Handling Efficient VNF Placement with Graph-Based Reinforcement Learning for SFC Fault Tolerance
Abstract
1. Introduction
- We formulated physical resources in MEC to obtain the virtual resource capability by leveraging a GCN to gather the states. The node cluster of VNF management and orchestration in user requests were used to interact with the GCN. It represents all the VNF deployments as nodes, and the message-passing method consists of feature nodes and links.
- The utilization of Markov decision process (MDP) formulation and a DRL algorithm was leveraged to learn an optimal network resource adjustment policy adaptively.
- This article proposed GRL-SFT, which combines GNN-DQN for SFC deployment within NFV architecture. The GRL-SFT framework was implemented in a simulation environment to conduct the experiment for evaluating the performance in terms of cumulative reward, delay, acceptance ratio, failure, and restoration ratio when processing different chain sizes and user request rates in different topology sizes.
2. Background Studies
2.1. VNF Placement Solution
2.2. Graph-Based Reinforcement Learning for SFC
2.3. SFC Fault Tolerance Awareness
3. Problem and Formulation
3.1. Substrate Network Model
3.2. Service Function Chaining Request Models
3.3. Problem Formulation
- (1)
- VNF placement: place the VNFs in the SFC request and properly install them onto the physical node.
- (2)
- VL selection: ensure the mapping of the links is consistent and proper between virtual and physical links for ordering the VNFs.
- (1)
- The processing delay of VNF instances for hosting on the physical node.
- (2)
- The propagation delay of data transportation over a physical link.
3.4. Markov Decision Process Models
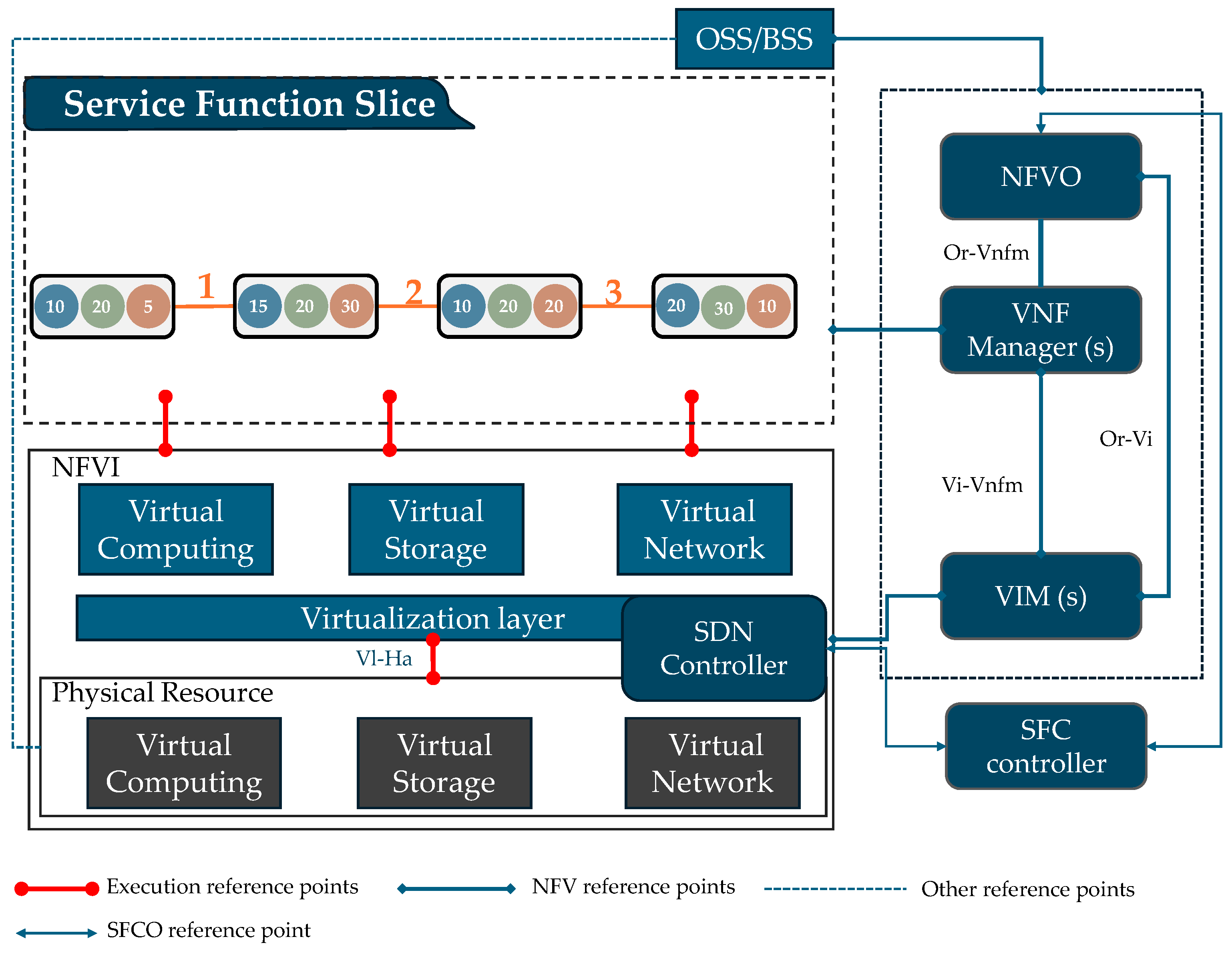
4. Proposed Network Scenario
4.1. Configuring SFC Execution Based on GNN-DRL Approach
- (1)
- The initialization of all the network parameters is configured as the first communication step in the SFC request, in which SFC inspects the packets in the control layer to consider two processing steps, which instantiates the SFC request or checks the available SFC requests. By considering this processing flow, the controller checks the resource based on the service criteria containing the information that used to be utilized or previously applied. On the other hand, besides optimizing the resource allocation of the SFC list requested, a GNN is implemented to perform a feature exaction of a node and the correlation of links in which the state transition of the adjacency matrix is multiple of the hidden state. The hidden state is the annotation matrix where node label vectors are set, including network topologies and ingress messages.
