Resilient Event-Triggered H∞ Control for a Class of LFC Systems Subject to Deception Attacks
Abstract
1. Introduction
- An integrated model of a networked power system is established, which simultaneously accounts for communication delays, stochastic deception attacks, and ETTS.
- An ETTS is proposed to minimize redundant transmission while enhancing control performance. Different from the traditional time-triggered scheme, ETTS effectively utilizes sampled data selectively, reducing the computation burden fairly.
- An event-triggered LFC design method is carefully developed to jointly optimize the output-feedback controller gain along with the communication parameters. Unlike conventional time-triggered controllers, the proposed LFC controller enhances control performance by effectively utilizing available information, even in the presence of deception attacks, achieving superior resilience compared to standard approaches.
2. Problem Setup
2.1. ETTS
2.2. Random Deception Attacks
- The LFC system (3), in the absence of external disturbances , should be AMSS;
- Under zero initial conditions, the system satisfies the performance requirement for any nonnegative noises , where represents a prescribed performance bound.
3. Main Results
- ;
- ;
- .
| Algorithm 1 Event-based controller design algorithm. | |
| Step 1. | Initialize values of , , , , , G, , ; |
| Step 2. | Formulate kinetic model (3) of the LFC system; |
| Step 3. | Design the employed event-based controller (10) that satisfies AMSS and the performance index; |
| Step 4. | Solve the LMIs in Theorem 2 and derive the controller gain K. |
