Software-Defined Virtual Private Network for SD-WAN
Abstract
1. Introduction
- Refactoring traditional VPNs with SDN architecture by proposing an overlay-based SD-WAN solution named SD-VPN and including its evaluating metrics;
- Proposing a joint placement algorithm of SD-VPN controllers and gateways for high-efficiency controllability and low-latency transmission;
- Proposing algorithms of overlay WAN service loading and offloading to orchestrate VPN services, routing rules, and QoS strategies;
- Implementing an SD-VPN system and evaluating it in both simulation environments and actual network systems.
2. Related Work
2.1. Research on VPNs
2.2. Research on SD-WANs
2.3. Summary
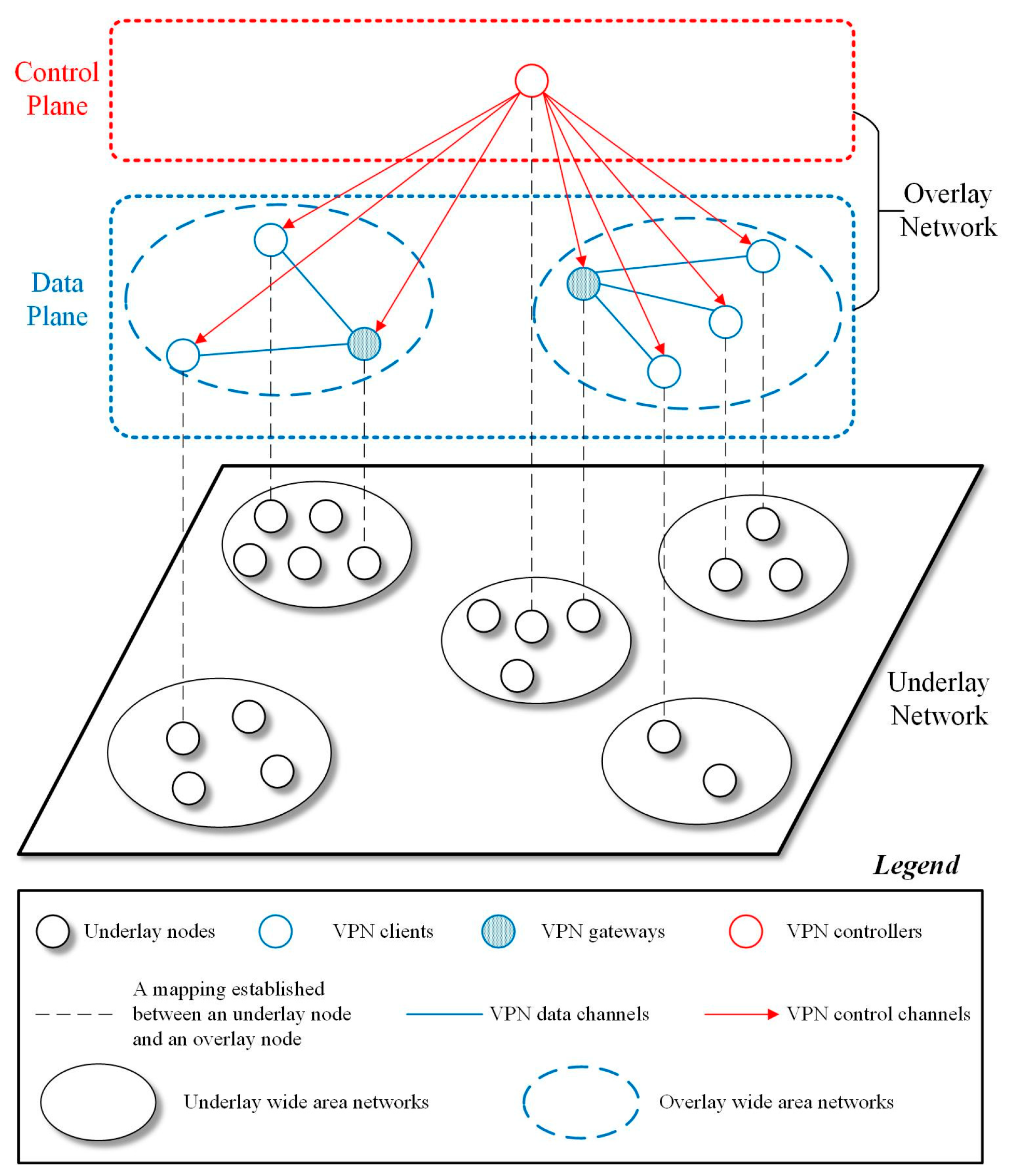
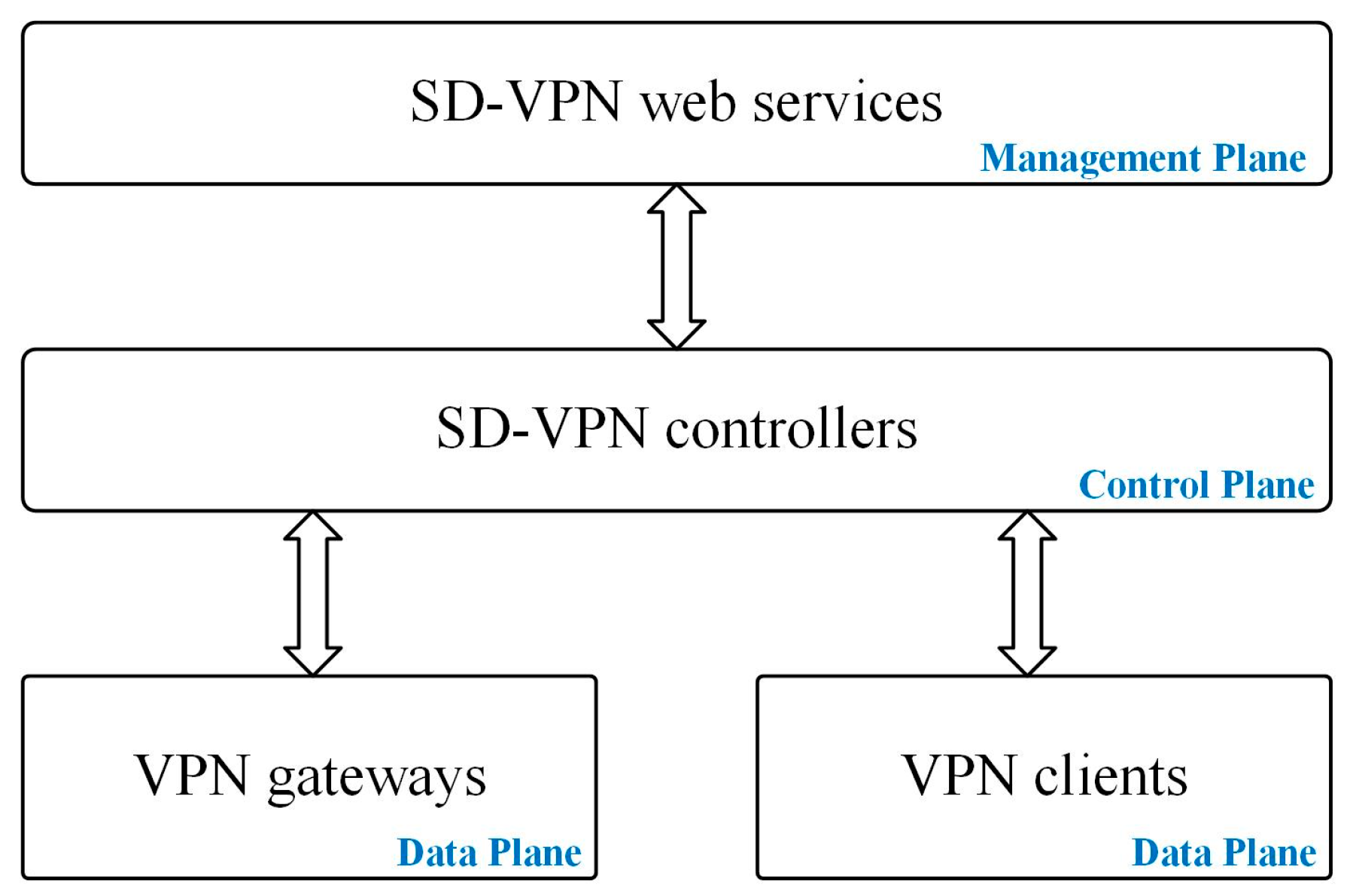
3. Software-Defined Virtual Private Network (SD-VPN)
3.1. Network Model
3.2. Problem Statement
3.3. Evaluating Metrics
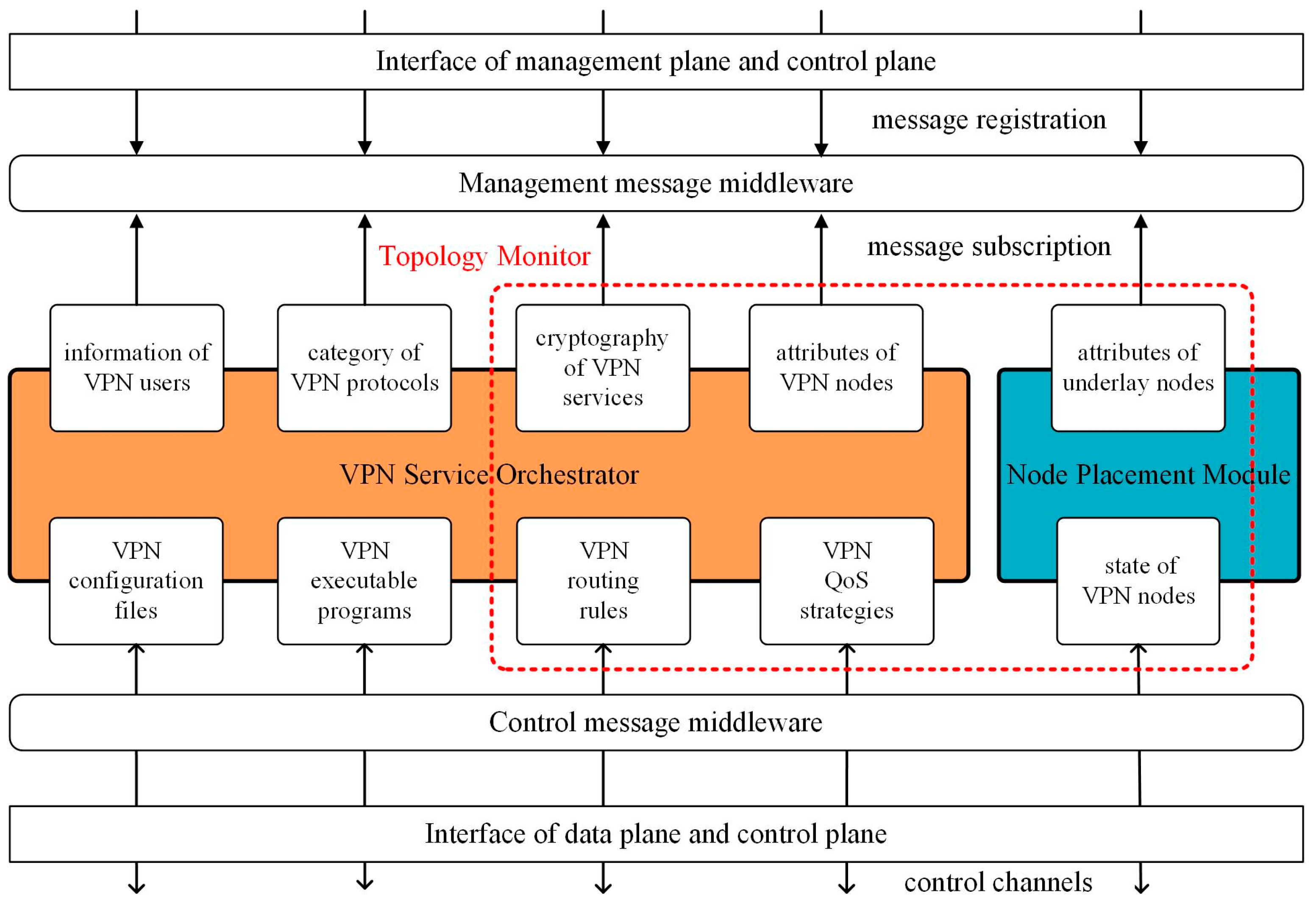
4. SD-VPN Controller
4.1. Modules and Interfaces
4.2. SD-VPN Node Placement
| Algorithm 1 Algorithm of a joint placement of VPN controllers and gateways | |
| Input: The graph of a VPN topology, The VPN nodes include controllers , gateways and clients , The number of VPN nodes of set ; The latency between nodes includes control latency and transmission latency The requirement of control latency and transmission latency Output: | |
| 1 | set |
| 2 | place on demands of users |
| 3 | for each do |
| 4 | find |
| 5 | add the gateway node into set |
| 6 | for each do |
| 7 | find |
| 8 | add the controller node into set |
| 9 | return |
4.3. SD-VPN Service Orchestration
| Algorithm 2 Algorithm of overlay WAN service loading | |
| Input: Graph of an underlay topology, The VPN nodes include controllers , gateways and clients, User-defined SFCs, , , , Output: Graph of an overlay WAN topology, | |
| 1 | for each do |
| 2 | check of |
| 3 | if is invalid or offline then |
| 4 | return; |
| 5 | ; |
| 6 | for each do |
| 7 | ; |
| 8 | for each do |
| 9 | ; |
| 10 | for each do |
| 11 | with results of executing ; |
| 12 | add ; |
| 13 | update of ; |
| 14 | return |
| Algorithm 3 Algorithm of overlay WAN service offloading | |
