Study of Network Security Based on Key Management System for In-Vehicle Ethernet
Abstract
:1. Introduction
2. In-Vehicle Ethernet and Key Management Technology
2.1. In-Vehicle Ethernet
2.2. Key Management Mechanism
3. Results—Key Management System
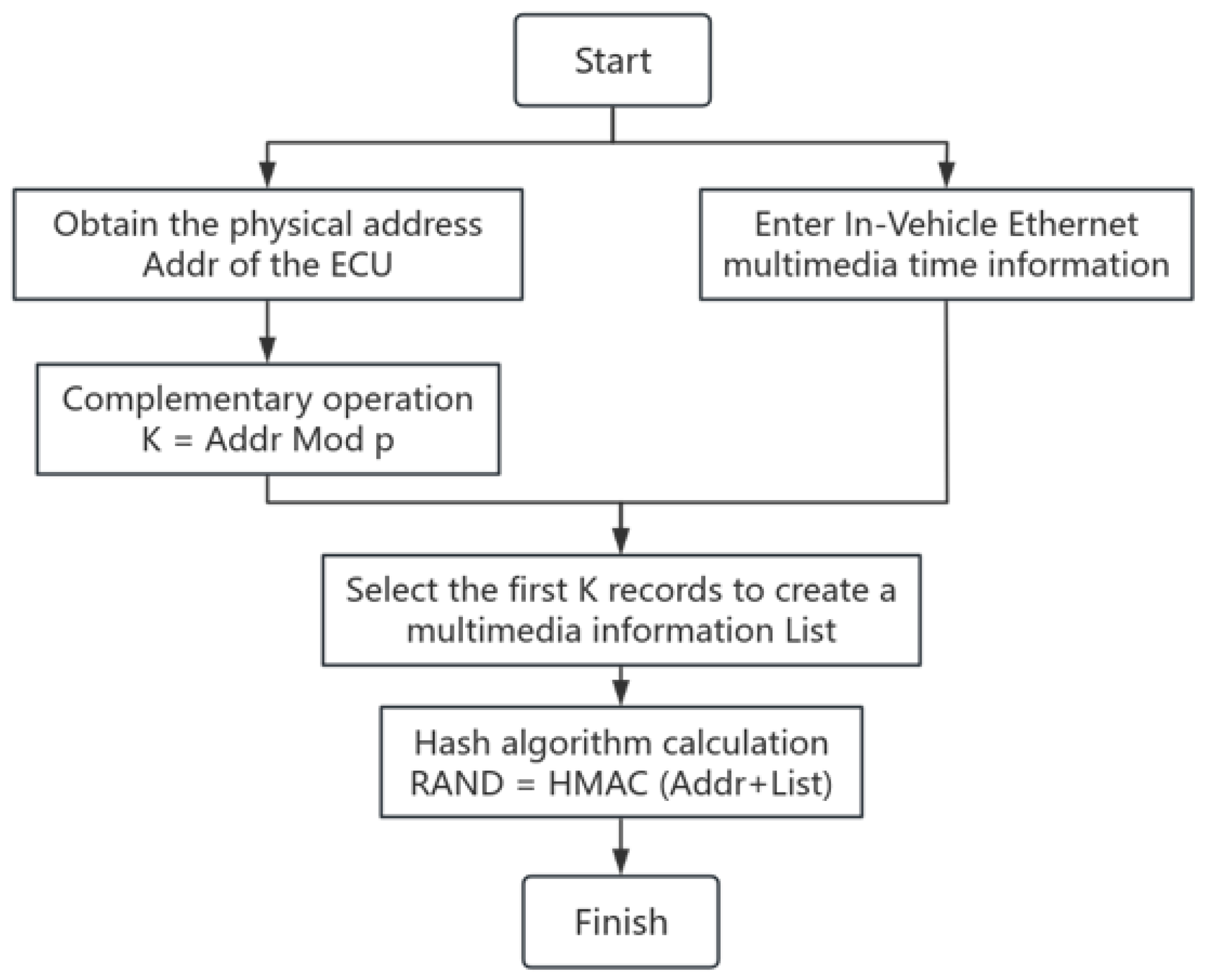
3.1. Key Generation
3.2. Key Distribution
| Algorithm 1 Session Key Distribution Algorithm |
| Input: Prime modulus p, Generator point G, Private keys private key A, private key B, Public keys public key A, public key B Output: Session Key |
| 1: 2: + Key Distribution.get random num(p) 3: G 4: G 5://Sign with own private key 6: S A←Schnorr Sign.sign(private key A, G.to bytes(), G, p) 7:S A to B 8://Verify signature S A 9: flag1←Schnorr Sign.verify(public key A, G.to bytes(),S A,G) 10: if not flag1 then 11: throw Exception(“Signature verification failed!”) 12: end if 13: 14: ←Key Distribution.get random num(p) 15: G 16: G 17://Sign with own private key 18: S B←Schnorr Sign.sign(private key B, G.to bytes(), G, p) 19:S B to A 20://Verify signature S B 21: flag2←Schnorr Sign.verify(public key B, G.to bytes().S B,G) 22: if not flag2 then 23: throw Exception(“Signature verification failed!”) 24: end if 25:G 26: ← G 27://Use EK-coordinate as encryption key 28: EK← G. EK() 29://Convert int to bytes 30: enc key←EK.to bytes((EK.bit length() + 7)//8,byteorder =’big’) 31://Use y-coordinate as authentication key 32: AK← G. AK() 33://Convert int to bytes 34: auth key←AK.to bytes((AK.bit length()+ 7)//8,byteorder =’big’) 35://Convert to Session Key format 36: session key←Session Key(enc key,auth key) 37: return session key |
3.3. Application of Key Management System
4. Model Validation
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Walrand, J.; Turner, M.; Myers, R. An Architecture for In-Vehicle Networks. IEEE Trans. Veh. Technol. 2021, 70, 6335–6342. [Google Scholar] [CrossRef]
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing. 2011. Available online: https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-145.pdf (accessed on 8 May 2024).
- Lee, Y.; Woo, S.; Song, Y.; Lee, J.; Lee, D.H. Practical Vulnerability-Information-Sharing Architecture for Automotive Security-Risk Analysis. IEEE Access 2020, 8, 120009–120018. [Google Scholar] [CrossRef]
