Recommendations for Responding to System Security Incidents Using Knowledge Graph Embedding
Abstract
:1. Introduction
- We propose a method to recommend security incident response strategies in edge computing, using the automatic generation of security knowledge graphs and knowledge graph embedding. We design an EdgeSecurity–BERT model that performs text extraction and preprocessing based on the latest security vulnerability data and extracts entity and relationship information, which is a component of a knowledge graph. In addition, we propose a method to recommend edge computing security incident response strategies through knowledge graph embedding;
- In the process of automatically creating EdgeSecurityKG, we measure the similarities of security vulnerabilities to effectively reflect the latest security technology trends and security threat rankings;
- We propose a knowledge graph embedding method for security incident response. We present a method for determining responses to security incidents, utilizing the generated EdgeSecurityKG.
2. Related Work
2.1. Intelligent Security Incident Responses
2.2. Knowledge Graph Embedding and Completion
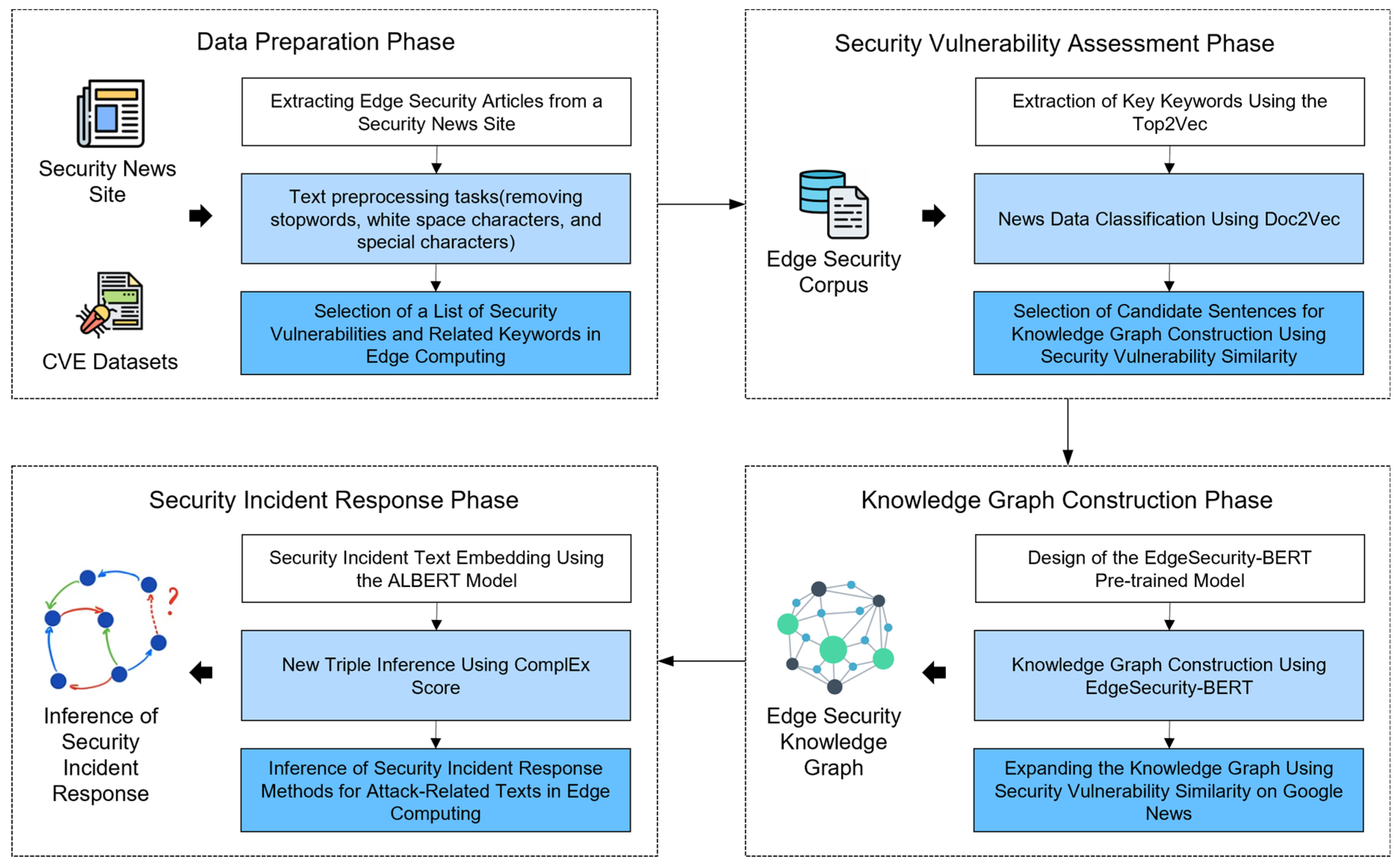
3. Recommendations for Responding to Security Incidents Using Knowledge Graph Embedding
3.1. Overall Process
3.2. Edge Computing Security Data Classification Using Security Vulnerability Similarities
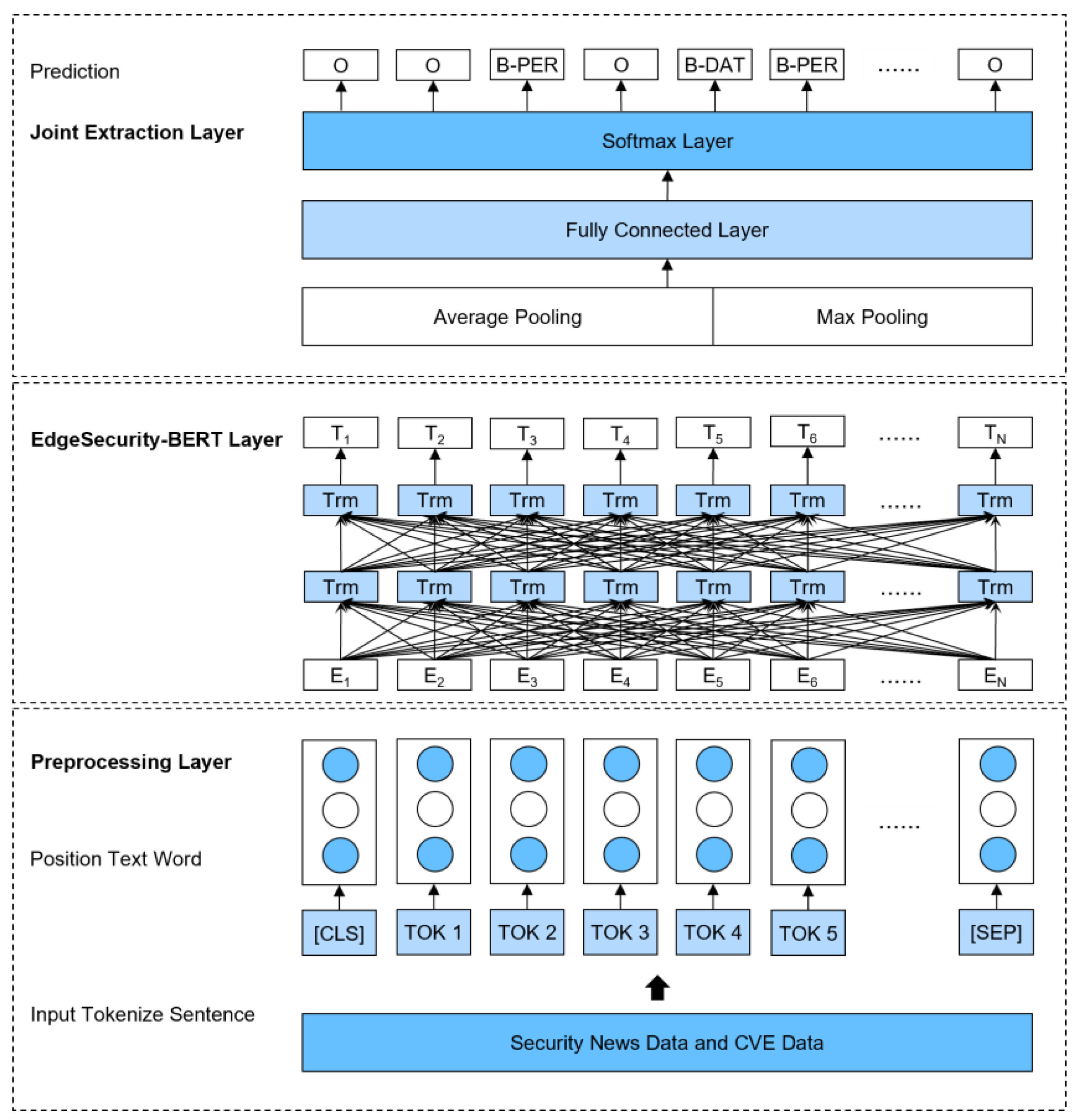
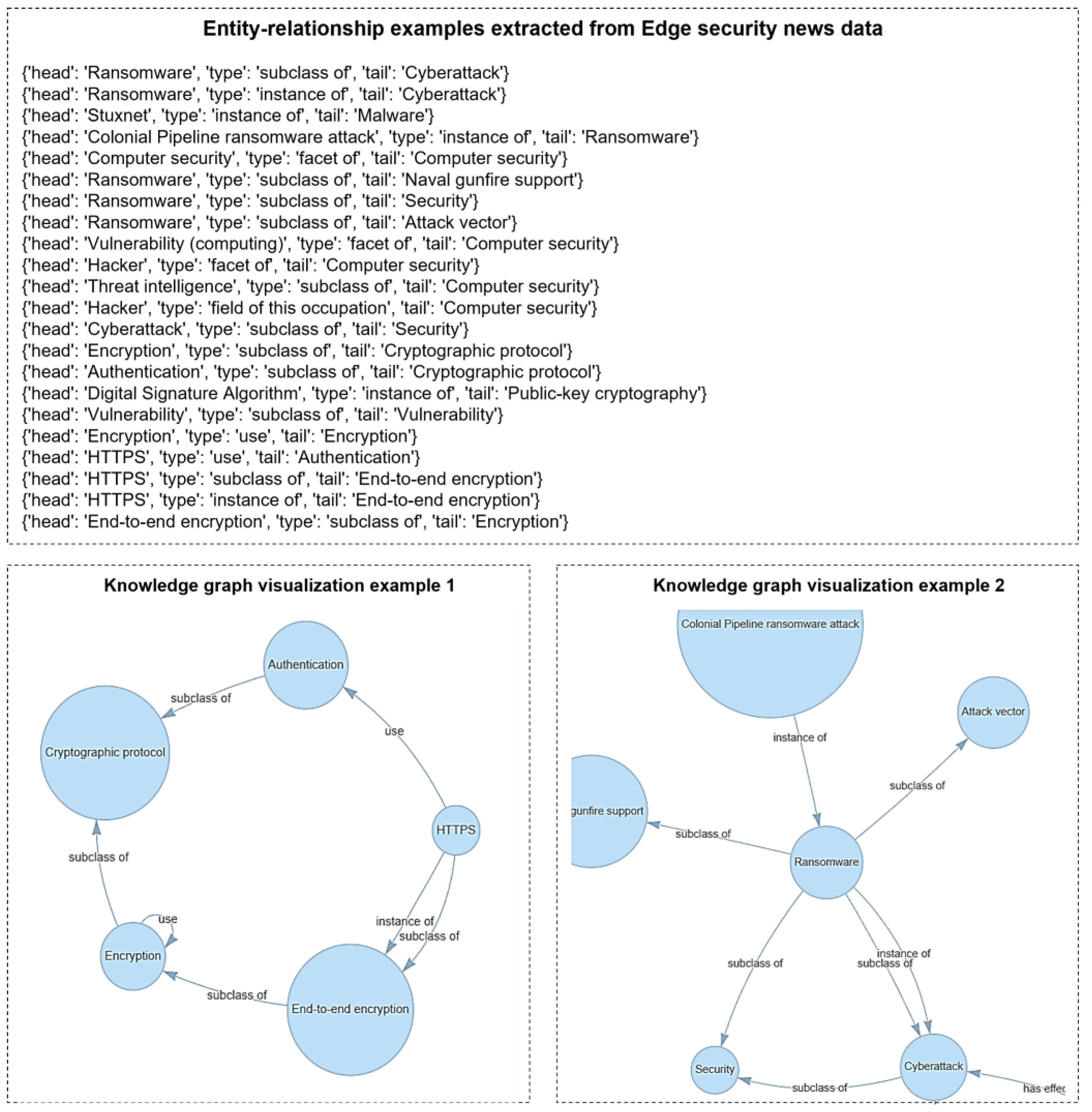
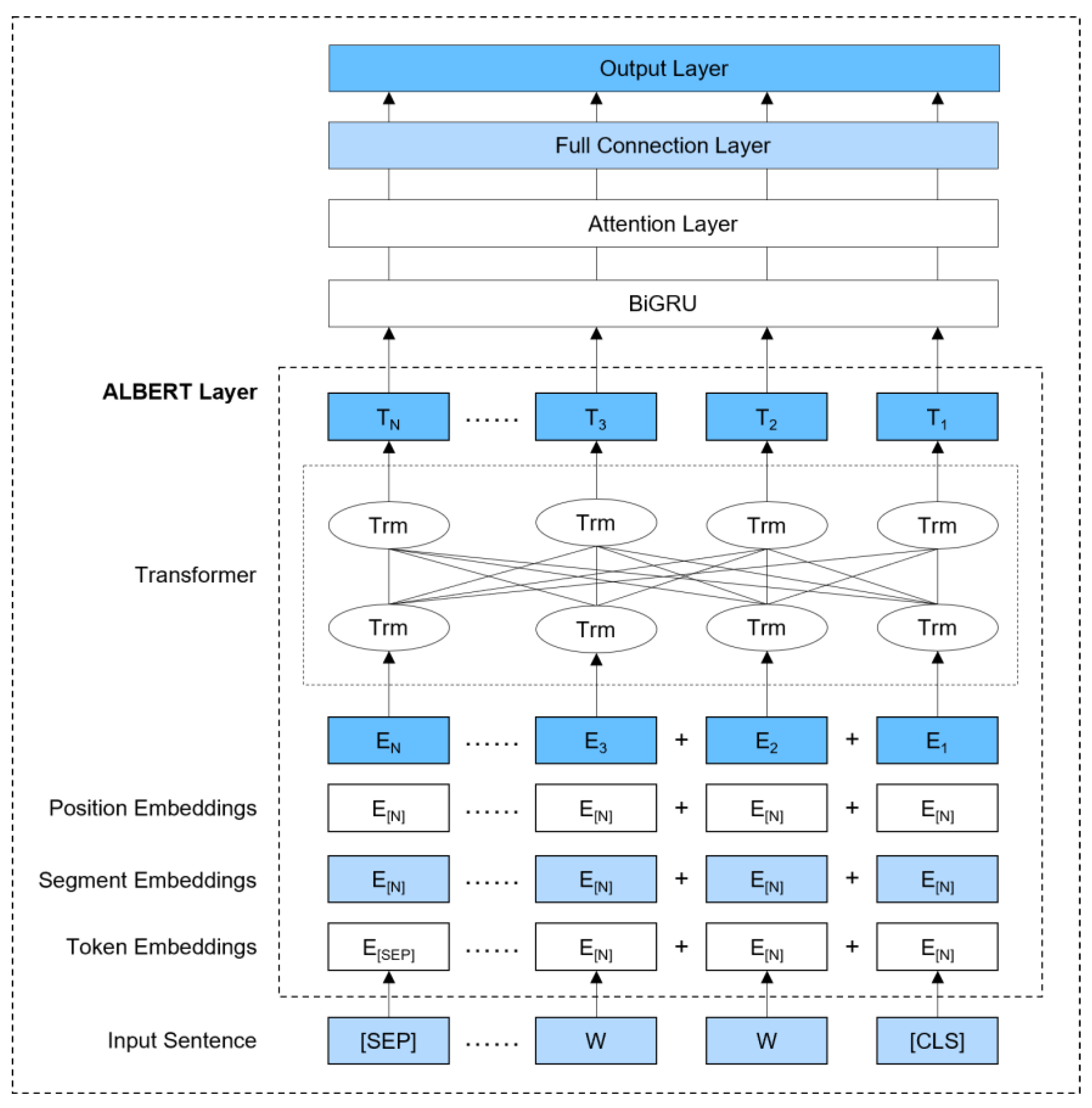
3.3. Automated Generation and Expansion of BERT-Based Edge Computing Security Knowledge Graph
3.4. Knowledge Graph Embedding for Responses to Security Incidents
4. Experiments and Assessment
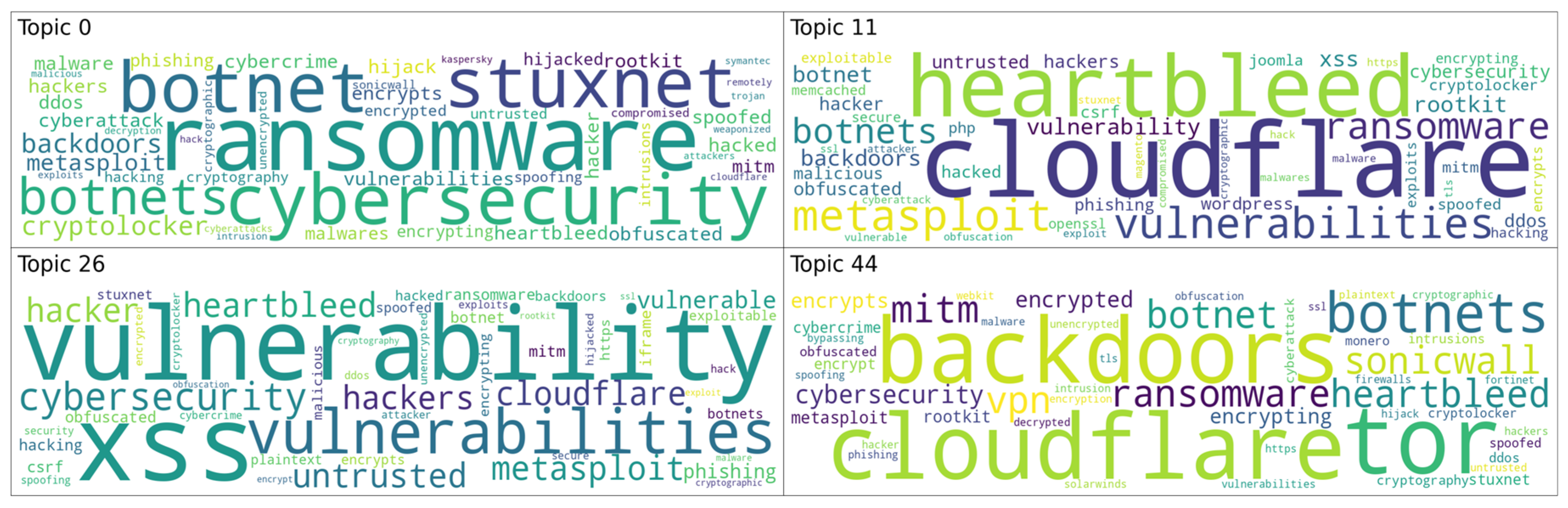
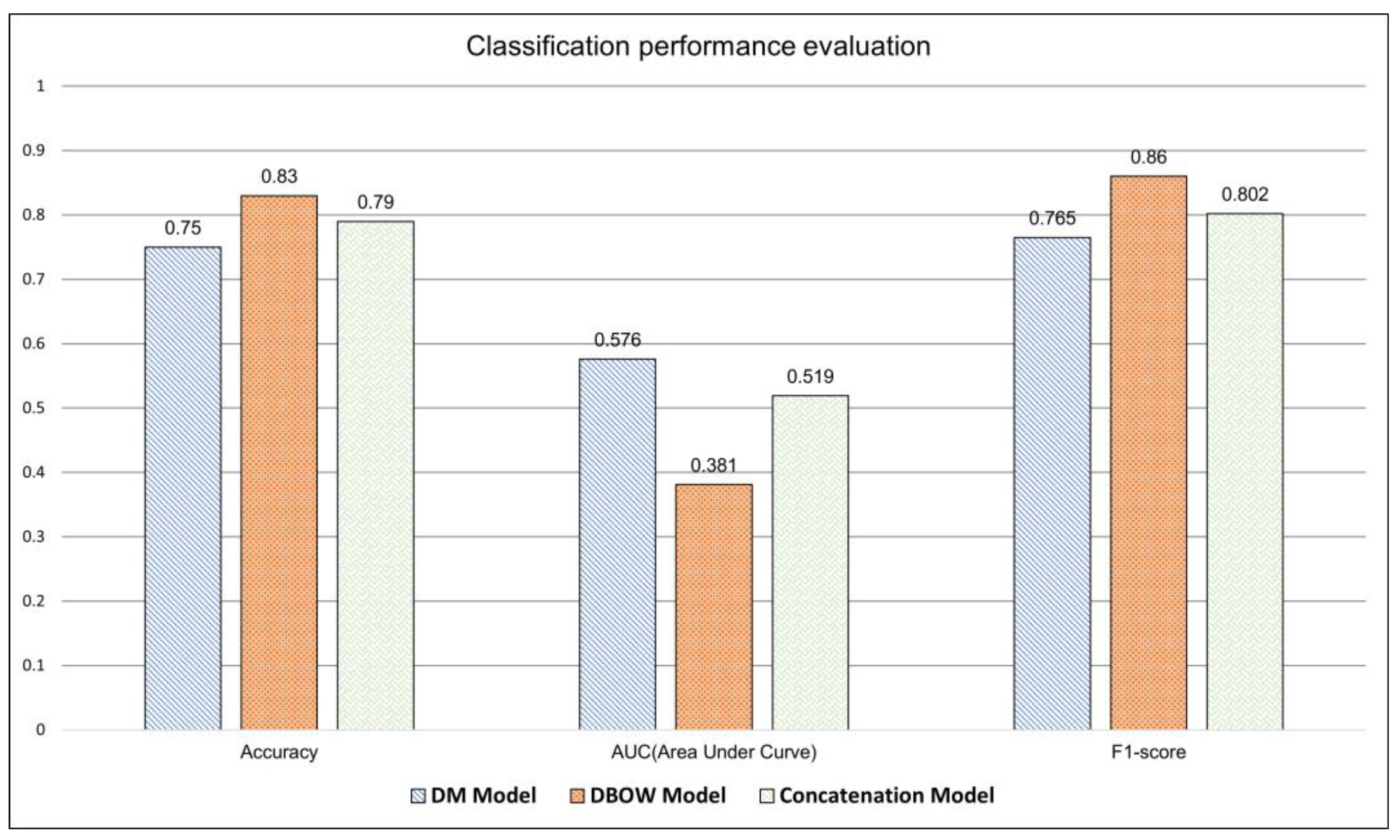
4.1. Experiment on Edge Computing Security Data Classification Using Security Vulnerability Similarity
4.2. Experiment on Knowledge Completion and Relation Prediction for Security Incident Responses
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| BERT | Bidirectional Encoder Representations from Transformers |
| CVE | Common Vulnerabilities and Exposures |
