Steganography in QR Codes—Information Hiding with Suboptimal Segmentation
Abstract
1. Introduction
Literature Review
2. Materials and Methods
2.1. Background: QR Codes
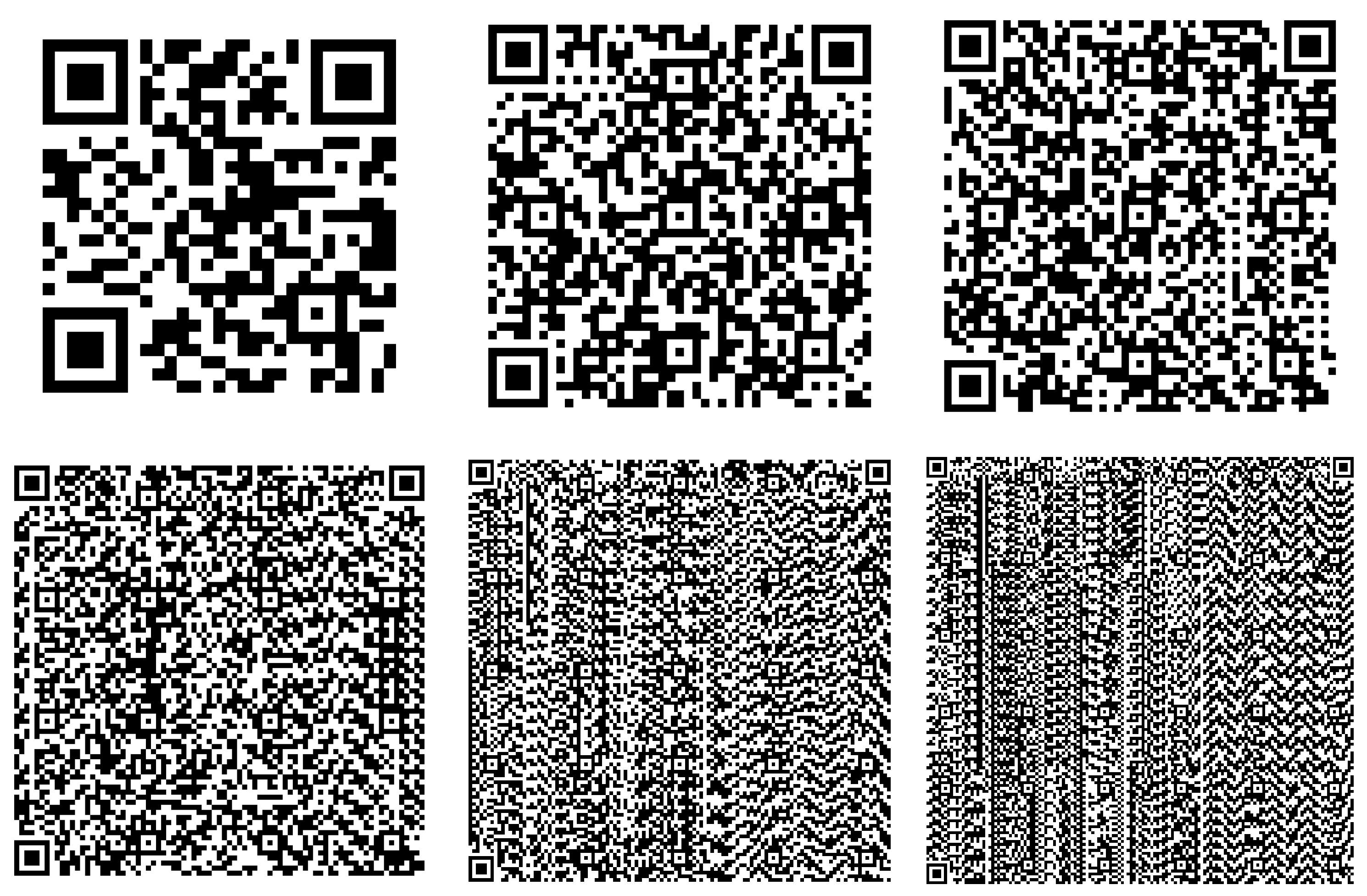
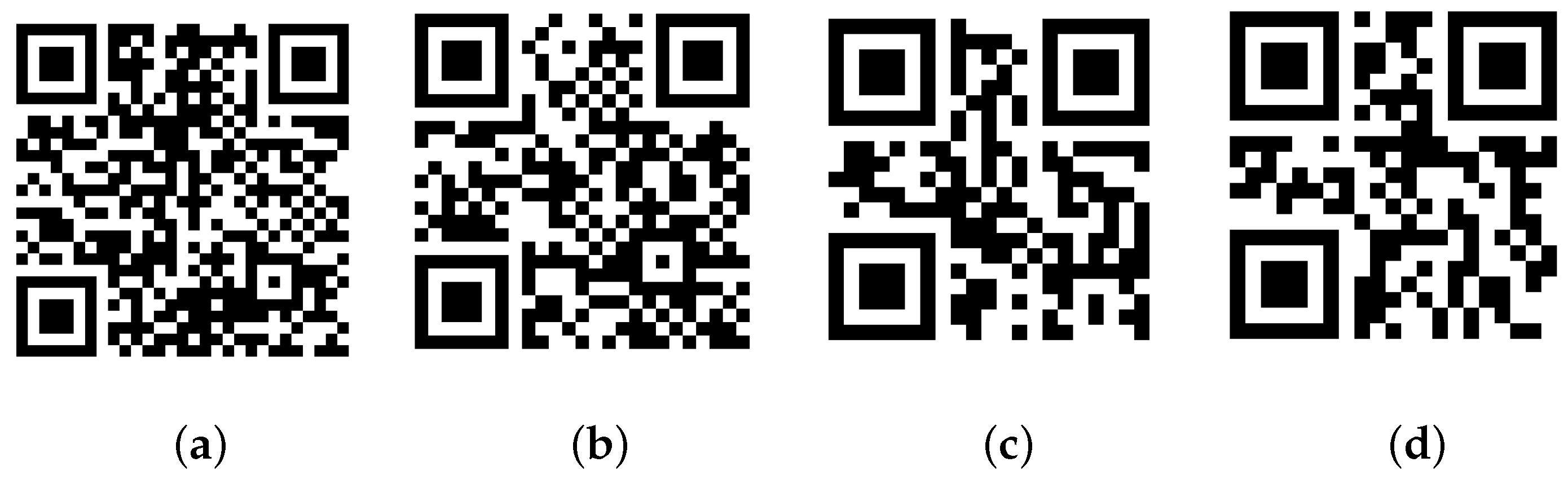
2.2. Steganographic Method of Suboptimal Segmentation
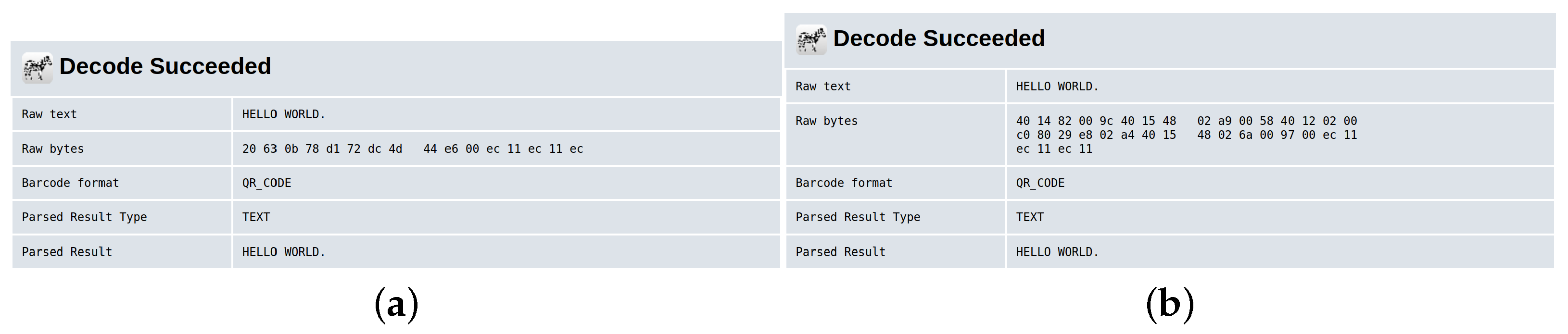
| Segment Content | Segment Type | Encoded Bit |
| H | byte | 1 |
| E | alphanumeric | 0 |
| L | alphanumeric | 0 |
| L | alphanumeric | 0 |
| O | alphanumeric | 0 |
| (space) | byte | 1 |
| W | alphanumeric | 0 |
| O | byte | 1 |
| R | byte | 1 |
| L | alphanumeric | 0 |
| D | alphanumeric | 0 |
| . | byte | 1 |
| Algorithm 1: Embedding algorithm |
 |
| Algorithm 2: Extracting algorithm |
 |
3. Results
4. Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| QR code | quick response code |
Appendix A. List of Tested Online QR Decoders (Accessed on 25 March 2024)
References
- Koptyra, K.; Ogiela, M. An Efficient Steganographic Protocol for WebP Files. Appl. Sci. 2023, 13, 12404. [Google Scholar] [CrossRef]
- Koptyra, K.; Ogiela, M. Steganography in IoT: Information Hiding with Joystick and Touch Sensors. Sensors 2023, 23, 3288. [Google Scholar] [CrossRef] [PubMed]
- Alexey, T. On Double-Sided QR-Codes. 2019. Available online: https://www.researchgate.net/publication/331165555_On_Double-Sided_QR-Codes (accessed on 25 March 2024).