- Nichiţelea, T.C.; Unguritu, M.G. Automotive Ethernet Applications Using Scalable Service-Oriented Middleware over IP: Service Discovery. In Proceedings of the 24th International Conference on Methods and Models in Automation and Robotics (MMAR), Miedzyzdroje, Poland, 26–29 August 2019. [Google Scholar]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2014, 16, 993–1006. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, T.; Zhao, H.; Ma, C. Risk Analysis of CAN Bus and Ethernet Communication Security for Intelligent Connected Vehicles. In Proceedings of the IEEE International Conference on Artificial Intelligence and Industrial Design (AIID), Guangzhou, China, 28–30 May 2021. [Google Scholar]
- Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef] [PubMed]
- Lee, T.Y.; Lin, I.A.; Liao, R.H. Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors 2020, 20, 641. [Google Scholar] [CrossRef] [PubMed]
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Petrovski, A.; Madzudzo, G.; Cheah, M. AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey. ACM Comput. Surv. 2023, 55, 1–40. [Google Scholar] [CrossRef]
- Luo, F.; Hou, S. Cyberattacks and Countermeasures for Intelligent and Connected Vehicles. SAE Int. J. Passeng. Cars Electron. Electr. Syst. 2019, 12, 55–66. [Google Scholar] [CrossRef]
- Martínez-Cruz, A.; Ramírez-Gutiérrez, K.A.; Feregrino-Uribe, C.; Morales-Reyes, A. Security on In-Vehicle Communication Protocols: Issues, Challenges, and Future Research Directions. Comput. Commun. 2021, 180, 1–20. [Google Scholar] [CrossRef]
- Pal, O.; Alam, B.; Thakur, V.; Singh, S. Key Management for Blockchain Technology. ICT Express 2021, 7, 76–80. [Google Scholar] [CrossRef]
- Banerjee, S.; Chunka, C.; Sen, S.; Goswami, R.S. An Enhanced and Secure Biometric Based User Authentication Scheme in Wireless Sensor Networks Using Smart Cards. Wirel. Pers. Commun. 2019, 107, 243–270. [Google Scholar] [CrossRef]
- Tian, Y.; Wang, Z.; Xiong, J.; Ma, J. A Blockchain-Based Secure Key Management Scheme with Trustworthiness in DWSNs. IEEE Trans. Ind. Inform. 2020, 16, 6193–6202. [Google Scholar] [CrossRef]
- Hossain, M.A.; Hossain, N.; Akhond, M.R.; Adnan, N.; Galib, S.M. Mathematical Solution of ULTE Based Salt Generation Password Based Key Derivation Function (PBKDF). Am. J. Agric. Sci. Eng. Technol. 2022, 6, 8–17. [Google Scholar] [CrossRef]
- Zhu, L.; Mao, H. Uniform Test Comparison of ULSI, PMMLCG, GFSRG and Super-Prime Method. In Proceedings of the 2010 International Conference on Computational Intelligence and Software Engineering, Wuhan, China, 10–12 December 2010. [Google Scholar]
- Lee, K.; Kim, H. Two-Round Multi-Signatures from Okamoto Signatures. Mathematics 2023, 11, 3223. [Google Scholar] [CrossRef]
