Comparative Analysis of Security Features and Risks in Digital Asset Wallets
Abstract
1. Introduction
2. Related Work
- Comparison and Organization of Three E-Wallet Types: Previous research frequently addressed ID wallets, payment wallets, and cryptocurrency wallets separately. In contrast, this paper organizes these three types under one classification system—encompassing the key players, assets, functions, technologies, and services of each wallet—so they can be analyzed on a common basis. Through this, we clarify the e-wallet-related terminology and scope, providing foundational references that subsequent studies may consult when examining specific wallet types.
- Comparative Analysis of Security Threats by Type: We collected and summarized threats and incident cases reported for traditional financial (payment) wallets and cryptocurrency wallets, describing how both fields share certain security issues despite differing operational environments while also identifying issues unique to each. This distinction helps future discussions on digital asset security determine which threats are common to both traditional finance and cryptocurrency and which are specialized in only one domain.
- Consideration of a Universal Wallet Perspective: Drawing on “super-app” examples, this paper addresses the possibility that ID, payment, and cryptocurrency wallets could merge on a single platform, an angle that introduces new questions from a security standpoint. For instance, we highlight overlooked challenges in individual studies—such as permission conflicts, session management, and key loss—when three different asset types are managed simultaneously in a single application. This examination suggests future implications for a universal wallet environment.
- Quantitative Analysis to Confirm Risk Reduction: We applied the security requirements derived in this paper to actual scenarios (super-app payment or transaction, distributed key recovery, and CBDC issuance) and conducted a deterministic stress test to compute residual expected losses and compare how much threats can be mitigated. Such a quantitative assessment indicates how effective each security mechanism might be when different e-wallets converge. It also provides valuable data for subsequent research, such as protocol design or empirical experimentation.
3. Classification of Electronic Wallet Type
3.1. Digital ID Wallets
3.1.1. Key Functions and Managed Information
3.1.2. Technology and Service Evolution
3.2. Digital Payment Wallets
3.2.1. Key Functions and Managed Information
3.2.2. Technology and Service Evolution
