Abstract
Recently, cloud computing resources have become one of the trending technologies that permit the user to manage diverse resources and a huge amount of data in the cloud. Task scheduling is considered one of the most significant challenges and ineffective management results in performance degradation. It is necessary to schedule the task effectively with maximum resource utilization and minimum execution time. Therefore, this paper proposes a novel technique for effective task scheduling with enhanced security in the cloud computing environment. A novel convolutional neural network optimized modified butterfly optimization (CNN-MBO) algorithm is proposed for scheduling the tasks, thereby maximizing the throughput and minimizing the makespan. Secondly, a modified RSA algorithm is employed to encrypt the data, thereby providing secure data transmission. Finally, our proposed approach is simulated under a cloudlet simulator and the evaluation results are analyzed to determine its performance. In addition to this, the proposed approach is compared with various other task scheduling-based approaches for various performance metrics, namely, resource utilization, response time, as well as energy consumption. The experimental results revealed that the proposed approach achieved minimum energy consumption of 180 kWh, a minimum response time of the 20 s, a minimum execution time of 0.43 s, and maximum utilization of 98% for task size 100.
1. Introduction
Resource allocation is defined as the process of scheduling and assigning resources and the advantage of the combined form of resource allocation and task scheduling is to reduce the entire system delay. The virtualization platform is used for resource allocation and the resources such as output and input devices, central processing unit (CPU), and memory will be virtualized through the virtualization platform. Due to the virtualization, the system has some improvements such as minimum execution time, energy minimization, and effectiveness of cloud resources in the data centers. The various issues such as energy management, server consolidation, data security, data management, managing automated services, and traffic problems mainly damage the performance, security, and availability of cloud computing [1]. The policies in resource allocation can identify the perfect task requirements before the utilization of the virtual machine. This policy will manage the availability of resources, and eliminate service level agreement violations and task deadlines. The standard techniques are employed to overcome the problems in task scheduling in cloud computing [2].
The scheduling problems in cloud computing are mainly concentrated around the task allocation and virtual servers. Security and energy consumption are the key elements of task scheduling, storage of data and information, and the processing of modern cloud systems. Blockchain technology can act as a secure and effective technology and the data can be stored in a small database instead of using a central data center for data storage. This will increase security and prevents database damage from attacks on the entire cloud system [3]. The large-scale difficult applications have various service components that require distinctive combinations of reliability and security. The various stages of reliability and security schemes are required on the cloud side. Due to the inadequate security service, the multi-cloud system can eliminate the inefficient adaptation between cloud services and tasks, information leakage, and extreme level of computing time [4]. The task allocation with resource problems falls under the NP-hard problem category and the quality of service will solve task scheduling problems in cloud computing.
For the development of storing, sensing, and computing, a large amount of data is produced, which has difficulties in implementation and design of security-critical systems [5]. Cloud computing technology is eminent for the processing of big data, which contains computing problems and data storage problems [6]. Cloud computing contains performance and security issues in resource allocation, which requires improvements for increasing the quality and reducing the computational cost. The storage of data and processing of data are implemented by using private clouds through the public clouds [7]. Cloud computing includes various phases such as parallel computing, utility computing, distributed computing, and grid computing, which results in the rapid growth of data centers. Due to rapid growth, some issues occurred such as performance reduction and response delay. The combined form of cloud computing and green communication technology can be used for developing the data center’s computing capabilities [8]. The process of scheduling and allocating resources and the advantage of an integrated form of resource allocation and task scheduling is to reduce overall system latency. Researchers developed several techniques for task scheduling algorithms. Meanwhile, these techniques have various issues such as energy management, server consolidation, data security, data management, managing automated services, and traffic problems, mainly damage the performance, security, and availability of cloud computing. This paper proposes a novel technique for effective task scheduling with enhanced security in the cloud computing environment.
This research paper accomplishes the following contributions.
- To design a task scheduling process using a novel convolutional neural network optimized modified butterfly optimization (CNN-MBO) algorithm thereby minimizing the response time and maximizing the resource utilization.
- Minimizing the total response time and makespan via optimal task scheduling process.
