Endpoint Device Risk-Scoring Algorithm Proposal for Zero Trust
Abstract
:1. Introduction
2. Related Work
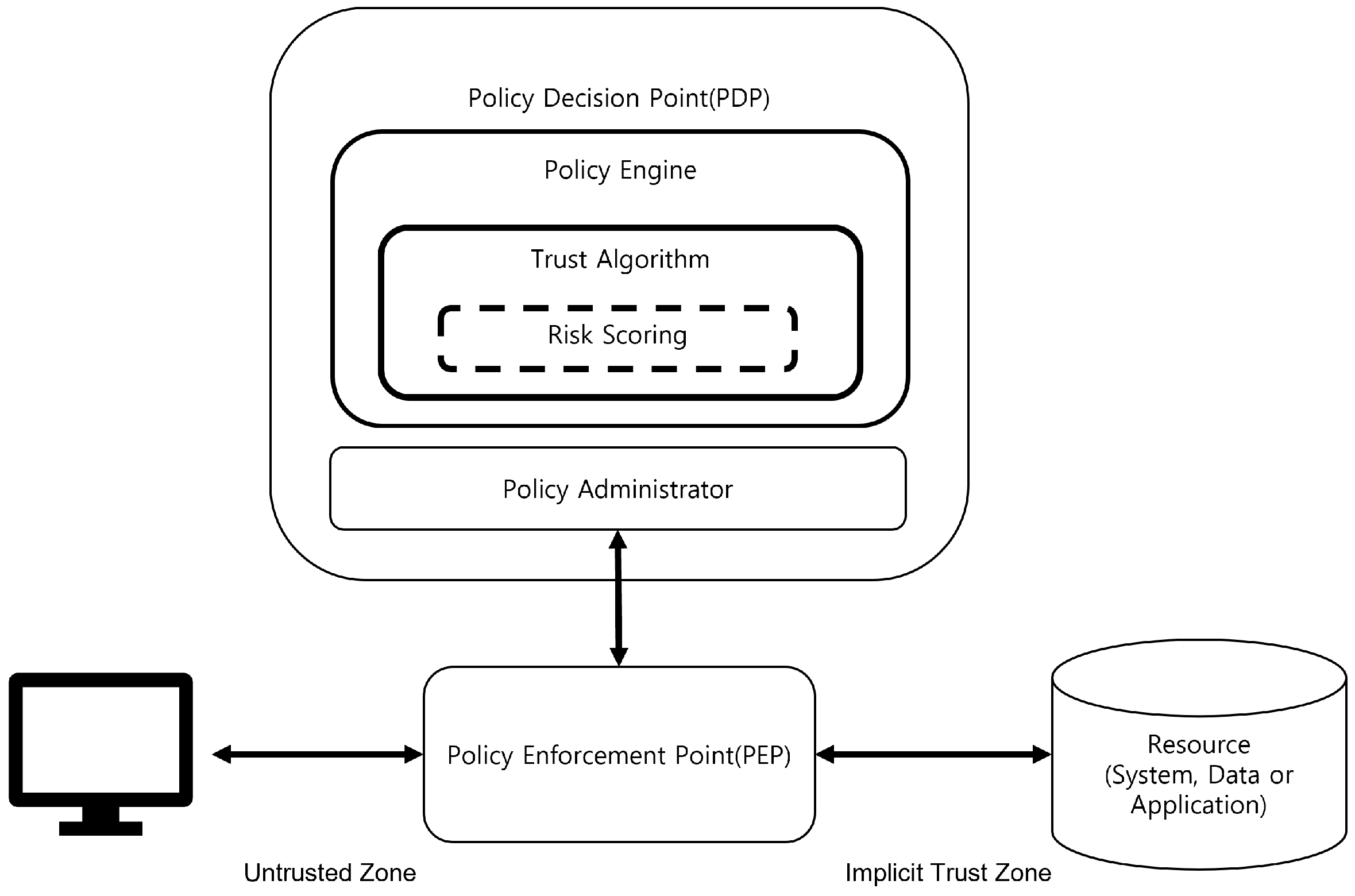
2.1. Trust Algorithm in Zero Trust
2.2. Device Risk Scoring Trends and Common Configuration Scoring System
2.2.1. Corporate Trends
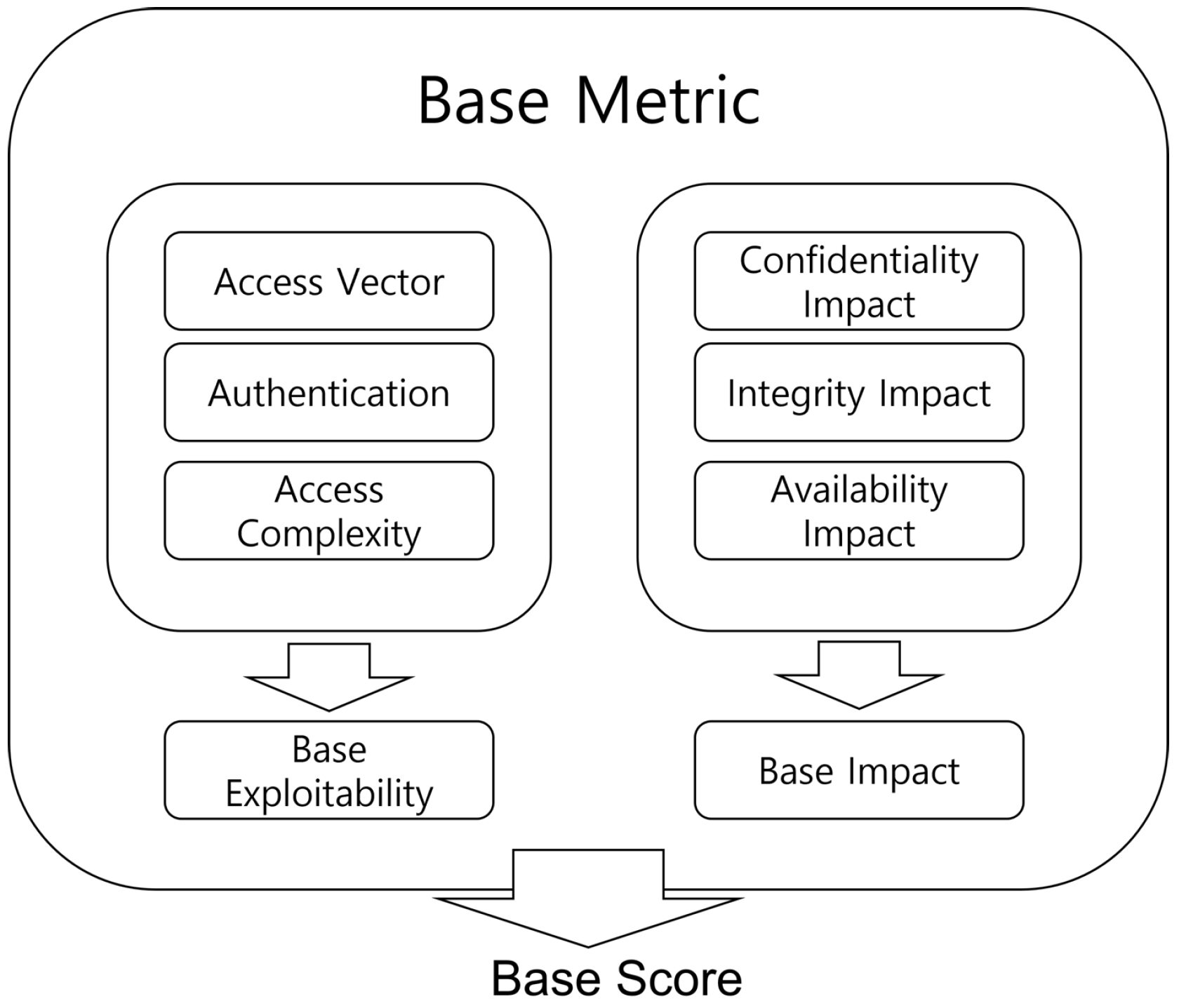
2.2.2. Common Configuration Scoring System