- Chow, Y.; Susilo, W.; Yang, G.; Phillips, J.G.; Pranata, I.; Barmawi, A. Exploiting the error correction mechanism in QR codes for secret sharing. In Proceedings of the Lecture Notes in Computer Science, Information Security and Privacy: 21st Australasian Conference, ACISP 2016, Proceedings, Part I, Melbourne, Australia, 4–6 July 2016; Volume 9722, pp. 409–425. [Google Scholar]
- Chow, Y.W.; Susilo, W.; Baek, J. Covert QR Codes: How to Hide in the Crowd. In International Conference on Information Security Practice and Experience; Springer International Publishing: Cham, Switzerland, 2017; pp. 678–693. [Google Scholar] [CrossRef]
- Cheng, Y.; Fu, Z.; Yu, B. Improved Visual Secret Sharing Scheme for QR Code Applications. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2393–2403. [Google Scholar] [CrossRef]
- Lin, P.Y.; Chen, Y.H.; Lu, E.J.L.; Chen, P.J. Secret Hiding Mechanism Using QR Barcode. In Proceedings of the 2013 International Conference on Signal-Image Technology & Internet-Based Systems (SITIS), Kyoto, Japan, 2–5 December 2013; pp. 22–25. [Google Scholar] [CrossRef]
- Bui, T.V.; Vu, N.K.; Nguyen, T.T.; Echizen, I.; Nguyen, T.D. Robust Message Hiding for QR Code. In Proceedings of the 2014 Tenth International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Kitakyushu, Japan, 27–29 August 2014; pp. 520–523. [Google Scholar] [CrossRef]
- Huang, P.C.; Chang, C.C.; Li, Y.H.; Liu, Y. Efficient QR Code Secret Embedding Mechanism Based on Hamming Code. IEEE Access 2020, 8, 86706–86714. [Google Scholar] [CrossRef]
- Chiang, Y.J.; Lin, P.Y.; Wang, R.Z.; Chen, Y.H. Blind QR Code Steganographic Approach Based upon Error Correction Capability. KSII Trans. Internet Inf. Syst. 2013, 7, 2527–2543. [Google Scholar] [CrossRef]
- Huang, P.C.; Li, Y.H.; Chang, C.C.; Liu, Y. Efficient Scheme for Secret Hiding in QR Code by Improving Exploiting Modification Direction. KSII Trans. Internet Inf. Syst. 2018, 12, 2348–2365. [Google Scholar] [CrossRef]
- Huang, P.C.; Chang, C.C.; Li, Y.H.; Liu, Y. High-payload secret hiding mechanism for QR codes. Multimed. Tools Appl. 2019, 78, 22331–22350. [Google Scholar] [CrossRef]