3.3. Cryptocurrency Wallets
3.3.1. Key Functions and Managed Information
3.3.2. Technology and Service Evolution
4. Electronic Wallet Security Analysis
4.1. Comparison of Electronic Wallet Functions and Security Elements
- Key Information Processing: ID wallets have strengthened multi-factor authentication to identify and authenticate legitimate users, whereas digital payment wallets support secure financial transactions by storing payment information and minimizing exposure. Cryptocurrency wallets require further development of decentralized custody wallet models to protect assets from private key misuse and insider fraud.
- Key Information Storage: ID wallets mitigate the risk of critical information theft by implementing certificates and one-time passwords (OTPs) in separate hardware (e.g., security tokens and embedded secure elements), yet they remain vulnerable to sophisticated man-in-the-middle attacks [34,48]. Payment wallets tokenize sensitive information to reduce exposure of actual card numbers and use one-time codes to prevent reuse. Since a cryptocurrency wallet’s private key is considered “something you have”, the field is evolving toward securely storing keys in embedded secure elements (e.g., TEEs).
- Key Information Recovery: When an electronic wallet is lost or stolen, recovery and reissuance processes are essential. ID and payment wallets generally involve reverification and issuance of new certificates or payment information. However, in distributed ledger environments, if a cryptocurrency wallet’s key is lost, accessing the associated assets becomes impossible, a unique characteristic of such wallets. Accordingly, technologies that enable key recovery and reissuance (e.g., key revocation or reissuance, authority distribution, multi-signature, and MPC) have gained importance to address private key loss or leakage.
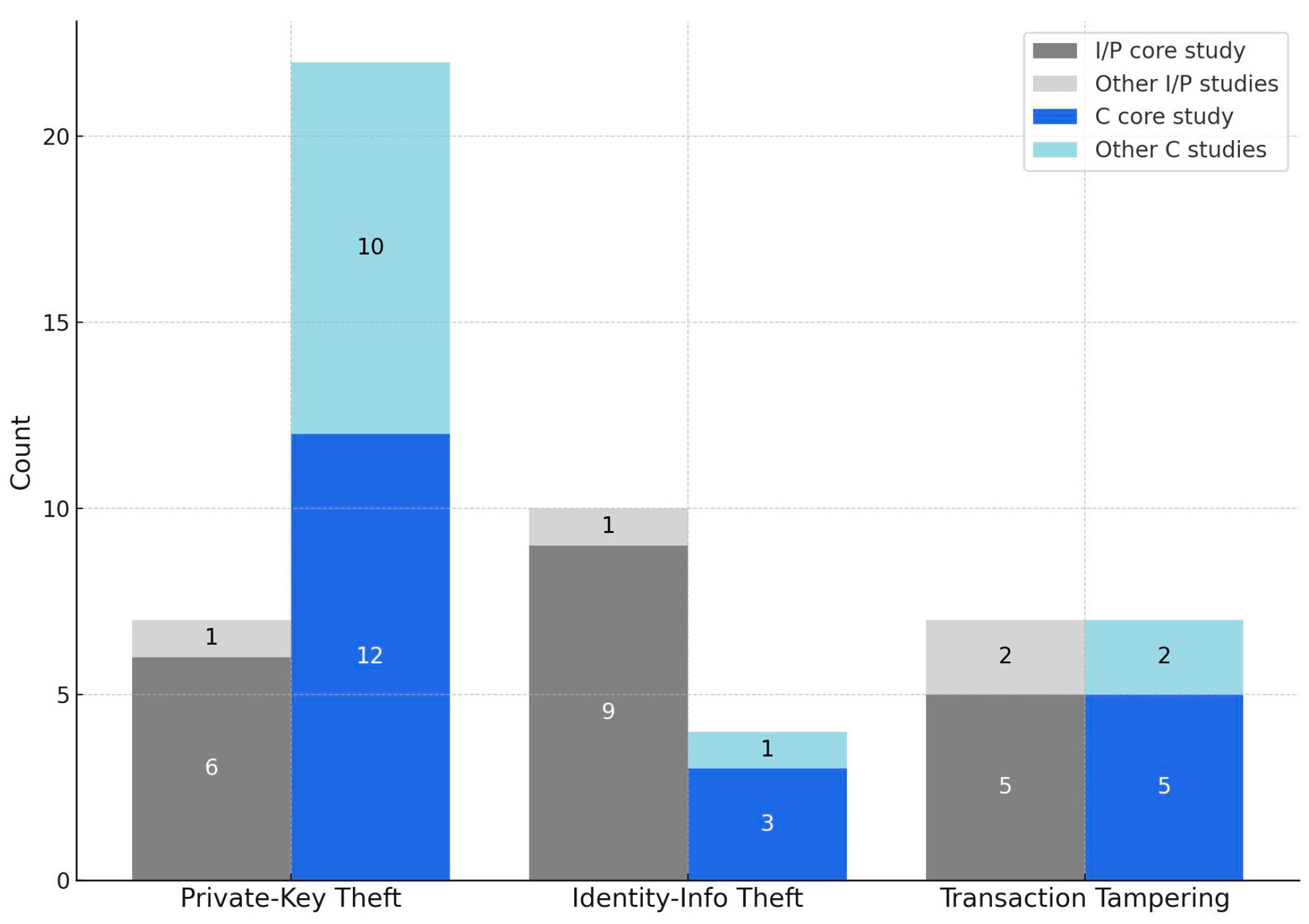
4.2. Literature-Based Threat Analysis of Electronic Wallets
4.3. Risk Matrix and Incident-Adjusted Quantitative Analysis
4.4. Implications and Integrated Security Requirements
5. Multi-Dimensional Risk Response Analysis for Electronic Wallets
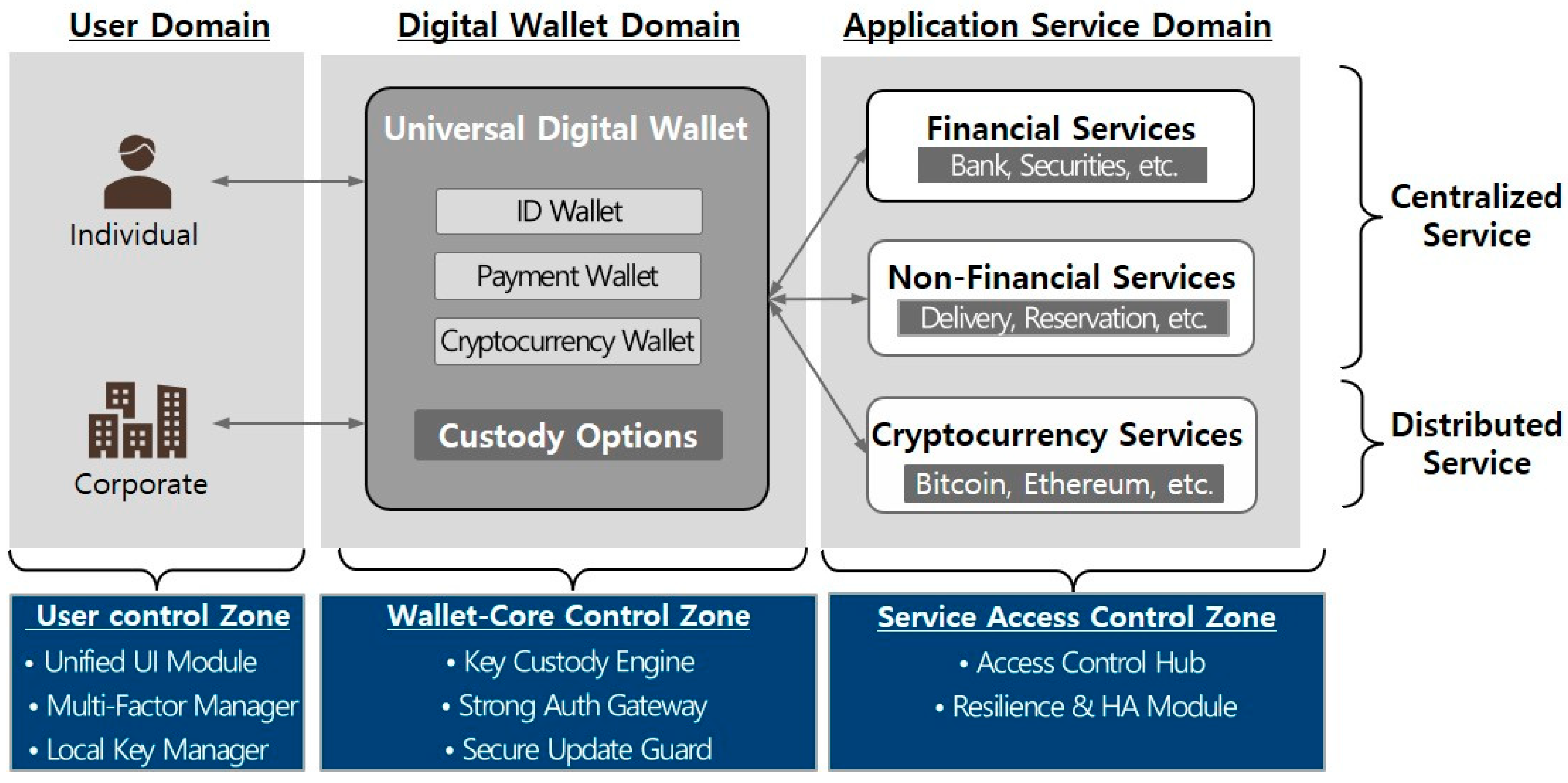
5.1. Security Measures in a Universal Wallet Environment
- (a)
- Unified UI Module: This module bundles ID, payment, and crypto asset wallets into a single interface, providing a consistent UX even in super-app and mini-app environments. It contributes to suppressing T1 (credential theft) and T2 (session hijacking) and protects the session through integrity signing (token binding).