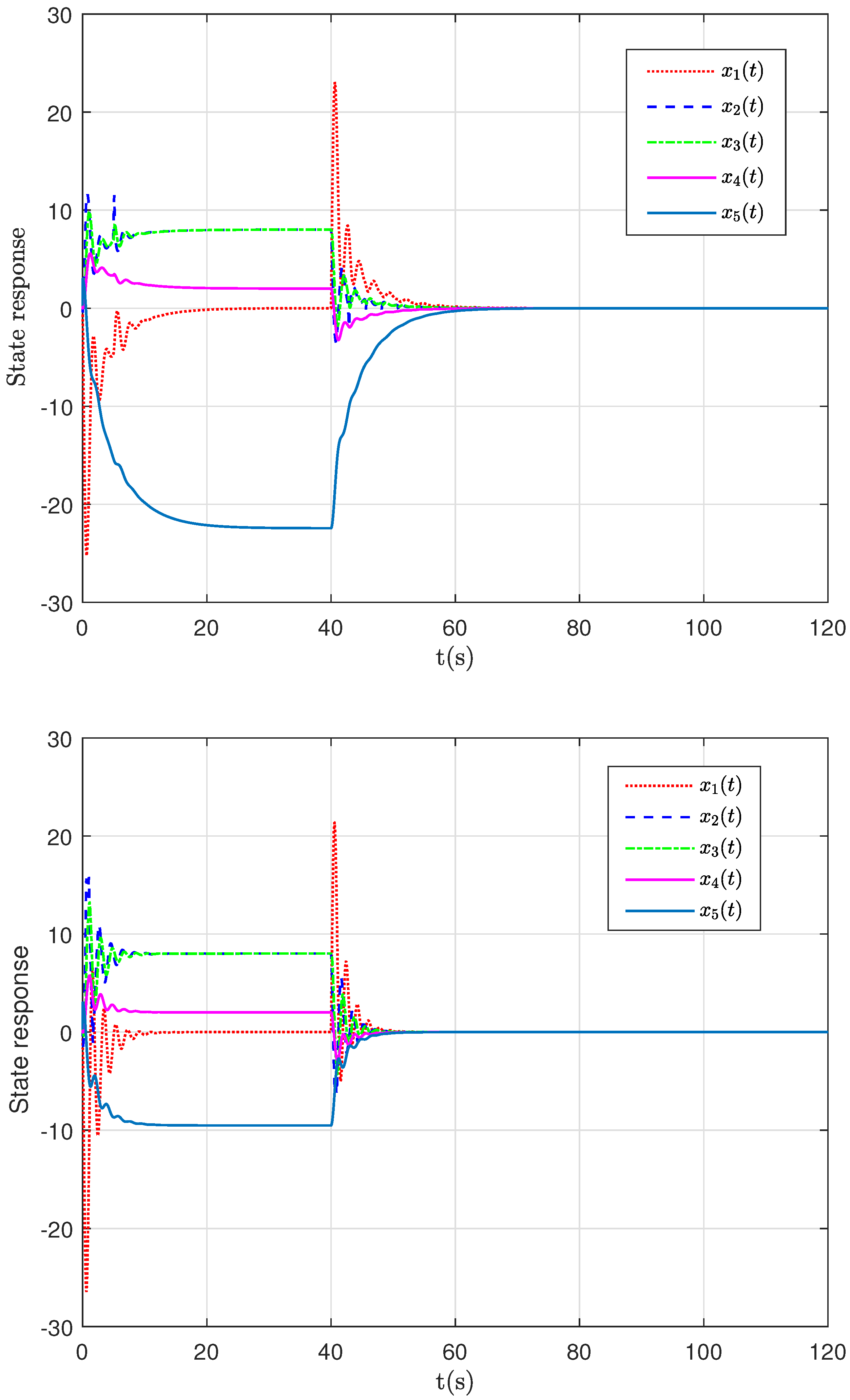
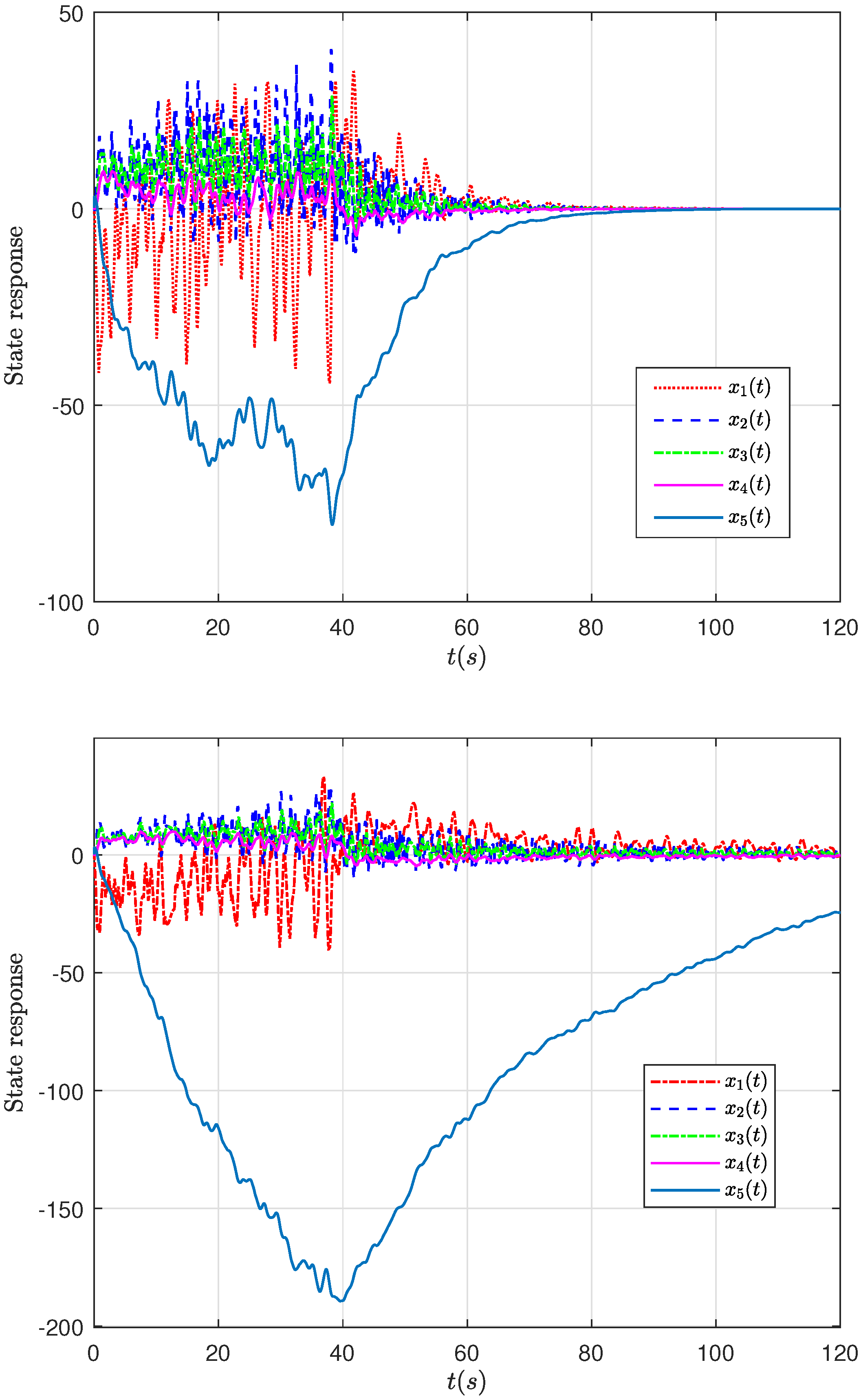
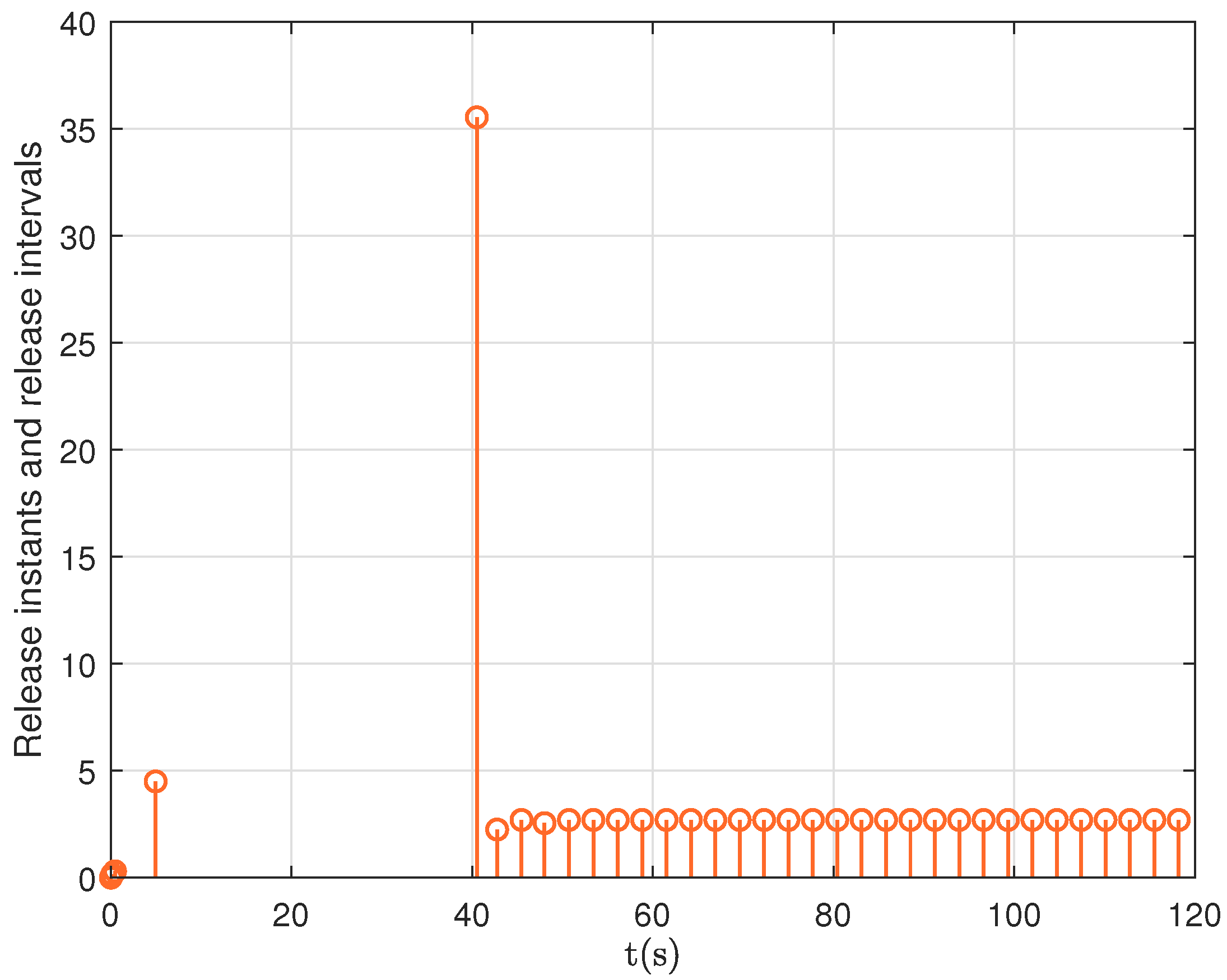
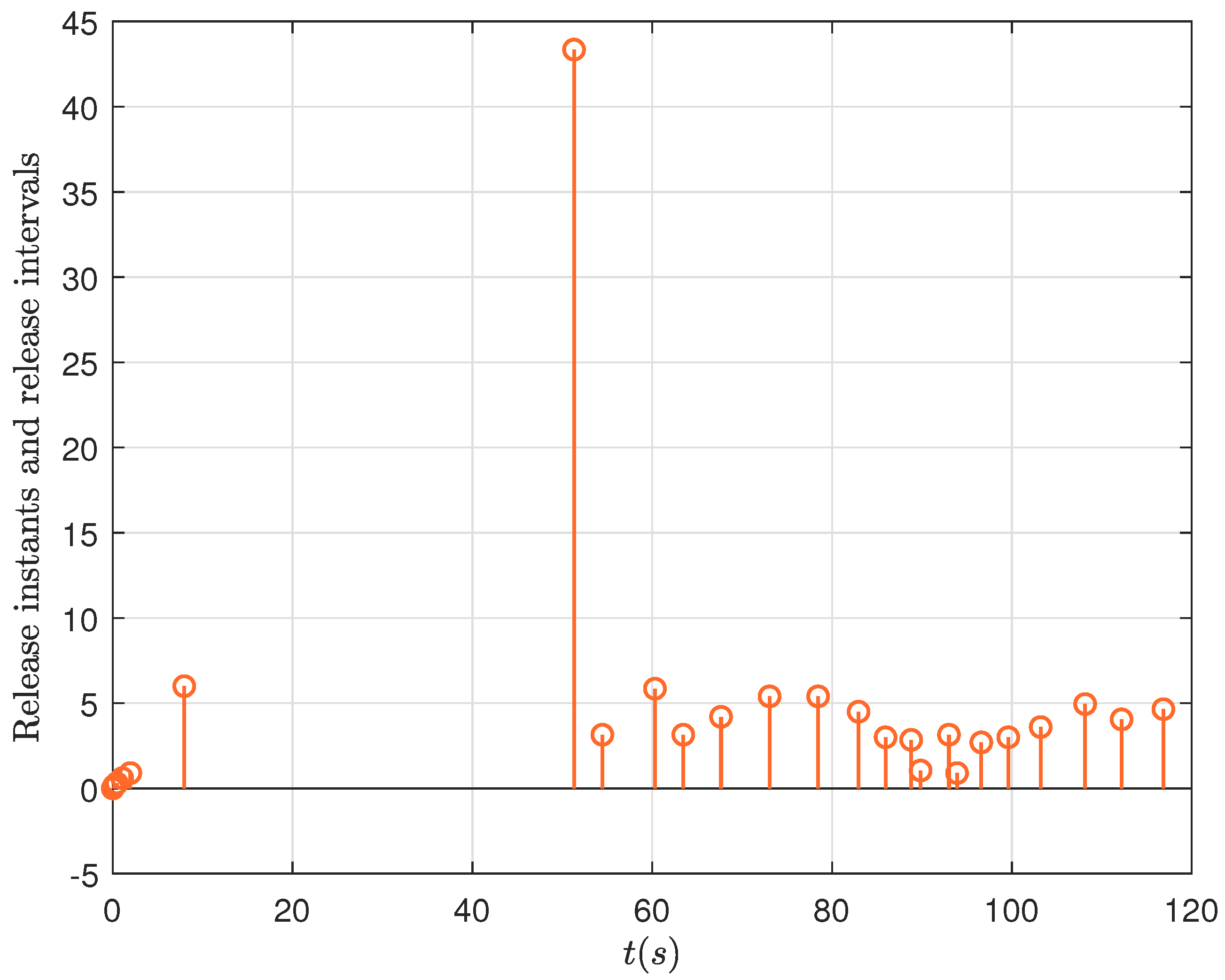
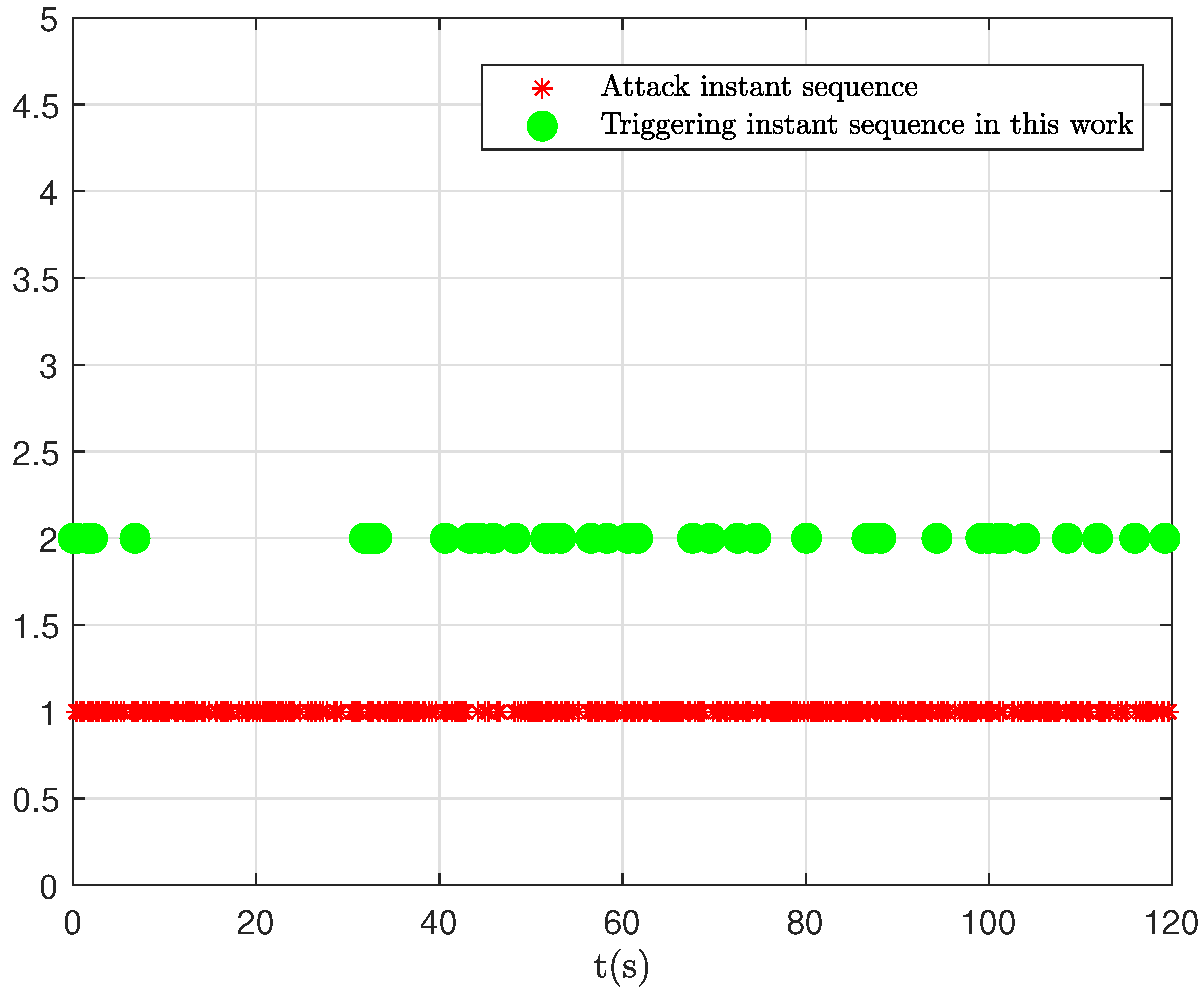
4. Case Studies
- Case 1: This case demonstrates that, in the absence of deception attacks, both Controller 1 and Controller 2 successfully stabilize the power system;
- Case 2: In this case, random deception attacks are introduced. Simulation results show that, compared to Controller 1, Controller 2 provides a significantly smoother and improved system response.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yilmaz, M.; Krein, P.T. Review of the impact of vehicle-to-grid technologies on distribution systems and utility interfaces. IEEE Trans. Power Electron. 2013, 28, 5673–5689. [Google Scholar] [CrossRef]
- Prabhakar, K.; Jain, S.K.; Padhy, P.K. Inertia estimation in modern power system: A comprehensive review. Electr. Power Syst. Res. 2022, 211, 10822. [Google Scholar] [CrossRef]
- Liu, D.; Zhang, X.; Tse, C.K. Effects of high level of penetration of renewable energy sources on cascading failure of modern power systems. IEEE J. Emerg. Sel. Top. Circuits Syst. 2022, 12, 98–106. [Google Scholar] [CrossRef]
- Liu, M.; Teng, F.; Zhang, Z.; Ge, P.; Sun, M.; Deng, R. Enhancing cyber-resiliency of DER-based smart grid: A survey. IEEE Trans. Smart Grid 2024, 15, 4998–5030. [Google Scholar] [CrossRef]
- Shangguan, X.C.; He, Y.; Zhang, C.K.; Jin, L.; Yao, W.; Jiang, L.; Wu, M. Control performance standards-oriented event-triggered load frequency control for power systems under limited communication bandwidth. IEEE Trans. Control Syst. Technol. 2022, 30, 860–868. [Google Scholar] [CrossRef]
