Threat Classification and Vulnerability Analysis on 5G Firmware Over-the-Air Updates for Mobile and Automotive Platforms
Abstract
1. Introduction
2. Background
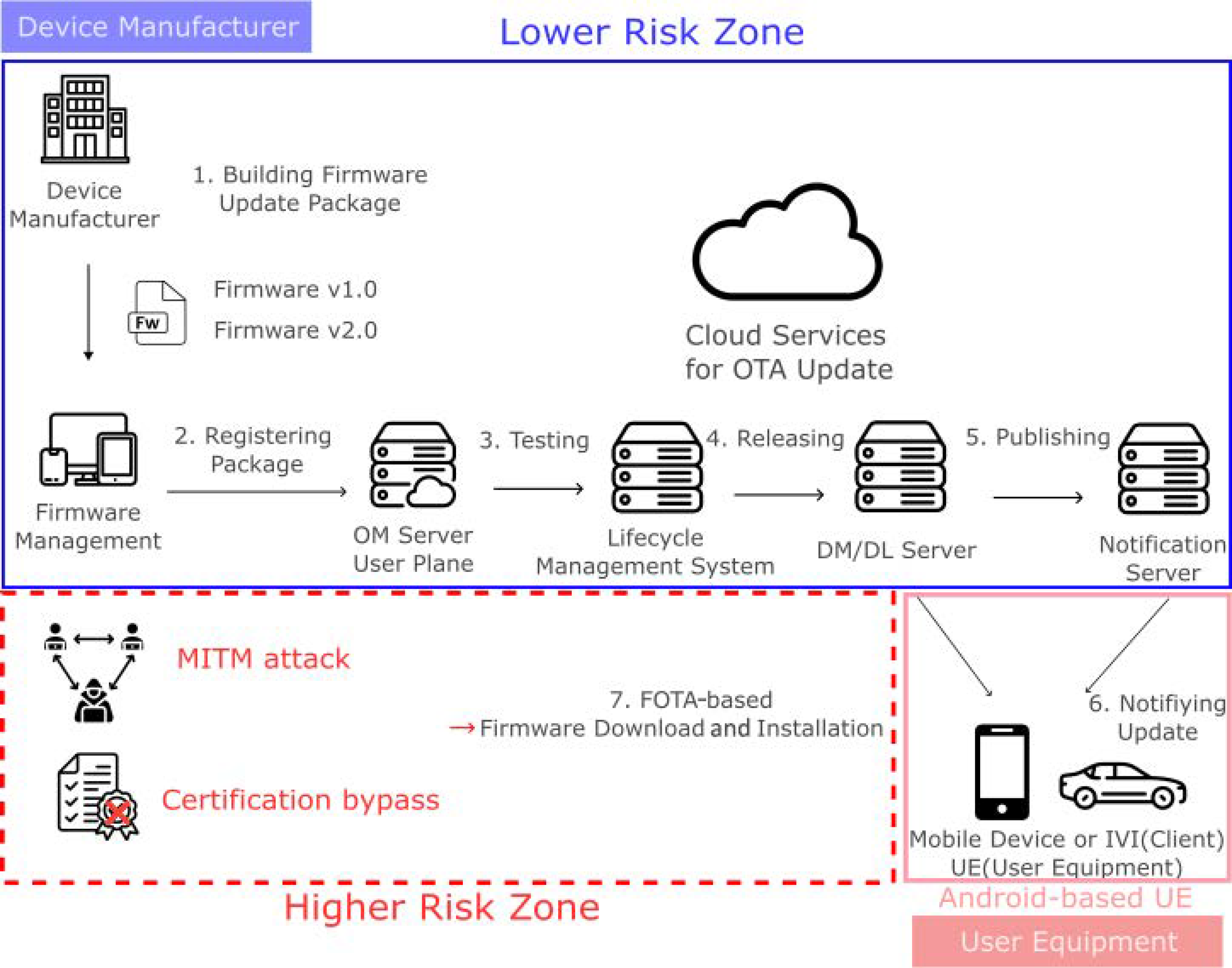
2.1. FOTA Firmware Update Process Using OMA-DM
- Building Firmware Update Package: Different versions of firmware are available, and they update to the latest version. The manufacturer creates a new firmware update package for the update and registers it with the administrative system that manages the operator’s firmware by version.
- Registering Package: The update package from the deployment phase is registered with the OM Server in the User Plane.
- Testing: Test the firmware for functionality and integrity before deploying it to a lifecycle management system.
- Releasing: When it is time to deploy the firmware, release the new version to the DM(Device Management)/DL(Download) server.
- Publishing: The DM/DL server sends a message from the notification server to the device, notifying it that a new update is available.
- Notifying Update: The device receives a notification from the notification server indicating that a new update is available.
- FOTA based Firmware Download & Installation: FOTA based Firmware Download & Installation: After authenticating with the DM server, the mobile device downloads the new firmware update package using the download descriptor. Subsequently, the integrity of the firmware update package is confirmed by comparing its hash value to the hash value received [17]. During this process, MitM and certificate bypass attacks are potential risks.