- (b)
- Multi-Factor Manager: This module flexibly combines primary authentication based on biometrics or passkeys with secondary authentication based on OTP or FIDO and also supports a central reregistration + distributed recovery approach. It minimizes user-side errors that lead not only to T1 and T2 but also T3 (key theft) and T4 (key loss).
- (c)
- Local Key Manager: This is designed so that, in addition to user certificates, fragments (or shares) of a private key can be stored and signed on the device, which reduces T3 and T4. When a crypto wallet requires distributed recovery, it also helps safely store MPC shares on the user’s device.
- (a)
- Key Custody Engine: By distributing private key management through MPC, it fundamentally mitigates T3 (private key theft) and T4 (key loss). It removes the single point of failure, ensuring that the entire key is not leaked even in the event of an insider attack or a single hacking incident.
- (b)
- Strong Auth Gateway: By implementing hierarchical identity proof, this unifies the different levels of trust in ID, payment, and crypto wallets into a single authentication flow. It serves as a second line of defense at the core level against T1 and T2 and is also responsible for session integrity and token validation.
- (c)
- Secure Update Guard: This performs triple-layer defense—signature verification → integrity measurement → runtime monitoring—for the wallet core, plugins, and mini-apps. It suppresses T6 (malware or supply chain attacks) and strengthens software supply chain security in a super-app environment where many external vendors and SDKs are integrated.
- (a)
- Access Control Hub: Through a finely grained RBAC/ABAC policy engine, this dynamically controls payment limits, the scope of smart contract calls, and user privileges. It blocks T5 (transaction tampering) and T2 (privilege misuse) at the approval stage and defends against retransmission or double-spending attempts during transactions.
- (b)
- Resilience and HA Module: By using a hardware root of trust based on TEE/PUF and a dual-node (hot-standby) configuration, this mitigates T7 (hardware side channel attacks) and T8 (availability disruption). Even in the event of a large-scale DDoS attack or node failure, it maintains service continuity through distributed nodes and disaster recovery (BC/DR) procedures.
5.2. Scenario-Based Threat Analysis and Quantitative Evaluation
5.2.1. Scenario Concept and Security Modules
5.2.2. Deterministic Stress Test and Quantitative Results
5.3. Discussion
5.3.1. Industrial Implications and Risk Mitigation Model
5.3.2. Additional Challenges
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Deloitte. A Market Overview of Custody for Digital Assets. In Digital Custodian Whitepaper; DASA: Austin, TX, USA, 2020. [Google Scholar]
- Lim, H.J.; Hwang, S. Proposal for New Work Item: Technical Guideline for Digital Asset Custodians Using TTP-Based Key Management Service; Contribution 341; ITU-T SG17: Geneva, Switzerland, 2023. [Google Scholar]
- Kim, M.; Lim, H.J. Analysis of Electronic Wallet Types and Security Features. J. Internet Comput. Serv. 2024, 25, 6. [Google Scholar]
- ENISA. An Introduction to Digital Currencies and Distributed Ledger Technologies; ENISA Report; ENISA: Athens, Greece, 2021. [Google Scholar]
- Financial Security Institute. Implementation of a Secure General-Purpose E-Wallet for Digital Assets. Research Report. 2023. Available online: https://www.fsec.or.kr/bbs/detail?menuNo=69&bbsNo=11387 (accessed on 15 May 2025).
- Bank of Korea. Analysis of the Current Status and Security Requirements of Digital Wallets. In Financial Informatization Promotion Council Research Report; Bank of Korea: Seoul, Republic of Korea, 2022. [Google Scholar]
- Kang, K. Trends in Blockchain and Web 3.0 Technology Ecosystems. Available online: http://weekly.tta.or.kr/weekly/files/20223709033746_weekly.pdf (accessed on 15 May 2025).
- Jokić, S.; Cvetković, A.S.; Adamović, S.; Ristić, N.; Spalević, P. Comparative Analysis of Cryptocurrency Wallets vs Traditional Wallets. Sci. Rev. Artic. 2019, 65, 65–75. [Google Scholar] [CrossRef]
- Cho, Y.; Jin, S. An Electronic ID Wallet System Providing User-Centered ID Management Functions. J. Electron. Telecommun. Trends 2008, 23, 10. [Google Scholar] [CrossRef]
- Jung, Y.; Lim, S.; Yi, O.; Lim, J.; Jin, S. A Secure Mobile Digital ID Wallet Using USIM of 3GPP. In Proceedings of the Fourth EuroFGI Workshop on Wireless and Mobility, Barcelona, Spain, 16–18 January 2008. [Google Scholar]
- Song, D.; Lim, S.; Lim, J.; Yi, O. A Digital ID Wallet User-oriented Mechanism in a Mobile Environment. J. Korea Inst. Inf. Secur. Cryptol. 2007, 17, 57–64. [Google Scholar] [CrossRef]
- Jøsang, A.; Rosenberger, C.; Miralabé, L.; Klevjer, H.; Varmedal, K.A.; Daveau, J.; Husa, K.E.; Taugbøl, P. Local User-Centric Identity Management. J. Trust. Manag. 2015, 2, 1–28. [Google Scholar] [CrossRef][Green Version]
- Steffens, E.J.; Nennker, A.; Ren, Z.; Yin, M.; Schneider, L. The SIM-Based Mobile Wallet. In Proceedings of the IEEE INGN Conference, Bordeaux, France, 26–29 October 2009. [Google Scholar] [CrossRef]
- Zhao, H.; Muftic, S. The Concept of Secure Mobile Wallet. In Proceedings of the IEEE WorldCIS Conference, London, UK, 21–23 February 2011. [Google Scholar] [CrossRef]
- Mjolsnes, S.F.; Rong, C. Localized Credentials for Server Assisted Mobile Wallet. In Proceedings of the IEEE ICCNMC Conference, Beijing, China, 16 October–19 October 2001. [Google Scholar] [CrossRef]
- European Central Bank. Study on Payment Methods and Digital Wallet. 2023. Available online: https://www.ecb.europa.eu/press/pr/date/2023/html/ecb.pr230424_1_annex~93abdb80da.en.pdf (accessed on 15 May 2025).
