Orchestrating Isolated Network Slices in 5G Networks
Abstract
1. Introduction
- We propose an integrated XVPN-OSM architecture that provides XVPN-as-a-Service (XVPNaaS) with (1) security isolation that results in secure communication between the involved VNFs of NSs, and NSIs, and (2) performance isolation between the slices.
- Since VNFs are instantiated in multiple domains architecture, a tenant may need or ask for the end-to-end confidentiality of the traffic passing the VNFs; thus, the presented architecture provides a point-to-point VPN solution.
- We implement a Proof-of-Concept (PoC) and evaluate the performance of different VPN solutions for providing slice isolation in a 5G SA environment.
- Our PoC involves an automated service instantiation incorporating WireGuard, OpenVPN and IPSec as VPN solutions. We use Open-Source MANO (OSM) [6] to orchestrate NSs and NSIs and establish different VPN tunnels between the VNFs. The OSM Northbound Interface (OSM-NBI) and juju proxy charms enable us to manage the different VPN solutions with our API easily.
- The performance evaluation shows that the presented XVPN-OSM architecture meets the required KPI values, including high throughput for eMBB slices and low latency for URLLC slices.
2. Background
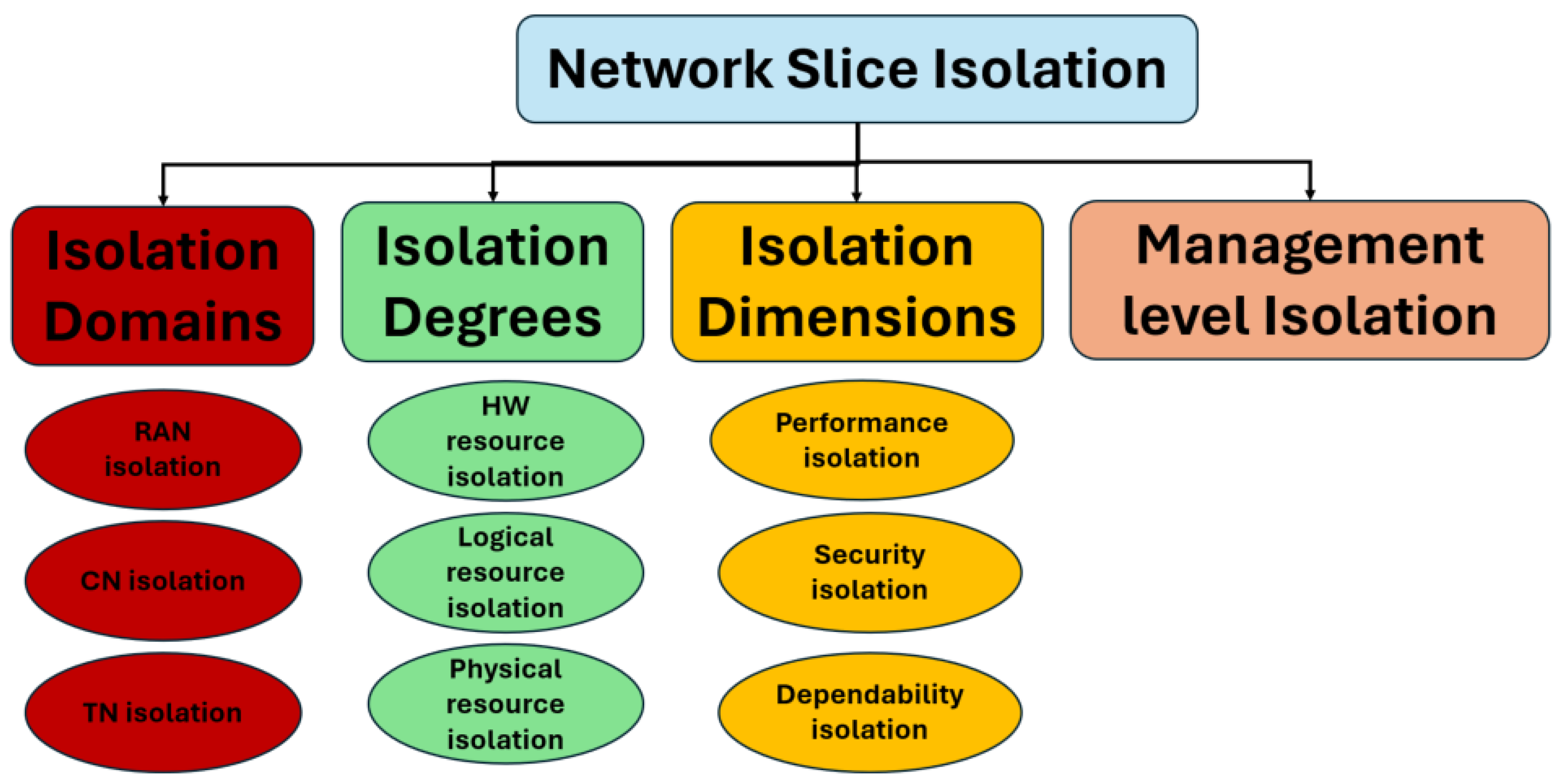
2.1. Isolation Concept
- Isolation dimensions: security, dependability and performance;
- Isolation degrees: hardware, physical and logical resources;
- Isolation domains: Radio Access Network (RAN), Transport Network (TN) and Core Network (CN); and
- Management level isolation.
