Abstract
With the advancement of communication technology, smart cities can provide remote services to users using mobile devices and Internet of Things (IoT) sensors in real time. However, the collected data in smart cities include sensitive personal information and data transmitted over public wireless channels, leaving the network vulnerable to security attacks. Thus, robust and secure authentication is critical to verify legitimate users and prevent malicious attacks. This paper reviews a recent authentication scheme for smart cities and identifies its susceptibilities to attacks, including insider attacks, sensor node capture, user impersonation, and random number leakage. We propose a secure and privacy-preserving authentication scheme for smart cities to resolve these security weaknesses. The scheme enables mutual authentication by incorporating biometric features to verify identity and using the physical unclonable function to prevent physical attacks. We evaluate the security of the proposed scheme via informal and formal analyses, including Burrows–Abadi–Needham logic, the real-or-random model, and the Automated Validation of Internet Security Protocols and Applications simulation tool. Finally, we compare the performance, demonstrating that the proposed scheme has better efficiency and security than existing schemes. Consequently, the proposed scheme is suitable for resource-constrained IoT-enabled smart cities.
1. Introduction
The smart city concept has evolved through the digitalization of urban management to enhance citizen welfare and optimize the administration of city services. This digital processing can be applied to several domains, including smart homes, energy management, intelligent transportation, healthcare, and industrial operations [1,2,3], improving daily life, environmental protection, public safety, and economic activities. With technological advancements, the Internet of Things (IoT) has facilitated smart city development. IoT systems enable wireless connectivity between various devices, including social media platforms, sensors, industrial machines, and mobile devices, within the smart city [4]. By applying such technology, smart cities can collect and exchange real-time data, enabling intelligent decision-making, location tracking, and efficient resource management [5]. Thus, smart cities can provide comfortable and adaptive services, such as supporting intelligent decision-making, efficient resource management, and location tracking accuracy [6].
While smart cities offer such advantages, they also bring some challenges and problems. Sensors and users generate smart city data, raising privacy issues. These data may include sensitive personal information, such as healthcare records, service transactions, location data, identity details, and service preferences [7,8]. If these data are leaked, the potential threats for privacy breaches become a critical problem [9]. Furthermore, IoT-enabled smart cities require efficient and lightweight communication because IoT devices have limited battery life, storage, and processing power [10]. Optimized communication has an influence on the performance of real-time city services. To ensure the successful and sustainable deployment of smart city technologies, it is crucial to maintain high-speed communication and implement robust security measures to protect sensitive data.
In addition, security attacks are important problems to solve when implementing smart cities. Heterogeneous networks comprising various devices provide smart city services, extending the attack surface of the network [11]. In smart city environments, data are transmitted via wireless channels. Messages transmitted over public channels are vulnerable to interception, reproduction, and unauthorized access, leading to potential data breaches [12]. Moreover, the sensors deployed in unattended or remote areas are vulnerable to physical attacks [13]. Mobile devices can be stolen, and stored values can be extracted via power analysis attacks. An attacker can impersonate a legitimate user and paralyze the network. Therefore, researchers have focused on authentication protocols to secure data exchanges between IoT devices and users to address these challenges. For example, authentication and key agreement (AKA) protocols effectively prevent unauthorized access across domains of varying scales, from industrial systems to wearable devices [14,15].
With the growing expansion of IoT systems in smart cities, protecting these systems with robust authentication protocols is imperative to maintaining the security and integrity of infrastructure and data in the city. Thus, a secure authentication scheme is required for IoT-enabled smart cities. In 2024, Nyangaresi et al. [16] proposed an efficient authentication scheme for smart cities using error correction codes and fuzzy commitment. They claimed their scheme ensures resistance to side-channeling attacks and has strong mutual authentication of communicating entities. However, the scheme by Nyangaresi et al. is vulnerable to insider, sensor node capture, user impersonation, and random number leakage attacks. Moreover, their scheme is unsuitable due to the high computational overhead of public key cryptography. Therefore, we propose a privacy-preserving authentication scheme to resolve the security vulnerabilities of the scheme by Nyangaresi et al. using physical unclonable functions (PUFs) and fuzzy extractors.
1.1. Research Contribution
The main contributions of this paper are outlined below:
- This work analyzes the scheme by Nyangaresi et al. [16] and demonstrates that it has security vulnerabilities, such as susceptibility to insider, sensor node capture, user impersonation, and random number leakage attacks.
- This work proposes a privacy-preserving authentication scheme for smart cities to address the security vulnerabilities of the scheme by Nyangaresi et al. [16]. The proposed scheme employs biometric information as an additional factor for secure user verification and applies PUF technology to defend against physical threats.
- This work demonstrates the security of the proposed scheme via an informal security analysis, which reveals the security properties and resistance to various attacks. The proposed scheme ensures mutual authentication and secure communication by verifying the legitimacy of entities.
- This work conducts formal analyses using Burrows–Abadi–Needham (BAN) logic, the real-or-random (ROR) model, and Automated Validation of Internet Security Protocols and Applications (AVISPA) simulation tools. The analyses evaluate mutual authentication, session key security, and resistance to man-in-the-middle (MitM) and replay attacks.
- This work demonstrates that the proposed scheme performs better than others in smart city applications. The proposed scheme is more suitable and efficient than other schemes for IoT-based smart city environments.
1.2. Organization
The remaining sections of this paper are organized as follows. We briefly discuss existing authentication schemes related to IoT-based smart city environments in Section 2. We introduce the network and adversary models of the proposed scheme, followed by a brief overview of PUFs and fuzzy extractors in Section 3. We present a review of Nyangaresi et al.’s scheme [16] in Section 4, and analyze security vulnerabilities of their scheme in Section 5. Then, we present our proposed scheme in Section 6. We demonstrate the security of the proposed scheme both informally and formally, using the BAN Logic, ROR model, and AVISPA tools in Section 7. We provide the performance evaluation of the protocol in Section 8 and the conclusion of this paper in Section 9. Table 1 summarizes the notation and definitions used in this paper.

Table 1.
Notation and definitions.
2. Related Work
With the increasing development of smart cities, numerous authentication schemes have been proposed to address various challenges in ensuring robust security and privacy. In 2019, Shuai et al. [17] introduced an efficient scheme for anonymous authentication in smart home environments. Their scheme achieves user anonymity and untraceability by encrypting the real identity using random numbers generated for each session. However, their scheme had security vulnerabilities, including node capture, device node impersonation attacks, and issues with forward secrecy [18]. Based on a cryptoanalysis of Shuai et al.’s scheme, Zou et al. [18] suggested a robust two-factor-based authentication scheme for smart homes. Their scheme enables successful mutual authentication and key establishment. In addition, they argued that their scheme ensures session key forward secrecy, user anonymity, and protection against all attacks. However, their scheme suffers from forgery, session key disclosure, and ephemeral secret leakage attacks.
Some researchers suggested multifactor authentication to provide comprehensive security and achieve a variety of desired security goals. Kaur et al. [19] proposed an enhanced authentication scheme utilizing a fuzzy verifier as an authentication factor. For example, the expression “” increases computational complexity and makes password-guessing more difficult, where is the password and v is the fuzzy verifier. Zou et al. [20] used three factors for their authentication scheme in smart factory environments. They demonstrate the resistance of their scheme against password guessing and smart card stolen attacks by combining multiple factors, such as biometric information, a password, and a smart card. Rangwani and Om [21] suggested a four-factor mutual authentication scheme for remote healthcare monitoring. They used the transformed bit string from the iris scan, which is unique even for twins, biometric data using a fuzzy commitment scheme, a password, and the identity of the user.