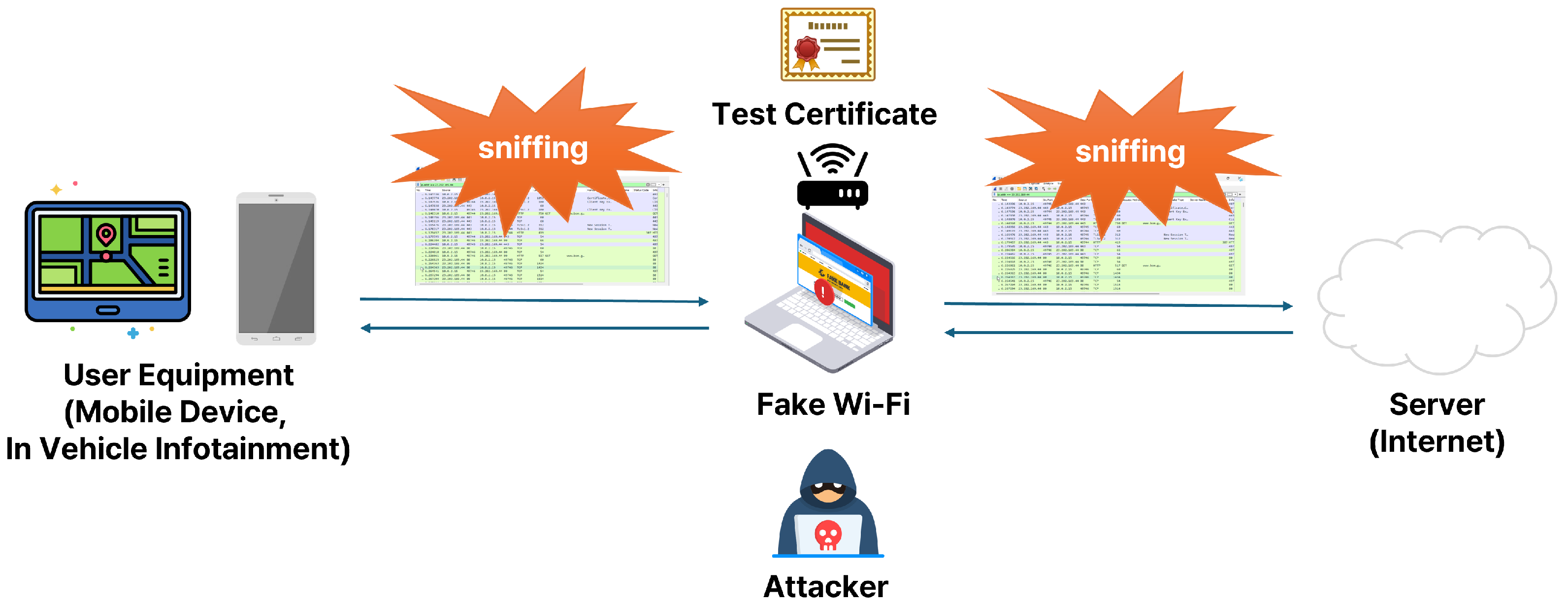
2.2. Man-in-the-Middle (MitM) Attack
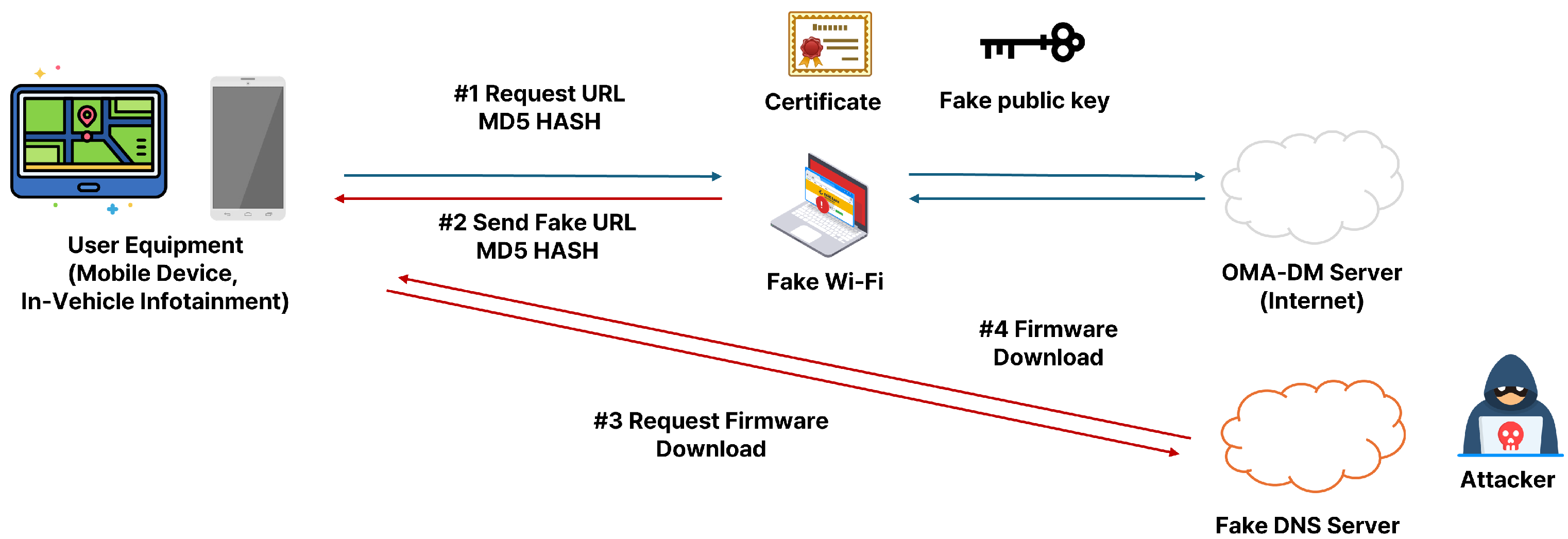
2.3. Bypass Certification
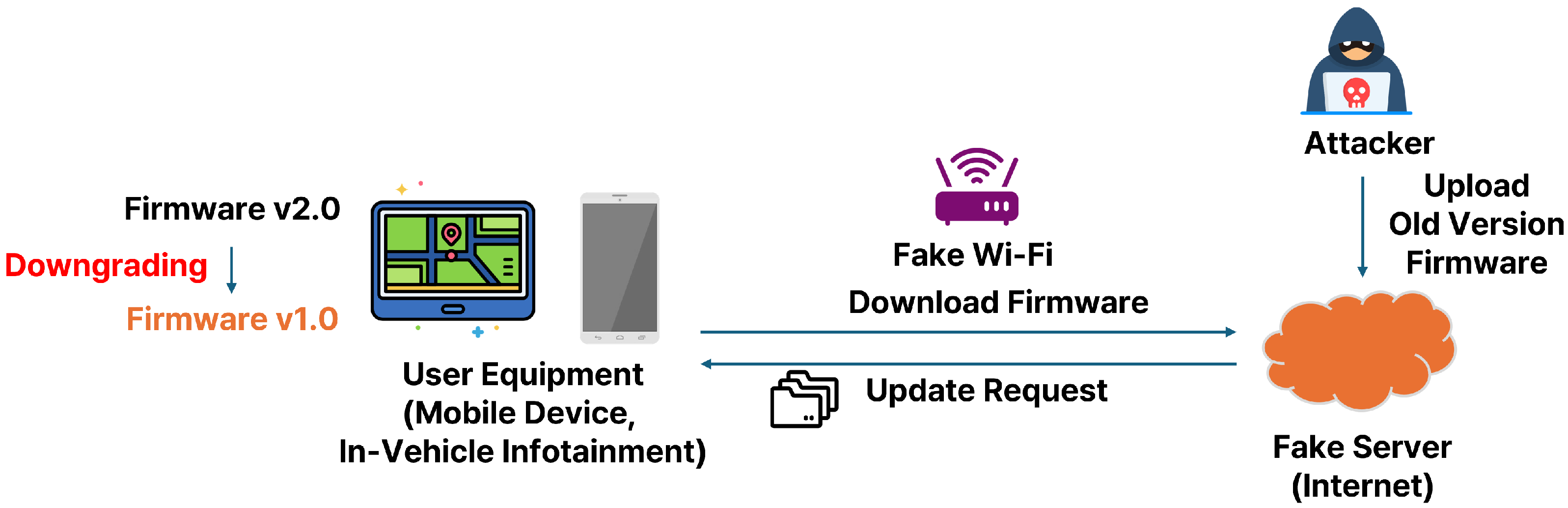
2.4. Downgrade Attack
3. Related Work
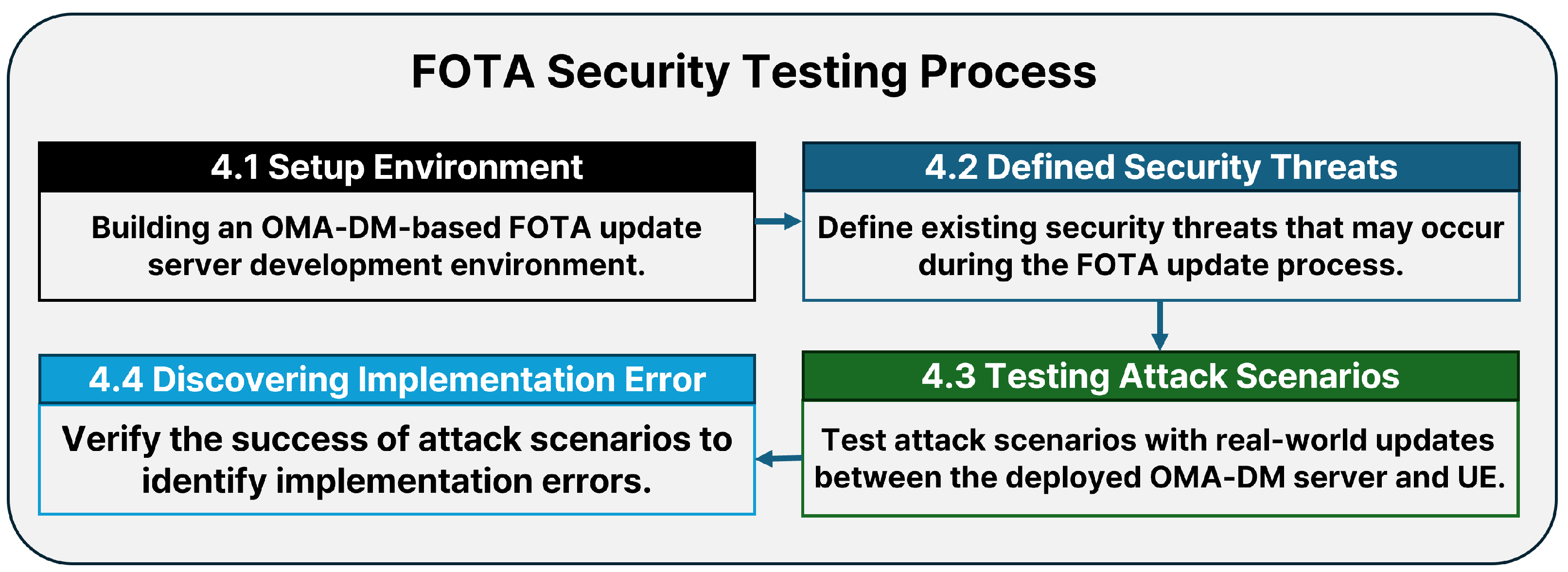
4. Security Testing Methods for the FOTA Update Process
4.1. Setup Environment
- The registered update package goes through a series of tests and then moves to the release phase.
- The tested update package is uploaded to the DL server, and subsequently, the DM server notifies the UE of the new update release via the notification server.
- The UE mutually authenticates with the DM server and retrieves a download descriptor from the DL server.
- The UE extracts the objectURI field from the download descriptor to determine the exact location of the firmware.
- The UE downloads the firmware, computes the MD5 hash value, and verifies it against the MD5 hash value in the installParam field of the download descriptor to ensure the integrity of the firmware update package.
- If the UE client successfully completes the integrity check, it sends a SUCCESS message to the entity in the installNotifyURI field and initiates the firmware update.
4.2. Define Security Threats
4.3. Testing Attack Scenarios
4.4. Discovering Implementation Error
