Joint Optimization of User Scheduling, Flight Path and Power Allocation in a UAV Secure Communication System
Abstract
1. Introduction
- •
- A joint optimization scheme of user scheduling, UAV flight path, and transmit power control is proposed. In the proposed optimization scheme, firstly, the relationship between UAV position and air–ground communication channel is deeply analyzed, and a time-varying channel model is established. Then, the optimization problem of maximizing the minimum secrecy rate of the system is formulated.
- •
- Given that the objective function of the optimization problem is a multivariate nonconvex function, and the problem includes numerous nonconvex constraints, it presents significant challenges to solve directly. Therefore, the optimization problem is initially decomposed through a combination of variable substitution and the difference of convex method, resulting in several univariate optimization problems. Subsequently, each subproblem is tackled by alternating iteration, ultimately yielding the UAV flight path and resource allocation that achieve optimal performance.
- •
- The simulation results verify the effectiveness and feasibility of the proposed algorithm, and verify that the proposed scheme is superior to other benchmark schemes, which can effectively improve the minimum security rate of the system and ensure the quality of service of users.
2. System Model and Problem Formulation
3. Proposed Algorithm
3.1. User Scheduling Optimization
3.2. Flight Path Optimization
3.3. Transmit Power Optimization
3.4. Overall Algorithm and Convergence
| Algorithm 1 Alternating iteration algorithm for problem (9). |
|
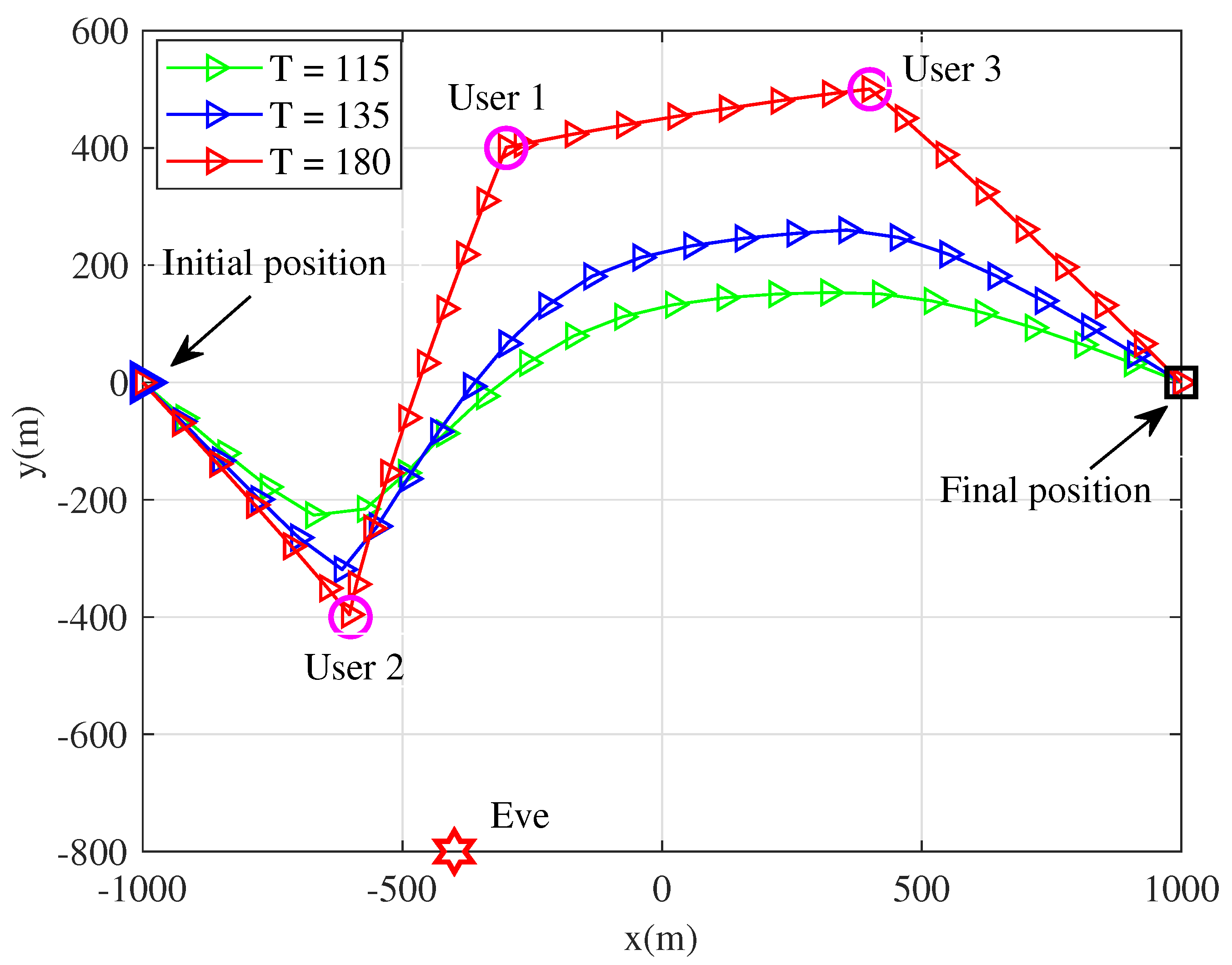
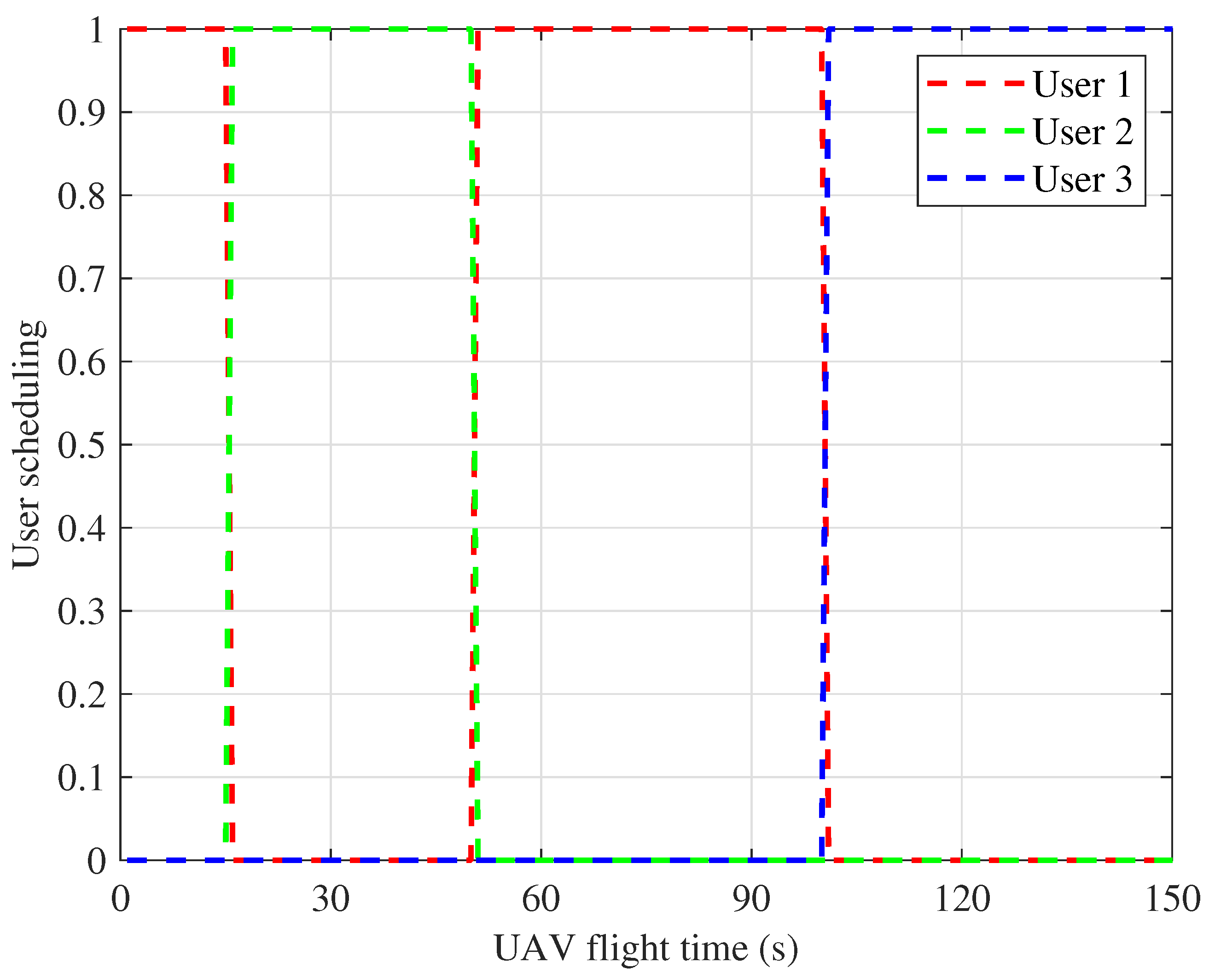
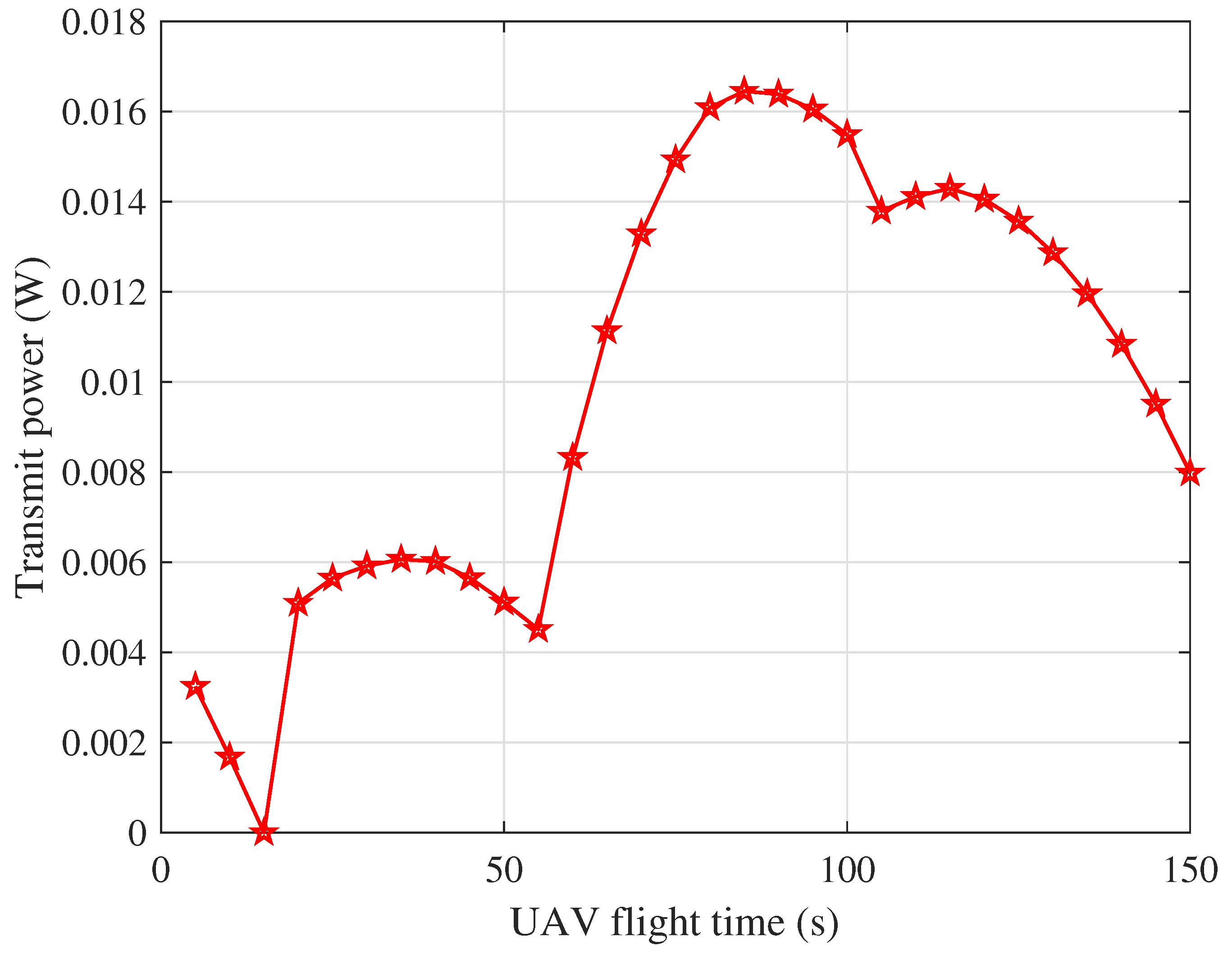
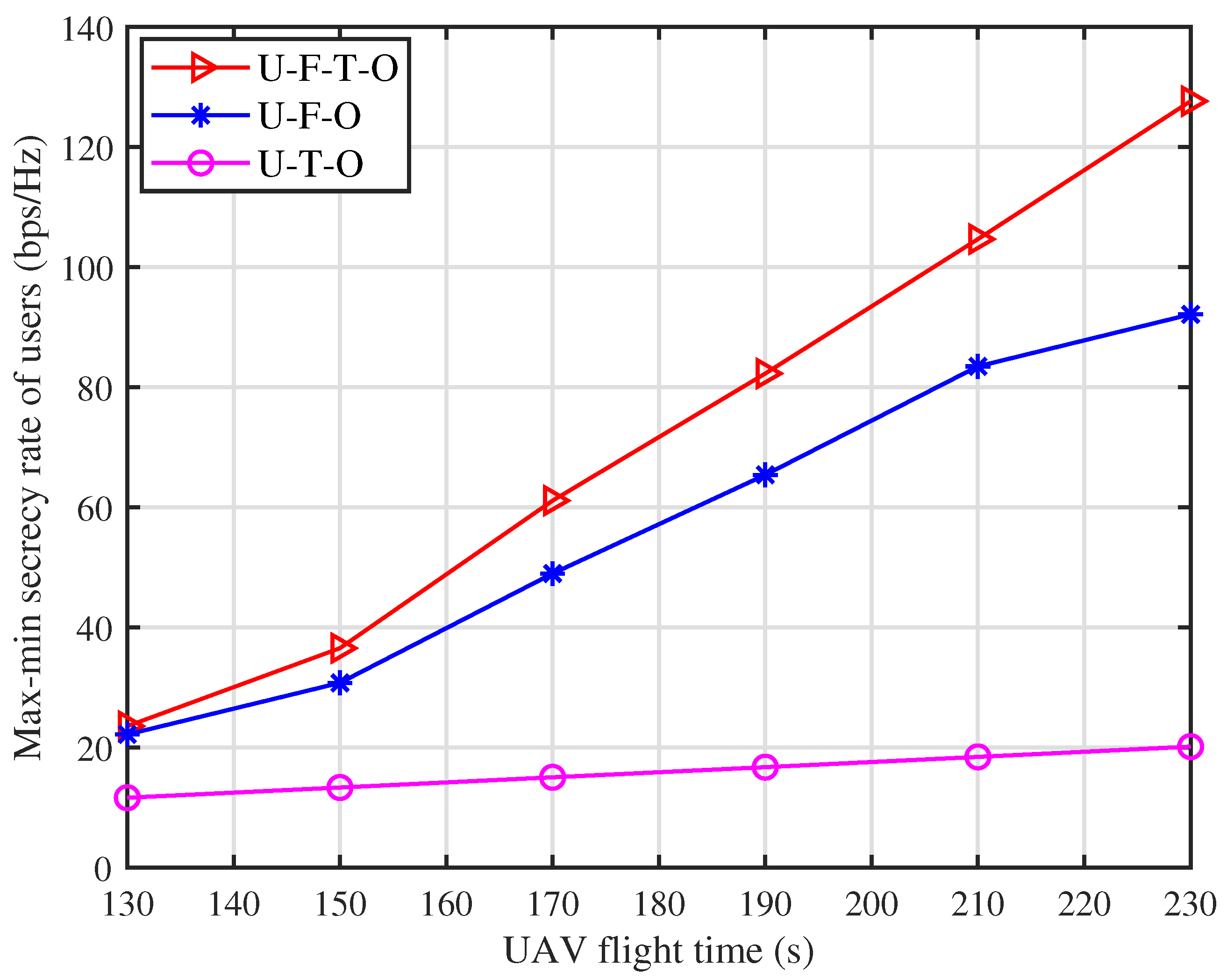
4. Numerical Results and Discussions
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, Z.; Zheng, J. Rate Meta Distribution of Downlink Base Station Cooperation for Cellular-Connected UAV Networks. IEEE Commun. Lett. 2022, 27, 756–760. [Google Scholar] [CrossRef]
- Li, X.; Yao, R.; Fan, Y.; Wang, P.; Xu, J. Secure Efficiency Map-Enabled UAV Trajectory Planning. IEEE Wirel. Commun. Lett. 2023, 12, 1324–1328. [Google Scholar] [CrossRef]
- Al-Ahmedi, S.A.; Shakir, M.Z.; Zaidi, S.A.R. Optimal 3D UAV Base Station Placement by Considering Autonomous Coverage Hole Detection, Wireless Backhaul and User Demand. J. Commun. Netw. 2020, 22, 467–475. [Google Scholar] [CrossRef]
- Wang, X.; Liu, X.; Cheng, C.T.; Deng, L.; Chen, X.; Xiao, F. A Joint User Scheduling and Trajectory Planning Data Collection Strategy for the UAV-Assisted WSN. IEEE Commun. Lett. 2021, 25, 2333–2337. [Google Scholar] [CrossRef]
- Chen, J.; Tang, J. UAV-Assisted Data Collection for Dynamic and Heterogeneous Wireless Sensor Networks. IEEE Wirel. Commun. Lett. 2022, 11, 1288–1292. [Google Scholar] [CrossRef]
- Ghdiri, O.; Jaafar, W.; Alfattani, S.; Abderrazak, J.B.; Yanikomeroglu, H. Offline and Online UAV-Enabled Data Collection in Time-Constrained IoT Networks. IEEE Trans. Green Commun. Netw. 2021, 5, 1918–1933. [Google Scholar] [CrossRef]