The smart city provides services according to numerous sensors which are deployed all over the cities, even in unattended areas. Researchers proposed authentication schemes considering the specifications of smart cities like the possibility of sensors or gateways being compromised. Xie et al. [22] proposed an authentication scheme designed to resist sensor node capture attacks in smart city environments. Their scheme distributes different secret keys among sensing devices, ensuring that an adversary cannot gain additional information from other captured devices. Furthermore, the long-term key cannot be extracted from the data stored in the sensor node due to protection by a cryptographic hash function. However, Xie et al.’s scheme has several security flaws, including untraceability and susceptibility to privileged insider, impersonation, and MitM attacks. Kumar et al. [23] proposed a multifactor authentication scheme utilizing PUF technologies for accessing remote sensors through a base station. With a session key update procedure, their scheme ensures the confidentiality of the session key among users, base stations, and sensor nodes. Although their scheme is lightweight and does not require a registration center, it fails to analyze critical security issues such as perfect forward secrecy, denial of service (DoS), and stolen verifier attacks. Badar et al. [24] devised a mutual authentication scheme for smart meters and service providers in smart city development. They used point multiplication with public keys, and provided physical attack resilience by using the PUF. In 2024, Nyangaresi et al. [16] presented an efficient authentication scheme in an IoT-enabled smart city environment. They lowered the number of elliptic curve cryptography (ECC) calculations and addressed security problems, including desynchronization, privileged insider attacks, and anonymity. However, their scheme has limitations in defending against insider, physical capture, user impersonation, and random number leakage attacks. Therefore, we propose a secure authentication scheme to resolve these shortcomings.
3. Preliminaries
This section presents the network and adversary models and discusses PUFs and fuzzy extractors.
3.1. Network Model
In this paper, the network model is composed of four entities: the registration authority (RA), users (U), gateway node (GW), and sensor nodes (SNs). As shown in Figure 1, users communicate remotely using their mobile devices and request sensor data. Once mutual authentication is successful, the remote user and the sensor generate a shared session key to communicate securely. The following descriptions offer a detailed introduction to each entity.
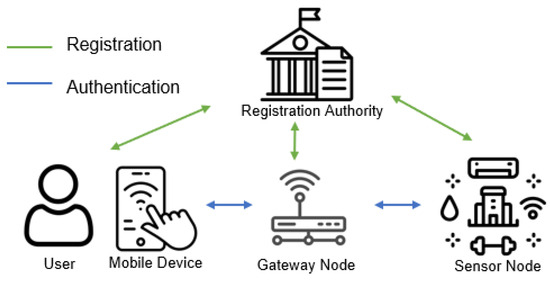
Figure 1.
Network model.
- Registration authority: The registration authority has sufficient storage capacity and computation power to register users, gateway nodes, and sensor nodes in the smart city. The registration authority is a trusted entity that manages the identification information for the user, gateway node, and sensor node.
- User: Users can employ their mobile devices to obtain sensor data remotely. To access data, users must first register with the registration authority. After registration, users can use their mobile devices to communicate with sensors through a gateway for successful authentication.
- Gateway node: The gateway is considered a semi-trusted entity in the scheme. Although the gateway can attempt to reveal the data using its information, it works properly as a bridge between users and sensor nodes in wireless networks. The sensor data must be authenticated by passing the gateways through insecure channels. Each gateway is responsible for managing the sensors within its designated region.
- Sensor node: The sensors are deployed everywhere in smart cities to collect environmental data. Before deployment, sensors register at the registration authority to obtain secret parameters for authentication. Through the gateway, sensors transfer collected data to legitimate users who require data. These sensors have limited computational power and storage capabilities.
3.2. Mathematical Preliminaries
In this section, we present some mathematical preliminaries for the proposed scheme in this paper, including a fuzzy extractor and physical unclonable function.
3.2.1. Fuzzy Extractors
According to [25], this section discusses the fundamental concepts of a fuzzy extractor. We utilize fingerprints in biometric applications due to their superior distinctiveness, permanence, and measurability compared to other biometric modalities [26]. The minutiae points and the singular point are extracted from the fingerprint image, and a BIO template is constructed by fitting a polynomial curve to the distances between each minutia and the singular point [27]. We identify users by performing template-matching based on the similarity between the generated and stored templates. Suppose a finite set L is a metric space with a distance function, where the biometric data . The biometric input data can be changed because of the scanning angle or noise when a user inputs the data into a device. The fuzzy extractor uses a helper string to control the margin of error for the noise. A helper string P is auxiliary data used with fuzzy extractors to recover secrets from noisy biometric inputs. Even if P is disclosed, P does not reveal information about the secret key R, which remains computationally indistinguishable from a uniform distribution. This indistinguishability can be quantified by the statistical distance, which measures how closely the distribution of R matches the uniform distribution. The statistical distance between two distributions X and Y is defined as
Helper strings enable fuzzy extractors to handle variations in biometric inputs, ensuring reliable secret recovery without increasing false rejection or false acceptance rates [28]. Therefore, the fuzzy extractor can encrypt biometric information into a consistent secret string. This mechanism comprises two procedures, and , explained below:
- : When a user inputs the biometric data , the probabilistic function generates a secret string and a helper string , where l and ∗ are lengths of bit strings.
- : When a user reimprints biometric data , could have some noise compared to the initial biometric data B. The procedure recovers the value using P.
Fuzzy extractors are preferable for constrained devices due to their minimal communication overhead, low energy consumption, and lack of reliance on uniformly distributed inputs or complex cryptographic assumptions [29].
3.2.2. Physical Unclonable Functions
The PUF was introduced as a physical security primitive [30], operating with a one-way function. The PUF circuit employs input and output bit string pairs called the challenge–response pair. After making a random string of bits as a challenge, the PUF generates responses to challenges based on the random physical differences for each device. The manufacturing process of PUF involves randomness that device producers cannot even control, making it impossible to copy identically [31]. These slight differences cause each PUF to respond uniquely to the same challenge. Therefore, PUFs are unclonable and help prevent attacks, including cloning and physical capture attacks. As the ideal stability of PUF is important, we have to consider environmental factors such as temperature variations, which can affect the response of some PUFs. Fortunately, in recent years, several types of ideal PUFs have been developed that guarantee the data stability of a PUF over a wide range of temperature and voltage fluctuations. For example, some ideal PUFs generate stable responses by relying on the randomness of soft gate oxide breakdown locations or intentionally permanent physical defects [32,33]. As a result, using ideal PUF design is a practical and feasible option while avoiding the need for stability enhancement technologies like helper data or fuzzy extractors [34] to save on computational and storage costs [35]. This paper uses ideal PUF design for stability and describes the process as , where C denotes a challenge and R represents a response. The properties of PUF are outlined as follows:
- The PUF has unclonable properties that prevent replication.
- The PUF response is unpredictable due to its physical characteristics.
- In the same device, the PUF responds identically to the same challenge.
- The PUF circuit is easy to estimate and implement.
In the verification phase, the device uses the stored challenge and generates the response. Then, the device compares this response with the parameter stored in its database. The verification is considered successful if the two values are equal.
3.3. Adversary Model
This section outlines the adversary model assumed for the security analysis of the proposed scheme. This work follows the Dolev–Yao (DY) threat model [36], which assumes that the adversary has full control over all messages transmitted via an open channel. In addition, this work considers the Canetti and Krawczyk (CK) threat model [37], where the adversary is capable of compromising secret information, such as ephemeral parameters or session states. These models are widely used in protocol analysis and help define the security assumptions [38,39,40]. The capabilities of the adversary are outlined below:
- Message control: The adversary can intercept, alter, delete, and inject malicious or forged messages during communication over a wireless public channel.
