Adaptive Event-Triggered Voltage Control of Distribution Network Subject to Actuator Attacks Using Neural Network-Based Sliding Mode Control Approach
Abstract
1. Introduction
- An AETS is devised with the primary objective of optimizing communication resource utilization. By strategically setting and adjusting trigger thresholds, AETS effectively curtails redundant data transmissions. Distinguishing itself from the conventional static event-triggered schemes (ETS) outlined in [25,26], AETS exhibits a dynamic capability to adapt its triggering conditions in response to state variations, thereby minimizing unnecessary communication. During periods of system stability, AETS further reduces communication frequency, leading to enhanced savings in communication resources. This adaptability renders AETS a more versatile and practical solution.
- The SMC method is introduced into a DN-VC system to suppress the effect of an actuator attack. Diverging from conventional SMC strategies [27] that rely on intricate control techniques to address chattering issues, this work presents an SMC law grounded in neural network (NN) technology. This approach not only ensures the attainability of the sliding mode but also effectively mitigates the chattering phenomenon, offering a more streamlined solution.
2. Problem Formulations
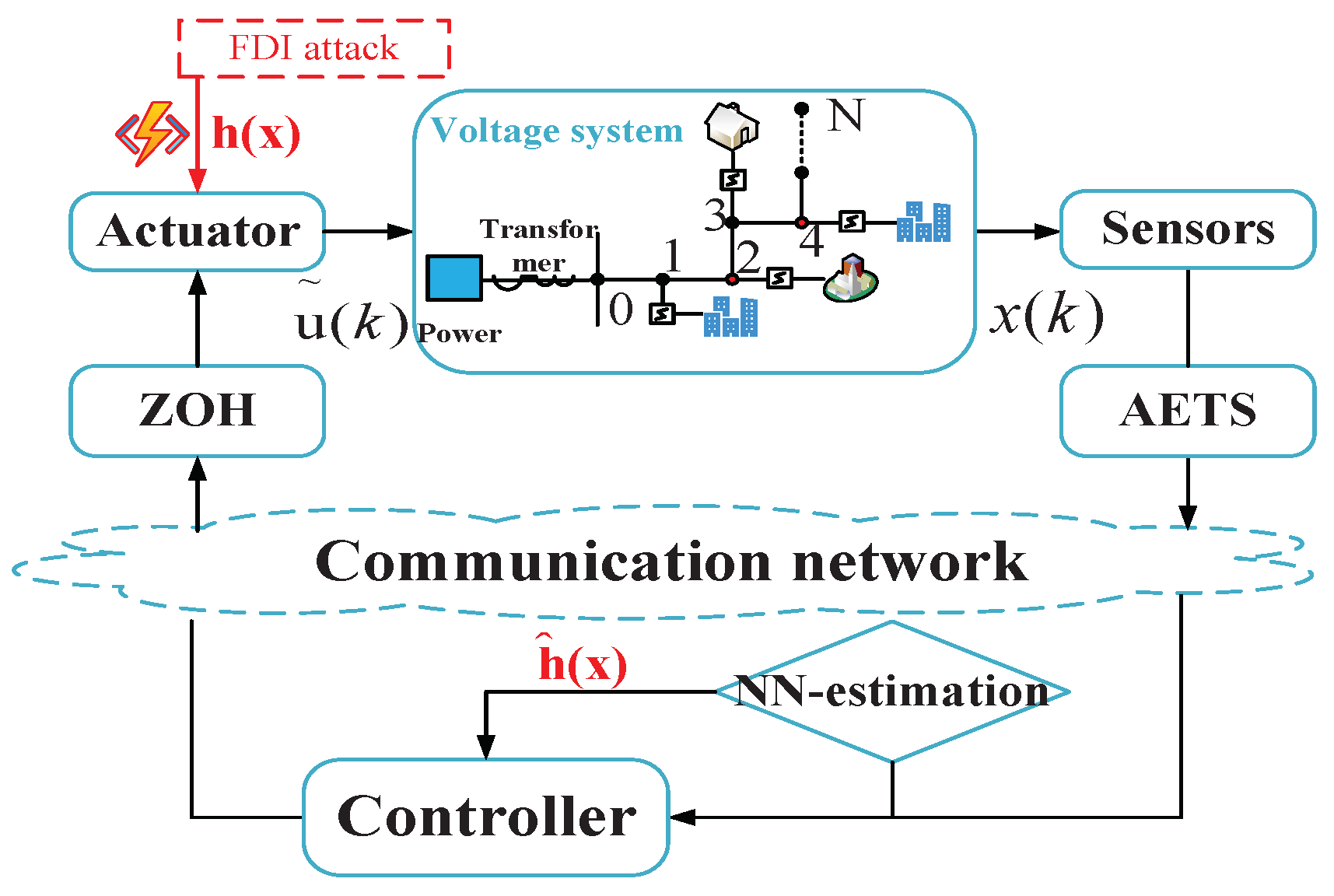
2.1. Voltage Control System under Actuator Attack
- It is worth noting that because the neural network technology is used to design the sliding mode control law, we do not make any special assumptions about the attack signal .