| NER | Named Entity Recognition |
| CLS | Special Classification Token |
| SEP | Special Separator Token |
| UNK | Unknown Token |
| ALBERT | A Lite BERT |
| ReLU | Rectified Linear Unit |
| DDoS | Distributed Denial of Service |
| DM | Distributed Memory |
| DBOW | Distributed Bag of Words |
| MR | Mean Rank |
References
- Kong, L.H.; Tan, J.L.; Huang, J.Q.; Chen, G.H.; Wang, S.T.; Jin, X.; Zeng, P.; Khan, M.; Das, S.K. Edge-computing-driven Internet of Things: A Survey. ACM Comput. Surv. 2022, 55, 1–41. [Google Scholar] [CrossRef]
- Pawlicki, M.; Pawlicka, A.; Kozik, R.; Choras, M. The survey and meta-analysis of the attacks, transgressions, countermeasures and security aspects common to the Cloud, Edge and IoT. Neurocomputing 2023, 551, 126533. [Google Scholar] [CrossRef]
- Kim, J.; Kim, K.; Sohn, M.; Park, G. Deep Model-Based Security-Aware Entity Alignment Method for Edge-Specific Knowledge Graphs. Sustainability 2022, 14, 8877. [Google Scholar] [CrossRef]
- Guo, W.; Chen, H.X.; Hang, F.L.; He, Y.J.; Zhang, J. Learning Representations Using RNN Encoder-Decoder for Edge Security Control. Comput. Intell. Neurosci. 2022, 2022, 4199044. [Google Scholar] [CrossRef] [PubMed]
- Liu, J.; Duan, L. A survey on knowledge graph-based recommender systems. In Proceedings of the 2021 IEEE 5th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 March 2021; pp. 2450–2453. [Google Scholar]
- Wang, P.; Liu, J.J.; Hou, D.D.; Zhou, S.C. A Cybersecurity Knowledge Graph Completion Method Based on Ensemble Learning and Adversarial Training. Appl. Sci. 2022, 12, 12947. [Google Scholar] [CrossRef]
- Ji, S.X.; Pan, S.R.; Cambria, E.; Marttinen, P.; Yu, P.S. A Survey on Knowledge Graphs: Representation, Acquisition, and Applications. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 494–514. [Google Scholar] [CrossRef]
- Pirrò, G. Building relatedness explanations from knowledge graphs. Semant. Web 2019, 10, 963–990. [Google Scholar] [CrossRef]
- Rossi, A.; Barbosa, D.; Firmani, D.; Matinata, A.; Merialdo, P. Knowledge Graph Embedding for Link Prediction: A Comparative Analysis. ACM Trans. Knowl. Discov. Data (TKDD) 2021, 15, 1–49. [Google Scholar] [CrossRef]