5. Verification of Security Threats and Attack Scenarios for the FOTA Update Process
5.1. Bypassing Certificate Verification During the FOTA Update Process
5.2. Inducing a Tampered Firmware Update During the FOTA Update Process
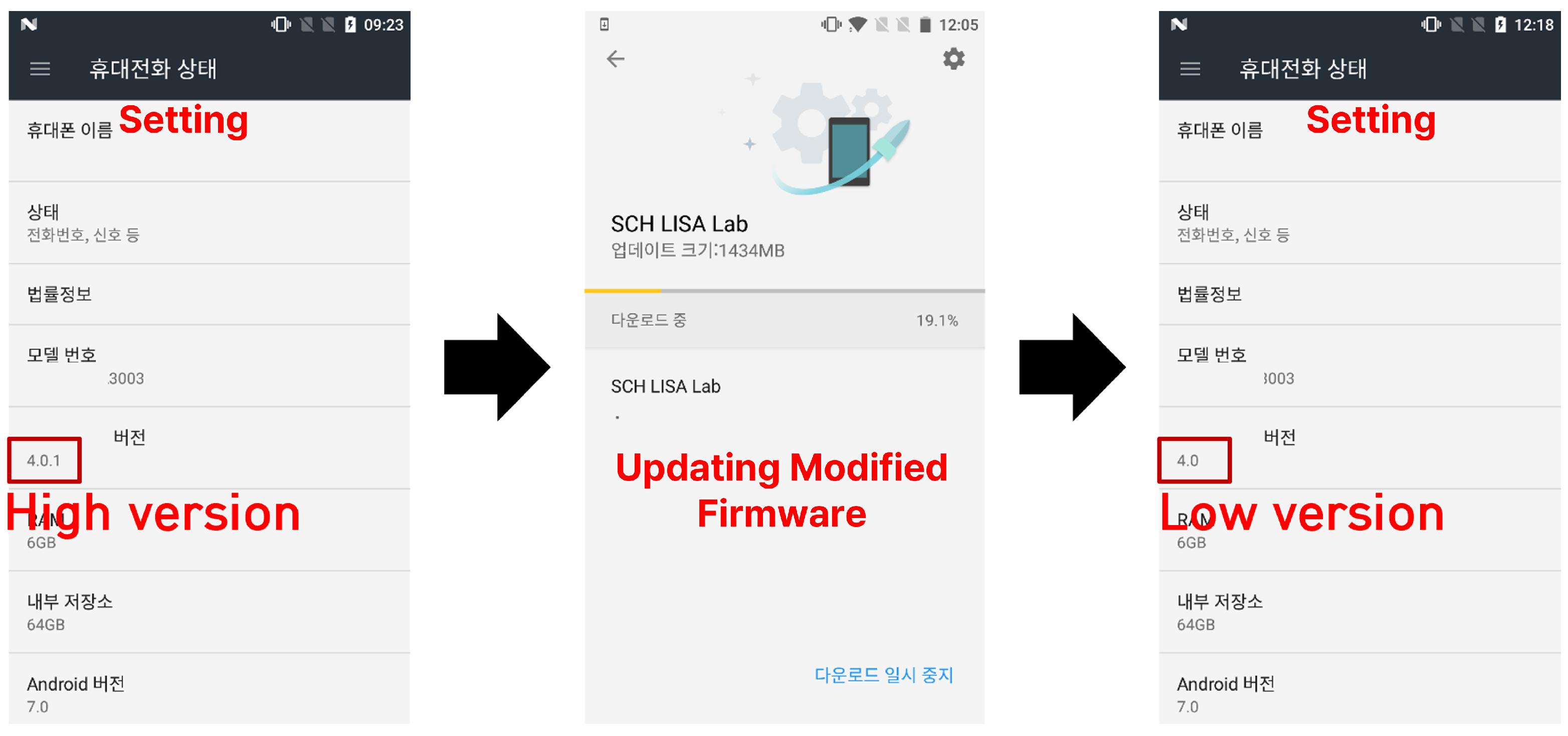
5.3. Firmware Downgrade Attack During the FOTA Update Process
6. Results of Security Assessment for FOTA Update Process
6.1. Comparison of Security Strength by Security Algorithm Used in the FOTA Update Process
6.2. Limitations of Security Assessment of FOTA Update Process
6.3. Industry-Level Discussion of FOTA Update Process Verification Results
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Korzeniewska, E.; Krawczyk, A. 5G technology as the succesive stage in the history of wireless telecommunication. In Proceedings of the 2019 IEEE International Conference on Modern Electrical and Energy Systems (MEES), Kremenchuk, Ukraine, 23–25 September 2019; IEEE: New York, NY, USA, 2019; pp. 470–473. [Google Scholar]
- Dawabsheh, A.; Owda, M. In-Vehicles Infotainment System Forensics Case Study. In Proceedings of the 2023 International Conference on Information Technology (ICIT), Kyoto, Japan, 9–10 Auguest 2023; IEEE: New York, NY, USA, 2023; pp. 32–37. [Google Scholar]