| Input: Graph of an underlay topology, Graph of an overlay WAN topology, The VPN nodes include controllers , gateways and clients, User-defined SFCs, , , , | |
| 1 | for each do |
| 2 | check of |
| 3 | if is invalid or offline then |
| 4 | return; |
| 5 | for each do |
| 6 | ; |
| 7 | ; |
| 8 | update of ; |
| 9 | for each do |
| 10 | ; |
| 11 | ; |
| 12 | update of ; |
5. SD-VPN System
6. Evaluations
6.1. Experiments and System Tests
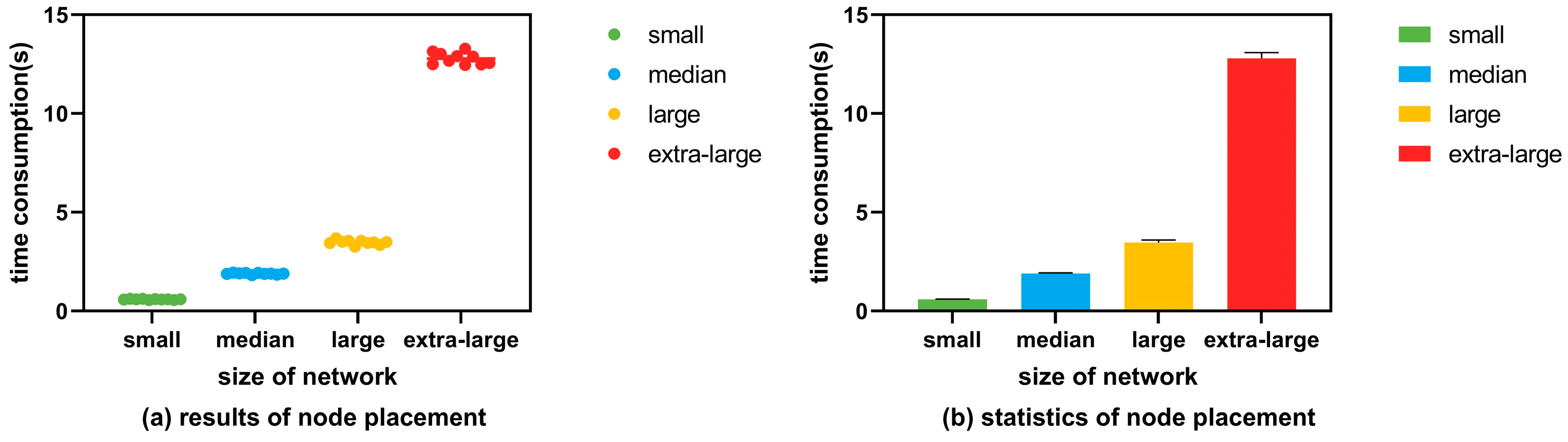
6.2. Evaluations of SD-VPN Node Placement
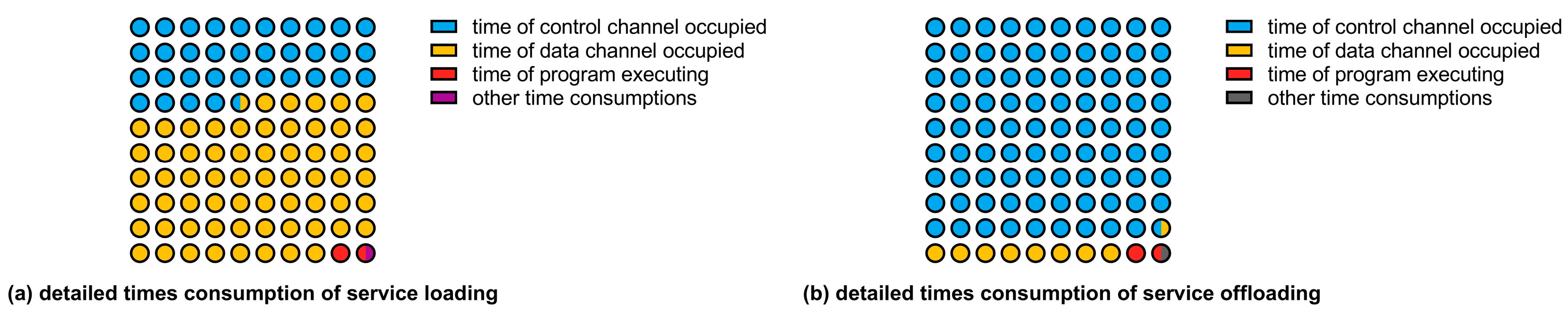
6.3. Evaluations of SD-VPN Service Orchestration
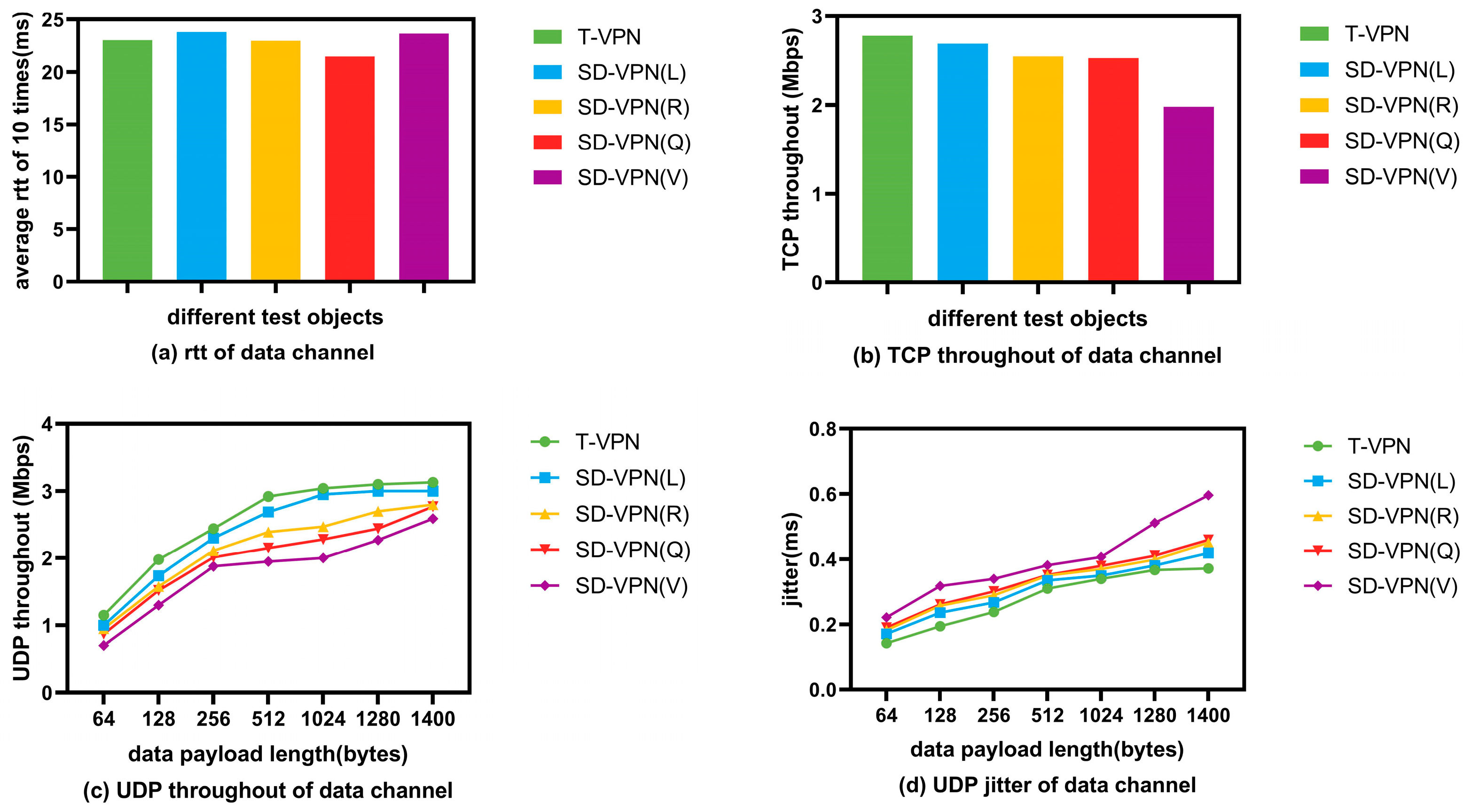
6.4. Evaluations of SD-VPN Data Transmission
6.5. Discussion and Future Work
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Silalahi, L.M.; Amaada, V.; Budiyanto, S.; Simanjuntak, I.U.V.; Rochendi, A.D. Implementation of auto failover on SD-WAN technology with BGP routing method on Fortigate routers at XYZ company. Int. J. Electron. Telecommun. 2024, 70, 5–11. [Google Scholar] [CrossRef]
- Kankipati, C.S.; Kancharla, K.; Rampalli, N.S.; Bandi, S.; Chintala, R.R. The Role of SD-WAN in Cloud Connectivity and Digital Transformation. In Proceedings of the 2023 4th International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 6–8 July 2023; pp. 1169–1173. [Google Scholar]
- Meetei, M.Z. Modeling and Analysis of Cloud Computing Security. In Proceedings of the 2017 IEEE 11th International Conference on Application of Information and Communication Technologies (AICT), Moscow, Russia, 20–22 September 2017; pp. 1–5. [Google Scholar]
- Meetei, M.Z. Mathematical model of security approaches on cloud computing. Int. J. Cloud Comput. 2017, 6, 187–210. [Google Scholar] [CrossRef]
- Soejantono, G.K.; Nashiruddin, M.I.; Hertiana, S.N.; Nugraha, M.A. Performance Evaluation of SD-WAN Deployment for XYZ Enterprise Company in Indonesia. In Proceedings of the 2021 IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Online, 27–30 October 2021; pp. 0311–0316. [Google Scholar]
- Troia, S.; Mazzara, M.; Zorello, L.M.M.; Pattavina, A. Resiliency in SD-WAN with eBPF monitoring: Municipal network and video streaming use cases. In Proceedings of the 2021 17th International Conference on the Design of Reliable Communication Networks (DRCN), Milan, Italy, 19–22 April 2021; pp. 1–3. [Google Scholar]
