2.1. Transmission
5.2.2. Integration
5.2.3. Constraint
- Participants exchange new revocation secrets;
- Exchange signed locked commitment transactions ;
- Exchange old revocation secrets;
- When participants reach the expected update , exchange signed unlocked commitment transactions .
5.2.4. Synergy
5.3. Adaptability Discussion
5.3.1. Consensus
5.3.2. Resource-Constrained Small Blockchain
6. Security in the UC Framework
6.1. Security Model
6.2. Ideal Function
6.3. Security Analysis
7. Experimental Study
7.1. Experimental Settings
7.1.1. Key Parameters
- DApp Workload Design. Each DApp employs the KVStore smart contract from the BLOCKBENCH [7] macro-benchmark suite, which executes read and write operations on key–value pairs. The experiments use YCSB workloads [66] in three configurations: mixed mode (50% reads, 50% writes), read-only mode, and write-only mode. To simulate cross-application transactions, state addresses are evenly distributed among DApps, and transactions are constructed by randomly combining two read/write operations. These transactions may execute within a single DApp or span two DApps.
- Node Configuration Scheme. System nodes are allocated based on the total number of DApps, with each DApp configured with four nodes. Each DApp connects to a single client that submits the workload. To evaluate ScaL2Chain’s fault tolerance against pure L1 solutions, we introduce temporary failures at each block interval, where nodes in ScaL2Chain fail with probability .
- Other Parameters. Following prior work [67], the block generation frequency does not affect the throughput but increases the latency when reduced. We therefore adopt standard settings: 1-second intervals for Raft and 10-second intervals for PoW. For the block capacity and ScaL2Chain batch size, larger values increase both the throughput and latency. We set both parameters to 256 transactions, approximating Ethereum’s average block size. Based on Ethereum’s address statistics, we configure the global state size to entries, shared across all DApps.
