Provably Secure and Privacy-Preserving Authentication Scheme for IoT-Based Smart Farm Monitoring Environment
Abstract
1. Introduction
1.1. Contributions
- This work offers a security analysis of the scheme by Rahaman et al. [15] and reveals its vulnerabilities to various attacks, including device capture, impersonation, insider, and ephemeral secret leakage attacks.
- We propose a secure and privacy-preserving authentication scheme that ensures enhanced security. A PUF is employed in the proposed scheme to ensure the security of the sensor. The proposed scheme can guarantee resistance against sensor capture attacks.
- We prove the security of the proposed scheme by using the “Burrows-Abadi-Needham (BAN) logic” [16], “real-or-random (RoR) model” [17], and “Automated Verification of Internet Security Protocols and Applications (AVISPA) simulation tool” [18,19] formally to demonstrate the robustness of the proposed scheme.
- We demonstrate the efficiency of the proposed scheme through a comparative analysis of the communication cost, computational cost, and security features with related works. The proposed scheme shows superior performance over previous works.
1.2. Organization
2. Related Work
3. Preliminaries
3.1. Physical Unclonable Function
- A PUF generates a unique response for each challenge.
- The physical structure of a PUF cannot be cloned.
- The response of a PUF is unpredictable and depends on physical circuits.
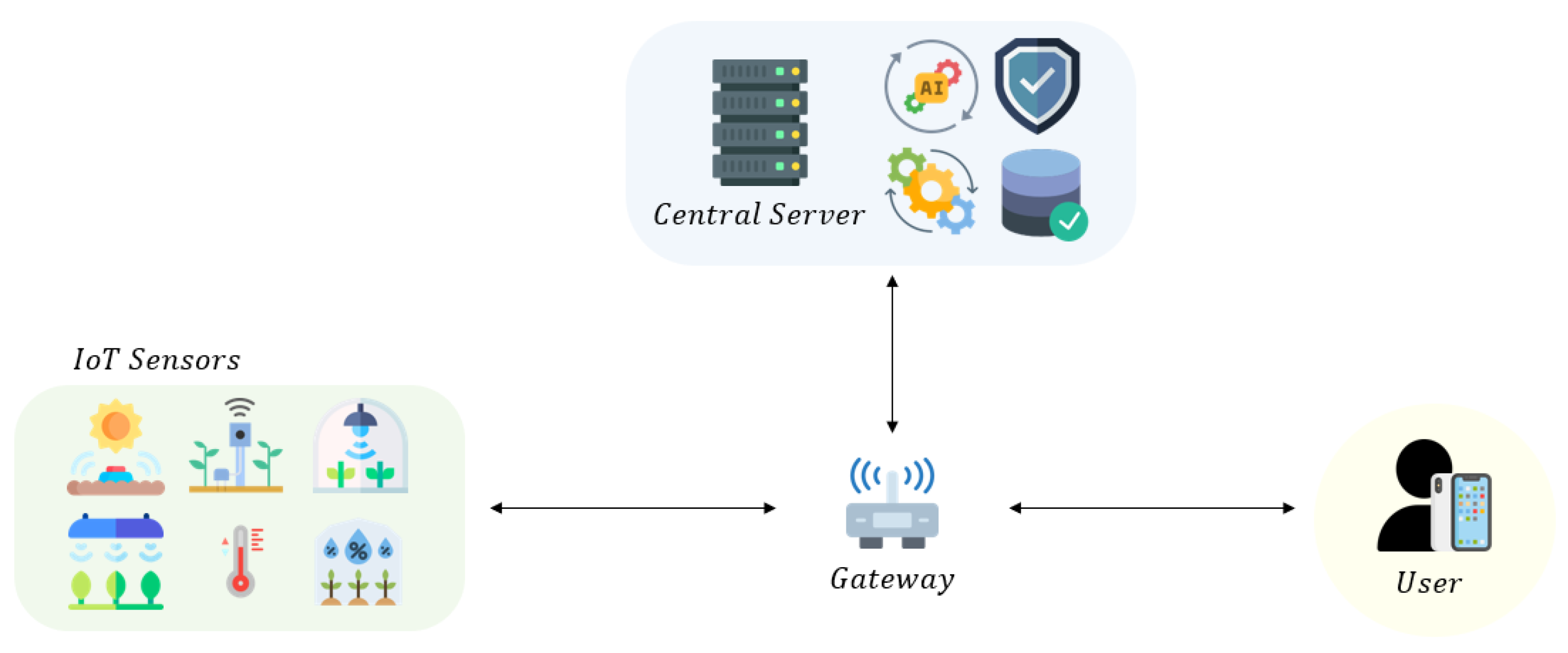
3.2. System Model
- Central server: As a trusted entity, the CS possesses sufficient computational and storage capabilities. The user and IoT sensor must be registered with the CS before mutual authentication. After the mutual authentication, the CS can store the sensor data and provide insights or decision support information to the user using an AI model. Deep learning models, like a CNN and LSTM, can analyze sensor data to detect crop diseases and pests and use this information to predict yields and harvest timing.