2.2. Related Work
3. XVPN-OSM System Architecture
- The Day-0 phase pertains to the instantiation of the VNF, which involves creating and editing charms, developing and validating VNF/NS/NSI Descriptors (VNFD/NSD/NSID) and VNF packaging and emulating;
- The Day-1 phase is focused on initializing the service, which comprises testing, releasing and deploying it;
- And finally, the Day-2 phase deals with the runtime actions of the VNFs, which includes operating and monitoring them.
4. XVPN-OSM Implementation
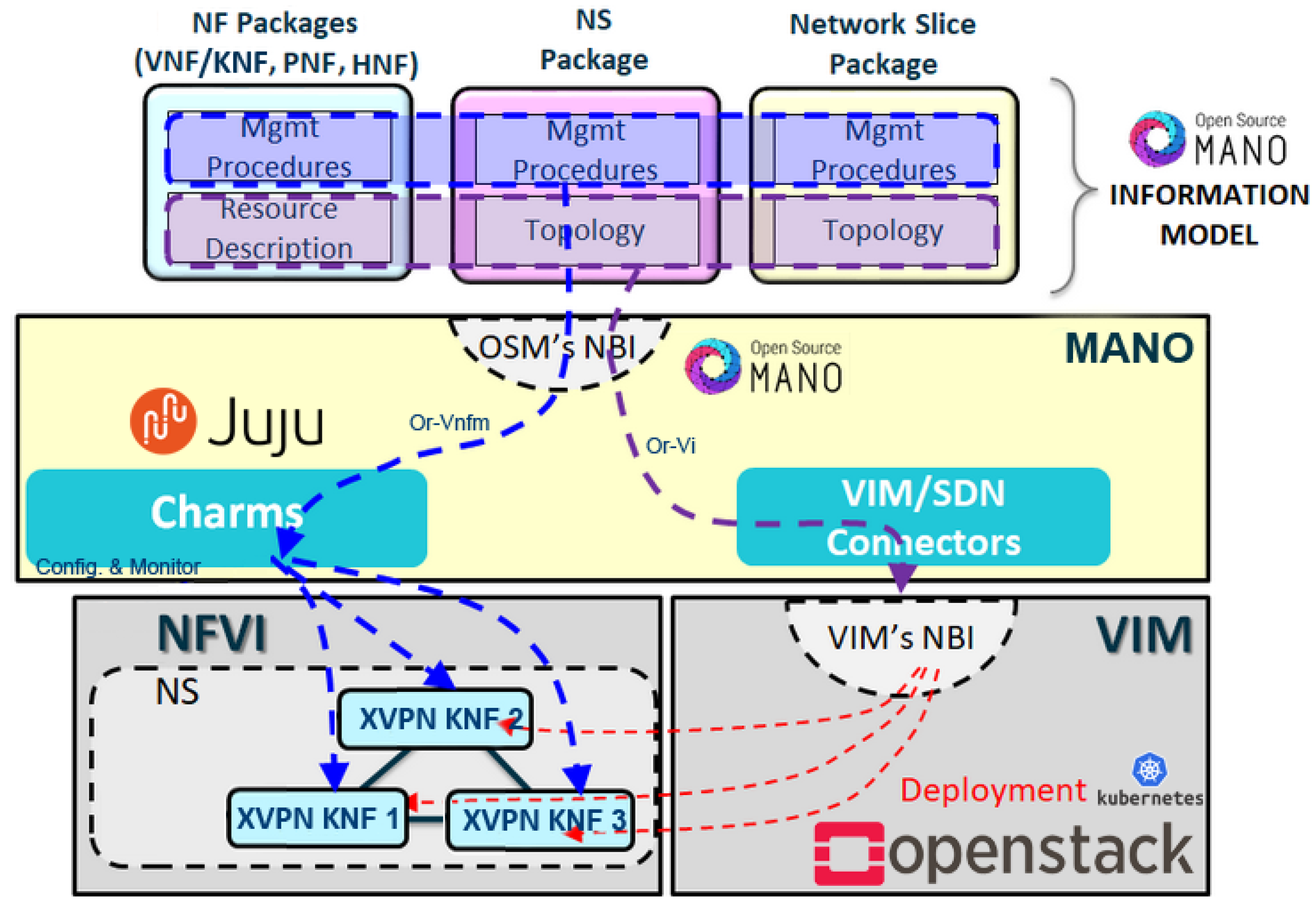
- Composing virtualized 5G SA services: The system architecture is given in Figure 4. For the sake of simplicity in the illustration, Figure 4 illustrates only one of the possibilities in which an E2E eMBB NSI with WG isolation has been established and the connection points and virtual links are not drawn. We implement the 5G network’s main components according to the free5GC solution, which includes:
- Virtualized version of UE generating real-life traffic along with gNB in the RAN domain;
- User Plane Function (UPF) in the Edge domain;
- Authentication Server Function (AUSF), Network Slice Selection Function (NSSF), Policy Control Function (PCF), Network Repository Function (NRF), Unified Data Repository (UDR), Access and Mobility Management Function (AMF), Session Management Function (SMF), Unified Data Management (UDM) and MongoDB in the CN domain.