- Liu, T.; Cui, M.; Zhang, G.; Wu, Q.; Chu, X.; Zhang, J. 3D Trajectory and Transmit Power Optimization for UAV-Enabled Multi-Link Relaying Systems. IEEE Trans. Green Commun. Netw. 2021, 5, 392–405. [Google Scholar] [CrossRef]
- Dabiri, M.T.; Sadough, S.M.S. Optimal Placement of UAV-Assisted Free-Space Optical Communication Systems with DF Relaying. IEEE Commun. Lett. 2020, 24, 155–158. [Google Scholar] [CrossRef]
- Li, M.; Tao, X.; Wu, H.; Li, N. Joint Trajectory and Resource Optimization for Covert Communication in UAV-Enabled Relaying Systems. IEEE Trans. Veh. Technol. 2022, 72, 5518–5523. [Google Scholar] [CrossRef]
- Zhang, H.; Shen, L.; Wang, N.; Mu, X. UAV Trajectory Optimization for PHY Secure Communication Against Cooperative Eavesdroppers. In Proceedings of the 2022 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Suzhou, China, 14–16 October 2022; pp. 289–293. [Google Scholar]
- Wang, S.; Li, L.; Ruby, R.; Ruan, X.; Zhang, J.; Zhang, Y. Secrecy-Energy-Efficiency Maximization for UAV-Enabled Two-Way Relay Systems. IEEE Trans. Veh. Technol. 2023, 72, 12900–12911. [Google Scholar] [CrossRef]
- Miao, J.; Zheng, Z. Cooperative Jamming for Secure UAV-Enabled Mobile Relay System. IEEE Access 2020, 8, 48943–48957. [Google Scholar] [CrossRef]
- Dang-Ngoc, H.; Nguyen, D.N.; Ho-Van, K.; Hoang, D.T.; Dutkiewicz, E.; Pham, Q.V.; Hwang, W.J. Secure Swarm UAV-Assisted Communications with Cooperative Friendly Jamming. IEEE Internet Things J. 2022, 9, 25596–25611. [Google Scholar] [CrossRef]