- Kim, T. Discussion on the Ecosystem of NFC Mobile Payment Services and the Role of TSM. Korea Information and Communications. Available online: https://www.kisdi.re.kr/report/view.do?key=m2101113025931&masterId=3934566&arrMasterId=3934566&artId=531290 (accessed on 15 May 2025).
- ENISA. Security of Mobile Payments and Digital Wallets; European Union Agency for Network and Information Security: Attiki, Greece, 2016. [Google Scholar]
- Heo, S. Analysis of Mobile Short-Range Payment Technology and Service Status. Payment Syst. Inf. Technol. 2013, 53, 1–32. Available online: https://research.kftc.or.kr/research/tech/5412 (accessed on 15 May 2025).
- Korea Internet; Security Agency (KISA). Cybersecurity Threats and Security Requirements for Digital Wallets. KISA Insight 2022. Available online: https://www.kisa.or.kr/20301?page=1 (accessed on 15 May 2025).
- Suratkar, S.; Shirole, M.; Bhirud, S. Cryptocurrency Wallet: A Review. In Proceedings of the IEEE ICCCSP Conference, Chennai, India, 28–29 September 2020. [Google Scholar] [CrossRef]
- Hardjono, T.; Lipton, A.; Pentland, A. Towards a Public Key Management Framework for Virtual Assets and Virtual Asset Service Providers. MIT J. FinTech 2021, 1, 2050001. [Google Scholar] [CrossRef]
- 2140.5-2020; IEEE Standard for a Custodian Framework of Cryptocurrency. IEEE: New York, NY, USA, 2020. [CrossRef]
- Jaroucheh, Z.; Ghaleb, B. Crypto Assets Custody: Taxonomy, Components, and Open Challenges. In Proceedings of the IEEE ICBC Conference, Dubai, United Arab Emirates, 1–5 May 2023. [Google Scholar] [CrossRef]
- Di Nicola, V.; Longo, R.; Mazzone, F.; Russo, G. Resilient Custody of Crypto-Assets, and Threshold Multisignatures. Mathematics 2020, 8, 1773. [Google Scholar] [CrossRef]
- Eyal, I. On Cryptocurrency Wallet Design. In Proceedings of the 3rd International Conference on Blockchain Economics, Security and Protocols, Virtual, 18–19 November 2021. [Google Scholar] [CrossRef]
- Jørgensen, K.P.; Beck, R. Universal Wallets. Bus. Inf. Syst. Eng. 2022, 64, 115–125. [Google Scholar] [CrossRef]
- Anwar, R.H.; Hussain, S.R.; Raza, M.T. In Wallet We Trust: Bypassing the Digital Wallets Payment Security for Free Shopping. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security ’24), Philadelphia, PA, USA, 14 August 2024. [Google Scholar]
- Keršič, V.; Vidovic, U.; Vrecko, A.; Domajnko, M.; Turkanović, M. Orchestrating Digital Wallets for On- and Off-Chain Decentralized Identity Management. IEEE Access 2023, 11, 78135–78151. [Google Scholar] [CrossRef]
- Deshpande, V.; Harish, J.; Khade, A.V. A Practical Recovery Mechanism for Blockchain Hardware Wallets. IEEE Access 2024, 12, 169928–169944. [Google Scholar] [CrossRef]
- Sandeep, S.K.V.; Fawad, I.; Gagan, A.R.; Reddy, B.K.; Avanish, B.; Dileep, V. Secure Bitcoin Hardware Wallet Design, Implementation, and Security Analysis. In Proceedings of the 7th IEEE International Conference ESCI, Pune, Maharashtra, India, 5–7 March 2025. [Google Scholar] [CrossRef]
- Houy, S.; Schmid, P.; Bartel, A. Security Aspects of Cryptocurrency Wallets—A Systematic Literature Review. ACM Comput. Surv. 2023, 56, 1–31. [Google Scholar] [CrossRef]
- Kouliaridis, V.; Karopoulos, G.; Kambourakis, G. Assessing the Security and Privacy of Android Official ID Wallet Apps. Information 2023, 14, 457. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology (NIST). Special Publication 800-63 Series (1, 2, and 3); CreateSpace: Scotts Valley, CA, USA, 2017. [Google Scholar]
- Patnode, M. Authentication in a Heterogeneous Environment. 2005. Available online: https://www.usenix.org/legacy/event/lisa08/tech/patnode_talk.pdf (accessed on 15 May 2025).
- Abe, T.; Itoh, H.; Takahashi, K. Implementing Identity Provider on Mobile Phone. In Proceedings of the DIM’07 Conference, Fairfax, VA, USA, 2 November 2007. [Google Scholar] [CrossRef]
- TTAK.KO-12.0359; Framework for Identity Managementusing Decentralized Identity. TTA Natl. Stand: Seongnam, Republic of Korea, 2020.
