Multi-Objective Region Encryption Algorithm Based on Adaptive Mechanism
Abstract
1. Introduction
2. Adaptive Mechanism Encryption Algorithm
2.1. Improved Polygon Segmentation Algorithm
| Algorithm 1: Polygon segmentation Algorithm |
| Input: yolov8 output rectangle yolo_res Output: The split rectangle list box_list 1. input_box = [box[2:] for box in yolo_res] 2. for i = 0 to len((input_box) do 3. union_flage = false 4. for j = i + 1 to len(input_box) do 5. if input_ box [i] intersects input_rec [j] then 6. Input_box[i] = input_box[i] and input_box[j] joint polygons 7. Delete input_box[j] 8. union_flage = true 9. end if 10. end for 11. if not union_flage 12. input_box[i] ->box_list 13. Delete input_box[i] 14. end if 15. end for 16. Dimples_list = [Look for the dimples of the polygon ploy for ploy in input_box] // Finding concave vertices 17. Dimples_list = [Sort the points in Dimples for Dimples in Dimples_list] 18. for i = 0 to (len(input_box)) do 19. for j = 0 to (len(Dimples_list[i])) do 20. Vertical_lines = A vertical straight line passing through Dimples_list[i][j] 21. intersections = Vertical_lines the intersection of the line and the polygon input_box[i] 22. for k = 0 to (len(intersections))do 23. Dividing_line = The line segment starts from Dimples_list[i][j] and ends at intersections[k] 24. if Dividing_line does not intersect with the polygon input_box[i] 25. if intersections[k] in the dimple set Dimples_list[i] 26. Dimples_list[i].remove(intersections[k]) 27. break 28. end if 29. end if 30. end for 31. res1, res2 = Splitting polygons with Dividing_line input_box[i] 32. if res1 is rectangular then 33. res1 -> box_list 34. input_box[i] = res2 35. else 36. input_box[i] = res1 37. res2 -> box_list 38. end if 39. end for 40. end for |
2.2. Encryption Resource Allocation Algorithm
| Algorithm 2: Encryption Resource Allocation Algorithm |
| Input: Yolov8 Output yolo_res, The list of divided small rectangles box_list, En cryption category Priority class_priority, CPU usage threshold cpu_threshold Output: An encrypted list out_box with encrypted properties 1. Get CPU usage cpu_usage 2. if cpu_usage < cpu_threshold[0] 3. All categories are fidelity encrypted using yolo_res -> cpu_box_list 4. else if cpu_usage < cpu_threshold[1] 5. In addition to class_priority [2] adjust the sampling rate encryption, other fidelity encryption using yolo_res -> cpu_box_list 6. else if cpu_usage < cpu_threshold[2] 7. In addition to class_priority[1,2] adjust the sampling rate encryption, other fidelity encryption using yolo_res -> cpu_box_list 8. else 9. All categories are encrypted with adjusted sample rate using yolo_res -> cpu_box_list 10. end if 11. for i in range(len(box_list)) 12. box_list[i].insert(0, 0) 13. for i range(len(cpu_box_list)) 14. if box_list[i] intersects with cpu_res[j] and cpu_box_list[j][0] == 1 15. box_list[i][0] = 1 16. end if 17. end for 18. end for |