7.1.2. Baseline Systems, Metrics, and Experimental Environment
7.2. Experimental Results
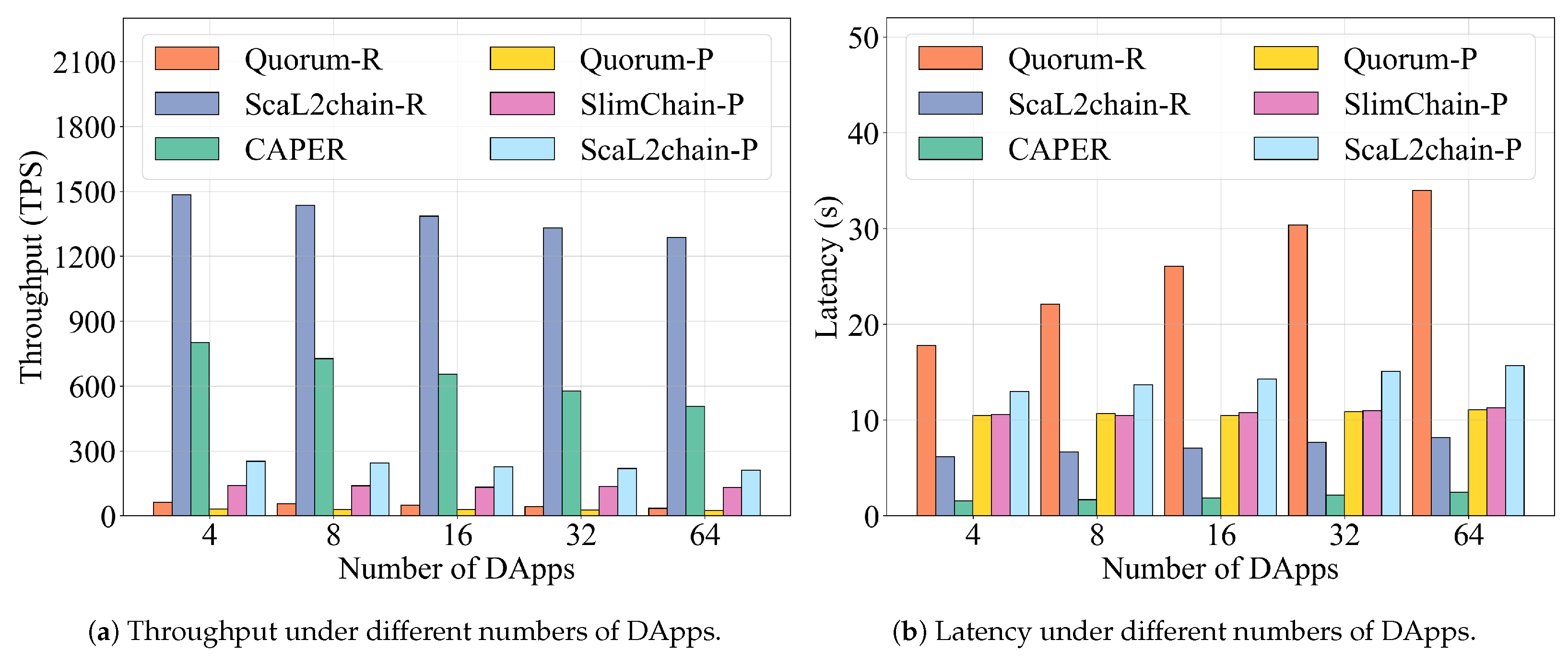
- Analysis of Impact of DApp Scale on System Performance. The experimental data in Figure 7 indicate that, as the number of DApps increases, the throughput of all permissioned blockchain systems exhibits a downward trend. Performance comparisons reveal that ScaL2Chain demonstrates significant scalability advantages: its throughput lead over Raft Quorum increases from 23.6 times to 35.8 times, while its advantage over CAPER grows from 1.9 times to 2.5 times. Regarding latency performance, the latency reduction of ScaL2Chain relative to Raft Quorum improves from 65.2% to 75.9%. ScaL2Chain employs a Layer-2 architecture and a four-stage TICS workflow to handle cross-chain interactions, whereas CAPER processes only intra-chain cross-application communications through a directed acyclic graph structure. Consequently, ScaL2Chain incurs a higher latency overhead than CAPER. However, as the number of DApps increases, ScaL2Chain’s latency multiple relative to CAPER decreases from 3.9 times to 3.3 times. These metrics robustly demonstrate the exceptional scalability of ScaL2Chain in permissioned networks. However, in comparisons with the performance of Quorum-P and SlimChain-P, the improvement of ScaL2Chain remains relatively constant, with performance advantages maintained between 7.9 and 8.4 times and 1.6 and 1.8 times, respectively. This phenomenon arises because the PoW consensus protocol in the L1 chain becomes the primary performance bottleneck, and its processing efficiency is unaffected by variations in the number of DApps.
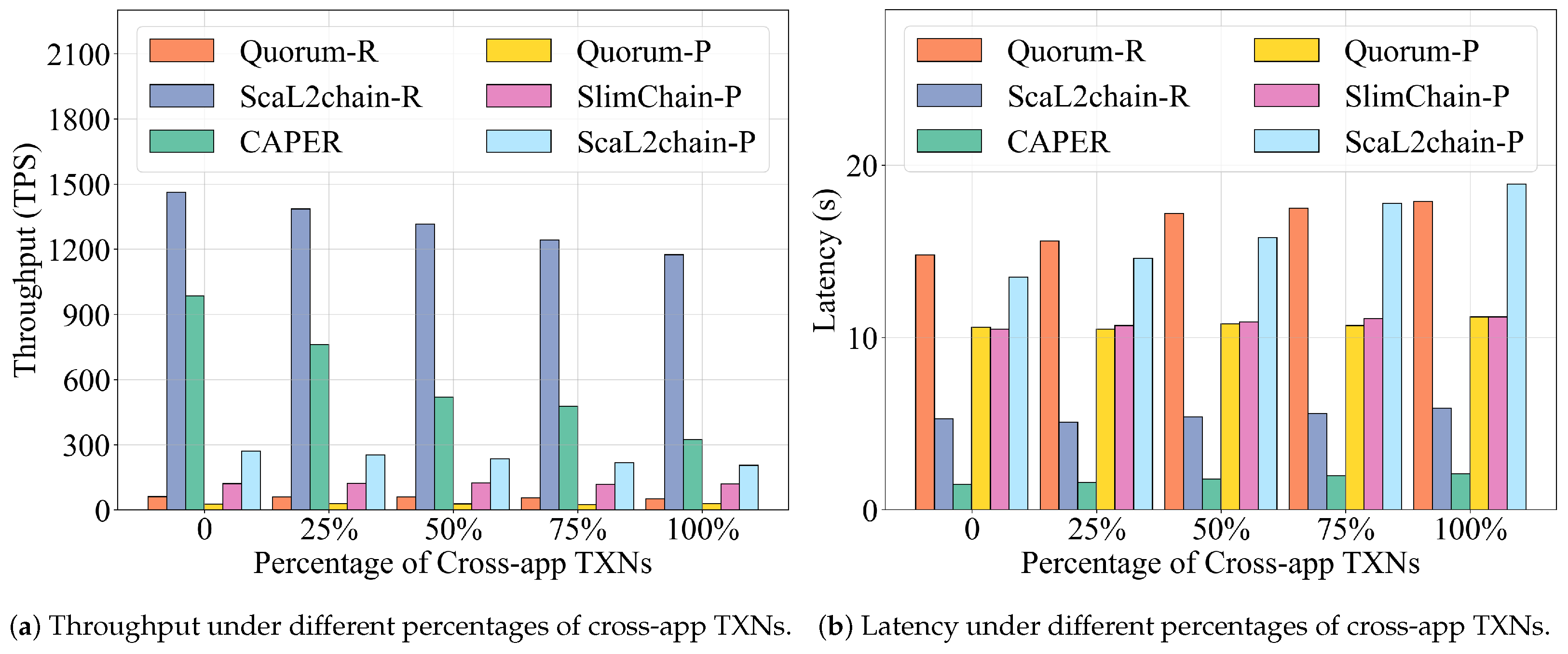
- Impact of Cross-Application Transaction Ratio on System Performance Constraints. Figure 8 shows that as the ratio of cross-application transactions increases from 0% to 100%, both CAPER and ScaL2Chain-R experience a decline in throughput and an increase in latency due to the need to execute Raft local consensus among DApps. Specifically, the processing capacity of ScaL2Chain-R