Securing the Internet of Health Things: Embedded Federated Learning-Driven Long Short-Term Memory for Cyberattack Detection
Abstract
1. Introduction
- We employ embedded feature selection techniques to minimize the computational complexity of the cyberattack detection model.
- We propose a novel approach for detecting multiple cyberattacks in IoHT environments using a Federated Learning (FL) framework integrated with Long Short-Term Memory (LSTM) networks (FL-LSTM).
- We ensure data privacy by enabling individual IoHT devices to collaboratively train a global model without sharing local data, thereby maintaining patient confidentiality.
- We utilize LSTM networks, known for their effectiveness in handling time-series data, to capture and analyze temporal patterns indicative of cyberthreats.
2. Related Work
3. Materials and Methods
3.1. Research Background
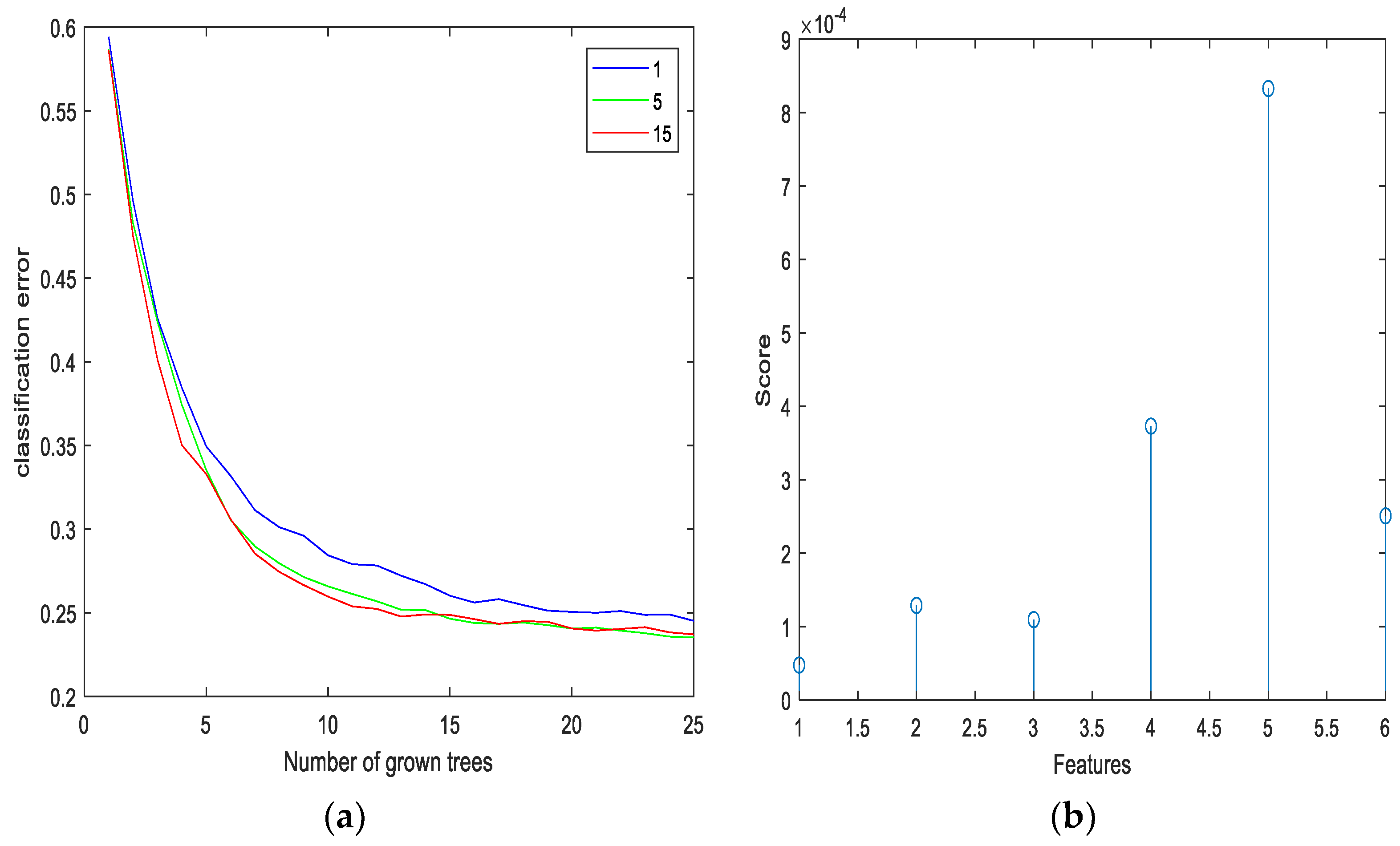
3.2. Research Dataset and Preprocessing
- ARP poisoning (ARP spoofing): In this type of attack, the attacker sends spoofed ARP messages over LAN networks and redirects the traffic from the intended host to the attacker. This diverts the traffic from the target address to another IP address, and subsequently generates a huge amount of malicious ARP packets in Wireshark.