CCSS Base Metrics and Base Score
| Algorithm 1 Base score equation |
|
3. Proposed User Device Risk Scoring for Zero Trust Access
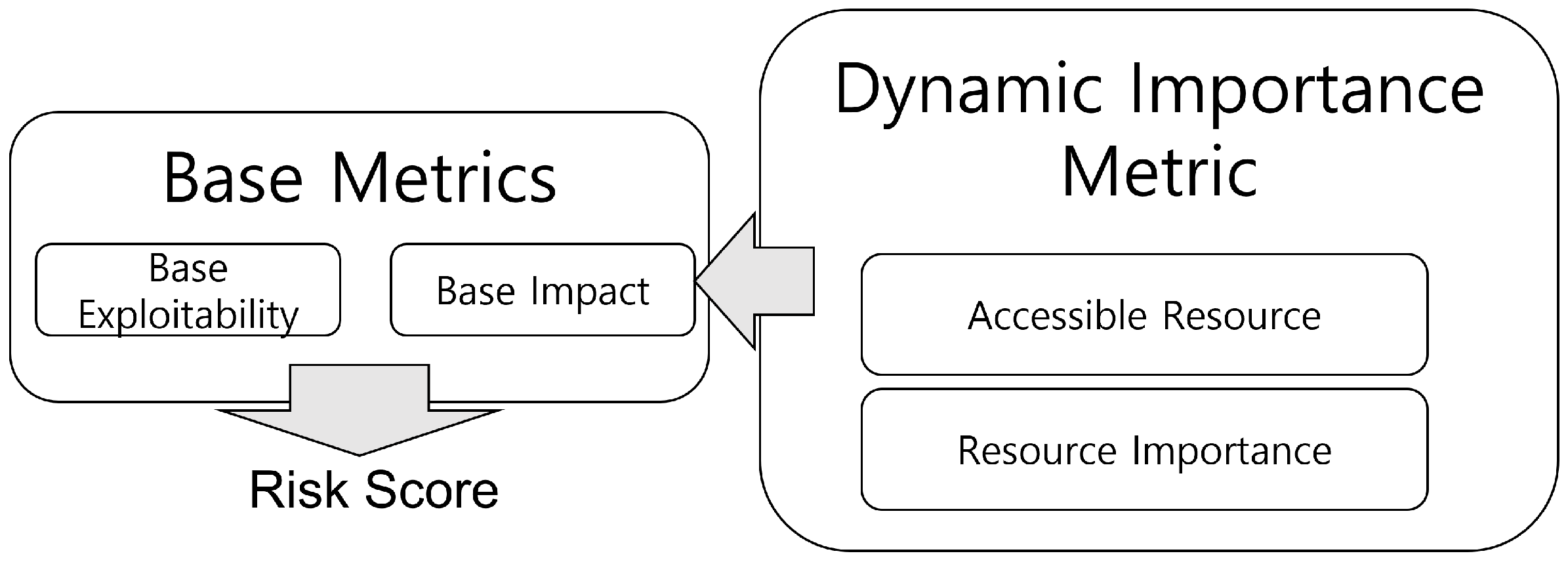
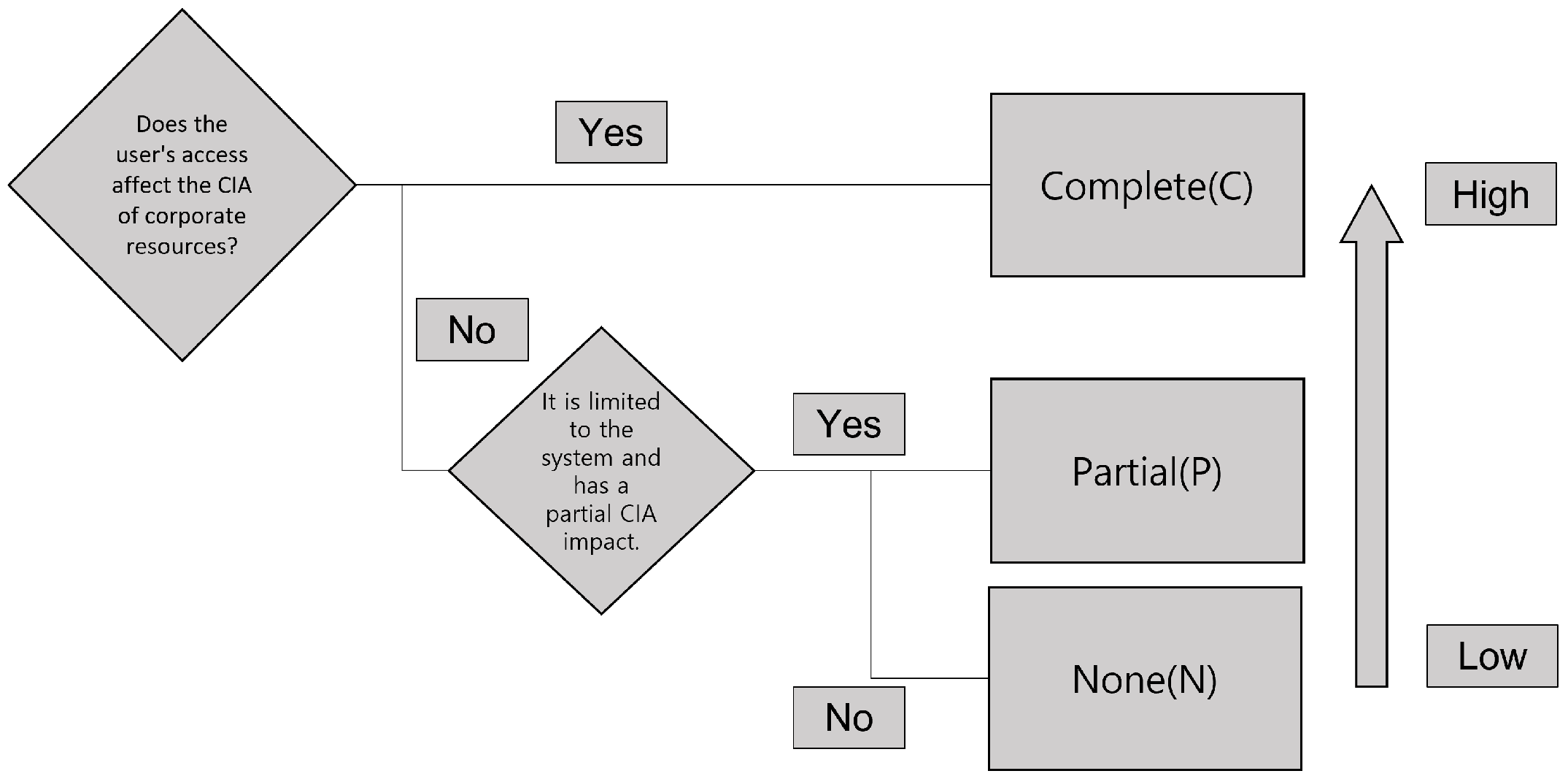
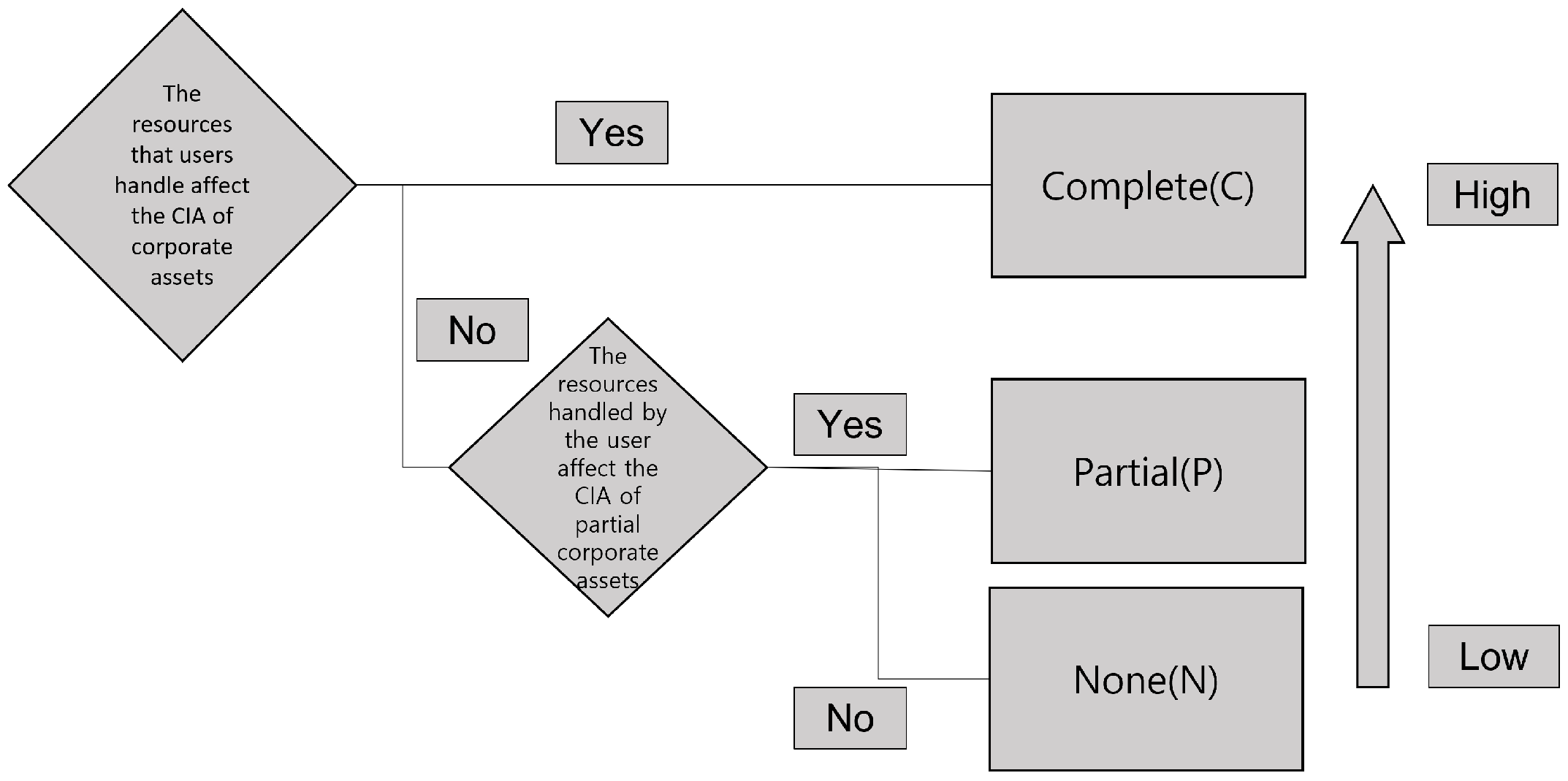
3.1. Dynamic Importance Metric
Dynamic Importance Metric Vector Diagram
3.2. Device Risk-Scoring Algorithm for Zero Trust
| Algorithm 2 Risk scoring algorithm |
|
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Waizenegger, L.; McKenna, B.; Cai, W.; Bendz, T. An affordance perspective of team collaboration and enforced working from home during COVID-19. Eur. J. Inf. Syst. 2020, 29, 429–442. [Google Scholar] [CrossRef]
- Green, N.; Tappin, D.; Bentley, T. Working from home before, during and after the Covid-19 pandemic: Implications for workers and organisations. N. Z. J. Employ. Relations 2020, 45, 5–16. [Google Scholar] [CrossRef]
- Mandal, S.; Khan, D.A.; Jain, S. Cloud-based zero trust access control policy: An approach to support work-from-home driven by COVID-19 pandemic. New Gener. Comput. 2021, 39, 599–622. [Google Scholar] [CrossRef] [PubMed]
- Kindervag, J.; Balaouras, S. No more chewy centers: Introducing the zero trust model of information security. Forrester Res. 2010, 3. [Google Scholar]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; Technical Report; National Institute of Standards and Technology: Washington, DC, USA, 2020.