- A modified RSA algorithm is employed to encrypt the data, thereby providing secure data transmission in the cloud system.
- To compare the proposed approach with various other task scheduling-based approaches for various performance metrics, namely, resource utilization, response time as well as energy consumption.
The rest of this paper is organized as follows: Section 2 explains the literature survey of various authors. The proposed methodology is described in Section 3 and this section has a brief explanation of the CNN-MBO method. Section 4 contains the result and discussion part and the conclusion part is explained in Section 5.
2. Related Works
Rekha et al. [9] proposed an efficient task allocation method for a cloud environment employing a genetic algorithm. An effective task allocation method was employed for acquiring minimum completion time. For task scheduling, throughput and makespan were the parameters utilized in this paper. The experimentation results demonstrated that the scheme achieved higher performance than the other methods. Energy consumption was not considered in this paper.
Sun et al. [10] discussed task scheduling security in the cloud environment. The functional domain construction was utilized for determining the sets of fog nodes included in the functional domain. The service time, success rate, average delay, and cost are the parameters employed in this paper. The results showed that the scheme achieved better performance when compared to the other techniques. However, this paper failed to focus on the reliability of service in the fog-clouds environment.
Nawrocki et al. [11] presented a security-aware task allocation model for resource management and secure task allocation in mobile cloud computing (MCC). To meet the consumers’ data confidentiality requirements, they developed a resource allocation protocol that assigns optimal and secure communication. A machine learning model is adopted for resource utilization and their model is evaluated in a MocSecSim environment. The results show that their model enhances the security level for task allocation with minimal processing time and energy consumption.
Li, W. et al. [12] presented an agent learning method in a trust basis form in a mobile cloud computing atmosphere that involved service composition. This technique was developed to increase user skills such as risks in security and provision of quality of service (QOS) uncertainty. The efficiency was analyzed by applying Java Agent Development Framework (JADE). The experimentation result showed that the scheme achieved improvement in the satisfaction of users and success rate for transactions through the fuzzy c-means (FCM) learning algorithm.
The cost and time expectation was achieved through optimized ACOA (Q-ACOA). The time, cost, and load balance-enhanced ant colony optimization (TCLB-EACO) algorithm, min-min (MM) algorithm, and the round robin scheduling (RR) algorithms were used in this scheme. The experimentation result demonstrated that the scheme evaluated the value of expected heuristic factor β is 4.5 and pheromone heuristic factor α is 3, which consumed low cost in Q-ACOA over related algorithms. However, the scheme does not execute the correlation process.
Amer, A.A. et al. [13] investigated an optimized collaborative scheduling (OCS) algorithm in a cloud computing and mobile-edge computing (MEC) scheme which involved resource-sharing methods for performing task prioritization. The presence of service satisfaction was verified by a resource optimization algorithm and the supply of resources was established. The experimentation results validated that the scheme achieved the best performance in a proposed scheduling algorithm over the previous scheduling algorithm. However, the scheme consumed more power and energy.
Zhu, Q.H. et al. [4] developed a multi-mound allocation (MMA) scheduling method called matching to optimize submitted tasks with respect to the total cost, makespan, reliability constraints, and security. Hybrid chaotic particle search (HCPS), modified artificial bee colony (MABC), and modified cuckoo search (MCS) are the techniques used to achieve these objectives. A better trade-off between time and economic cost, higher resource utilization lower cost, and shorter makespan is achieved using this technique.
The symmetric key cryptographic technique was proposed by Sohal, M. et al. [14] based on binary deoxyribonucleic acid (BDNA) and asymmetric deoxyribonucleic acid (ADNA) which involved data encryption on the client side for the analysis of cloud computing security. This technique was evaluated to reduce the usage of more encryption algorithms. The scheme related the developed technique with the existing Data Encryption Standard (DES), Advanced Encryption Standard (AES), Blowfish, and deoxyribonucleic acid (DNA) symmetric key algorithms. The experimentation analysis revealed that the scheme reached better encryption time, throughput, and ciphertext size than symmetric key algorithms. Table 1 describes the literary works of task scheduling in cloud computing based on several authors.

Table 1.