- (2)
- The NFVO is used to conduct the extraction, initialize VNFFG, and define the specific order of the SFs. After the NFVO gathers information averaging the degree to which the CPU load, memory, and capacity utilization increases or decreases from the threshold value, virtual network function management (VNFM) defines the procedure of instantiating or deleting the VNFs due to SFC requests and acknowledges the NFVO.
- (3)
- Along with the GNN embedding process, which realizes a distributed identified information input representation vector that may represent many independent factors, the embedding process is applied with a VNF vector and the node encoding/decoding (considering the final representation of the encoder and accomplishing the final step to process VNFs either on node selection or removal) of input VNF types of vectors.
- (4)
- The NFV creates a new record of the chain identifier for operating with additional resource migration, update, and deletions; then, sends it to the SFC orchestrator (SFCO). The SFCO creates a service function path (SFP) flow rule for a new SDN controller routing table. Finally, the SDN adds flow entry, acknowledges updates into the flow table of layer 3, and makes the SFCO conscious of the successful operation.
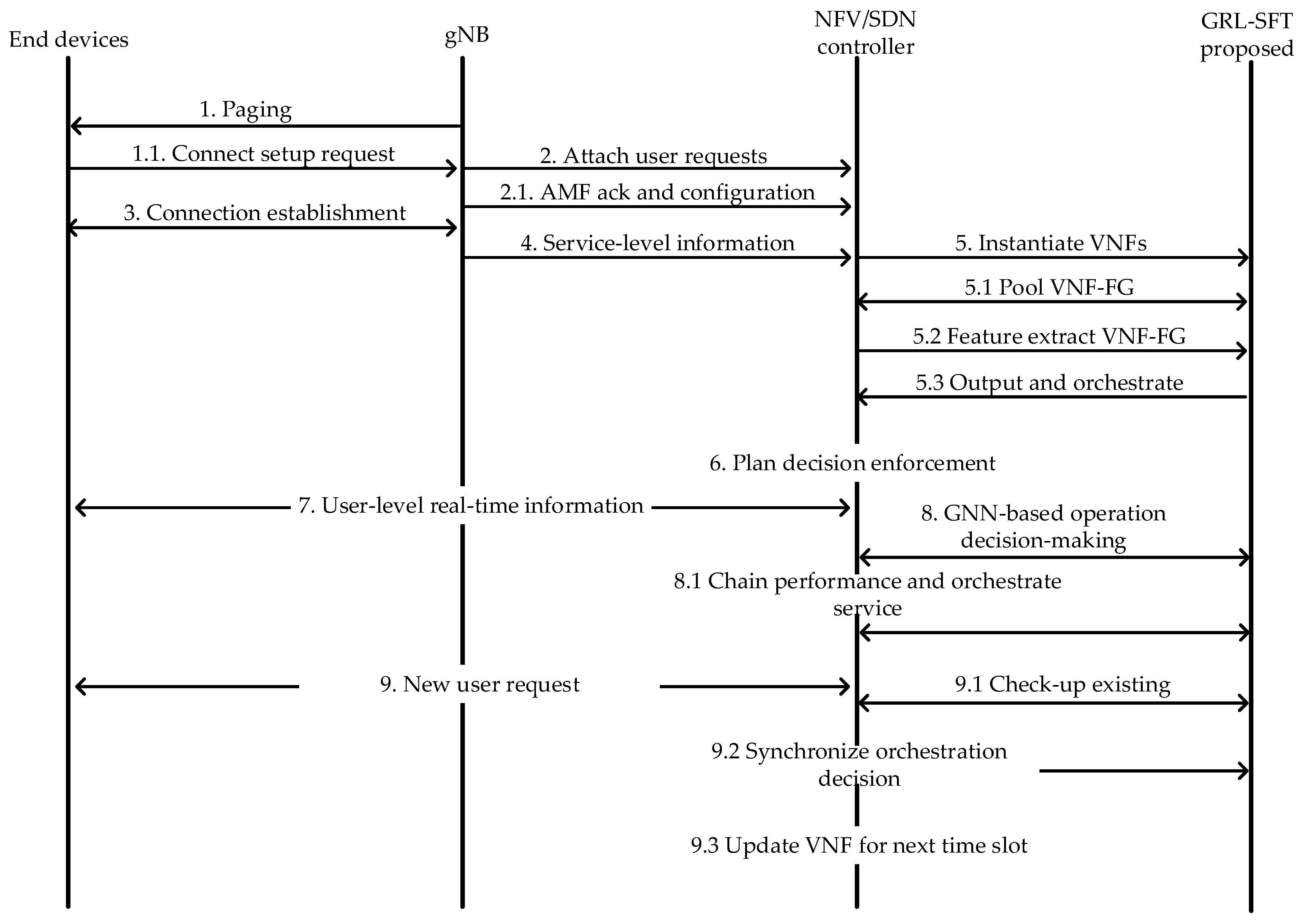
4.2. Selecting SFC-Enabled GNNs in Control Entities
- (1)
- Paging initializes the IoT device’s status to establish the corresponding feedback on the state. The connection setup request of radio resource control (RRC) is connected and initialized to the network function for broadcasting and connecting in mobility.