- Device compromise: The adversary can extract sensitive data from lost or stolen mobile devices. Through power analysis attacks [41], the adversary can retrieve private information, including credentials and other stored parameters.
- Various attacks: The adversary can perform various attacks, such as replay, privileged insider, impersonation, and sensor node capture.
4. Review of Nyangaresi et al.’s Scheme
This section presents the authentication scheme by Nyangaresi et al. [16], which was proposed for a smart city. Their scheme includes the system setup, registration of sensor node and user, login, authentication, and key negotiation phases.
4.1. System Setup Phase
The scheme by Nyangaresi et al. uses ECC to establish key agreements between entities. At first, a gateway chooses an elliptic curve E over and an additive group G, with generator P having a large prime order q. The generates a secret key n and computes the corresponding public key , while keeping both n and its primary key private. Finally, publishes the set of parameters .
4.2. Registration Phase
In this phase, sensor nodes and users should perform the registration process with the corresponding . The communication is assumed to be secure during this phase. The assigns secret values to and for subsequent authentication and key agreement.
4.2.1. Sensor Node Registration
The sensor node is registered at the gateway node and is deployed in the smart city to collect and exchange data. This phase executes the following two steps.
- Step 1:
- The selects a unique identity for and derives a secret key . Those parameters are sent to via a secure channel.
- Step 2:
- Upon receiving the message , the stores the parameters.
4.2.2. User Registration
All users should register with the to acquire data from . This phase describes the registration process of , which is explained in the next 3 steps.
- Step 1:
- Through the , the generates a unique identity , password , and random number . Next, computes and inputs biometric data into the . Then, composes and sends a registration request to through a secure channel.
- Step 2:
- The chooses a random codephrase for the , and derives , , , , . After that, stores in its database and constructs a registration response . The message is sent to over a secure channel.
- Step 3:
- Upon receiving the response, stores parameters in the memory of .
4.3. Login, Authentication, and Key Negotiation Phase
To access data from , the sends a login request message to through the . Upon receiving , authenticates the user to verify registration and then establishes a session key shared among , , and . The detailed steps are described below.
- Step 1:
- The inputs into the , which uses an error correcting code to compute and recover if the Hamming distance between and is within the acceptable threshold. Afterward, checks whether , where . After the biometric validation is successfully completed, inputs and . Then, the computes and checks whether . If validated, chooses random nonces and computes , , , , , , , where . Finally, composes the login request message and sends it to the through a public channel.
- Step 2:
- After receiving , the computes , . Next, confirms whether exists in its database. When is found and identified, computes , , , , , . Then, confirms whether . If validated, generates and computes , , , , . Finally, construct the authentication message and sends it to the over a public channel.
- Step 3:
- Upon obtaining , calculates , , , . Subsequently, checks whether , and, if equal, generates as a random nonce. Then, calculates , , . Finally, composes the authentication response message , which is transmitted to via a public channel.
- Step 4:
- After receiving from the , computes , , . If equals , computes , , . Finally, constructs that is sent to the .
- Step 5:
- computes , , , and . After that, checks whether . If is valid, the session key is set as and key negotiation is completed.
5. Cryptoanalysis of Nyangaresi et al.’s Scheme
This section demonstrates that the scheme by Nyangaresi et al. [16] is susceptible to security attacks, including insider, sensor node capture, user impersonation, and random number leakage attacks. A detailed discussion is provided in the following sections.
5.1. Insider Attack
This work assumes that an adversary is registered at gateway node . As a legitimate user, can successfully authenticate with the and . Moreover, can obtain authentication information via legitimate communication. The can compute the session key of other users using this acquired information.
- Step 1:
- An adversary completes the authentication phase using his/her identity and password as a legitimate user. During this phase, intercepts the message and derives the secret key which is shared between and .
- Step 2:
- The eavesdrops parameters from the messages exchanged by another user via a public channel. Since the parameter is consistently used during the authentication phase, can obtain the session key between and .
- Step 3:
- Using the secret key , computes , . Next, derives , , and . Finally, can compute the session key .
Therefore, the scheme by Nyangaresi et al. cannot resist insider attacks.
5.2. Physical Capture Attack
The can obtain a stolen or lost user’s mobile device and attempt to extract the stored parameters in it. If attempts to guess from , can compute the user’s biometric information . Moreover, sensor nodes are typically placed in unattended or hostile environments; thus, can easily capture them and potentially access sensitive user information. If obtains parameters , can compute the as described in Section 5.1. In addition, can determine another user’s identity and the secret parameter . By intercepting the messages , can compute , , and . Therefore, Nyangaresi et al.’s scheme cannot prevent sensor node capture attacks.
5.3. User Impersonation Attack
Following Section 5.2, can infer and . Afterward, can generate the login request message to impersonate another authorized user.
- Step 1:
- An adversary generates random nonces and . Then, computes , .
- Step 2:
- Using the obtained parameters , computes , , and . Finally, can successfully compose and impersonate a user .
Therefore, the scheme by Nyangaresi et al. cannot prevent user impersonation attacks.
5.4. Random Number Leakage Attack
According to Section 3.3, this work assumes that can reveal random nonces , and . Adversary can eavesdrop on authentication messages via a public channel and calculate the session key . The details are described in the following steps.
- Step 1:
- After obtaining parameters from the public messages, computes , , and .
- Step 2:
- Finally, calculates the .
Therefore, Nyangaresi et al.’s scheme cannot prevent random number leakage attacks.
6. Proposed Scheme
According to Section 3.1, we propose a privacy-preserving authentication scheme for smart cities that utilizes biometrics and PUFs to address the security weaknesses of the existing scheme [16]. The proposed scheme comprises three phases: registration, login, and authentication.
6.1. Registration Phase
Smart cities are planned environments where data collection types and citizen services provided to citizens are predefined. Sensor deployment locations and gateway coverage areas are determined through location-based mapping. During registration, the RA assigns the appropriate gateway to each sensor node based on this mapping. Prior to the deployment in the smart city, gateways and sensors must be registered with the registration authority. Users within a smart city must also register their identities at the registration authority for authenticated communication. The registration phase processes these via secure channels.
6.1.1. Gateway Node Registration
A gateway node registers its identity with the registration authority. Then, receives a secret key for mutual authentication between sensors and users within its responsible area.
- Step 1:
- The gateway node selects its unique identity . Then, sends to as shown in Figure 2.
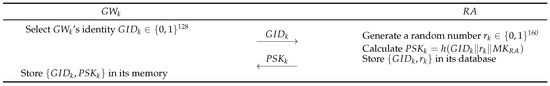 Figure 2. Gateway node registration of proposed scheme.
Figure 2. Gateway node registration of proposed scheme. - Step 2:
- If the received does not exist in the database, processes a registration phase for . The generates a random number and computes . The stores in its database and sends to .
- Step 3:
- After receiving from , stores with in its memory.
6.1.2. Sensor Node Registration
Sensor nodes register at the registration authority to deploy in a smart city, obtaining secret values for the authentication and session key. Moreover, sensor nodes have a secret key used for a secret shared session key with a gateway node. Figure 3 shows the registration process for sensor nodes, and the following steps are explained in detail.
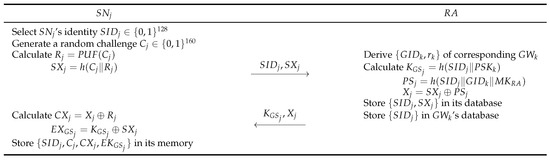
Figure 3.
Sensor node registration of proposed scheme.