- Ma, J.T.; Qiao, Y.Q.; Hu, G.W.; Wang, Y.J.; Zhang, C.Q.; Huang, Y.Z.; Sangaiah, A.K.; Wu, H.G.; Zhang, H.P.; Ren, K. ELPKG: A High-Accuracy Link Prediction Approach for Knowledge Graph Completion. Symmetry 2019, 11, 1096. [Google Scholar] [CrossRef]
- Chao, L.L.; He, J.S.; Wang, T.F.; Chu, W. PairRE: Knowledge Graph Embeddings via Paired Relation Vectors. arXiv 2021, arXiv:2011.03798. [Google Scholar]
- Wang, Q.; Mao, Z.D.; Wang, B.; Guo, L. Knowledge Graph Embedding: A Survey of Approaches and Applications. IEEE Trans. Knowl. Data Eng. 2017, 29, 2724–2743. [Google Scholar] [CrossRef]
- Jaradeh, M.Y.; Oelen, A.; Farfar, K.E.; Prinz, M.; D’Souza, J.; Kismihók, G.; Stocker, M.; Auer, S. Open research knowledge graph: Next generation infrastructure for semantic scholarly knowledge. In Proceedings of the 10th International Conference on Knowledge Capture, Los Angeles, CA, USA, 19–21 November 2019; pp. 243–246. [Google Scholar]
- Mondal, I.; Hou, Y.; Jochim, C. End-to-end construction of NLP knowledge graph. In Findings of the Association for Computational Linguistics: ACL-IJCNLP 2021; Association for Computational Linguistics: Toronto, ON, Canada, 2021; pp. 1885–1895. [Google Scholar]
- Chen, Z.; Wang, Y.; Zhao, B.; Cheng, J.; Zhao, X.; Duan, Z. Knowledge graph completion: A review. IEEE Access 2020, 8, 192435–192456. [Google Scholar] [CrossRef]
- Gesese, G.A.; Biswas, R.; Alam, M.; Sack, H. A survey on knowledge graph embeddings with literals: Which model links better literal-ly? Semant. Web 2021, 12, 617–647. [Google Scholar] [CrossRef]
- Tian, L.; Zhou, X.; Wu, Y.-P.; Zhou, W.-T.; Zhang, J.-H.; Zhang, T.-S. Knowledge graph and knowledge reasoning: A systematic review. J. Electron. Sci. Technol. 2022, 20, 100159. [Google Scholar] [CrossRef]
- Liu, Y. DKG-PIPD: A Novel Method About Building Deep Knowledge Graph. IEEE Access 2021, 9, 137295–137308. [Google Scholar] [CrossRef]
- Chen, X.; Jia, S.; Xiang, Y. A review: Knowledge reasoning over knowledge graph. Expert Syst. Appl. 2020, 141, 112948. [Google Scholar] [CrossRef]
- Zou, X. A survey on application of knowledge graph. J. Phys. Conf. Ser. 2020, 1487, 012016. [Google Scholar] [CrossRef]