- Zhang, Z.; Deng, R.; Yau, D.K.Y. Vulnerability of the load frequency control against the network parameter attack. IEEE Trans. Smart Grid 2024, 15, 921–933. [Google Scholar] [CrossRef]
- Bu, X.; Yu, W.; Cui, L.; Hou, Z.; Chen, Z. Event-triggered data-driven load frequency control for multiarea power systems. IEEE Trans. Ind. Inf. 2022, 18, 5982–5991. [Google Scholar] [CrossRef]
- Zhong, Q.; Yang, J.; Shi, K.; Zhong, S.; Li, Z.; Sotelo, M.A. Event-triggered H∞ load frequency control for multi-area nonlinear power systems based on non-fragile proportional integral control strategy. IEEE Trans. Intell. Transp. Syst. 2022, 23, 12191–12201. [Google Scholar] [CrossRef]
- Wang, H.; Chen, S.; Li, M.; Zhu, C.; Wang, Z. Demand-driven charging strategy-based distributed routing optimization under traffic restrictions in internet of electric vehicles. IEEE Internet Things J. 2024, 11, 35917–35927. [Google Scholar] [CrossRef]
- Islam, S.; Iqbal, A.; Marzband, M.; Khan, I.; Al-Wahedi, A.M. State-of-the-art vehicle-to-everything mode of operation of electric vehicles and its future perspectives. Renew. Sustain. Energy Rev. 2022, 166, 112574. [Google Scholar] [CrossRef]
- Liu, S.; Luo, W.; Wu, L. Co-design of distributed model-based control and event-triggering scheme for load frequency regulation in smart grids. IEEE Trans. Syst. Man Cybern. B Cybern. 2018, 50, 3311–3319. [Google Scholar] [CrossRef]