- Asif, R.; Ghanem, K. AI secured SD-WAN architecture as a latency critical IoT enabler for 5G and beyond communications. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; pp. 1–6. [Google Scholar]
- Navarro, A.; Canonico, R.; Botta, A. Software Defined Wide Area Networks: Current Challenges and Future Perspectives. In Proceedings of the 2023 IEEE 9th International Conference on Network Softwarization (NetSoft), Madrid, Spain, 19–23 June 2023; pp. 350–353. [Google Scholar]
- Yalda, K.G.; Hamad, D.J.; Ţăpuş, N. A survey on Software-defined Wide Area Network (SD-WAN) architectures. In Proceedings of the 2022 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 9–11 June 2022; pp. 1–5. [Google Scholar]
- Lee, S.; Chan, K.Y.; Chen, T.Y. Design and implementation of an sd-wan vpn system to support multipath and multi-wan-hop routing in the public internet. Authorea Prepr. 2023. [Google Scholar] [CrossRef]
- Azwee, K.; Alkhattali, M.; Dow, M. Exploring the Effectiveness of VPN Architecture in Enhancing Network Security for Mobile Networks: An Investigation Study. Int. J. Netw. Secur. Its Appl. 2023, 15, 33–40. [Google Scholar] [CrossRef]
- Barguil, S.; Lopez, V.; Manta-Caro, C.; De Lerma, A.M.L.; De Dios, O.G.; Echeverry, E.; Fernandez-Palacios, J.P.; Karvonen, J.; Kemppainen, J.; Maya, N.; et al. Field Trial of Programmable L3 VPN Service Deployment Using SDN-Based Multi-domain Service Provisioning over IP/Optical Networks. IEEE Netw. 2021, 35, 217–224. [Google Scholar] [CrossRef]
- Akinsanya, M.O.; Ekechi, C.C.; Okeke, C.D. Virtual private networks (vpn): A conceptual review of security protocols and their application in modern networks. Eng. Sci. Technol. J. 2024, 5, 1452–1472. [Google Scholar] [CrossRef]
- Antoniuk, J.; Plechawska-Wójcik, M. Comparative analysis of VPN protocols: Comparative analysis of VPN protocols. J. Comput. Sci. Inst. 2023, 27, 138–144. [Google Scholar] [CrossRef]
- Fu, C.; Wang, B.; Wang, W.; Mu, R.; Sun, Y.; Xin, G.; Zhang, Y. A Generic High-Performance Architecture for VPN Gateways. Electronics 2024, 13, 2031. [Google Scholar] [CrossRef]
