A Trusted Execution Environment RISC-V System-on-Chip Compatible with Transport Layer Security 1.3
Abstract
1. Introduction
- The TEE-HW framework. A high-security computer system must be developed, and an open-source TEE-HW framework must be developed to interface with the Keystone open-source TEE software framework [23]. The suggested TEE-HW framework must address the following requirements. It must be safe, simple to use, adaptable for different security needs, and, most significantly, simple to upgrade with a new defense mechanism. Many architectural features are left optional and can be easily changed by modifying the Makefile system’s parameters. The RISC-V open-source community is welcome to reuse the TEE-HW framework’s source codes [34]. Future security developers will benefit from such open-source TEE hardware.
- TEE-HW with cryptographic accelerators. A unique system designed specifically for TEE was created based on the suggested TEE-HW framework. True Random Number Generator (TRNG), Advanced Encryption Standard Galois/Counter Mode (AES_GCM), and Secure Hash Algorithm 3 (SHA-3) are among the several introduced crypto-cores. Besides the required crypto-cores, we also introduced several crypto-cores for the Transport Layer Security 1.3 (TLS 1.3), such as HMAC-SHA2, Digital Signature Algorithm (Ed-DSA or EC-DSA), Rivest–Shamir–Adleman (RSA), and Authenticated Encryption with Associated Data (AEAD). Furthermore, a hidden write-only memory, which is inaccessible to TEE processors, is another feature of the Ed25519 crypto-core. The keys produced by the Ed25519 module will be kept in this write-only memory. We investigated the performance of the suggested TEE hardware with crypto-cores using FPGA and VLSI implementation. We also looked into the TEE boot performance.