- Yang, S.; Lao, K.-W.; Hui, H.; Chen, Y. Secure distributed control for demand response in power systems against deception cyber-attacks with arbitrary patterns. IEEE Trans. Power Syst. 2024, 39, 7277–7290. [Google Scholar] [CrossRef]
- Liu, X.; Yang, G.-H. Optimal intermittent deception attacks with energy constraints for cyber-physical systems. IEEE Trans. Man Cybern. B Cybern. 2024, 54, 5889–5900. [Google Scholar] [CrossRef]
- Lu, K.D.; Wu, Z.-G. Resilient event-triggered load frequency control for cyber-physical power systems under DoS attacks. IEEE Trans. Power Syst. 2023, 38, 5302–5313. [Google Scholar] [CrossRef]
- Zhou, S.; Deng, C.; Fan, S.; Wang, B.; Che, W.-W. Resilient distributed Nash equilibrium control for nonlinear MASs under DoS attacks. IEEE Trans. Cybern. 2025, 55, 2316–2326. [Google Scholar] [CrossRef]
- Zhang, G.; Li, J.; Bamisile, O.; Xing, W.; Cai, D.; Huang, Q. An H∞ load frequency control scheme for multi-area power system under cyber-attacks and time-varying delays. IEEE Trans. Power Syst. 2023, 38, 1336–1349. [Google Scholar] [CrossRef]
- Khooban, M.H.; Niknam, T.; Shasadeghi, M.; Dragicevic, T.; Blaabjerg, F. Load frequency control in microgrids based on a stochastic noninteger controller. IEEE Trans. Sustain. Energy 2018, 9, 853–861. [Google Scholar] [CrossRef]
- Hu, S.; Ge, X.; Chen, X.; Yue, D. Resilient load frequency control of islanded AC microgrids under concurrent false data injection and denial-of-service attacks. IEEE Trans. Smart Grid 2023, 14, 690–700. [Google Scholar] [CrossRef]