- (2)
- Access points gain the message from the initialized IoT device and utilize AMF in 5G. After that, AMF acknowledges and immediately establishes the configuration connection process.
- (3)
- After negotiating, AMF and IoT devices proceed with the connection establishment process.
- (4)
- With service-level information, negotiation is completed on which the access point carries the information of IoT devices. Then, SDN/NFV gathers and creates the flow table, and NFV determines the properties and capabilities of the resource.
- (5)
- NFV initializes to set up the SFC for supplying differentiated requests. Meanwhile, VNF-FG pooling enables the consolidation and sharing of VNF resources across multiple tenants or services, promoting resource efficiency and flexibility. Each VNF-FG can be represented as a graph, where the network functions are represented as nodes, and the connections between them are represented as graph representations. The GNN extracts the features of the node as a graph structure and propagates them through the network edges aggregated. Otherwise, it allows for classification and link prediction tasks with VNF-FG pooling. The output and analysis are conducted to calculate the short path of traversing from one node to another node. It can define the optimal path of VNF and identify performance-initialized resources.
- (6)
- Through efficiency classification, the SDN controller interacts with the GNN proposed for gathering the state observations and applies the action value for network policy orchestration.
- (7)
- Notifications with user-level status are addressed to orchestrate resources on demanding IoT devices.
- (8)
- After applying the rule of policy from the SDN/NFV controller, IoT devices update the user-level status of real-time information to the controller again.
- (9)
- The controller gathers users on demand and checks with previous states’ observations to modify the real-time orchestration resource.
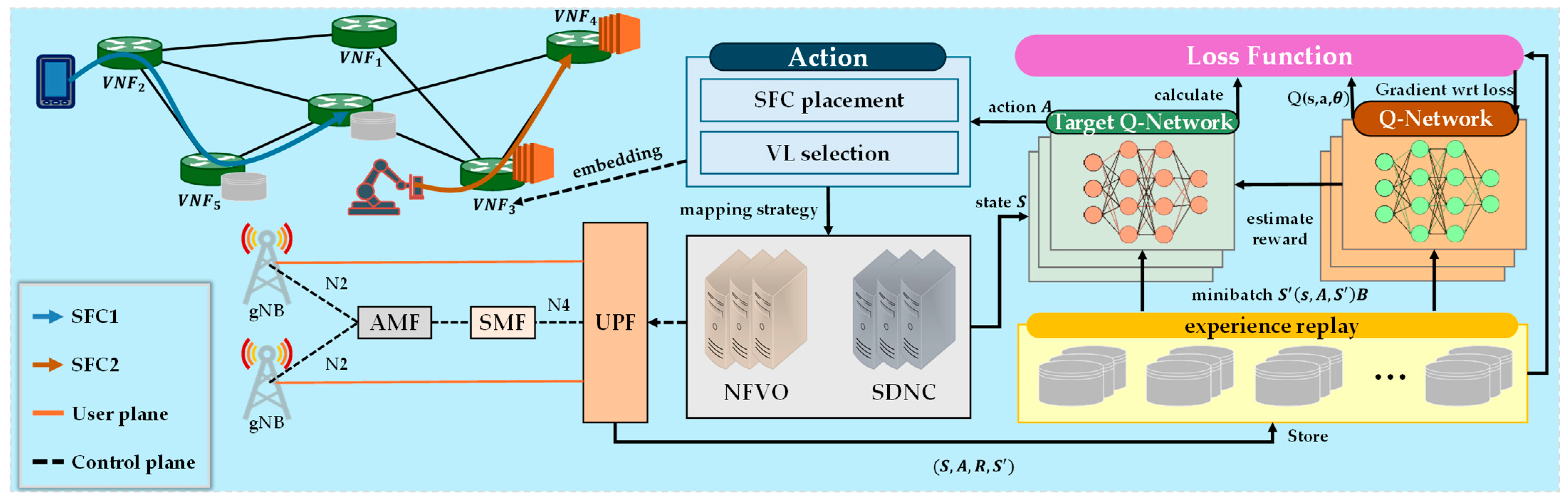
5. Proposed VNF Placement Solution
5.1. Proposed Methods-Based Solutions
5.1.1. Graph Neural Network-Based Approach
5.1.2. DRL-Based Approaches
5.2. Designed GRL-SFT Framework
| Algorithm 1: GNN-DRL for optimal policy and action in SFC placement | |||||
| Input: GCN representation of SFC request with the requirement of VNFs and VLs | |||||
| Output: Optimal deployment and placement of locations for each VNF instance | |||||
| 1: | initial replay memory | ||||
| 2: | for episode i = 0 to 1000 do | ||||
| 3: | Observe env. selection | ||||
| 4: | If exploration ): do | ||||
| 5: | Construct GCN from state ) of the network environment at time t, env.select_property.resource | ||||
| 6: | GCN passes the prediction value function | ||||
| 7: | Approximate for using value function | ||||
| 8: | For each difference do | ||||
| 9: | . (,) | ||||
| 10: | ) | ||||
| 11: | End | ||||
| 12: | |||||
| 13: | Construct GCN from the state ) | ||||
| 14: | GCN passes to value function | ||||
| 15: | |||||
| 16: | Else if do | ||||
| 17: | |||||
| 18: | |||||
| 19: | |||||
| 20: | end | ||||
6. Performance Evaluation
6.1. Simulation Setup
- Resource greed for SFC (RGD-SFC) is a conventional approach to designing, managing, and optimizing SFC in a network that relies on making decisions based on locally optimal selection at each step.