2.3. Chaotic Fusion XOR Encryption Algorithm
| Algorithm 3: Chaotic fusion XOR encryption algorithm |
| Input: Plain Image P Output: Cipher Image C Key generation 1. hash = SHA-512(P) 2. 3. // Scrambling phase 4. pixels = img.flatten() // Convert to one dimensional array 5. [valD,idxD] =sort(D) 6. pixels = pixels(idxD) // Chaotic sequence D scrambles pixels // Diffusion stage 7. 8. 9. R = [pixels(1), pixels(2),……pixels(MN)] 10. G = [pixels(MN), pixels(MN + 1),……pixels(2MN)] 11. B = [pixels(2MN), pixels(2MN + 1),……pixels(3MN)] 12. rules = [‘ACGT’,‘CATG’,‘GTAC’,‘TCGA’] // encoding rules 13. //Chaotic sequence F implements the encoding of R, G, B three-channel pixel values 14. 15. 16. rules = [‘ACGT’,‘CATG’,‘GTAC’,‘TCGA’,‘CTAG’,‘AGCT’,‘TGCA’,‘GATC’] // 8 kinds of XOR objects 17. //Chaotic sequence G selects an XOR object for R, G, B three-channel base sequence 18. 19. 20. rules = [‘ACGT’,‘CATG’,‘GTAC’,‘TCGA’] // decoding rules 21. //Chaotic sequence H selects decoding rules for R, G, B three-channel base sequences 22. 23. 24. Cipher = np.arry(R + G + B).reshape(M,N,3) |
3. Adaptive Mechanism Encryption and Decryption Process
3.1. Adaptive Mechanism Encryption Process
| Algorithm 4: Adaptive mechanism encryption process |
| Input: Image to be encrypted, box_list with image fidelity properties [Whether to adjust image, x, y, w, h] Output: Ciphertext with steganographic data content. 1. for i = len(box_list)do 2. img = input_img(box_list[i]) 3. write_box.append(box_list[i][1]:[4]) // Save the pixel source area [x, y, w, h] 4. if box_list[i][0] == 1 then // Do not adjust the sampling rate 5. write_box.append(box_list[i][1]:[4]) //[x, y, w1, h1] 6. encrypt_img = Gets the encrypt_key from img and encrypts img with the encrypt_key 7. write_key.append(encrypt_key) 8. writes encrypt_img to the [x, y, w1, h1] region of out_img 9. else then //Adjust sampling rate 10. zip_rec = box_list[i][1]:[2] + [ box_list[i][3]/2] + [ box_list[i][4]/2] 11. write_box.append(zip_rec) //[x,y,w1,h1] 12. img = img.resize(box_list[i][3]/2, box_list[i][4]/2) 13. encrypt_img = Gets the encrypt_key from img and encrypts img with the encrypt_key 14. write_key.append(encrypt_key) 15. encode_back = encode_img.resize(box_list[i][3], box_list[i][4]) // Fill the background area 16. Writes encode_back to the [x, y, w, h] region of out_img and encrypt_img to the [x, y, w1, h1] region 17. end if 18. end for 19. Cipher image = LSB_write(write_box, write_key, out_img) |
3.2. Adaptive Mechanism Decryption Process
| Algorithm 5: Adaptive encryption algorithm decryption process |