- Global Moabile Suppliers Association (GSA). 5G Stand-Alone June 2022 Summary. August 2022. Available online: https://gsacom.com/paper/5g-stand-alone-june-2022-summary/ (accessed on 12 December 2024).
- Halder, S.; Ghosal, A.; Conti, M. Secure over-the-air software updates in connected vehicles: A survey. Comput. Netw. 2020, 178, 107343. [Google Scholar] [CrossRef]
- Alliance, O.M. Firmware Update Management Object; Version, 1-0; Open Mobile Alliance Ltd.: San Diego, CA, USA, 2006. [Google Scholar]
- Lim, H.J.; Park, S.H.; Lee, D.Y.; Chung, T.M. u-MoDEM: Ubiquitous mobile device environment manager based on OMA-DM. In Proceedings of the 2008 10th International Conference on Advanced Communication Technology, Phoenix Park, Republic of Korea, 17–20 February 2008; IEEE: New York, NY, USA, 2008; Volume 1, pp. 283–287. [Google Scholar]
- Amini, M.; Asemian, G.; Kantarci, B.; Ellement, C.; Erol-Kantarci, M. Deep Fusion Intelligence: Enhancing 5G Security Against Over-the-Air Attacks. IEEE Trans. Mach. Learn. Commun. Netw. 2005, 3, 263–279. [Google Scholar] [CrossRef]
- Brusilovsky, A.; McDonald, I. 5G and the Need for Platform Integrity. J. ICT Stand. 2020, 8, 15–28. [Google Scholar] [CrossRef]