- Jin, S. EU eIDAS 2.0 and the European Digital Identity Wallet. TTA J. 2024, 211, 90–95. Available online: https://www.tta.or.kr/tta/preportNewsNDownload.do?sfn=20240311011443491_ZwAw.pdf (accessed on 15 May 2025).
- Lee, J. The Emergence of the European Digital Identity Wallet and Its Impact on the Korean Financial Sector. e-Finance Financ. Secur. 2024, 34, 41–54. Available online: https://www.fsec.or.kr/bbs/detail?menuNo=242&bbsNo=11385 (accessed on 15 May 2025).
- Kim, J. Trends and Security Considerations of Digital Wallets. Electron. e-Finance Financ. Secur. 2022, 27, 56–94. Available online: https://www.fsec.or.kr/bbs/detail?menuNo=242&bbsNo=6756 (accessed on 15 May 2025).
- Kim, S. Current Status and Implications of New Types of Payment Services at Home and Abroad. Payment Syst. Inf. Technol. 2013, 51, 1–30. Available online: https://research.kftc.or.kr/research/tech/5347 (accessed on 15 May 2025).
- Financial Security Institute. Research on Strengthening Security Technology for App Cards. In App Card Consortium Research Report; Financial Security Institute: Seoul, Republic of Korea, 2014. [Google Scholar]
- Lee, D. Trends and Implications of Mobile Payment Innovations. In BOK Issue Note; Bank of Korea: Seoul, Republic of Korea, 2013. [Google Scholar]
- Kim, T. TSM Models and Implications in Mobile Payment Services. Payment Syst. Inf. Technol. 2013, 51, 31–57. Available online: https://research.kftc.or.kr/research/tech/5346 (accessed on 15 May 2025).
- ISO/TR 23576; Blockchain and Distributed Ledger Technologies—Security Management of Digital Asset Custodians. International Organization for Standardization (ISO): Geneva, Switzerland, 2020.
- Global Digital Finance. Crypto Asset Safekeeping and Custody: Key Considerations and Takeaways. In Global Digital Finance Whitepaper; Global Digital Finance: London, UK, 2019; Available online: https://www.gdf.io/resources/crypto-asset-safekeeping-custody-key-considerations-and-takeaways (accessed on 15 May 2025).
- Std 2842-2021; IEEE Standards Association. Practice for Secure Multi-Party Computation. IEEE Comput. Soc.: Washington, DC, USA, 2021.
- Hiltgen, A.; Kramp, T.; Weigold, T. Secure Internet Banking Authentication. IEEE Secur. Priv. 2006, 4, 21–29. [Google Scholar] [CrossRef]
- ISO/IEC27005; 3rd ed. Information Technology—Security Techniques—Information Security Risk Management. ISO/IEC: Geneva, Switzerland, July 2018.
- Edge, K.; Raines, R.; Grimaila, M.; Baldwin, R.; Bennington, R.; Reuter, C. The Use of Attack and Protection Trees to Analyze Security for an Online Banking System. In Proceedings of the IEEE HICSS Conference, Waikoloa, HI, USA, 3–6 January 2007. [Google Scholar] [CrossRef]
- Eisentraut, J.; Holzer, S.; Klioba, K.; Křetínský, J.; Pin, L.; Wagner, A. Assessing Security of Cryptocurrencies with Attack-Defense Trees: Proof of Concept and Future Directions. In ICTAC; Springer: Berlin/Heidelberg, Germany, 2021; Volume LNCS 12819, pp. 214–234. [Google Scholar] [CrossRef]
- Chung, J.; Kang, H. Study of Methodologies for Compliance with the Travel Rules When Trading Virtual Assets by Virtual Asset Operators (VASPs)With a Focus on the FATF’s Interpretative Note to Recommendation 15(INR 15), Paragraph 7(b). Korean J. Law Econ. 2020, 17, 331–352. [Google Scholar] [CrossRef]
- Lee, D. Review of Key Security Threats and Considerations for Super Apps. e-Finance Financ. Secur. 2023, 33, 124–133. Available online: https://www.fsec.or.kr/bbs/detail?menuNo=242&bbsNo=11341 (accessed on 15 May 2025).
- Weinert, A. Your Pa$$word doesn’t matter, Microsoft Tech Community Blog. 10 March 2020. Available online: https://techcommunity.microsoft.com/t5/azure-active-directory-identity/your-pa-ord-doesn-t-matter/ba-p/731984 (accessed on 1 June 2025).
- Google Security Blog, New research: How Effective is Basic Account Hygiene at Preventing Hijacking. 17 May 2019. Available online: https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html (accessed on 1 June 2025).
- Fireblocks, Secure MPC: Eliminating the Single Point of Compromise—MPC-CMP Whitepaper, Rev. 1 September 2023. Available online: https://www.fireblocks.com/wp-content/uploads/2023/09/Secure-MPC-Framework-OP.pdf (accessed on 1 June 2025).
- IBM Security and Ponemon Institute. Cost of a Data Breach Report 2024; IBM Corp.: Armonk, NY, USA, 2024; Available online: https://www.ibm.com/reports/data-breach (accessed on 1 June 2025).
- TRM Labs. 2025 Crypto Crime Report; TRM Labs Inc.: San Francisco, CA, USA, February 2025; Available online: https://www.trmlabs.com/resources/reports/2025-crypto-crime-report (accessed on 1 June 2025).
- Chainalysis Team, $2.2 Billion Stolen from Crypto Platforms in 2024, but Hacked Volumes Stagnate Toward Year-End as DPRK Slows Activity, Chainalysis Blog. 19 December 2024. Available online: https://www.chainalysis.com/blog/crypto-hacking-stolen-funds-2025/ (accessed on 1 June 2025).