- Denial-of-Service (DoS) attack: DoS attacks usually entail large amounts of data being sent to the server, potentially impacting its reliability or stability. This is realized with the help of Ettercap, an open-source network security tool for man-in-the-middle attacks on local area networks (LANs).
- Smurf attack: A Smurf attack is a kind of distributed DoS attack. Usually, a high quantity of echo requests will be flooded into the server during this type of attack.
- Nmap port scan: Nmap port scans are categorized as a type of attack in the ECU-IOHT dataset, underscoring their role in the reconnaissance phase of cyberattacks.
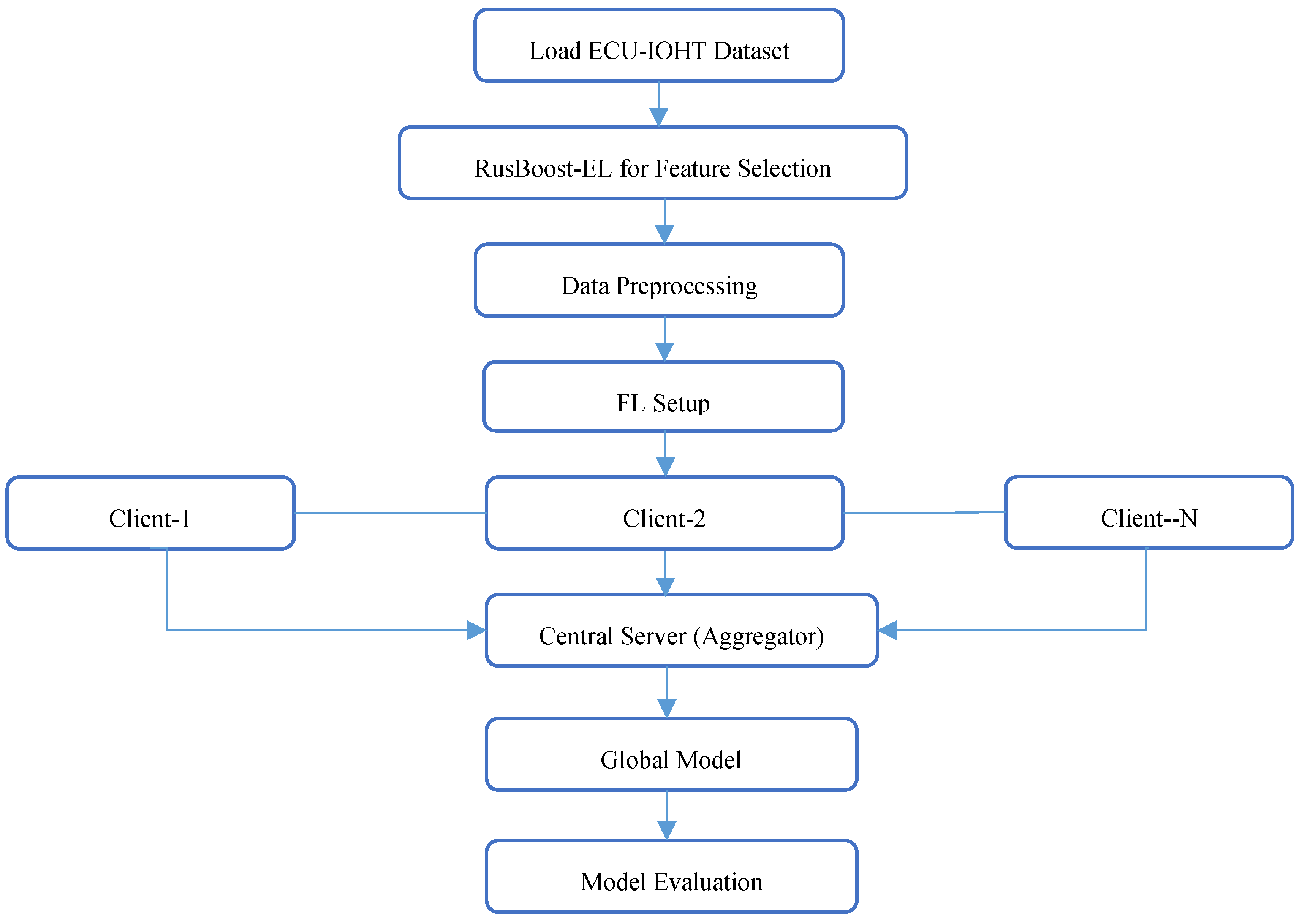
3.3. Proposed Embedded Federated Learning-Driven Long Short-Term Memory (EFL-LSTM) Model
4. Subjective and Quantitative Evaluation
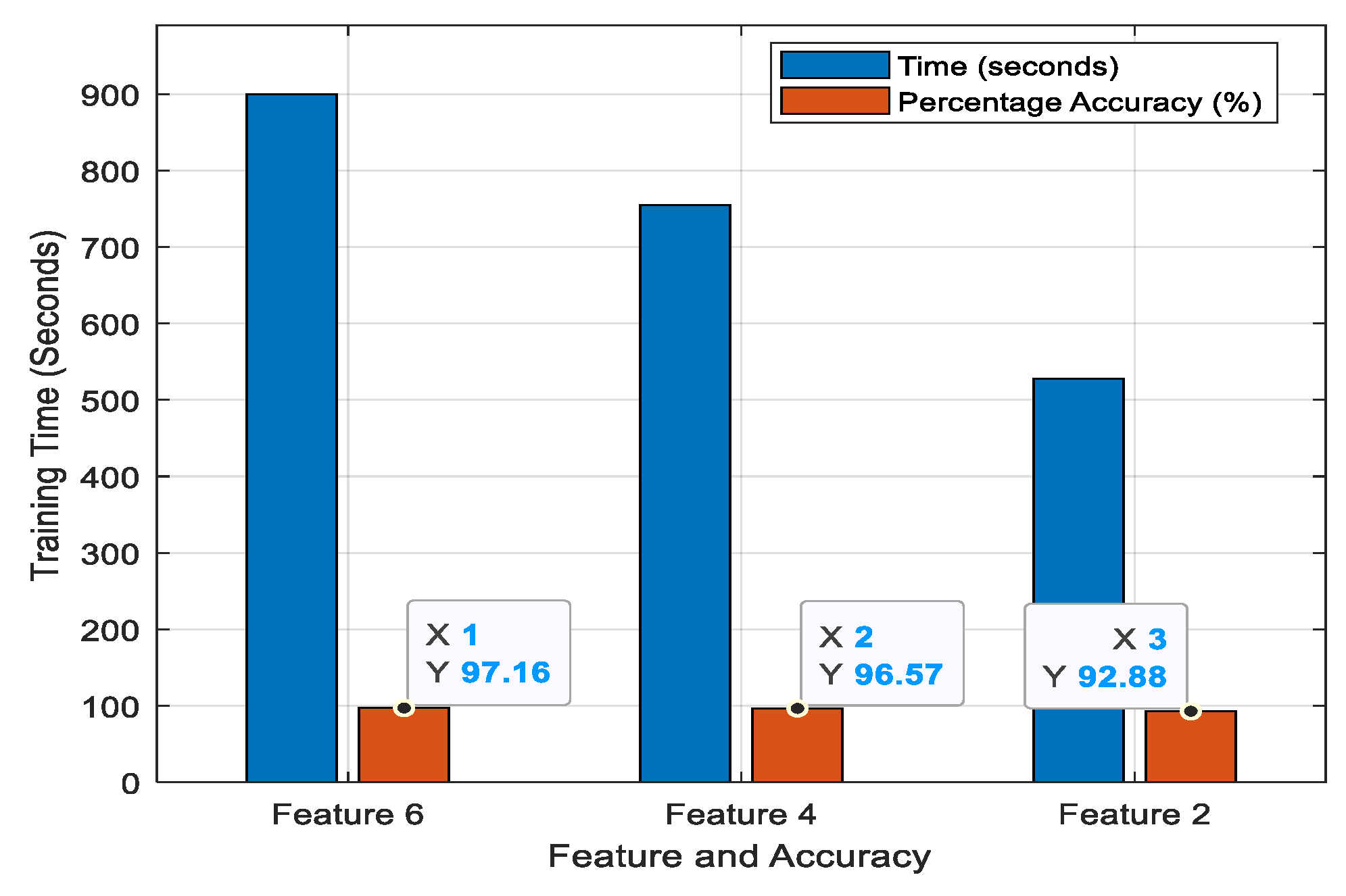
4.1. Subjective Analysis
4.2. Quantitative Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhang, Y.; Zhu, D.; Wang, M.; Li, J.; Zhang, J. A Comparative Study of Cyber Security Intrusion Detection in Healthcare Systems. Int. J. Crit. Infrastruct. Prot. 2024, 44, 100658. [Google Scholar] [CrossRef]
- Saheed, Y.K.; Arowolo, M.O. Efficient Cyber Attack Detection on the Internet of Medical Things-Smart Environment Based on Deep Recurrent Neural Network and Machine Learning Algorithms. IEEE Access 2021, 9, 161546–161554. [Google Scholar] [CrossRef]
- Suleski, T.; Ahmed, M.; Yang, W.; Wang, E. A Review of Multi-Factor Authentication in the Internet of Healthcare Things. Digit. Health 2023, 9, 20552076231177144. [Google Scholar] [CrossRef] [PubMed]
- Suleski, T.; Ahmed, M. A Data Taxonomy for Adaptive Multifactor Authentication in the Internet of Health Care Things. J. Med. Internet Res. 2023, 25, e44114. [Google Scholar] [CrossRef] [PubMed]
- Donga, L.; Raj, R.K.; Mishra, S. Internet of Healthcare Things (IoHT): Towards a Digital Chain of Custody. In Proceedings of the 2022 IEEE 10th International Conference on Healthcare Informatics (ICHI 2022), Dallas, TX, USA, 14–17 June 2022; pp. 524–526. [Google Scholar] [CrossRef]
- Siemens Healthcare GmbH. Embracing Healthcare 4.0. Available online: https://www.siemens-healthineers.com/insights/news/embracing-healthcare-4-0.html (accessed on 13 June 2024).