- Step 1:
- The sensor node selects its identity and generates a random challenge . calculates a PUF response , and . sends to .
- Step 2:
- If the does not exist in the database, derives corresponding parameters of , which is responsible for the area where will be deployed. Then, calculates , , and . The stores the sensor information in its database and in the gateway node database. Finally, transmit secret parameters to .
- Step 3:
- After receiving these parameters, calculates , . stores values .
6.1.3. User Registration
Users must register with the to access and receive remote services with as legitimate users. Through the , users input their , and factors and process the registration phase, which is ready to authenticate with sensors. Figure 4 describes each user registration step, detailed as follows:
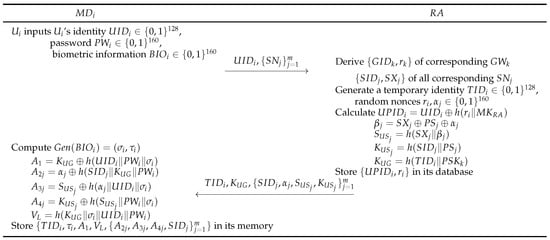
Figure 4.
User registration of the proposed scheme.
- Step 1:
- The user inputs ’s unique identity , password , and biometric data into . The requires access to sensor nodes , and sends the requirements and to .
- Step 2:
- The derives stored information of that communicates with , as well as that manages those sensors. Then, selects a temporary random identity and generates a random number . Then, calculates parameters , , , and required for authentication. The stores in its database and sends to .
- Step 3:
- When the response is received, computes a secret parameter and a helper string from , and encrypts secret keys using . The computes , , , , , and . Finally, stores parameters in its database and completes registration successfully.
6.2. Login and Authentication Phase
In the login phase, enters his credential information , , and into his . The computes and if , it rejects the login request, considering the user illegitimate. To access data of , composes and sends it to . During authentication, the user and sensor perform the following steps via the gateway to establish a secure session key and achieve mutual authentication. Figure 5 illustrates the login and authentication phase.
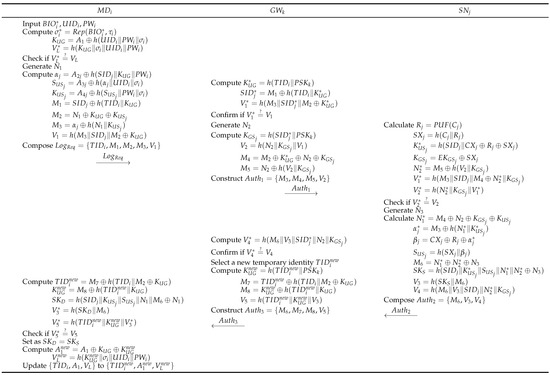
Figure 5.
Login and authentication of proposed scheme.
- Step 1:
- The first inputs , and into . Then, computes , , . If equals , the login is successful and is authenticated. Next, generates and computes , , and . Then, composes the message , where , , , . The sends to .
- Step 2:
- Upon receipt of the message, the computes , , . Then, verifies whether . If this is valid, the generates and computes , , , . constructs the authentication message and transmits to .
- Step 3:
- On receiving , the calculates , , , , , , . After that, checks whether equals . If this is correct, generates and calculates , , , , , , , . Finally, sends to .
- Step 4:
- When receives the response from , computes and checks the validity of compared with . If the verification is successful, randomly selects a new temporary identity for subsequent communication of . Then, computes , , , . Finally, constructs the message and transmits it to .
- Step 5:
- After obtaining , computes , , , , , and . Next, verifies whether . If the values do not match, the session is aborted. Otherwise, the session key is set as , and key agreement is successful between and . Followed by the successful authentication phase, computes , and updates to . After that, erases from its database to prevent any backward key secrecy violations.
6.3. Dynamic Node Addition Phase
There is a possibility that some of the deployed sensor nodes may not work properly or may be physically stolen by an attacker. When fresh nodes need to be deployed to continue services, the new nodes can be added into the network through the dynamic node addition phase. The following steps describe the dynamic node addition phase.
- Step 1:
- Before the new node is deployed, executes the sensor node registration phase. By following the Section 6.1.2, the stores and the stores in its memory.
- Step 2:
- After the successful registration of and its deployment, informs the gateway about its addition. The calculates , , and . The encrypts its identity by the secret key and sends it to .
- Step 3:
- After receiving the messages about a new sensor addition, the verify the legitimacy of by using . Then, broadcasts for the new node addition. Then, users can request access to the newly deployed node.
7. Security Analysis
This work demonstrates the scheme security using informal and formal analysis methods. We describe the security features of attack resistance via an informal analysis. Moreover, this work employs widely used formal analyses, including BAN logic, the ROR model, and AVISPA simulation.
7.1. Informal Analysis
This section reveals that the scheme supports numerous security features and resists many typical security attacks in a smart city.
7.1.1. Session Key Disclosure Attacks
The goal of is to compute a valid session key by intercepting public communication messages. For every session, the session key is , where , and are random nonces. The random nonces are freshly chosen for every new session. The session key depends on a secret key , shared between legitimate users and the sensor. Even the secret key is only shared between the sensor and respective users. If wants to know the random nonces, must know the shared keys with sensors and the shared keys with gateway and . Each random nonce is encrypted by keys and as indicated in messages and . Therefore, the proposed scheme can resist session key disclosure attacks.
7.1.2. Denial of Service Attacks
The adversary can conduct a DoS attack to block user access. Adversary A can continuously attempt to issue fake request messages. intercepts and replaces parameters and sends it to the gateway. However, the gateway first checks whether the received is valid. If any parameter in the request message is changed, is never matched and validated. The parameter is related to , and then is related to and to be used to compute these messages. Since cannot know a secret shared key, the session is terminated upon validation failure. Therefore, the proposed scheme can resist DoS attacks.
7.1.3. Replay Attacks
may try to impersonate a legitimate user by resending messages from a previous session. However, is unable to access the previous messages through this replay because the scheme checks the freshness of all exchanged messages using random nonces , , and . These random nonces compose all parameters in authentication messages . Consequently, the proposed scheme can withstand replay attacks.
7.1.4. Desynchronization Attacks
We assume that a user does not receive the correct response from a gateway due to unexpected terminations, or may attempt desynchronization attacks. may change the messages that update the user’s temporary identity and the corresponding shared secret key . However, a user checks the message by validating if is the same. The parameter includes a shared parameter not only with a gateway but also with a sensor. If it fails to verify, the session is terminated. Moreover, the gateway does not need to store a temporary identity of a user. Therefore, the scheme has resistance to desynchronization attacks.
7.1.5. Insider Attacks
As a legitimate user, can register at the registration authority and authenticate to and . Using his authentication messages and parameters, attempts to compromise other legal users’ sessions. To compute session key , must need the secret shared keys {, , , , }, which are masked by hash functions and XOR operations with random nonces . Therefore, the proposed scheme is resilient to insider attacks.
7.1.6. Privileged Insider Attacks
A privileged insider attacker can intercept a legitimate user ’s registration request message . Then, attempts to compute a session key by using public communication messages of the user. However, is unable to obtain the session key of . To compute the session key , needs to know and , which are shared between and . Since cannot obtain these parameters from the registration message alone, the proposed scheme remains secure against privileged insider attacks.
7.1.7. User Impersonation Attacks
An unauthorized adversary attempts to authenticate with sensors to impersonate a legitimate user. To impersonate the user, an adversary must construct a registration request . However, cannot compute parameters due to a shared secret key between and , which is updated in every session.