When connecting the UEs to the gNB, the air interface is simulated, resembling the real wireless link. Then, we verify that the diverse Edge and CN components operate as anticipated and deliver service to the UEs. The UEs then connect to an external network through the UPF and via the gNB. In this first implementation step, we still need to include a VPN solution between the involved components. Our architecture builds the NS by spreading the service components into separate KNFs. This approach allows splitting the KNFs into two separate Kubernetes clusters called RAN/Edge cluster and Core cluster. These two Kubernetes clusters are deployed on two OpenStack VIMs. Such a multi-VIM environment allows us to emulate cases in which the Edge component (UPF) can be deployed closer to the end-users. This policy enables us to mimic the MEC technology in order to overcome the latency requirement in URLLC use cases. The KNFs distributed to the remote site can communicate with the CN securely with the help of an established VPN solution. - Automatic XVPN Peering: Manually setting up VPN tunnels between several interfaces can be time-consuming. Thus, we use Juju relations for automatic peering, with no extra information given to the other end of the peer at the time of instantiating the NS. The first step in the automatic peering is the establishment of relationships between KNFs on both sides. Then the paired KNFs retrieve information like a public key, endpoint and listening port to communicate with each other. To establish XVPN connectivity on all interfaces, we changed the IP address configuration in the components. Changing the interface addresses is necessary to route application data over the XVPN tunnel and, at the same time to ensure that applications inside the KNF have been installed and started correctly, even when waiting for the tunnel establishment. Besides, to verify that the NS runs a specific VPN solution, we connect UEs and observe that they connect to the Data Network (an external network such as the Internet) and they get service.