- Duo, B.; Luo, J.; Li, Y.; Hu, H.; Wang, Z. Joint Trajectory and Power Optimization for Securing UAV Communications Against Active Eavesdropping. China Commun. 2021, 18, 88–99. [Google Scholar] [CrossRef]
- Wang, W.; Tang, J.; Zhao, N.; Liu, X.; Zhang, X.Y.; Chen, Y.; Qian, Y. Joint Precoding Optimization for Secure SWIPT in UAV-Aided NOMA Networks. IEEE Trans. Commun. 2020, 68, 5028–5040. [Google Scholar] [CrossRef]
- Diao, D.; Wang, B.; Cao, K.; Dong, R.; Cheng, T. Enhancing Reliability and Security of UAV-Enabled NOMA Communications with Power Allocation and Aerial Jamming. IEEE Trans. Veh. Technol. 2022, 71, 8662–8674. [Google Scholar] [CrossRef]
- Chen, X.; Yang, Z.; Zhao, N.; Chen, Y.; Wang, J.; Ding, Z.; Yu, F.R. Secure Transmission via Power Allocation in NOMA-UAV Networks with Circular Trajectory. IEEE Trans. Veh. Technol. 2020, 69, 10033–10045. [Google Scholar] [CrossRef]
- Zhao, J.; Chen, M.; Yang, Z.; Cang, Y.; Tao, Z.; Lyu, Z.; Huang, C.; Zhang, Z. Secure Resource Allocation for UAV Assisted Joint Sensing and Comunication Networks. In Proceedings of the 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 10–13 April 2022; pp. 1856–1861. [Google Scholar]
- Wang, W.; Li, X.; Wang, R.; Cumanan, K.; Feng, W.; Ding, Z.; Dobre, O.A. Robust 3D-Trajectory and Time Switching Optimization for Dual-UAV-Enabled Secure Communications. IEEE J. Sel. Areas Commun. 2021, 39, 3334–3347. [Google Scholar] [CrossRef]