| Input: Cipher image Output: Plain image 1. read_box,read_key = LSB_read(Cipher) // Read the steganographic key and the location of the encryption region from the ciphertext 2. for i = 0 to len(read_box) do 3. img = input_img(read_box[]) // [x, y, w1, h1] 4. decrypt_img = Decrypts img with key[i] 5. if w1 = w and h1 = h then 6. out_img = img 7. else 8. out_img = img.resize(read_box[][2], read_box[][3]) 9. end if 10. Save out_img to the region [x, y, w, h] of the image Cipher 11. end for |
4. Experiment
4.1. Experimental Process
4.2. Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Vijayakumar, M.; Ahilan, A. An optimized chaotic S-box for real-time image encryption scheme based on 4-dimensional memristive hyperchaotic map. Ain Shams Eng. J. 2024, 15, 102620. [Google Scholar] [CrossRef]
- Liu, H.; Teng, L.; Unar, S.; Liu, P.; Wang, X. Fingerprint image encryption based on chaos and nonlinear dynamic “X” model diffusion. J. Inf. Secur. Appl. 2024, 82, 103723. [Google Scholar] [CrossRef]
- Toktas, F.; Erkan, U.; Yetgin, Z. Cross-channel color image encryption through 2D hyperchaotic hybrid map of optimization test functions. Expert Syst. Appl. 2024, 249, 123583. [Google Scholar] [CrossRef]
- Liu, X.; Tong, X.; Zhang, M.; Wang, Z. Constructing of n-dimensional non-degenerate chaotic maps and its application for robust image encryption. Appl. Math. Model. 2024, 130, 16–24. [Google Scholar] [CrossRef]
- Zhang, H.; Hu, H.; Ding, W. VSDHS-CIEA: Color image encryption algorithm based on novel variable-structure discrete hyperchaotic system and cross-plane confusion strategy. Inf. Sci. 2024, 665, 120332. [Google Scholar] [CrossRef]
- Wang, X.; Liu, P. A new full chaos coupled mapping lattice and its application in privacy image encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 69, 1291–1301. [Google Scholar] [CrossRef]
- Masood, F.; Boulila, W.; Alsaeedi, A.; Khan, J.S.; Ahmad, J.; Khan, M.A.; Rehman, S.U. A novel image encryption scheme based on Arnold cat map, Newton-Leipnik system and Logistic Gaussian map. Multimed. Tools Appl. 2022, 81, 30931–30959. [Google Scholar] [CrossRef]
- Ye, G.; Jiao, K.; Huang, X. Quantum logistic image encryption algorithm based on SHA-3 and RSA. Nonlinear Dyn. 2021, 104, 2807–2827. [Google Scholar] [CrossRef]
- Ur Rehman, A.; Liao, X.; Ashraf, R.; Ullah, S.; Wang, H. A color image encryption technique using exclusive-OR with DNA complementary rules based on chaos theory and SHA-2. Optik 2018, 159, 348–367. [Google Scholar] [CrossRef]
- Almasoud, A.S.; Alabduallah, B.; Alqahtani, H.; Aljameel, S.S.; Alotaibi, S.S.; Mohamed, A. Chaotic image encryption algorithm with improved bonobo optimizer and DNA coding for enhanced security. Heliyon 2024, 10, e25257. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, G.; Di, J. An image encryption scheme based on the four-dimensional chaotic system and the mealy finite state machine. Phys. Scr. 2024, 99, 055204. [Google Scholar] [CrossRef]