- Users: The user refers to farmers or farm managers with mobile devices to access smart farming systems. After the authentication, the user can directly view the sensor data and receive the AI analysis results from the CS.
- IoT sensors: The IoT sensors deployed in smart farms have limited resources. They collect numerous real-time data, including temperature, humidity, soil condition, rain volume, and pest presence.
- Gateway: The gateway exchanges data between three other entities, acting as a communication relay.
3.3. Notation
3.4. Adversary Model
- Adversary can eavesdrop, intercept, delete, forge, and resend messages exchanged via a public channel [46].
- Adversary can obtain a stolen mobile user device and retrieve the secret values stored on it through a power analysis attack.
- Adversary can register as a legitimate user on the and participate in mutual authentication.
- Adversary can obtain session-specific ephemeral secrets and long-term private keys of the after the session termination.
- Adversary can try to perform privileged insider, DoS, and impersonation attacks, among others.
3.5. Review of Rahaman et al.’s Scheme
3.5.1. Registration Phase
- Step 1:
- First, transmits its identity to the via a secure channel.
- Step 2:
- The computes a shared secret value with its master key. Then, the securely transmits to .
- Step 3:
- chooses its real identity , password , and temporary identity . Next, calculates the encrypted password . Then, transmits to the .
- Step 4:
- The computes the user’s secret value and after receiving the message. The transmits to via a secure channel and stores and in a database.
- Step 5:
- stores in a mobile device.
3.5.2. Login and Authentication Phase
- Step 1:
- enters identity and password in the mobile device, which computes and verifies . If it matches, the mobile device generates a random number and a timestamp , and computes and . Then, the mobile device sends to via a public channel.
- Step 2:
- When the authentication request is obtained from , selects a random number and computes and . Next, transmits a message to the .
- Step 3:
- The receives a message from and first validates timestamp . If valid, the retrieves against . The computes , , and and checks . The computes and and checks . If matched, the generates random number and timestamp . Afterward, the computes , , , and , and then transmits to .
- Step 4:
- verifies and calculates , , and . Then, sends the rest of message to .
- Step 5:
- also confirms the validity of . If legitimate, the user computes and shares a session key with the and .
4. Cryptanalysis of Rahaman et al.’s Scheme
4.1. Stolen Mobile Device Attacks
- Step 1:
- Adversary extracts the stored secret credentials in the user’s mobile device, intercepts , and is transmitted via a public channel.
- Step 2:
- calculates , , and a session key .
- Step 3:
- Furthermore, can calculate the session key for all users with and messages transmitted through a public channel. eavesdrops on , and from the message of another user and computes , , and . Finally, can compute another user’s session key .
4.2. User Impersonation Attacks
- Step 1:
- acquires a legitimate user’s mobile device and obtains the stored credentials .
- Step 2:
- generates timestamp and random number and calculates and using the credentials of the legitimate user.
- Step 3:
- receives the message from and transmits it with its information to the , which calculates the session key with the random number from .
4.3. User Insider Attacks
- Step 1:
- obtains the hash value of the master key via registration and eavesdrops on , and transmitted on a public channel.
- Step 2:
- calculates , , and .
- Step 3:
- Finally, knows all the information , and needed to establish a session key of another legitimate user and computes .
