A Software Defect Prediction Method Based on Program Semantic Feature Mining
Abstract
1. Introduction
- First, this paper proposes a method for extracting code semantic information through syntax structure information and code text information. This method first extracts the syntax structure information and code text information, and then combines it to form semantic information. The semantic information provides the basis platform for the research on the influence of program semantics on software defects.
- This paper proposes a method for the influence of software defects on program semantics, of which the research on the influence of program semantics in software defects is completed by mining defect features in the program semantic information.
2. Related Work
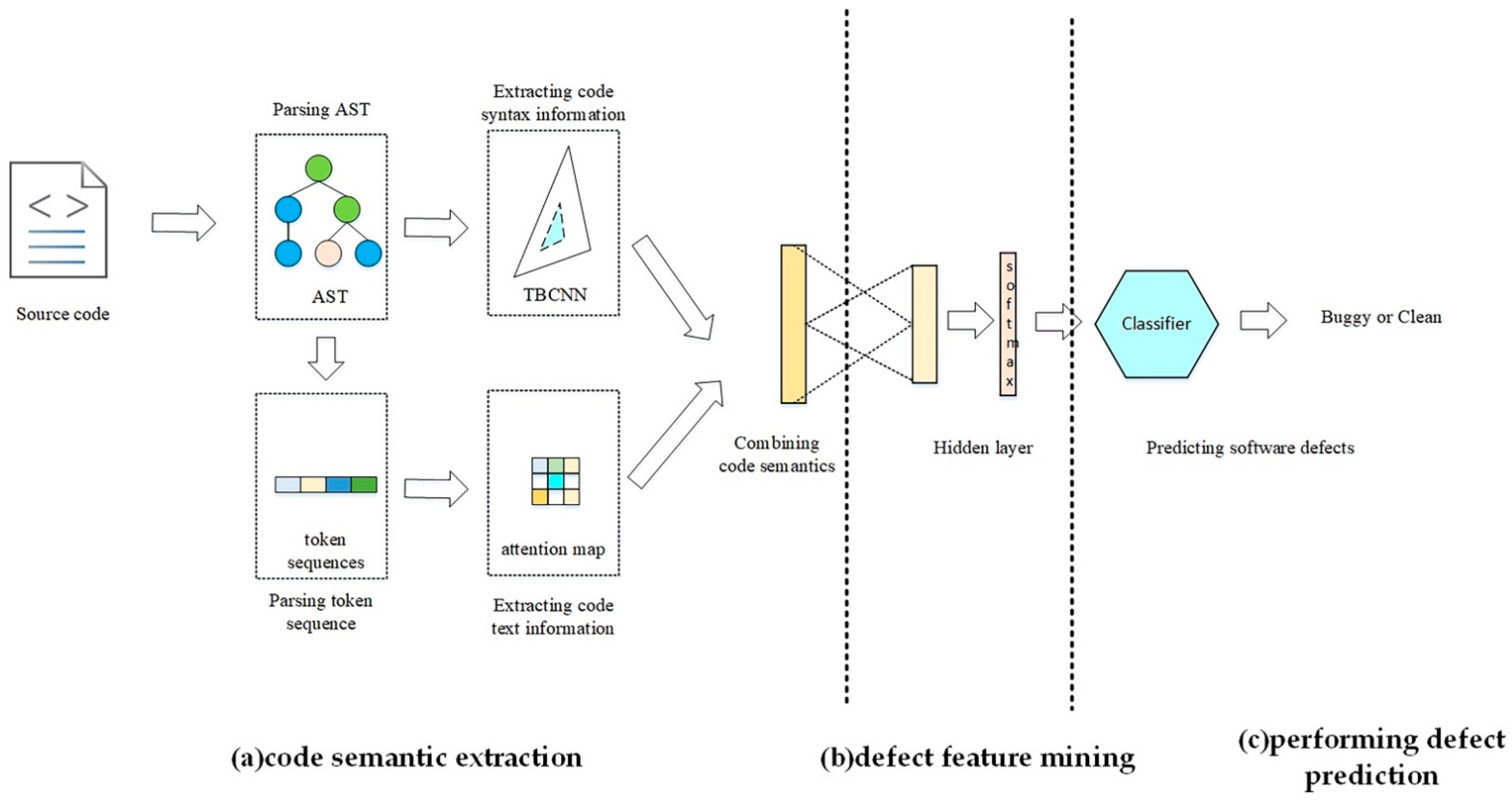
3. Component Design
3.1. Code Semantic Extraction
3.1.1. Parsing AST
3.1.2. Parsing Token Sequence
| Algorithm 1 parsing token sequence algorithm |
| Input: AST |
| Output: token seq |
| 1: Initialize queue = {AST}, seq = {} |
| 2: while queue not empty do |
| 3: node = queue.pop(0) |
| 4: seq.append(node.value) |
| 5: if node is not leaf node then |
| 6: queue.append(node.children) |
| 7: end if |
| 8: end while |
| 9: return seq |
3.1.3. Extracting Code Syntax Information
3.1.4. Extracting Code Text Information
3.1.5. Combining Code Semantics
3.2. Defect Feature Mining
3.3. Performing Defect Prediction
4. Experiment
4.1. Research Question
- RQ1: Compared with other deep learning methods, does the method in this paper have a better performance?