- Kazemi, S.M.; Poole, D. SimplE Embedding for Link Prediction in Knowledge Graphs. Adv. Neural Inf. Process. Syst. 2018, 31, 4289–4300. [Google Scholar]
- Sun, H.Y.; Grishman, R. Lexicalized Dependency Paths Based Supervised Learning for Relation Extraction. Comput. Syst. Sci. Eng. 2022, 43, 861–870. [Google Scholar] [CrossRef]
- Portisch, J.; Hladik, M.; Paulheim, H. KGvec2go—Knowledge Graph Embeddings as a Service. arXiv 2020, arXiv:2003.05809. [Google Scholar]
- Nguyen, D.Q. A Survey of Embedding Models of Entities and Relationships for Knowledge Graph Completion. arXiv 2017, arXiv:1703.08098. [Google Scholar]
- Berrendorf, M.; Faerman, E.; Vermue, L.; Tresp, V. Interpretable and Fair Comparison of Link Prediction or Entity Alignment Methods. In Proceedings of the 2020 IEEE/WIC/ACM International Joint Conference on Web Intelligence and Intelligent Agent Technology (WI-IAT), Melbourne, Australia, 14–17 December 2020; pp. 371–374. [Google Scholar]
- Zhao, Y.; Zhang, A.; Xie, R.; Liu, K.; Wang, X. Connecting embeddings for knowledge graph entity typing. arXiv 2020, arXiv:2007.10873. [Google Scholar]
- Jia, N.; Cheng, X.; Su, S. Improving knowledge graph embedding using locally and globally attentive relation paths. In Advances in Information Retrieval, Proceedings of the 42nd European Conference on IR Research, ECIR 2020, Lisbon, Portugal, 14–17 April 2020; Springer: Cham, Switzerland, 2020; pp. 17–32. [Google Scholar]
- Qiu, X.; Sun, T.; Xu, Y.; Shao, Y.; Dai, N.; Huang, X. Pre-trained models for natural language processing: A survey. Sci. China Technol. Sci. 2020, 63, 1872–1897. [Google Scholar] [CrossRef]
- Zouaq, A.; Martel, F. What is the schema of your knowledge graph? Leveraging knowledge graph embeddings and clustering for expressive taxonomy learning. In Proceedings of the International Workshop on Semantic Big Data; Association for Computing Machinery: Portland, OR, USA, 2020; pp. 1–6. [Google Scholar]
- Nickel, M.; Rosasco, L.; Poggio, T. Holographic embeddings of knowledge graphs. arXiv 2015, arXiv:1510.04935. [Google Scholar] [CrossRef]
- Dettmers, T.; Minervini, P.; Stenetorp, P.; Riedel, S. Convolutional 2d knowledge graph embeddings. arXiv 2017, arXiv:1707.01476. [Google Scholar] [CrossRef]