4.4. Sensor Capture Attacks
- Step 1:
- Adversary obtains the sensor credentials from a captured sensor and eavesdrops on , and transmitted on a public channel.
- Step 2:
- calculates , , and . Finally, can calculate the session key .
4.5. Ephemeral Secret Leakage Attacks
4.6. User Untraceability
5. Proposed Scheme
5.1. Initialization Phase
5.2. User Registration Phase
- Step 1:
- chooses identity and password and generates random number . The user transmits its identity to the for registration.
- Step 2:
- The generates random number and calculates the user’s temporary identity and shared secret value . The also computes to hide . Then, the transmits and to securely and stores with .
- Step 3:
- After receiving that, computes a value for hiding random number , a value for login , and .
5.3. Sensor Registration Phase
- Step 1:
- chooses identity and challenge value . The sensor transmits its identity to the over a secure channel.
- Step 2:
- The generates random number and computes shared secret value with the master key. Then, the transmits to securely and stores and .
- Step 3:
- computes and . The sensor stores .
5.4. Login and Authentication Phase
- Step 1:
- inserts and . The user computes and and checks . If it matches, generates random number and timestamp . calculates , , and , and then sends a login request message to the over a public channel.
- Step 2:
- The first verifies whether timestamp is valid. If valid, the computes , , , and . If matches the received , the retrieves and generates timestamp and random number . The computes , , and , and then transmits to the sensor.
- Step 3:
- validates timestamp and computes , , , and . checks whether and match. If they match, generates timestamp and random number and computes a shared session key , , and . Finally, sends to the .
- Step 4:
- The verifies the legitimacy of . Then, the computes , , and . The compares and , and if equal, the computes the user’s new temporary identity , , and . Afterward, the generates and computes , , , and . Last, the updates to and , and sends to over a public channel.
- Step 5:
- validates timestamp . If valid, computes , , , , and . checks whether and are the same. If they are the same, computes a new temporary identity and updates and .
6. Security Analysis
6.1. Informal Security Analysis
6.1.1. Resistance to Stolen Mobile Device Attacks
6.1.2. Resistance to Impersonation Attacks
6.1.3. Resistance to Off-Line Guessing Attacks
6.1.4. Resistance to Insider Attacks
6.1.5. Resistance to Sensor Capture Attacks
6.1.6. Resistance to Replay and MITM Attacks
6.1.7. Resistance to Ephemeral Secret Leakage Attacks
6.1.8. Resistance to Stolen Verifier Attacks
6.1.9. Resistance to Privileged Insider Attacks
6.1.10. Resistance to Denial-of-Service Attacks
6.1.11. Support User Anonymity and Untraceability
6.1.12. Support Perfect Forward Secrecy
6.1.13. Support Mutual Authentication
6.2. Formal Proof Under BAN Logic
6.2.1. Rules
- Message meaning rule (MMR):
- Nonce verification rule (NVR):
- Jurisdiction rule (JR):
- Belief rule (BR):
- Freshness rule (FR):
6.2.2. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Goal 5:
- Goal 6:
- Goal 7:
- Goal 8:
6.2.3. Idealized Forms
- :
- :
- :
- :
6.2.4. Assumptions
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
6.2.5. BAN Logic Proof
- Step 1:
- can be derived from :
- Step 2:
- By employing the MMR with and , can be derived:
- Step 3:
- By employing the FR with and , can be derived:
- Step 4:
- By employing the NVR with and , can be derived:
- Step 5:
- can be obtained from :
- Step 6:
- can be derived by applying the MMR to and :
- Step 7:
- By employing the FR with and , can be derived:
- Step 8:
- By employing the NVR with and , can be derived:
- Step 9:
- can be obtained from :
- Step 10:
- By employing the MMR with and , can be derived:
- Step 11:
- By employing the FR with and , can be derived:
- Step 12:
- By employing the NVR with and , can be derived:
- Step 13:
- and can be derived from and . and can calculate a session key :
- Step 14:
- and can be derived by employing the JR with and , and and , respectively:
- Step 15:
- can be derived from :
- Step 16:
- By employing the MMR with and , can be derived:
- Step 17:
- By employing the FR with and , can be derived:
- Step 18:
- By employing the NVR with and , can be derived:
- Step 19:
- and can be derived from and . and can calculate the session key :
- Step 20:
- and can be derived by employing the JR with and , and and , respectively:
6.3. Formal Proof Under RoR Model
- : This query corresponds to a passive attack where eavesdrops on messages sent via a public channel between , , and .
