Abstract
Improving the training quality of education and training institutions is one of the important reasons for the sustainable development of training institutions. However, traditional education and training institutions lack supervision, and the process system is not standardized, resulting in a lack of authenticity and reliability of information in the training process. Because most of the traditional education and training systems are centralized, it is difficult to share training data between institutions and relevant departments. Therefore, in view of the problems of data tampering and resource sharing in the field of education and training, combined with the node complexity of education and training scenarios, we propose an education and training blockchain platform suitable for multi-node scenarios to ensure the authenticity of the training data and traceability. In this consortium chain, we design specific ledger structures and corresponding smart contracts to meet different business logic requirements. According to different business data types, we optimize the ledger storage method. To improve chaincode utilization and system transaction throughput, we explore different system configuration rules and provide useful insights. Finally, several experiments are performed to evaluate the security and efficiency of the proposed system.
1. Introduction
1.1. Background
With the rapid development of society, the demand for talents increases, which also promotes the continuous expansion of the scale of education and training institutions. At the same time, the emergence of the Internet is gradually helping the education and training systems achieve structural reform. However, in this development process, there are still some problems. First, there are challenges with data security and information privacy in traditional training management systems [1]. Due to the low cost of counterfeiting and the lack of relevant credit records for counterfeiting, the phenomenon of counterfeiting training certificates has always been common, for example, arbitrarily fabricating and falsifying personal training records and achievements for personal benefit. This reduces the credibility of the data and creates unfair competition. Once this happens, it will be difficult for users and relevant management personnel to trace and verify false information. Moreover, educational institutions, themselves, may have problems, such as false propaganda and inconsistent qualifications [2]. According to statistics, in 2022, more than 1500 training institutions will have been found to have committed training fraud across the country [3]. On the other hand, in previous training systems, data storage mostly relied on system centers or third-party organizations. The data generated during the education and training process is stored in an independent database through corresponding network technology and the web. If there is a problem with the system center, it will cause irreversible damage. Additionally, the centralized information management mode also has the possibility of information leakage and forgery [4].
As education becomes more popular, safe and convenient sharing of education and training data can bring great convenience to educational institutions and employers. In the era of rapid network digitalization, the contradiction between online learning and the centralized management mechanisms of education and training institutions is becoming more and more obvious. Moreover, traditional education and training institutions lack awareness of reform, and their technical and practical capabilities in recording learners’ learning behaviors are relatively backward. In response to the above problems, combining the advantages of decentralization and anonymity provided by the blockchain to build a reliable training management system can effectively help improve the efficiency and quality of data management in the training process [5]. For example, we can use the difference in the hash value of each transaction’s data to prevent malicious data tampering [6]. Through the sharing mechanism to improve information transparency, data regarding training and assessments stored in the blockchain network can be traced as needed. The security of data in the system is improved through identity verification, and only those who have passed identity verification and obtained certain authority can operate on the student’s information [7], in order to prevent the information in the database from being maliciously tampered with, as well as to add more regulatory agencies to ensure the rigor and reliability of the entire assessment process [8]. At the same time, we embed the assessment process and rules into the digital code through blockchain technology and store them in a shared database in a transparent manner [9], in order to improve the credibility of the system through smart contracts. When the set rules are triggered, the script code will automatically execute the predefined logic and procedures. This process cannot be interfered with, manipulated, or tampered with at will, so all participants in the alliance are automatically supervised [10].
1.2. Related Works
In recent years, as blockchain technology has gradually matured, it has made conceptual progress at a higher level. It is applied to new educational scenarios to improve the actual needs of sharing, delivering, and protecting student education and training records and to improve the security and reliability of educational institution management mechanisms through effectiveness and privacy control [11]. Governments and organizations, private companies, and public-private alliances have also gradually used blockchain technology to solve transparency, traceability, and many other key issues in the education industry. They hope to establish a safe and reliable education management platform through blockchain technology, in order to improve the comprehensive supervision ability of the education and training industry and build a full ecosystem of education and training integration [12]. The earliest blockchain university in the world is Woolf University, an academic institution built entirely on blockchain. Students can select the courses that interest them, and blockchain technology will be used to record the students’ grades and credits. Students can obtain a graduation certificate after completing the credits. As early as October 2016, the Ministry of Industry and Information Technology pointed out in the “China Blockchain Technology and Application Development White Paper” [13] that the transparency and reliability of the blockchain system are fully applicable to the academic field and have greatly promoted the progress of the education industry.