- Si-Ahmed, A.; Al-Garadi, M.A.; Boustia, N. Survey of Machine Learning Based Intrusion Detection Methods for Internet of Medical Things. Appl. Soft Comput. 2022, 140, 110227. [Google Scholar] [CrossRef]
- Rasool, R.U.; Ahmad, H.F.; Rafique, W.; Qayyum, A.; Qadir, J. Security and Privacy of Internet of Medical Things: A Contemporary Review in the Age of Surveillance, Botnets, and Adversarial ML. J. Netw. Comput. Appl. 2022, 201, 103332. [Google Scholar] [CrossRef]
- Mohamad Noor, M.B.; Hassan, W.H. Current Research on Internet of Things (IoT) Security: A Survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Algethami, S.A.; Alshamrani, S.S. A Deep Learning-Based Framework for Strengthening Cybersecurity in Internet of Health Things (IoHT) Environments. Appl. Sci. 2024, 14, 4729. [Google Scholar] [CrossRef]
- Al Abdulwahid, A. Detection of Middlebox-Based Attacks in Healthcare Internet of Things Using Multiple Machine Learning Models. Comput. Intell. Neurosci. 2022, 2022, 2037954. [Google Scholar] [CrossRef]
- Firat Kilincer, I.; Ertam, F.; Sengur, A.; Tan, R.S.; Rajendra Acharya, U. Automated Detection of Cybersecurity Attacks in Healthcare Systems with Recursive Feature Elimination and Multilayer Perceptron Optimization. Biocybern. Biomed. Eng. 2023, 43, 30–41. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and Development of RNN Anomaly Detection Model for IoT Networks. IEEE Access 2022, 10, 62722–62750. [Google Scholar] [CrossRef]
- Singh, S.K.; Kumar, M.; Tanwar, S.; Park, J.H. GRU-Based Digital Twin Framework for Data Allocation and Storage in IoT-Enabled Smart Home Networks. Future Gener. Comput. Syst. 2024, 153, 391–402. [Google Scholar] [CrossRef]
- Kumar, M.; Kumar Singh, S.; Kim, S. Predictive Analytics for Mortality: FSRNCA-FLANN Modeling Using Public Health Inventory Records. IEEE Access 2024, 12, 81252–81264. [Google Scholar] [CrossRef]
- Mothukuri, V.; Khare, P.; Parizi, R.M.; Pouriyeh, S.; Dehghantanha, A.; Srivastava, G. Federated-Learning-Based Anomaly Detection for IoT Security Attacks. IEEE Internet Things J. 2022, 9, 2545–2554. [Google Scholar] [CrossRef]
- Hijazi, N.M.; Aloqaily, M.; Guizani, M.; Ouni, B.; Karray, F. Secure Federated Learning with Fully Homomorphic Encryption for IoT Communications. IEEE Internet Things J. 2023, 11, 4289–4300. [Google Scholar] [CrossRef]