Literature survey based on several authors.
3. Proposed Methodology
The significant objective of this paper is to design an optimal task-scheduling process with minimum response time, energy consumption, as well as maximum resource utilization. The workflow of the proposed approach containing various task managers is depicted in Figure 1, in which the workload is split into numerous clusters. This paper proposes a CNN-optimized MBO approach for optimal scheduling of tasks and modified RSA is employed to secure the data stored in the cloud storage system. The following section depicts the detailed steps involved in the proposed approach.
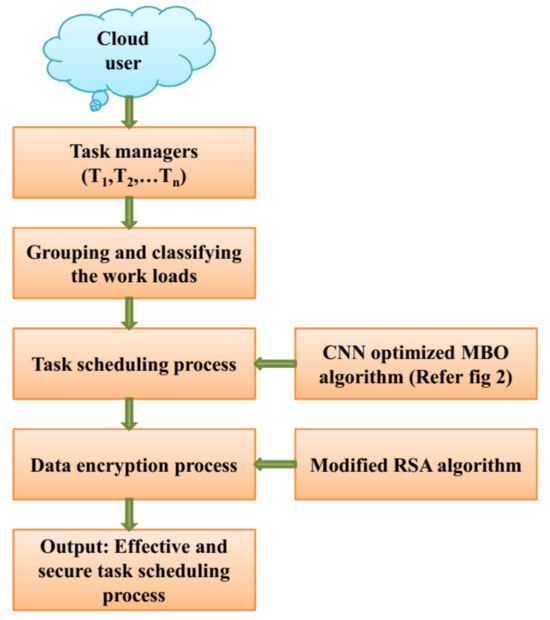
Figure 1.
Proposed workflow.
3.1. Task Scheduling Process Based on CNN-MBO Algorithm
The task scheduling process is optimized using several parameters of multiple service providers such as user request, task type, task dependency, etc. Initially, the user request is set up, which consists of to task units. Then the task type is defined that is comprised of 1 to tasks [15]. The term indicates the total number of tasks that exist in the task unit. The task dependency achieved by the task unit is considered as .
The term indicates dependencies of task units. Therefore, to enhance the performance of task scheduling in a cloud computing environment, we adopted the CNN-MBO algorithm. It not only enhances scheduling performance but also reduces time loss. A detailed description of the proposed CNN-MBO approach for task scheduling is deliberated as follows in Figure 1.
3.1.1. Convolutional Neural Network (CNN)
One of the types of deep neural networks (DNN) is utilized for classifying and analyzing images. Information extraction and processing vary by CNN. Generally, CNNs have convolutional layers, pooling layers, and fully connected layers. Convolutional layers have kernels that slide down and across the input to produce output by multiplying each weight in the kernel with the corresponding matrix element value over which the kernel acts. The result is then summed to obtain the output. The kernel has weights that are updated through backpropagation during the training process. Pooling layers are used to reduce the dimensionality of the feature maps and for more robust feature detection. CNNs have seen limited use in task scheduling problems compared to other neural networks [16].
Convolutional Layer
One of the CNN core layers has a convolutional layer. These layers are smaller in size and they have filters but they cover the entire image by shifting. The convolutional mechanism takes place by calculating the dot product among the filter and image. The dot products among the filter and image are summarized through the filter region.
Pooling Layer
The pooling layer operated downsampling. Different classes of the pooling function exist. The most commonly employed functions are those of maximum pooling. The maximal pooling filters returned the maximal values for every subregion. If the maximal pooling filters are utilized for the size feature , then it resulted in a size feature.
Fully Connected Layer
The preceding layer neurons are associated with each neuron with subsequent layers in the fully connected layer. Then it is expressed as:
The bias is represented by , and the input through the previous layer being denoted . In the fully connected layer, the hidden layer sparsity will avoid the problem of overfitting in CNN.
Softmax Function Layer
The probability distributions of the event with various events are computed by using the softmax function layer. The softmax layer’s operation is calculated and expressed in the following equation:
Classification Output Layer
The loss is computed during the training of the output layer of the CNN. The goal of CNN is to reduce the cost function for predicting the data. Then the existent cost function is calculated and expressed in the following function:
Then the cross-entropy is expressed as:
The target value is represented as and the predicted value is denoted . The weight function of CNN is optimized using a modified butterfly optimization algorithm which is discussed as follows.
