Introducing Security Mechanisms in OpenFog-Compliant Smart Buildings
Abstract
1. Introduction
- It identifies the state-of-the-art security mechanisms that must be used to guarantee a certain degree of cybersecurity in smart building applications.
- It presents a scalable architecture, based on the OpenFog reference architecture (IEEE 1934 standard), to provide security by design in smart building applications. The presented approach promotes the use of free and open-source software and hardware technologies and may be used to integrate low-cost IoT devices.
- It presents guidelines to help developers and implementers create secure smart building applications, even if they are not experts in cybersecurity.
- It illustrates how to apply the presented approach to develop smart building secure applications by means of a proof of concept implementation at the Faculty of Engineering of Vitoria-Gasteiz.
2. Background
2.1. Vulnerabilities in Smart Buildings
2.2. Security Requirements in Smart Buildings
- Data Storage: In smart buildings, data are stored on the nodes of the fog layer temporarily or indefinitely. These nodes must be especially protected against cyberattacks. Within this category, key protection should be taken into account. According to [23], it is recommended to include anti-tampering protections, as well as detection and recovery mechanisms.
- Device Interconnection: The communication among fog and edge devices must be properly encrypted to protect communications against cyberattacks. This approach protects the information used in smart building applications from unauthorized access.
- Communication with the Cloud: Information exchange with the cloud must be secure and reliable, avoiding information leakage. So, secure protocols that encrypt the information must be used. Also, institutional firewalls are necessary to filter, identify, and categorize each element of the data flow preventing access by unauthorized parties.
- Data Protection: Confidential data of both users and entities connecting to the network must also be considered. Each element has its particular identification, and it is necessary to ensure that unauthorized entities do not access them or make a copy to try to access the architecture.
2.3. Openfog Security View
- Cryptographic functions: Most security services involving confidentiality, integrity, authentication and non-repudiation require cryptographic functions to provide secure execution environments for trusted software or data integrity. Cryptography may be implemented in different ways, either in software or by means of hardware security processors, such as Platform Security Processor (PSP) or Trusted Platform Module (TPM). Symmetric or asymmetric ciphers may be used to implement cryptographic algorithms with different levels of security and computational cost.
- Node security aspect: Node integrity is a fundamental part of security as it makes up the bulk of the architecture’s structure. The Trusted Computing Base (TCB) refers to the platform hardware, software and networking components that if violated would compromise the ability of the system to enforce its security policies. The root of trust is at the heart of the TCB and the security of the fog node. Security needs to be anchored in the hardware so that it cannot be circumvented. The Hardware Root of Trust (HW-RoT) is the key to a fog node’s TCB. Fog nodes should support a HW-RoT to ensure that non-verified code is executed in the boot process. This is a key stage to confirm the node security. It is critical that fog nodes have a method to securely establish a root of trust during the boot process, ensuring that the firmware and the system software have not been tampered with.
- Network security aspect: Fog computing applications are deployed between the frontend devices and the cloud computing data centers. The ITU-X.805 Recommendation [34], identifies two operational planes in order to provide end-to-end security communications: Security Provisioning and Security Monitoring and Management, with three functional layers: Communications Security, Services Security and Applications Security. Security Monitoring and Management typically involves the configuration of several network security appliances such as Firewalls, Deep Packet Inspection (DPI), Intrusion Detection and Protection Systems (IPS/IDS), System/Network Events and State Monitoring. The communications occurring in the Device-Fog-Cloud computing continuum can be categorized into three kinds of communication pathways:
- –
- Node-to-Device: It covers the communication between edge devices and fog nodes. Among many Internet resource-constrained IoT devices, limited cryptographic capability is available. Techniques such as symmetric ciphers using manually installed keys are commonly used in these kinds of devices. These devices must be installed in physically protected environments and connected via hardware connections to one or more fog nodes that can provide most of the X.800 communication security services. The use of wireless technologies is common in this communication pathway, in particular, MQTT over WiFi and TLS for publish-subscribe messaging and 802.1X for authentication purposes.
- –
- Node-to-Node: It covers the communication among several fog nodes. Fog nodes coordinate between them in order to accomplish specific objectives. This layer combines the client-server computing model, typically over HTTPS, and the publish-subscribe messaging patterns, with MQTT being one of the most commonly used protocols. Strong authentication and non-repudiation services shall be implemented using security credentials derived from the hardware root-of-trust installed in the fog node.
- –
- Node-to-Cloud: It covers the communication between fog nodes and cloud services. Strong authentication and non-repudiation services shall be implemented using security credentials derived from the hardware root-of-trust installed in the fog node. Almost all these communications are currently conducted as web service transactions over TCP/IP protocols.
- Data security aspect: Encryption algorithms are used to enforce most data security aspects. OpenFog classifies data in three categories: data in use, during data processing; data at rest, when resides on non-volatile storage devices, such as hard disks or SSDs; data in motion when they are sent or received on network interfaces as packets. Memory encryption technologies could be implemented for data in use. The encryption of data at rest limits the access to the data to those with the correct keys. Three encryption methods are generally used for data at rest: full disk encryption; file system encryption and file system access control mechanisms. The use of technologies, such as TLS or VPNs, allows encrypting data in motion.
2.4. Related Work
3. Secure Smart Buildings Based on the OpenFog Standard
3.1. Openfog-Based Architecture for Secure Smart Buildings