- : This query presents stolen mobile device attacks. can retrieve the confidential values stored in a user’s mobile device.
- : This query corresponds to an active attack in which adversary transmits a message M to and accepts the corresponding response.
- : This query determines whether a session key is real or random. Before the game begins, flips a fair coin. If , the returned key is the valid session key, and if , it is a random string. Otherwise, if the result is , cannot distinguish the session key.
- : In this game, performs a real attack on the proposed scheme. must randomly select a bit c before starting the game. Therefore, the probability is presented in Equation (1):
- : An eavesdropping attack is performed by through the query. attempts to compute a session key using messages transmitted over a public channel. Then, uses the query to determine whether the computed session key is real. In the proposed scheme, , and are required to compute the session key. However, cannot calculate the session key; hence, the probability of success in this game is equal to that of :
- : In this game, tries to forge a message using the and queries. To do this, must determine a hash collision because messages are generated as hash values of secret parameters and random numbers. However, due to the one-way nature of the hash function, it is difficult for to determine the hash collision. Thus, based on the birthday paradox [49], Equation (3) can be derived:
- : Similar to , uses and queries. However, due to the property of PUF explained in Section 3.1, cannot succeed in . Therefore, the equation is expressed as follows:
- : uses the query to obtain values , , , and stored in the user’s mobile device. To compute the session key using these values, must recover via the user’s real identity and password . Therefore, because must guess and simultaneously, the equation can be derived according to Zipf’s law [48] as follows:
6.4. Formal Proof Under AVISPA Simulation
7. Performance Analysis
7.1. Computational Costs
7.2. Communication Costs
7.3. Energy Consumption
7.4. Security Features
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Navarro, E.; Costa, N.; Pereira, A. A systematic reviews of IoT solutions for smart farming. Sensors 2020, 20, 4143. [Google Scholar] [CrossRef]
- FAO. The Future of Food and Agriculture: Trends and Challenges; FAO: Rome, Italy, 2017; ISBN 978-92-5-109551-5. [Google Scholar]
- ElBeheiry, N.; Balog, R.S. Technologies driving the shift to smart farming:A review. IEEE Sens. J. 2020, 23, 1752–7169. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R. Enhancing smart farming through the applications of Agriculture 4.0 technologies. Int. J. Intell. Netw. 2022, 3, 150–164. [Google Scholar] [CrossRef]
- Misra, N.N.; Dixit, Y.; Al-Mallahi, A.; Bhullar, M.S.; Upadhyay, R.; Martynenko, A. IoT, big data, and artificial intelligence in agriculture and food industry. IEEE Internet Things J. 2020, 9, 6305–6324. [Google Scholar] [CrossRef]
- AlZubi, A.A.; Galyna, K. Artificial intelligence and internet of things for sustainable farming and smart agriculture. IEEE Access 2023, 11, 78686–78692. [Google Scholar] [CrossRef]
- Fuentes, A.; Yoon, S.; Kim, S.C.; Park, D.S. A robust deep-learning-based detector for real-time tomato plant diseases and pests recognition. Sensors 2017, 17, 2022. [Google Scholar] [CrossRef] [PubMed]
- Shandilya, U.; Khanduja, V. Intelligent farming system with weather forecast support and crop prediction. In Proceedings of the 2020 5th International Conference on Computing, Communication and Security (ICCCS), Patna, India, 14–16 October 2020; pp. 1–6. [Google Scholar]