In the future, in the field of education, blockchain can promote more credible education and training information, as well as more efficient education and training governance, by establishing a real-time query database, a traceable information base, and a reshapeable learning ecology [14]. “Blockchain + education” will help the relevant regulatory authorities solve the basic problems of education and training governance and become an effective means of education and training management [15]. Although some work has combined blockchain with the education industry, there are still some shortcomings. ZhangL et al. put forward a suggestion and plan to implement the blockchain into the education information management system [16]. However, the plan lacks a specific and complete information flow framework and does not discuss and connect with actual cases, making it unconvincing. In [17], researchers propose a highly available blockchain for educational consortiums. Network deployment, based on the Kubernetes structure, improves the traceability and security of data in the education field. In [18], blockchain technology is applied to the DNS (domain name system). Designing a safe and efficient domain name system (B-DNS) by building a new block data structure is also worth learning from. In [19,20], the confidentiality of blockchain transactions is improved through a zero-knowledge verification scheme. In the case of data sharing, the privacy disclosure of users is greatly reduced. In terms of performance optimization, in [21,22], by introducing deterministic sorting technology and a new framework supporting Boolean range queries, the flexibility of transaction sorting is improved, and the performance of the system is further optimized. However, whether it can actually be applied to the multi-node model in the field of education and training remains to be studied. In this paper, we improve the performance of the system through multitasking workload optimization. In short, educational data is more complex, and there are still many problems that need to be solved in practical applications. Additionally, as blockchain technology continues to advance, the proposed system should also be constantly updated. For example, since the Hyperledger Composer has been depreciated, the implementation becomes less valuable.
The purpose of this paper is to combine blockchain technology research and realize an educational institution alliance management platform centered on training institutions. The education and training situation is transmitted by leaving data traces, and the whole process of training transaction information, assessment, and evaluation is carried out on the chain, fixed, and stored, and an information security mechanism with the participation of multiple departments is established. This paper’s main contribution is as follows:
- By combining web applications and blockchain, a highly available education and training platform, based on alliance blockchain, is built to meet the needs of educational scenarios. This effectively realizes the information exchange between education departments, training institutions, human resource centers, and other nodes on the chain and improves data security and traceability. Reasonably use the advantages of PostgreSQL, MySQL, and Redis storage components to realize the optimal “on-chain and off-chain” information storage methods.
- Realize the joint management of private data and access control policies, ensure the legality of data access in the alliance, and prevent unauthorized access. Additionally, through the development of reasonable smart contracts, the credibility and reliability of the system can be improved.
- Through comparative experiments, the network configuration and transaction scale on the chain are adjusted, and the load balancing of the chain agents is realized, which greatly improves the performance of the system.
This paper is divided into six chapters. The structure is as follows: Section 2 reviews blockchain technology and its classification. The Section 3 introduces the architecture and scheme of the development platform. The Section 4 describes various configurations of the system and the realization functions of the system. Section 5 evaluates the system’s performance. The Section 6 summarizes and looks forward to the research.
2. Preliminary
2.1. Blockchain Technology
Blockchain originated from Bitcoin and was originally used to solve various transactions in the financial field [23]. It is essentially a distributed database, a new technology that combines peer-to-peer networks, distributed storage, digital certificates, and other multi-disciplinary fields [24]. As a key technology for decentralization and distributed ledgers, blockchain is stored in a chain structure. A chain is formed according to the hash value order of the block, and each block includes a block body and a block header [25], as shown in Figure 1. The block header loads the metadata of the block, for example, the timestamp and hash of the previous block. The body of a block contains a list of all transactions recorded in that block. It does not require any third-party confirmation to ensure that all parties in the open network are credible. Synchronizing data in the network through a consensus mechanism provides the possibility of developing a reliable system for data storage and sharing [26]. Currently, systems combined with blockchain are becoming more and more popular. Different from systems that rely on central nodes, blockchain systems rely on data backup redundancy to ensure security and are no longer threatened by single-point failures [27]. With the gradual maturity of blockchain technology, relevant researchers have used the characteristics of blockchain to integrate it with a variety of cutting-edge technologies. For example, combining blockchain with artificial intelligence [28] can provide verifiability and auditability for the federated learning process; combining blockchain with cloud technology [29] can further optimize the query efficiency and controllability of system data. It can be seen from this that blockchain technology has broad development prospects.
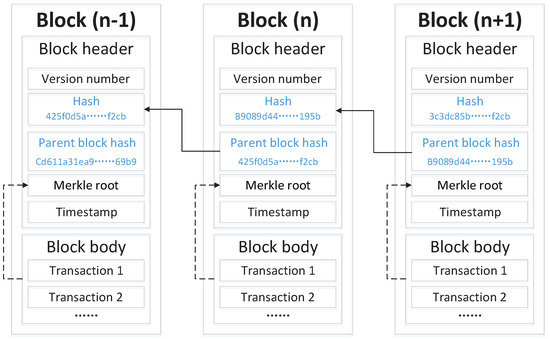
Figure 1.
Blockchain structure.
2.2. Public Chain and Private Chain
Various types of blockchains can be basically divided into public blockchains and permissioned blockchains [30]. The general public can access public chains, such as Ethereum and Bitcoin. The latter can only be used by authorized users [31]. In this study, based on the advantages of different Hyperledger frameworks, we chose the Hyperledger Fabric framework. Members of the Hyperledger Fabric network form a sub-network that provides a pluggable ordering service to establish a consensus on transactions in order and then broadcast blocks to nodes. Additionally, the subnet is an authorized access network that provides the MSP-based access control function. Nodes jointly maintain member information for MSP module verification; only members in the sub-network can see the transactions they participate in and have the right to access smart contracts (chain codes) and transaction data [32]. The privacy of all participants is maintained in the channel, thereby ensuring the security of transaction data [33]. Table 1 summarizes the types and characteristics of the different Hyperledger frameworks.