- Wang, B.; Shen, T.; Long, G.D.; Zhou, T.Y.; Wang, Y.; Chang, Y. Structure-Augmented Text Representation Learning for Efficient Knowledge Graph Completion. arXiv 2021, arXiv:2004.14781. [Google Scholar]
- Dutt, R.; Bhattacharjee, K.; Gangadharaiah, R.; Roth, D.; Rose, C. PerKGQA: Question answering over personalized knowledge graphs. In Findings of the Association for Computational Linguistics: NAACL 2022; Association for Computational Linguistics: Seattle, WA, USA, 2022; pp. 253–268. [Google Scholar]
- Kacupaj, E.; Plepi, J.; Singh, K.; Thakkar, H.; Lehmann, J.; Maleshkova, M. Conversational question answering over knowledge graphs with transformer and graph attention networks. arXiv 2021, arXiv:2104.01569. [Google Scholar]
- Mezni, H.; Benslimane, D.; Bellatreche, L. Context-aware service recommendation based on knowledge graph embedding. IEEE Trans. Knowl. Data Eng. 2021, 34, 5225–5238. [Google Scholar] [CrossRef]
- Chen, S.; Liu, X.; Gao, J.; Jiao, J.; Zhang, R.; Ji, Y. Hitter: Hierarchical transformers for knowledge graph embeddings. arXiv 2020, arXiv:2008.12813. [Google Scholar]
- Yao, L.; Mao, C.; Luo, Y. KG-BERT: BERT for knowledge graph completion. arXiv 2019, arXiv:1909.03193. [Google Scholar]
- Tang, X.; Zhang, J.; Chen, B.; Yang, Y.; Chen, H.; Li, C. BERT-INT: A BERT-based interaction model for knowledge graph alignment. In Proceedings of the Twenty-Ninth International Joint Conference on Artificial Intelligence (IJCAI), Yokohama, Japan, 11–17 January 2021; pp. 3174–3180. [Google Scholar]
- Allodi, L.; Massacci, F. Comparing Vulnerability Severity and Exploits Using Case-Control Studies. ACM Trans. Inf. Syst. Secur. (TISSEC) 2014, 17, 1–20. [Google Scholar] [CrossRef]
- Chen, X.; Xie, H.; Li, Z.; Cheng, G. Topic analysis and development in knowledge graph research: A bibliometric review on three decades. Neurocomputing 2021, 461, 497–515. [Google Scholar] [CrossRef]
- Li, J.; Sun, A.X.; Han, J.L.; Li, C.L. A Survey on Deep Learning for Named Entity Recognition. IEEE Trans. Knowl. Data Eng. 2022, 34, 50–70. [Google Scholar] [CrossRef]