- Anti-tampering mechanisms. All nodes must provide mechanisms to ensure that the firmware and system software have not been tampered with. Also, physical protection of the nodes must be guaranteed.
- Common and low-cost technologies. The architecture employs widely used technologies. Particularly, Free and Open Source Software (FOSS) technologies and open hardware devices are preferred.
- Zero-trust security. In order to reduce the risk of threats in the system, connectivity among nodes is restricted to the essential services. In addition, a hierarchical structure among nodes is proposed.
- Security Monitoring and Management. Several security appliances are used to detect attacks, such as Firewalls, Deep Packet Inspection (DPI), Intrusion Detection and Protection Systems (IPS/IDS) as well as System/Network Event and State Monitoring Systems.
- Critical data protection. This applies to both data at rest, i.e., stored in all nodes of the hierarchy, and data in motion, i.e., data transmitted by means of networking technologies.
3.1.1. Architecture Layers
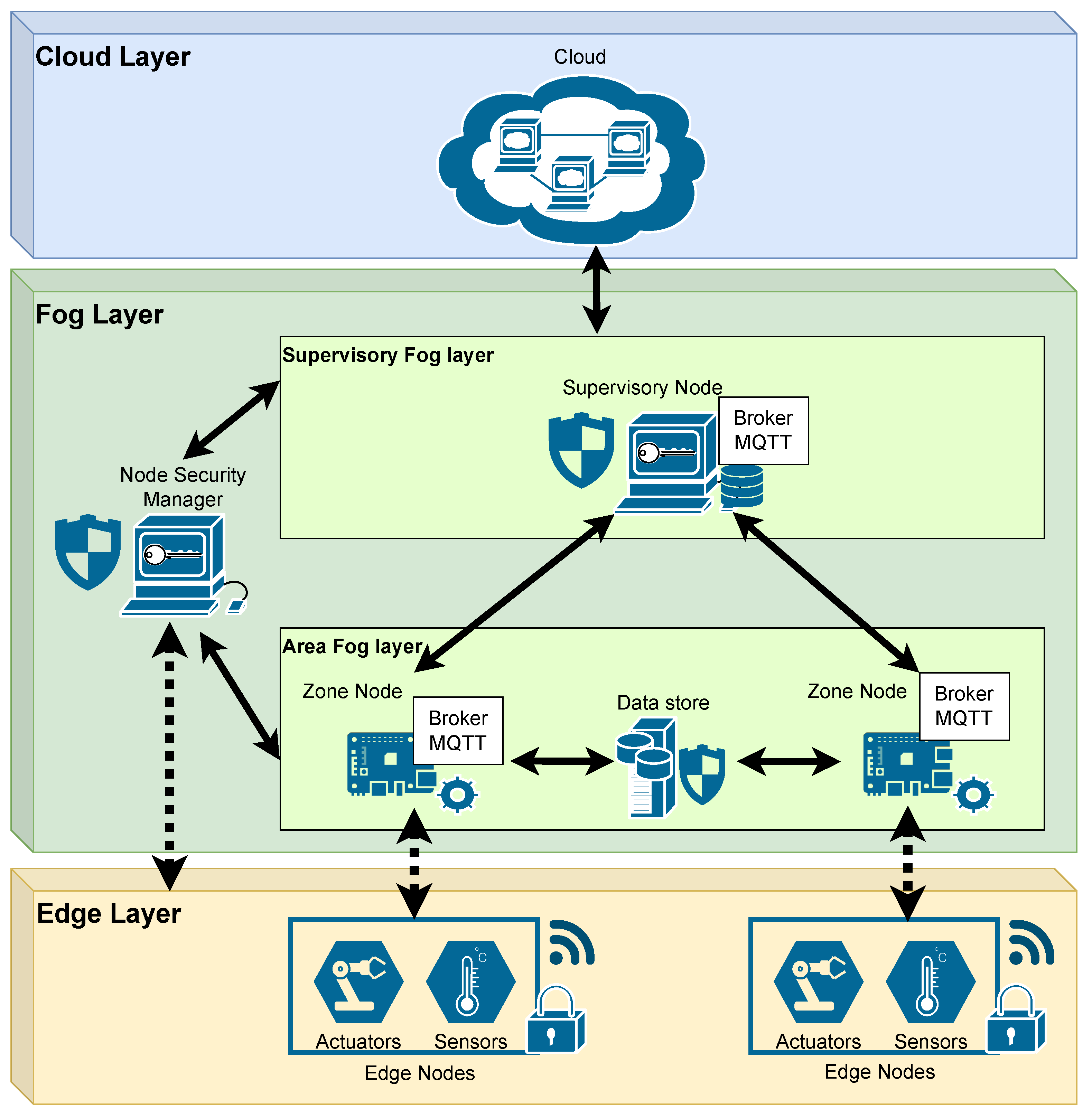
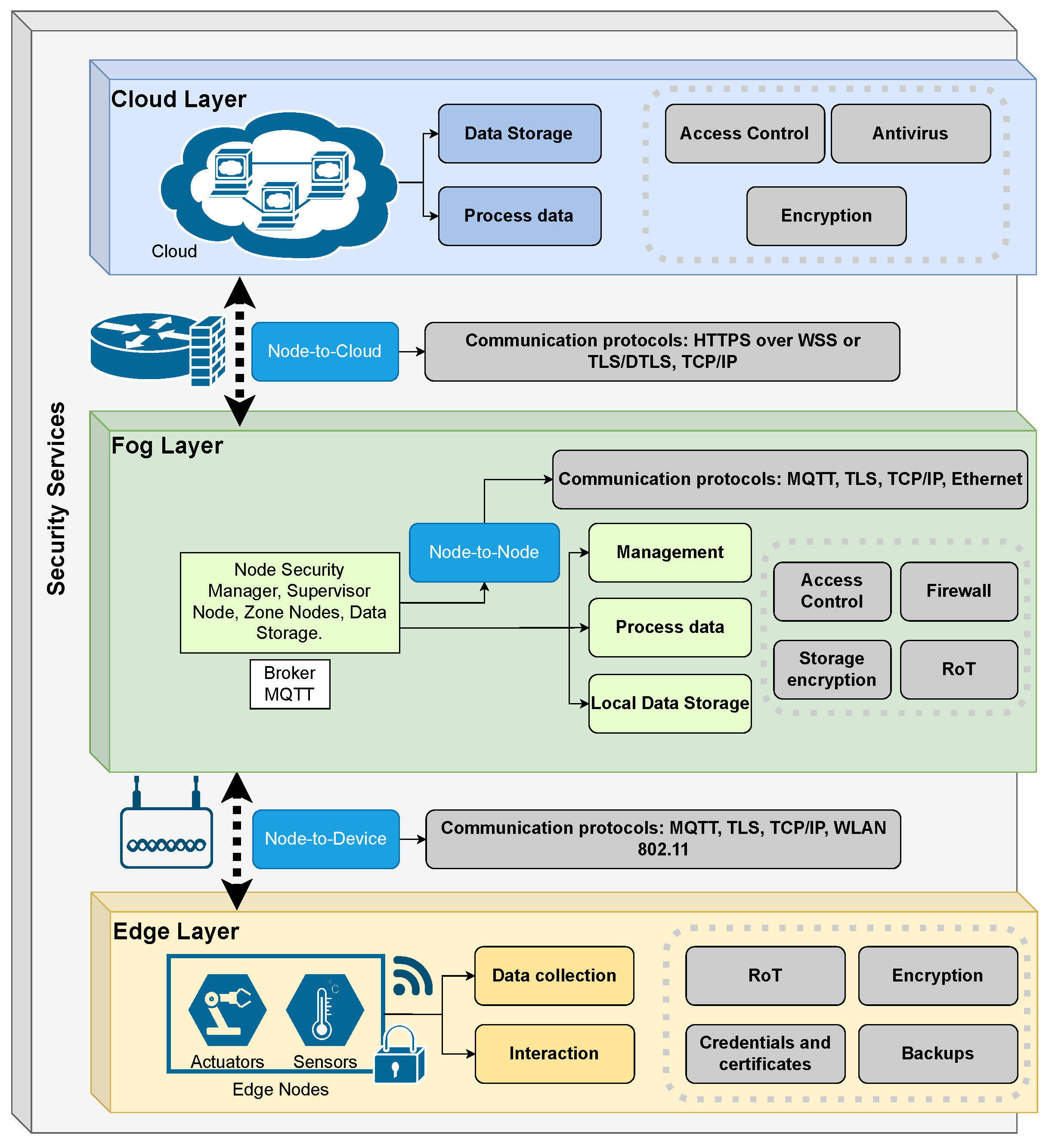
- Edge layer: This layer includes sensor and actuator devices involved in the operation of the buildings. Typically, these devices (1) evaluate safety and comfort-related parameters, such as building occupancy, indoor air quality, or fire detection systems, (2) are responsible for security operations, such as security cameras or motion sensors, and (3) execute local operations by means of actuators, such as intelligent climate control systems or automated lighting systems. These resource-constrained IoT devices are the most exposed ones in the architecture, so in order to be included in smart building applications several security mechanisms must be introduced. They need anti-tampering hardware systems to ensure software protection.
- Fog layer: This layer plays a key role in ensuring scalability and reliability. It is divided into two sub-layers of nodes: Zone nodes and supervisory nodes. Zone nodes, at the bottom of this layer, are responsible for specific areas in the building. These nodes process and store data locally and execute control operations in a restricted area. For security reasons, they are not visible from the Internet, their communication is restricted to connecting with a set of edge devices and the supervisory nodes. Typically, zone nodes are implemented over low-cost SBC platforms such as Raspberry Pi, or virtualized as containers in order to be centralized. Supervisory fog nodes are at the upper fog layer. These nodes are responsible for coordinating the operation of the whole building by supervising the operation of the zone nodes. Also, they act as proxies with cloud services for different operations.
- Cloud layer: This layer allows the use of certain advanced cloud services in smart building applications. These services may be related to different operations, such as weather forecasts, massive data storage, or data analysis. In order to avoid security flaws, only supervisory nodes are allowed to use cloud services. Since these nodes are exposed to the external Internet, they must be carefully configured to avoid or minimize the effect of external attacks.
3.1.2. Security Features
- Hardware Root of Trust: The HW-RoT is a hardware component that establishes a secure and trusted point of initiation for the chain of trust in a system. An example of such a component would be a security chip, such as a Trusted Platform Module (TPM), which stores cryptographic keys and other security credentials. This chip ensures that only trusted software and hardware are loaded during boot-up, thus creating a secure environment for the node. In the OpenFog context, this security chip is typically developed as part of a SoC (System on Chip), integrating various security functions directly into the node hardware.
- Secure Communications: Secure communications among the nodes in the architecture may be achieved by means of encryption services and identity brokering mechanisms. The cryptographic functions must ensure confidentiality (with private keys), integrity, authentication, and key generation (with public keys), while also establishing long-term credentials (with certificates). Only communication technologies involving security credentials and message encryption are considered able to provide confidentiality, integrity and availability.The MQTT protocol over TLS is suitable for Node-to-Device and Node-to-Node communications in big smart buildings. This protocol allows client devices to receive updates without constantly requesting them, reducing resource consumption and making MQTT ideal for high-latency networks [77]. Despite the limitations of this protocol, it is becoming widely adopted for resource-constrained IoT devices, since it is fast, simple, reliable, highly scalable and with a low implementation cost. The defense mechanisms are discussed in detail in [78]. Several MQTT implementations regarding security issues are analyzed in [79].The node-to-cloud communication, i.e., between the supervisory fog nodes and the cloud, is provided by means of the HTTPS protocol. This protocol, widely accepted on the Internet, uses encryption for secure communication over TCP/IP networks. HTTPS encrypts the messages by means of the TLS protocol. Thus, HTTPS provides authentication of the accessed website and protection of the privacy and integrity of the transmitted data.
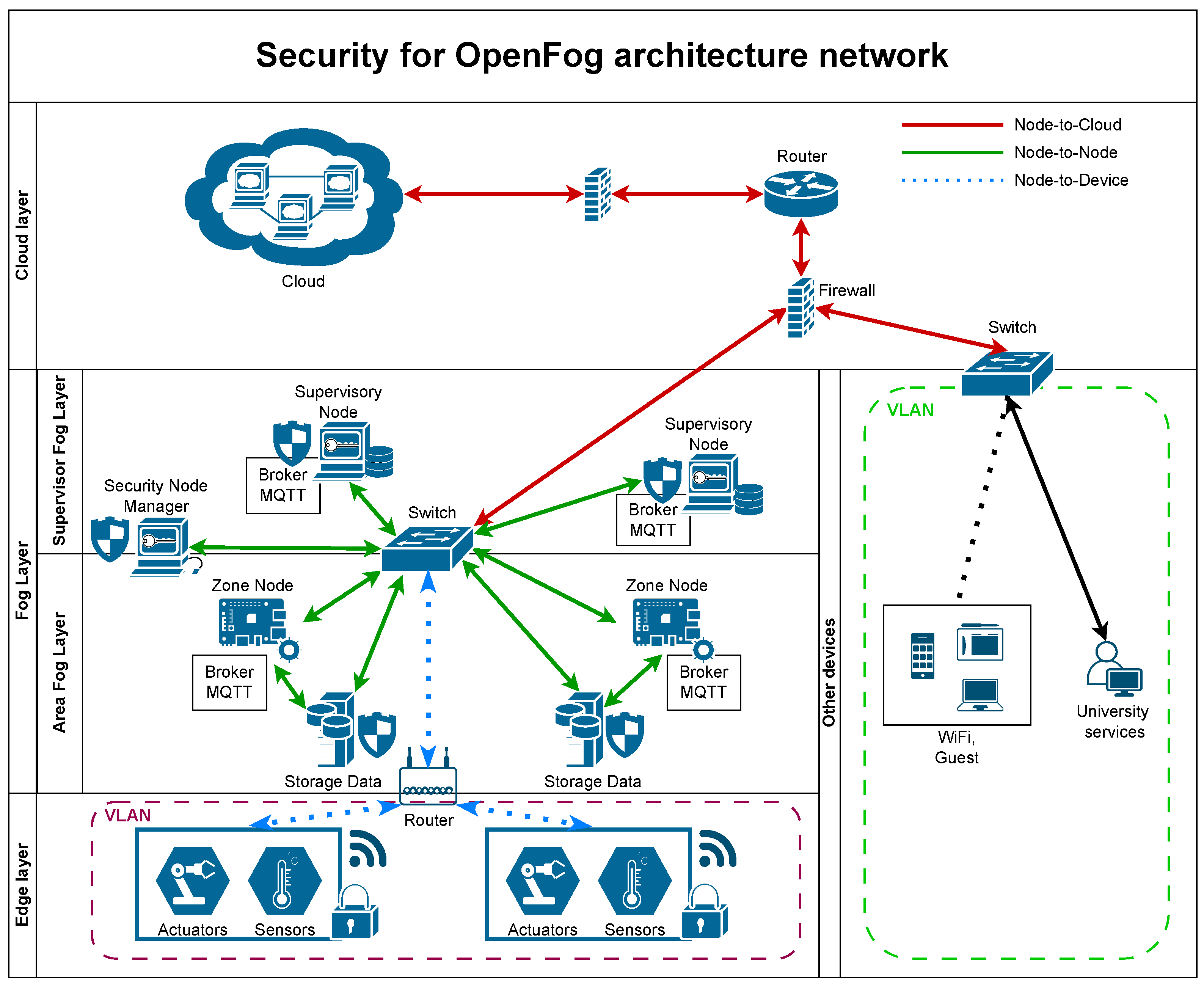
- Network configuration: Figure 2 shows the network structure of the architecture. In order to reduce the risk of threats in the system, connectivity among nodes will be restricted to the essential services (zero-trust), organized in a hierarchical way. The architecture may benefit from the use of existing communication infrastructures already available in the buildings.Edge nodes use corporate WiFi networks to establish Node-to-Device communication with the zone nodes, in the fog layer. This proven technology is a flexible alternative to connect devices in most public and private buildings since it is typically deployed to reach every corner of the buildings by means of the existing infrastructure. The use of a specific VLAN helps isolate different network segments and provides an additional layer of security by restricting communication to authorized devices within this VLAN. For security reasons, the horizontal communication among edge devices is disabled, so that only zone nodes are allowed to connect to a group of edge devices. In addition, all nodes, especially the nodes in the fog layer, must be protected by firewalls.The Node-to-Cloud communication is enforced by the supervisory fog nodes. These are the unique nodes allowed to connect to cloud services, not accessible from the Internet neither the zone nodes nor the edge nodes. Configuration efforts must be focused on the supervisory fog nodes.