- Wu, Z.; Liu, T.; Jia, X.; Sun, C. Security design of OTA upgrade for intelligent connected vehicle. In Proceedings of the 2021 1st International Conference on Control and Intelligent Robotics, Guangzhou, China, 18–20 June 2021; pp. 736–739. [Google Scholar]
- Lakshmeshwar, S.; Anand, D.; Segaran, D. Suspend and Resume Feature for OMA DM Large Object Delivery. In Proceedings of the 2008 The 3rd International Conference on Grid and Pervasive Computing-Workshops, Kunming, China, 25–28 May 2008; IEEE: New York, NY, USA, 2008; pp. 206–212. [Google Scholar]
- Guangyu, C.; Jian, C.; Haisheng, G.; Zhipeng, G.; Xuesong, Q. OMA-DM based mobile device diagnostics and monitoring mechanism. In Proceedings of the 2009 Global Mobile Congress, Shanghai, China, 12–14 October 2009; IEEE: New York, NY, USA, 2009; pp. 1–6. [Google Scholar]
- Kim, M.; Park, J.; Jeong, E.; Oh, I.; Yim, K.; Park, J. OTA Vulnerability on User Equipment in Cloud Services. In Proceedings of the 2018 International Conference on Information Technology Systems and Innovation (ICITSI), Bandung, Indonesia, 22–26 October 2018; IEEE: New York, NY, USA, 2018; pp. 425–428. [Google Scholar]
- Brubaker, C.; Jana, S.; Ray, B.; Khurshid, S.; Shmatikov, V. Using frankencerts for automated adversarial testing of certificate validation in SSL/TLS implementations. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; IEEE: New York, NY, USA; pp. 114–129.