- TEE-HW with isolated RoT. A heterogeneous architecture for RoT-based secure boot flow was suggested by combining an isolated MicroController Unit (MCU) and Linux-bootable TEE processors. While the concealed MCU handles key generation, secure boot, and root key storage, the TEE side typically runs the TEE software stack. After reset, the very first authentication is performed by the hidden MCU. Then, the other crypto-keys are created and stored in memory. Finally, the boot process is transferred to the TEE processors to boot into the Linux kernel. By this setup, all resources are available for the hidden MCU to use, but after boot, all the peripherals inside the hidden MCU are inaccessible by the TEE domain. The secure boot procedure and the remote administration tool (RoT) are no longer within the TEE domain. This makes the secure boot procedure flexible and capable of withstanding potential future threats. The proposed architecture was developed and tested on both FPGA and VLSI on a 180 nm process.
2. Background Knowledge
2.1. Trusted Execution Environment
2.2. Keystone
3. The Crypto-Accelerators
3.1. True Random Number Generator (TRNG)
3.2. SHA3-512
3.3. Advanced Encryption Standard (AES)—Galois/Counter Mode (GCM)
3.4. Hash-Based Message Authentication Code (HMAC) with Secure Hash Algorithm 2 (SHA2)
3.5. Elliptic Curve (EC) and Edward Curve (Ed) Digital Signature Algorithm (DSA)
3.6. Rivest–Shamir–Adleman (RSA)
3.7. Authenticated Encryption with Associated Data (AEAD)
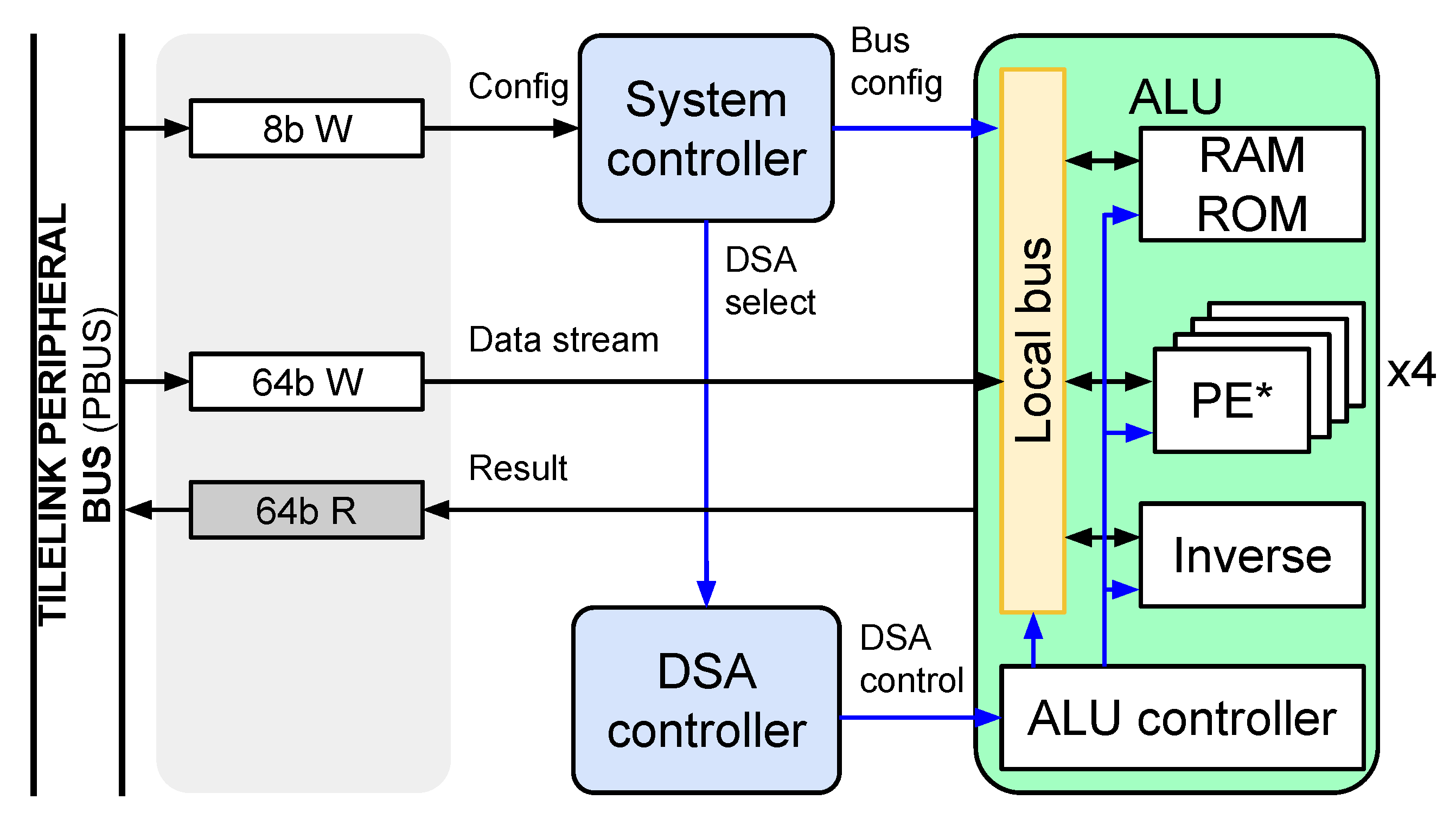
4. TEE System-on-Chip
4.1. The Isolated Sub-System
4.2. The Isolated TEE System
5. Secured Boot Flow
6. Experimental Results
6.1. Experimental Setups
6.2. Resource and Power Consumption
6.3. Performance Analysis
6.4. Security Analysis
6.5. Comparison and Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Quarkslab. Introduction to Trusted Execution Environment: ARM’s TrustZone. Retrieved Oct. 2018, 8, 2019. [Google Scholar]
- Oracle Corporation. Working with UEFI Secure Boot. Available online: https://docs.oracle.com/en/operating-systems/oracle-linux/secure-boot/sboot-OverviewofSecureBoot.html#sb-overview (accessed on 21 June 2024).