- Deep q-learning for SFC (DQL-SFC) is an approach that has only one estimator, which attempts to learn both the behavior and target policies to achieve an optimal solution.
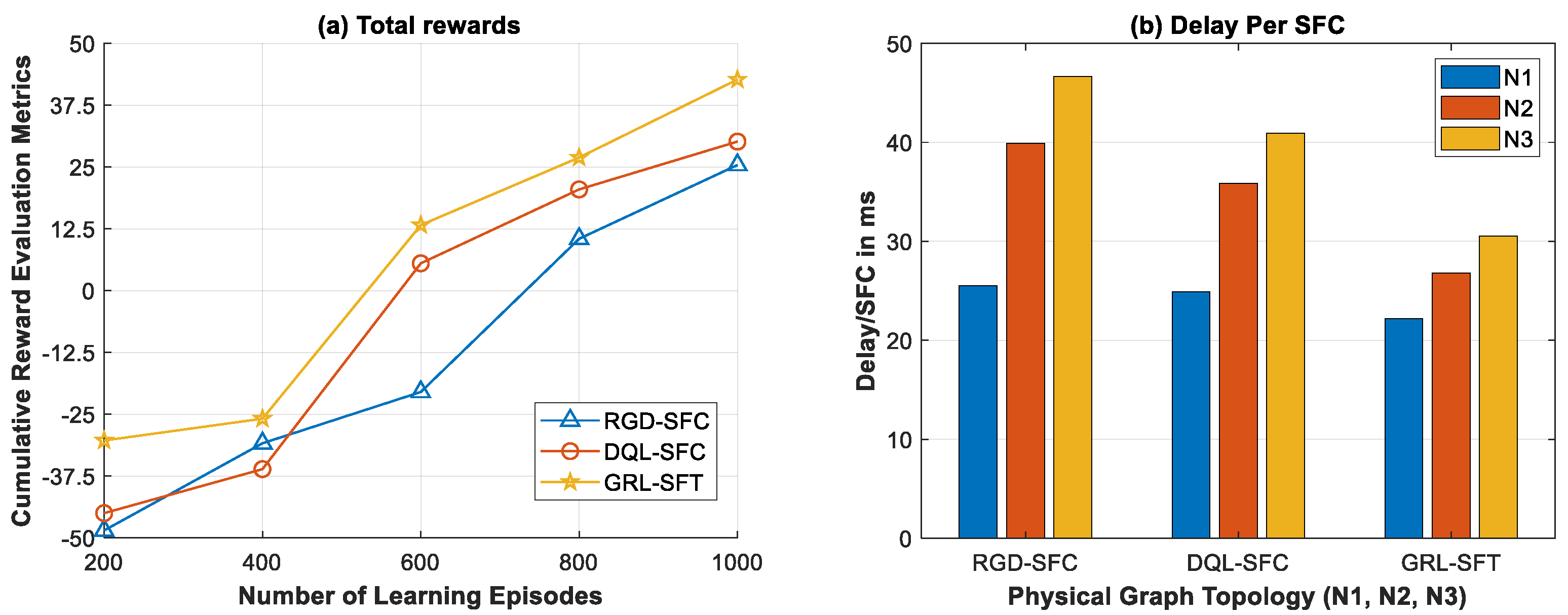
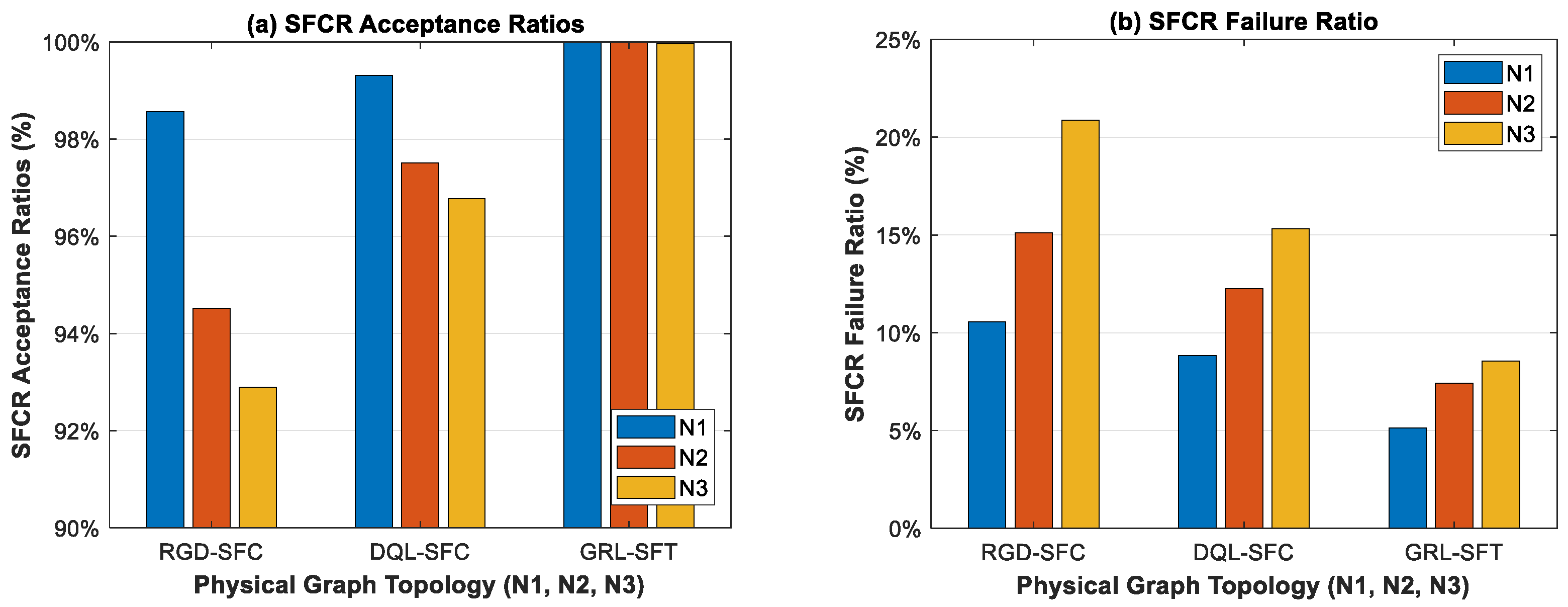
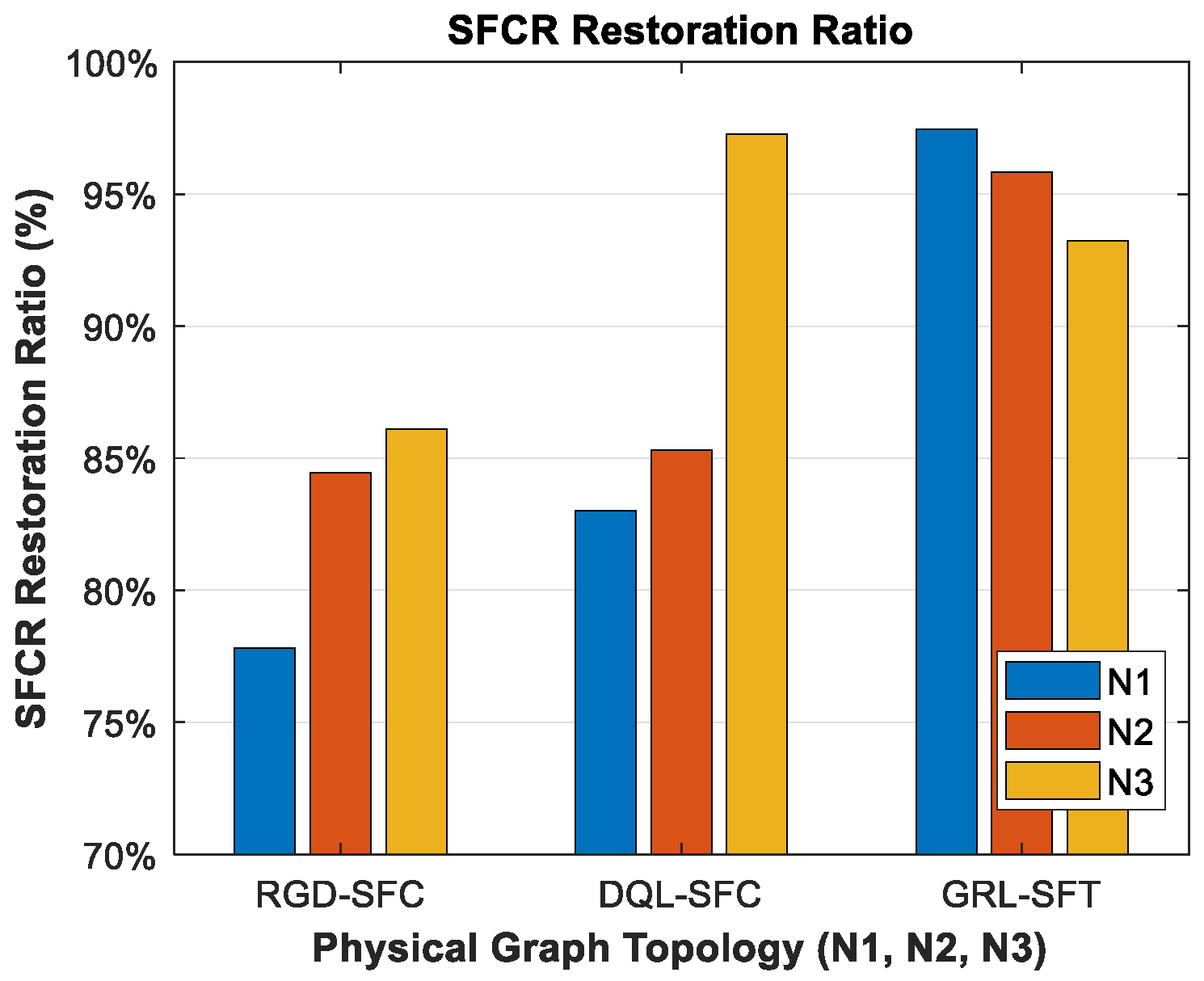
6.2. Results and Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Au Gupta, A.; Jha, R.K. A Survey of 5G Network: Architecture and Emerging Technologies. IEEE Access 2015, 3, 1206–1232. [Google Scholar] [CrossRef]
- Dogra, A.; Jha, R.K.; Jain, S. A Survey on beyond 5G Network with the Advent of 6G: Architecture and Emerging Technologies. IEEE Access 2020, 9, 67512–67547. [Google Scholar] [CrossRef]
- Aboubakar, M.; Kellil, M.; Roux, P. A Review of IoT Network Management: Current Status and Perspectives. J. King Saud Univ. Comput. Inf. Sci. 2021, 34, 4163–4176. [Google Scholar] [CrossRef]
- Mijumbi, R.; Serrat, J.; Gorricho, J.-L.; Bouten, N.; De Turck, F.; Boutaba, R. Network Function Virtualization: State-of-The-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 236–262. [Google Scholar] [CrossRef]
- Dung; Lien, Y.-H.; Liu, B.-H.; Chu, S.-I.; Nguyen, T.N. Virtual Network Function Placement for Serving Weighted Services in NFV-Enabled Networks. IEEE Syst. J. 2023, 17, 5648–5659. [Google Scholar] [CrossRef]
- Umrao, B.K.; Yadav, D.K. Placement of Virtual Network Functions for Network Services. Int. J. Netw. Manag. 2023, 33, e2232. [Google Scholar] [CrossRef]
- Kim, Y.; Kwak, J.; Lee, H.-W.; Chong, S. Dynamic Computation and Network Chaining in Integrated SDN/NFV Cloud Infrastructure. IEEE Trans. Cloud Comput. 2021, 11, 367–382. [Google Scholar] [CrossRef]
- Troia, S.; Savi, M.; Nava, G.; Maria, L.; Schneider, T.; Maier, G. Performance Characterization and Profiling of Chained CPU-Bound Virtual Network Functions. Comput. Netw. 2023, 231, 109815. [Google Scholar] [CrossRef]
- Zhu, M.; Oki, E. Robust Function Deployment against Uncertain Recovery Time in Different Protection Types with Workload-Dependent Failure Probability. Comput. Netw. 2023, 231, 109826. [Google Scholar] [CrossRef]
- Nine, Z.; Kosar, T.; Bulut, M.F.; Hwang, J. GreenNFV: Energy-Efficient Network Function Virtualization with Service Level Agreement Constraints. In Proceedings of the SC ’23: Proceedings of the International Conference for High Performance Computing, Networking, Storage and Analysis, New York, NY, USA, 12–17 November 2023. [Google Scholar] [CrossRef]
- Bizanis, N.; Kuipers, F.A. SDN and Virtualization Solutions for the Internet of Things: A Survey. IEEE Access 2016, 4, 5591–5606. [Google Scholar] [CrossRef]