- Park, J. A Study on Technologies to Analyze Vulnerabilities of OTA Protocol of Mobile Device. Master’s Thesis, Soonchunhyang University, Asan-si, Republic of Korea, February 2017; pp. 1–68. [Google Scholar]
- Alliance, O.M. Oma Device Management Tree and Description; Approved Version; Open Mobile Alliance Ltd.: San Diego, CA, USA, 2006; Volume 1. [Google Scholar]
- Alliance, O.M. Policy Evaluation, Enforcement and Management Architecture; Open Mobile Alliance Ltd.: San Diego, CA, USA, 2012; Version 1.0; Available online: https://www.openmobilealliance.org/release/PEEM/V1_0-20120724-A/OMA-AD-Policy_Evaluation_Enforcement_Management-V1_0-20120724-A.pdf (accessed on 2 October 2023).
- Rivest, R. RFC1321: The MD5 Message-Digest Algorithm. MIT Laboratory for Computer Science and RSA Data Security, Inc. 1992. Available online: https://www.rfc-editor.org/rfc/rfc1321 (accessed on 2 October 2023).
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Bharat, B.; Sahoo, G.; Rai, A.K. Man-in-the-middle attack in wireless and computer networking—A review. In Proceedings of the 2017 3rd International Conference on Advances in Computing, Communication & Automation (ICACCA) (Fall), Dehradun, India, 15–16 September 2017; IEEE: New York, NY, USA, 2017. [Google Scholar]
- Chordiya, A.R.; Majumder, S.; Javaid, A.Y. Man-in-the-middle (mitm) attack based hijacking of http traffic using open source tools. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018; IEEE: New York, NY, USA, 2018; pp. 438–443. [Google Scholar]
- Georgiev, M.; Iyengar, S.; Jana, S.; Anubhai, R.; Boneh, D.; Shmatikov, V. The most dangerous code in the world: Validating SSL certificates in non-browser software. In Proceedings of the 2012 ACM Conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012; pp. 38–49. [Google Scholar]
- Bates, A.; Pletcher, J.; Nichols, T.; Hollembaek, B.; Tian, D.; Butler, K.R.; Alkhelaifi, A. Securing SSL certificate verification through dynamic linking. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 394–405. [Google Scholar]
- El-Hajj, W. The most recent SSL security attacks: Origins, implementation, evaluation, and suggested countermeasures. Secur. Commun. Netw. 2012, 5, 113–124. [Google Scholar] [CrossRef]
- Hossain, M.S.; Paul, A.; Islam, M.H.; Atiquzzaman, M. Survey of the Protection Mechanisms to the SSL-based Session Hijacking Attacks. Netw. Protoc. Algorithms 2018, 10, 83–108. [Google Scholar] [CrossRef]
- March, A.; Imine, Y.; Ouarnoughi, H.; Tarridec, T.; Gallais, A. Firmware integrity protection: A survey. IEEE Access 2023, 11, 77952–77979. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, J.; Wang, Y.; Zhai, S.; Li, Z.; He, Y.; Sun, K.; Li, Q.; Zhang, N. Your firmware has arrived: A study of firmware update vulnerabilities. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 5627–5644. [Google Scholar]
- Bakhshi, T.; Ghita, B.; Kuzminykh, I. A review of IoT firmware vulnerabilities and auditing techniques. Sensors 2024, 24, 708. [Google Scholar] [CrossRef] [PubMed]
- El Jaouhari, S. Toward a secure firmware ota updates for constrained iot devices. In Proceedings of the 2022 IEEE International Smart Cities Conference (ISC2), Paphos, Cyprus, 26–29 September 2022; IEEE: New York, NY, USA, 2022; pp. 1–6. [Google Scholar]
- Blázquez, E.; Pastrana, S.; Feal, Á.; Gamba, J.; Kotzias, P.; Vallina-Rodriguez, N.; Tapiador, J. Trouble over-the-air: An analysis of fota apps in the android ecosystem. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; IEEE: New York, NY, USA, 2021; pp. 1606–1622. [Google Scholar]
- Jeyalakshmi, V.; Vijayakumari, G. Secured reconfigurable software defined radio using ota software download. Int. J. Adv. Netw. Appl. 2012, 3, 1276. [Google Scholar]
- Dudek, S. Mobile IoT Modules Vulnerable to FOTA Updates Backdooring at Scale. Available online: https://penthertz.com/blog/mobile-iot-modules-FOTA-backdooring-at-scale.html (accessed on 5 January 2025).