- Sabt, M.; Achemlal, M.; Bouabdallah, A. Trusted Execution Environment: What It is, and What It is Not. In Proceedings of the IEEE Trustcom/BigDataSE/ISPA (TrustCom), Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 57–64. [Google Scholar]
- Intel Corp. Intel Software Guard Extensions (Intel SGX) Developer Guide; Intel Corp.: Santa Clara, CA, USA, 2018. [Google Scholar]
- Costan, V.; Devadas, S. Intel SGX Explained. Cryptology ePrint Archive, Report 2016/086, January 2016. Available online: https://eprint.iacr.org/2016/086 (accessed on 21 June 2024).
- Costan, V.; Lebedev, I.; Devadas, S. Secure Processors Part I: Background, Taxonomy for Secure Enclaves and Intel SGX Architecture. Found. Trends® Electron. Des. Autom. 2017, 11, 1–248. [Google Scholar] [CrossRef]
- Costan, V.; Lebedev, I.; Devadas, S. Secure Processors Part II: Intel SGX Security Analysis and MIT Sanctum Architecture. Found. Trends® Electron. Des. Autom. 2018, 11, 249–361. [Google Scholar] [CrossRef]
- ARM Ltd. ARM Security Technology: Building a Secure System Using TrustZone Technology; Technical Report PRD29-GENC-009492C; ARM Ltd.: Cambridge, UK, 2009. [Google Scholar]
- Pinto, S.; Santos, N. Demystifying Arm TrustZone: A Comprehensive Survey. ACM Comput. Surv. 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Buhren, R.; Werling, C.; Seifert, J.-P. Insecure Until Proven Updated: Analyzing AMD SEV’s Remote Attestation. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS), London, UK, 11–15 November 2019; pp. 1087–1099. [Google Scholar]
- Baumann, A.; Peinado, M.; Hunt, G. Shielding Applications from an Untrusted Cloud with Haven. In Proceedings of the USENIX Symposium on Operating Systems Design and Implementation (OSDI), Broomfield, CO, USA, 6–8 October 2014; pp. 267–283. [Google Scholar]
- Tsai, C.-C.; Porter, D.E.; Vij, M. Graphene-SGX: A Practical Library OS for Unmodified Applications on SGX. In Proceedings of the USENIX Annual Technical Conference (ATC), Santa Clara, CA, USA, 12–14 July 2017; pp. 645–658. [Google Scholar]
- Arnautov, S.; Trach, B.; Gregor, F.; Knauth, T.; Martin, A.; Priebe, C.; Lind, J.; Muthukumaran, D.; O’Keeffe, D.; Stillwell, M.L.; et al. SCONE: Secure Linux Containers with Intel SGX. In Proceedings of the USENIX Symposium on Operating Systems Design and Implementation (OSDI), Savannah, GA, USA, 2–4 November 2016; pp. 689–703. [Google Scholar]
- Ferraiuolo, A.; Baumann, A.; Hawblitzel, C.; Parno, B. Komodo: Using Verification to Disentangle Secure-Enclave Hardware from Software. In Proceedings of the ACM Symposium on Operating Systems Principles (SOSP), Shanghai, China, 28–31 October 2017; pp. 287–305. [Google Scholar]
- Linaro Ltd. Open Portable Trusted Execution Environment; Linaro Ltd.: Cambridgeshire, UK, 2021. [Google Scholar]
- Brasser, F.; Gens, D.; Jauernig, P.; Sadeghi, A.-R.; Stapf, E. SANCTUARY: ARMing TrustZone with User-space Enclaves. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 24–27 February 2019; pp. 1–15. [Google Scholar]
- Kaplan, D. Protecting VM Register State with SEV-ES. White Paper 17 February 2017. Available online: https://www.amd.com/content/dam/amd/en/documents/epyc-business-docs/white-papers/Protecting-VM-Register-State-with-SEV-ES.pdf (accessed on 21 June 2024).