- Bouarroudj, W.; Boufaida, Z.; Bellatreche, L. Named entity disambiguation in short texts over knowledge graphs. Knowl. Inf. Syst. 2022, 64, 325–351. [Google Scholar] [CrossRef] [PubMed]
- Devlin, J.; Chang, M.W.; Lee, K.; Toutanova, K. BERT: Pre-training of Deep Bidirectional Transformers for Language Understanding. arXiv 2018, arXiv:1810.04805. [Google Scholar]
- Lakshika, M.; Caldera, H. Knowledge Graphs Representation for Event-Related E-News Articles. Mach. Learn. Mach. Learn. Knowl. Extr. 2021, 3, 802–818. [Google Scholar] [CrossRef]
- Ma, X.; Wang, Z.; Ng, P.; Nallapati, R.; Xiang, B. Universal text representation from bert: An empirical study. arXiv 2019, arXiv:1910.07973 2019. [Google Scholar]
- Opdahl, A.L.; Al-Moslmi, T.; Dang-Nguyen, D.-T.; Gallofré Ocaña, M.; Tessem, B.; Verres, C. Semantic knowledge graphs for the news: A review. ACM Comput. Surv. 2022, 55, 1–38. [Google Scholar] [CrossRef]
- Lan, Z.; Chen, M.; Goodman, S.; Gimpel, K.; Sharma, P.; Soricut, R. Albert: A lite bert for self-supervised learning of language representations. arXiv 2019, arXiv:1909.11942. [Google Scholar]
- Sun, Z.; Huang, J.; Hu, W.; Chen, M.; Guo, L.; Qu, Y. Transedge: Translating relation-contextualized embeddings for knowledge graphs. In Proceedings of the International Semantic Web Conference, Auckland, New Zealand, 26–30 October 2019; pp. 612–629. [Google Scholar]
- Zhang, Y.Y.; Dai, H.J.; Kozareva, Z.; Smola, A.J.; Song, L. Variational Reasoning for Question Answering with Knowledge Graph. arXiv 2017, arXiv:1709.04071. [Google Scholar] [CrossRef]
- Liu, Z.; Jiang, M.; Lin, H. A graph-based spatial temporal logic for knowledge representation and automated reasoning in cognitive robots. arXiv 2020, arXiv:2001.07205. [Google Scholar]
- Kingma, D.P.; Ba, J. Adam: A method for stochastic optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]


| Category | Related Hacking Techniques and Key Keywords |
|---|---|
| Data Leakage | Data Sniffing; Man-in-the-Middle Attacks; Packet Capture |
| Physical Security | Physical Tampering; Hardware Hacking; Lockpicking |
| Device Authentication Management | Credential Theft; Session Hijacking; Password Cracking |