drops from 1462 TPS to 1176 TPS, while that of CAPER decreases from 986 TPS to 324 TPS. ScaL2Chain-R employs a batching strategy that requires only two global consensus rounds. Consequently, its throughput advantage over CAPER amplifies as the cross-application transaction ratio increases, rising from an initial 1.5 times to 3.6 times. In terms of latency, the latency overhead multiple of ScaL2Chain-R compared to CAPER decreases from 3.5 times to 2.8 times, indicating that the batching strategy effectively mitigates delays caused by local consensus in high cross-application transaction scenarios.
- Regulation Effect of Read/Write Operation Ratio on System Performance. The experiments adjusting the read/write operation ratio of workloads, shown in Figure 9, indicate that, under purely read load conditions, all systems can achieve outstanding throughput values exceeding 13,000 TPS, primarily due to the absence of a consensus protocol overhead in read operations. However, as the ratio of write operations increases, the processing performance of all systems shows a downward trend. From the perspective of latency, the consensus overhead of ScaL2Chain is comparable to that of CAPER, PoW Quorum, and SlimChain.
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Shamir, A. On the generation of cryptographically strong pseudorandom sequences. ACM Trans. Comput. Syst. (TOCS) 1983, 1, 38–44. [Google Scholar] [CrossRef]
- Dziembowski, S.; Eckey, L.; Faust, S.; Malinowski, D. Perun: Virtual payment hubs over cryptocurrencies. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 106–123. [Google Scholar]
- Ozdemir, A.; Wahby, R.; Whitehat, B.; Boneh, D. Scaling verifiable computation using efficient set accumulators. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Berkeley, CA, USA, 12–14 August 2020; pp. 2075–2092. [Google Scholar]
- Garay, J.; Kiayias, A.; Leonardos, N. The bitcoin backbone protocol: Analysis and applications. J. ACM 2024, 71, 1–49. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/en/bitcoin-paper (accessed on 17 March 2025).