- Sev-Snp, A.M.D. Strengthening VM Isolation with Integrity Protection and More. White Paper January 2020. Available online: https://www.amd.com/content/dam/amd/en/documents/epyc-business-docs/white-papers/SEV-SNP-strengthening-vm-isolation-with-integrity-protection-and-more.pdf (accessed on 21 June 2024).
- Hex Five Security, Inc. MultiZone Hex-Five Security; Hex Five Security, Inc.: Redwood Shores, CA, USA, 2024. [Google Scholar]
- Costan, V.; Lebedev, I.; Devadas, S. Sanctum: Minimal Hardware Extensions for Strong Software Isolation. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 857–874. [Google Scholar]
- Weiser, S.; Werner, M.; Brasser, F.; Malenko, M.; Mangard, S.; Sadeghi, A.-R. TIMBER-V: Tag-Isolated Memory Bringing Fine-Grained Enclaves to RISC-V. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–27 February 2019; pp. 1–15. [Google Scholar]
- Bahmani, R.; Brasser, F.; Dessouky, G.; Jauernig, P.; Klimmek, M.; Sadeghi, A.-R.; Stapf, E. CURE: A Security Architecture with CUstomizable and Resilient Enclaves. In Proceedings of the USENIX Security Symposium (USENIX Security), Virtual Event, 11–13 August 2021; pp. 1073–1090. [Google Scholar]
- Lee, D.; Kohlbrenner, D.; Shinde, S.; Asanovic, K.; Song, D. Keystone: An Open Framework for Architecting Trusted Execution Environments. In Proceedings of the European Conference on Computer Systems (EUROSYS), Heraklion, Greece, 27–30 April 2020; pp. 1–16. [Google Scholar]
- He, F.; Zhang, H.; Wang, H.; Xu, M.; Yan, F. Chain of Trust Testing Based on Model Checking. In Proceedings of the International Conference on Networks Security, Wireless Communications and Trusted Computing (NSWCTC), Wuhan, China, 24–25 April 2010; Volume 1, pp. 273–276. [Google Scholar]
- AMD Inc. Inside a Deeply Embedded Security Processor. In Proceedings of the Black Hat USA, Virtual Event, 1–6 August 2020; AMD Inc.: Santa Clara, CA, USA, 2020. [Google Scholar]
- ARM Ltd. ARM Security IP: CryptoCell-700 Family; ARM Ltd.: Cambridge, UK, 2017. [Google Scholar]
- Intel Corp. Intel Active Management Technology (AMT) Developers Guide; Intel Corp.: Santa Clara, CA, USA, 2024. [Google Scholar]
- Rambus, Inc. Security CryptoManager Provisioning; Rambus, Inc.: Sunnyvale, CA, USA, 2022. [Google Scholar]
- lowRISC CIC. OpenTitan. Available online: https://github.com/lowRISC/opentitan (accessed on 21 June 2024).
- ISO/IEC 11889-1:2015; Information Technology—Trusted Platform Module Library—Part 1: Architecture. ISO/IEC: Geneva, Switzerland, 2015.
- Furtak, A.; Bulygin, Y.; Bazhaniuk, O.; Loucaides, J.; Matrosov, A.; Gorobets, M. BIOS and Secure Boot Attacks Uncovered. In Proceedings of the Ekoparty Security Conference, Buenos Aires, Argentina, 29–31 October 2014; pp. 1–79. [Google Scholar]
- Cui, E.; Li, T.; Wei, Q. RISC-V Instruction Set Architecture Extensions: A Survey. IEEE Access 2023, 11, 24696–24711. [Google Scholar] [CrossRef]
- Hoang, T.T.; Duran, C.; Serrano, R.; Sarmiento, M.; Nguyen, K.D.; Tsukamoto, A.; Suzaki, K.; Pham, C.K. Trusted Execution Environment Hardware by Isolated Heterogeneous Architecture for Key Scheduling. IEEE Access 2022, 10, 46014–46027. [Google Scholar] [CrossRef]
- PHAM Laboratory. TEE Hardware Platform. Available online: https://github.com/uec-hanken/tee-hardware (accessed on 21 June 2024).