Table 1.
The main classification and characteristics of the Hyperledger framework.
3. The Proposed Platform
In this chapter, the architecture design and model scheme of the platform are described.
3.1. Platform Architecture
This article uses Hyperledger Fabric to develop a decentralized education and training management platform that supports identity verification, reliability, and data sharing. Organizations in the alliance network include education management departments, education and training institutions, and human resource departments. Together with the front-end management interface, it forms a management platform for education and training. The platform architecture is shown in Figure 2. In the alliance network, each newly joined entity becomes a network node through the consensus stage and maintains a complete ledger.
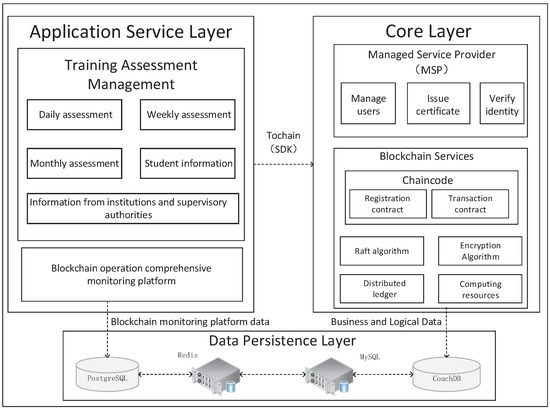
Figure 2.
The platform architecture.
In this paper, the management platform built with Hyperledger Fabric consists of three parts: the application service layer, the core layer, and the data storage layer. Each layer interacts in the form of an application programming interface (API) or software development kit (SDK). Each layer is developed and maintained relatively independently, which can reduce mutual influence and improve system scalability. The system uses a browser/server (B/S) architecture to provide services to users and separates the front- and back-ends to reduce module coupling. When operating information is transmitted, such as the basic information and assessment of newly added trainees, all data transmission is carried out in JavaScript Object Notation (JSON) format.
The application service layer is divided into education, training management, and a comprehensive monitoring platform for blockchain operations. The education and training management module includes functions to operate on role registration and related information. The front-end calls the API interface specified by the service layer and uploads the form request parameters (basic personnel information, training information, etc.) generated by the web page to the back-end, and the back-end calls the appropriate contract function (registration query, audit, and other contracts) to implement the requested business requirements. Connect to the blockchain network through the encapsulated API. According to the request parameters, select the connected channel and endorsement node to endorse the transaction, and finally, obtain the response data in JSON format. The web side parses the response data and renders the result on the page.
The blockchain operation’s comprehensive monitoring platform monitors and operates the nodes in the alliance network. The monitoring content includes smart contracts, the number and operation of nodes, transaction history, etc., as shown in Figure 3.
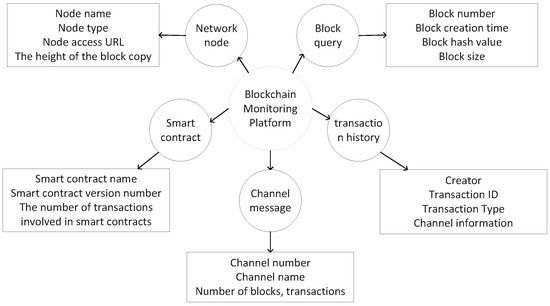
Figure 3.
Blockchain operation monitoring platform.
The core layer includes functions such as chain code and MSP authorization. There will be no central node in the distributed network of blockchain. Therefore, a decision-making mechanism is needed to facilitate consensus decisions among participants in the network. The consensus mechanism is a mechanism for coordinating parties to process information [34]. On this platform, we chose Raft (leader election) [35] as the consensus algorithm. It can provide an efficient consensus method in the governance process. After the front-end is connected to the blockchain network, the transaction is sent to the designated channel. The endorsement nodes in the alliance endorse and return the endorsement result, together with the digital signature to the sender. After confirming that the transaction is correct, the sorting node in the blockchain network will sort the transaction through the Raft algorithm, and the completed transactions are stored in blocks [36]. The accounting nodes in the network are synchronized through the P2P protocol, and the information is finally recorded in the ledger. Distributed ledgers are used to achieve multi-party, consistent, decentralized data storage, and broken ledgers can be repaired by synchronizing ledgers. The business-related smart contracts in this study run in Docker containers, and the chaincode service provides a secure container environment and lifecycle management.
The data storage layer ensures data persistence. In this consortium chain, all participating identity authentication information, trainee training records, and other business information are stored in CunchDB. We construct a MySQL database to store related data, such as system management information. By building a Redis cache database to store common transaction data, the concurrency and performance of a large number of transactions in the system can be improved. PostgreSQL to provide data for the monitoring page. It adopts the classic client-server model (C/S), that is, one client corresponds to one server daemon. This daemon process analyzes the query request from the client, retrieves data by generating a plan tree, and finally, formats and outputs the result and returns it to the client.