- Mehraj, S.; Banday, M.T. Establishing a zero trust strategy in cloud computing environment. In Proceedings of the 2020 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 22–24 January 2020; pp. 1–6. [Google Scholar]
- Department of Defense Chief Information Officer. Department of Defense Zero Trust Strategy. 2020. Available online: https://dodcio.defense.gov/Portals/0/Documents/Library/DoD-ZTStrategy.pdf (accessed on 2 December 2022).
- Patil, A.P.; Karkal, G.; Wadhwa, J.; Sawood, M.; Reddy, K.D. Design and implementation of a consensus algorithm to build zero trust model. In Proceedings of the 2020 IEEE 17th India Council International Conference (INDICON), New Delhi, India, 10–13 December 2020; pp. 1–5. [Google Scholar]
- Uehara, M. Zero Trust Security in the Mist Architecture. In Proceedings of the Complex, Intelligent and Software Intensive Systems: Proceedings of the 15th International Conference on Complex, Intelligent and Software Intensive Systems (CISIS-2021), Asan, Republic of Korea, 1–3 July 2021; Springer: Cham, Switzerland, 2021; pp. 185–194. [Google Scholar]
- Cybersecurity Framework. Available online: https://www.nist.gov/cyberframework/updating-nist-cybersecurity-framework-journey-csf-20 (accessed on 6 December 2022).
- Kerman, A. Zero Trust Cybersecurity: ‘Never Trust, Always Verify’. NIST Blog, 2020. Available online: https://www.nist.gov/blogs/taking-measure/zero-trust-cybersecurity-never-trust-always-verify (accessed on 6 December 2022).
- Dimitrakos, T.; Dilshener, T.; Kravtsov, A.; La Marra, A.; Martinelli, F.; Rizos, A.; Rosetti, A.; Saracino, A. Trust aware continuous authorization for zero trust in consumer internet of things. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 1801–1812. [Google Scholar]
- What Is a Zero Trust Architecture—Paloaltonetworks.com. Available online: https://www.paloaltonetworks.com/cyberpedia/what-is-a-zero-trust-architecture (accessed on 6 December 2022).
- Staff, I.T. Implementing a Zero Trust Security Model at Microsoft-Inside Track Blog—Microsoft.com. Available online: https://www.microsoft.com/insidetrack/blog/implementing-a-zero-trust-security-model-at-microsoft/ (accessed on 6 December 2022).
- Conway, A. New Data from Microsoft Shows How the Pandemic Is Accelerating the Digital Transformation of Cyber-Security—Microsoft Security Blog—microsoft.com. Available online: https://www.microsoft.com/en-us/security/blog/2020/08/19/microsoft-shows-pandemic-accelerating-transformation-cyber-security/ (accessed on 6 December 2022).
- Brenduns. Configure Microsoft Defender for Endpoint in Microsoft Intune—Learn.microsoft.com. Available online: https://learn.microsoft.com/en-us/mem/intune/protect/advanced-threat-protection-configure (accessed on 6 December 2022).
- Siosulli. Microsoft Secure Score—Learn.microsoft.com. Available online: https://learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-secure-score?view=o365-worldwide (accessed on 6 December 2022).