- Serrano, R.; Duran, C.; Hoang, T.-T.; Sarmiento, M.; Nguyen, K.-D.; Tsukamoto, A.; Suzaki, K.; Pham, C.-K. A Fully Digital True Random Number Generator with Entropy Source Based in Frequency Collapse. IEEE Access 2021, 9, 105748–105755. [Google Scholar] [CrossRef]
- Dworkin, M.J. SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. August 2015. Available online: https://www.nist.gov/publications/sha-3-standard-permutation-based-hash-and-extendable-output-functions?pub_id=919061 (accessed on 21 June 2024).
- FIPS-197; Advanced Encryption Standard (AES). NIST Standard: Gaithersburg, MD, USA, November 2001.
- Krawczyk, H.; Bellare, M.; Canetti, R. RFC2104: HMAC: Keyed-Hashing for Message Authentication. February 1997. Available online: https://dl.acm.org/doi/abs/10.17487/RFC2104 (accessed on 21 June 2024).
- Nir, Y.; Langley, A. RFC8439: ChaCha20 and Poly1305 for IETF Protocols. June 2018. Available online: https://datatracker.ietf.org/doc/rfc8439/ (accessed on 21 June 2024).
- lowRISC CIC. IBex RISC-V Core. Available online: https://github.com/lowRISC/ibex (accessed on 21 June 2024).
- Barker, E.; Roginsky, A.; Davis, R. Recommendation for Cryptographic Key Generation; Technical Report; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2020.
- SiFive, Inc. SiFive TileLink Specication; SiFive, Inc.: Santa Clara, CA, USA, 2019. [Google Scholar]
- ARM. AMBA AXI and ACE Protocol Specification; Technical Report ARM IHI 0022H.c; ARM: Cambridge, UK, 2021. [Google Scholar]
- Hofmann, O.S.; Kim, S.; Dunn, A.M.; Lee, M.Z.; Witchel, E. InkTag: Secure Applications on an Untrusted Operating System. ACM SIGPLAN Not. 2013, 48, 265–278. [Google Scholar] [CrossRef]
- Stratify Labs. Dhrystone Benchmarking on MCUs; Stratify Labs: Highland, UT, USA, 2019. [Google Scholar]
- Kumar, V.B.Y.; Chattopadhyay, A.; Yahya, J.H.; Mendelson, A. ITUS: A Secure RISC-V System-on-Chip. In Proceedings of the IEEE International System-on-Chip Conference (SOCC), Singapore, 3–6 September 2019; pp. 418–423. [Google Scholar]
- Yahya, J.H.; Wong, M.M.; Pudi, V.; Bhasin, S.; Chattopadhyay, A. Lightweight Secure-Boot Architecture for RISC-V System-on-Chip. In Proceedings of the International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 11–13 March 2019; pp. 216–223. [Google Scholar]
- Nasahl, P.; Schilling, R.; Werner, M.; Mangard, S. HECTOR-V: A Heterogeneous CPU Architecture for a Secure RISC-V Execution Environment. In Proceedings of the ACM Asia Conference on Computer and Communications Security (ASIA CCS), Hong Kong, China, 7–11 June 2021; pp. 187–199. [Google Scholar]
- SiFive, Inc. Securing the RISC-V Revolution; SiFive, Inc.: Santa Clara, CA, USA, 2019. [Google Scholar]














| Instance | LUTs | Registers | BRAM | Size (KB) | DSP Blocks | ||
|---|---|---|---|---|---|---|---|