3.1.2. Modified Butterfly Optimization Algorithm
Most traditional optimization methods such as cuckoo search, firefly optimization, artificial bee colony, particle swarm, and genetic algorithm are utilized to find the optimal solution. However, these techniques rely on slope information to update the solution, and the position of the initial solution affects the final solution quality. Among all methods, the BOA algorithm provides better performance. The BOA algorithm is a nature-inspired algorithm and has been widely used to solve complex optimization problems in various fields. The butterfly optimization algorithm (BOA) revealed its efficiency with the robust and straightforward strategy to acquire optimum solutions to different optimization difficulties—it has particular deficiencies. Due to the switching probability of higher values, greater numbers of candidates are utilized for the global search. In this algorithm, some of the candidates are moving to the local search stage, which constructs the algorithm weakest in local searchability. This algorithm has suffered from premature convergence and it does not avoid the local optima. The Steven power law is utilized for updating the exponent of power value. For enhancing the exploration capability, Lagrange interpolation is utilized and the local searching scheme is updated by the strategy of Lévy flight. The modified BOA (MBOA) was employed for balancing local exploitation and global exploration [15]. Then the modifications are described below:
The BOA switching probability is customized for increasing the efficiency of this algorithm. An arbitrary selection of exploitation and exploration phases based on the chosen value of switching probability is recognized to sometimes cause the BOA to misplace direction and deviate from the global optimal solution. Thus, this paper proposed a convolutional neural network optimized modified butterfly optimization (CNN-MBO) algorithm to enhance the exploitation and exploration capacity effectively and better balance the algorithm in two stages of switching [17].
Primarily, the value is taken as 0.3. Due to the scattered position or randomness of butterflies, more of the butterflies will not sense the best butterfly’s fragrance. The local stage of the BOA is termed by the randomly moving butterflies. The switch probabilities are expressed and calculated in the following equation:
Modification of Fragrance Generation
Every butterfly fragrance generation is modified by the exponent power values as well as a sensory modality. The exponent power is taken in the ranges of [0.2, 0.6]. Based on Steven’s power law, the power exponent value for fragrance is fixed as 0.6. The smaller number of butterflies received the fragrance with the best butterflies and the total number of butterflies is enhanced by receiving the fragrance with the best butterfly. The new changed fragrance is calculated and generated utilizing the following equation:
The sensor modality is represented by , the objective of the best solution is indicated by , the current iteration number is denoted by , and the mean objective values and current objective functions are denoted by and . The exponent power and the sensor modality are represented by and .
Lagrange Interpolation
The Lagrange interpolation is utilized for reducing the exploitation ability of the algorithm. The three-point Lagrange interpolation is employed for increasing the ability of the algorithm. The Lagrange interpolation application with the global stage of the BOA ensured the ability of exploitation in the stage.
Lévy Flight Searching Process
In the mLBOA, the exploitation stage is modified and expressed as below;
The dimension is represented by , the Lévy flight search method or Lévy flight random walk is multiplied through the random number . The search orientation is evaluated by the direction vector value .
3.1.3. Proposed CNN-Optimized MBO Approach for Efficient Task Scheduling
Figure 2 illustrates the flow diagram of the proposed CNN-optimized MBO approach for an efficient task scheduling process. At first, the input dataset is fed into the neural network that extracts the significant data features. In CNN, the inputted data are flattened to vectors before passing to a fully connected layer. Generally, the highly trained fully connected layer necessitates many parameters, which create over-fitting problems. Therefore, to provide continuous representation and optimize weight function, the modified butterfly optimization (MBO) algorithm is employed. Thus, the CNN-MBO algorithm optimizes the task-scheduling process in an effective manner.