- Rashid, M.M.; Kamruzzaman, J.; Hassan, M.M.; Imam, T.; Gordon, S. Cyberattacks Detection in Iot-Based Smart City Applications Using Machine Learning Techniques. Int. J. Environ. Res. Public Health 2020, 17, 9347. [Google Scholar] [CrossRef]
- Saharkhizan, M.; Azmoodeh, A.; Dehghantanha, A.; Choo, K.K.R.; Parizi, R.M. An Ensemble of Deep Recurrent Neural Networks for Detecting IoT Cyber Attacks Using Network Traffic. IEEE Internet Things J. 2020, 7, 8852–8859. [Google Scholar] [CrossRef]
- Khan, F.; Jan, M.A.; Alturki, R.; Alshehri, M.D.; Shah, S.T.; Rehman, A.U. A Secure Ensemble Learning-Based Fog-Cloud Approach for Cyberattack Detection in IoMT. IEEE Trans. Ind. Inform. 2023, 19, 10125–10132. [Google Scholar] [CrossRef]
- Rehman, S.U.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Shafiq, M.; Javed, A.R.; Jalil, Z.; Bashir, A.K. DIDDOS: An Approach for Detection and Identification of Distributed Denial of Service (DDoS) Cyberattacks Using Gated Recurrent Units (GRU). Future Gener. Comput. Syst. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Al-Kahtani, M.S.; Mehmood, Z.; Sadad, T.; Zada, I.; Ali, G.; Elaffendi, M. Intrusion Detection in the Internet of Things Using Fusion of GRU-LSTM Deep Learning Model. Intell. Autom. Soft Comput. 2023, 37, 2279–2290. [Google Scholar] [CrossRef]
- Hong, W.C.; Huang, D.R.; Chen, C.L.; Lee, J.S. Towards Accurate and Efficient Classification of Power System Contingencies and Cyber-Attacks Using Recurrent Neural Networks. IEEE Access 2020, 8, 123297–123309. [Google Scholar] [CrossRef]
- Kumar, M.; Kim, C.; Son, Y.; Singh, S.K.; Kim, S. Empowering Cyberattack Identification in IoHT Networks with Neighborhood-Component-Based Improvised Long Short-Term Memory. IEEE Internet Things J. 2024, 11, 16638–16646. [Google Scholar] [CrossRef]
- Liu, H.; Zhou, M.; Liu, Q. An Embedded Feature Selection Method for Imbalanced Data Classification. IEEE/CAA J. Autom. Sin. 2019, 6, 703–715. [Google Scholar] [CrossRef]
- Abbas, S.; Hejaili, A.A.; Sampedro, G.A.; Abisado, M.; Almadhor, A.S.; Shahzad, T.; Ouahada, K. A Novel Federated Edge Learning Approach for Detecting Cyberattacks in IoT Infrastructures. IEEE Access 2023, 11, 112189–112198. [Google Scholar] [CrossRef]