3.2. Platform Solution
There are several "roles" in the management chain process framework diagram of the training management platform based on Hyperledger Fabric. Figure 4 shows the relationship between roles, education and training institutions (ETI), local education bureaus (LEB), and local human resources centers (LHRC) that form an alliance chain, with students (S), C-level teachers (CT), B-level teachers (BT), and A-level teachers (AT) together forming the RSETP. At system initialization, each organization contains a superadministrative account. According to the different identities of each participant, the corresponding level of read and write permissions is formulated [37].
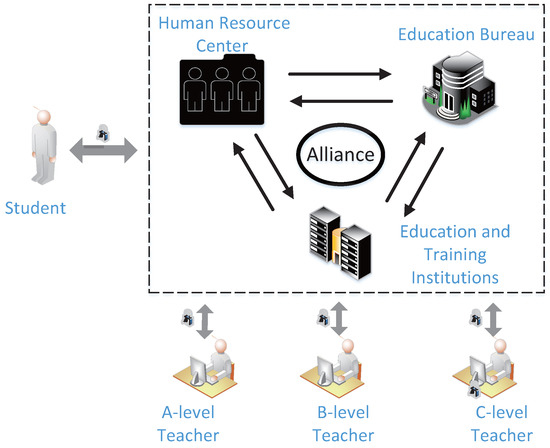
Figure 4.
System stakeholders.
- Education and Training Institutions(ETI): As an important platform and driving force for adult education, it ensures high-quality training for students. In order to prevent insufficient qualifications and false propaganda about education and training institutions, educational institutions need to apply for registration with the local education bureau and can only join the alliance chain after approval. Students can study at this educational institution and obtain corresponding training results and certificates.
- Local Education Bureau (LEB): Focus on filing information on training institutions and teachers, including basic information, working experience, educational background, and whether they have teacher qualifications. Training institutions are required to strengthen their own platform management. If personnel engaged in training activities in training institutions violate laws and regulations, the violations will be recorded.
- Local Human Resource Center (LHRC): The trainees’ information, including basic information and educational background, is filed at the LHRC. When the employer hires the trainee, the trainee’s training information and process can be clearly questioned. The trainee’s training record can be queried by accessing the alliance network, and the illegal or falsified results can be traced back to ensure the fairness of each trainee’s education and training.
- Student (S): Students who want to join the education alliance training institution need to provide their own basic information. After passing the certification process for educational institutions, they can enter the institution for training. The trainee’s information is stored on the blockchain.
- C-level Teacher (CT): Each institution has different levels of training teachers, and each teacher needs to be certified by ETI and LEB. After confirming the corresponding training qualifications, he can join the network for teaching and assessing students. The CT will judge the day’s performance based on each student’s daily performance and upload the daily training situation to the alliance network for storage.
- B-level Teacher (BT): Score each student’s one-week training situation, and after confirming that it is correct, upload the information to the alliance network for storage.
- A-level Teacher (AT): Refer to each trainee’s one-month comprehensive training situation to score the trainee. After the training is over, it will be decided, according to the trainee’s performance during the whole training period, whether the trainee can get the certificate of passing the training, and the trainee who does not meet the graduation standard will not be awarded a graduation certificate.
During the entire training management process, if there is a new educational institution in a certain place to carry out training courses, the educational training institution will form an alliance chain with the local education bureau and the local human resources center, a certificate authority (CA) in the federation issues digital certificates and public and private keys to each organization. Each organization creates its own nodes, including peer nodes, ordering nodes, etc. Each peer node in the organization can install multiple chain codes to meet different business needs and store a blockchain ledger. When new students or teachers join the institution for training, the institution first verifies and stores their information. Teachers of different levels in each institution have different grading permissions. According to the pre-established scoring details, each student is scored, and each scoring record is saved to the blockchain network. If, after the trainee graduates, the employer finds that the trainee’s level is not up to standard, it can appeal to the human resources department to review the trainee’s training information. Figure 5 shows the specific workflow of the system. From the acceptance of students by educational institutions to the graduation of students, the process can be divided into the following steps, in detail:
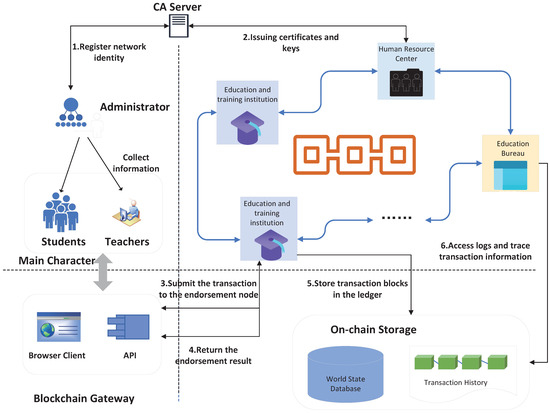
Figure 5.
System workflow.
- Step 1.
- This step will register each role in the blockchain network. All participants in the system need to register on the network and record their identity information. The network will provide each participant with a unique identity. Before each transaction, the identity information of both parties needs to be verified. Only after the identity information has been correctly verified can the transactions and information exchange in the network continue.
- Step 2.
- When a student signs up for training at an educational institution, the corresponding institution will record basic information, such as the student’s identity information, training courses, and time. After the information is confirmed to be correct, all information will be uploaded to the blockchain network through the designated ordering node for storage.
- Step 3.