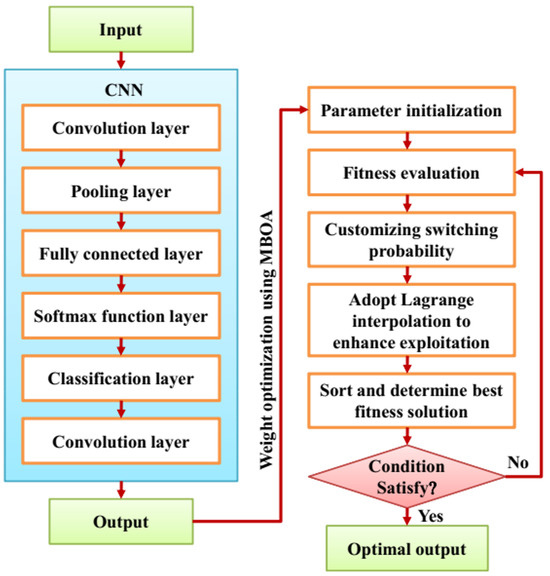
Figure 2.
Flow diagram for CNN-MBO approach for efficient task scheduling.
3.1.4. Complexity Analysis
This section focus on studying the time complexity using big-O notation, therefore the approach with higher speed will be presented. The population size, N, the number of tasks, n, and the maximum iteration are the main elements that have higher impact on speed. The time complexity of HDE in big-O is O(T ∗ n ∗ N).
3.2. Modified RSA (MRSA) Based Encryption Process
Information leakage (data loss) is the most significant cause of security issue that arises in cloud computing task. In order to tackle this security issue, the data encryption approach is necessary. The data encryption approach safeguards sensitive information and private data from unauthorized users by providing safe and secure cipher keys. In this work, data are securely stored in the cloud and communicated between the user and the server by adopting a modified RSA. A brief illustration of this technique is described as follows.
Modified RSA
In this paper, a modified RSA (MRSA) algorithm is employed for storing secure data in the cloud storage system. The MRSA algorithm comprises three vital phases, namely, the key generation phase, the encryption phase, as well as decryption phase. For the RSA encryption and decryption based on BOA, the RSA algorithm requires modification of BOA components to improve speed. The modified BOA algorithm is used in MRSA to reduce the processing time of encryption and decryption. The MRSA algorithm provides more security and speed in the encryption and decryption process as compared to RSA.
A detailed description of each respective phase involved in the MRSA algorithm is discussed below.
Key Generation Process
In an asymmetric key cryptosystem, a set of private and public keys must be created by every user. For this, decryption uses one key and encryption uses the other key.
- a, b, c, and d are the four distinct prime numbers chosen, i.e., .
- Evaluate and .
- Evaluate and and then create the primary numbers.
- Select 2 public keys, T2 from and T1 from . The condition below must be fulfilled when finding those values.and .This is related to another T2 value.
- The extended Euclid’s algorithm is used to establish and private keys.
Encryption Process
During the encryption process, the plain text or secret data are encrypted using two diverse public keys, P1 and P2, by employing the modular exponential technique. The formula to encrypt the data is mentioned in equation.
From the above equation, and signify the chipper text and plain text, respectively.
Decryption Process
The secret data received are unscrambled by employing the modular exponential technique as mentioned above by employing two private keys, namely, M2. The notation and description of variables are presented in Table 2.

Table 2.
Notations and description of variables.
4. Results and Discussions
This section describes the analysis to determine the efficiency of the proposed convolutional neural network-based modified butterfly optimization (CNN-MBO). Metrics such as resource utilization, response time, energy consumption, and execution time are computed. The proposed CNN-MBO is simulated in a cloudlet simulator.
4.1. Experimental Setup
The experiments of the proposed CNN-MBO method are evaluated with various components and their specifications are depicted in Table 3.

Table 3.
Experimental configuration.
4.2. Parameter Settings
The parameters utilized to tune the proposed method are delineated in Table 4.

Table 4.
Parameter settings.
4.3. Performance Metrics
4.3.1. Resource Utilization
Resource utilization is defined as the total number of allocated resources used by a task to finish its execution. The mathematical expression is given as:
From Equation (17), the unutilized resource and available resource are denoted as and .
4.3.2. Energy Consumption
The amount of energy utilized while allocating resources in the cloud server is termed energy consumption.