- Yang, R.; He, H.; Wang, Y.; Qu, Y.; Zhang, W. Dependable Federated Learning for IoT Intrusion Detection against Poisoning Attacks. Comput. Secur. 2023, 132, 103381. [Google Scholar] [CrossRef]
- Dao, N.N.; Phan, T.V.; Sa’ad, U.; Kim, J.; Bauschert, T.; Do, D.T.; Cho, S. Securing Heterogeneous IoT With Intelligent DDoS Attack Behavior Learning. IEEE Syst. J. 2022, 16, 1974–1983. [Google Scholar] [CrossRef]
- Günen, M.A. Fast Building Detection Using New Feature Sets Derived from a Very High-Resolution Image, Digital Elevation and Surface Model. Int. J. Remote Sens. 2024, 45, 1477–1497. [Google Scholar] [CrossRef]
- Gupta, A.; Misra, S.; Pathak, N.; Das, D. FedCare: Federated Learning for Resource-Constrained Healthcare Devices in IoMT System. IEEE Trans. Comput. Soc. Syst. 2023, 10, 1587–1596. [Google Scholar] [CrossRef]
- Nair, A.K.; Sahoo, J.; Raj, E.D. Privacy Preserving Federated Learning Framework for IoMT Based Big Data Analysis Using Edge Computing. Comput. Stand. Interfaces 2023, 86, 103720. [Google Scholar] [CrossRef]
- Singh, P.; Gaba, G.S.; Kaur, A.; Hedabou, M.; Gurtov, A. Dew-Cloud-Based Hierarchical Federated Learning for Intrusion Detection in IoMT. IEEE J. Biomed. Health Inform. 2023, 27, 722–731. [Google Scholar] [CrossRef]
- Adil, M.; Javaid, N.; Qasim, U.; Ullah, I.; Shafiq, M.; Choi, J.G. LSTM and Bat-Based Rusboost Approach for Electricity Theft Detection. Appl. Sci. 2020, 10, 4378. [Google Scholar] [CrossRef]
- Elayan, H.; Aloqaily, M.; Guizani, M. Sustainability of Healthcare Data Analysis IoT-Based Systems Using Deep Federated Learning. IEEE Internet Things J. 2022, 9, 7338–7346. [Google Scholar] [CrossRef]
- Lakhan, A.; Mohammed, M.A.; Nedoma, J.; Martinek, R.; Tiwari, P.; Vidyarthi, A.; Alkhayyat, A.; Wang, W. Federated-Learning Based Privacy Preservation and Fraud-Enabled Blockchain IoMT System for Healthcare. IEEE J. Biomed. Health Inform. 2023, 27, 664–672. [Google Scholar] [CrossRef] [PubMed]
- Ahmed, J.; Nguyen, T.N.; Ali, B.; Javed, M.A.; Mirza, J. On the Physical Layer Security of Federated Learning Based IoMT Networks. IEEE J. Biomed. Health Inform. 2023, 27, 691–697. [Google Scholar] [CrossRef]
- Ketu, S.; Mishra, P.K. Internet of Healthcare Things: A Contemporary Survey. J. Netw. Comput. Appl. 2021, 192, 103179. [Google Scholar] [CrossRef]