| Network Segregation and Firewalls | Port Scanning; Firewall Evasion; VPN Exploits |
| Updates and Patch Management | Exploiting Known Vulnerabilities; Zero-Day Attacks; Encryption |
| Encryption | Cryptanalysis; Key Cracking; SSL Stripping |
| DDoS Attacks | Botnets; Traffic Flooding; Amplification Attacks |
| Device Complexity | Protocol Manipulation; Firmware Hacking; Configuration Exploits |
| Vulnerabilities of Default Settings | Default Credential Exploitation; Factory Reset Attacks |
| Absence of Logging and Monitoring | Stealth Attacks; Intrusion Concealment; Log Manipulation |
| Example 1 of Security News Data | ||
| As ransomware attacks against critical infrastructure skyrocket, new research shows that threat actors behind such disruptions are increasingly shifting from using email messages as an intrusion route to purchasing access from cybercriminal enterprises that have already infiltrated major targets. “Ransomware operators often buy access from independent cybercriminal groups who… | ||
| CVE-ID | Document Similarity | Security Vulnerability Similarity |
| CVE-2020-6023 | 0.21358260244737504 | 263.1456 |
| CVE-2020-6022 | 0.21188648759031214 | 227.5123 |
| CVE-2020-6012 | 0.1846109167994328 | 158.6411 |
| CVE-2021-42258 | 0.17519347541004693 | 112.5398 |
| CVE-2020-28950 | 0.1750353043365507 | 102.8419 |
| Example 2 of Security News Data | ||
| A new set of critical vulnerabilities has been disclosed in the Realtek RTL8170C Wi-Fi module that an adversary could abuse to gain elevated privileges on a device and hijack wireless communications. “Successful exploitation would lead to the complete control of the Wi-Fi module and potential root access on the OS (such as Linux or Android) of the embedded device that… | ||
| CVE-ID | Document Similarity | Security Vulnerability Similarity |
| CVE-2020-25855 | 0.4746279862237799 | 186.5433 |
| CVE-2020-25856 | 0.21188648759031214 | 227.5123 |
| CVE-2021-43282 | 0.46691596828290133 | 165.8799 |
| CVE-2020-25857 | 0.462240646796948 | 121.5677 |
| CVE-2020-25854 | 0.45093828499370875 | 112.8531 |
| Inference Process | Result |
|---|---|
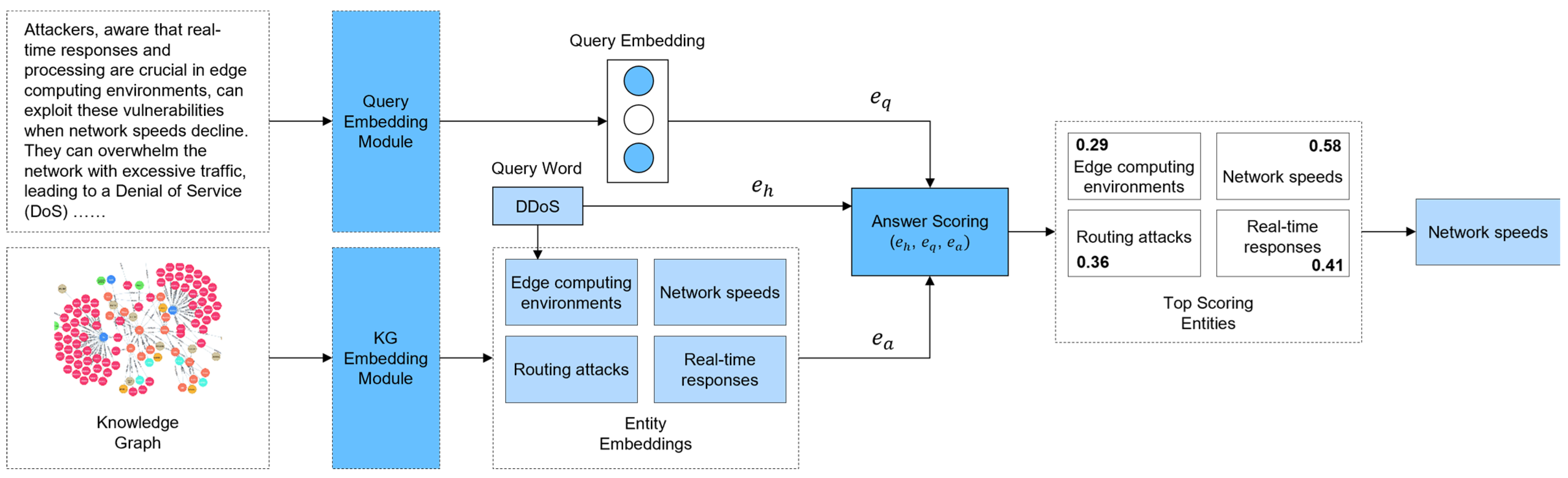