| Total system | 97,040 | 100.00% | 52,099 | 100.00% | 28 | 619 | 16 |
| Rocket | 12,465 | 12.84% | 7530 | 14.45% | 12 | 544 | 2 |
| core | 3478 | 3.58% | 1521 | 2.92% | 0 | 0 | 2 |
| dcache | 2107 | 2.17% | 3716 | 3.77% | 2 | 16 | 0 |
| icache | 5982 | 6.16% | 3716 | 7.13% | 2 | 16 | 0 |
| Ibex 1 | 4929 | 5.08% | 2575 | 4.94% | 2 | 8 | 0 |
| BootROM | 38 | 0.04% | 43 | 0.08% | 4 | 32 | 0 |
| EDEC | 41,353 | 42.61% | 9524 | 18.28% | 8 | 2 | 0 |
| RSA | 7087 | 7.30% | 6589 | 12.65% | 0 | 0 | 0 |
| AEAD | 5925 | 6.12% | 2497 | 4.79% | 0 | 0 | 7 |
| Chacha | 3118 | 3.21% | 2497 | 4.79% | 0 | 0 | 0 |
| Poly | 1268 | 1.31% | 2023 | 3.88% | 0 | 0 | 7 |
| SHA3 | 6200 | 6.39% | 2820 | 5.41% | 0 | 0 | 0 |
| AES_GCM | 2635 | 2.71% | 4400 | 8.45% | 0 | 0 | 0 |
| HMAC-SHA2 | 2178 | 2.24% | 1425 | 2.74% | 2 | 1 | 0 |
| TRNG | 136 | 0.14% | 563 | 1.08% | 0 | 0 | 0 |
| Other * | 9708 | 10.00% | 9613 | 18.45% | 0 | 0 | 0 |
| Gate Eqiv. | Area | Power | |||||
|---|---|---|---|---|---|---|---|
| (NAND2) | % | Leakage (nW) | Dynamic (mW) | Total (mW) | % | ||
| Total | 460,195 | 14,744,115 | 100.00 | 5487 | 3075 | 3075 | 100 |
| Rocket | 75,030 | 5,100,826 | 34.59 | 1213 | 425 | 425 | 13.82 |
| core | 15,337 | 372,392 | 2.53 | 177 | 182 | 182 | 5.92 |
| dcache | 25,398 | 2,509,375 | 17.02 | 456 | 154 | 154 | 5.01 |
| icache | 32,127 | 2,169,710 | 14.72 | 555 | 77 | 77 | 2.50 |
| IBex 1 | 17,681 | 737,478 | 5.00 | 201 | 69 | 69 | 2.24 |
| BootROM | 4272 | 70,672 | 0.48 | 21 | 11 | 11 | 0.36 |
| ECED | 166,720 | 3,638,115 | 24.68 | 1664 | 1311 | 1311 | 42.63 |
| RSA | 35,754 | 827,563 | 5.61 | 385 | 226 | 226 | 7.35 |
| AEAD | 30,345 | 783,675 | 5.32 | 349 | 223 | 223 | 7.25 |
| Chacha | 16,723 | 402,309 | 2.73 | 178 | 85 | 85 | 2.76 |
| Poly | 10,966 | 308,602 | 2.09 | 136 | 89 | 89 | 2.89 |
| SHA3 | 26,873 | 669,773 | 4.54 | 292 | 156 | 156 | 5.07 |
| AES_GCM | 20,753 | 532,594 | 3.61 | 266 | 80 | 80 | 2.60 |
| HMAC-SHA2 | 13,155 | 529,278 | 3.58 | 176 | 92 | 92 | 2.99 |
| TRNG | 268 | 3983 | 0.03 | 1 | 0.15 | 0.15 | 0.01 |
| Other * | 41,655 | 1,139,247 | 7.74 | 605 | 308 | 308 | 10.03 |
| Process | CMOS 180 nm | |
| Cores | Rocket | |
| ISA | RV32GC | |
| Caches | Instruction | 16-KB (Rocket) + 4-KB (Ibex) |
| Data | 16-KB (Rocket) + 4-KB (Ibex) | |
| L2 | 512-KB | |
| Die | 5.0 × 5.0-mm2 | |
| 4560.52 × 4561.16-m2 | ||
| Area | Core | =20.79-mm2 |
| ≈1,535,406-NAND2 | ||
| Cell | 466,882 | |
| MOSFET | 7,982,582 | |
| VDD | I/O | 1.8-V |
| Core | 1.0-V to 2.0-V | |
| Peak performance | at 2.0-V = 30-MHz = 7.6-mW/MHz | |
| Core | ISA | Dhrystone/s | DMIPS/MHz | Changes |
|---|---|---|---|---|
| Rocket | RV64GC | 150,511 | 1.713 | 3.95× |
| RV32IMC | 138,197 | 1.573 | 3.62× | |
| IBex | RV32IMC | 38,165 | 0.434 | 1.00× |
 , and ○, respectively, rank the performance from best to worst.