- Dinh, T.T.A.; Wang, J.; Chen, G.; Liu, R.; Ooi, B.C.; Tan, K.L. Blockbench: A framework for analyzing private blockchains. In Proceedings of the 2017 ACM International Conference on Management of Data, Chicago, IL, USA, 14–19 May 2017; pp. 1085–1100. [Google Scholar]
- Ren, K.; Ho, N.M.; Loghin, D.; Nguyen, T.T.; Ooi, B.C.; Ta, Q.T.; Zhu, F. Interoperability in blockchain: A survey. IEEE Trans. Knowl. Data Eng. 2023, 35, 12750–12769. [Google Scholar] [CrossRef]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–2. [Google Scholar]
- Kwon, J.; Buchman, E. Cosmos whitepaper. Netw. Distrib. Ledgers 2019, 27, 1–32. [Google Scholar]
- Belchior, R.; Vasconcelos, A.; Guerreiro, S.; Correia, M. A survey on blockchain interoperability: Past, present, and future trends. ACM Comput. Surv. (CSUR) 2021, 54, 1–41. [Google Scholar] [CrossRef]
- Ou, W.; Huang, S.; Zheng, J.; Zhang, Q.; Zeng, G.; Han, W. An overview on cross-chain: Mechanism, platforms, challenges and advances. Comput. Netw. 2022, 218, 109378. [Google Scholar] [CrossRef]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments; Satoshi Nakamoto Institute: Seattle, WA, USA, 2016. [Google Scholar]
- El-Hindi, M.; Binnig, C.; Arasu, A.; Kossmann, D.; Ramamurthy, R. BlockchainDB: A shared database on blockchains. Proc. Vldb Endow. 2019, 12, 1597–1609. [Google Scholar] [CrossRef]
- Pan, Z.; Ying, Z.; Wang, Y.; Zhang, C.; Zhang, W.; Zhou, W.; Zhu, L. Feature-Based Machine Unlearning for Vertical Federated Learning in IoT Networks. IEEE Trans. Mob. Comput. 2025, 24, 5031–5044. [Google Scholar] [CrossRef]
- Pan, Z.; Hu, L.; Tang, W.; Li, J.; He, Y.; Liu, Z. Privacy-preserving multi-granular federated neural architecture search–a general framework. IEEE Trans. Knowl. Data Eng. 2021, 35, 2975–2986. [Google Scholar] [CrossRef]
- Gudgeon, L.; Moreno-Sanchez, P.; Roos, S.; McCorry, P.; Gervais, A. Sok: Layer-two blockchain protocols. In Proceedings of the Financial Cryptography and Data Security: 24th International Conference, FC 2020, Kota Kinabalu, Malaysia, 10–14 February 2020; Revised Selected Papers 24. Springer: Berlin/Heidelberg, Germany, 2020; pp. 201–226. [Google Scholar]
- Herlihy, M. Atomic cross-chain swaps. In Proceedings of the 2018 ACM Symposium on Principles of Distributed Computing, Egham, UK, 23–27 July 2018; pp. 245–254. [Google Scholar]
- Herlihy, M.; Liskov, B.; Shrira, L. Cross-chain deals and adversarial commerce. arXiv 2019, arXiv:1905.09743. [Google Scholar] [CrossRef]
- Buterin, V. On-Chain Scaling to Potentially 500 tx/sec Through Mass tx Validation. Ethereum Blog. 2018. Available online: https://ethresear.ch/t/on-chain-scaling-to-potentially-500-tx-sec-through-mass-tx-validation/3477 (accessed on 12 March 2025).
- Gluchowski, A. Zero-Knowledge Rollups. Matter Labs. 2019. Available online: https://ethereum.org/en/developers/docs/scaling/zk-rollups/ (accessed on 18 March 2025).