- Teraura, N.; Sakurai, K. Information Hiding in Subcells of a Two-Dimensional Code. In Proceedings of the 1st IEEE Global Conference on Consumer Electronics 2012, GCCE, Tokyo, Japan, 2–5 October 2012; pp. 652–656. [Google Scholar] [CrossRef]
- Uttarwar, S.V.; Bagade, A.M. Two-Level QR Code for Secured Message Sharing and Document Authentication. Int. J. Adv. Res. Comput. Commun. Eng. 2017, 6, 508–511. [Google Scholar] [CrossRef]
- Rani, M.M.S.; Euphrasia, K.R. Data Security through QR Code Encryption and Steganography. Adv. Comput. Int. J. (ACIJ) 2016, 7. [Google Scholar] [CrossRef]
- Chen, W.Y.; Wang, J.W. Nested image steganography scheme using QR-barcode technique. Opt. Eng. 2009, 48, 057004. [Google Scholar] [CrossRef]
- Chung, C.H.; Chen, W.Y.; Tu, C.M. Image hidden technique using QR-Barcode. In Proceedings of the Fifth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kyoto, Japan, 12–14 September 2009; pp. 522–525. [Google Scholar] [CrossRef]
- Dey, S.; Mondal, K.; Nath, J.; Nath, A. Advanced Steganography Algorithm Using Randomized Intermediate QR Host Embedded with Any Encrypted Secret Message: ASA_QR Algorithm. Int. J. Mod. Educ. Comput. Sci. (IJMECS) 2012, 4, 59–67. [Google Scholar] [CrossRef]
- Wu, W.C.; Lin, Z.W.; Wong, W.T. Application of QR-Code Steganography Using Data Embedding Technique. In Information Technology Convergence, Lecture Notes in Electrical Engineering; Springer: Amsterdam, The Netherlands, 2013; Volume 253, pp. 597–605. [Google Scholar] [CrossRef]
- Koptyra, K.; Ogiela, M. Information Hiding in QR Codes using Segment Manipulation. In Proceedings of the 2024 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Biarritz, France, 11–15 March 2024; pp. 397–400. [Google Scholar] [CrossRef]
- ISO/IEC 18004:2015; Information Technology—Automatic Identification and Data Capture Techniques—QR Code Bar Code Symbology Specification. International Organization for Standardization: Geneva, Switzerland, 2015.
- Ricson, E. Qr Code Usage Statistics 2022–2023: 433% Scan Increase and 438% Generation Boost. 2024. Available online: https://www.qrcode-tiger.com/qr-code-statistics-2022-q1 (accessed on 25 March 2024).
- Koptyra, K.; Ogiela, M.R. Lightweight and efficient approach for multi-secret steganography. Int. J. Embed. Syst. 2020, 12, 434–440. [Google Scholar] [CrossRef]