, and ○, respectively, rank the performance from best to worst.
 , and ○, respectively, rank the performance from best to worst.
, and ○, respectively, rank the performance from best to worst.| CURE | HECTOR-V | WorldGuard | ITUS | This | |
|---|---|---|---|---|---|
| [22] | [48] | [49] | [46,47] | Work | |
| Open-source | ○ | ○ |  | ○ |  |
| Secure boot |  | ● |  | ● | ● |
| Flexible boot | ● | ● | ● | ○ | ● |
| TEE isolation | ○ | ○ | ○ | ● | ● |
| Exclusive TEE processor |  | ● |  | ○ | ○ |
| Exclusive secure storage | ○ | ● | ○ | ● | ● |
| Secure I/O paths | ● | ● |  | ○ | ○ |
| Crypto. accel. | ○ | ○ |  | ● | ● |
| SCA resilience | ● | ● |  | ○ | ○ |
| Hardware cost | ● |  | ● | ○ |  |
| High expressiveness |  | ● |  | ○ |  |
| Low porting efforts | ○ | ○ |  | ● | ● |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kieu-Do-Nguyen, B.; Nguyen, K.-D.; Dang, T.-K.; The Binh, N.; Pham-Quoc, C.; Tran, N.-T.; Pham, C.-K.; Hoang, T.-T. A Trusted Execution Environment RISC-V System-on-Chip Compatible with Transport Layer Security 1.3. Electronics 2024, 13, 2508. https://doi.org/10.3390/electronics13132508
Kieu-Do-Nguyen B, Nguyen K-D, Dang T-K, The Binh N, Pham-Quoc C, Tran N-T, Pham C-K, Hoang T-T. A Trusted Execution Environment RISC-V System-on-Chip Compatible with Transport Layer Security 1.3. Electronics. 2024; 13(13):2508. https://doi.org/10.3390/electronics13132508
Chicago/Turabian StyleKieu-Do-Nguyen, Binh, Khai-Duy Nguyen, Tuan-Kiet Dang, Nguyen The Binh, Cuong Pham-Quoc, Ngoc-Thinh Tran, Cong-Kha Pham, and Trong-Thuc Hoang. 2024. "A Trusted Execution Environment RISC-V System-on-Chip Compatible with Transport Layer Security 1.3" Electronics 13, no. 13: 2508. https://doi.org/10.3390/electronics13132508
APA StyleKieu-Do-Nguyen, B., Nguyen, K.-D., Dang, T.-K., The Binh, N., Pham-Quoc, C., Tran, N.-T., Pham, C.-K., & Hoang, T.-T. (2024). A Trusted Execution Environment RISC-V System-on-Chip Compatible with Transport Layer Security 1.3. Electronics, 13(13), 2508. https://doi.org/10.3390/electronics13132508