- Node Management and Network Management: OpenFog introduces the concept of Out-of-Band (OOB) management, which refers to remote control of nodes from a centralized point, allowing the management of software, resources, security and health monitoring of the nodes. This approach provides an additional layer of control, as it enables administrators to manage multiple nodes from a single control node. The Node Security Manager centralizes the tasks related to the management of the keys and certificates of the nodes. In some cases, existing corporate infrastructures may be used for network security monitoring and management tasks. For example, Directory Services Management, Firewalls, Deep Packet Inspection (DPI), Intrusion Detection and Protection Systems (IPS/IDS) as well as System/Network Event and State Monitoring Systems may be used to manage the connectivity among the nodes of the architecture.
- Data storage: Protecting sensitive data, including keys, credentials, passwords and user/device identifiers is another essential aspect of the architecture. This information, usually stored in files, can be encrypted using different mechanisms, such as the File Encryption Key (FEK) or the Encrypting File System (EFS). The configuration of file system permissions in OS-based platforms may ensure that these files are accessible only to authorized users. Finally, an adequate backup policy is essential to avoid accidental data losses, especially in the fog layer.
- Containerization (Recommended): The use of containerization may improve the security of the critical nodes in the fog layer since containers increase the system’s resilience to attacks. OpenFog recommends to prioritize the use of containers over virtual machines (VMs). It uses a lightweight executable that is more versatile and secure than a VM due to its isolated Operating System (OS). Unlike VMs, which share resources, this approach has its own libraries, creating a self-contained environment. This isolation reduces cross-contamination risk and limits the impact of security breaches, offering additional protection. Thus, fog nodes could be executed in containers in order to provide higher security and flexibility.
3.1.3. Security Dimensions
- Access control: Resource access is only granted to authorized users and devices. These resources include network elements, stored information, information flows, or services and applications.The recommended way of providing access control is by means of the IEEE 802.1X standard [80]. This approach, in combination with a centralized authentication, authorization and accounting (AAA) management service, like Radius, provides an authentication mechanism for connecting to a LAN or WLAN. Directory services, such as LDAP, also play an important role in IP applications to share information about users, systems, networks, services and applications. The use of the 802.1X standard may not be available in some edge platforms. Although it is not recommended, if no other means are available, the combined use of pre-shared keys and MAC addresses may provide a minimum level of access control security for node-to-device connectivity.
- Authentication: It allows confirmation of the validity of the identities of the communication participants (i.e., users, devices and applications). It avoids masquerading or unauthorized attempts in communication.All devices must provide a HW-RoT in order to establish a secure and trusted point of initiation of the chain of trust in a system, ensuring a secure boot. The use of credentials, e.g., X509 certificates, is also needed for providing authentication at the nodes. Since edge nodes are not connected to the Internet, a local certificate authority (CA) may be established locally, in the institution, to create the certificates installed in the edge nodes.
- Non-repudiation: It prevents participants from denying the execution of a particular action. It supplies evidence to prove that every event or action has been carried out.The use of network and device logs for networking operations and local node tasks, respectively, may assist in achieving non-repudiation features. Critical operations should be signed with the certificates installed in the nodes.
- Data confidentiality: Confidentiality requires that data must only be understood by authorized participants. It involves both data at rest and data in motion.Diverse mechanisms are used, such as encryption, access control lists and file permissions. In the case of nodes with an OS, confidentiality may be enforced by encrypting disk information or by arranging file system configuration permissions. Confidentiality of data in motion is enforced by means of secure protocols over TLS, namely MQTT and HTTPS.
- Communication security: The information flow must be guaranteed between authorized end points so that the information is not diverted or intercepted in transit.Communication security is achieved by means of a secure stack of protocols over TCP/IP. In the case of node-to-device communications, MQTT over TLS is used as an application protocol. These data are transmitted over a WiFi VLAN, with access credentials serving as the first level of security, Node-to-Node communication is also enforced by means of MQTT over TLS, transmitted over wired networks, mostly Ethernet. Finally, Node-to-Cloud communication is provided by the corporate TCP/IP infrastructure involving diverse security appliances, such as corporate firewalls as well as other devices like IDS/IPS.
- Data integrity: Data must be correct and accurate. They must be protected against unauthorized modification, deletion, creation and replication.The use of encrypted protocols based on the use of certificates may guarantee the integrity of the data in motion. Additionally, critical data should be signed in order to ensure integrity. Access to the devices must be protected through hardware measures, such as flash encryption or physical access control. Antimalware packages and End Point Protection and Response (EDR) systems may contribute to protecting the integrity of the data. Finally, a backup policy should be established to avoid accidental data loss, especially in the fog layer.
- Availability: There must not be a denial of authorized access to the application services and resources. Disaster recovery solutions must be also included.Several mechanisms may be used to ensure edge node availability. The combination of a secure network configuration, involving network partitioning and connectivity restrictions, increases availability. If possible, nodes should have personal firewalls in order to restrict the connectivity to a certain number of ports and addresses. Device firewalls may complement corporate firewalls to achieve higher availability. The use of containerization may improve system availability. Finally, network monitoring and management appliances, such as IDS/IPS systems, are necessary to monitor the network and detect attacks early.
- Privacy: Protecting the information that could be derived from observing the network activity.The combination of previous measures guarantees privacy, In particular, secure end-to-end communications and data protection measures contribute to the privacy of the data in the applications. Also, a secure network configuration must be established.
3.2. Ensuring Security: Implementation Guidelines
- Ensure that all devices in the architecture satisfy the OpenFog hardware and software requirements. Besides HW-RoT, nodes should support symmetric key ciphers (AES with at least 128-bit keys or Triple-DES), asymmetric key ciphers (DH, RSA, DSA, ECDH, ECDSA or ECQV), cryptographic hash functions [81], true random number generators [82]) and message authentication codes (CCM, GCM, GMAC, CMAC or HMAC).
- Create a structure of certificates. This involves creating the certificates through a trusted Certificate Authority (CA) and installing them on the respective devices. Since the architecture design assumes that edge nodes are not available from the internet, the certificates installed on these nodes could be created by a local CA. Also, the configuration of the MQTT broker must include a user key and password for all Edge and Fog nodes in order to establish Node-to-device and node-to-node communication.
- Encrypt the firmware in Edge devices to secure the keys used for accessing networking services, e.g., MQTT or WiFi, as well as other sensitive data of the application.
- Define a separate WiFi VLAN to connect all edge layer nodes. This approach provides WiFi connectivity to all edge nodes in a more restrictive way. This approach achieves two major benefits: reducing interference with non-smart building applications and limiting the possibility of attacks. In addition, horizontal device-to-device communications in the Edge layer should not be allowed. Node-to-device communication, between the Edge and Fog layers, is limited to a few zone nodes, preferably connected to a wired network.
- Create a hierarchy of fog nodes that can be scaled to cover buildings of different sizes. Two types of fog nodes are used (see Figure 1): zone nodes and supervisory nodes. Zone nodes must run an MQTT broker to provide connectivity to a set of Edge nodes. Supervisory nodes must also run an MQTT broker to collect data from zone nodes. They need to be able to identify each other, which is achieved using the MQTT access configuration and associated access credentials.
- Robust security requires running accredited anti-virus software to protect the nodes against potential malware threats. Corporate and personal firewalls should be configured to grant access to a limited number of trusted devices and ports. IPS/IDS should detect and protect against suspicious activities.
- To secure communication between the cloud and fog/edge nodes, HTTPS is needed to encrypt data and apply strong authentication using certificates and multi-factor authentication.