- MazeBolt Technologies, Cost of Damaging DDoS Attacks in 2025: Annual Trends Report, MazeBolt Blog. February 2025. Available online: https://mazebolt.com/blog/cost-of-damaging-ddos-attacks-in-2025-annual-trends-report/ (accessed on 1 June 2025).

| Stage | Features | Major Services |
|---|---|---|
| Internet Expansion Period (Late 1990s ~) |
| e-Commerce services such as Amazon, Alibaba, eBay, and PayPal |
| Mobile Expansion Period (2010s ~) |
| Alipay, Amazon Pay, Google Wallet, Samsung Wallet, and Apple Wallet |
| Blockchain Expansion Period (2020 ~) |
| Metamask Wallet, Decent Wallet, Ledger Vault Wallet, Hexlant Octet, BitGo, and other custodial wallets |
| Problem Setting and Related Studies | Identified Gaps | How Our Paper Addresses the Gaps |
|---|---|---|
|
|
|
|
|
|
| Type | Description | Examples |
|---|---|---|
| Personal Information | Information to verify personal identity | Resident registration card, driver’s license, etc. |
| Ownership Information | Information to confirm qualifications, authority, or ownership | Certificates, card information, etc. |
| Activity Information | Information for proof of actions and activities | Transaction records, statements of accounts, etc. |
| Field | Examples |
|---|---|
| Payment Services | Offline merchant payments via mobile cards, etc. Mobile peer-to-peer (P2P), peer-to-business (P2B), and business-to-business (B2B) transfers |
| Commerce Services | Various loyalty services such as coupons and discounts Various tickets and vouchers Location-based services |
| Banking Services | Bill payments, pension deposits, and withdrawals Account information and transaction history inquiries Investment and asset management |
| ID Services | Various forms of identification Electronic certificates—access restrictions through login, etc. |
| Category | Information Storage Method | Transmission Method | Examples |
|---|---|---|---|
| NFC | USIM | Barcode Reader | App Card, Google Wallet, etc. |
| Micro SD | |||
| NFC | Apple Pay, etc. | ||
| Embedded SE | |||
| MST | Samsung Wallet, etc. | ||
| Non-NFC | Server |
| Implementation Method | Details | Implementation Forms |
|---|---|---|
| SW (Software) |
| Web wallets, mobile wallets |
| HW (Hardware) |
| USB wallets, smart card wallet |
| Cloud (Server-based) |
| Centralized exchange wallets, proprietary wallet services |
| Type | Characteristics | Major Operators |
|---|---|---|
| ⓐ | The individual or business directly manages the private key, which is the means of accessing the asset. | Decent Wallet (Seoul, Republic of Korea), WEMIX Wallet Wallet (Seoul, Republic of Korea), Ledger Vault (Paris Region, France) |
| ⓑ | The customer registers a wallet they own (linking the account and wallet address) or trades through an exchange wallet. | Digital asset exchange platforms |