7.1.8. Man-in-the-Middle Attacks
During the authentication phase, may intercept and modify the authentication messages in the middle. However, as discussed in Section 7.1.7, cannot construct a login request message and other messages . Additionally, the PUF response cannot be modified due to the unclonable property of PUFs. Therefore, the proposed scheme has resistance to MitM attacks.
7.1.9. Forgery Attacks
may try to modify messages during the authentication phase. However, such attempts can be easily detected by the gateways, sensors, and users using the verification values . It is impossible to compute without passing through all entities. The random nonce , which is used to compute a session key, is doubly encrypted by for a sensor and for a gateway, respectively. Moreover, the key parameter is not transmitted through the public channel and is only known between and . Thus, the proposed scheme prevents forgery attacks.
7.1.10. Physical Capture Attacks
Users can lose their mobile devices, and we assume that can extract parameters stored in a mobile device . However, cannot obtain users’ information without knowing , , and simultaneously, since the stored parameters are encrypted using XOR operations and one-way hash functions. Here, , , , . In addition, cannot obtain with only a helper string without . Similarly, the sensors deployed within a smart city could be compromised. attempts to compute a session key after extraction of stored data in sensors . However, the secret key shared with a gateway and the secret parameter are encrypted using the PUF’s response , which is unclonable. Thus, the proposed scheme is robust against physical capture attacks.
7.1.11. Random Number Leakage Attacks
In the scheme, the session key is derived including ephemeral random numbers , where . Based on Section 3.3, can reveal all random numbers during the authentication phase. Nevertheless, cannot compute without the secret parameters and , which are only shared between and . Moreover, it is impossible to calculate because only knows , which is protected by . Accordingly, the proposed scheme provides security against random number leakage attacks.
7.1.12. Mutual Authentication
In the proposed scheme, each entity verifies the validity of the messages to ensure they come from legitimate entities. The authentication is verified using the values , where , , , , . The determines the legitimacy of by checking and consistently ensures message freshness. During this verification, can confirm the correctness of and . In each session, the login request message differs even for the same user because of the random nonces . Since is calculated using , the can confirm the legitimacy and freshness of both and by the validation of . The parameter includes random nonces and , which are generated in every session. The checks the legitimacy of by verifying . Since includes the random nonce generated by , the can believe the freshness of messages. Similarly, checks and can confirm the legitimacy of both and because comprises . The messages one entity sends to another can be verified; thus, the scheme can achieve mutual authentication.
7.1.13. Key Agreement
The session key is established between and to protect the exchanged sensor data. In the scheme, the semi-trusted gateway does not know the session key, but the authentication phase is processed through the gateway. Upon receiving the authentication message , computes values , , , . According to Section 7.1.12, can check the legitimacy of and and derive . Similarly, can compute using the received authentication message and known secret parameters . In the session key , the parameter identifies the sensor that communicates with the user. The secret parameters and ensure secure communication between the legitimate user and the sensor. Additionally, the random nonces and are refreshed in every session, making it difficult for an adversary to compute the session key. Therefore, and securely proceed with a session key agreement between only themselves.
7.1.14. Anonymity and Untraceability
In the scheme, cannot know the real identity of a user . The identity is used in the login process, but it is stored in with encryption of the hash function with and , which is difficult to reproduce. In the registration phase, is also masked by RA’s primary key and instead receives a temporary identity for authentication. During the authentication phase, the user does not use . In addition, is updated in every session, and the proposed scheme ensures anonymity and untraceability.
7.1.15. Perfect Forward Secrecy
If obtains the primary key from the registration authority, then may attempt to calculate the session key . However, cannot affect the confidentiality of past communications because the session key comprises random nonces generated for each session. These random nonces ensure that the session key is different in every session, even when the same user and sensor communicate. The secret value guarantees secure communication between the legitimate user and the sensor. Moreover, includes a random value known only to and . Even when multiple users access the same sensor, each user has a different session key. Accordingly, the proposed scheme provides perfect forward secrecy.
7.1.16. Modeling Attacks
Modeling attacks on PUFs aim to construct a predictive model by using a sufficient number of collected challenge–response pairs (CRPs). Using the trained model, can potentially predict valid responses to challenges. However, in the proposed scheme, the PUF mechanism is used only for protecting stored parameters and does not expose CRPs to public channels. During the authentication phase, computes the PUF response and secret parameters . CRPs are not transmitted via an open channel. Even if intercepts all communication, no additional CRPs can be obtained. This restricts the adversary’s ability to collect a sufficient dataset for model training. Consequently, the proposed scheme is resilient against modeling attacks on PUFs, as it limits CRP exposure and prevents adversaries from building a reliable model.
7.2. BAN Logic
We demonstrate that the proposed scheme ensures mutual authentication through widely used BAN logic analysis. Table 2 presents the notations and descriptions used in BAN logic. The following section introduces the BAN logic rules and the security goals of the scheme. To apply the BAN logic proof to the scheme, we idealize the communication messages and provide the necessary assumptions. Finally, we outline the entire proof process in the following section.

Table 2.
Notations of BAN logic.
7.2.1. Rules
The BAN logic is based on the five basic rules summarized below.
1. Message meaning rule (MMR):
2. Nonce verification rule (NVR):
3. Jurisdiction rule (JR):
4. Belief rule (BR):
5. Freshness rule (FR):
7.2.2. Goals
The principals of the user, gateway, and sensor are denoted by U, G, and S, respectively. The goals of the proposed scheme describe the user U and sensor S to establish a session key, as presented below:
- :
- :
- :
- :
7.2.3. Idealized Forms
This framework transmits messages in the idealized form and omits other messages because they cannot efficiently provide the logical properties of a BAN logic proof. Messages for the proposed scheme are formed as follows:
- :
- :
- :
- :
7.2.4. Assumptions
We assume that the shared key is correctly distributed and that timestamps are fresh. Using BAN logic notation, these assumptions are expressed as follows:
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
7.2.5. BAN Logic Proof
We prove the goals of the proposed scheme using BAN logic rules and the mentioned assumptions. The following steps present the detailed procedure of the BAN logic proof.
- Step 1:
- According to , we can obtain .
- Step 2:
- From the MMR using and , we can obtain .
- Step 3:
- From the FR using , we can obtain .
- Step 4:
- From the NVR using and , we can obtain .
- Step 5:
- According to , we can obtain .
- Step 6:
- From the MMR using and , we can obtain .
- Step 7:
- From the NVR using and , we can obtain .
- Step 8:
- According to , we can obtain .
- Step 9:
- From the MMR using and , we can obtain .
- Step 10:
- From the FR using , we can obtain .
- Step 11:
- From the NVR using and , we can obtain .
- Step 12:
- According to and , we can obtain .
- Step 13:
- From the MMR using and , we can obtain .
- Step 14:
- From the FR using , we can obtain .
- Step 15:
- From the NVR using and , we can obtain .
- Step 16:
- According to , we can obtain .
- Step 17:
- From the MMR using and , we can obtain .
- Step 18:
- From the FR using , we can obtain .
- Step 19:
- From the NVR using and , we can obtain .
- Step 20:
- Since the session key is , we can obtain from and . From , , and , we can obtain .
- Step 21:
- From the JR using , , , and , we can obtain and .
7.3. ROR Model
This section describes the semantic security of the proposed scheme with the analysis of the ROR model [42]. This work defines three participants in the authentication phase of the scheme: user , gateway node , and sensor node , which are the user, gateway node, and sensor node, respectively. In the ROR model, adversary can use various queries, including Execute, CorruptD, Send, and Test, to attempt to disclose the session key. The queries are described in detail below.
- Execute(, , ): can intercept the messages transmitted between , , and through a public channel. The query indicates an eavesdropping attack.