- Kabulov, A.; Berdimurodov, M. Optimal Representation in the Form of Logical Functions of Microinstructions of Cryptographic Algorithms (RSA, El-Gamal). In Proceedings of the 2021 International Conference on Information Science and Communications Technologies, Tashkent, Uzbekistan, 3–5 November 2021. [Google Scholar]
- Tu, B.; Chen, Y.; Cui, H.; Wang, X. Fast Two-Party Signature for Upgrading ECDSA to Two-Party Scenario Easily. Theor. Comput. Sci. 2024, 986, 114325. [Google Scholar] [CrossRef]
- Du, S.; Ye, G. IWT and RSA Based Asymmetric Image Encryption Algorithm. Alex. Eng. J. 2023, 66, 979–991. [Google Scholar] [CrossRef]
- Crites, E.; Komlo, C.; Maller, M. Fully Adaptive Schnorr Threshold Signatures. In Proceedings of the Annual International Cryptology Conference 43rd Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2023. [Google Scholar]




| Symbols | Functional Description |
|---|---|
| ECU_Tx | Sending node |
| ECU_Rx | Receiving node |
| Public key of the sending node | |
| Private key of the sending node | |
| Public key of the receiving node | |
| Private key of the receiving node | |
| C | Ciphertext |
| MIE | Plaintext |
| Using random number Key RAND_Key | |
| A random number mapped to a finite field | |
| S | Secret key |
| EK | Encryption key |
| AK | Authentication key |
| M1 | Message sent by ECU_Tx to ECU_Rx |
| M2 | Message sent by ECU_Rx to ECU_Tx |
| ECDSA | Okamoto | ElGamal | RSA | Schnorr | |
|---|---|---|---|---|---|
| Memory overhead | |||||
| Storage space (byte) | 64 | 768 | 512 | 256 | 65 |
| Key agreement time: (ms) | 3.234 | 14.733 | 10.233 | 29.4 | 1.533 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, J.; Zuo, Q.; Jin, W.; Wu, Y.; Xu, Y.; Xu, Y. Study of Network Security Based on Key Management System for In-Vehicle Ethernet. Electronics 2024, 13, 2524. https://doi.org/10.3390/electronics13132524
Chen J, Zuo Q, Jin W, Wu Y, Xu Y, Xu Y. Study of Network Security Based on Key Management System for In-Vehicle Ethernet. Electronics. 2024; 13(13):2524. https://doi.org/10.3390/electronics13132524
Chicago/Turabian StyleChen, Jiaoyue, Qihui Zuo, Wenquan Jin, Yujing Wu, Yihu Xu, and Yinan Xu. 2024. "Study of Network Security Based on Key Management System for In-Vehicle Ethernet" Electronics 13, no. 13: 2524. https://doi.org/10.3390/electronics13132524
APA StyleChen, J., Zuo, Q., Jin, W., Wu, Y., Xu, Y., & Xu, Y. (2024). Study of Network Security Based on Key Management System for In-Vehicle Ethernet. Electronics, 13(13), 2524. https://doi.org/10.3390/electronics13132524