| ⓒ | The business stores the customer’s private key. | Korea Digital Asset Custody (KDAC), Korea Digital Asset (KODA), Coinbase Custody (USA), etc. |
| The encrypted private key of the asset owner is backed up and stored (no control rights). | Kakao Klip Wallet (Seongnam, Republic of Korea), WEMIX Play Wallet (Seoul, South Korea), etc. | |
| ⓓ | Using cryptographic techniques such as multi-signature, the control rights of the private key are shared and jointly controlled by the custodian and the customer. | Hexlant Octet Wallet (Seoul, Republic of Korea), Hatch Labs Hennessy Wallet (Republic of Korea), SKT TopPort Wallet (Seoul, Republic of Korea), BitGo (Palo Alto, CA, USA), Fireblocks (New York, NY, USA), Coinbase WaaS (San Francisco, CA, USA), etc. |
| Category | Kakao Klip | SKT Topport | Hexlant Octet | Ledger Vault | BitGo | Coinbase Custody | Fireblocks | Coinbase WaaS |
|---|---|---|---|---|---|---|---|---|
| Private Key Management Authority | Service Provider | All Participants | All Participants | Service Provider | All Participants | Service Provider | Service Provider | All Participants |
| Custody Method | Proprietary Custody | Partial Custody | Partial Custody | Self-Custody | Partial Custody | Proprietary Custody | Partial Custody | Partial Custody |
| Key Custody Applied Technology | - | MPC | Multi-Signature | - | Multi-Signature | MPC, Multi-Signature | MPC | MPC |
| Category | Digital ID Wallet | Digital Payment Wallet | Digital Cryptocurrency Wallet | |
|---|---|---|---|---|
| Functions and Features | Emergence Period | Early 2000s | Late 2000s | After 2018 |
| Functions |
|
|
| |
| Major Characteristics |
|
|
| |
| Major Participants |
|
|
| |
| Service Examples |
|
|
| |
| Security Features | Primary Information | Certificates and certifications, including IDs and resident registration numbers | Payment information, such as credit card numbers and account numbers | Private keys, crypto assets (NFTs, etc.) |
| Purpose of User Instructions | Request for entity verification | Confirmation of transaction intention | Confirmation of transaction intention | |
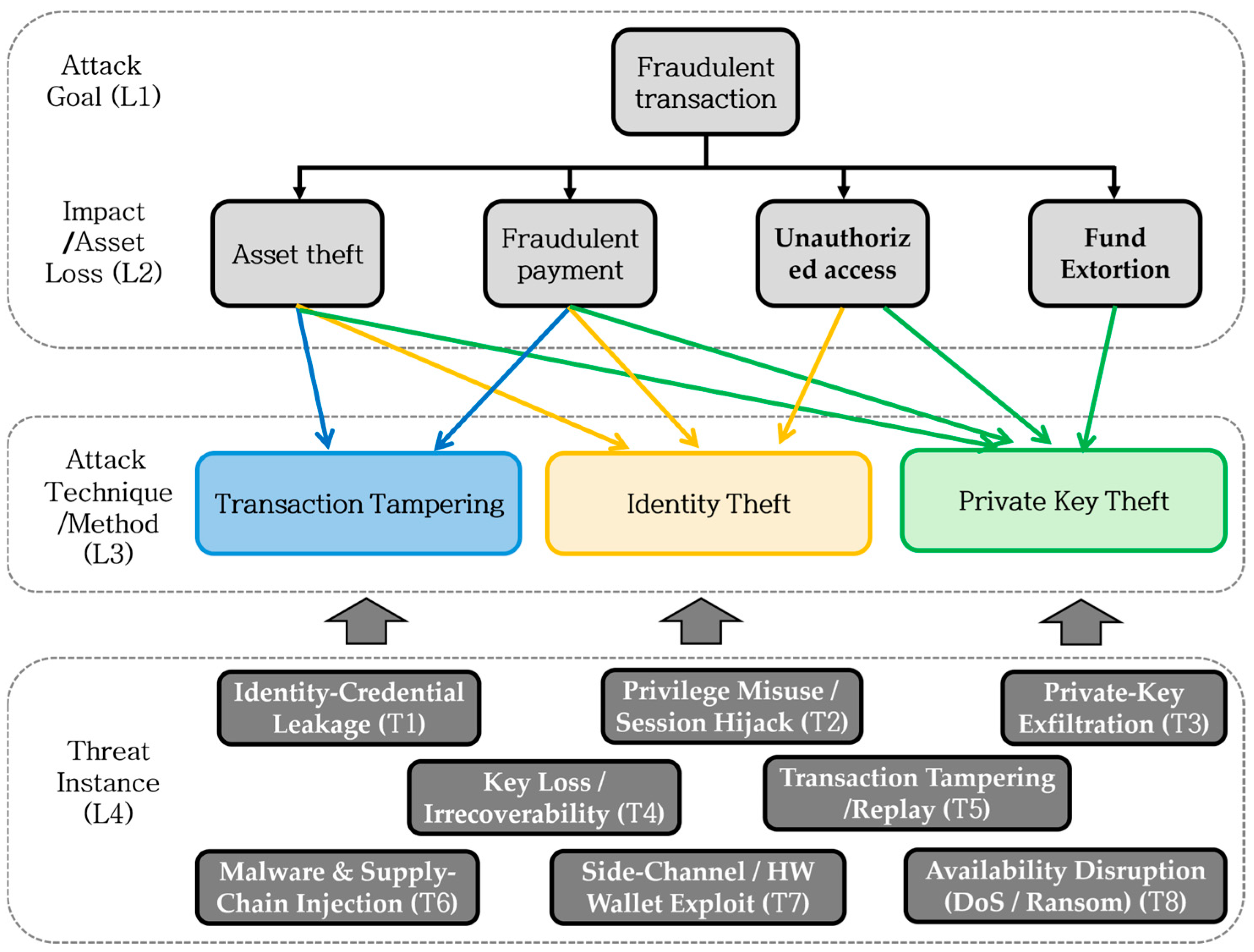
| Major Threats | ID information exposure and theft, identity forgery | Payment information exposure and theft, transaction integrity compromise | Private key theft, privilege misuse | |
| Access Control Enhancement | Multi-factor authentication, transaction signing [34] | Tokenization, multi-factor authentication (device information authentication, biometric authentication, etc.) | Distributed key management via partial custody approach | |
| Primary Information Storage | Security tokens, embedded SE (TEE, etc.) | Embedded SE (i.e., TEE, etc.), tokenization (server-based payment model) | Distributed custodian wallet | |
| Recovery Method (Access to Existing Records) | Reverification and reregistration (yes) | Reverification and reregistration (yes) | Not possible without a separate mechanism but can be implemented using cryptographic methods such as multi-signature and MPC (yes) |