- Elhanashi, A.; Dini, P.; Saponara, S.; Zheng, Q. Integration of Deep Learning into the IoT: A Survey of Techniques and Challenges for Real-World Applications. Electronics 2023, 12, 4925. [Google Scholar] [CrossRef]
- Koptyra, K.; Ogiela, M.R. Multiply information coding and hiding using fuzzy vault. Soft Comput. 2019, 23, 4357–4366. [Google Scholar] [CrossRef]





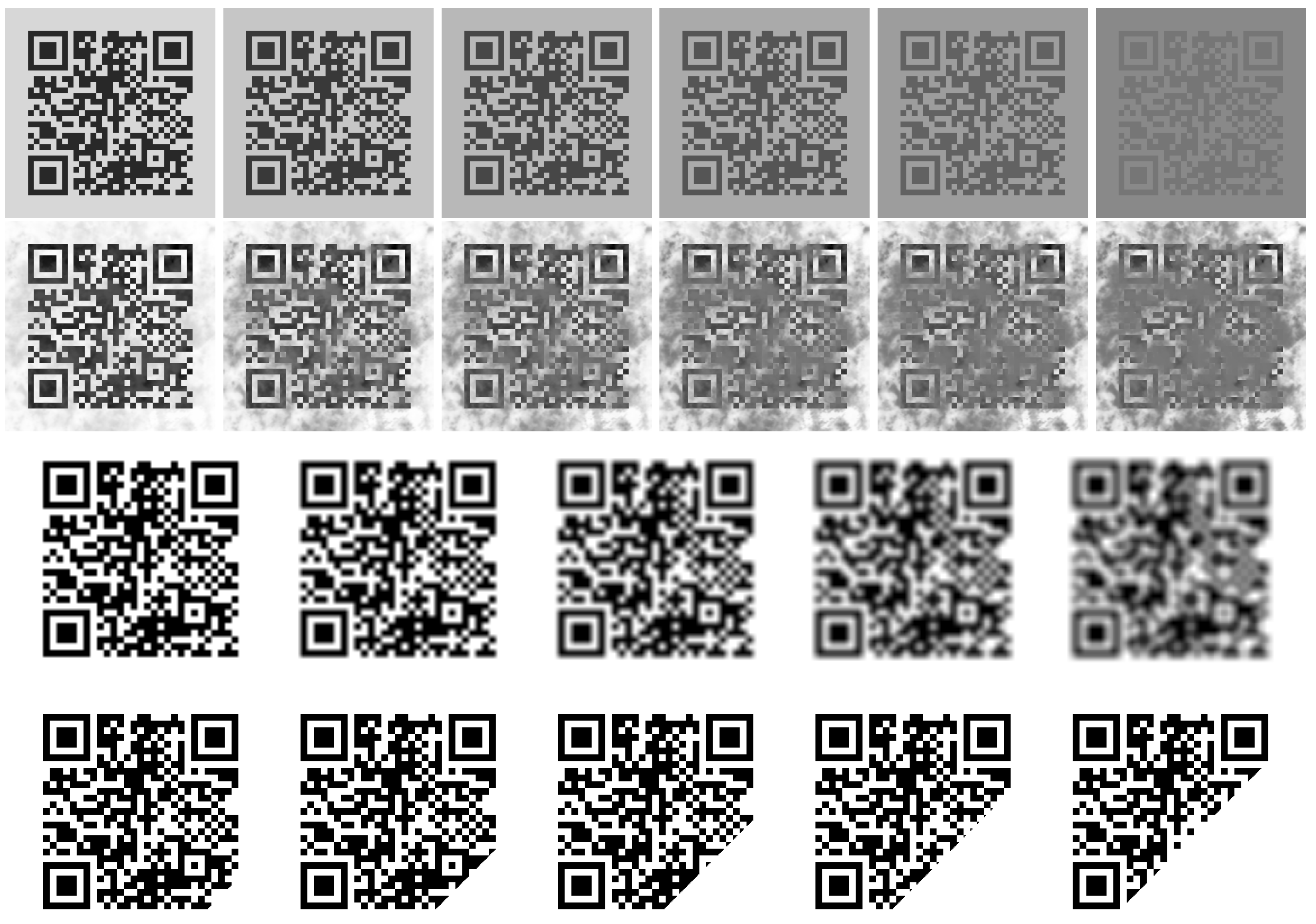
| Stego Code | Pure Code | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Contrast | T1 | −30 | −45 | −60 | −75 | −90 | −115 | −30 | −45 | −60 | −75 | −90 | −115 |
| T2 | −30 | −45 | −60 | −75 | −90 | −115 | −30 | −45 | −60 | −75 | −90 | −115 | |
| T3 | −30 | −45 | −60 | −75 | −90 | −115 | −30 | −45 | −60 | −75 | −90 | −115 | |
| Noise | T1 | 50% | 100% | 150% | 200% | 250% | 300% | 50% | 100% | 150% | 200% | 250% | 300% |
| T2 | 50% | 100% | 150% | 200% | 250% | 300% | 50% | 100% | 150% | 200% | 250% | 300% | |
| T3 | 50% | 100% | 150% | 200% | 250% | 300% | 50% | 100% | 150% | 200% | 250% | 300% | |
| Blur | T1 | 1 | 2 | 3 | 4 | 5 | 1 | 2 | 3 | 4 | 5 | ||
| T2 | 1 | 2 | 3 | 4 | 5 | 1 | 2 | 3 | 4 | 5 | |||
| T3 | 1 | 2 | 3 | 4 | 5 | 1 | 2 | 3 | 4 | 5 | |||
| Cropping * | T1 | 1% | 5% | 10% | 20% | 30% | 1% | 5% | 10% | 20% | 30% | ||
| T2 | 1% | 5% | 10% | 20% | 30% | 1% | 5% | 10% | 20% | 30% | |||
| T3 | 1% | 5% | 10% | 20% | 30% | 1% | 5% | 10% | 20% | 30% | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koptyra, K.; Ogiela, M.R. Steganography in QR Codes—Information Hiding with Suboptimal Segmentation. Electronics 2024, 13, 2658. https://doi.org/10.3390/electronics13132658
Koptyra K, Ogiela MR. Steganography in QR Codes—Information Hiding with Suboptimal Segmentation. Electronics. 2024; 13(13):2658. https://doi.org/10.3390/electronics13132658
Chicago/Turabian StyleKoptyra, Katarzyna, and Marek R. Ogiela. 2024. "Steganography in QR Codes—Information Hiding with Suboptimal Segmentation" Electronics 13, no. 13: 2658. https://doi.org/10.3390/electronics13132658
APA StyleKoptyra, K., & Ogiela, M. R. (2024). Steganography in QR Codes—Information Hiding with Suboptimal Segmentation. Electronics, 13(13), 2658. https://doi.org/10.3390/electronics13132658