- Zhao, N.; Yue, D.; Dou, C.; Shi, T. Distributed dynamic event-triggered cooperative control of multiple TCLs and HESS for improving frequency regulation. IEEE Trans. Ind. Inf. 2024, 20, 1539–1549. [Google Scholar] [CrossRef]
- Hossain, M.M.; Peng, C.; Wang, Y.-L.; Du, X. Handshake logic-based event-triggered load frequency control for smart grids under DoS attacks. IEEE Trans. Ind. Inf. 2022, 18, 3863–3872. [Google Scholar] [CrossRef]
- Hu, S.; Ge, X.; Zhang, W.; Yue, D. DoS-resilient load frequency control of multi-area power systems: An attack-parameter-dependent approach. IEEE Trans. Inf. Forensics Secur. 2024, 19, 3423–3434. [Google Scholar] [CrossRef]
- Peng, C.; Zhang, J.; Yan, H. Adaptive event-triggering H∞ load frequency control for network-based power systems. IEEE Trans. Ind. Electron. 2018, 65, 1685–1694. [Google Scholar] [CrossRef]
- Peng, C.; Li, J.; Fei, M. Resilient event-triggering H∞ load frequency control for multi-area power systems with energy-limited DoS attacks. IEEE Trans. Power Syst. 2016, 32, 4110–4118. [Google Scholar] [CrossRef]
- Hu, Z.; Zhang, K.; Su, R.; Wang, R.; Li, Y. Robust cooperative load frequency control for enhancing wind energy integration in multi-area power systems. IEEE Trans. Autom. Sci. Eng. 2024, 22, 1508–1518. [Google Scholar] [CrossRef]
- Yue, D.; Tian, E.; Han, Q.-L. A delay system method for designing event-triggered controllers of networked control systems. IEEE Trans. Autom. Control 2013, 58, 475–481. [Google Scholar] [CrossRef]
- Hossain, M.M.; Peng, C.; Su, H.-T.; Xie, S. Bandwidth allocation-based distributed event-triggered LFC for smart grids under hybrid attacks. IEEE Trans. Smart Grid 2022, 13, 820–830. [Google Scholar] [CrossRef]