- CorruptD(): Using this query, obtains the data stored in the mobile device of a user .
- Send(, ): can transmit and receive a message between other participants , , and .
- Test(): This query executes a coin flip test to verify the semantic security of the session key. If , a random string is returned; if , the session key is returned. Otherwise, gets a value. The session key is secure if cannot distinguish between the random string and the session key.
Theorem 1.
Let attempt to break the session key security of the proposed scheme. Let be the advantage of to calculate the session key in polynomial time. We define and as the range space of the hash function and PUF , respectively. Then, we denote , and as the number of , and queries executed by . and are Zipf’s parameters [43], and is the number of bits in the biometric information of a user .
Proof.
We conduct four games, (where ), based on the attack procedures of . The term denotes the probability that wins each game by correctly guessing the result c in . The proof processes for and are shown as follows:
: This game involves attempting an attack without any information to guess a random bit c. Therefore, we can derive the following Equation (2).
: performs query to attempt an eavesdropping attack. Then, uses the query to guess whether the return value is a random string or a session key . However, is unable to compute through the eavesdropping attack. Since gains no advantage from winning , and are indistinguishable. Therefore, we obtain the following equation.
: In this game, performs an “active attack” by using “Send” and “Hash” queries. In the scheme, all parameters and messages are composed of secret keys and random numbers. In addition, they are masked by a one-way hash function , which is resistant to hash collisions. Based on the birthday paradox [44], the probability of hash collision is given by , where represents the length of a hash output and equals . As and are indistinguishable, except when the collision of happens, we can obtain the advantage of in as follows:
: Similar to , performs and queries. As explained in Section 3.2.2, the secure properties of the PUF make it difficult to guess or compute the response of the PUF. Therefore, we can obtain the following equation:
: In the final game , executes the query to obtain parameters stored in a mobile device. Then, attempts to compute secret keys , where , , , and . must simultaneously guess the user’s identity , password , and biometric secret key to calculate . Guessing all of them in polynomial time is a computationally infeasible task; hence, cannot derive the session key . Furthermore, the probability of guessing is roughly , where the length of is bits. We can apply Zipf’s law [43] on the password and executes queries. Then, we can derive the following equation:
After executing all the games, performs the query, guessing whether or . Since cannot gain any advantage in guessing c, we obtain the following equation:
By applying the triangle inequality to Equation (8), we can derive the following result:
By multiplying both sides of Equation (9) by 2, we can obtain the required result:
Therefore, we prove Theorem 1. □
7.4. AVISPA Simulation
The AVISPA [45,46] is a simulation tool to analyze the security of protocols for formal verification. In the AVISPA simulation, adversary has attack capabilities based on the DY model. The AVISPA uses “High-Level Protocol Specification Language (HLPSL)”. In this section, we show the whole process of the proposed scheme written in HLPSL codes and the output of AVISPA simulation. We use “On-the-Fly Model Checker (OFMC)” [47] and “Constraint Logic-based Attack Searcher (CL-AtSe)” [48] backend models because these two models support XOR operation. If the summary displays ‘Safe’, the scheme has been proven to resist man-in-the-middle (MitM) and replay attacks [49].
7.4.1. HLPSL Specification
This work defines four roles for user , gateway , sensor , and registration authority , denoted by “U”, “G”, “S”, and “RA”, respectively. Then, we comprise the role specifications for the session, goal, and environment of the proposed scheme. Figure 6 presents the source code for the role of , and we will explain its role in detail as an example. In the registration and authentication phases, recognizes four agents: user (U), gateway (G), sensor (S), and registration authority (RA). “(SN, RV)” means that agents send and receive messages through a public channel channel(dy) which follows the DY model. At first, initializes the state to 0 (State = 0) and receives the start signal “RV(start)”. In the state = 1, “RV({TIDi’.H(TIDi’.H(GIDk.Rk.MKra)).SIDj.ALPj’. H(H(Cj.Puf(Cj)).xor(xor(H(Cj.Puf(Cj)),H(SIDj.GIDk.MKra)),ALPj’)). H(SIDj.H(SIDj.GIDk. MKra)))}_SKru)” indicates that the receives messages from the RA. The “SKru” ensures that the registration messages are transmitted via a secure channel. After that, sends the authentication request message to through a public channel. “SN(TIDi’.M1’.M2’.M3’.V1’)” means that sends . In the state = 3, computes a session key and authenticates completely with .
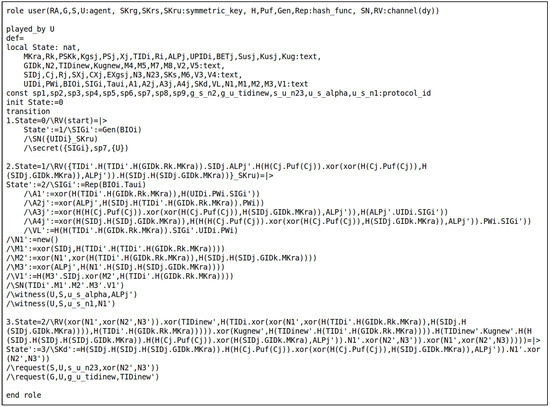
Figure 6.
Role of user (U).
7.4.2. AVISPA Simulation Result
The HLPSL code is converted into “Intermediate Format (IF)” by the AVISPA simulation translator. From the IF code, the backend models generate the simulation outputs in “Output Format (OF)”, which is ‘SUMMARY’. Figure 7 shows the summaries of the proposed scheme under the OFMC and CL-AtSe backend models. In the case of OFMC, the search time is 22.33 s and the number of visited nodes is 0. In CL-AtSe, the result reveals four analyzed states and takes 6.39 s for translation. Both simulation outputs are “SAFE,” and therefore we demonstrate that the scheme prevents replay and MitM attacks.
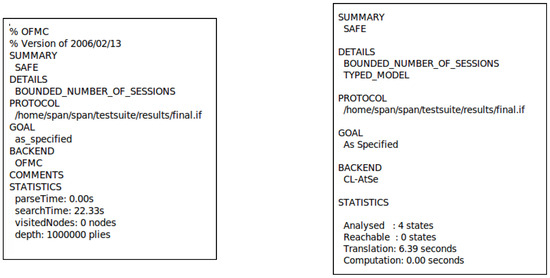
Figure 7.
Simulation results based on OFMC and CL-AtSe models.
8. Performance Comparison
This section discusses the scheme performance regarding computational costs, communication costs, energy consumption, and security features. The comparison results reveal that the scheme provides better overall performance than other related schemes.
8.1. Computational Costs
We analyzed computational costs of the proposed and related schemes [16,17,18,19,20,21,22,23,24,34,35]. We approximated the execution time for each cryptographic operation, referring to the work [50]. The execution time of operations is measured using the MIRACL library [51]. The evaluations were conducted with the following configurations on each platform:
- GWN: Intel Core i5-11400 processor (Intel Corporation, Santa Clara, CA, USA), 24 GB RAM, 2.6 GHz, running Ubuntu 20.04 LTS 64-bit.
- User and Sensor: Raspberry Pi 4 Model B (Raspberry Pi Ltd., Cambridge, UK), 8 GB RAM, ARM Cortex-A72 1.5 GHz processor, running Ubuntu 20.04 LTS 64-bit.
We do not consider the execution time for XOR, concatenation, and mod operations because these are minimal and negligible. In addition, we assume that according to [21]. Table 3 shows the execution time for each cryptographic operation.

Table 3.
Cryptographic operations and execution time (ms).