- Raj, J.R.; Srinivasulu, S. Design of IoT based VPN gateway for home network. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 561–564. [Google Scholar]
- Arashloo, M.T.; Shirshov, P.; Gandhi, R.; Lu, G.; Yuan, L. A scalable VPN gateway for multi-tenant cloud services. ACM SIGCOMM Comput. Commun. Rev. 2018, 48, 49–55. [Google Scholar] [CrossRef]
- Elizabeth, S.J.M.; Xavier, J.P.F.; Rubén, P.C.M. SD-WAN Software defined networking using DMVPN for corporate enterprises. In Proceedings of the 2023 18th Iberian Conference on Information Systems and Technologies (CISTI), Aveiro, Portugal, 20–23 June 2023; pp. 1–6. [Google Scholar]
- Mostafaei, H.; Lospoto, G.; Di Lallo, R.; Rimondini, M.; Di Battista, G. A framework for multi-provider virtual private networks in software-defined federated networks. Int. J. Netw. Manag. 2020, 30, e2116. [Google Scholar] [CrossRef]
- Mirkhanzadeh, B.; Taheri, N.; Khorsandi, S. SDxVPN: A software-defined solution for VPN service providers. In Proceedings of the NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 180–188. [Google Scholar]
- Lospoto, G.; Rimondini, M.; Vignoli, B.G.; Di Battista, G. Rethinking virtual private networks in the software-defined era. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 379–387. [Google Scholar]
- Bringhenti, D.; Sisto, R.; Valenza, F. Automating VPN configuration in computer networks. IEEE Trans. Dependable Secur. Comput. 2024; ahead of print. [Google Scholar]
- Juma, M.; Monem, A.A.; Shaalan, K. Hybrid end-to-end VPN security approach for smart IoT objects. J. Netw. Comput. Appl. 2020, 158, 102598. [Google Scholar] [CrossRef]
- Gentile, A.F.; Fazio, P.; Miceli, G. A Survey on the Implementation and Management of Secure Virtual Private Networks (VPNs) and Virtual LANs (VLANs) in Static and Mobile Scenarios. Telecom 2021, 2, 430–445. [Google Scholar] [CrossRef]
- Fu, C.L.; He, Q.G.; Wang, B.L.; Han, X.X. A Communication Supportable Generic Model for Mobile VPN on Android OS. In Proceedings of the 2016 IEEE Symposium on Computers and Communication (ISCC), Messina, Italy, 27–30 June 2016; pp. 1039–1046. [Google Scholar]