- In fact, currently known cyberattacks do not follow certain rules. However, most studies assume that the attack signal obeys a certain probability distribution or has an upper bound, so the research on network attack in this paper is more practical.
2.2. AETS Scheme and Time-Delays Model
- The sensor samples the data with a time-driven scheme, and the sampling data set is .
- Whether the sampled data are sent depends on whether the event-triggered condition (see Formula (3)). The set of transmissions that are successfully sent out is .
- The controllers and actuators generate their actions in zero-order-hold (ZOH) fashion.
- The expression of AETS avoids the denominator of the event-triggered threshold function being zero, thereby ensuring that the designed event-triggered function has mathematical significance.
- By designing an appropriate σ, a better trade-off between control performance and communication efficiency can be achieved.
- When the system state is unstable, will increase, resulting in a smaller event-triggered threshold and faster transmission frequency, enhancing the ability to control and regulate the system. Conversely, it can save network resources.
2.3. Neural Network-Based Estimation of Attack Signal
2.4. Design of Sliding Mode Surface
3. Main Results
3.1. Asymptotical Stability Analysis
- ,
- with
- with
- with
3.2. Design of Sliding Mode Switching Controller
| Algorithm 1 Technical line of the proposed security solution. |
|
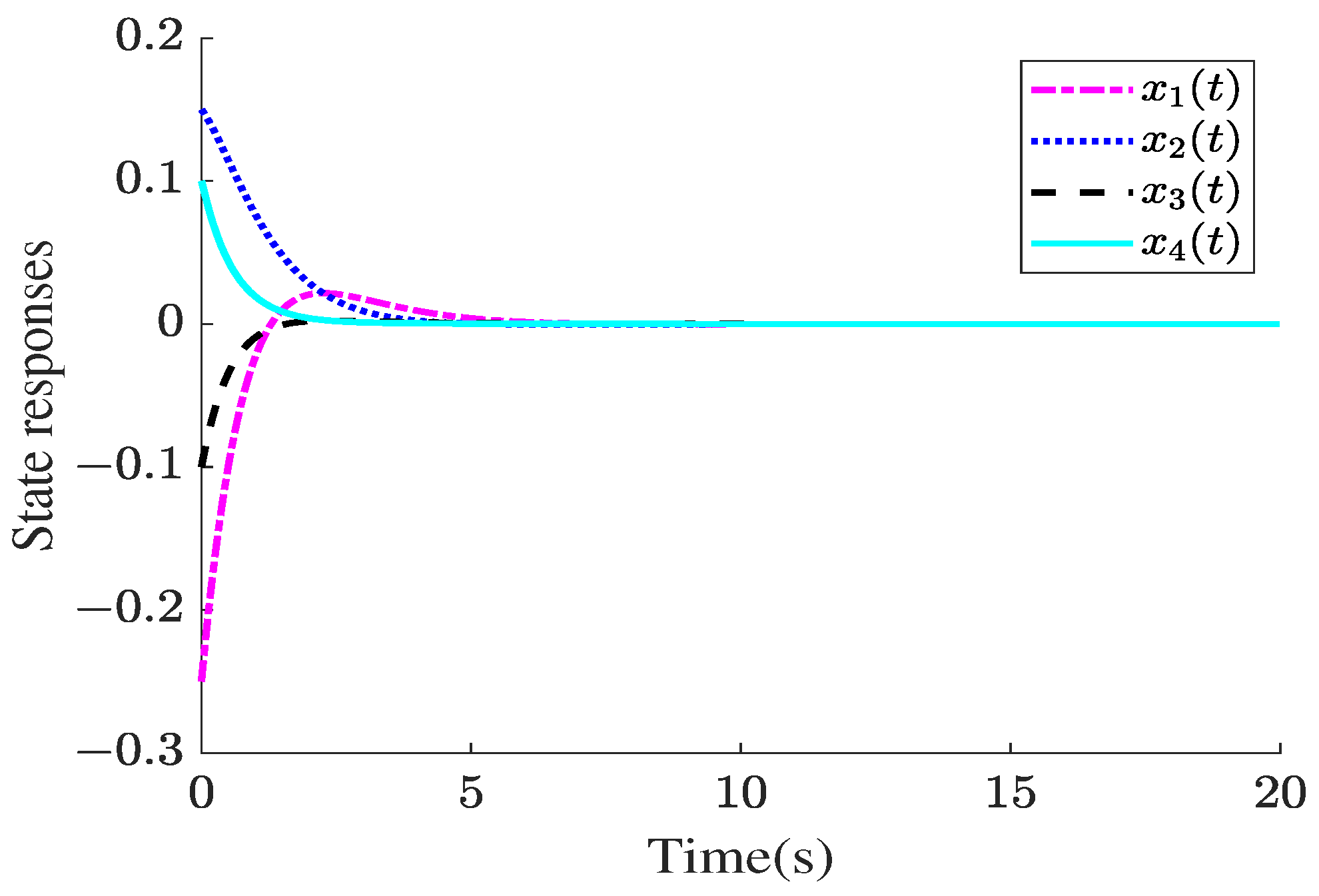
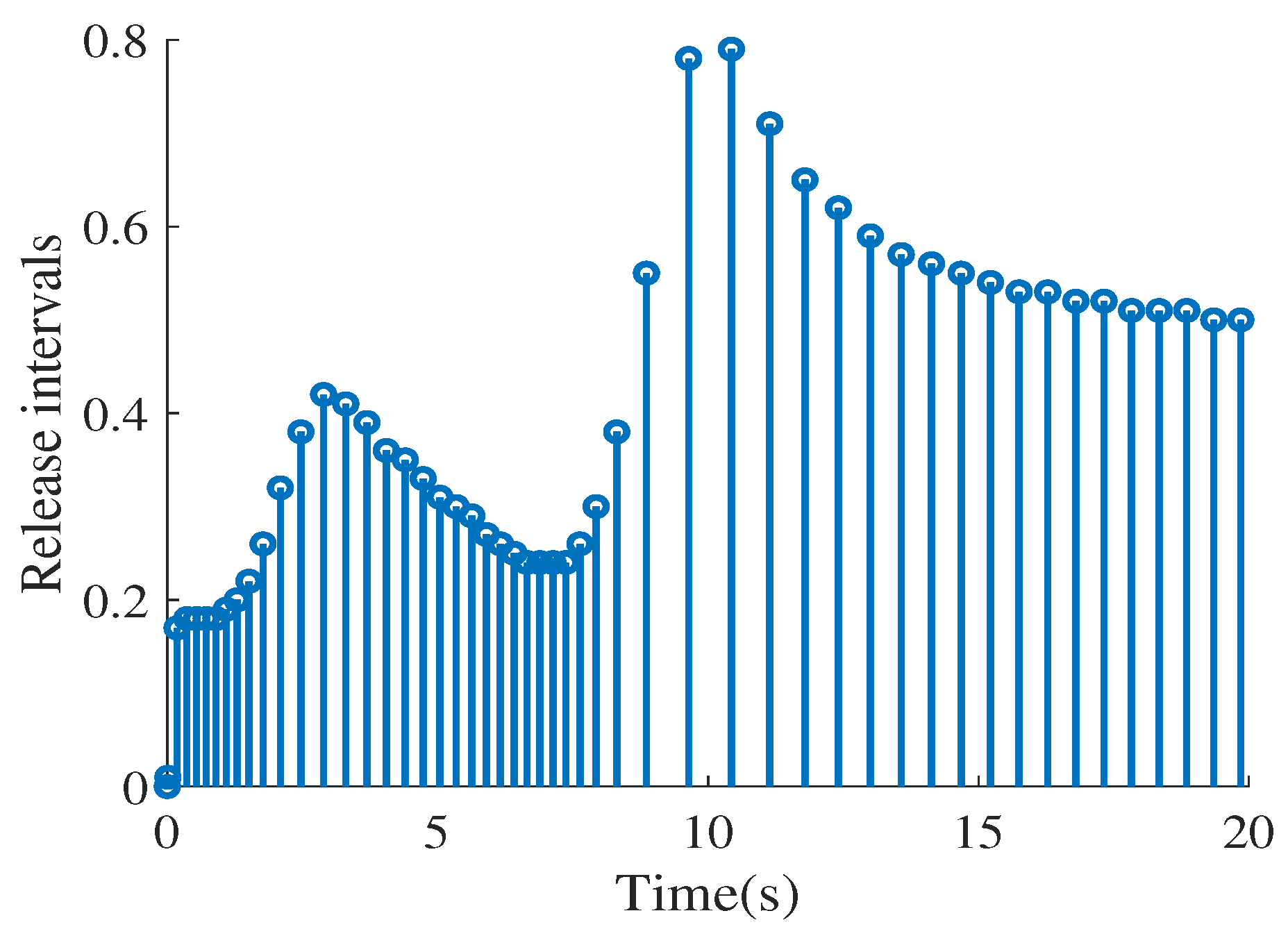
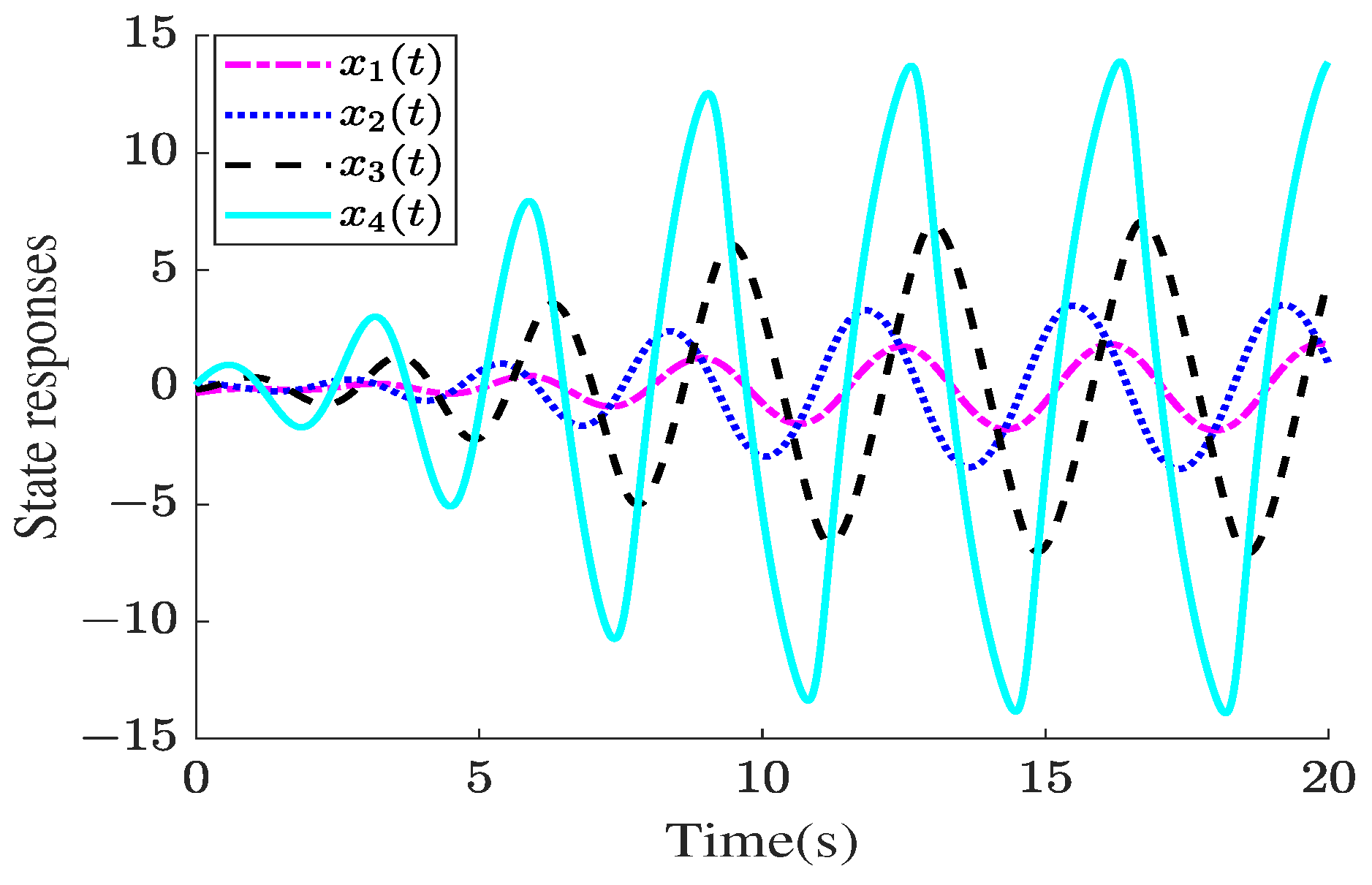
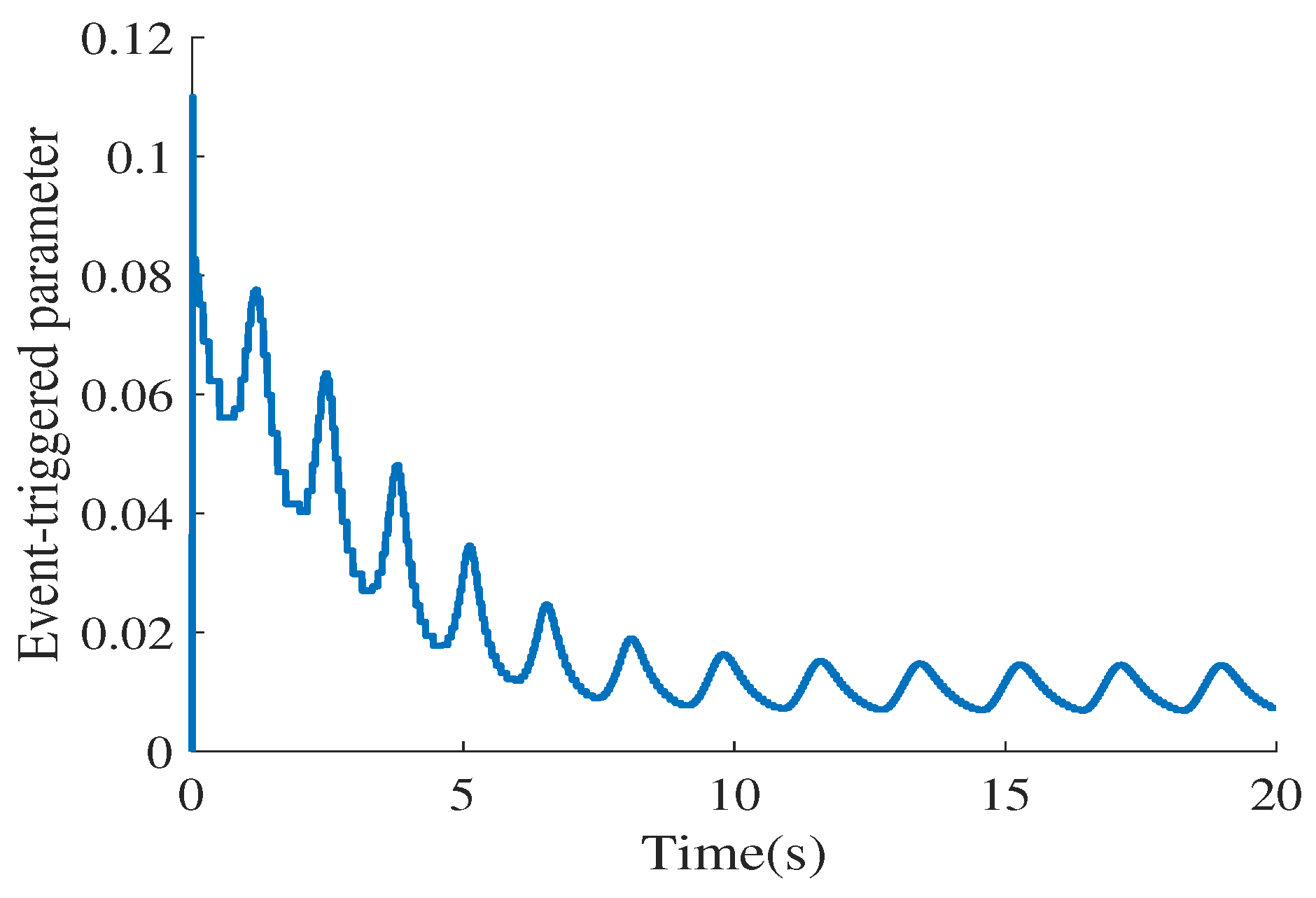
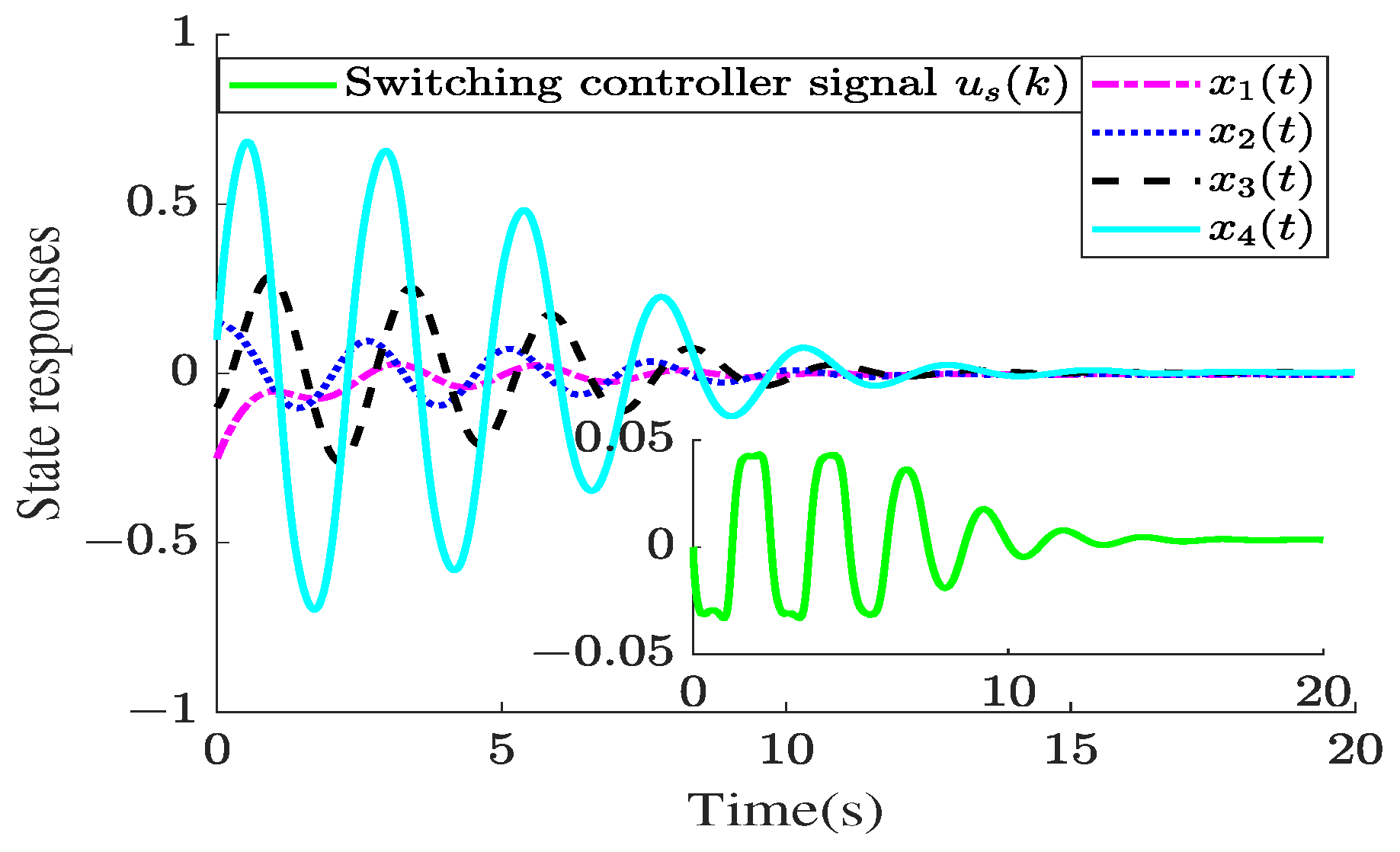
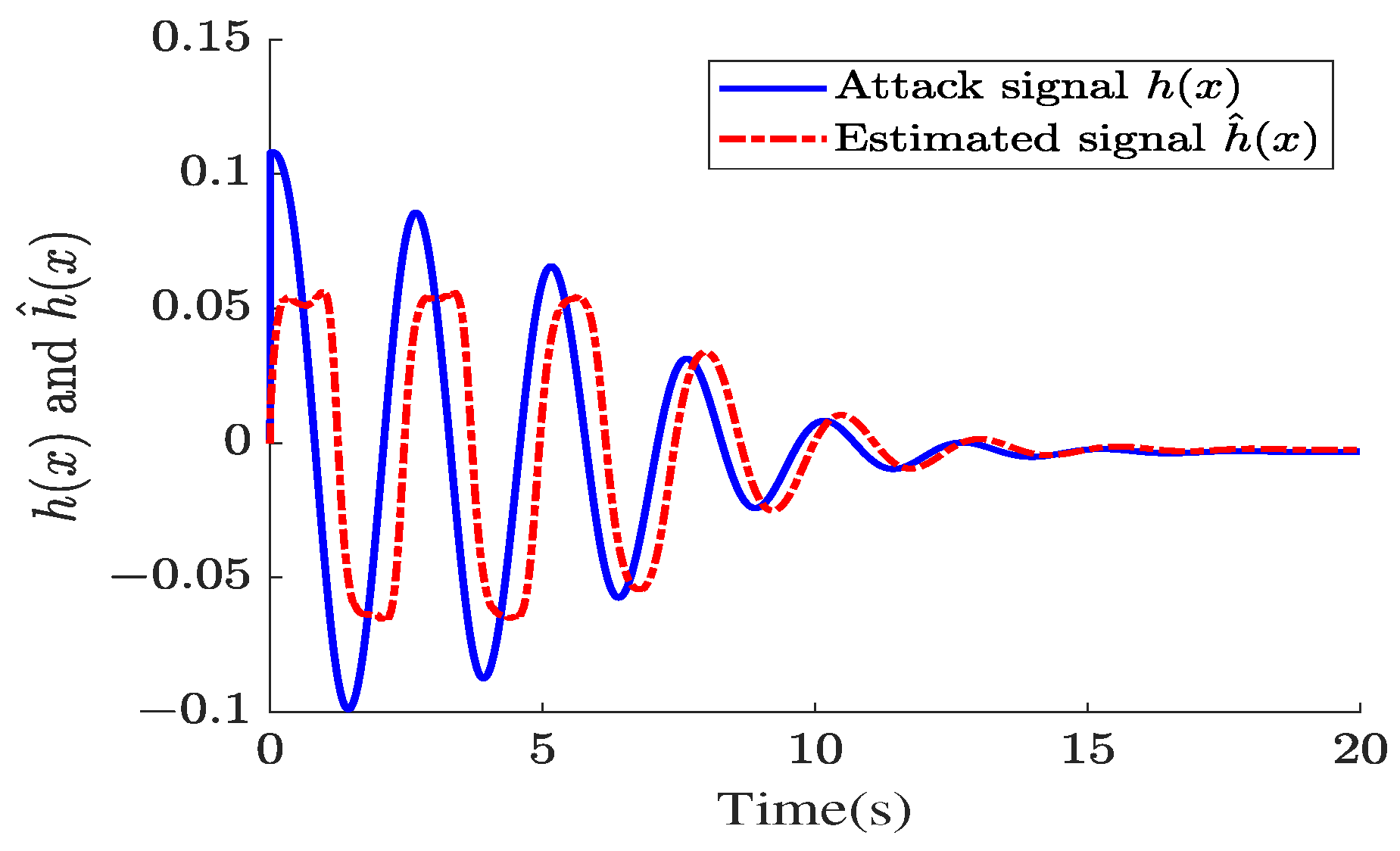
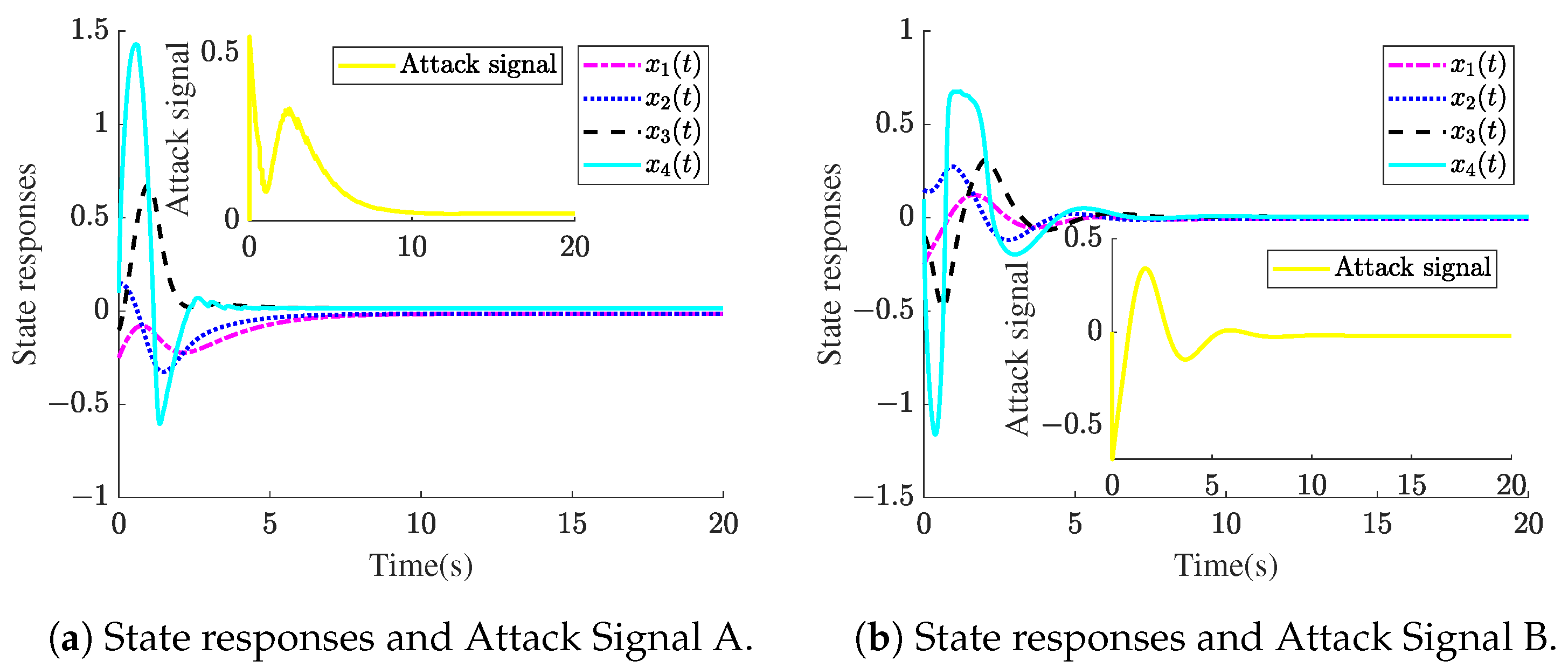
4. Illustrative Examples
5. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Murray, W.; Adonis, M.; Raji, A. Voltage control in future electrical distribution networks. Renew. Sustain. Energy Rev. 2021, 146, 111100. [Google Scholar] [CrossRef]
- Nandhini, E.; Sivaprakasam, A. A review of various control strategies based on space vector pulse width modulation for the voltage source inverter. IETE J. Res. 2022, 68, 3187–3201. [Google Scholar] [CrossRef]
- Baleboina, G.M.; Mageshvaran, R. A survey on voltage stability indices for power system transmission and distribution systems. Front. Energy Res. 2023, 11, 1159410. [Google Scholar] [CrossRef]