3.3. Prevention of Cyber-Attacks with the Security Model
4. Case Study
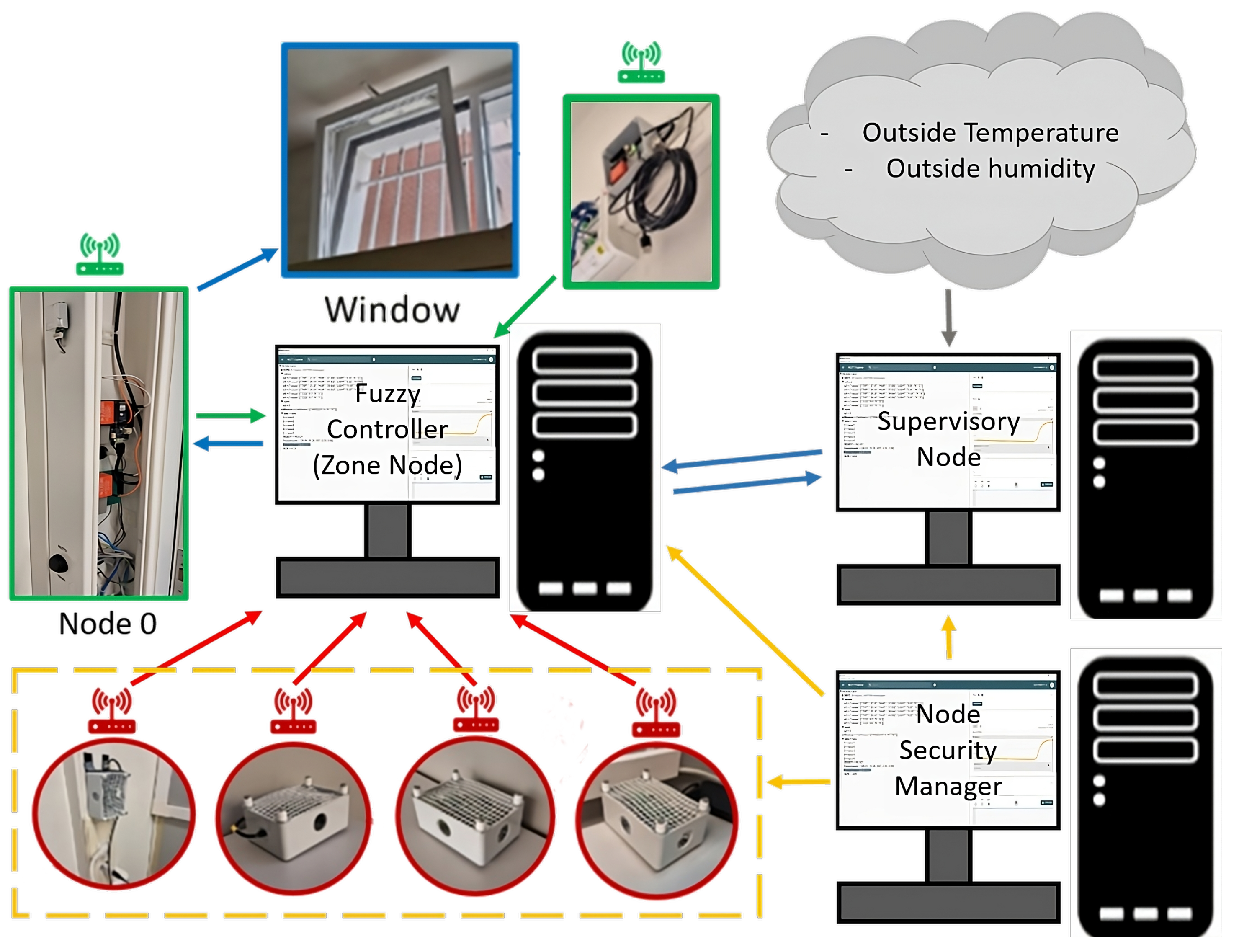
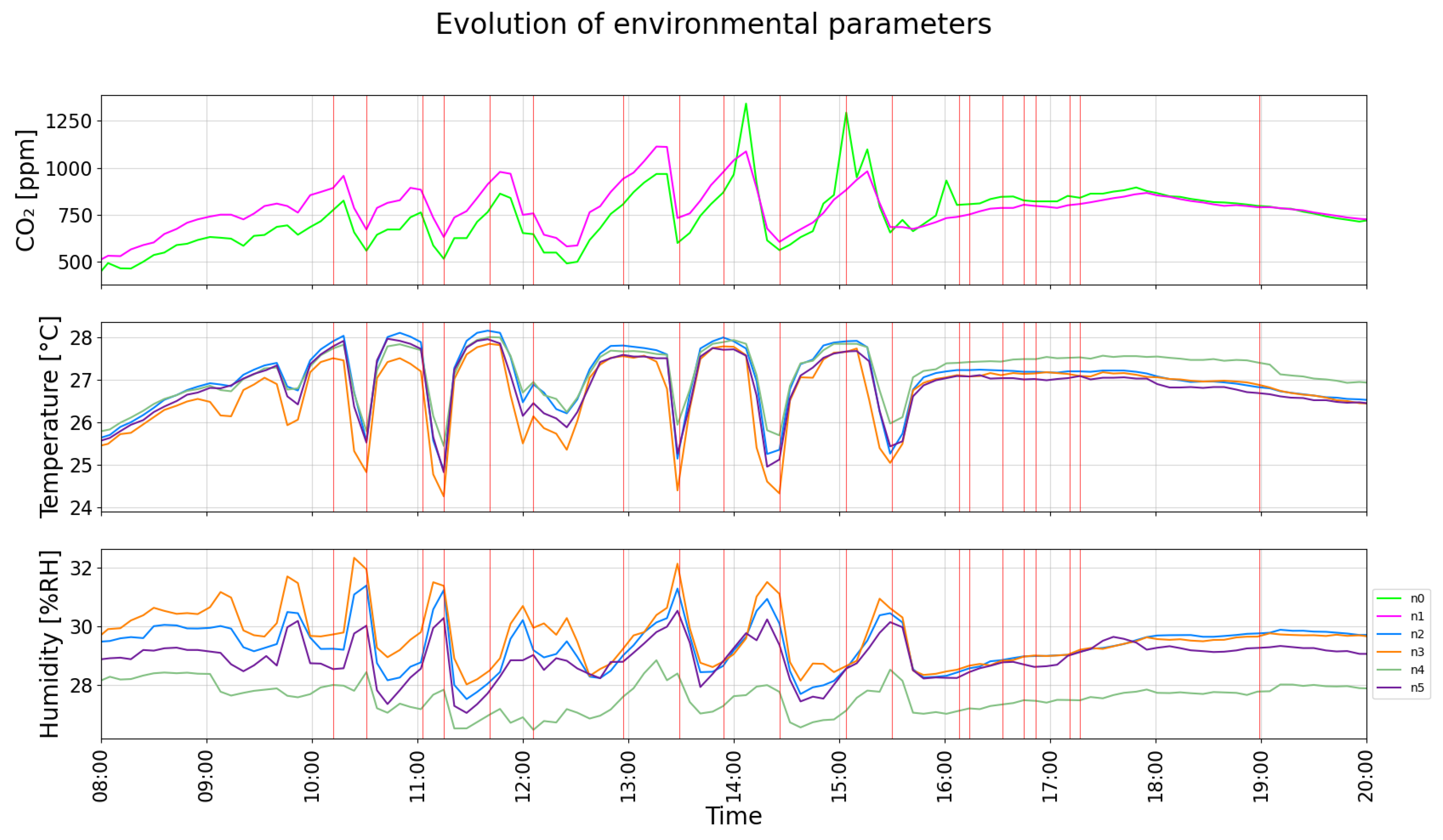
- Fog Layer: The IEQ fog layer comprises the supervisory and zone nodes. The supervisory node is responsible for centralizing the interaction with cloud services and coordinating the behavior of several zone nodes at the building level. The zone node is responsible for registering and processing the data in specific areas of the building, but it lacks direct Internet connectivity. This node executes an algorithm, based on Fuzzy logic, which is responsible for collecting the values of the target parameters in local areas of the building and making a decision accordingly. This decision involves controlling the actuator, in this case, opening or closing the window for some time.
- Edge Layer: Edge nodes (smart sensors and actuators) are scattered in selected areas of the building. They are responsible for measuring the environmental parameters and enforcing the response of the actuators. Prototypes of the smart nodes have been built over an ad hoc Printed Circuit Board (PCB) that integrates the selected sensors. In the proof-of-concept application, there are two node categories:
- –
- Smart nodes Group A: They measure IEQ parameters, namely temperature, humidity, and light intensity. Nodes N2, N3, N4 and N5 belong to this group in the proof-of-concept application.
- –
- Smart nodes Group B: These nodes measure environmental parameters, such as the amount of CO2, and control the behavior of the actuators. Nodes N0 and N1 belong to this group, but only N0 is responsible for controlling the actuator that opens/closes the window.
4.1. Components and Materials Used in the Architecture
- Edge Layer: Edge IoT devices are the most exposed since they are scattered throughout a wide area. Following OpenFog’s recommendations, physical protection has been designed to encapsulate each node’s hardware. This protection safeguards the hardware from physical tampering. In the deployed proof-of-concept, ESP32-S2-Saola-1V1.2 boards [84] were used. They offer significant advantages in terms of cost and availability. This board meets the requirements of the OpenFog standard, allowing features like flash encryption and HW-RoT. Additionally, the board’s libraries enable the implementation of security measures, such as secure network connections with usernames and passwords, as well as the use of certificates.
- Fog Layer: This layer includes three fog nodes: zone node, supervisory node and Node Security Manager (NMS). Desktop computers running Windows 10 were used to implement all nodes. The zone node hosts the MQTT broker and executes environmental control algorithms. The NSM provides additional security services, such as the creation of certificates and key creation, using OpenSSL as well as device and communication monitoring services. In this proof-of-concept application, the OOB network monitoring and diagnostic tasks were carried out directly by the networking staff, since they monitor all the traffic at the University.
4.2. Implementing Security Mechanisms
- Access control: At the edge layer, the Pre-Shared Key (PSK) is used due to its ability to provide simple but effective authentication of client devices. While the use of stronger measures is recommended, the combination of PSK and filtering by MAC addresses represents the minimum viable alternative for granting access to the WiFi VLAN. In the fog layer, the Lightweight Directory Access Protocol (LDAP), associated with corporate credentials, is implemented to ensure that only authorized personnel can access the corresponding resources. In the Fog layer, the use of the IEEE802.1X in combination with a centralized AAA (Authentication, Authorisation and Audit) provides access control capabilities to the network services.
- Authentication: At the edge layer, all smart sensors have a HW-RoT that grants a secure boot by only running trusted software. These nodes also include flash memory encryption to protect stored data and private keys, as well as security measures against physical fault injection attacks. At the fog layer, all devices are equipped with TPM NTC 7.2.1.0 version 2.0 TPM security hardware to verify their identity, complemented by two-factor authentication, requiring username and password for authorized personnel access. This access allows verification of the permissions assigned to the user, ensuring that only personnel with the appropriate authorization can interact with the information. All layers make use of x509 certificates for robust and consistent authentication across the communication infrastructure.
- Non-repudiation: Within the network infrastructure, activity monitoring is carried out on Node-to-Device, Node-to-Node and Node-to-Cloud communications. In the presented proof of concept, network monitoring was carried out by the University staff. In parallel, at the fog level, the computer operating system, Windows 10, has an integrated logging mechanism that records all operations performed, thus providing an additional layer of audit and control of system activity.
- Data confidentiality: In the edge layer, certificates in MQTT over TLS are used for Node-to-Device communication and credentials such as user names and passwords to prevent unauthorized access and queries. In the fog layer, in addition to the encryption of communications using certificates, access is controlled through a list of user permissions, restricting access to specific areas of the system. At the cloud layer, Node-to-Cloud communication is secured by means of the HTTPS protocol, which encrypts communications. File permission and access control lists ensure that only authorized personnel can access these communications.
- Communication security: The combination of WiFi VLAN, TCP/IP, and MQTT over TLS provides secure Node-to-Device communications, by means of encryption and authentication. Wired networks are used for node-to-node communications in the fog layer. In addition, the use of corporate firewalls and IDS/IPS systems implements some security features. Node-to-Cloud communication is enforced by means of the HTTPS protocol. In this case, security is enhanced with the use of corporate firewalls and IDS/IPS systems, managed by the networking staff of the University.
- Data integrity: The edge layer ensures data integrity by encrypting the flash memory and using the Digital Signature peripheral, on the ESP32-S2-Saola-1V1.2, to generate RSA digital signatures. This approach protects critical data and private keys from unauthorized access. At the fog layer, the zone and supervisory nodes safeguard the received data, using memory encryption and backups to prevent loss, while the anti-malware and corporate EDR systems may contribute to ensuring the data integrity in these nodes.
- Availability: At the edge layer, only a list of authorized devices are allowed to connect to the WiFi VLAN, following the zero trust principle. These nodes are also restricted to prevent access to higher layers of the network, restricting the communication capabilities in the network. Moving up to the fog layer, the PCs are shielded with the personal firewall system provided by the Windows OS. This approach blocks unauthorized access and maintains the security of the network architecture. In Node-to-Cloud communications, the node is protected from malware attacks by a corporate anti-virus and EDR system, complemented by corporate firewalls and IDS/IPS systems.
- Privacy: At the edge layer, fog layer and cloud layer, the use of the previous mechanisms may help to improve the privacy of the applications. It is important that network activities do not reveal private data, maintaining the confidentiality and integrity of information across the university network.
4.3. Following Implementation Guidelines
- Fog nodes have the requirements recommended by the OpenFog standard [27] (e.g., TPM module, HW-RoT, personal Firewall and credentials) [85]. Edge nodes have also been analyzed to check that ESP32-S2-Saola-1V1.2 board [84] satisfy the security aspects required by OpenFog (e.g., Secure Boot, Flash encryption, certificates and credentials).