- Khan, F.A.; Ahmed, J.; Alsuhibany, S.A. A New Multi Chaos-Based Compression Sensing Image Encryption. Comput. Mater. Contin. 2023, 76, 437–453. [Google Scholar]
- Qian, X.; Yang, Q.; Li, Q.; Liu, Q.; Wu, Y.; Wang, W. A novel color image encryption algorithm based on three-dimensional chaotic maps and reconstruction techniques. IEEE Access 2021, 9, 61334–61345. [Google Scholar] [CrossRef]
- Liang, Q.; Zhu, C. A new one-dimensional chaotic map for image encryption scheme based on random DNA coding. Opt. Laser Technol. 2023, 160, 109033. [Google Scholar] [CrossRef]
- Chen, Z.; Ye, G. An asymmetric image encryption scheme based on hash SHA-3, RSA and compressive sensing. Optik 2022, 267, 169676. [Google Scholar] [CrossRef]
- Wang, X.; Liu, C.; Jiang, D. An efficient double-image encryption and hiding algorithm using a newly designed chaotic system and parallel compressive sensing. Inf. Sci. 2022, 610, 300–325. [Google Scholar] [CrossRef]
- Liu, H.; Teng, L.; Zhang, Y.; Si, R.; Liu, P. Mutil-medical image encryption by a new spatiotemporal chaos model and DNA new computing for information security. Expert Syst. Appl. 2024, 235, 121090. [Google Scholar] [CrossRef]
- Xue, H.W.; Du, J.; Li, S.L.; Ma, W.J. Region of interest encryption for color images based on a hyperchaotic system with three positive Lyapunov exponets. Opt. Laser Technol. 2018, 106, 506–516. [Google Scholar] [CrossRef]
- Singh, K.N.; Singh, O.P.; Baranwal, N.; Singh, A.K. An efficient chaos-based image encryption algorithm using real-time object detection for smart city applications. Sustain. Energy Technol. Assess. 2022, 53, 102566. [Google Scholar] [CrossRef]
- Jamal, S.S.; Hazzazi, M.M.; Khan, M.F.; Bassfar, Z.; Aljaedi, A.; ul Islam, Z. Region of interest-based medical image encryption technique based on chaotic S-boxes. Expert Syst. Appl. 2024, 238, 122030. [Google Scholar] [CrossRef]
- Chen, R.; Li, X.; Teng, L.; Wang, X. Selective region medical image encryption algorithm based on cascade chaos and two-dimensional Joseph traversal. Phys. Scr. 2023, 98, 035227. [Google Scholar] [CrossRef]
- Liu, Y.; Qu, X.; Xin, G. A ROI-based reversible data hiding scheme in encrypted medical images. J. Vis. Commun. Image Represent. 2016, 39, 51–57. [Google Scholar] [CrossRef]
- Shan, Y.; He, M.; Yu, Z.; Wu, H. Pixel level image encryption based on semantic segmentation. In Proceedings of the 2018 International Conference on Control, Artificial Intelligence, Robotics & Optimization (ICCAIRO), Prague, Czech Republic, 19–21 May 2018; pp. 147–152. [Google Scholar]