- Kjorveziroski, V.; Bernad, C.; Gilly, K.; Filiposka, S. Full-mesh VPN performance evaluation for a secure edge-cloud continuum. Softw. Pract. Exp. 2024, 54, 1543–1564. [Google Scholar] [CrossRef]
- Chua, C.H.; Ng, S.C. Open-Source VPN Software: Performance Comparison for Remote Access. In Proceedings of the 5th International Conference on Information Science and Systems, Beijing, China, 24–27 November 2022; pp. 29–34. [Google Scholar]
- Pudelko, M.; Emmerich, P.; Gallenmüller, S.; Carle, G. Performance analysis of VPN gateways. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 23–25 June 2020; pp. 325–333. [Google Scholar]
- Wu, Z.; Xiao, M. Performance evaluation of VPN with different network topologies. In Proceedings of the 2019 IEEE 2nd International Conference on Electronics Technology (ICET), Chengdu, China, 10–13 May 2019; pp. 51–55. [Google Scholar]
- Guo, Z.; Dou, S.; Jiang, W.; Xia, Y. Toward Improved Path Programmability Recovery for Software-Defined WANs Under Multiple Controller Failures. IEEE/ACM Trans. Netw. 2023, 32, 143–158. [Google Scholar] [CrossRef]
- Scarpitta, C.; Sidoretti, G.; Mayer, A.; Salsano, S.; Abdelsalam, A.; Filsfils, C. High Performance Delay Monitoring for SRv6 Based SD-WANs. IEEE Trans. Netw. Serv. Manag. 2023, 21, 1067–1081. [Google Scholar] [CrossRef]
- Altheide, F.; Buttgereit, S.; Rossberg, M. Increasing Resilience of SD-WAN by Distributing the Control Plane [Extended Version]. IEEE Trans. Netw. Serv. Manag. 2024. [Google Scholar] [CrossRef]
- Zhang, P.; He, F.; Zhang, H.; Hu, J.; Huang, X.; Wang, J.; Yin, X.; Zhu, H.; Li, Y. Real-time malicious traffic detection with online isolation forest over sd-wan. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2076–2090. [Google Scholar] [CrossRef]
- Yiliyaer, S.; Kim, Y. Secure access service edge: A zero trust-based framework for accessing data securely. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; pp. 0586–0591. [Google Scholar]
- Lembke, J.; Ravi, S.; Roman, P.L.; Eugster, P. Secure and reliable network updates. ACM Trans. Priv. Secur. 2022, 26, 1–41. [Google Scholar] [CrossRef]
- Henrici, D.; Wischhof, L. Site Connectivity with Towalink–Implementing an Open Source “SD-WAN Light”. In Proceedings of the 2022 30th Telecommunications Forum (TELFOR), Belgrade, Serbia, 15–16 November 2022; pp. 1–4. [Google Scholar]