- Since this is a proof-of-concept system, self-signed certificates have been managed manually using the Node Security Manager. Self-signed certificates offer significant advantages [86]. Also, this is a versatile way to manage certificates for specific intended purposes [87]. All certificates and private keys for edge devices were created using OpenSSL [88]. The following commands are an example of the most relevant onesThis command establishes the type of certificate, the duration, and the version and creates the public certificate and key:After generating the public certificate and key, the broker certificate must be defined:openssl req -new -x509 -days 365 -extensions v3_ca -keyout ca.key -out ca.crt -subj /CN="ID_My_server"This last line saves the public and server certificates:openssl req -out mosquitto.csr -key mosquitto.key -new -subj /CN="server_IP"The certificates for the clients are made by this command:openssl x509 -req -in mosquitto.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out mosquitto.crt -days 365openssl req -out esp.csr -key esp.key -new -subj /CN="IP_client"
- The use of flash encryption of firmware and sensor node keys [89] and the use of TPM modules in fog nodes ensures that devices connecting to the architecture’s network are authorized and that data are not vulnerable.The supervisory and zone nodes as well as the NSM node are located in a restricted access area. These computers are equipped with restricted access policies for only university staff. The encryption of the firmware such as the flash memory encryption, and the secure keys used for accessing the architecture network protect the information, communications and the system [90,91,92].
- All MAC addresses of the edge nodes have been registered by the central networking services of the Basque Country University to grant them access to the WiFi VLAN that it is also created by them. Within the VLAN, the edge nodes are hidden from each other. This means that if one device is hacked, it does not put the other sensor nodes at risk, since direct connection among them is not allowed. Only the zone and NSM nodes can connect bidirectionally with edge devices. The security configuration of the system verifies that all devices attempting to connect are trusted by using security keys, credentials and certificates.
- The configuration of the MQTT broker includes the required credentials and certificates. In the MQTT setup, certificates have been activated, including client certificates, user and password. The anonymous access has been disabled to prevent unauthorized access to the MQTT broker. The certificates and Inbound/Outbound rules created in the personal firewall limit the connectivity to only the devices shown in the image are able to connect.
- All fog nodes are equipped with the corporate antivirus software of the University. This approach protects devices from malware and trojans, as recommended by the Threat model (see Table 1). The Windows OS has been configured to provide personal firewalls that restrict access from edge devices using a set of selected ports. Figure 5 shows a configuration example of the personal firewall rules in the zone node.
- The use of LDAP directory services and the use of certificates protects against unauthorized access and it is used to encrypt communications. In Node-to-Cloud communication, the use of HTTPS provides a secure and reliable communication means with the cloud application. The corporate firewall has been configured so that only trusted devices can access the architecture’s network.
4.4. Experimental Results
4.4.1. Operation of the Proof-of-Concept IEQ System
4.4.2. Security Tests over the IEQ System
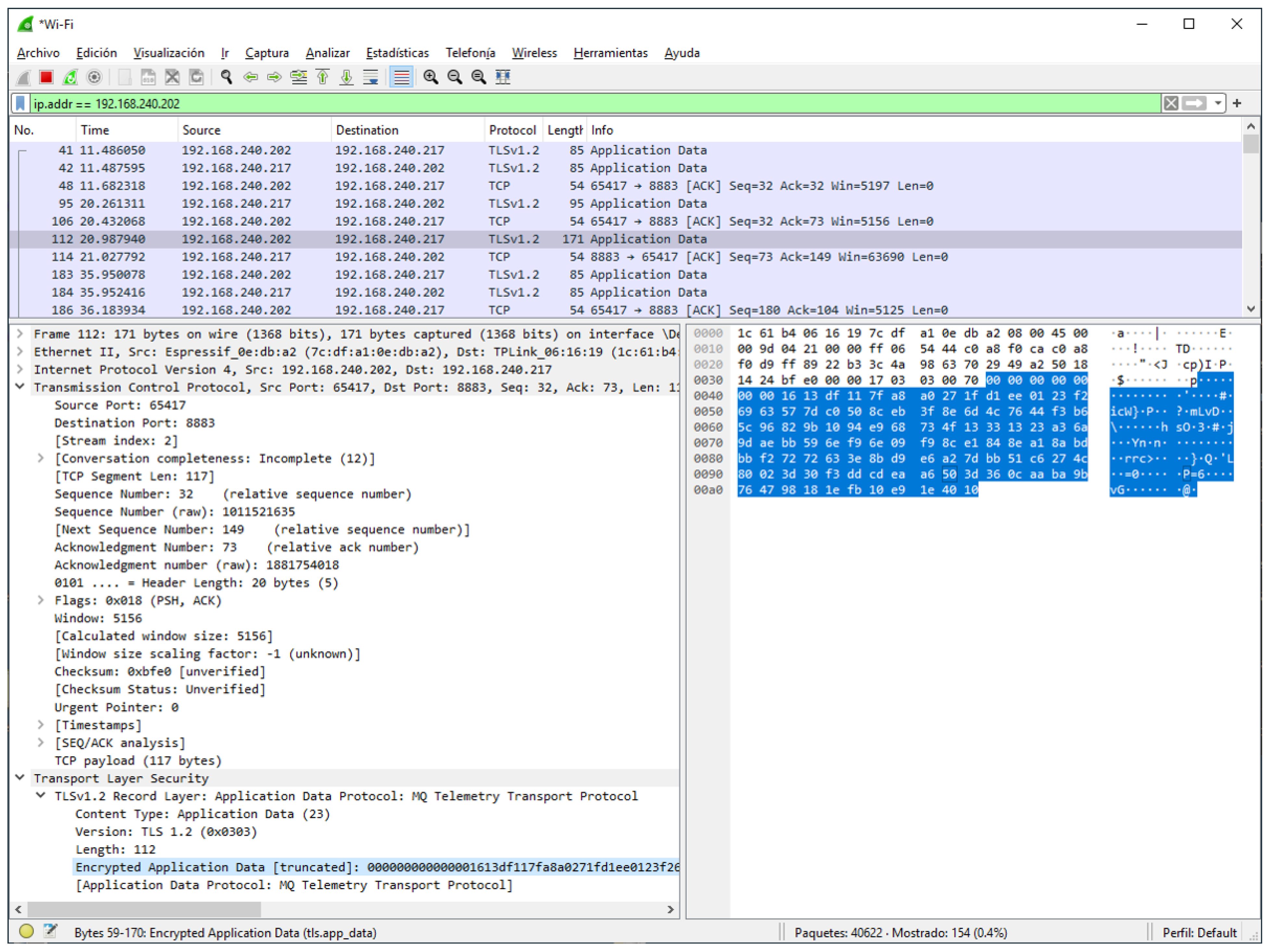
- Capture of the traffic generated by the proof-of-concept IEQ system: This test involved using the Wireshark network packet analyzer. Wireshark is a free and open-source packet analyzer used for network troubleshooting, analysis, software and communications protocol development among others.In this test, Wireshark was used to capture the messages exchanged between two nodes of the IEQ system application. These nodes were the Zone node, with the following IP addresses: 192.168.240.217 and one Smart node type A, with IP address 192.168.240.202).Figure 9 shows a capture of Wireshark in which it is possible to extract some information from the network traffic, such as the IP addresses as well as the identification of the MQTT protocol. It also detected that the reception TCP port in 192.168.240.217 was 8883, which is a common alternative when MQTT messages over TLS are sent. This information may allow attackers to guess that the computer with IP address 192.168.240.217 is executing the MQTT broker.The data within the TCP segment is encrypted, making it inaccessible and thereby preventing sniffing attacks. Additionally, the TLS protocol mandates the use of certificates that are linked to particular computers. For this reason, the presented approach reduces several threats such as MITM attacks among others.