- Heidary, J.; Gheisarnejad, M.; Rastegar, H.; Khooban, M.H. Survey on microgrids frequency regulation: Modeling and control systems. Electr. Power Syst. Res. 2022, 213, 108719. [Google Scholar] [CrossRef]
- Kim, S.J.; Park, K.J.; Lu, C. A survey on network security for cyber–physical systems: From threats to resilient design. IEEE Commun. Surv. Tutor. 2022, 24, 1534–1573. [Google Scholar] [CrossRef]
- Aoufi, S.; Derhab, A.; Guerroumi, M. Survey of false data injection in smart power grid: Attacks, countermeasures and challenges. J. Inf. Secur. Appl. 2020, 54, 102518. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A. Comprehensive survey and taxonomies of false data injection attacks in smart grids: Attack models, targets, and impacts. Renew. Sustain. Energy Rev. 2022, 163, 112423. [Google Scholar] [CrossRef]
- Tufail, S.; Parvez, I.; Batool, S.; Sarwat, A. A survey on cybersecurity challenges, detection, and mitigation techniques for the smart grid. Energies 2021, 14, 5894. [Google Scholar] [CrossRef]
- Duo, W.; Zhou, M.; Abusorrah, A. A survey of cyber attacks on cyber physical systems: Recent advances and challenges. IEEE/CAA J. Autom. Sin. 2022, 9, 784–800. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Wu, Y.; Wei, D.; Feng, J. Network attacks detection methods based on deep learning techniques:A survey. Secur. Commun. Netw. 2020, 2020, 8872923. [Google Scholar] [CrossRef]