- Gelberger, A.; Yemini, N.; Giladi, R. Performance Analysis of Software-Defined Networking (SDN). In Proceedings of the 2013 IEEE 21st International Symposium on Modelling, Analysis and Simulation of Computer and Telecommunication Systems, San Francisco, CA, USA, 14–16 August 2013. [Google Scholar] [CrossRef]
- Maleh, Y.; Qasmaoui, Y.; El Gholami, K.; Sadqi, Y.; Mounir, S. A Comprehensive Survey on SDN Security: Threats, Mitigations, and Future Directions. J. Reliab. Intell. Environ. 2022, 9, 201–239. [Google Scholar] [CrossRef]
- Ali, J.; Jhaveri, R.H.; Alswailim, M.; Roh, B. ESCALB: An Effective Slave Controller Allocation-Based Load Balancing Scheme for Multi-Domain SDN-Enabled-IoT Networks. J. King Saud Univ. Comput. Inf. Sci. 2023, 35, 101566. [Google Scholar] [CrossRef]
- Karakoç, E.; Çeken, C. Secure SLA Management Using Smart Contracts for SDN-Enabled WSN. KSII Trans. Internet Inf. Syst. 2023, 17, 3003–3029. [Google Scholar]
- Abid, A.; Manzoor, M.F.; Farooq, M.S.; Farooq, U.; Hussain, M. Challenges and Issues of Resource Allocation Techniques in Cloud Computing. KSII Trans. Internet Inf. Syst. 2020, 14, 2815–2839. [Google Scholar]
- Li, P.; Liu, G.; Guo, S.; Zeng, Y. Traffic-Aware Efficient Consistency Update in NFV-Enabled Software Defined Networking. Comput. Netw. 2023, 228, 109755. [Google Scholar] [CrossRef]
- Chen, L.; Tang, H.; Zhao, Y.; You, W.; Wang, K. A Privacy-Preserving and Energy-Efficient Offloading Algorithm Based on Lyapunov Optimization. KSII Trans. Internet Inf. Syst. 2022, 16, 2490–2506. [Google Scholar]
- Singh, R.; Sukapuram, R.; Chakraborty, S. A Survey of Mobility-Aware Multi-Access Edge Computing: Challenges, Use Cases and Future Directions. Ad Hoc Netw. 2023, 140, 103044. [Google Scholar] [CrossRef]
- Ren, Y.; Guo, A.; Song, C. Multi-Slice Joint Task Offloading and Resource Allocation Scheme for Massive MIMO Enabled Network. KSII Trans. Internet Inf. Syst. 2023, 17, 794–815. [Google Scholar]
- Kim, D.-Y.; Lee, S.; Kim, M.; Kim, S. Edge Cloud Selection in Mobile Edge Computing (MEC)-Aided Applications for Industrial Internet of Things (IIoT) Services. Comput. Syst. Sci. Eng. 2023, 47, 2049–2060. [Google Scholar] [CrossRef]
- Eang, C.; Ros, S.; Kang, S.; Song, I.; Tam, P.; Math, S.; Kim, S. Offloading Decision and Resource Allocation in Mobile Edge Computing for Cost and Latency Efficiencies in Real-Time IoT. Electronics 2024, 13, 1218. [Google Scholar] [CrossRef]
- Kang, S.; Ros, S.; Song, I.; Tam, P.; Math, S.; Kim, S. Real-Time Prediction Algorithm for Intelligent Edge Networks with Federated Learning-Based Modeling. Comput. Mater. Contin. 2023, 77, 1967–1983. [Google Scholar] [CrossRef]