- Network exploration with Nmap: The software used, Nmap (Network Mapper), is a free and open-source network discovery and security auditing tool. Nmap is frequently used to discover hosts and services on a computer network by sending packets and analyzing the responses. This application is frequently used for exploring IP networks.In this test a zero-trust approach was been followed. So, the network and the Firewall were configured to restrict the number of devices. Attackers could use this technology to identify the IP addresses of devices connected to the network and the ports used. Figure 10 shows all devices connected to the WiFi VLAN. In the figure, it is possible to find the IP addresses of nine devices. Devices highlighted in blue are smart nodes powered by ESP32 boards. The IP address of the zone node is 192.168.240.217, the supervisory node is 192.168.240.1, and the IP address of the attacker is 192.168.240.228.Figure 10 shows that the zone node (192.168.240.217) has only one open port to accept connections, which is 8883. Although it may be changed, this port is the default MQTT security port for the MQTT broker used in the test. Firewalls were configured to refuse the connections to other ports. Also, the smart nodes (in blue) did not show any open TCP port. Finally, the supervisory node has some open ports for remote configuration and monitoring.The use of network scanning tools that allow obtaining MAC and IP information poses potential risks. For this reason, the presented approach uses a configuration that reduces the exposition in the operation network to avoid attacks. This approach allows us to mitigate attacks such as MITM, DoS/DDoS, or IP Spoofing. The security measures in place prevent unauthorized access and manipulation, ensuring the integrity and resilience of our network.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AAA | Authentication, Authorization and Accounting |
| AES | Advanced Encryption Standard |
| AI | Artificial Intelligence |
| AIoT | Artificial Intelligence of Things |
| ANN | Artificial Neural Network |
| CA | Certificate Authority |
| CCM | Counter with Cipher Block Chaining-Message Authentication Code |
| CIA | Confidentiality, Integrity and Availability |
| CMAC | Cipher-based Message Authentication Code |
| DDoS | Distributed Denial of Service |
| DH | Diffie-Hellman |
| DPI | Deep Packet Inspection |
| DSA | Digital Signature Algorithm |
| ECDH | Elliptic Curve Diffie-Hellman |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| ECQV | Elliptic Curve Qu-Vanstone |
| EFS | Encrypting File System |
| EDR | Endpoint Detection and Response |
| ESM | Event and State Monitoring |
| FEK | File Encryption Key |
| FIPS | Federal Information Processing Standards |
| FOSS | Free and Open Source Software |
| GCM | Galois/Counter Mode |
| GMAC | Galois Message Authentication Code |
| HAS | Home Automation System |
| HMAC | Hash-based Message Authentication Code |
| HW-RoT | Hardware Root of Trust |
| IAQ | Indoor Air Quality |
| ICC | Industrial Communications Consortium |
| IEQ | Indoor Environmental Quality |
| IIRA | Industrial Internet Reference Architecture |
| IMSA | Intelligent Manufacturing System Architecture |
| IoT | Internet of Things |
| IPS/IDS | Intrusion Detection and Protection System |
| IVRA | Industrial Value Chain Reference Architecture |
| LDAP | Lightweight Directory Access Protocol |
| MAC | Media Access Control |
| MUD | Manufacturer Usage Description |
| NIST | National Institute of Standards and Technology |
| NSM | Node Security Manager |
| OOB | Out-of-Band |
| OS | Operating System |
| PSK | Pre-Shared Key |
| PSP | Platform Security Processor |
| PVC | Polyvinyl Chloride |
| RAMI 4.0 | Reference Architecture Model Industrie 4.0 |
| RSA | Rivest-Shamir-Adleman |
| SBC | Single Board Computing |
| SDN | Software Defined Networking |
| SHA | Secure Hash Algorithm |
| SME | Small or Medium-sized Enterprise |
| SoC | System on Chip |
| TCB | Trusted Computing Base |
| TPM | Trusted Platform Module |
| VLAN | Virtual Local Area Network |
| VM | Virtual Machine |
| VPN | Virtual Private Network |
References
- Jia, M.; Komeily, A.; Wang, Y.; Srinivasan, R.S. Adopting Internet of Things for the development of smart buildings: A review of enabling technologies and applications. Autom. Constr. 2019, 101, 111–126. [Google Scholar] [CrossRef]
- Jiang, T.; Li, Z.; Jin, X.; Chen, H.; Li, X.; Mu, Y. Flexible operation of active distribution network using integrated smart buildings with heating, ventilation and air-conditioning systems. Appl. Energy 2018, 226, 181–196. [Google Scholar] [CrossRef]
- Huotari, M.; Malhi, A.; Främling, K. Machine Learning Applications for Smart Building Energy Utilization: A Survey. Arch. Comput. Methods Eng. 2024, 31. [Google Scholar] [CrossRef]
- Starace, G.; Tiwari, A.; Colangelo, G.; Massaro, A. Advanced Data Systems for Energy Consumption Optimization and Air Quality Control in Smart Public Buildings Using a Versatile Open Source Approach. Electronics 2022, 11, 3904. [Google Scholar] [CrossRef]
- Bushnag, A. An improved air quality and climate control monitoring system using fuzzy logic for enclosed areas. J. Ambient. Intell. Humaniz. Comput. 2023, 14, 6339–6347. [Google Scholar] [CrossRef]
- Toral, I.M.; Calvo, I.; Xenakis, J.; Artetxe, E.; Barambones, O. Architecture for Smart Buildings Based on Fuzzy Logic and the OpenFog Standard. Electronics 2023, 12, 4889. [Google Scholar] [CrossRef]
- Vanus, J.; Gorjani, O.M.; Bilik, P. Novel proposal for prediction of CO2 course and occupancy recognition in intelligent buildings within IoT. Energies 2019, 12, 4541. [Google Scholar] [CrossRef]
- Khazaei, B.; Shiehbeigi, A.; Kani, A.R.H.M.A. Modeling indoor air carbon dioxide concentration using artificial neural network. Int. J. Environ. Sci. Technol. 2019, 16, 729–736. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, B.; Ma, J.; Jin, Q. Artificial intelligence of things (AIoT) data acquisition based on graph neural networks: A systematical review. Concurr. Comput. Pract. Exp. 2023, 35, e7827. [Google Scholar] [CrossRef]
- Verma, A.; Prakash, S.; Srivastava, V.; Kumar, A.; Mukhopadhyay, S.C. Sensing, Controlling, and IoT Infrastructure in Smart Building: A Review. IEEE Sens. J. 2019, 19, 9036–9046. [Google Scholar] [CrossRef]
- Eini, R.; Linkous, L.; Zohrabi, N.; Abdelwahed, S. Smart building management system: Performance specifications and design requirements. J. Build. Eng. 2021, 39, 102222. [Google Scholar] [CrossRef]
- Minoli, D.; Sohraby, K.; Occhiogrosso, B. IoT Considerations, Requirements, and Architectures for Smart Buildings-Energy Optimization and Next-Generation Building Management Systems. IEEE Internet Things J. 2017, 4, 269–283. [Google Scholar] [CrossRef]
- Sabireen, H.; Neelanarayanan, V. A Review on Fog Computing: Architecture, Fog with IoT, Algorithms and Research Challenges. ICT Express 2021, 7, 162–176. [Google Scholar] [CrossRef]
- Martin, B.A.; Michaud, F.; Banks, D.; Mosenia, A.; Zolfonoon, R.; Irwan, S.; Schrecker, S.; Zao, J.K. OpenFog security requirements and approaches. In Proceedings of the 2017 IEEE Fog World Congress, FWC 2017, Santa Clara, CA, USA, 30 October–1 November 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Rahimi, M.; Songhorabadi, M.; Kashani, M.H. Fog-based smart homes: A systematic review. J. Netw. Comput. Appl. 2020, 153, 102531. [Google Scholar] [CrossRef]
- Omoniwa, B.; Hussain, R.; Javed, M.A.; Bouk, S.H.; Malik, S.A. Fog/edge computing-based IoT (FECIoT): Architecture, applications, and research issues. IEEE Internet Things J. 2019, 6, 4118–4149. [Google Scholar] [CrossRef]
- Li, G.; Ren, L.; Fu, Y.; Yang, Z.; Adetola, V.; Wen, J.; Zhu, Q.; Wu, T.; Candan, K.S.; O’Neill, Z. A critical review of cyber-physical security for building automation systems. Annu. Rev. Control 2023, 55, 237–254. [Google Scholar] [CrossRef]
- Guan, Y.; Shao, J.; Wei, G.; Xie, M. Data Security and Privacy in Fog Computing. IEEE Netw. 2018, 32, 106–111. [Google Scholar] [CrossRef]
- Heartfield, R.; Loukas, G.; Budimir, S.; Bezemskij, A.; Fontaine, J.R.; Filippoupolitis, A.; Roesch, E. A taxonomy of cyber-physical threats and impact in the smart home. Comput. Secur. 2018, 78, 398–428. [Google Scholar] [CrossRef]
- Sivanathan, A.; Loi, F.; Gharakheili, H.H.; Sivaraman, V. Experimental evaluation of cybersecurity threats to the smart-home. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bhubaneswar, India, 17–20 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Mulero-Palencia, S.; Baeza, V.M. Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool. Electronics 2023, 12, 4815. [Google Scholar] [CrossRef]
- Gebremichael, T.; Ledwaba, L.P.; Eldefrawy, M.H.; Hancke, G.P.; Pereira, N.; Gidlund, M.; Akerberg, J. Security and Privacy in the Industrial Internet of Things: Current Standards and Future Challenges. IEEE Access 2020, 8, 152351–152366. [Google Scholar] [CrossRef]
- Atlam, H.F.; Wills, G.B. IoT Security, Privacy, Safety and Ethics. Internet Things 2020, 123–149. [Google Scholar] [CrossRef]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Nakagawa, E.Y.; Antonino, P.O.; Schnicke, F.; Capilla, R.; Kuhn, T.; Liggesmeyer, P. Industry 4.0 reference architectures: State of the art and future trends. Comput. Ind. Eng. 2021, 156, 107241. [Google Scholar] [CrossRef]
- Adoption of OpenFog Reference Architecture for Fog Computing (IEEE Standard 1934–2018). IEEE Communications Society. 2018. Available online: https://ieeexplore.ieee.org/document/8423800 (accessed on 6 November 2023).
- OpenFog Reference Architecture for Fog Computing 2017. Available online: https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf (accessed on 6 November 2023).
- Barton, M.; Budjac, R.; Tanuska, P.; Gaspar, G.; Schreiber, P. Identification Overview of Industry 4.0 Essential Attributes and Resource-Limited Embedded Artificial-Intelligence-of-Things Devices for Small and Medium-Sized Enterprises. Appl. Sci. 2022, 12, 5672. [Google Scholar] [CrossRef]
- Dodson, D.; Montgomery, D.; Polk, T.; Ranganathan, M.; Souppaya, M.; Johnson, S.; Kadam, A.; Pratt, C.; Thakore, D.; Walker, M.; et al. Securing Small-Business and Home Internet of Things (IoT) Devices: Mitigating Network-Based Attacks Using Manufacturer Usage Description (MUD); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021. [CrossRef]
- Jhanjhi, N.Z.; Humayun, M.; Almuayqil, S.N. Cyber Security and Privacy Issues in Industrial Internet of Things. Comput. Syst. Sci. Eng. 2021, 37, 361–380. [Google Scholar] [CrossRef]
- Kuo, P.H.; Mourad, A.; Lu, C.; Berg, M.; Duquennoy, S.; Chen, Y.Y.; Hsu, Y.H.; Zabala, A.; Ferrari, R.; Gonzalez, S.; et al. An integrated edge and Fog system for future communication networks. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference Workshops, WCNCW 2018, Barcelona, Spain, 15–18 April 2018; pp. 338–343. [Google Scholar] [CrossRef]
- Seliem, M.; Elgazzar, K.; Khalil, K. Towards Privacy Preserving IoT Environments: A Survey. Wirel. Commun. Mob. Comput. 2018, 2018, 1032761. [Google Scholar] [CrossRef]
- X.805: Security Architecture for Systems Providing End-to-End Communications. Available online: https://www.itu.int/rec/T-REC-X.805-200310-I/en (accessed on 17 July 2024).