- Crowther, K.G.; Upadrashta, R.; Ramach, G. Securing over-the-air firmware updates (FOTA) for industrial internet of things (IIOT) devices. In Proceedings of the 2022 IEEE International Symposium on Technologies for Homeland Security (HST), Virtual, 14–15 November 2022; IEEE: New York, NY, USA, 2022; pp. 1–8. [Google Scholar]
- Villegas, M.M.; Astudillo, H. OTA updates mechanisms: A taxonomy and techniques catalog. In Proceedings of the XXI Simposio Argentino de Ingeniería de Software (ASSE 2020)-JAIIO 49 (Modalidad Virtual), Virtual, 26–30 October 2020. [Google Scholar]
- El Jaouhari, S.; Bouvet, E. Secure firmware Over-The-Air updates for IoT: Survey, challenges, and discussions. Internet Things 2022, 18, 100508. [Google Scholar] [CrossRef]
- Sowmya, K.; Srinivasan, C.; Lakshmy, K.V.; Kumar Bansal, T. A secure protocol for the delivery of firmware updates over the air in iot devices. In Soft Computing and Signal Processing: Proceedings of 3rd ICSCSP 2020; Springer: Singapore, 2021; Volume 1, pp. 213–224. [Google Scholar]
- Infineon. Secured Firmware Over-The-Air (FOTA) Update in TRAVEOTM T2G MCU. 2023. Available online: https://www.infineon.com/cms/en/product/gated-document/an229058-secured-firmware-over-the-air-fota-update-in-traveo-t2g-mcu-8ac78c8c7cdc391c017d0d3e8f7c67e6/ (accessed on 7 January 2025).
- Doddapaneni, K.; Lakkundi, R.; Rao, S.; Kulkarni, S.G.; Bhat, B. Secure fota object for iot. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks Workshops (LCN Workshops), Singapore, 9 October 2017; IEEE: New York, NY, USA, 2017; pp. 154–159. [Google Scholar]
- Le, D.H.; Nguyen, V.N. Design of a Secure Firmware Over-The-Air for Internet of Things Systems. In International Conference on Intelligence of Things; Springer Nature: Cham, Switzerland, 2023; pp. 320–331. [Google Scholar]
- Lethaby, N. A More Secure and Reliable OTA Update Architecture for IoT Devices; Texas Instruments: Dallas, TX, USA, 2018. [Google Scholar]
- Kim, G.; Jung, I.Y. Integrity assurance of OTA software update in smart vehicles. Int. J. Smart Sens. Intell. Syst. 2019, 12, 1. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Sun, L.; Nakajima, T. A framework for self-verification of firmware updates over the air in vehicle ECUs. In Proceedings of the 2008 IEEE Globecom Workshops, New Orleans, LA, USA, 30 November–4 December 2008; IEEE: New York, NY, USA; pp. 1–5.
- Kirk, R.; Nguyen, H.N.; Bryans, J.; Shaikh, S.A.; Wartnaby, C. A formal framework for security testing of automotive over-the-air update systems. J. Log. Algebr. Methods Program. 2023, 130, 100812. [Google Scholar] [CrossRef]
- Mahmood, S.; Nguyen, H.N.; Shaikh, S.A. Systematic threat assessment and security testing of automotive over-the-air (OTA) updates. Veh. Commun. 2022, 35, 100468. [Google Scholar] [CrossRef]
- Li, B.; Hu, W.; Da, L.; Wu, Y.; Wang, X.; Li, Y.; Yuan, C. Over-the-air upgrading for enhancing security of intelligent connected vehicles: A survey. Artif. Intell. Rev. 2024, 57, 314. [Google Scholar] [CrossRef]
- Mayilsamy, K.; Ramachandran, N.; Moses, B.J.S.; Ravikumar, A. A hybrid approach to enhance data security in wireless vehicle firmware update process. Wirel. Pers. Commun. 2022, 125, 665–684. [Google Scholar] [CrossRef]
- Mansor, H.; Markantonakis, K.; Akram, R.N.; Mayes, K. Let’s get mobile: Secure FOTA for automotive system. In Network and System Security, Proceedings of the 9th International Conference, NSS 2015, New York, NY, USA, 3–5 November 2015; Proceedings 9; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 503–510. [Google Scholar]
- Borse, M.; Shendkar, P.; Undre, Y.; Mahadik, A.; Patil, R. Study of hybrid cryptographic techniques for vehicle FOTA system. In Mobile Computing and Sustainable Informatics: Proceedings of ICMCSI 2023; Springer Nature: Singapore, 2023; pp. 417–430. [Google Scholar]
- Fornari, S. Funambol Mobile Open Source; Packet Publishing: Birmingham, UK, 2009. [Google Scholar]
- Krawczyk, H.; Bellare, M.; Canetti, R. HMAC: Keyed-Hashing for Message Authentication (No. rfc2104). February 1997. Available online: https://datatracker.ietf.org/doc/html/rfc2104 (accessed on 17 September 2022).