We calculate the costs required for each entity: user, gateway, and sensor node. By applying the execution time in Table 3, we calculate the computation cost of the proposed scheme as follows: (a user: ms; a gateway node: ms; a sensor node: ms). Table 4 represents the total operations and computation costs of related and proposed schemes. Although the scheme [35] has the lowest computational overhead, the proposed scheme ranks second with only a difference of 0.0716 ms. Consequently, the proposed scheme ensures high efficiency for smart city environments compared with related schemes [16,17,18,19,20,21,22,23,24,34,35]. For clarity, we include the scheme [24] in Table 4, where the “user” column refers to a smart meter (platform: “User and Sensor”), and the “sensor” column refers to a service provider (platform: “GWN”).

Table 4.
Total computational costs.
8.2. Communication Costs
According to [52], we define that the elliptic curve point, asymmetric encryption/decryption, symmetric encryption/decryption, hash digest, random nonces, identity, and timestamp are 320, 1024, 256, 160, 160, 128, and 32 bits, respectively. In the proposed scheme, four messages are exchanged between entities as described in Section 6.2. The communication costs for each message are as follows: (: 768 bits; : 640 bits; : 480 bits; : 640 bits). The total communication cost for the proposed scheme is 768 + 640 + 480 + 640 = 2528 bits. The results indicate that Alruwaili et al.’s scheme achieves the lowest communication cost, followed by the proposed scheme. However, the computational cost of Alruwaili et al.’s scheme is more than about six times higher than that of our scheme. Consequently, our scheme has a lower overall communication cost compared with related schemes [16,17,18,19,20,21,22,23,24,34,35]. Table 5 describes the communication cost analysis of each scheme.

Table 5.
Total communication costs.
8.3. Energy Consumption
During the authentication phase, energy is consumed to compute parameters and exchange messages between entities. Since sensor nodes have limited resources, the high energy consumption has the potential to affect low performance. We can calculate energy consumption as [53]. and denote the energy consumption during computation and communication, respectively. According to [53], we can calculate energy consumption of operation computation as . The energy consumption of , , , , , , and are 3.2942 mJ, 0.0126 mJ, 0.0126 mJ, 0.0056 mJ, 6.6696 mJ, 3.2942 mJ, and 0.0088 mJ. In addition, communication energy consumption can be calculated as . We assumed energy costs of sending messages J where is the bytes of messages, and receiving messages J where is the bytes of messages. Therefore, in our scheme, energy consumption of the sensor node can be assumed as mJ and mJ, i.e., 0.2078 mJ in total. The results of the energy consumption comparison are shown in Table 6.

Table 6.
Energy consumption of sensor.
8.4. Security Features
We compare the security features of the proposed scheme with those of related schemes [16,17,18,19,20,21,22,23,24]. The following describes each security feature: : “resistance to session key disclosure attacks”; : “resistance to DoS attacks”; : “resistance to replay attacks”; : “resistance to desynchronization attacks”; : “resistance to insider attacks”; : “resistance to privileged insider attacks”; : “resistance to user impersonation attacks”; : “resistance to MitM attacks”; : “resistance to forgery attacks”; : “resistance to physical capture attacks”; : “resistance to random number leakage attacks”; : “mutual authentication”; : “key agreement”; : “anonymity and untraceability”; and : “perfect forward secrecy”. The comparison results of each scheme are presented in Table 7. The results demonstrate that the proposed scheme can provide secure communication for smart cities.

Table 7.
Security features.
9. Conclusions
The implementation of IoT has advanced smart urban services, but challenges such as data privacy and security threats drive the need for secure authentication schemes. In this paper, we reviewed Nyangaresi et al.’s authentication scheme [16] for smart cities. According to cryptoanalysis of their scheme, it is vulnerable to various security attacks, such as insider, sensor node capture, user impersonation, and random number leakage attacks. Therefore, we present a secure authentication scheme to resolve these security flaws. The scheme employs only hash functions and XOR operations to reduce the computational and communication cost burdens. Moreover, the scheme applies PUF and fuzzy extractor functions to address security threats. The critical concern of this paper is ensuring resistance against various security attacks, such as physical node capture, DoS, and user impersonation. Finally, this work demonstrates the security via informal and formal security analyses and its improved performance via comparisons with related schemes. The experimental results on real devices demonstrate that the proposed scheme has suitability for real-time applications in IoT-based smart cities, offering low cost, energy efficiency, and secure communication. In future work, we plan to extend our evaluation through real-world deployment and simulation.
Author Contributions
Conceptualization, C.K.; methodology, C.K. and S.S.; software, C.K. and S.S.; validation, S.S. and Y.P.; formal analysis, C.K. and S.S.; writing—original draft preparation, C.K.; writing—review and editing, S.S. and Y.P.; supervision, Y.P.; project administration, Y.P. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korean government (Ministry of Science and ICT) (RS-2024-00450915).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Gaur, A.; Scotney, B.; Parr, G.; McClean, S. Smart city architecture and its applications based on IoT. Procedia Comput. Sci. 2015, 52, 1089–1094. [Google Scholar] [CrossRef]
- Prajapat, S.; Gautam, D.; Kumar, P.; Jangirala, S.; Das, A.K.; Park, Y.; Lorenz, P. Secure lattice-based aggregate signature scheme for vehicular Ad Hoc networks. IEEE Trans. Veh. Technol. 2024, 73, 12370–12384. [Google Scholar] [CrossRef]
- Okonta, D.E.; Vukovic, V. Smart cities software applications for sustainability and resilience. Heliyon 2024, 10, e32654. [Google Scholar] [CrossRef]
- Belli, L.; Cilfone, A.; Davoli, L.; Ferrari, G.; Adorni, P.; Di Nocera, F.; Dall’Olio, A.; Pellegrini, C.; Mordacci, M.; Bertolotti, E. IoT-enabled smart sustainable cities: Challenges and approaches. Smart Cities 2020, 3, 1039–1071. [Google Scholar] [CrossRef]
- Kim, T.H.; Ramos, C.; Mohammed, S. Smart city and IoT. Future Gener. Comput. Syst. 2017, 76, 159–162. [Google Scholar] [CrossRef]
- Mishra, P.; Singh, G. Energy management systems in sustainable smart cities based on the internet of energy: A technical review. Energies 2023, 16, 6903. [Google Scholar] [CrossRef]
- Fabrègue, B.F.; Bogoni, A. Privacy and security concerns in the smart city. Smart Cities 2023, 6, 586–613. [Google Scholar] [CrossRef]
- Shafiq, M.; Gu, Z.; Cheikhrouhou, O.; Alhakami, W.; Hamam, H. The Rise of “Internet of Things”: Review and Open Research Issues Related to Detection and Prevention of IoT-Based Security Attacks. Wireless Commun. Mobile Comput. 2022, 2022, 8669348. [Google Scholar] [CrossRef]
- Eckhoff, D.; Wagner, I. Privacy in the smart city—Applications, technologies, challenges, and solutions. IEEE Commun. Surv. Tutorials 2017, 20, 489–516. [Google Scholar] [CrossRef]