- Krzyzanowski, B.; Manson, S.M. Twenty Years of the Health Insurance Portability and Accountability Act Safe Harbor Provision: Unsolved Challenges and Ways Forward. JMIR Med. Inform. 2022, 10, e37756. [Google Scholar] [CrossRef] [PubMed]
- Javed, A.R.; Fahad, L.G.; Farhan, A.A.; Abbas, S.; Srivastava, G.; Parizi, R.M.; Khan, M.S. Automated Cognitive Health Assessment in Smart Homes Using Machine Learning. Sustain. Cities Soc. 2021, 65, 102572. [Google Scholar] [CrossRef]
- Adler, A.I.; Painsky, A. Feature Importance in Gradient Boosting Trees with Cross-Validation Feature Selection. Entropy 2022, 24, 687. [Google Scholar] [CrossRef]
- Christo, V.R.E.; Nehemiah, H.K.; Brighty, J.; Kannan, A. Feature Selection and Instance Selection from Clinical Datasets Using Co-Operative Co-Evolution and Classification Using Random Forest. IETE J. Res. 2022, 68, 2508–2521. [Google Scholar] [CrossRef]
- Vong, C.M.; Du, J. Accurate and Efficient Sequential Ensemble Learning for Highly Imbalanced Multi-Class Data. Neural Netw. 2020, 128, 268–278. [Google Scholar] [CrossRef]
- Zhao, Y.; Chen, J.; Wu, D.; Teng, J.; Yu, S. Multi-Task Network Anomaly Detection Using Federated Learning. ACM Int. Conf. Proc. Ser. 2019, 24, 273–279. [Google Scholar] [CrossRef]
- Sung, Y.; Jang, S.; Jeong, Y.S.; Park, J.H. Malware Classification Algorithm Using Advanced Word2vec-Based Bi-LSTM for Ground Control Stations. Comput. Commun. 2020, 153, 342–348. [Google Scholar] [CrossRef]
- Ahmed, M.; Byreddy, S.; Nutakki, A.; Sikos, L.F.; Haskell-Dowland, P. ECU-IoHT: A Dataset for Analyzing Cyberattacks in Internet of Health Things. Ad Hoc Netw. 2021, 122, 102621. [Google Scholar] [CrossRef]
- Zuech, R.; Hancock, J.; Khoshgoftaar, T.M. Detecting Web Attacks Using Random Undersampling and Ensemble Learners. J. Big Data 2021, 8, 75. [Google Scholar] [CrossRef]
- Jadav, D.; Jadav, N.K.; Gupta, R.; Tanwar, S.; Alfarraj, O.; Tolba, A.; Raboaca, M.S.; Marina, V. A Trustworthy Healthcare Management Framework Using Amalgamation of AI and Blockchain Network. Mathematics 2023, 11, 637. [Google Scholar] [CrossRef]
- Hady, A.A.; Ghubaish, A.; Salman, T.; Unal, D.; Jain, R. IoMT Intrusion Detection. Available online: https://www.cse.wustl.edu/~jain/ehms/index.html (accessed on 20 June 2024).