4.3.3. Response Time
The elapsed time between the arrival time of task and the completion time of task is defined as the response time.
4.4. Performance Analysis
Figure 3 depicts the response time analysis with different task sizes. The proposed CNN-MBO model is compared with the fuzzy c-means learning (FCM) algorithm [18], the time, cost, and load balance-enhanced ant colony optimization (TCLB-EACO) algorithm, genetic algorithm (GA) [19], and optimized collaborative scheduling (OCS). The response time for a different number of task sizes is graphically represented. The proposed CNN-MBO model achieves a faster response time compared to other methods. For a low number of task sizes, the response time of the proposed CNN-MBO model is 20 s.
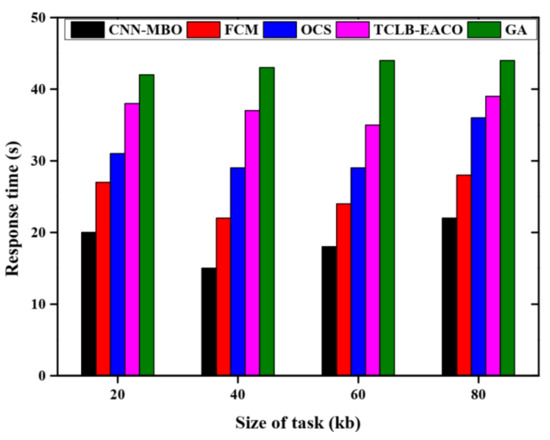
Figure 3.
Response time analysis.
A comparative analysis of the execution time of various methods is represented in Figure 4. The proposed CNN-MBO model obtains minimum execution time, which provides effective results. The method has a higher execution time compared to other methods. The execution time reached by the proposed CNN-MBO model is about 0.43 s.
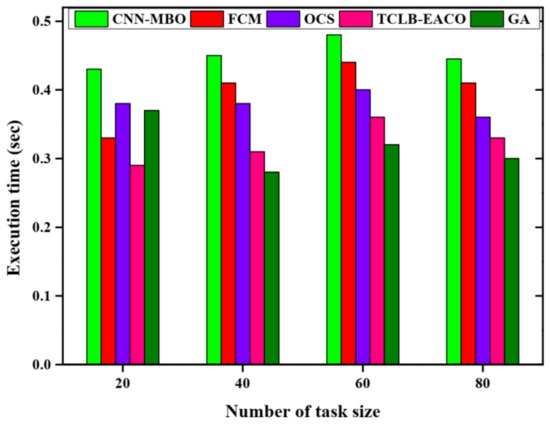
Figure 4.
Execution time analysis.
Figure 5 represents the resource utilization evaluation of various methods. The resource utilization rate of the proposed CNN-MBO model is compared with the resource utilization rate of FCM, TCLB-EACO, GA, and OCS. The resulting analysis shows that the proposed CNN-MBO model has a higher resource utilization rate compared to existing methods. As the number of task sizes increases, resource utilization gradually increases. The resource utilization rate of the proposed CNN-MBO model is about 98% for 100 task sizes.
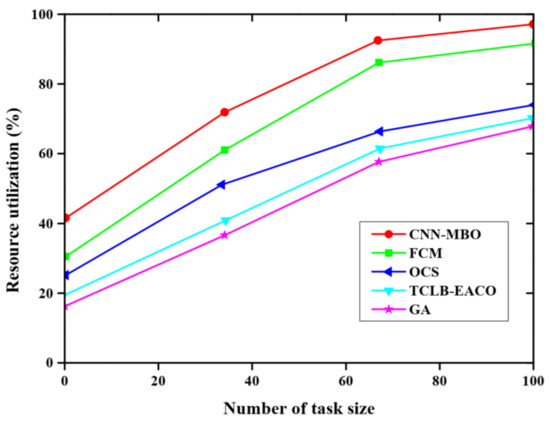
Figure 5.
Resource utilization analysis.
Energy consumption analysis of various methods is given in Figure 6. The proposed method has achieved lower energy consumption compared to FCM, TCLB-EACO, GA, and OCS. Energy consumption for different task sizes is determined. When the task size is 20, the total energy consumed is 180 kWh.