- After the training every day, the CT will evaluate the performance of all the students on the day, according to the pre-established assessment standards and upload the evaluation information for each S to the blockchain network. The corresponding contract will automatically detect the evaluation information, and the information of an authentication failure will not be recorded in the blockchain network. for example, if the assessment score exceeds the maximum standard score. After confirming that the information is correct, the ledger will be updated.
- Step 4.
- The BT judges the weekly results of the students, scores them weekly, and uploads them to the blockchain network. In order to execute the smart contract corresponding to the weekly assessment, and after confirming that the information is correct, it will be uploaded to the blockchain network for storage.
- Step 5.
- The AT will give students a monthly score after the monthly training. The AT will carry out the final assessment and certification of each S after all the training courses are over. Whether the S has passed the education and training, based on his or her performance throughout the entire training period, is determined. All data will be operated at various stages in the chain, and the integrity of the data will be guaranteed.
- Step 6.
- As an authoritative third party, the local education bureau needs to authenticate and record various information about the teachers in the education alliance institution. Only teachers who meet the teaching conditions can serve in the institution and assess the students to ensure the teaching quality of the teachers. The local human resources center mainly records the training situation of the training and assessment personnel. According to actual needs, managers can trace the specified training records in the alliance network to check whether the assessment records for each S are accurate. By viewing the signature information of each administrator, the legitimacy and validity of the assessment information can be verified. Once the assessment information is untrue and the student’s grades are unqualified, etc., the assessment teacher can be traced back according to the transaction records.
3.3. Ledger Design
RSETP is a permission-based network that provides some needed services to designated users. Our system consists of three main components: a permissioned consortium chain, on-chain and off-chain storage, and manipulation of student-centric information through the RSETP client interface. Hyperledger can generate new identities for modeling participants as needed and append them to the participant registry. The Hyperledger network requires blockchain identities as a form of credential, storing a mapping of genetic characters to participants in the identity registry [38]. All identity management services are performed by peers controlled by the organization deploying the blockchain consortium. In our RSETP, at any time, new participants (S, AT, etc.) with appropriate identity functions can be added. The permissions of each role in the organization have been set in the access authorization rules, so only the roles that have completed registration on the platform and passed identity verification have the corresponding authority to authorize transactions. Without the correct private key, no one can gain access to the blockchain platform. In RSETP, the administrator passes the request data generated by the web page to the blockchain network through the corresponding API, and the data is encoded and packaged into blocks during the transaction process. Each block has a block header, which is used to verify the validity of the entire block.
The ledger contains the state of the world and a blockchain. The essence of the world state is a database that saves the current state of the network ledger [39]. The chain on the peer is a transaction log that records changes in the state of the world. The world state is saved in the form of key-value pairs, which have good interactions with the data in JSON format. Figure 6 depicts the relationship between state entities. Students or teachers are associated with training institutions and other departments through a specific relationship table, and the information exchange between various regulatory agencies enables managers to perform flexible operations.
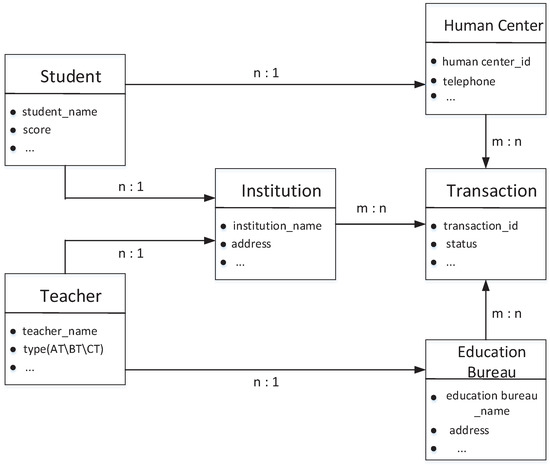
Figure 6.
Ledger Structure Diagram.
4. System Implementation
This chapter describes the configuration of the platform and gives the implementation functions.
4.1. Configuration
The entire alliance network in RSETP has four hosts, each with four Intel(R) Core(TM) i5-10500 CPUs running at 3 GHz and 8 GB of RAM in an Ubuntu 18.04 environment. It is divided into four different organizations, each of which contains peer, orderer, and CouchDB nodes. Each platform node runs in its own Docker container. The party uploading the information uses a verified transaction to ensure that the transaction is safely delivered to the peer node. The chaincode developed in this study is also included on the peer nodes, and each organization verifies the requested transaction and shares it with other organizations by updating the chain. Figure 7 shows the network configuration.
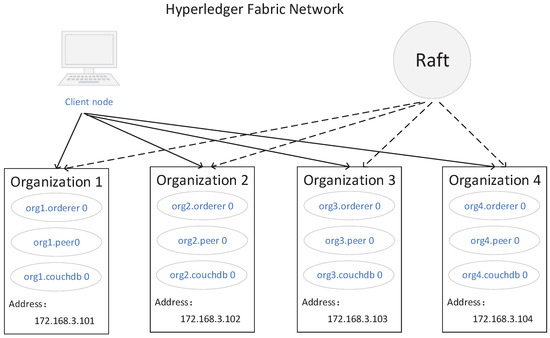
Figure 7.