- Huang, H.; Tian, J.; Yin, H.; Min, G.; Wu, D.; Miao, W. RQAP: Resource and QoS Aware Placement of Service Function Chains in NFV-Enabled Networks. IEEE Trans. Serv. Comput. 2023, 16, 4526–4539. [Google Scholar] [CrossRef]
- Ros, S.; Tam, P.; Kang, S.; Song, I.; Kim, S. A survey on state-of-the-art experimental simulations for privacy-preserving federated learning in intelligent networking. Electron. Res. Arch. 2024, 32, 1333–1364. [Google Scholar] [CrossRef]
- Nie, M.; Chen, D.; Wang, D. Reinforcement Learning on Graphs: A Survey. IEEE Trans. Emerg. Top. Comput. Intell. 2023, 7, 1065–1082. [Google Scholar] [CrossRef]
- Zhou, J.; Cui, G.; Hu, S.; Zhang, Z.; Yang, C.; Liu, Z.; Wang, L.; Li, C.; Sun, M. Graph Neural Networks: A Review of Methods and Applications. AI Open 2020, 1, 57–81. [Google Scholar] [CrossRef]
- Hu, H.; Kang, Q.; Zhao, S.; Wang, J.; Fu, Y. Service Function Chain Deployment Method Based on Traffic Prediction and Adaptive Virtual Network Function Scaling. Electronics 2022, 11, 2625. [Google Scholar] [CrossRef]
- Rankothge, W.; Le, F.; Russo, A.; Lobo, J. Optimizing Resource Allocation for Virtualized Network Functions in a Cloud Center Using Genetic Algorithms. IEEE Trans. Netw. Serv. Manag. 2017, 14, 343–356. [Google Scholar] [CrossRef]
- Thiruvasagam, P.K.; Chakraborty, A.; Mathew, A.; Murthy, C.S.R. Reliable Placement of Service Function Chains and Virtual Monitoring Functions with Minimal Cost in Softwarized 5G Networks. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1491–1507. [Google Scholar] [CrossRef]
- Pei, J.; Hong, P.; Xue, K.; Li, D. Efficiently Embedding Service Function Chains with Dynamic Virtual Network Function Placement in Geo-Distributed Cloud System. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 2179–2192. [Google Scholar] [CrossRef]
- Chen, J.; Chen, J.; Zhang, H. DRLEC: Multi-Agent DRL Based Elasticity Control for VNF Migration in SDN/NFV Networks. In Proceedings of the 2021 26th IEEE Asia-Pacific Conference on Communications (APCC), Kuala Lumpur, Malaysia, 11–13 October 2021. [Google Scholar] [CrossRef]
- Tam, P.; Ros, S.; Song, I.; Kang, S.; Kim, S. A Survey of Intelligent End-To-End Networking Solutions: Integrating Graph Neural Networks and Deep Reinforcement Learning Approaches. Electronics 2024, 13, 994. [Google Scholar] [CrossRef]
- Habibi, F.; Mahdi, D.; Khonsari, A.; Ghaderi, M. Accelerating Virtual Network Embedding with Graph Neural Networks. In Proceedings of the 16th International Conference on Network and Service Management (CNSM), Izmir, Turkey, 2–6 November 2020. [Google Scholar] [CrossRef]
- Sun, P.; Lan, J.; Li, J.; Guo, Z.; Hu, Y. Combining Deep Reinforcement Learning with Graph Neural Networks for Optimal VNF Placement. IEEE Commun. Lett. 2020, 25, 176–180. [Google Scholar] [CrossRef]