- RQ2: Can the semantic information extracted by the method in this paper be directly applied to software defect prediction?
4.2. Experiment Dataset
4.3. Performance Indicators
4.4. Performance Indicators
4.5. Analysis
- Compared with other deep learning methods, did the method in this paper have a better performance (RQ1)?
- Can the semantic information extracted by the method in this paper be directly applied to software defect prediction (RQ2)?
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Pachouly, J.; Ahirrao, S.; Kotecha, K.; Selvachandran, G.; Abraham, A. A systematic literature review on software defect prediction using artificial intelligence: Datasets, Data Validation Methods, Approaches, and Tools. Eng. Appl. Artif. Intell. 2022, 111, 104773. [Google Scholar] [CrossRef]
- Fan, G.; Diao, X.; Yu, H.; Yang, K.; Chen, L. Software Defect Prediction via Attention-Based Recurrent Neural Network. Sci. Program. 2019, 2019, 6230953. [Google Scholar] [CrossRef]
- Jin, Z.; Liu, F.; Li, G. Program comprehension: Present and future. Ruan Jian Xue Bao/J. Softw. 2019, 30, 110–126. (In Chinese) [Google Scholar]
- Qiu, S.; Cai, Z.; Lu, L. Cost-sensitive Convolutional Neural Network Module for Software Defect Prediction. J. Comput. Sci. 2019, 46, 156–160. (In Chinese) [Google Scholar]
- Radjenović, D.; Heričko, M.; Torkar, R.; Živkovič, A. Software fault prediction metrics: A systematic literature review. Inf. Softw. Technol. 2013, 55, 1397–1418. [Google Scholar] [CrossRef]
- Wang, T.; Han, L.; Fu, C.; Zou, D.; Liu, M. Static Detection Model and Framework for Software Vulnerability. J. Comput. Sci. 2016, 43, 80–86+116. (In Chinese) [Google Scholar]
- Liu, W.; Jiang, H. Severity Assessment of Software Defect Reports Based on Feature Selection. J. Comput. Eng. 2019, 45, 80–85. (In Chinese) [Google Scholar]
- Li, L.; Shi, K.; Ren, Z. Cross-project defect prediction method based on feature selection and TrAdaboost. J. Comput. Appl. 2022, 42, 1554–1562. (In Chinese) [Google Scholar]
- Li, J.; He, P.; Zhu, J.; Lyu, M.R. Software defect prediction via convolutional neural network. In Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security (QRS), Prague, Czech, 25–29 July 2017. [Google Scholar]
- Wang, S.; Liu, T.; Tan, L. Automatically learning semantic features for defect prediction. In Proceedings of the 2016 IEEE/ACM 38th International Conference on Software Engineering (ICSE), Austin, TX, USA, 14–22 May 2016. [Google Scholar]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Dam, H.K.; Pham, T.; Ng, S.W.; Tran, T.; Grundy, J.; Ghose, A.; Kim, C.J. A deep tree-based model for software defect prediction. arXiv 2018, arXiv:1802.00921. [Google Scholar]
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A Survey on Access Control in the Age of Internet of Things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Tian, Z.; Luo, C.; Qiu, J.; Du, X.; Guizani, M. A Distributed Deep Learning System for Web Attack Detection on Edge Devices. IEEE Trans. Ind. Inform. 2019, 16, 1963–1971. [Google Scholar] [CrossRef]
- Pan, C.; Lu, M.; Xu, B.; Gao, H. An Improved CNN Model for Within-Project Software Defect Prediction. Appl. Sci. 2019, 9, 2138. [Google Scholar] [CrossRef]
- Huang, X.; Fan, G.; Yu, H.; Yang, X. Software Defect Prediction via Heavy Son-based Abstract Syntax Tree. J. Comput. Eng. 2021, 47, 230–235+248. (In Chinese) [Google Scholar]