- Reddi, S.; Rao, P.M.; Saraswathi, P.; Jangirala, S.; Das, A.K.; Jamal, S.S.; Park, Y. Privacy-preserving electronic medical record sharing for IoT-enabled healthcare system using fully homomorphic encryption, IOTA, and masked authenticated messaging. IEEE Trans. Ind. Inform. 2024, 20, 10802–10813. [Google Scholar] [CrossRef]
- Gupta, M.; Abdelsalam, M.; Khorsandroo, S.; Mittal, S. Security and privacy in smart farming: Challenges and opportunities. IEEE Access 2020, 8, 34564–34584. [Google Scholar] [CrossRef]
- Wazid, M.; Singh, J.; Pandey, C.; Sherratt, R.S.; Das, A.K.; Giri, D.; Park, Y. Explainable Deep Learning-Enabled Malware Attack Detection for IoT-Enabled Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2025, 26, 7231–7244. [Google Scholar] [CrossRef]
- Farooq, M.S.; Riaz, S.; Abid, A.; Abid, K.; Naeem, M.A. A survey on the Role of IoT in Agriculture for the Implementation of Smart Farming. IEEE Access 2019, 7, 156237–156271. [Google Scholar] [CrossRef]
- Gao, N.; Meng, S.; Li, C.; Meng, S.; Tang, W.; Jin, S. RIS-assisted wireless link signatures for specific emitter identification. IEEE Trans. Wirel. Commun. 2024, 23, 17872–17883. [Google Scholar] [CrossRef]
- Gao, N.; Liu, Y.; Zhang, Q.; Li, X.; Jin, S. Let RFF do the talking: Large language model enabled lightweight RFFI for 6G edge intelligence. Sci. China Inf. Sci. 2025, 68, 170308. [Google Scholar] [CrossRef]
- Rahaman, M.; Lin, C.Y.; Pappachan, P.; Gupta, B.B.; Hsu, C.H. Privacy-centric AI and IoT solutions for smart rural farm monitoring and control. Sensors 2024, 24, 4157. [Google Scholar] [CrossRef] [PubMed]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. TOCS 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 30 April 2025).
- SPAN: A Security Protocol Animator for AVISPA. Available online: https://people.irisa.fr/Thomas.Genet/span/ (accessed on 30 April 2025).
- He, Y.; Huang, F.; Wang, D.; Zhang, R. Outage probability analysis of MISO-NOMA downlink communications in UAV-assisted agri-IoT with SWIPT and TAS enhancement. IEEE Trans. Netw. Sci. Eng. 2025, 12, 2151–2164. [Google Scholar] [CrossRef]
- Yu, M.; Zhang, H.; Ma, J.; Duan, X.; Kang, S.; Li, J. Cold Chain Logistics Supervision of Agricultural Products Supported Using Internet of Things Technology. IEEE Internet Things J. 2024, 12, 3502–3511. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Karuppiah, M.; Conti, M. A secure user authentication and key-agreement scheme using wireless sensor networks for agriculture monitoring. Future Gener. Comput. Syst. 2018, 84, 200–215. [Google Scholar] [CrossRef]
- Chen, M.; Lee, T.F.; Pan, J.I. An enhanced lightweight dynamic pseudonym identity based authentication and key agreement scheme using wireless sensor networks for agriculture monitoring. Sensors 2019, 19, 1146. [Google Scholar] [CrossRef] [PubMed]
- Vangala, A.; Das, A.K.; Mitra, A.; Das, S.K.; Park, Y. Blockchain-enabled authenticated key agreement scheme for mobile vehicles-assisted precision agricultural IoT networks. IEEE Trans. Inf. Forensics Secur. 2022, 18, 904–919. [Google Scholar] [CrossRef]
- Itoo, S.; Khan, A.A.; Ahmad, M.; Idrisi, M.J. A secure and privacy-preserving lightweight authentication and key exchange algorithm for smart agriculture monitoring system. IEEE Access 2023, 11, 56875–56890. [Google Scholar] [CrossRef]
- Abduljabbar, Z.A.; Nyangaresi, V.O.; Jasim, H.M.; Ma, J.; Hussain, M.A.; Hussien, Z.A.; Aldarwish, A.J. Elliptic curve cryptography-based scheme for secure signaling and data exchanges in precision agriculture. Sustainability 2023, 15, 10264. [Google Scholar] [CrossRef]
- Jabbari, A.; Mohasefi, J.B. Improvement of a user authentication scheme for wireless sensor networks based on internet of things security. Wirel. Pers. Commun. 2021, 116, 2565–2591. [Google Scholar] [CrossRef]