- Li, Z.; Wang, S.; Wen, M.; Wu, Y.-C. Secure Multicast Energy-Efficiency Maximization With Massive RISs and Uncertain CSI: First-Order Algorithms and Convergence Analysis. IEEE Trans. Wirel. Commun. 2022, 21, 6818–6833. [Google Scholar] [CrossRef]
- Li, Z.; Lin, Q.; Wen, Y.-C.W.M.; Ng, D.W.K.; Nallanathan, A. Enhancing Physical Layer Security With RIS Under Multi-Antenna Eavesdroppers and Spatially Correlated Channel Uncertainties. IEEE Trans. Commun. 2024, 72, 1532–1547. [Google Scholar] [CrossRef]
- Luo, X.; Xie, J.; Xiong, L.; Wang, Z.; Tian, C. 3-D Deployment of Multiple UAV-Mounted Mobile Base Stations for Full Coverage of IoT Ground Users with Different QoS Requirements. IEEE Commun. Lett. 2022, 26, 3009–3013. [Google Scholar] [CrossRef]
- Guan, X.; Huang, Y.; Dong, C.; Wu, Q. User Association and Power Allocation for UAV-Assisted Networks: A Distributed Reinforcement Learning Approach. China Commun. 2020, 17, 110–122. [Google Scholar] [CrossRef]
- Sazak, M.D.; Demirtas, A.M. UAV-BS Trajectory Optimization Under Coverage, Backhaul and QoS Constraints Using Q-Learning. In Proceedings of the 2022 International Balkan Conference on Communications and Networking (BalkanCom), Sarajevo, Bosnia and Herzegovina, 22–24 August 2022; pp. 157–161. [Google Scholar]
- Lin, X.; Yajnanarayana, V.; Muruganathan, S.D.; Gao, S.; Asplund, H.; Maattanen, H.L.; Bergstrom, M.; Euler, S.; Wang, Y.P. The Sky Is Not the Limit: LTE for Unmanned Aerial Vehicles. IEEE Commun. Mag. 2018, 56, 204–210. [Google Scholar] [CrossRef]