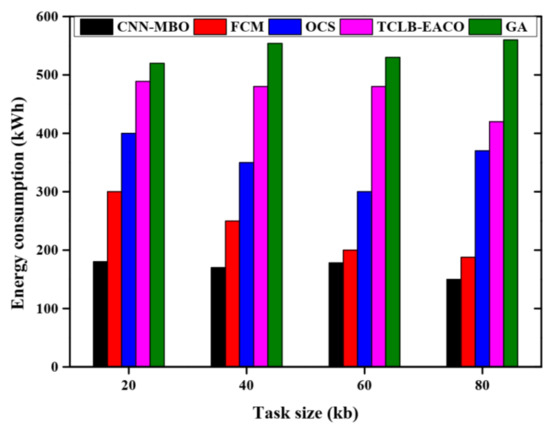
Figure 6.
Energy consumption analysis.
5. Conclusions
This paper proposed a novel convolutional neural network optimized modified butterfly optimization (CNN-MBO) algorithm by minimizing the response time and maximizing the resource utilization. Here, a modified RSA algorithm is employed to encrypt the data, thereby providing secure data transmission. The proposed approach is simulated under a cloudlet simulator and the evaluation results are analyzed to determine its performance. Metrics such as resource utilization, response time, energy consumption, and execution time are computed to determine the effectiveness of the proposed CNN-MBO model. In the proposed work, the energy consumed is very low, and response time is also minimum. The resource utilization rate of the proposed CNN-MBO model is about 98% for 100 task size, which is higher than FCM, TCLB-EACO, GA, and OCS, respectively. However, the arrival time of the task is delayed. In the future, the proposed approach will be implemented in a real-time environment to determine the effectiveness of the system also to enhance the QoS based on task scheduling algorithms by considering the arrival time of the task.
Author Contributions
Conceptualization, S.B. (Sahar Badri) and M.R.; Methodology, D.M.A., S.H.H. (Syed Humaid Hasan), S.H.H. (Syed Hamid Hasan) and S.B. (Surbhi Bhatia); Validation, D.M.A. and M.R.; Formal analysis, S.B. (Sahar Badri) and D.M.A.; Investigation, S.H.H. (Syed Humaid Hasan) and S.H.H. (Syed Hamid Hasan); Resources, F.A. and S.B. (Surbhi Bhatia); Data curation, F.A.; Writing—original draft, D.M.A., S.H.H. (Syed Humaid Hasan), S.H.H. (Syed Hamid Hasan) and M.R.; Writing—review & editing, F.A. and S.B. (Surbhi Bhatia); Project administration, S.B. (Sahar Badri). All authors have read and agreed to the published version of the manuscript.
Funding
The Deanship of Scientific Research (DSR) at King Abdulaziz University (KAU), Jeddah, Saudi Arabia, has funded this project, under grant No. (RG-91-611-42).