- Dong, Y.; Li, H.; Wei, X.; Tang, D. Software Defect Prediction based on the Features Fusion of Program Structure and Semantics. J. Comput. Eng. Appl. 2022, 58, 84–93. (In Chinese) [Google Scholar]
- Cheng, X.; Zhang, G.; Wang, H.; Sui, Y. Path-sensitive code embedding via contrastive learning for software vulnerability detection. In Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual, 18–22 July 2022. [Google Scholar]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A Malicious Bot-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques. IEEE Internet Things J. 2020, 8, 3242–3254. [Google Scholar] [CrossRef]
- Tian, Z.; Li, M.; Qiu, M.; Sun, Y.; Su, S. Block-DEF: A secure digital evidence framework using blockchain. Inf. Sci. 2019, 491, 151–165. [Google Scholar] [CrossRef]
- Kovačević, Z.; Ravber, M.; Liu, S.-H.; Črepinšek, M. Automatic compiler/interpreter generation from programs for Domain-Specific Languages: Code bloat problem and performance improvement. J. Comput. Lang. 2022, 70, 101105. [Google Scholar] [CrossRef]
- Xie, B.; Li, S.; Li, M.; Liu, C.H.; Huang, G.; Wang, G. SePiCo: Semantic-Guided Pixel Contrast for Domain Adaptive Semantic Segmentation. IEEE Trans. Pattern Anal. Mach. Intell. 2023, 1–17. [Google Scholar] [CrossRef]
- Yang, D.; Zhu, T.; Wang, S.; Wang, S.; Xiong, Z. LFRSNet: A robust light field semantic segmentation network combining contextual and geometric features. Front. Environ. Sci. 2022, 10, 1443. [Google Scholar] [CrossRef]
- Sheng, H.; Cong, R.; Yang, D.; Chen, R.; Wang, S.; Cui, Z. UrbanLF: A Comprehensive Light Field Dataset for Semantic Segmentation of Urban Scenes. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 7880–7893. [Google Scholar] [CrossRef]
- Shi, K.; Lu, Y.; Chang, J.; Wei, Z. PathPair2Vec: An AST path pair-based code representation method for defect prediction. J. Comput. Lang. 2020, 59, 100979. [Google Scholar] [CrossRef]
- Khalilian, A.; Baraani-Dastjerdi, A.; Zamani, B. APRSuite: A suite of components and use cases based on categorical decomposition of automatic program repair techniques and tools. J. Comput. Lang. 2019, 57, 100927. [Google Scholar] [CrossRef]
- Fu, W.; Menzies, T. Revisiting unsupervised learning for defect prediction. In Proceedings of the 2017 11th Joint Meeting on Foundations of Software Engineering, ESEC/FSE 2017, ACM, New York, NY, USA, 4–8 September 2017; pp. 72–83. [Google Scholar]
- Yang, Y.; Zhou, Y.; Liu, J.; Zhao, Y.; Lu, H.; Xu, L.; Leung, H. Effort-aware just-in-time defect prediction: Simple unsupervised models could be better than supervised models. In Proceedings of the 2016 24th ACM SIGSOFT International Symposium on Foundations of Software Engineering, Seattle, WA, USA, 13–18 November 2016; pp. 157–168. [Google Scholar]
- Kovačević, Ž.; Mernik, M.; Ravber, M.; Črepinšek, M. 2020: From Grammar Inference to Semantic Inference—An Evolutionary Approach. Mathematics 2020, 8, 816. [Google Scholar] [CrossRef]
- Elbosaty, A.T.; Abdelmoez, W.; Elfakharany, E. Within-Project Defect Prediction Using Improved CNN Model via Extracting the Source Code Features. In Proceedings of the 2022 International Arab Conference on Information Technology (ACIT), Abu Dhabi, United Arab Emirates, 22–24 November 2022. [Google Scholar]
- Available online: https://github.com/c2nes/javalang (accessed on 1 July 2014).