- Lei, W.C.; Chang, Y.P.; Chou, L.D. MINIWAN: A new framework for simulating multi-segment network topology based on mininet. In Proceedings of the 2022 13th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 19–21 October 2022; pp. 105–107. [Google Scholar]
- Scarpitta, C.; Ventre, P.L.; Lombardo, F.; Salsano, S.; Blefari-Melazzi, N. EveryWAN-an open-source SD-WAN solution. In Proceedings of the 2021 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Mauritius, Mauritius, 7–8 October 2021; pp. 1–7. [Google Scholar]
- Dou, S.; Qi, L.; Yao, C.; Guo, Z. Exploring the impact of critical programmability on controller placement for software-defined wide area networks. IEEE/ACM Trans. Netw. 2023, 31, 2575–2588. [Google Scholar] [CrossRef]
- Qi, L.; Dou, S.; Guo, Z.; Li, C.; Li, Y.; Zhu, T. Low control latency SD-WANs for metaverse. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems Workshops (ICDCSW), Bologna, Italy, 10–13 July 2022; pp. 266–271. [Google Scholar]
- Adekoya, O.; Aneiba, A. An adapted nondominated sorting genetic algorithm iii (nsga-iii) with repair-based operator for solving controller placement problem in software-defined wide area networks. IEEE Open J. Commun. Soc. 2022, 3, 888–901. [Google Scholar] [CrossRef]
- Chakraborty, A.; Misra, S.; Maiti, J. Mobility-Aware Controller Orchestration in Multi-Tier Service-Oriented Architecture for IoT. IEEE Trans. Veh. Technol. 2021, 71, 1820–1831. [Google Scholar] [CrossRef]
- Cai, N.; Han, Y.; Ben, Y.; An, W.; Xu, Z. An effective load balanced controller placement approach in software-defined WANs. In Proceedings of the MILCOM 2019-2019 IEEE Military Communications Conference (MILCOM), Norfolk, VA, USA, 12–14 November 2019. [Google Scholar]
- Mojez, H.; Bidgoli, A.M.; Javadi, H.H.S. Star capacity-aware latency-based next controller placement problem with considering single controller failure in software-defined wide-area networks. J. Supercomput. 2022, 78, 13205–13244. [Google Scholar] [CrossRef]
- Fan, C.; Zhang, X.; Zhao, Y.; He, Y.; Yang, Y. Dynamic relay node selection and routing for cloud-native Software Defined WANs. Comput. Netw. 2024, 241, 110219. [Google Scholar] [CrossRef]