- NST creation: After having a working NS with XVPN connectivity between the interfaces, we include it in two NSTs, for eMBB and for URLLC services, to observe if and how the performance is affected by providing security with each VPN solution. The NSTs have different values of quality indicators corresponding to different 5G QoS Identifiers (5QIs) [29]. The QoS parameters correspond to eMBB and URLLC use cases, respectively. Further, the NSTs are prepared with only the management interfaces of the KNFs. The management interfaces are attached to the external connection points in the NSTs.
- Multi-VIM deployment: When using OpenStack, the external floating IP address is, by default, unknown inside a VM or a container. However, the VCA can retrieve the management IP address to perform its actions. To find the floating IP addresses of the KNFs, we use the same function that Juju employs for its proxypeer connection between a Juju unit at the VCA and the Kubernetes Deployment Unit (KDU) in the KNF. After the endpoint IP address is found, the 5G SA components on separate VIMs connect automatically with the created VPN connectivity. A requirement for Multi-VIM connectivity is to deploy a port opened in the firewalls.
- Append installation of a specific VPN solution (IPSec, OpenVPN or WireGuard) in cloud-init.
- Include name and parameters for Day-1 and Day-2 actions in the actions.yaml file.
- Implement relations between VNFs in the metadata.yaml file.
- Include the Python code to append the charm script. The name of the relationship must correspond to the name used in metadata.yaml and the listener in the __init__ function of the Python script.
- Implement the actions from actions.yaml into Day-1 and Day-2 operations in the VNFDs. The relevant actions need to be implemented in the initial-config-primitive section in the VNFDs in order to create the XVPN tunnel as a Day-1 operation. Day-2 actions are positioned in the config-primitive section.
- Employ Day-2 actions for additional configuration and maintenance (establishing a new connection to a VNF) while the default implementation sets up the XVPN.