Hyperledger Fabric network configuration.
In RSETP, the system is built on Hyperledger fabric version 2.2, and the consensus algorithm is Raft. Raft is a distributed consensus algorithm in Hyperledger Fabric. The Raft algorithm will eventually elect a leader node. The sorting process of the Raft algorithm is relatively stable, and re-elections can be automatically performed, even if there is downtime [40]. Each node communicates through the Raft algorithm, similar to cluster services.
4.2. Implementation
In RSETP, the logic design of smart contracts (node.js) will be completed in advance. The contract is deployed in advance in the designated endorsement node, with the goal of providing the necessary services to various institutions and trading centers throughout the network. There are two main types of contracts on the platform: registration contracts and transaction contracts. It mainly includes the functions of organization registration, role registration, student assessment and scoring, and obtaining assessment information.
- (a)
- Registration contracts
The registration contract provides services such as organization registration and personnel registration for the platform.
Institution registration: Each institution provides the necessary information (educational_name, address, etc.). Each newly joined organization has its own CA to register and issue the corresponding digital certificates. The registration agency obtains all parameters from the request method through the files defined in the Hyperledger network in advance, registers the agency, and creates a network identity. The private key, certificate, and other information of the registered organization will be converted into a hash value for storage, and the organization will become a legal participant in the network. The registration process for LCB and LHRC is similar to institutional registration. Algorithm 1 summarizes this process.
| Algorithm 1: Institution Registration. |
 |
Role registration: In the role registration stage, first enter the basic information of the students or teachers (student_name, score, create_time, total_time). The registration transaction is submitted to the blockchain network through the corresponding SDK, and the chaincode in the endorsement node is matched to the corresponding registration method to verify the legitimacy of the request parameters. After the verification is complete, the role will be registered in the network according to the requested transaction information, and a specified network identity will be generated for the role. In this alliance chain, the registration process for each role is similar. Algorithm 2 summarizes this process.
| Algorithm 2: Student Registration. |
 |
- (b)
- Transaction contracts
The transaction contract mainly provides functions such as querying, scoring, and updating information. Applicants can perform compound queries and other operations to realize the business requirements of RSETP. The query operation does not need to send a request to the orderer node; it can be executed directly on the peer. So, this operation will take less time than registration, updating, etc.
Student assessment function: In this alliance chain, the assessment personnel of each institution can conduct performance assessment work on students in different stages, according to their respective authority levels, and record the corresponding assessment and results. For example, CT can evaluate the students’ daily performance, while AT has higher authority and can conduct a comprehensive evaluation based on the students’ monthly performance. Additionally, in this alliance chain, the assessment standards of each institution are unified to ensure the quality of trainee training. Every time the examiner makes a score, he first uploads the requested parameters (score, teacher name, etc.) to the corresponding chaincode. If the transaction is legal, the transaction generates a new hash function value and saves it to the blockchain. If it is illegal, the transaction will be rejected on the chain. For example, the "score" cannot be less than zero. Algorithm 3 describes the process.
| Algorithm 3: Student Assessment Function. |
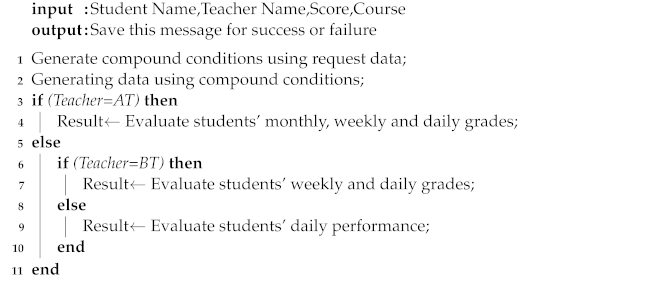 |
Obtain student information: The traditional blockchain system uses the levelDB database for data storage, which has certain limitations. In this consortium chain, we use Couchdb to store data, and Couchdb supports operations such as complex queries. We can specify complex query conditions to search for data according to the needs of the actual situation. For example, we use fields such as student_name, teacher_name, and data as request data, upload this transaction information to the blockchain network, and judge the legality of this transaction. After the request is passed, the corresponding node will match the method corresponding to the transaction in the chaincode, execute the corresponding logic, and return the corresponding query result, according to the custom query conditions and rules. Algorithm 4, below, summarizes this process.
| Algorithm 4: Obtain student training records. |
 |
4.3. Application User Interface
- (a)
- Student information management interface
This interface mainly displays the basic information of all students in the educational institution, including the name, age, date of enrollment, and corresponding assessment status. When a new student joins the training, the administrator will record the student’s information. Upload the student information, along with the secret key information, to the blockchain. The blockchain network checks the transaction. If the record is correct, it will be saved to the blockchain, and a success message will be returned. The interface contains two query boxes, which can accurately find the basic information of a student or a student within a certain period of time through a joint query.