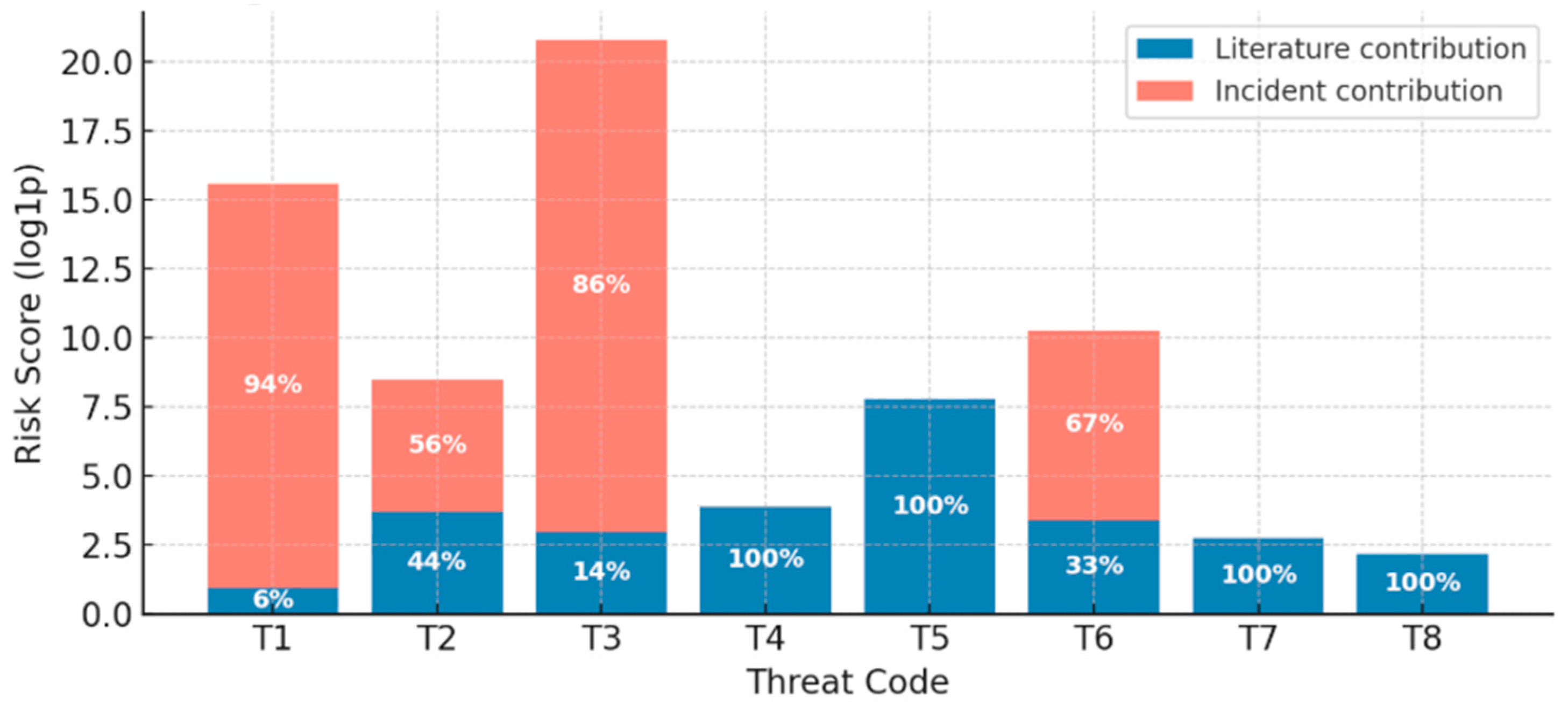
| Threat Code | Threat Name | Lit-Freq | Incident-Freq | Severity (1–5) | Risk (log1p) |
|---|---|---|---|---|---|
| T1 | Identity Credential Leakage | 11 | 169 | 3 | 15.6 |
| T2 | Privilege Misuse or Session Hijack | 7 | 9 | 3 | 8.5 |
| T3 | Private Key Exfiltration | 9 | 54 | 5 | 20.8 |
| T4 | Key Loss or Irrecoverability | 6 | 0 | 2 | 3.9 |
| T5 | Transaction Tampering or Replay | 6 | 0 | 4 | 7.8 |
| T6 | Malware and Supply Chain Injection | 4 | 8 | 4 | 10.3 |
| T7 | Side Channel or HW Wallet Exploit | 1 | 0 | 4 | 2.8 |
| T8 | Availability Disruption (DoS or Ransom) | 2 | 0 | 2 | 2.2 |
| Risk Factor | Loss | Leakage | Theft | Misuse | Mapped Threat Code(s) | |
|---|---|---|---|---|---|---|
| ⓐ | Intentional Misbehavior 1 | O | O | O | O | T2, T3 |
| ⓑ | External Attack or Intrusion 2 | O | O | O | O | T1, T5, T6, T7, T8 |
| ⓒ | Unintentional Misbehavior 3 | O | O | X | X | T4, T6 |
| Scenario | Threat | Frequency (Cases/Year) | Single Incident Impact (USD M) | (USD M/Year) | (USD M) | Control Effectiveness | Risk Reduction Rate | |
|---|---|---|---|---|---|---|---|---|
| ① Integrated Payment and Trading Super-App | T1 | 3 | 0.35 1 | 1.05 | 10 | MFA·access control hub reduced T1 and T2 by 70% and T5 by 60% | 0.32 | 62% |
| T2 | 2 | 0.15 1 | 0.30 | – | 0.09 | |||
| T5 | 1 | 4.0 2 | 4.00 | – | 1.60 | |||
| Total | 5.35 | 2.01 | ||||||
| ② MPC-Based Distributed Key Recovery | T3 | 0.5 | 14.0 3 | 7.00 | 20 | MPC·HW shield reduce all items by 80% | 1.40 | 80% |
| T4 | 1 | 2.0 1 | 2.00 | – | 0.40 | |||
| T7 | 0.3 | 5.0 2 | 1.50 | – | 0.30 | |||
| Total | 10.50 | 2.10 | ||||||
| ③ CBDC Issuance and Burning Approval | T5 | 0.2 | 30.0 2 | 6.00 | 30 | Threshold-Sig + DDoS absorption reduced T5 by 90% and T8 by 70% | 0.60 | 86% |
| T8 | 3 | 0.50 4 | 1.50 | – | 0.45 | |||
| Total | 7.50 | 1.05 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lim, H.-J.; Lee, S.; Kim, M.; Lee, W. Comparative Analysis of Security Features and Risks in Digital Asset Wallets. Electronics 2025, 14, 2436. https://doi.org/10.3390/electronics14122436
Lim H-J, Lee S, Kim M, Lee W. Comparative Analysis of Security Features and Risks in Digital Asset Wallets. Electronics. 2025; 14(12):2436. https://doi.org/10.3390/electronics14122436
Chicago/Turabian StyleLim, Hyung-Jin, Sokjoon Lee, Moonseong Kim, and Woochan Lee. 2025. "Comparative Analysis of Security Features and Risks in Digital Asset Wallets" Electronics 14, no. 12: 2436. https://doi.org/10.3390/electronics14122436
APA StyleLim, H.-J., Lee, S., Kim, M., & Lee, W. (2025). Comparative Analysis of Security Features and Risks in Digital Asset Wallets. Electronics, 14(12), 2436. https://doi.org/10.3390/electronics14122436