- Decker, C.; Wattenhofer, R. A fast and scalable payment network with bitcoin duplex micropayment channels. In Proceedings of the Stabilization, Safety, and Security of Distributed Systems: 17th International Symposium, SSS 2015, Edmonton, AB, Canada, 18–21 August 2015; Proceedings 17. Springer: Berlin/Heidelberg, Germany, 2015; pp. 3–18. [Google Scholar]
- Yin, Z.; Zhang, B.; Xu, J.; Lu, K.; Ren, K. Bool network: An open, distributed, secure cross-chain notary platform. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3465–3478. [Google Scholar] [CrossRef]
- Scaffino, G.; Aumayr, L.; Avarikioti, Z.; Maffei, M. Glimpse:{On-Demand}{PoW} Light Client with {Constant-Size} Storage for {DeFi}. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 733–750. [Google Scholar]
- Deng, Z.; Li, T.; Tang, C.; He, D.; Zheng, Z. PSSC: Practical and Secure Sidechain Construction for Heterogeneous Blockchains Orienting IoT. IEEE Internet Things J. 2023, 11, 4600–4613. [Google Scholar] [CrossRef]
- Nußbaum, A.; Schütte, J.; Hao, L.; Schulzrinne, H.; Alt, F. Tremble: Transparent emission monitoring with blockchain endorsement. In Proceedings of the 2021 IEEE International Conferences on Internet of Things (iThings) and IEEE Green Computing & Communications (GreenCom) and IEEE Cyber, Physical & Social Computing (CPSCom) and IEEE Smart Data (SmartData) and IEEE Congress on Cybermatics (Cybermatics), Melbourne, Australia, 6–8 December 2021; pp. 59–64. [Google Scholar]
- Thyagarajan, S.A.; Malavolta, G.; Moreno-Sanchez, P. Universal atomic swaps: Secure exchange of coins across all blockchains. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–26 May 2022; pp. 1299–1316. [Google Scholar]
- Westerkamp, M.; Diez, M. Verilay: A verifiable proof of stake chain relay. In Proceedings of the 2022 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Shanghai, China, 2–5 May 2022; pp. 1–9. [Google Scholar]
- Istanbul BFT. 2018. Available online: https://github.com/ethereum/EIPs/issues/650 (accessed on 17 March 2025).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Chase, J.P.M. Quorum: A Permissioned Implementation of Ethereum. 2018. Available online: https://github.com/jpmorganchase/quorum (accessed on 12 March 2025).
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the 2014 USENIX Annual Technical Conference (USENIX ATC 14), Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. In Proceedings of the OSDI ’99: Third Symposium on Operating Systems Design and Implementation, New Orleans, LA, USA, 22 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Buchman, E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains. Ph.D. Thesis, University of Guelph, Guelph, ON, Canada, 2016. [Google Scholar]
- Yin, M.; Malkhi, D.; Reiter, M.K.; Gueta, G.G.; Abraham, I. HotStuff: BFT consensus in the lens of blockchain. arXiv 2018, arXiv:1803.05069. [Google Scholar]
- Gueta, G.G.; Abraham, I.; Grossman, S.; Malkhi, D.; Pinkas, B.; Reiter, M.; Seredinschi, D.A.; Tamir, O.; Tomescu, A. SBFT: A scalable and decentralized trust infrastructure. In Proceedings of the 2019 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Portland, OR, USA, 24–27 June 2019; pp. 568–580. [Google Scholar]
- Behl, J.; Distler, T.; Kapitza, R. Hybrids on steroids: SGX-based high performance BFT. In Proceedings of the Twelfth European Conference on Computer Systems, Belgrade, Serbia, 23–26 April 2017; pp. 222–237. [Google Scholar]
- Dang, H.; Dinh, T.T.A.; Loghin, D.; Chang, E.C.; Lin, Q.; Ooi, B.C. Towards scaling blockchain systems via sharding. In Proceedings of the 2019 International Conference on Management of Data, Amsterdam, The Netherlands, 30 June–5 July 2019; pp. 123–140. [Google Scholar]
- Amiri, M.J.; Agrawal, D.; Abbadi, A.E. Caper: A cross-application permissioned blockchain. Proc. VLDB Endow. 2019, 12, 1385–1398. [Google Scholar] [CrossRef]
- Greenspan, G. Multichain Private Blockchain-White Paper. 2015, Volume 85. Available online: http://www.multichain.com/download/MultiChain-White-Paper.pdf (accessed on 12 March 2025).
- Xu, C.; Zhang, C.; Xu, J.; Pei, J. SlimChain: Scaling blockchain transactions through off-chain storage and parallel processing. Proc. VLDB Endow. 2021, 14, 2314–2326. [Google Scholar] [CrossRef]
- Network, R. What Is the Raiden Network. 2018. Available online: https://raiden.network/101.html (accessed on 13 March 2025).