- Rkhami, A.; Quang Pham, T.A.; Hadjadj-Aoul, Y.; Outtagarts, A.; Rubino, G. On the Use of Graph Neural Networks for Virtual Network Embedding. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020. [Google Scholar] [CrossRef]
- Chantre, H.; da Fonseca, N.L.S. Reliable Broadcasting in 5G NFV-Based Networks. IEEE Commun. Mag. 2018, 56, 218–224. [Google Scholar] [CrossRef]
- Kothandaraman, B.; Du, M.; Sköldström, P. Centrally Controlled Distributed VNF State Management. In Proceedings of the 2015 ACM SIGCOMM Workshop on Hot Topics in Middleboxes and Network Function Virtualization, New York, NY, USA, 21 August 2015. [Google Scholar] [CrossRef]
- Yang, B.; Xu, Z.; Chai, W.K.; Liang, W.; Tuncer, D.; Galis, A.; Pavlou, G. Algorithms for Fault-Tolerant Placement of Stateful Virtualized Network Functions. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018. [Google Scholar] [CrossRef]
- Yuan, G.; Xu, Z.; Yang, B.; Liang, W.; Chai, W.K.; Tuncer, D.; Galis, A.; Pavlou, G.; Wu, G. Fault Tolerant Placement of Stateful VNFs and Dynamic Fault Recovery in Cloud Networks. Comput. Netw. 2020, 166, 106953. [Google Scholar] [CrossRef]
- Pei, J.; Hong, P.; Pan, M.; Liu, J.; Zhou, J. Optimal VNF Placement via Deep Reinforcement Learning in SDN/NFV-Enabled Networks. IEEE J. Sel. Areas Commun. 2020, 38, 263–278. [Google Scholar] [CrossRef]
- Roig, J.S.P.; Gutierrez-Estevez, D.M.; Gunduz, D. Management and Orchestration of Virtual Network Functions via Deep Reinforcement Learning. IEEE J. Sel. Areas Commun. 2019, 38, 304–317. [Google Scholar] [CrossRef]
- Lantz, B.; O’Connor, B. A Mininet-Based Virtual Testbed for Distributed SDN Development. In Proceedings of the 2015 ACM Conference on Special Interest Group on Data Communication—SIGCOMM ’15, London, UK, 17–21 August 2015. [Google Scholar] [CrossRef]
- Castillo-Lema, J.; Neto, A.V.; de Oliveira, F.; Kofuji, S.T. Mininet-NFV: Evolving Mininet with OASIS TOSCA NVF Profiles towards Reproducible NFV Prototyping. In Proceedings of the 2019 IEEE Conference on Network Softwarization (NetSoft), Paris, France, 24–28 June 2019. [Google Scholar] [CrossRef]

| Acronym | Description | Acronym | Description |
|---|---|---|---|
| 5G | Fifth generation | QoS | Quality of service |
| B5G | Beyond the fifth generation | SDN | Software-defined networking |
| CAPEX | Capital expense | SF | Service function |
| DRL | Deep reinforcement learning | SFC | Service function chaining |
| GCN | Graph convolutional network | SFCO | Service function chaining orchestration |
| GNN | Graph neural network | VIM | Virtual infrastructure management |