- Zhai, J. Event-triggered control for p-normal uncertain nonlinear systems. Nonlinear Dyn. 2024, 112, 3661–3677. [Google Scholar] [CrossRef]
- Ren, H.; Cheng, Z.; Qin, J.; Lu, R. Deception attacks on event-triggered distributed consensus estimation for nonlinear systems. Automatica 2023, 154, 111100. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, Z.; Ma, Z.; Zhao, N. Prescribed performance adaptive neural event-triggered control for switched nonlinear cyber–physical systems under deception attacks. Neural Netw. 2024, 179, 106586. [Google Scholar] [CrossRef]
- Guo, Z.; Shi, D.; Johansson, K.-H.; Shi, L. Optimal linear cyber-attack on remote state estimation. IEEE Trans. Control Netw. Syst. 2017, 4, 4–13. [Google Scholar] [CrossRef]
- Li, T.; Wang, Z.; Zou, L.; Chen, B.; Yu, L. A dynamic encryption–decryption scheme for replay attack detection in cyber–physical systems. Automatica 2023, 151, 110926. [Google Scholar] [CrossRef]
- Guo, Z.; Shi, D.; Johansson, K.-H.; Shi, L. Worst-case stealthy innovation-based linear attack on remote state estimation. Automatica 2018, 89, 117–124. [Google Scholar] [CrossRef]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.R.; Dong, Z.Y. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid 2017, 8, 1630–1638. [Google Scholar] [CrossRef]
- Chen, P.; Zhang, D.; Yu, L.; Yan, H. Dynamic event-triggered output feedback control for load frequency control in power systems with multiple cyber attacks. IEEE Trans. Syst. Man Cybern. B Cybern. 2022, 52, 6246–6258. [Google Scholar] [CrossRef]