| Research | Year | Techniques | Medical Security | Multiple Attacks | Data Privacy | Solution of Imbalanced Classification |
|---|---|---|---|---|---|---|
| Saheed et al. [2] | 2021 | DRNN, DTs, KNN, RF | Yes | No | No | No |
| Adil et al. [33] | 2020 | LSTM, RUSBoost | No | No | No | Yes |
| Saharkhizan et al. [19] | 2020 | LSTM-based Ensemble Learning | No | Yes | No | No |
| Abbas et al. [26] | 2023 | Federated Deep Neural Network | No | No | Yes | Yes |
| Al-khatani et al. [22] | 2023 | LSTM-GRU | No | No | No | No |
| Kumar et al. [24] | 2024 | LSTM-DAG Network | Yes | Yes | No | No |
| Elayan et al. [34] | 2022 | Deep FL | Yes | No | Yes | No |
| Lakhan et al. [35] | 2023 | FL and Blockchain | Yes | No | Yes | No |
| Ahmed et al. [36] | 2023 | FL | Yes | No | Yes | No |
| Proposed Work | 2024 | RUSBoost-based EL and LSTM-based FL | Yes | Yes | Yes | Yes |
| Method | Parameter | Type/Value |
|---|---|---|
| Ensemble Learning-based feature selection | Learner | Decision Tree (DT) |
| Number of learning cycles | 50 | |
| Boosting principle | Random Undersampling and Boosting (RusBoost) | |
| Proposed EFL-LSTM classification network | Learning algorithm | Adam |
| Maximum epochs | 10 | |
| Mini batch size | 64 | |
| Initial learning rate | 0.01 | |
| Initial learning schedule | Piecewise | |
| Learning rate drop period | 5 | |
| Learning rate drop factor | 0.1 | |
| Number of clients | 5 |
| Technique | Accuracy | Recall | Specificity | Precision | FPP | F1 Score | MCC | K |
|---|---|---|---|---|---|---|---|---|
| Embedded LSTM | 0.9325 | 0.7160 | 0.9457 | 0.8954 | 0.0228 | 0.7737 | 0.7906 | 0.8868 |
| Proposed EFL-LSTM | 0.9716 | 0.7933 | 0.9932 | 0.9396 | 0.0068 | 0.8237 | 0.8363 | 0.9112 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kumar, M.; Kim, S. Securing the Internet of Health Things: Embedded Federated Learning-Driven Long Short-Term Memory for Cyberattack Detection. Electronics 2024, 13, 3461. https://doi.org/10.3390/electronics13173461
Kumar M, Kim S. Securing the Internet of Health Things: Embedded Federated Learning-Driven Long Short-Term Memory for Cyberattack Detection. Electronics. 2024; 13(17):3461. https://doi.org/10.3390/electronics13173461
Chicago/Turabian StyleKumar, Manish, and Sunggon Kim. 2024. "Securing the Internet of Health Things: Embedded Federated Learning-Driven Long Short-Term Memory for Cyberattack Detection" Electronics 13, no. 17: 3461. https://doi.org/10.3390/electronics13173461
APA StyleKumar, M., & Kim, S. (2024). Securing the Internet of Health Things: Embedded Federated Learning-Driven Long Short-Term Memory for Cyberattack Detection. Electronics, 13(17), 3461. https://doi.org/10.3390/electronics13173461