- Wang, S.; Bi, S.; Zhang, Y. Locational detection of the false data injection attack in a smart grid: A multilabel classification approach. IEEE Internet Things J. 2020, 7, 8218–8227. [Google Scholar] [CrossRef]
- Lu, K.; Wu, Z. Constrained-differential-evolution-based stealthy sparse cyber-attack and countermeasure in an AC smart grid. IEEE Trans. Ind. Inform. 2021, 18, 5275–5285. [Google Scholar] [CrossRef]
- Shi, J.; Liu, S.; Chen, B.; Yu, L. Distributed data-driven intrusion detection for sparse stealthy FDI attacks in smart grids. IEEE Trans. Circuits Syst. II Express Briefs 2020, 68, 993–997. [Google Scholar] [CrossRef]
- Ijaz, S.; Galea, M.; Hamayun, M.T.; Ijaz, H.; Javaid, U. A new output integral sliding mode fault-tolerant control and fault estimation scheme for uncertain systems. IEEE Trans. Autom. Sci. Eng. 2023; early access. [Google Scholar] [CrossRef]
- Huang, S.; Xiong, L.; Zhou, Y.; Gao, F.; Jia, Q.; Li, X.; Li, X.; Wang, Z.; Khan, M.W. Distributed Predefined-Time Control for Power System with Time Delay and Input Saturation. IEEE Trans. Power Syst. 2024; early access. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A.; Chilamkurti, N. Data-driven approach for state prediction and detection of false data injection attacks in smart grid. J. Mod. Power Syst. Clean Energy 2022, 11, 455–467. [Google Scholar] [CrossRef]
- Kang, W.; Chen, M.; Guan, Y.; Tang, L.; Guerrero, J.M. Distributed event-triggered optimal control method for heterogeneous energy storage systems in smart grid. IEEE Trans. Sustain. Energy 2022, 13, 1944–1956. [Google Scholar] [CrossRef]
- Ge, P.; Chen, B.; Teng, F. Event-triggered distributed model predictive control for resilient voltage control of an islanded microgrid. Int. J. Robust Nonlinear Control 2021, 31, 1979–2000. [Google Scholar] [CrossRef]
- Ding, S.; Xie, X.; Liu, Y. Event-triggered static/dynamic feedback control for discrete-time linear systems. Inf. Sci. 2020, 524, 33–45. [Google Scholar] [CrossRef]
- Behera, A.K.; Bandyopadhyay, B.; Cucuzzella, M.; Ferrara, A. A survey on event-triggered sliding mode control. IEEE J. Emerg. Sel. Top. Ind. Electron. 2021, 2, 206–217. [Google Scholar] [CrossRef]
- Ge, X.; Han, Q.; Ding, L.; Wang, Y. Dynamic event-triggered distributed coordination control and its applications: A survey of trends and techniques. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 3112–3125. [Google Scholar] [CrossRef]