- Katzer, M.; Katzer, M. Microsoft Secure Score. In Securing Office 365: Masterminding MDM and Compliance in the Cloud; Apress: California, MA, USA, 2018; pp. 97–156. [Google Scholar]
- Samaniego, M.; Deters, R. Zero-Trust Hierarchical Management in IoT. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018; pp. 88–95. [Google Scholar] [CrossRef]
- Scarfone, K.; Mell, P. The Common Configuration Scoring System (CCSS): Metrics for Software Security Configuration Vulnerabilities; NIST Interagency Report; NIST: Gaithersburg, MD, USA, 2010.
- Kasprzyk, R.; Stachurski, A. A concept of standard-based vulnerability management automation for IT systems. Comput. Sci. Math. Model. 2016, 3, 33–38. [Google Scholar] [CrossRef]
- Torkura, K.A.; Sukmana, M.I.; Meinig, M.; Kayem, A.V.; Cheng, F.; Graupner, H.; Meinel, C. Securing cloud storage brokerage systems through threat models. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 759–768. [Google Scholar]
- Wicaksana, A.; Wira, J.C. Security Analysis of Private Blockchain Implementation for Digital Diploma. Int. J. Innov. Comput. Inf. Control 2022, 18, 1601–1615. [Google Scholar]
- Yu, X.; Shu, Z.; Li, Q.; Huang, J. BC-BLPM: A multi-level security access control model based on blockchain technology. China Commun. 2021, 18, 110–135. [Google Scholar] [CrossRef]
- Albuali, A.; Mengistu, T.; Che, D. ZTIMM: A zero-trust-based identity management model for volunteer cloud computing. In Proceedings of the Cloud Computing–CLOUD 2020: 13th International Conference, Held as Part of the Services Conference Federation, SCF 2020, Honolulu, HI, USA, 18–20 September 2020; Springer: Cham, Switzerland, 2020; pp. 287–294. [Google Scholar]
- Ge, Y.; Zhu, Q. Trust Threshold Policy for Explainable and Adaptive Zero-Trust Defense in Enterprise Networks. In Proceedings of the 2022 IEEE Conference on Communications and Network Security (CNS), Austin, TX, USA, 3–5 October 2022; pp. 359–364. [Google Scholar]


| Item | CCSS Vector | CCSS Base Score | Risk Score (AR:C/RI:C) | Risk Score (AR:N/RI:N) |
|---|---|---|---|---|
| Auto login settings | AV:L/AU:N/AC:L /C:P/I:P/A:P/ | 4.6 | 4.6 | 2.5 |
| USB AutoRun | AV:L/AU:N/AC:L /C:C/I:C/A:C/ | 7.2 | 7.2 | 3.8 |
| Vulnerable password settings | AV:N/AU:N/AC:H /C:C/I:P/A:N/ | 6.1 | 6.1 | 4 |
| Antivirus software installation | AV:N/AU:N/AC:L /C:C/I:C/A:C/ | 10 | 10 | 7.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, U.H.; Hong, J.-h.; Kim, A.; Son, K.H. Endpoint Device Risk-Scoring Algorithm Proposal for Zero Trust. Electronics 2023, 12, 1906. https://doi.org/10.3390/electronics12081906
Park UH, Hong J-h, Kim A, Son KH. Endpoint Device Risk-Scoring Algorithm Proposal for Zero Trust. Electronics. 2023; 12(8):1906. https://doi.org/10.3390/electronics12081906
Chicago/Turabian StylePark, Ui Hyun, Jeong-hyeop Hong, Auk Kim, and Kyung Ho Son. 2023. "Endpoint Device Risk-Scoring Algorithm Proposal for Zero Trust" Electronics 12, no. 8: 1906. https://doi.org/10.3390/electronics12081906
APA StylePark, U. H., Hong, J.-h., Kim, A., & Son, K. H. (2023). Endpoint Device Risk-Scoring Algorithm Proposal for Zero Trust. Electronics, 12(8), 1906. https://doi.org/10.3390/electronics12081906