- Chanal, P.M.; Kakkasageri, M.S. Security and Privacy in IoT: A Survey. Wirel. Pers. Commun. 2020, 115, 1667–1693. [Google Scholar] [CrossRef]
- Chen, W.; Ding, D.; Dong, H.; Wei, G. Distributed Resilient Filtering for Power Systems Subject to Denial-of-Service Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1688–1697. [Google Scholar] [CrossRef]
- Casteur, G.; Aubaret, A.; Blondeau, B.; Clouet, V.; Quemat, A.; Pical, V.; Zitouni, R. Fuzzing attacks for vulnerability discovery within MQTT protocol. In Proceedings of the 2020 International Wireless Communications and Mobile Computing, IWCMC 2020, Limassol, Cyprus, 15–19 June 2020; pp. 420–425. [Google Scholar] [CrossRef]
- Ahmad, F.; Kurugollu, F.; Adnane, A.; Hussain, R.; Hussain, F. MARINE: Man-in-the-Middle Attack Resistant Trust Model in Connected Vehicles. IEEE Internet Things J. 2020, 7, 3310–3322. [Google Scholar] [CrossRef]
- Alkhwaja, I.; Albugami, M.; Alkhwaja, A.; Alghamdi, M.; Abahussain, H.; Alfawaz, F.; Almurayh, A.; Min-Allah, N. Password Cracking with Brute Force Algorithm and Dictionary Attack Using Parallel Programming. Appl. Sci. 2023, 13, 5979. [Google Scholar] [CrossRef]
- Chen, B.; Ho, D.W.; Hu, G.; Yu, L. Secure Fusion Estimation for Bandwidth Constrained Cyber-Physical Systems under Replay Attacks. IEEE Trans. Cybern. 2018, 48, 1862–1876. [Google Scholar] [CrossRef] [PubMed]
- Prabadevi, B.; Jeyanthi, N. A Review on Various Sniffing Attacks and its Mitigation Techniques. Indones. J. Electr. Eng. Comput. Sci. 2018, 12, 1117–1125. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Slowinska, M.; Theodorakopoulos, G.; Burnap, P. A Supervised Intrusion Detection System for Smart Home IoT Devices. IEEE Internet Things J. 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Esquivel-Vargas, H.; Caselli, M.; Peter, A. Automatic deployment of specification-based intrusion detection in the BACnet Protocol. In Proceedings of the CPS-SPC 2017—Proceedings of the 2017 Workshop on Cyber-Physical Systems Security and PrivaCy, co-Located with CCS 2017, Dallas, TX, USA, 3 November 2017; Volume 17, pp. 25–36. [Google Scholar] [CrossRef]
- Zheng, Z.; Reddy, A.L. Safeguarding building automation networks: THE-driven anomaly detector based on traffic analysis. In Proceedings of the 2017 26th International Conference on Computer Communications and Networks, ICCCN 2017, Vancouver, BC, Canada, 31 July–3 August 2017. [Google Scholar] [CrossRef]
- Yang, Y.S.; Lee, S.H.; Chen, W.C.; Yang, C.S.; Huang, Y.M.; Hou, T.W. Securing SCADA Energy Management System under DDos Attacks Using Token Verification Approach. Appl. Sci. 2022, 12, 530. [Google Scholar] [CrossRef]
- Sheikh, A.; Kamuni, V.; Patil, A.; Wagh, S.; Singh, N. Cyber Attack and Fault Identification of HVAC System in Building Management Systems. In Proceedings of the 2019 9th International Conference on Power and Energy Systems, ICPES 2019, Perth, WA, Australia, 10–12 December 2019. [Google Scholar] [CrossRef]
- Hachem, J.E.; Chiprianov, V.; Babar, M.A.; Khalil, T.A.; Aniorte, P. The Journal of Systems and Software Modeling, analyzing and predicting security cascading attacks in smart buildings systems-of-systems Systems-of-systems Security modeling and analysis Model driven engineering Software architecture Multi-agent systems simulation Smart buildings. J. Syst. Softw. 2020, 162, 110484. [Google Scholar] [CrossRef]
- Peacock, M. Anomaly Detection in BACnet/IP Managed Building Automation Systems. Ph.D. Thesis, Edith Cowan University, Joondalup, Australia, 2019. [Google Scholar]
- Zhang, F.; Kodituwakku, H.A.D.E.; Hines, J.W.; Coble, J. Multilayer Data-Driven Cyber-Attack Detection System for Industrial Control Systems Based on Network, System, and Process Data. IEEE Trans. Ind. Inform. 2019, 15, 4362–4369. [Google Scholar] [CrossRef]
- Fauri, D.; Kapsalakis, M.; dos Santos, D.R.; Costante, E.; den Hartog, J.; Etalle, S. Leveraging semantics for actionable intrusion detection in building automation systems. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) LNCS; Springer Science+Business Media: Berlin, Germany, 2019; Volume 11260, pp. 113–125. [Google Scholar] [CrossRef]
- Zhang, S.; Rong, J.; Wang, B. A privacy protection scheme of smart meter for decentralized smart home environment based on consortium blockchain. Int. J. Electr. Power Energy Syst. 2020, 121, 106140. [Google Scholar] [CrossRef]
- Feng, T.; Zhang, B.; Liu, C.; Zheng, L. Security assessment and improvement of building ethernet KNXnet/IP protocol. Discov. Appl. Sci. 2024, 6, 162. [Google Scholar] [CrossRef]
- Daneshgar, F.F.; Abbaspour, M. Extracting fuzzy attack patterns using an online fuzzy adaptive alert correlation framework. Secur. Commun. Netw. 2016, 9, 2245–2260. [Google Scholar] [CrossRef]
- Ban, X.; Ding, M.; Liu, S.; Chen, C.; Zhang, J. IoTFuzz: Automated Discovery of Violations in Smart Homes with Real Environment. IEEE Internet Things J. 2024, 11, 10183–10196. [Google Scholar] [CrossRef]
- Fovino, I.N.; Coletta, A.; Carcano, A.; Masera, M. Critical state-based filtering system for securing SCADA network protocols. IEEE Trans. Ind. Electron. 2012, 59, 3943–3950. [Google Scholar] [CrossRef]
- Ding, D.; Han, Q.L.; Xiang, Y.; Ge, X.; Zhang, X.M. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing 2018, 275, 1674–1683. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure Three-Factor Authentication Protocol for Multi-Gateway IoT Environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [PubMed]
- Elnour, M.; Meskin, N.; Khan, K.; Jain, R. Application of data-driven attack detection framework for secure operation in smart buildings. Sustain. Cities Soc. 2021, 69, 102816. [Google Scholar] [CrossRef]
- Paridari, K.; Mady, A.E.D.; Porta, S.L.; Chabukswar, R.; Blanco, J.; Teixeira, A.; Sandberg, H.; Boubekeur, M. Cyber-Physical-Security Framework for Building Energy Management System. In Proceedings of the 2016 ACM/IEEE 7th International Conference on Cyber-Physical Systems, ICCPS 2016—Proceedings, Vienna, Austria, 11–14 April 2016. [Google Scholar] [CrossRef]
- Ji, X.; Li, C.; Zhou, X.; Zhang, J.; Zhang, Y.; Xu, W. Authenticating Smart Home Devices via Home Limited Channels. ACM Trans. Internet Things 2020, 1, 24. [Google Scholar] [CrossRef]
- Lahmadi, A.; Duque, A.; Heraief, N.; Francq, J. MitM Attack Detection in BLE Networks Using Reconstruction and Classification Machine Learning Techniques. Commun. Comput. Inf. Sci. 2020, 1323, 149–164. [Google Scholar] [CrossRef]
- Aloseel, A.; Al-Rubaye, S.; Zolotas, A.; He, H.; Shaw, C. A Novel Approach for Detecting Cyberattacks in Embedded Systems Based on Anomalous Patterns of Resource Utilization-Part i. IEEE Access 2021, 9, 103204–103229. [Google Scholar] [CrossRef]
- McBride, J.; Hernandez-Castro, J.; Arief, B. Earworms Make Bad Passwords: An Analysis of the Nokē Smart Lock Manual Override. In Proceedings of the 2017 International Workshop on Secure Internet of Things, SIoT 2017, Oslo, Norway, 15 September 2017; pp. 30–39. [Google Scholar] [CrossRef]
- Helen, D. Exploring cyber attacks in blockchain technology enabled green smart city. In Green Blockchain Technology for Sustainable Smart Cities; Elsevier: Amsterdam, The Netherlands, 2023. [Google Scholar] [CrossRef]
- Acar, A.; Fereidooni, H.; Abera, T.; Sikder, A.K.; Miettinen, M.; Aksu, H.; Conti, M.; Sadeghi, A.R.; Uluagac, S. Peek-a-boo: I see your smart home activities, even encrypted! In Proceedings of the WiSec 2020—Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Linz, Austria, 8–10 July 2020; pp. 207–218. [Google Scholar] [CrossRef]
- Vaccari, I.; Cambiaso, E.; Aiello, M. Evaluating Security of Low-Power Internet of Things Networks. Int. J. Comput. Digit. Syst. 2019, 8, 101–114. [Google Scholar] [CrossRef]
- Liu, X.; Zeng, Q.; Du, X.; Valluru, S.L.; Fu, C.; Fu, X.; Luo, B. SniffMislead: Non-intrusive privacy protection against wireless packet sniffers in smart homes. In Proceedings of the 24th International Symposium on Research in Attacks, Intrusions and Defenses, San Sebastian, Spain, 6–8 October 2021; pp. 33–47. [Google Scholar] [CrossRef]
- Ahlawat, B.; Sangwan, A.; Sindhu, V. IOT System Model, Challenges and Threats. Artic. Int. J. Sci. Technol. Res. 2020, 9, 6771–6776. [Google Scholar]
- Kumar, A.; Sharma, S.; Goyal, N.; Singh, A.; Cheng, X.; Singh, P. Secure and energy-efficient smart building architecture with emerging technology IoT. Comput. Commun. 2021, 176, 207–217. [Google Scholar] [CrossRef]
- Filho, G.P.; Meneguette, R.I.; Maia, G.; Pessin, G.; Gonçalves, V.P.; Weigang, L.; Ueyama, J.; Villas, L.A. A fog-enabled smart home solution for decision-making using smart objects. Future Gener. Comput. Syst. 2020, 103, 18–27. [Google Scholar] [CrossRef]
- Froiz-Míguez, I.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. Design, Implementation and Practical Evaluation of an IoT Home Automation System for Fog Computing Applications Based on MQTT and ZigBee-WiFi Sensor Nodes. Sensors 2018, 18, 2660. [Google Scholar] [CrossRef]
- Gordon, H.; Batula, C.; Tushir, B.; Dezfouli, B.; Liu, Y. Securing smart homes via software-defined networking and low-cost traffic classification. In Proceedings of the 2021 IEEE 45th Annual Computers, Software, and Applications Conference, COMPSAC 2021, Madrid, Spain, 12–16 July 2021; pp. 1049–1057. [Google Scholar] [CrossRef]
- Younus, M.U.; ul Islam, S.; Ali, I.; Khan, S.; Khan, M.K. A survey on software defined networking enabled smart buildings: Architecture, challenges and use cases. J. Netw. Comput. Appl. 2019, 137, 62–77. [Google Scholar] [CrossRef]
- Alabady, S.A.; Al-Turjman, F.; Din, S. A Novel Security Model for Cooperative Virtual Networks in the IoT Era. Int. J. Parallel Program. 2020, 48, 280–295. [Google Scholar] [CrossRef]
- Tan, L.; Yu, K.; Ming, F.; Cheng, X.; Srivastava, G. Secure and Resilient Artificial Intelligence of Things: A HoneyNet Approach for Threat Detection and Situational Awareness. IEEE Consum. Electron. Mag. 2022, 11, 69–78. [Google Scholar] [CrossRef]
- Cisco, C.M. AAA PROTOCOLS: Authentication, Authorization, and Accounting for the Internet. IEEE Internet Comput. 1999, 3, 75–79. [Google Scholar]
- Katsikeas, S.; Fysarakis, K.; Miaoudakis, A.; Bemten, A.V.; Askoxylakis, I.; Papaefstathiou, I.; Plemenos, A. Lightweight & secure industrial IoT communications via the MQ telemetry transport protocol. In Proceedings of the IEEE Symposium on Computers and Communications, Heraklion, Greece, 3–6 July 2017; pp. 1193–1200. [Google Scholar] [CrossRef]
- Lakshminarayana, S.; Praseed, A.; Thilagam, P.S. Securing the IoT Application Layer from an MQTT Protocol Perspective: Challenges and Research Prospects. IEEE Commun. Surv. Tutor. 2024, 1. [Google Scholar] [CrossRef]
- Mishra, B.; Kertesz, A. The use of MQTT in M2M and IoT systems: A survey. IEEE Access 2020, 8, 201071–201086. [Google Scholar] [CrossRef]
- IEEE. 802.1X-2020-IEEE Standard for Local and Metropolitan Area Networks–Port-Based Network Access Control; IEEE: Piscataway, NJ, USA, 2020; ISBN 978-1-5044-6440-6. Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=9018454 (accessed on 6 June 2024).