- Jiang, Y.; Su, L.; Feng, W.; Ge, N. Congestion-Aware Algorithms for Service Function Chaining in Software-Defined Wide Area Networks. In Proceedings of the ICC 2023-IEEE International Conference on Communications, Rome, Italy, 28 May–1 June 2023; pp. 1086–1092. [Google Scholar]
- Leivadeas, A.; Pitaev, N.; Falkner, M. Analyzing the performance of SD-WAN enabled service function chains across the globe with AWS. In Proceedings of the 2023 ACM/SPEC International Conference on Performance Engineering, Coimbra, Portugal, 15–19 April 2023; pp. 125–135. [Google Scholar]
- Zhang, Y.; Xu, C.; Muntean, G.M. Revenue-Oriented Service Offloading through Fog-Cloud Collaboration in SD-WAN. In Proceedings of the GLOBECOM 2022-2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 5753–5758. [Google Scholar]
- Perez, R.; Zabala, A.; Banchs, A. Alviu: An intent-based SD-WAN orchestrator of network slices for enterprise networks. In Proceedings of the 2021 IEEE 7th International Conference on Network Softwarization (NetSoft), Tokyo, Japan, 28 June–2 July 2021; pp. 211–215. [Google Scholar]
- Koné, B.; Kora, A.D. Management and orchestration for network function virtualization in a VoIP testbed: A multi-domain case. In Proceedings of the 2021 44th International Conference on Telecommunications and Signal Processing (TSP), Virtual, 26–28 July 2021; pp. 372–376. [Google Scholar]
- De Sousa, N.F.S.; Perez, D.A.L.; Rosa, R.V.; Santos, M.A.; Rothenberg, C.E. Network service orchestration: A survey. Comput. Commun. 2019, 142, 69–94. [Google Scholar] [CrossRef]
- Iddalagi, P.; Mishra, A. Impact Analysis of Tunnel Probing Protocol on SD-WAN’s Mainstream Traffic. In Proceedings of the 2023 15th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 3–8 January 2023; pp. 252–259. [Google Scholar]


| Categories | Symbols | Descriptions |
|---|---|---|
| user-defined SFCs | Attributes of VPN nodes | |
| Information on VPN users and requirements for QoS | ||
| Category of VPN protocols | ||
| C | Cryptography of VPN services | |
| automate-generated SFCs | F | VPN configuration files |
| VPN executable programs | ||