- Wang, X.; Wang, Y. Multiple medical image encryption algorithm based on scrambling of region of interest and diffusion of odd-even interleaved points. Expert Syst. Appl. 2023, 213, 118924. [Google Scholar] [CrossRef]
- Jawad, L.M. A novel region of interest for selective color image encryption technique based on new combination between GLCM texture features. In Proceedings of the 2021 National Computing Colleges Conference (NCCC), Taif, Saudi Arabia, 27–28 March 2021; pp. 1–6. [Google Scholar]
- Kayani, M.; Mohsin Riaz, M.; Ghafoor, A. Efficient Region of Interest Encryption Based on a New Chaotic Map. Int. J. Bifurc. Chaos 2022, 32, 2250175. [Google Scholar] [CrossRef]
- Zhang, Z.; Tang, J.; Ni, H.; Huang, T. Image adaptive encryption algorithm using a novel 2D chaotic system. Nonlinear Dyn. 2023, 111, 10629–10652. [Google Scholar] [CrossRef]
- Tuli, R.; Soneji, H.N.; Churi, P. PixAdapt: A novel approach to adaptive image encryption. Chaos Solitons Fractals 2022, 164, 112628. [Google Scholar] [CrossRef]
- Eppstein, D. Graph-theoretic solutions to computational geometry problems. In International Workshop on Graph-Theoretic Concepts in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1–16. [Google Scholar]
- Patro, K.A.K.; Acharya, B. An efficient dual-layer cross-coupled chaotic map security-based multi-image encryption system. Nonlinear Dyn. 2021, 104, 2759–2805. [Google Scholar] [CrossRef]
- Zhang, Z.; Cao, Y.; Jahanshahi, H.; Mou, J. Chaotic color multi-image compression-encryption/LSB data type steganography scheme for NFT transaction security. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101839. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Lone, P.N.; Mir, U.H.; Gaffar, A. Hyperchaotic image encryption using DNA coding and discrete cosine transform. J. Frankl. Inst. 2023, 360, 13318–13338. [Google Scholar] [CrossRef]
- Lone, P.N.; Singh, D. Application of algebra and chaos theory in security of color images. Optik 2020, 218, 165155. [Google Scholar] [CrossRef]




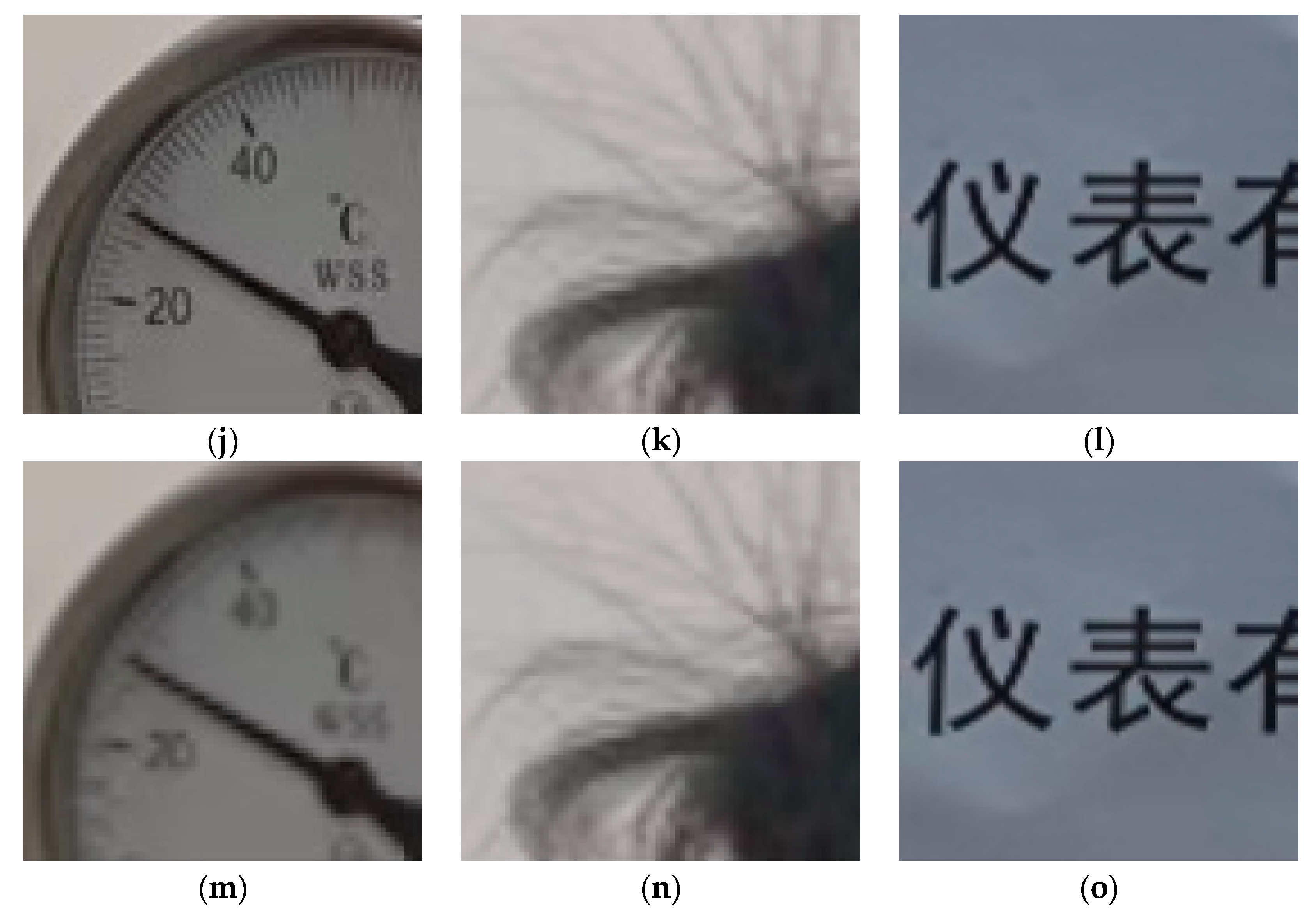
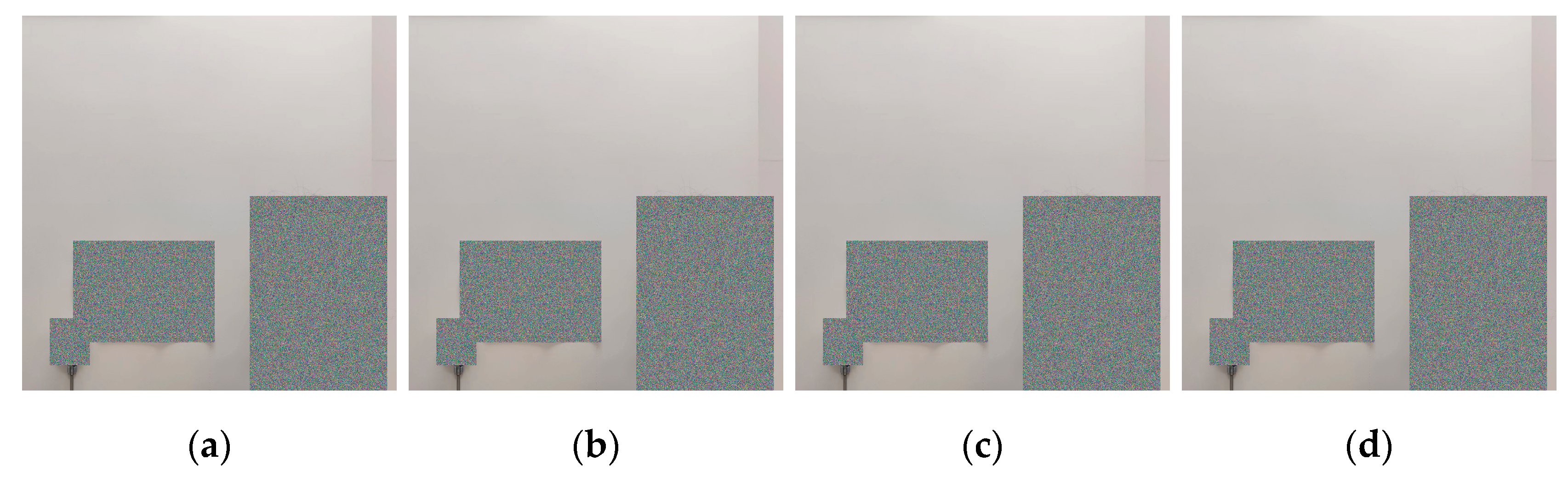

| System | CPU | RAM | Software | Object Detection | Dataset | Model |
|---|---|---|---|---|---|---|
| Win11 | Inter Core i7-11390H, CPU@3.40 GHz 3.42 GHz | 16 GB | Pycharm Communit 2022 | Yolov8 | Self-built, including about 800 pictures of instruments | multi_encode.onnx |
| Image | NPCR | UACI | ||||
|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |
| clock | 99.6323 | 99.6091 | 99.5718 | 33.3300 | 33.4198 | 33.2817 |
| board | 99.6283 | 99.5945 | 99.5978 | 33.4108 | 33.4391 | 33.5169 |
| people | 99.6198 | 99.6049 | 99.5923 | 33.4490 | 33.4290 | 33.5218 |
| Image | Direction | Plain Cropped Image | Encrypted Cropped Image | ||||