- Dobraunig, C.; Eichlseder, M.; Mendel, F. Analysis of SHA-512/224 and SHA-512/256. In Proceedings of the Advances in Cryptology–ASIACRYPT 2015: 21st International Conference on the Theory and Application of Cryptology and Information Security, Auckland, New Zealand, 29 November–3 December 2015. [Google Scholar] [CrossRef]
- May, W.E. Approved Random Number Generators for FIPS PUB 140-2, Security Requirements for Cryptographic Modules; FIPS PUB. 2021. Available online: www.nist.gov/cmvp (accessed on 6 June 2024).
- Weather API—OpenWeatherMap. Available online: https://openweathermap.org/api (accessed on 6 June 2024).
- ESP32 S2 WROVER ESP32 S2 WROVER I Datasheet. 2022. Available online: www.espressif.com (accessed on 17 January 2024).
- Device protection in Windows Security—Microsoft Support. Available online: https://support.microsoft.com/en-us/windows/device-protection-in-windows-security-afa11526-de57-b1c5-599f-3a4c6a61c5e2 (accessed on 8 July 2024).
- Garba, A.; Khoury, D.; Balian, P.; Haddad, S.; Sayah, J.; Chen, Z.; Guan, Z.; Hamdan, H.; Charafeddine, J.; Al-Mutib, K. LightCert4IoTs: Blockchain-Based Lightweight Certificates Authentication for IoT Applications. IEEE Access 2023, 11, 28370–28383. [Google Scholar] [CrossRef]
- Li, B.; Lin, J.; Wang, Q.; Wang, Z.; Jing, J. Locally-Centralized Certificate Validation and its Application in Desktop Virtualization Systems. IEEE Trans. Inf. Forensics Secur. 2021, 16, 1380–1395. [Google Scholar] [CrossRef]
- OpenSSL. Available online: https://www.openssl.org/ (accessed on 8 July 2024).
- Flash Encryption ESP32 ESP-IDF Programming Guide Latest Documentation. Available online: https://docs.espressif.com/projects/esp-idf/en/latest/esp32/security/flash-encryption.html (accessed on 8 July 2024).
- LUKS on Raspberry Pi|LUKS-on-Raspberry-Pi. Available online: https://rr-developer.github.io/LUKS-on-Raspberry-Pi/ (accessed on 8 July 2024).
- Raspberry Pi-Full Disk Encryption|Kali Linux Documentation. Available online: https://www.kali.org/docs/arm/raspberry-pi-with-luks-full-disk-encryption-2/ (accessed on 8 July 2024).
- Increasing security|The Raspberry Pi Guide. Available online: https://raspberrypi-guide.github.io/other/Improve-raspberry-pi-security (accessed on 8 July 2024).




| Threat Categories | Confidentiality Violation | Integrity Violation | Authentication Violation | Availability Violation | Privacy Violation | |
| Intents | Leakinginformationthroughovert/covertchannels | Modifyingdata/codewithoutproperauthorization | Masqueradingone entity asanother entity | Renderingresourcesunreachable/unavailable | Leakingsensitiveinformationof an entity(incl. identity) | |
| Attack Venues | Insider Attacks | Data Leaks | DataAlteration | Identity/Password/Key Leaks | EquipmentSabotage | Data/IdentityLeaks |
| Hardware Attacks | HardwareTrojans, Side ChannelAttacks | HardwareTrojans | Hardware Trojans | RadioJamming, BandwidthExhaustion | HardwareTrojans, Side ChannelAttacks | |
| Software Attacks | Malware | Malware | Malware | DoS/DDoS, ResourceDepletion | Malware, SocialNetworkAnalyses | |
| Network Based Attacks | Eavesdropping | Message/TransactionReplay | Spoofing, Man-in-MiddleAttacks | DoS/DDoS, SubnetFlooding | Traffic PatternAnalyses | |
| Type of Attack | Proposed Solutions | Description |
|---|---|---|
| DoS/DDoS | [42, 43, 44, 45, 46, 47, 48] | Anomaly detection when theserver is saturated by excessivedata traffic preventing the useof online services and sites. |
| Tampering | [49, 50, 51, 52] | Secure hardware systemsagainst physical tampering andunauthorised access. |
| Fuzzing attack | [53, 54] | System alerts when the data arebeing exploited by the attack orfuzz models for testing systemsto seek vulnerabilities. |
| Replay attack | [42, 45, 46, 55, 56, 57] | Protect the authenticity andtimeliness ofcommunications to securethe network between devices. |
| MITM | [42, 57, 58, 59, 60, 61] | Ensure the confidentiality ofinformation transferred betweentwo entities. |
| Password Brute-Force attack | [57, 62, 63, 64] | Introduce good user andpassword policies. |
| Sniffing | [65, 66, 67, 68] | Encryption from maliciousactivities where an attackerintercepts and captures networktraffic to gain unauthorized accessto sensitive information. |
| IP Spoofing | [42, 52, 57] | Protect against false identities ofentities impersonating users ordevices to avoid compromisingthe IoT architecture. |
| X.805 Security Dimensions | Node-to-Cloud Security Functions | Node-to-Node Security Functions | Node-to-Device Security Functions |
|---|---|---|---|
| Access control | IEEE 802.1X, Centralized AAA, Directory services (LDAP) | IEEE 802.1X, Centralized AAA, Directory services (LDAP) | IEEE 802.1X, Centralized AAA, Directory services (LDAP), PSK+MAC |
| Authentication | HW-RoT (TPM), X509 certificates, Credentials | HW-RoT (TPM), X509 certificates, Credentials | HW-RoT, X509 certificates, Credentials |
| Non-repudiation | Network and device logs.Signed data and operations | Network and device logs.Signed data and operations | Network and device logs (if available).Signed data and operations |
| Data confidentiality | Encryption, Access controllist and file permissions. HTTPS | Encryption, Access control listand file permissions. MQTTover TLS | Encryption, Access control list andfile permissions. MQTT over TLS |
| Communication security | HTTPS, corporate andpersonal firewalls, IDS/IPS systems | MQTT over TLS, corporateand personal firewalls, IDS/IPS | MQTT over TLS, WiFi VLAN, corporate and personal (if aviable)firewalls |
| Data integrity | File encryption systems, Backups, Signed data, Antimalware, EDR systems. | File encryption systems, Backups, Signed data, Antimalware, EDR systems. | File encryption systems, Backups, Signed data, Antimalware, EDR systems. (If available) |
| Availability | Secure network configuration(zero-trust), network partitioning, corporate and personal firewalls, IDS/IPS systems. Containerization | Secure network configuration(zero-trust), network partitioning, corporate and personal firewalls, IDS/IPS systems, Containerization | Secure network configuration(zero-trust), network partitioning, VLANs, corporate andpersonal firewalls, |
| Privacy | Secure end-to-end communicationtechnologies, secure networkconfiguration | Secure end-to-end communicationtechnologies, secure networkconfiguration | Secure end-to-end communicationtechnologies, secure networkconfiguration |
| X.805 Security Dimensions | Node-to-Cloud Security Functions | Node-to-Node Security Functions | Node-to-Device Security Functions |
|---|---|---|---|
| Access control | IEEE 802.1X, Centralized AAA, Directory services (LDAP) | IEEE 802.1X, Centralized AAA, Directory services (LDAP) | PSK + MAC |
| Authentication | HW-RoT (TPM), X509 certificates, Credentials | HW-RoT (TPM), X509 certificates, Credentials | HW-RoT, X509 certificates, Credentials |
| Non-repudiation | Network and device logs.Signed data and operations | Network and device logs.Signed data and operations | Network and device logs (if available).Signed data and operations |
| Data confidentiality | Encryption, Access controllist and file permissions. HTTPS | Encryption, Access control listand file permissions. MQTTover TLS | Encryption. MQTT over TLS |
| Communication security | HTTPS, corporate andpersonal firewalls, IDS/IPS systems | MQTT over TLS, corporateand personal firewalls, IDS/IPS | MQTT over TLS, WiFi VLAN, corporate(if available)firewalls |
| Data integrity | Encrypted memory, Backups, Signed data, Antimalware, EDR systems. | Encrypted memory, Backups, Signed data, Antimalware, EDR systems. | Encrypted memory, Signed data |
| Availability | Secure network configuration(zero-trust), network partitioning, corporate and personal firewalls, IDS/IPS systems. | Secure network configuration(zero-trust), network partitioning, corporate and personal firewalls, IDS/IPS systems, | Secure network configuration(zero-trust), network partitioning, VLANs, corporate andpersonal firewalls, |
| Privacy | Secure end-to-end communicationtechnologies, secure networkconfiguration | Secure end-to-end communicationtechnologies, secure networkconfiguration | Secure end-to-end communicationtechnologies, secure networkconfiguration |
| Group A | Group B | |
|---|---|---|
| Nodes | N2, N3, N4, and N5 | N0 and N1 |
| Paramaters to measure | Temperature, humidity, and light intensity | CO2 |
| Sensors | - BME680 - KPS-3227-SP1C | - MH-Z19B |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Martín Toral, I.; Calvo, I.; Villar, E.; Gil-García, J.M.; Barambones, O. Introducing Security Mechanisms in OpenFog-Compliant Smart Buildings. Electronics 2024, 13, 2900. https://doi.org/10.3390/electronics13152900
Martín Toral I, Calvo I, Villar E, Gil-García JM, Barambones O. Introducing Security Mechanisms in OpenFog-Compliant Smart Buildings. Electronics. 2024; 13(15):2900. https://doi.org/10.3390/electronics13152900
Chicago/Turabian StyleMartín Toral, Imanol, Isidro Calvo, Eneko Villar, Jose Miguel Gil-García, and Oscar Barambones. 2024. "Introducing Security Mechanisms in OpenFog-Compliant Smart Buildings" Electronics 13, no. 15: 2900. https://doi.org/10.3390/electronics13152900
APA StyleMartín Toral, I., Calvo, I., Villar, E., Gil-García, J. M., & Barambones, O. (2024). Introducing Security Mechanisms in OpenFog-Compliant Smart Buildings. Electronics, 13(15), 2900. https://doi.org/10.3390/electronics13152900