- Mengali, U. Synchronization Techniques for Digital Receivers, 3rd ed.; University of Pisa: Pisa, Italy, 1997. [Google Scholar]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming, Version 2.1; CVX Research, Inc.: Austin, TX, USA, 2014. [Google Scholar]
- Nemirovski, A.S.; Todd, M.J. Interior-Point Methods for Optimization. Acta Numerica 2008, 17, 191–234. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, L.; Yao, R.; Xie, Y.; Fan, Y.; Zuo, X.; Xu, J.; Zhong, R.; Zheng, S.; Li, X. Joint Optimization of User Scheduling, Flight Path and Power Allocation in a UAV Secure Communication System. Electronics 2024, 13, 2443. https://doi.org/10.3390/electronics13132443
Liu L, Yao R, Xie Y, Fan Y, Zuo X, Xu J, Zhong R, Zheng S, Li X. Joint Optimization of User Scheduling, Flight Path and Power Allocation in a UAV Secure Communication System. Electronics. 2024; 13(13):2443. https://doi.org/10.3390/electronics13132443
Chicago/Turabian StyleLiu, Lipei, Rugui Yao, Yi Xie, Ye Fan, Xiaoya Zuo, Juan Xu, Ruikang Zhong, Shijie Zheng, and Xudong Li. 2024. "Joint Optimization of User Scheduling, Flight Path and Power Allocation in a UAV Secure Communication System" Electronics 13, no. 13: 2443. https://doi.org/10.3390/electronics13132443
APA StyleLiu, L., Yao, R., Xie, Y., Fan, Y., Zuo, X., Xu, J., Zhong, R., Zheng, S., & Li, X. (2024). Joint Optimization of User Scheduling, Flight Path and Power Allocation in a UAV Secure Communication System. Electronics, 13(13), 2443. https://doi.org/10.3390/electronics13132443