- Wang, X.; Sun, J.; Wang, G.; Allgöwer, F.; Chen, J. Data-driven control of distributed event-triggered network systems. IEEE/CAA J. Autom. Sin. 2023, 10, 351–364. [Google Scholar] [CrossRef]
- Wu, J.; Peng, C.; Yang, H.; Wang, Y. Recent advances in event-triggered security control of networked systems: A survey. Int. J. Syst. Sci. 2022, 53, 2624–2643. [Google Scholar] [CrossRef]
- Li, M.; Long, Y.; Li, T.; Chen, C. Consensus of linear multi-agent systems by distributed event-triggered strategy with designable minimum inter-event time. Inf. Sci. 2022, 609, 644–659. [Google Scholar] [CrossRef]
- Inomoto, R.S.; de Almeida Monteiro, J.B.; Sguarezi Filho, A. Boost converter control of PV system using sliding mode control with integrative sliding surface. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 5522–5530. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhan, M.; Shi, Y.; Liu, C. Event-based finite-time boundedness of discrete-time network systems. Int. J. Control. Autom. Syst. 2020, 18, 2562–2571. [Google Scholar] [CrossRef]
- Sun, H.; Huang, J.; Chen, Z.; Wang, Z. State-sensitive event-triggered path following control of autonomous ground vehicles. Intell. Robot. 2023, 3, 257–273. [Google Scholar] [CrossRef]