- Khalil, R.; Zamyatin, A.; Felley, G.; Moreno-Sanchez, P.; Gervais, A. Commit-Chains: Secure, Scalable Off-Chain Payments. Cryptology ePrint Archive. 2018. Available online: https://eprint.iacr.org/2018/642 (accessed on 16 July 2025).
- Poon, J.; Buterin, V. Plasma: Scalable autonomous smart contracts. White Pap. 2017, 1–47. [Google Scholar]
- Stipsits, M. Scalable Integration of Ethereum in a Microservice Based Application Through Layer 2 Rollups. 2023. Available online: https://pub.fh-campuswien.ac.at/obvfcwhsacc/content/titleinfo/8874847 (accessed on 16 July 2025).
- Matter labs. zkSync: Scaling and Privacy Engine for Ethereum. 2019. Available online: https://docs.zksync.io/ (accessed on 19 March 2025).
- Lind, J.; Naor, O.; Eyal, I.; Kelbert, F.; Sirer, E.G.; Pietzuch, P. Teechain: A secure payment network with asynchronous blockchain access. In Proceedings of the 27th ACM Symposium on Operating Systems Principles, Huntsville, ON, Canada, 27–30 October 2019; pp. 63–79. [Google Scholar]
- Back, A.; Corallo, M.; Dashjr, L.; Friedenbach, M.; Maxwell, G.; Miller, A.; Poelstra, A.; Timón, J.; Wuille, P. Enabling Blockchain Innovations with Pegged Sidechains. 2014, Volume 72, pp. 201–224. Available online: http://www.opensciencereview.com/papers/123/enablingblockchain-innovations-with-pegged-sidechains (accessed on 20 March 2025).
- Bez, M.; Fornari, G.; Vardanega, T. The scalability challenge of ethereum: An initial quantitative analysis. In Proceedings of the 2019 IEEE International Conference on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 4–9 April 2019; pp. 167–176. [Google Scholar]
- Jo, Y.; Park, C. Enhancing ethereum PoA clique network with DAG-based BFT consensus. In Proceedings of the 2024 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Dublin, Ireland, 27–31 May 2024; pp. 655–659. [Google Scholar]
- Cappabianca, F.; Barbolini, M.; Natale, L. Snow avalanche risk assessment and mapping: A new method based on a combination of statistical analysis, avalanche dynamics simulation and empirically-based vulnerability relations integrated in a GIS platform. Cold Reg. Sci. Technol. 2008, 54, 193–205. [Google Scholar] [CrossRef]
- Zhang, M.; Zhang, X.; Zhang, Y.; Lin, Z. Security of cross-chain bridges: Attack surfaces, defenses, and open problems. In Proceedings of the 27th International Symposium on Research in Attacks, Intrusions and Defenses, Padua, Italy, 30 September–2 October 2024; pp. 298–316. [Google Scholar]
- Goes, C. The interblockchain communication protocol: An overview. arXiv 2020, arXiv:2006.15918. [Google Scholar] [CrossRef]
- Wood, G. Polkadot: Vision for a heterogeneous multi-chain framework. White Pap. 2016, 21, 4662. [Google Scholar]
- Wood, G. XCM: The Cross-Consensus Message Format. 2021. Available online: https://polkadot.com/blog/xcm-the-cross-consensus-message-format/ (accessed on 16 July 2025).