- Kumar, D. A secure and efficient user authentication protocol for wireless sensor network. Multimed. Tools Appl. 2021, 80, 27131–27154. [Google Scholar] [CrossRef]
- Mo, J.; Hu, Z.; Shen, W. A provably secure three-factor authentication protocol based on chebyshev chaotic mapping for wireless sensor network. IEEE Access 2022, 10, 12137–12152. [Google Scholar] [CrossRef]
- Huang, W. ECC-based three-factor authentication and key agreement scheme for wireless sensor networks. Sci. Rep. 2024, 14, 1787. [Google Scholar] [CrossRef]
- Alotaibi, M. An enhanced symmetric cryptosystem and biometric-based anonymous user authentication and session key establishment scheme for WSN. IEEE Access 2018, 6, 70072–70087. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Al Jabban, M.A.B.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An efficient authentication and key agreement scheme based on ECDH for wireless sensor network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Badshah, A.; Waqas, M.; Muhammad, F.; Abbas, G.; Abbas, Z.H.; Chaudhry, S.A.; Chen, S. AAKE-BIVT: Anonymous authenticated key exchange scheme for blockchain-enabled Internet of Vehicles in smart transportation. IEEE Trans. Intell. Transp. Syst. 2022, 24, 1739–1755. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Bhuiyan, M.Z.A.; Wu, F.; Karuppiah, M.; Kumari, S. A robust ECC-based provable secure authentication protocol with privacy preserving for industrial Internet of Things. IEEE Trans. Ind. Inform. 2017, 14, 3599–3609. [Google Scholar] [CrossRef]
- Rangwani, D.; Sadhukhan, D.; Ray, S.; Khan, M.K.; Dasgupta, M. An improved privacy preserving remote user authentication scheme for agricultural wireless sensor network. Trans. Emerg. Telecommun. Technol. 2021, 32, e4218. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Lee, J.H. Provably secure signature-based anonymous user authentication protocol in an Internet of Things-enabled intelligent precision agricultural environment. Concurr. Comput. Pract. Exp. 2023, 35, e6187. [Google Scholar] [CrossRef]
- Guo, Y.; Guo, Y. CS-LAKA: A lightweight authenticated key agreement protocol with critical security properties for IoT environments. IEEE Trans. Serv. Comput. 2023, 16, 4102–4114. [Google Scholar] [CrossRef]
- Wang, F.; Song, J. Cryptanalysis of Two Lightweight Authentication Protocols for IoT Environments. In Proceedings of the 2024 10th International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2024; pp. 405–409. [Google Scholar]
- Nyangaresi, V.O.; Yenurkar, G.K. Anonymity preserving lightweight authentication protocol for resource-limited wireless sensor networks. High-Confid. Comput. 2024, 4, 100178. [Google Scholar] [CrossRef]
- Khan, R.A.; Mushtaq, S.; Lone, S.A.; Gupta, R.; Moon, A.H. Integrating ABHA for authentication and key exchange: A hybrid security framework for smart healthcare in India. Peer-to-Peer Netw. Appl. 2025, 18, 130. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. A robust authentication protocol for wireless medical sensor networks using blockchain and physically unclonable functions. IEEE Internet Things J. 2022, 9, 20214–20228. [Google Scholar] [CrossRef]
- Bathalapalli, V.K.; Mohanty, S.P.; Kougianos, E.; Yanambaka, V.P.; Baniya, B.K.; Rout, B. A puf-based approach for sustainable cybersecurity in smart agriculture. In Proceedings of the 2021 19th OITS International Conference on Information Technology (OCIT), Bhubaneswar, India, 16–18 December 2021; pp. 375–380. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Advances in Cryptology—EUROCRYPT 2002, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based Internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Kwon, D.; Son, S.; Kim, M.; Lee, J.; Das, A.K.; Park, Y. A secure self-certified broadcast authentication protocol for intelligent transportation systems in UAV-assisted mobile edge computing environments. IEEE Trans. Intell. Transp. Syst. 2024, 25, 19004–19017. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Advances in Cryptology—EUROCRYPT 2000, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques Bruges, Belgium, 14–18 May 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 156–171. [Google Scholar]