- Ashraf, J.; Keshk, M.; Moustafa, N.; Abdel-Basset, M.; Khurshid, H.; Bakhshi, A.D.; Mostafa, R.R. IoTBoT-IDS: A Novel Statistical Learning-Enabled Botnet Detection Framework for Protecting Networks of Smart Cities. Sustain. Cities Soc. 2021, 72, 103041. [Google Scholar] [CrossRef]
- Martínez-Ballesté, A.; Pérez-Martínez, P.A.; Solanas, A. The pursuit of citizens’ privacy: A privacy-aware smart city is possible. IEEE Commun. Mag. 2013, 51, 136–141. [Google Scholar] [CrossRef]
- Balaji, S.; Nathani, K.; Santhakumar, R. IoT technology, applications and challenges: A contemporary survey. Wirel. Pers. Commun. 2019, 108, 363–388. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. A robust authentication protocol for wireless medical sensor networks using blockchain and physically unclonable functions. IEEE Internet Things J. 2022, 9, 20214–20228. [Google Scholar] [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans. Intell. Transp. Syst. 2021, 23, 2316–2330. [Google Scholar] [CrossRef]
- Rao, P.M.; Deebak, B.D. Security and privacy issues in smart cities/industries: Technologies, applications, and challenges. J. Ambient Intell. Hum. Comput. 2023, 14, 10517–10553. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Abduljabbar, Z.A.; Mutlaq, K.A.A.; Bulbul, S.S.; Ma, J.; Aldarwish, A.J.Y.; Honi, D.G.; Al Sibahee, M.A.; Neamah, H.A. Smart city energy efficient data privacy preservation protocol based on biometrics and fuzzy commitment scheme. Sci. Rep. 2024, 14, 16223. [Google Scholar] [CrossRef] [PubMed]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Zou, S.; Cao, Q.; Wang, C.; Huang, Z.; Xu, G. A robust two-factor user authentication scheme-based ECC for smart home in IoT. IEEE Syst. J. 2021, 16, 4938–4949. [Google Scholar] [CrossRef]
- Kaur, D.; Kumar, D. Cryptanalysis and improvement of a two-factor user authentication scheme for smart home. J. Inf. Secur. Appl. 2021, 58, 102787. [Google Scholar] [CrossRef]
- Zou, S.; Cao, Q.; Lu, R.; Wang, C.; Xu, G.; Ma, H.; Cheng, Y.; Xi, J. A robust and effective 3-factor authentication protocol for smart factory in IIoT. Comput. Commun. 2024, 220, 81–93. [Google Scholar] [CrossRef]
- Rangwani, D.; Om, H. Four-factor mutual authentication scheme for health-care based on wireless body area network. J. Supercomput. 2022, 78, 5744–5778. [Google Scholar] [CrossRef]
- Xie, Q.; Li, K.; Tan, X.; Han, L.; Tang, W.; Hu, B. A secure and privacy-preserving authentication protocol for wireless sensor networks in smart city. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 119. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, S.; Singh, P.K. A secure and efficient computation based multifactor authentication scheme for Intelligent IoT-enabled WSNs. Comput. Electr. Eng. 2023, 105, 108495. [Google Scholar] [CrossRef]
- Badar, H.M.S.; Mahmood, K.; Akram, W.; Ghaffar, Z.; Umar, M.; Das, A.K. Secure authentication protocol for home area network in smart grid-based smart cities. Comput. Electr. Eng. 2023, 108, 108721. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the Advances in Cryptology-Eurocrypt 2004, Interlaken, Switzerland, 2–6 May 2004; pp. 523–540. [Google Scholar]
- Sumalatha, U.; Prakasha, K.K.; Prabhu, S.; Nayak, V.C. A Comprehensive Review of Unimodal and Multimodal Fingerprint Biometric Authentication Systems: Fusion, Attacks, and Template Protection. IEEE Access 2024, 12, 64300–64334. [Google Scholar] [CrossRef]
- Ali, S.S.; Ganapathi, I.I.; Mahyo, S.; Prakash, S. Polynomial Vault: A Secure and Robust Fingerprint based Authentication. IEEE Trans. Emerging Top. Comput. 2021, 9, 612–625. [Google Scholar] [CrossRef]
- Blanton, M.; Aliasgari, M. Analysis of reusability of secure sketches and fuzzy extractors. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1433–1445. [Google Scholar] [CrossRef]
- Zhang, M.; Marin, E.; Oswald, D.; Singelée, D. FuzzyKey: Comparing Fuzzy Cryptographic Primitives on Resource-Constrained Devices. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Lübeck, Germany, 11–12 November 2021; pp. 289–309. [Google Scholar]
- Maes, R. Physically Unclonable Functions: Constructions, Properties and Applications, 1st ed.; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Chuang, K.-H.; Bury, E.; Degraeve, R.; Kaczer, B.; Linten, D.; Verbauwhede, I. A physically unclonable function using soft oxide breakdown featuring 0% native BER and 51.8 fJ/bit in 40-nm CMOS. IEEE J. Solid-State Circuits 2019, 54, 2765–2776. [Google Scholar] [CrossRef]
- Wang, W.-C.; Yona, Y.; Diggavi, S.N.; Gupta, P. Design and analysis of stability-guaranteed PUFs. IEEE Trans. Inf. Forensics Security 2018, 13, 978–992. [Google Scholar] [CrossRef]
- Alruwaili, O.; Alotaibi, F.M.; Tanveer, M.; Chaoui, S.; Armghan, A. PSAF-IoT: Physically secure authentication framework for the Internet of Things. IEEE Access 2024, 12, 78549–78561. [Google Scholar] [CrossRef]
- Sarbishaei, G.; Modarres, A.M.A.; Jowshan, F.; Khakzad, F.Z.; Mokhtari, H. Smart Home Security: An Efficient Multi-Factor Authentication Protocol. IEEE Access 2024, 12, 106253–106272. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Thechniques (EUROCRYPT’02), Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- Ryu, J.; Son, S.; Lee, J.; Park, Y.; Park, Y. Design of secure mutual authentication scheme for metaverse environments using blockchain. IEEE Access 2022, 10, 98944–98958. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based Internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Kwon, D.; Son, S.; Kim, M.; Lee, J.; Das, A.K.; Park, Y. A secure self-certified broadcast authentication protocol for intelligent transportation systems in UAV-assisted mobile edge computing environments. IEEE Trans. Intell. Transp. Syst. 2024, 25, 19004–19017. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Public Key Cryptography-PKC 2005, Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3386, pp. 65–84. [Google Scholar]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the Advances in Cryptology—EUROCRYPT 2000: International Conference on the Theory and Application of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. In Computer Aided Verification; Etessami, K., Rajamani, S.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- SPAN: A Security Protocol Animator for AVISPA. Available online: https://people.irisa.fr/Thomas.Genet/span/ (accessed on 5 March 2025).
- Basin, D.; Mödersheim, S.; Vigano, L. OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Turuani, M. The CL-Atse protocol analyser. In Proceedings of the International Conference on Rewriting Techniques and Applications (RTA), Seattle, WA, USA, 12–14 August 2006; pp. 227–286. [Google Scholar]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Network Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Lee, C.; Oh, M.; Kwon, D.; Park, Y.; Park, Y. PLAKA-MD: PUF-Based Lightweight Authentication and Key Agreement Scheme for Medical Devices in IoHT. IEEE Internet Things J. 2025. early access. [Google Scholar] [CrossRef]
- MIRACL Cryptographic SDK: Multiprecision Integer and Rational Arithmetic Cryptographic Library. Available online: https://github.com/miracl/MIRACL (accessed on 5 March 2025).
- Chen, C.-M.; Chen, Z.; Kumari, S.; Lin, M.-C. Lap-ioht: A lightweight authentication protocol for the internet of health things. Sensors 2022, 22, 5401. [Google Scholar] [CrossRef] [PubMed]
- Sun, Y.; Cao, J.; Ma, M.; Zhang, Y.; Li, H.; Niu, B. EAP-DDBA: Efficient anonymity proximity device discovery and batch authentication mechanism for massive D2D communication devices in 3GPP 5G HetNet. IEEE Trans. Depend. Secur. Comput. 2020, 19, 370–387. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).