| MANO | Management and orchestration | VM | Virtual machine |
| MPNN | Message-passing neural network | VL | Virtual link |
| NFV | Network functions virtualization | VNF | Virtual network function |
| NFVI | Network functions virtualization infrastructure | VNFM | Virtual network function management |
| OPEX | Operating expense | VNFFG | Virtual network function forwarding graph |
| Notation | Description |
|---|---|
| The set of the physical network | |
| The set of MEC nodes | |
| The set of the links | |
| Number of timeslots | |
| Physical computing resources on node | |
| Upper-bound capacities of physical node-v (CPU, memory, disk) | |
| The resource capacity remaining at timeslot (CPU, memory, disk) of the node- | |
| The request of the resource capacity at time-t (CPU, memory, disk) of node-v | |
| The set of the bandwidth resource at time-t of , with participants in | |
| The set of VNFs | |
| The set of virtual links | |
| The number of VNFs in SFC requests for services | |
| Propagation delay of the processing time of node |
| Parameters | Specifications |
|---|---|
| Physical topology size (N1, N2, N3) | (75V, 150E), (100V, 200E), (125V, 250E) |
| Maximum tolerable delay | 50 ms–100 ms |
| VNF instance randomly | (0,10) |
| CPU capacities of node | 2000 Mips |
| Traffic rate | 1000 packet/s–5000 packet/s |
| Delay on link | ≤2 ms |
| Simulation time | 1000 s |
| NFVO and SDNC | Ryu 4.34 |
| Network topology platform | Mininet and Mini-NFV |
| Number of episodes | 2000 |
| Exploration rate | 0.5 |
| Discount factor | 0.95 |
| Reply memory capacity | 4000 |
| Learning rate | 0.001 |
| Batch size | (32,128) |
| Hidden layer dimensions | (32,64), (64,128), (128,256) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ros, S.; Tam, P.; Song, I.; Kang, S.; Kim, S. Handling Efficient VNF Placement with Graph-Based Reinforcement Learning for SFC Fault Tolerance. Electronics 2024, 13, 2552. https://doi.org/10.3390/electronics13132552
Ros S, Tam P, Song I, Kang S, Kim S. Handling Efficient VNF Placement with Graph-Based Reinforcement Learning for SFC Fault Tolerance. Electronics. 2024; 13(13):2552. https://doi.org/10.3390/electronics13132552
Chicago/Turabian StyleRos, Seyha, Prohim Tam, Inseok Song, Seungwoo Kang, and Seokhoon Kim. 2024. "Handling Efficient VNF Placement with Graph-Based Reinforcement Learning for SFC Fault Tolerance" Electronics 13, no. 13: 2552. https://doi.org/10.3390/electronics13132552
APA StyleRos, S., Tam, P., Song, I., Kang, S., & Kim, S. (2024). Handling Efficient VNF Placement with Graph-Based Reinforcement Learning for SFC Fault Tolerance. Electronics, 13(13), 2552. https://doi.org/10.3390/electronics13132552