| VPN routing rules, including Generic Routing Encapsulation (GRE) tunnels, static routing rules, and Network Address Translation (NAT) forwarding rules | ||
| VPN QoS strategies |
| Names | Parameters | Descriptions |
|---|---|---|
| MacBook Pro | CPU | 2.3 GHz 8 cores Intel Core i9 |
| GPU | Radeon Pro 560X 4 GB, Intel UHD Graphics 630 1536 MB | |
| RAM | 16 GB 2400 MHz DDR4 | |
| OS | macOS 14.4.1 (23E224) |
| Parameters | Small | Medium | Large | Extra-Large |
|---|---|---|---|---|
| 30 | 100 | 500 | 1000 | |
| 3 | 10 | 20 | 50 | |
| 1 | 3 | 5 | 10 | |
| 20 ms | 30 ms | 30 ms | 50 ms | |
| 20 ms | 30 ms | 30 ms | 50 ms |
| Names | Parameters | Descriptions |
|---|---|---|
| Cloud server | CPU | Intel (R) Xeon(R) CPU E5-2680 v3 @ 2.50 GHz |
| RAM | 1G | |
| NIC | Red Hat, Inc Virtio network device | |
| OS | Linux version 3.10.0-514.16.1.el7.x86_64(Red Hat 4.8.5-11) | |
| Gateway device | CPU | Intel(R) Atom (TM) CPU D525 @1.80 GHz |
| RAM | 1G | |
| NIC | Intel Corporation 82583 V Gigabit Network Connection | |
| OS | Linux version 3.10.0-514.16.1.el7.x86_64(Red Hat 4.8.5-11) |
| Symbols | Descriptions |
|---|---|
| T-VPN | The SD-VPN is deployed as a traditional VPN without controllers |
| SD-VPN(L) | The SD-VPN controller is at leisure. |
| SD-VPN(R) | The SD-VPN controller is busy with routing-related transactions. |
| SD-VPN(Q) | The SD-VPN controller is busy with QoS-related transactions. |
| SD-VPN(V) | The SD-VPN controller is busy with VPN-related transactions. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fu, C.; Wang, B.; Liu, H.; Wang, W. Software-Defined Virtual Private Network for SD-WAN. Electronics 2024, 13, 2674. https://doi.org/10.3390/electronics13132674
Fu C, Wang B, Liu H, Wang W. Software-Defined Virtual Private Network for SD-WAN. Electronics. 2024; 13(13):2674. https://doi.org/10.3390/electronics13132674
Chicago/Turabian StyleFu, Chunle, Bailing Wang, Hongri Liu, and Wei Wang. 2024. "Software-Defined Virtual Private Network for SD-WAN" Electronics 13, no. 13: 2674. https://doi.org/10.3390/electronics13132674
APA StyleFu, C., Wang, B., Liu, H., & Wang, W. (2024). Software-Defined Virtual Private Network for SD-WAN. Electronics, 13(13), 2674. https://doi.org/10.3390/electronics13132674