- (b)
- Daily, weekly, and monthly points assessment interface
The daily, weekly, and monthly assessment interfaces are all independent. Behind each student’s information, there will be corresponding daily, weekly, and monthly assessment interfaces. The assessment interface includes the student’s daily, weekly, and monthly assessment scores. The students on this interface will be sorted and displayed on the interface according to their grades, from high to low. The monthly, weekly, and daily assessments are assessed by managers at three different levels to ensure the quality of each trainer’s training. When a problem occurs, it can be traced through the blockchain network to find out what caused it.
- (c)
- Blockchain operation monitoring comprehensive platform interface
The blockchain operating platform supports real-time data monitoring. This page contains essential functions such as blockchain network node query, block query, transaction history query, and smart contract query. Realize the security management and control of the system platform throughout its entire life cycle. The monitoring data information displayed on this page includes network node information, block information, transaction history information, contract information, and channel information. The network real-time data monitoring function dynamically displays the operating parameters of the blockchain network through the real-time push function.
5. Performance Testing
In this chapter, we evaluate and test RSETP from several aspects, including response time, scalability, and data access controllability, to ensure the feasibility of the system. The evaluation experiments will be run on four desktop computers. The configuration of the machine is shown in the Table 2. We use Hyperledger Fabric (version 2.2) and Docker (version 18.02) to build the virtual environment. Each node runs in a docker container, simulating the system. The purpose of using docker containers is for more convenient deployment and more efficient use of computing resources. The communication bandwidth between each node is about 3 Gbps.

Table 2.
System configuration of the experimental machine.
Performance testing is generally used to determine the responsiveness and stability of a system under a specific workload. Among them, stress testing is a simple form of performance testing [41]. We use the Apache Bench (version 2.4.46) load testing tool to test the system by sending simulated request data on two specified HTTP interfaces.
5.1. Response Time Test
In this system, we use the SDK agent to connect the on-chain and off-chain, and we write the SDK in node.js. It is a single-threaded task, but it does all the packaging work. When the system hash calculation volume and transaction volume are relatively large, it also becomes the bottleneck for system performance, and there are concurrency problems. To address this, we will launch a unique SDK agent for each organization. The back-end code identifies users of different organizations, dispatches corresponding on-chain tasks to corresponding chain instances, and performs load balancing through nginx. In this experimental environment, we adjusted the network configuration of the system and started an appropriate number of token chain services. Before and after the configuration modification, the performance of the query and creation functions of the platform improved.
Query operations: First, in this system, the performance of query operations is evaluated by transaction completion time. We sequentially send transaction data of 100, 200,… 500 entries to evaluate the time overhead of the system. From Figure 8, we can see that, in all cases, the time cost increases linearly with the number. However, the network response time after the configuration adjustment (ACM) is significantly faster than the network before the configuration adjustment (BCM). It only takes 0.6 s to complete the query of 500 data records. It can be seen that the query efficiency of the system has been improved to a certain extent.
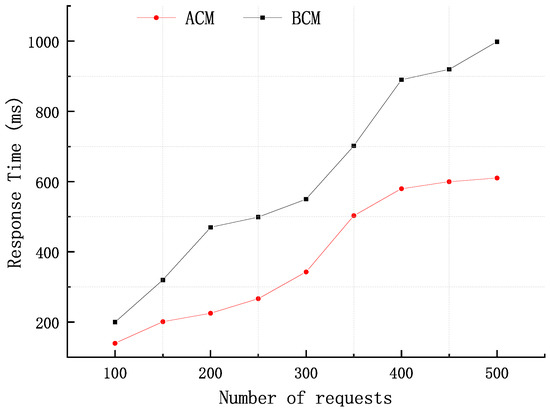
Figure 8.
Query Request Test.
Scalability: The idea of multi-tasking loads also helps to improve the scalability performance of the system. In RSETP, the throughput of RSETP is evaluated by the total number of transactions completed per unit time (RPS). RPS is the speed after each transaction is fully closed. In the experiment, we increased the number of master nodes from 4 to 16, and the scaling performance can be seen through testing. Figure 9 compares the response results under ACM and BCM. For ACM, when the number of nodes is expanded from 4 to 16, the throughput rises from 1000 RPS to around 3300 RPS. For BCM, the throughput remains stable at around 500 RPS. Moreover, the system can theoretically expand nodes indefinitely, and additional organization members can be added to the Docker instance added to the network.
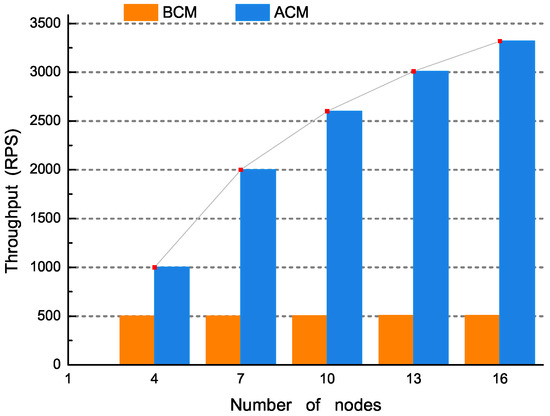
Figure 9.
Scaling performance.