- Breidenbach, L.; Cachin, C.; Chan, B.; Coventry, A.; Ellis, S.; Juels, A.; Koushanfar, F.; Miller, A.; Magauran, B.; Moroz, D.; et al. Chainlink 2.0: Next steps in the evolution of decentralized oracle networks. Chain Labs 2021, 1, 1–136. [Google Scholar]
- Zarick, R.; Pellegrino, B.; Banister, C. Layerzero: Trustless omnichain interoperability protocol. arXiv 2021, arXiv:2110.13871. [Google Scholar] [CrossRef]
- Bowe, S.; Chiesa, A.; Green, M.; Miers, I.; Mishra, P.; Wu, H. Zexe: Enabling decentralized private computation. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 947–964. [Google Scholar]
- Canetti, R.; Dodis, Y.; Pass, R.; Walfish, S. Universally composable security with global setup. In Proceedings of the Theory of Cryptography: 4th Theory of Cryptography Conference, TCC 2007, Amsterdam, The Netherlands, 21–24 February 2007; Proceedings 4. Springer: Berlin/Heidelberg, Germany, 2007; pp. 61–85. [Google Scholar]
- Dziembowski, S.; Faust, S.; Hostáková, K. General state channel networks. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 15–19 October 2018; pp. 949–966. [Google Scholar]
- Dziembowski, S.; Eckey, L.; Faust, S.; Hesse, J.; Hostáková, K. Multi-party virtual state channels. In Proceedings of the Advances in Cryptology–EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019; Proceedings, Part I 38. Springer: Berlin/Heidelberg, Germany, 2019; pp. 625–656. [Google Scholar]
- Aumayr, L.; Ersoy, O.; Erwig, A.; Faust, S.; Hostáková, K.; Maffei, M.; Moreno-Sanchez, P.; Riahi, S. Generalized channels from limited blockchain scripts and adaptor signatures. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 6 December 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 635–664. [Google Scholar]
- Aumayr, L.; Moreno-Sanchez, P.; Kate, A.; Maffei, M. Blitz: Secure {Multi-Hop} payments without {Two-Phase} commits. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Online, 11–13 August 2021; pp. 4043–4060. [Google Scholar]
- Scaffino, G.; Aumayr, L.; Bastankhah, M.; Avarikioti, Z.; Maffei, M. Alba: The Dawn of Scalable Bridges for Blockchains. Cryptology ePrint Archive. 2024. Available online: https://eprint.iacr.org/2024/197 (accessed on 16 July 2025).
- Katz, J.; Maurer, U.; Tackmann, B.; Zikas, V. Universally composable synchronous computation. In Proceedings of the Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2013; pp. 477–498. [Google Scholar]
- YCSB. 2022. Available online: https://github.com/brianfrankcooper/YCSB (accessed on 23 March 2025).
- Baliga, A.; Subhod, I.; Kamat, P.; Chatterjee, S. Performance Evaluation of the Quorum Blockchain Platform. arXiv 2018, arXiv:1809.03421. [Google Scholar] [CrossRef]






| Solution | Scalability Enhancement | Cost Efficiency | Complex Contract Support | High Throughput | Universal Compatibility |
|---|---|---|---|---|---|
| Bool Network [23] | ✗ | ✗ | ✗ | ✗ | ✔ |
| Glimpse [24] | ✗ | ✔ | ✗ | ✗ | ✗ |
| PSSC [25] | ✔ | ✔ | ✗ | ✔ | ✔ |
| Tremble [26] | ✔ | ✔ | ✗ | ✔ | ✗ |
| Universal Atomic Swaps [27] | ✗ | ✔ | ✗ | ✗ | ✔ |
| Verilay [28] | ✗ | ✔ | ✗ | ✗ | ✗ |
| ScaL2Chain | ✔ | ✔ | ✔ | ✔ | ✔ |
| Parameter | Values |
|---|---|
| Number of DApps | 4, 8, 16, 32, 64 |
| Percentage of cross-app transactions | 0%, 25%, 50%, 75%, 100% |
| DApp node failure rate | 0%, 10%, 20%, 30% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, H.; Ying, Z.; Cai, J.; Yang, R. ScaL2Chain: Towards a Scalable Protocol for Multi-Chain Decentralized Applications. Electronics 2025, 14, 2895. https://doi.org/10.3390/electronics14142895
Yang H, Ying Z, Cai J, Yang R. ScaL2Chain: Towards a Scalable Protocol for Multi-Chain Decentralized Applications. Electronics. 2025; 14(14):2895. https://doi.org/10.3390/electronics14142895
Chicago/Turabian StyleYang, Haonan, Zuobin Ying, Jianping Cai, and Runjie Yang. 2025. "ScaL2Chain: Towards a Scalable Protocol for Multi-Chain Decentralized Applications" Electronics 14, no. 14: 2895. https://doi.org/10.3390/electronics14142895
APA StyleYang, H., Ying, Z., Cai, J., & Yang, R. (2025). ScaL2Chain: Towards a Scalable Protocol for Multi-Chain Decentralized Applications. Electronics, 14(14), 2895. https://doi.org/10.3390/electronics14142895