|---|---|---|---|---|---|---|---|
| R | G | B | R | G | B | ||
| Horizontal | 0.9932 | 0.9929 | 0.9280 | −0.0039 | −0.0045 | −0.0204 | |
| people | Vertical | 0.9940 | 0.9938 | 0.9931 | 0.0067 | −0.0140 | −0.0376 |
| Diagonal | 0.9895 | 0.9902 | 0.9888 | 0.0057 | −0.0044 | −0.0023 | |
| Horizontal | 0.9819 | 0.9815 | 0.9782 | −0.0154 | −0.0159 | −0.0151 | |
| clock | Vertical | 0.9742 | 0.9742 | 0.9775 | 0.0324 | −0.0377 | −0.0399 |
| Diagonal | 0.9746 | 0.9593 | 0.9595 | −0.0064 | −0.0082 | −0.0277 | |
| Horizontal | 0.9539 | 0.9532 | 0.9598 | −0.0227 | −0.0010 | 0.0074 | |
| board | Vertical | 0.9551 | 0.9555 | 0.9506 | −0.0257 | −0.0021 | 0.0089 |
| Diagonal | 0.9199 | 0.9080 | 0.9154 | −0.0096 | −0.0197 | −0.0080 | |
| Image | Horizontal | Vertical | Diagonal | |
|---|---|---|---|---|
| Peppers | Ref. [8] | 0.0012 | −0.0017 | 0.0023 |
| Ref. [13] | 0.0016 | −0.0013 | 0.0011 | |
| ours | −0.0066 | −0.0095 | −0.0084 | |
| Lena | Ref. [6] | −0.001 | 0.0025 | −0.0067 |
| Ref. [14] | 0.001045 | 0.001042 | 0.000325 | |
| ours | −0.0170 | −0.0200 | −0.0047 |
| Image | ROI Size | CPU Utilization | Encrypt Time (s) | Decrypt Time (s) |
|---|---|---|---|---|
| image1 | unjustment | 9.6843 | 10.3964 | |
| (30%,50%) | 8.9383 | 9.3633 | ||
| (50%,70%) | 3.6093 | 3.3798 | ||
| >70% | 2.9824 | 2.4863 |
| Algorithm | Encryption Time | Decryption Time | Computer Configuration |
|---|---|---|---|
| Ref. [9] | 3.4826 | 3.9547 | A PC with Intel Core i7-11390H, CPU@3.40 GHz 3.42 GHz, 16 GB RAM, pycharm 2022 community |
| Ref. [7] | 2.000 | NA | A PC with Intel Core (TM) i5-4200U CPU @1.6 GHz, 8 GB RAM, MATLAB 2017(a) |
| Ref. [14] | 0.9654 | 0.8181 | A PC with AMD R7 5800H CPU 3.20 GHz, 16.0 GB RAM, MATLAB R2019a |
| Ours | 0.4595 | 0.4643 | A PC with Intel Core i7-11390H, CPU@3.40 GHz 3.42 GHz, 16 GB RAM, pycharm 2022 community |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, J.; Gao, B.; Xiong, X.; Liu, Z.; Pei, C. Multi-Objective Region Encryption Algorithm Based on Adaptive Mechanism. Electronics 2024, 13, 2463. https://doi.org/10.3390/electronics13132463
Wang J, Gao B, Xiong X, Liu Z, Pei C. Multi-Objective Region Encryption Algorithm Based on Adaptive Mechanism. Electronics. 2024; 13(13):2463. https://doi.org/10.3390/electronics13132463
Chicago/Turabian StyleWang, Juan, Boyong Gao, Xingchuang Xiong, Zilong Liu, and Chenbo Pei. 2024. "Multi-Objective Region Encryption Algorithm Based on Adaptive Mechanism" Electronics 13, no. 13: 2463. https://doi.org/10.3390/electronics13132463
APA StyleWang, J., Gao, B., Xiong, X., Liu, Z., & Pei, C. (2024). Multi-Objective Region Encryption Algorithm Based on Adaptive Mechanism. Electronics, 13(13), 2463. https://doi.org/10.3390/electronics13132463