- Hindle, A.; Barr, E.T.; Gabel, M.; Su, Z.; Devanbu, P. On the naturalness of software. Commun. ACM 2016, 59, 122–131. [Google Scholar] [CrossRef]
- Mou, L.; Li, G.; Jin, Z.; Zhang, L.; Wang, T. TBCNN: A tree-based convolutional neural network for programming language processing. arXiv 2014, arXiv:1409.5718. [Google Scholar]
- He, Z.; Peters, F.; Menzies, T.; Yang, Y. Learning from open-source projects: An empirical study on defect prediction. In Proceedings of the 2013 ACM/IEEE International Symposium on Empirical Software Engineering and Measurement, Baltimore, MR, USA, 10–11 October 2013. [Google Scholar]

| Project | Description | Version | Total Number of Files | Ratio in Defect Files (%) |
|---|---|---|---|---|
| Camel | Enterprise integration framework | 1.0 | 339 | 3.8 |
| 1.2 | 590 | 36.6 | ||
| 1.4 | 840 | 17.3 | ||
| 1.6 | 926 | 20.3 | ||
| Lucene | Text search engine library | 2.0 | 186 | 48.9 |
| 2.2 | 234 | 61.1 | ||
| 2.4 | 329 | 61.4 | ||
| Xalan | A library for transforming XML files | 2.4 | 667 | 15.9 |
| 2.5 | 754 | 50.3 | ||
| 2.6 | 875 | 47.0 | ||
| Synapse | Data transport adapters | 1.0 | 16 | 10.2 |
| 1.1 | 55 | 26.8 | ||
| 1.2 | 86 | 33.6 | ||
| Poi | Java library to access Microsoft format files | 2.0 | 307 | 11.4 |
| 2.5 | 380 | 65.3 | ||
| 3.0 | 438 | 64.2 | ||
| log4j | Record for logs | 1.0 | 114 | 28.1 |
| 1.1 | 100 | 34.0 | ||
| 1.2 | 188 | 95.7 |
| Project | Train Dataset | Test Dataset | 2T-CNN | DP-CNN | Improved-CNN | DBN | PSFM |
|---|---|---|---|---|---|---|---|
| Camel | 1.0 | 1.2 | 0.396 | 0.497 | 0.487 | 0.346 | 0.533 |
| Lucene | 2.2 | 2.4 | 0.723 | 0.756 | 0.701 | 0.694 | 0.762 |
| Xalan | 2.5 | 2.6 | 0.643 | 0.696 | 0.780 | 0.540 | 0.669 |
| Synapse | 1.1 | 1.2 | 0.624 | 0.556 | 0.655 | 0.533 | 0.503 |
| Poi | 2.0 | 2.5 | 0.518 | 0.703 | 0.444 | 0.745 | 0.790 |
| log4j | 1.0 | 1.1 | 0.618 | 0.462 | 0.400 | 0.535 | 0.507 |
| average F-measure | - | - | 0.587 | 0.612 | 0.579 | 0.566 | 0.627 |
| Project | Train Dataset | Test Dataset | Sem Method | PSFM Method |
|---|---|---|---|---|
| Camel | 1.0 | 1.2 | 0.523 | 0.533 |
| 1.4 | 1.6 | 0.475 | 0.498 | |
| Lucene | 2.2 | 2.4 | 0.752 | 0.762 |
| 2.0 | 2.2 | 0.755 | 0.759 | |
| Xalan | 2.5 | 2.6 | 0.641 | 0.669 |
| 2.4 | 2.5 | 0.613 | 0.625 | |
| Synapse | 1.1 | 1.2 | 0.512 | 0.503 |
| 1.0 | 1.1 | 0.497 | 0.501 | |
| Poi | 2.0 | 2.5 | 0.741 | 0.790 |
| 2.5 | 3.0 | 0.780 | 0.782 | |
| log4j | 1.0 | 1.1 | 0.511 | 0.507 |
| 1.1 | 1.2 | 0.496 | 0.505 | |
| - | - | 0.608 | 0.619 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yao, W.; Shafiq, M.; Lin, X.; Yu, X. A Software Defect Prediction Method Based on Program Semantic Feature Mining. Electronics 2023, 12, 1546. https://doi.org/10.3390/electronics12071546
Yao W, Shafiq M, Lin X, Yu X. A Software Defect Prediction Method Based on Program Semantic Feature Mining. Electronics. 2023; 12(7):1546. https://doi.org/10.3390/electronics12071546
Chicago/Turabian StyleYao, Wenjun, Muhammad Shafiq, Xiaoxin Lin, and Xiang Yu. 2023. "A Software Defect Prediction Method Based on Program Semantic Feature Mining" Electronics 12, no. 7: 1546. https://doi.org/10.3390/electronics12071546
APA StyleYao, W., Shafiq, M., Lin, X., & Yu, X. (2023). A Software Defect Prediction Method Based on Program Semantic Feature Mining. Electronics, 12(7), 1546. https://doi.org/10.3390/electronics12071546