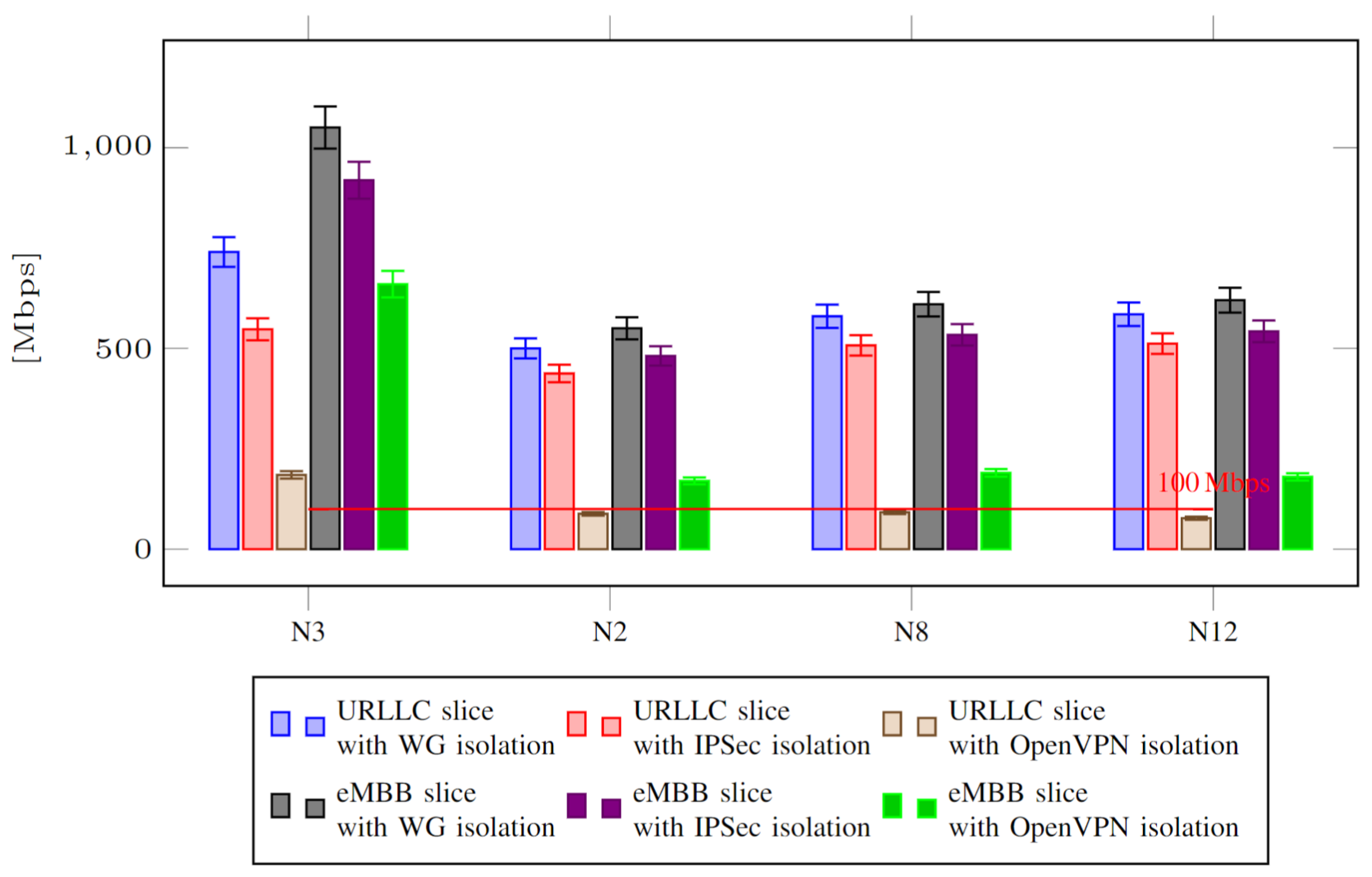
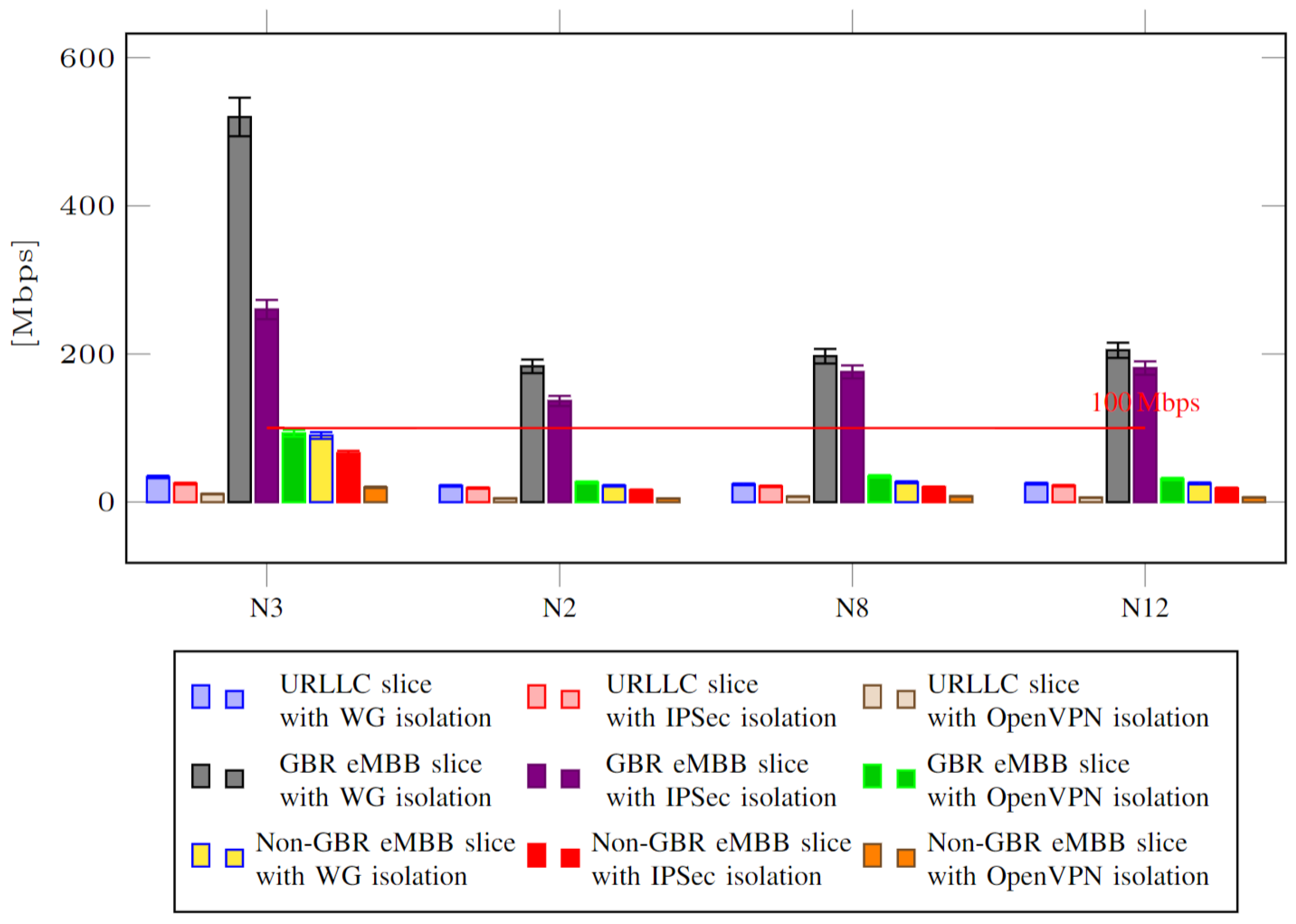
5. Results
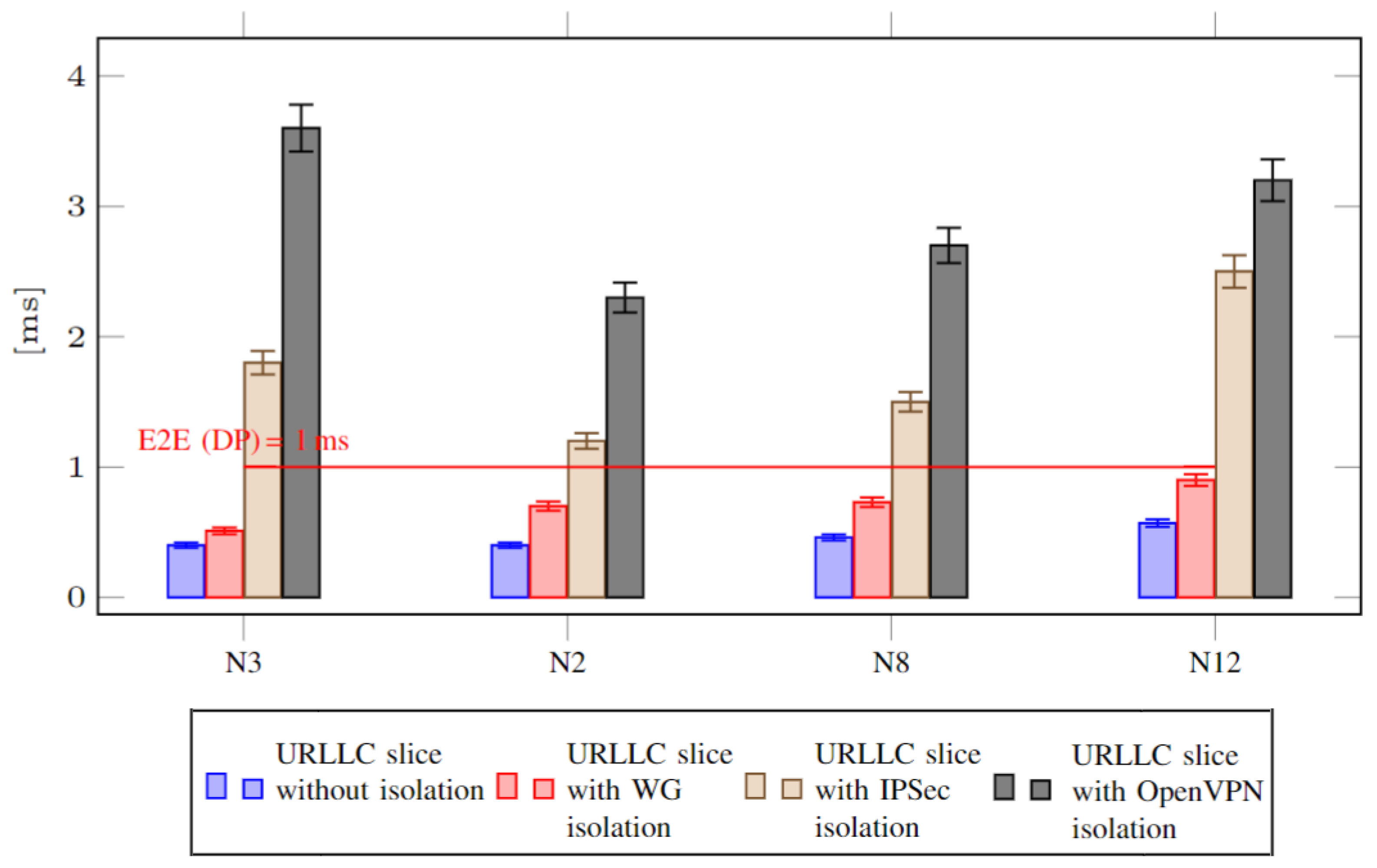
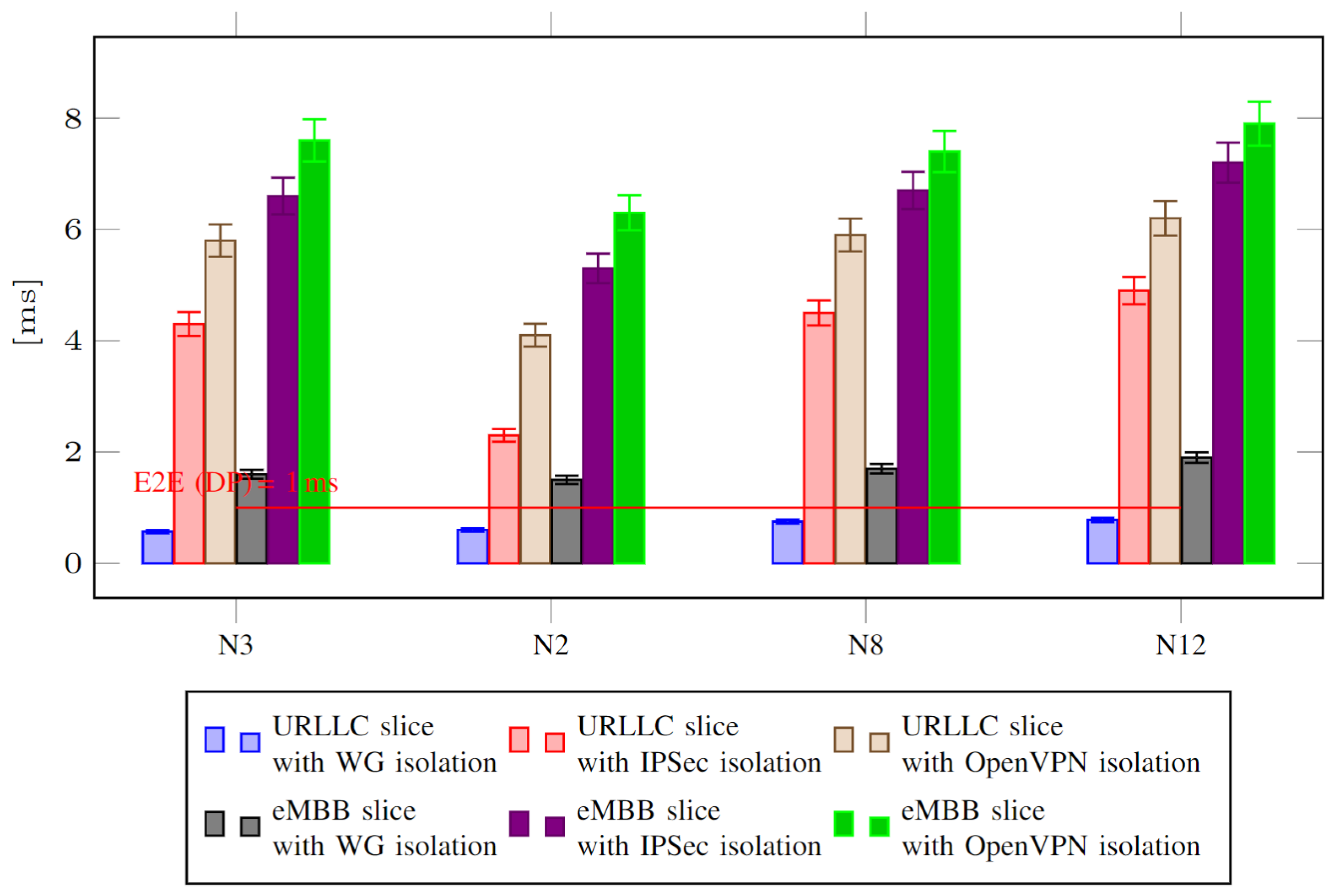
- Measuring throughput and latency in the DP over the N3 interface (which connects gNB and UPF);
- Measuring throughput and latency between components in the CP over the N2 interface (which connects gNB and AMF), N8 interface (which connects AMF and UDM) and N12 interface (which connects AMF and AUSF).
5.1. Lab Environment
- Kubernetes cluster (RAN/Edge cluster) for the DP components with all worker nodes operating kernel 5.0.0-23-generic, with gtp5g kernel module;
- Kubernetes cluster (Core cluster) for the CP components with a persistent volume provisioner and SCTP support;
- Multus-Container Network Interface (Multus-CNI) deployed on each cluster;
- Helm3 to communicate with each cluster;
- A physical network interface on each Kubernetes node on the two clusters; and
- A physical network interface on each Kubernetes node on the DP cluster to connect the UPF to the Data Network.
5.2. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| Abb. | Definition | Abb. | Definition |
| 5G | fifth-generation | API | Application Programming Interface |
| AMF | Access and Mobility Management Function | AUSF | Authentication Server Function |
| CN | Core Network | CP | Control Plane |
| CNI | Container Network Interface | DDoS | Distributed Denial-of-Service |
| DP | Data Plane | E2E | End-to-End |
| GBR | Guaranteed Bit Rate | IMSI | International Mobile Subscriber Identity |
| KDU | Kubernetes Deployment Unit | KMS | Key Management System |
| KNF | Kubernetes-based VNF | KPI | Key Performance Indicator |
| LCM | Life-Cycle Management | MANO | Management and Orchestration |
| MEC | Multi-access Edge Computing | MNO | Mobile Network Operator |
| NBI | Northbound Interface | NFV | Network Function Virtualization |
| NFVI | NFV Infrastructure | NS | Network Service |
| NSD | NS Descriptor | NSI | Network Slice Instance |
| NSID | NSI Descriptor | NSSF | Network Slice Selection Function |