- Kumar, D.D.; Mukharzee, J.D.; Reddy, C.V.D.; Rajagopal, S.M. Safe and secure communication using SSL/TLS. In Proceedings of the 2024 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 5–7 March 2024; IEEE: New York, NY, USA, 2024; pp. 1–6. [Google Scholar]
- Lee, H.K.; Malkin, T.; Nahum, E. Cryptographic strength of SSL/TLS servers: Current and recent practices. In Proceedings of the 7th ACM SIGCOMM Conference on Internet Measurement, San Diego, CA, USA, 24–26 October 2007; pp. 83–92. [Google Scholar]
- Maetouq, A.; Daud, S.M.; Ahmad, N.A.; Maarop, N.; Sjarif, N.N.A.; Abas, H. Comparison of hash function algorithms against attacks: A review. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 98–103. [Google Scholar] [CrossRef]
- Kamra, S.; Sharma, M.; Leekha, A. Secure hashing algorithms and their comparison. In Proceedings of the 2019 6th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 13–15 March 2019; IEEE: New York, NY, USA; pp. 788–792.
- Gupta, S.; Yadav, S.K.; Singh, A.P.; Maurya, K.C. A comparative study of secure hash algorithms. In Proceedings of the First International Conference on Information and Communication Technology for Intelligent Systems; Springer International Publishing: Berlin/Heidelberg, Germany, 2016; Volume 2, pp. 125–133. [Google Scholar]
- Stute, M.; Heinrich, A.; Lorenz, J.; Hollick, M. Disrupting continuity of apple’s wireless ecosystem security: New tracking, DoS, and MitM attacks on iOS and macOS through bluetooth low energy, AWDL, and Wi-Fi. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Online, 11–13 August 2021; pp. 3917–3934. [Google Scholar]
- McKay, K.; Cooper, D. Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations, 2nd draft ed; No. NIST Special Publication (SP) 800-52 Rev. 2 (Draft); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar]
- Bol, T.; Fisher, G. Selection of Hashing Algorithms. 2000. Available online: https://doi.org/10.1002/spe.4380200207 (accessed on 9 January 2023).
- Barker, E. NIST Special Publication 800-175B Guideline for Using Cryptographic Standards in the Federal Government: Cryptographic Mechanisms. 2016. Available online: https://doi.org/10.6028/NIST.SP.800-175Br1 (accessed on 9 January 2023).
- Dang, Q. Nist Special Publication 800-107 Recommendation for Applications Using Approved Hash Algorithms; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2009; Available online: https://doi.org/10.6028/NIST.SP.800-107r1 (accessed on 9 January 2023).




| Risk of Threats | Attack Methods | MD5 | HMAC |
|---|---|---|---|
| Jamming | Blocking or distorting the original communication signal by generating signals or noise from outside with malicious intent. | NA | NA |
| Sniffing | Attacks that spy on communication channels for firmware transmission. | NA | NA |
| Modification | Attacks through update firmware tampering during the update process. | A | NA |
| Hijacking | Attack that intercepts firmware files in the middle. | A | NA |
| Fabrication | Technology to launch attacks by counterfeiting firmware. | A | A |
| Spoofing | An attack utilizing disguised URL to download firmware. | A | NA |
| AP Camouflage | By deceiving the victim into using a standard AP, the victim is urged to connect to the UE. | A | A |
| Masquerading | Download the firmware by cloning it to a standard UE. | A | A |
| Mobile | Vehicle | ||||||
|---|---|---|---|---|---|---|---|
| Manufacturer | A | B | C | D | E | F | G |
| FOTA Type | OMA-DM | OMA-DM | SSL/TLS | SSL/TLS | JSON | JSON | SSL/TLS |
| Protocol | SSL/TLS | HTTP | SSL/TLS | SSL/TLS | HTTP | HTTP | SSL/TLS |
| Algorithm | MD5 | Digital Signature | MD5 | Digital Signature | MD5 | MD5 | Digital Signature |
| Risk of MitM | P | P | NP | NP | P | P | NP |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oh, I.; Sahlabadi, M.; Yim, K.; Lee, S. Threat Classification and Vulnerability Analysis on 5G Firmware Over-the-Air Updates for Mobile and Automotive Platforms. Electronics 2025, 14, 2034. https://doi.org/10.3390/electronics14102034
Oh I, Sahlabadi M, Yim K, Lee S. Threat Classification and Vulnerability Analysis on 5G Firmware Over-the-Air Updates for Mobile and Automotive Platforms. Electronics. 2025; 14(10):2034. https://doi.org/10.3390/electronics14102034
Chicago/Turabian StyleOh, Insu, Mahdi Sahlabadi, Kangbin Yim, and Sunyoung Lee. 2025. "Threat Classification and Vulnerability Analysis on 5G Firmware Over-the-Air Updates for Mobile and Automotive Platforms" Electronics 14, no. 10: 2034. https://doi.org/10.3390/electronics14102034
APA StyleOh, I., Sahlabadi, M., Yim, K., & Lee, S. (2025). Threat Classification and Vulnerability Analysis on 5G Firmware Over-the-Air Updates for Mobile and Automotive Platforms. Electronics, 14(10), 2034. https://doi.org/10.3390/electronics14102034