Data Availability Statement
The data is available on request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Walia, N.K.; Kaur, N. Performance Analysis of the Task Scheduling Algorithms in the Cloud Computing Environments. In Proceedings of the 2021 2nd International Conference on Intelligent Engineering and Management (ICIEM) 2021, London, UK, 28–30 April 2021; pp. 108–113. [Google Scholar]
- Bharany, S.; Sharma, S.; Bhatia, S.; Rahmani, M.K.I.; Shuaib, M.; Lashari, S.A. Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability 2022, 14, 6159. [Google Scholar] [CrossRef]
- Abouyoussef, M.; Bhatia, S.; Chaudhary, P.; Sharma, S.; Ismail, M. Blockchain-Enabled online diagnostic platform of suspected patients of COVID-19 like pandemics. IEEE Internet Things Mag. 2021, 4, 94–99. [Google Scholar] [CrossRef]
- Zhu, Q.H.; Tang, H.; Huang, J.J.; Hou, Y. Task scheduling for multi-cloud computing subject to security and reliability constraints. IEEE/CAA J. Autom. Sin. 2021, 8, 848–865. [Google Scholar] [CrossRef]
- Zhou, J.; Sun, J.; Cong, P.; Liu, Z.; Zhou, X.; Wei, T.; Hu, S. Security-critical energy-aware task scheduling for heterogeneous real-time MPSoCs in IoT. IEEE Trans. Serv. Comput. 2019, 13, 745–758. [Google Scholar] [CrossRef]
- Kummar, S.; Bhushan, B.; Bhatia, S. Blockchain Based Big Data Solutions for Internet of Things (IoT) and Smart Cities. In New Trends and Applications in Internet of Things (IoT) and Big Data Analytics; Springer: Cham, Switzerland, 2022; pp. 225–253. [Google Scholar]
- Alghazzawi, D.; Bamasaq, O.; Bhatia, S.; Kumar, A.; Dadheech, P.; Albeshri, A. Congestion Control in Cognitive IoT-Based WSN Network for Smart Agriculture. IEEE Access 2021, 9, 151401–151420. [Google Scholar] [CrossRef]
- Lu, Y.; Sun, N. An effective task scheduling algorithm based on dynamic energy management and efficient resource utilization in green cloud computing environment. Clust. Comput. 2019, 22, 513–520. [Google Scholar] [CrossRef]
- Rekha, P.M.; Dakshayini, M. Efficient task allocation approach using genetic algorithm for cloud environment. Clust. Comput. 2019, 22, 1241–1251. [Google Scholar] [CrossRef]
- Sun, Y.; Jin, R.; Lin, K.; Liu, W. High-performance isolation computing technology for smart IoT healthcare in cloud environments. IEEE Internet of Things 2021, 8, 16872–16879. [Google Scholar]
- Nawrocki, P.; Pajor, J.; Sniezynski, B.; Kolodziej, J. Modeling adaptive security-aware task allocation in mobile cloud computing. Simul. Model. Pract. Theory 2022, 116, 102491. [Google Scholar] [CrossRef]
- Li, W.; Cao, J.; Hu, K.; Xu, J.; Buyya, R. A trust-based agent learning model for service composition in mobile cloud computing environments. IEEE Access 2019, 7, 34207–34226. [Google Scholar] [CrossRef]
- Amer, A.A.; Talkhan, I.E.; Ahmed, R.; Ismail, T. An Optimized Collaborative Scheduling Algorithm for Prioritized Tasks with Shared Resources in Mobile-Edge and Cloud Computing Systems. Mob. Netw. Appl. 2022, 27, 1444–1460. [Google Scholar] [CrossRef]
- Sohal, M.; Sharma, S. BDNA-A DNA inspired symmetric key cryptographic technique to secure cloud computing. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 1417–1425. [Google Scholar] [CrossRef]
- Kumar, A.; Gandhi, C.P.; Zhou, Y.; Kumar, R.; Xiang, J. Improved deep convolution neural network (CNN) for the identification of defects in the centrifugal pump using acoustic images. Appl. Acoust. 2020, 167, 107399. [Google Scholar] [CrossRef]
- Bal, P.K.; Mohapatra, S.K.; Das, T.K.; Srinivasan, K.; Hu, Y.C. A Joint Resource Allocation, Security with Efficient Task Scheduling in Cloud Computing Using Hybrid Machine Learning Techniques. Sensors 2022, 22, 1242. [Google Scholar] [CrossRef] [PubMed]
- Sharma, S.; Chakraborty, S.; Saha, A.K.; Nama, S.; Sahoo, S.K. mLBOA: A Modified Butterfly Optimization Algorithm with Lagrange Interpolation for Global Optimization. J. Bionic Eng. 2022, 19, 1161–1176. [Google Scholar] [CrossRef]
- Bhatia, S. New improved technique for initial cluster centers of K means clustering using Genetic Algorithm. In Proceedings of the International Conference for Convergence for Technology-2014, Pune, India, 6–8 April 2014; pp. 1–4. [Google Scholar]
- Bhalla, K.; Koundal, D.; Bhatia, S.; Rahmani, M.K.I.; Tahir, M. Fusion of infrared and visible images using fuzzy based siamese convolutional network. Computers. Mater. Contin. 2022, 70, 5503–5518. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).