| NRF | Network Repository Function | PCF | Policy Control Function |
| PoC | Proof-of-Concept | QoS | Quality-of-Service |
| QI | QoS Identifier | RAN | Radio Access Network |
| SA | Standalone | SF | Service Function |
| SDN | Software-Defined Networking | SMF | Session Management Function |
| SSH | Secure Shell | SSL | Secure Socket Layer |
| SSTP | Secure Socket Tunneling Protocol | TN | Transport Network |
| TLS | Transport Layer Security | UPF | User Plane Function |
| URLLC | Ultra-Reliable Low-Latency Communications | VCA | VNF Configuration and Abstraction |
| VM | Virtual Machine | VNFD | VNF Descriptor |
| VIM | Virtualized Infrastructure Manager | VPN | Virtual Private Network |
| VPNaaS | VPN-as-a-Service | WG | WireGuard |
References
- Blanco, B.; Fajardo, J.O.; Giannoulakis, I.; Kafetzakis, E.; Peng, S.; Pérez-Romero, J.; Trajkovska, I.; Sayyad Khodashenas, P.; Goratti, L.; Paolino, M.; et al. Technology pillars in the architecture of future 5G mobile networks: NFV, MEC and SDN. Comput. Stand. Interfaces 2017, 54, 216–228. [Google Scholar] [CrossRef]
- Kotulski, Z.; Nowak, T.; Sepczuk, M.; Tunia, M.; Artych, R.; Bocianiak, K.; Osko, T.; Wary, J. On end-to-end approach for slice isolation in 5G networks. Fundamental challenges. In Proceedings of the Federated Conference on Computer Science and Information Systems (FedCSIS), Prague, Czech Republic, 3–6 September 2017; pp. 783–792. [Google Scholar]
- Kotulski, Z.; Nowak, T.W.; Sepczuk, M.; Tunia, M.A. 5G networks: Types of isolation and their parameters in RAN and CN slices. Comput. Netw. 2020, 171, 107135. [Google Scholar] [CrossRef]
- Schneider, P.; Mannweiler, C.; Kerboeuf, S. Providing strong 5G mobile network slice isolation for highly sensitive third-party services. In Proceedings of the IEEE Wireless Comm. and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Whitestack. Open Multi-Vendor NFV Showcase, 1st ed.; Technical Report; ETSI: Sophia Antipolis, France, 2019. [Google Scholar]
- ETSI OSM. Deploying a 5G Network. Available online: https://osm.etsi.org/ (accessed on 3 July 2023).