| Attack-related Sample Text | Attackers, aware that real-time responses and processing are crucial in edge computing environments, can exploit these vulnerabilities when network speeds decline. They can overwhelm the network with excessive traffic, leading to a denial-of-service (DoS) or distributed-denial-of-service (DDoS) attack, incapacitating network functionality. They can also conduct routing attacks by manipulating network-routing information to cause service delays. How can these attacks be defended against? |
| Concept Extraction | attackers; real-time responses; edge computing environments; network speeds; excessive traffic; denial of service (DoS); distributed denial of service (DDoS); network functionality; routing attacks; network-routing information; service delays |
| Relationship Extraction |
|
| New Relationship Extraction Using Inference |
|
| Response Method Formula Generated Through Inference Results |
|
| Method | EdgeSecurityKG without Security Vulnerability Similarity Applied | EdgeSecurityKG with Security Vulnerability Similarity Applied | ||
|---|---|---|---|---|
| Metric | MR | Hits@10 | MR | Hits@10 |
| TransE | 512.12 | 0.491 | 614.74 | 0.514 |
| TransH | 491.08 | 0.415 | 531.67 | 0.446 |
| HolE [30] | 152.56 | 0.549 | 212.98 | 0.561 |
| ConvE [31] | 835.81 | 0.311 | 934.51 | 0.42 |
| EdgeSecurity–BERT | 323.76 | 0.674 | 451.87 | 0.783 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, H.; Choi, J. Recommendations for Responding to System Security Incidents Using Knowledge Graph Embedding. Electronics 2024, 13, 171. https://doi.org/10.3390/electronics13010171
Kim H, Choi J. Recommendations for Responding to System Security Incidents Using Knowledge Graph Embedding. Electronics. 2024; 13(1):171. https://doi.org/10.3390/electronics13010171
Chicago/Turabian StyleKim, HyoungJu, and Junho Choi. 2024. "Recommendations for Responding to System Security Incidents Using Knowledge Graph Embedding" Electronics 13, no. 1: 171. https://doi.org/10.3390/electronics13010171
APA StyleKim, H., & Choi, J. (2024). Recommendations for Responding to System Security Incidents Using Knowledge Graph Embedding. Electronics, 13(1), 171. https://doi.org/10.3390/electronics13010171