- Li, X.; Wei, G.; Ding, D.; Liu, S. Recursive filtering for time-varying discrete sequential systems subject to deception attacks: Weighted try-once-discard protocol. IEEE Trans. Syst. Man Cybern. B Cybern. 2021, 52, 3704–3713. [Google Scholar] [CrossRef]
- Liu, Q.; Zhao, C.; Liu, M.; Deng, R.; Cheng, P. Submodularity-based false data injection attack strategy in DC microgrids. IEEE Trans. Inf. Forensics Secur. 2025, 20, 2342–2352. [Google Scholar] [CrossRef]
- Pham, T.N.; Nahavandi, S.; Trinh, H.; Wong, K.P. Static output feedback frequency stabilization of time-delay power systems with coordinated electric vehicles state of charge control. IEEE Trans. Power Syst. 2017, 32, 3862–3874. [Google Scholar] [CrossRef]
- Zhang, X.-M.; Han, Q.-L.; Yu, X. Survey on Recent Advances in Networked Control Systems. IEEE Trans. Ind. Inf. 2016, 12, 1740–1752. [Google Scholar] [CrossRef]
- Zhang, X.M.; Han, Q.-L.; Ge, X. A novel approach to H∞ performance analysis of discrete-time networked systems subject to network-induced delays and malicious packet dropouts. Automatica 2022, 136, 110010. [Google Scholar] [CrossRef]
- Park, P.; Ko, J.-W.; Jeong, C. Reciprocally convex approach to stability of systems with time-varying delays. Automatica 2011, 47, 235–238. [Google Scholar] [CrossRef]
- Crusius, C.A.; Trofino, A. Sufficient LMI conditions for output feedback control problems. IEEE Trans. Autom. Control 1999, 44, 235–238. [Google Scholar] [CrossRef]
- Xiao, Z.; Jiang, Y.; Yao, Z.; He, Z.; Jiang, Y.; Li, Y. A hybrid data-driven power loss minimization method of dual-active bridge converters. IEEE Trans. Power Electron. 2024, 39, 5820–5832. [Google Scholar] [CrossRef]