- Gonzalez, A.J.; Ordonez-Lucena, J.; Helvik, B.E.; Nencioni, G.; Xie, M.; Lopez, D.R.; Grønsund, P. The isolation concept in the 5G network slicing. In Proceedings of the 2020 European Conference on Networks and Communications (EuCNC), Dubrovnik, Croatia, 15–18 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 12–16. [Google Scholar]
- Kotulski, Z.; Nowak, T.W.; Sepczuk, M.; Tunia, M.; Artych, R.; Bocianiak, K.; Osko, T.; Wary, J.P. Towards constructive approach to end-to-end slice isolation in 5G networks. EURASIP J. Inf. Secur. 2018, 2018, 2. [Google Scholar] [CrossRef]
- Cominardi, L.; Deiss, T.; Filippou, M.; Sciancalepore, V.; Giust, F.; Sabella, D. MEC support for network slicing: Status and limitations from a standardization viewpoint. IEEE Commun. Stand. Mag. 2020, 4, 22–30. [Google Scholar] [CrossRef]
- Salahdine, F.; Liu, Q.; Han, T. Towards secure and intelligent network slicing for 5g networks. IEEE Open J. Comput. Soc. 2022, 3, 23–38. [Google Scholar] [CrossRef]
- Gligoroski, D.; Kralevska, K. Expanded Combinatorial Designs as Tool to Model Network Slicing in 5G. IEEE Access 2019, 7, 54879–54887. [Google Scholar] [CrossRef]
- Sathi, V.N.; Srinivasan, M.; Thiruvasagam, P.K.; Chebiyyam, S.R.M. A Novel Protocol for Securing Network Slice Component Association and Slice Isolation in 5G Networks. In Proceedings of the Proceedings of the 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, MSWIM ’18, Montreal, QC, Canada, 28 October–2 November 2018; pp. 249–253. [Google Scholar]
- Marabissi, D.; Fantacci, R. Highly Flexible RAN Slicing Approach to Manage Isolation, Priority, Efficiency. IEEE Access 2019, 7, 97130–97142. [Google Scholar] [CrossRef]
- Sattar, D.; Matrawy, A. Towards Secure Slicing: Using Slice Isolation to Mitigate DDoS Attacks on 5G Core Network Slices. In Proceedings of the 2019 IEEE Conference on Communications and Network Security (CNS), Washington, DC, USA, 10–12 June 2019; pp. 82–90. [Google Scholar]
- Kim, H. 5G core network security issues and attack classification from network protocol perspective. J. Internet Serv. Inf. Secur. 2020, 10, 1–15. [Google Scholar]
- Hantouti, H.; Benamar, N.; Taleb, T. Service Function Chaining in 5G amp; Beyond Networks: Challenges and Open Research Issues. IEEE Netw. 2020, 34, 320–327. [Google Scholar] [CrossRef]
- Mahyoub, M.; Abdulghaffar, A.; Alalade, E.; Matrawy, A. A Security-aware Network Function Sharing Model for 5G Slicing. arXiv 2023, arXiv:2303.03492. [Google Scholar]
- Srinivasan, T.; Venkatapathy, S.; Jo, H.G.; Ra, I.H. VNF-Enabled 5G Network Orchestration Framework for Slice Creation, Isolation and Management. J. Sens. Actuator Netw. 2023, 12, 65. [Google Scholar] [CrossRef]
- Alemany, P.; Molina, A.; Dangerville, C.; Asensio, R.; Ayed, D.; Muñoz, R.; Casellas, R.; Martínez, R.; Skarmeta, A.; Vilalta, R. Management and enforcement of secured E2E network slices across transport domains. Opt. Fiber Technol. 2022, 73, 103010. [Google Scholar] [CrossRef]
- Chang, C.Y.; Ruiz, T.G.; Paolucci, F.; Jiménez, M.A.; Sacido, J.; Papagianni, C.; Ubaldi, F.; Scano, D.; Gharbaoui, M.; Giorgetti, A.; et al. Performance isolation for network slices in industry 4.0: The 5growth approach. IEEE Access 2021, 9, 166990–167003. [Google Scholar] [CrossRef]
- Haga, S.; Esmaeily, A.; Kralevska, K.; Gligoroski, D. 5G Network Slice Isolation with WireGuard and Open Source MANO: A VPNaaS Proof-of-Concept. In Proceedings of the 2020 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Leganes, Spain, 10–12 November 2020; pp. 181–187. [Google Scholar] [CrossRef]
- Vidal, I.; Nogales, B.; Lopez, D.; Rodríguez, J.; Valera, F.; Azcorra, A. A Secure Link-Layer Connectivity Platform for Multi-Site NFV Services. Electronics 2021, 10, 1868. [Google Scholar] [CrossRef]
- Kielland, S.; Esmaeily, A.; Kralevska, K.; Gligoroski, D. Secure Service Implementation with Slice Isolation and WireGuard. In Proceedings of the 2022 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Athens, Greece, 5–8 September 2022; pp. 148–153. [Google Scholar] [CrossRef]
- ETSI OSM. ETSI-NFV-NSD. Available online: http://osm-download.etsi.org/repository/osm/debian/ReleaseTEN/docs/osm-im/osm_im_trees/etsi-nfv-nsd.html (accessed on 3 July 2023).