- Yu, S.; Park, K.; Park, Y. A Machine Learning Attack-Resistant PUF-based Robust and Efficient Mutual Authentication Scheme in Fog-enabled IoT Environments. IEEE Internet Things J. 2025, 12, 20652–20669. [Google Scholar] [CrossRef]
- Sun, Y.; Cao, J.; Ma, M.; Zhang, Y.; Li, H.; Niu, B. EAP-DDBA: Efficient anonymity proximity device discovery and batch authentication mechanism for massive D2D communication devices in 3GPP 5G HetNet. IEEE Trans. Dependable Secur. Comput. 2020, 19, 370–387. [Google Scholar] [CrossRef]






| Schemes | Contributions | Limitations |
|---|---|---|
| [22] |
|
|
| [23] |
|
|
| [25] |
|
|
| [26] |
|
|
| [27] |
|
|
| [28] |
|
|
| [29] |
|
|
| [30] |
|
|
| [31] |
|
|
| [32] |
|
|
| [34] |
|
|
| [35] |
|
|
| [36] |
|
|
| [37] |
|
|
| [39] |
|
|
| [15] |
|
|
| Notation | Description |
|---|---|
| i-th user | |
| j-th sensor | |
| Central server | |
| Master key of | |
| Password of | |
| Real identity of | |
| Pseudo-identity of | |
| Real identity of | |
| Challenge/response of | |
| Session key between , , and | |
| Random numbers | |
| Timestamp | |
| Hash function | |
| Physical unclonable function | |
| Concatenation function | |
| ⊕ | Exclusive-or operation |
| Notation | Descriptions |
|---|---|
| Principals | |
| Statements | |
| Session key | |
| once said | |
| believes | |
| receives | |
| controls | |
| is encrypted with K | |
| and share a key K | |
| is fresh |
| 0.309 ms | 2.288 ms | 2.288 ms | 0.016 ms | 0.018 ms | 0.216 ms |
| Scheme | User | Server | Sensor | Total Cost (ms) |
|---|---|---|---|---|
| Moghadam et al. [32] | 15.529 | |||
| Li et al. [34] | 15.641 | |||
| Rangwani et al. [35] | 13.478 | |||
| Vangala et al. [36] | 44.874 | |||
| Guo et al. [37] | 12.176 | |||
| Nyangaresi et al. [39] | 10.815 | |||
| Rahaman et al. [15] | 5.253 | |||
| Proposed | 11.649 |
| Scheme | Number of Messages | Communication Cost (Bits) |
|---|---|---|
| Moghadam et al. [32] | 4 | 2144 |
| Li et al. [34] | 4 | 2720 |
| Rangwani et al. [35] | 4 | 2528 |
| Vangala et al. [36] | 4 | 3712 |
| Guo et al. [37] | 3 | 2400 |
| Nyangaresi et al. [39] | 4 | 2752 |
| Rahaman et al. [15] | 4 | 2016 |
| Proposed | 4 | 2048 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jang, H.; Choi, J.; Son, S.; Kwon, D.; Park, Y. Provably Secure and Privacy-Preserving Authentication Scheme for IoT-Based Smart Farm Monitoring Environment. Electronics 2025, 14, 2783. https://doi.org/10.3390/electronics14142783
Jang H, Choi J, Son S, Kwon D, Park Y. Provably Secure and Privacy-Preserving Authentication Scheme for IoT-Based Smart Farm Monitoring Environment. Electronics. 2025; 14(14):2783. https://doi.org/10.3390/electronics14142783
Chicago/Turabian StyleJang, Hyeonjung, Jihye Choi, Seunghwan Son, Deokkyu Kwon, and Youngho Park. 2025. "Provably Secure and Privacy-Preserving Authentication Scheme for IoT-Based Smart Farm Monitoring Environment" Electronics 14, no. 14: 2783. https://doi.org/10.3390/electronics14142783
APA StyleJang, H., Choi, J., Son, S., Kwon, D., & Park, Y. (2025). Provably Secure and Privacy-Preserving Authentication Scheme for IoT-Based Smart Farm Monitoring Environment. Electronics, 14(14), 2783. https://doi.org/10.3390/electronics14142783