| Parameters | Meaning |
|---|---|
| f | frequency deviation |
| governor valve position | |
| turbine output power | |
| incremental changes in EVs | |
| load disturbance | |
| control input | |
| thermal turbine | |
| participation factor | |
| D | load damping coefficient |
| M | inertia constant |
| governor | |
| droop characteristic | |
| speed governor | |
| turbine time constant | |
| gain constant | |
| time constant | |
| b | frequency bias constant |
| D | M | b | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 0.0083 | 0.1667 | 2.4 | 0.08 | 0.3 | 0.42 | 1 | 1 | 0.425 | 0.8 | 0.2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Xi, Z.; Zhang, B.; Zhang, T.; He, C. Resilient Event-Triggered H∞ Control for a Class of LFC Systems Subject to Deception Attacks. Electronics 2025, 14, 2713. https://doi.org/10.3390/electronics14132713
Wang Y, Xi Z, Zhang B, Zhang T, He C. Resilient Event-Triggered H∞ Control for a Class of LFC Systems Subject to Deception Attacks. Electronics. 2025; 14(13):2713. https://doi.org/10.3390/electronics14132713
Chicago/Turabian StyleWang, Yunfan, Zesheng Xi, Bo Zhang, Tao Zhang, and Chuan He. 2025. "Resilient Event-Triggered H∞ Control for a Class of LFC Systems Subject to Deception Attacks" Electronics 14, no. 13: 2713. https://doi.org/10.3390/electronics14132713
APA StyleWang, Y., Xi, Z., Zhang, B., Zhang, T., & He, C. (2025). Resilient Event-Triggered H∞ Control for a Class of LFC Systems Subject to Deception Attacks. Electronics, 14(13), 2713. https://doi.org/10.3390/electronics14132713