- ETSI OSM. ETSI-NFV-VNFD. Available online: https://tinyurl.com/2p9yp7cr (accessed on 3 July 2023).
- ETSI Community. Osm Scope, Functionality, Operation and Integration Guidelines; Standard Issue 1; European Telecommunications Standards Institute: Sophia Antipolis, France, 2019. [Google Scholar]
- Technical Team. Deploying a 5G Network. Available online: https://free5gc.org/ (accessed on 3 July 2023).
- Esmaeily, A.; Kralevska, K.; Gligoroski, D. A Cloud-based SDN/NFV Testbed for End-to-End Network Slicing in 4G/5G. In Proceedings of the 2020 6th IEEE Conference on Network Softwarization (NetSoft), Ghent, Belgium, 29 June–3 July 2020; pp. 29–35. [Google Scholar] [CrossRef]
- ETSI. System architecture for the 5G System (5GS); Technical Report TS 123 501 V16.6.0; ETSI: Sophia Antipolis, France, 2020. [Google Scholar]
- ETSI. Why Do We Need 5G? Available online: https://www.etsi.org/technologies/mobile/5g (accessed on 3 July 2023).
- 3GPP. Study on Scenarios and Requirements for Next Generation Access Technologies; V18.0.0; 3GPP: Sophia Antipolis, France, 2024. [Google Scholar]
- Fettweis, G.; Boche, H.; Wiegand, T.; Zielinski, E.; Schotten, H.; Merz, P.; Hirche, S.; Festag, A.; Häffner, W.; Meyer, M.; et al. The Tactile Internet-ITU-T Technology Watch Report; International Telecommunication Union (ITU): Geneva, Switzerland, 2014. [Google Scholar]
- Mohammed, N.A.; Mansoor, A.M.; Ahmad, R.B. Mission-critical machine-type communication: An overview and perspectives towards 5G. IEEE Access 2019, 7, 127198–127216. [Google Scholar] [CrossRef]
- 5Gamericas. New Services and Applications With 5G Ultra-Reliable Low Latency Communications. Available online: https://www.5gamericas.org/wp-content/uploads/2019/07/5G_Americas_URLLLC_White_Paper_Final__updateJW.pdf (accessed on 16 April 2024).
- Khichane, A. Setup free5GC on Multiple Clusters. Available online: https://github.com/free5gc/free5gc. (accessed on 3 July 2023).
- ETSI OSM. OSM Usage. Available online: https://osm.etsi.org/docs/user-guide/latest/05-osm-usage.html#osm-usage. (accessed on 3 July 2023).


| Related Work | 5G SA PoC | Cloud-Native | Isolation Type | SoA VPN Solutions |
|---|---|---|---|---|
| [12] | ✗ | ✗ | Security | ✗ |
| [13] | ✗ | ✗ | Performance | ✓ |
| [14] | ✗ | ✗ | Security | ✗ |
| [15] | ✗ | ✗ | Security | ✓ |
| [16] | ✗ | ✗ | ✗ | ✗ |
| [17] | ✗ | ✗ | Security & performance | ✗ |
| [18] | ✗ | ✗ | Security & performance | ✓ |
| [19] | ✗ | ✗ | Security | ✗ |
| [20] | ✗ | ✗ | Performance | ✗ |
| [21] | ✗ | ✗ | Security & performance | ✓ |
| [22] | ✗ | ✗ | Performance | ✓ |
| [23] | ✗ | ✗ | Security & performance | ✓ |
| This work | ✓ | ✓ | Security & performance | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Esmaeily, A.; Kralevska, K. Orchestrating Isolated Network Slices in 5G Networks. Electronics 2024, 13, 1548. https://doi.org/10.3390/electronics13081548
Esmaeily A, Kralevska K. Orchestrating Isolated Network Slices in 5G Networks. Electronics. 2024; 13(8):1548. https://doi.org/10.3390/electronics13081548
Chicago/Turabian StyleEsmaeily, Ali, and Katina Kralevska. 2024. "Orchestrating Isolated Network Slices in 5G Networks" Electronics 13, no. 8: 1548. https://doi.org/10.3390/electronics13081548
APA StyleEsmaeily, A., & Kralevska, K. (2024). Orchestrating Isolated Network Slices in 5G Networks. Electronics, 13(8), 1548. https://doi.org/10.3390/electronics13081548