- Sun, N.; Niu, Y.; Chen, B. Optimal integral sliding mode control for a class of uncertain discrete-time systems. Optim. Control Appl. Methods 2014, 35, 468–478. [Google Scholar] [CrossRef]





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, F. Adaptive Event-Triggered Voltage Control of Distribution Network Subject to Actuator Attacks Using Neural Network-Based Sliding Mode Control Approach. Electronics 2024, 13, 2960. https://doi.org/10.3390/electronics13152960
Zhang F. Adaptive Event-Triggered Voltage Control of Distribution Network Subject to Actuator Attacks Using Neural Network-Based Sliding Mode Control Approach. Electronics. 2024; 13(15):2960. https://doi.org/10.3390/electronics13152960
Chicago/Turabian StyleZhang, Fang. 2024. "Adaptive Event-Triggered Voltage Control of Distribution Network Subject to Actuator Attacks Using Neural Network-Based Sliding Mode Control Approach" Electronics 13, no. 15: 2960. https://doi.org/10.3390/electronics13152960
APA StyleZhang, F. (2024). Adaptive Event-Triggered Voltage Control of Distribution Network Subject to Actuator Attacks Using Neural Network-Based Sliding Mode Control Approach. Electronics, 13(15), 2960. https://doi.org/10.3390/electronics13152960