Create operations: Compared with the query operation, the consensus process will make the process of creating operations on the chain more cumbersome, and some service configurations will also affect the efficiency of creating operations. In RSETP, we mainly discuss the impact of block size and transaction number on throughput and set parameters, such as the block generation time and block size, as quantitative values. The experimental consensus protocol is RAFT, and the batch timeout is set to 2 s. We evaluate the throughput under ACM and BCM based on the storage with block sizes of 100 KB, 200 KB, 300 KB, 450 KB, and 600 KB, respectively. We estimate that the size of each transaction data in the system is within 10 k, and the transactions in the system all fall within this range.
Figure 10 plots the throughput curves for different scenarios. By comparing (a) and (b), it can be seen that the throughput has increased significantly after the configuration modification. Additionally, when the block size is set to 450 K, the efficiency of RSETP is basically optimal, and its maximum throughput is around 260 RPS. After the block size exceeds 450 k, continuing to increase the block size cannot improve the throughput of the system. The experimental results show that our research is effective.
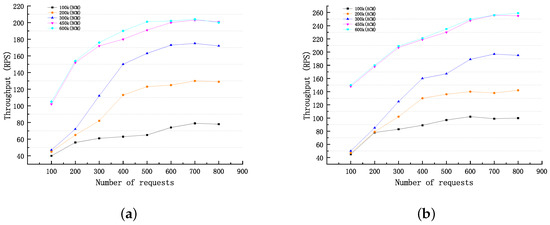
Figure 10.
Create Request Test. (a) Before Configuration Modification. (b) After Configuration Modification.
5.2. Data Access Controllability RSETP
Ensure data privacy with granular access controls assigned to students, faculty, and more. In the Hyperledger network, the model operates based on the defined participant identities. Therefore, malicious users cannot access RSETP data. Channels in the network are structured according to access policies that regulate access to channel storage (such as smart contracts, ledger states, etc.). These channels are composed of nodes that define RSETP privacy and confidentiality. RSETP protects data from unauthorized access, tampering, and similar security breaches. Because it is a decentralized network topology, it is not threatened by a single point of failure or the infiltration of the central repository. Decentralized deployment eliminates the need to work with privatized centralized repositories. The system ensures the availability of RSETP data items, without requiring third-party or member verification. Compared with the process of sending messages to trusted users for authorization control, the system can reduce the time cost in emergency situations.
6. Conclusions
This paper uses the Hyperledger Fabric architecture to design a blockchain education and training management system. Facing the difficulties in the management of education and training information, a blockchain training management and monitoring platform module has been built, which effectively realizes the information exchange of nodes on the chain, such as education and training institutions and regulatory departments, in order to solve the data problems existing in the management process of education and training institutions, disclosure, and counterfeiting issues. Through on-chain and off-chain design ideas, the storage aspects of the blockchain system are optimized. Through flexible network configuration, system performance optimization can be realized. Additionally, the feasibility and efficiency of RSETP are verified through experiments. The solution we propose is suitable for the education and training management system of a multi-node alliance.
In future research, we plan to optimize the on-chain agent of the system, so that organizational users can directly package transactions on the chain at the front-end. This requires each user to obtain its own private key and certificate through the CA first, and an encryption card can be introduced to ensure the security of the key and improve the overall performance. Additionally, we need to combine the opinions of more relevant parties, such as government departments, to further standardize data processing and promote the implementation of educational blockchain projects.
Author Contributions
Conceptualization, X.W.; Methodology, X.W.; Software, R.C.; Investigation, R.C.; Resources, X.W.; Writing—original draft, R.C.; Writing—review & editing, X.L.; Visualization, X.L.; Supervision, X.W.; Project administration, X.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the National Key Research and Development Project (No. 2021YFF0901300), Major Scientific and Technological Innovation Projects of Shandong Province, China (No. 2019JZZY010132), and Key Research and Development Program of Shandong Province, China (No. 2021RKY02021).
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available due to restrictions eg privacy.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Alammary, A.; Alhazmi, S.; Almasri, M.; Gillani, S. Blockchain-based applications in education: A systematic review. Appl. Sci. 2019, 9, 2400. [Google Scholar] [CrossRef]
- Li, Z.Z.; Joseph, K.L.; Yu, J.; Gasevic, D. Blockchain-based solutions for education credentialing system: Comparison and implications for future development. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; pp. 79–86. [Google Scholar]
- The Ministry of Education Has Surveyed 82,246 Training Institutions Across the Country. Available online: https://t.ynet.cn/baijia/32779121.html (accessed on 17 May 2022).
- Zhang, X.; Chen, X. Data security sharing and storage based on a consortium blockchain in a vehicular ad-hoc network. IEEE Access 2019, 7, 58241–58254. [Google Scholar] [CrossRef]
- Taylor, P.; Dargahi, T.; Dehghantanha, A.; Parizi, R.; Choo, K.-K.R. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Vasishta, M.V.A.; Palanisamy, B.; Sural, S. Decentralized Authorization using Hyperledger Fabric. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; pp. 238–243. [Google Scholar]
- Nabben, K. Blockchain security as “people security”: Applying sociotechnical security to blockchain technology. In Principles and Practice of Blockchains; Springer: Berlin/Heidelberg, Germany, 2023; pp. 367–392. [Google Scholar]
- Mohanta, B.; Jena, D.; Panda, S.S.; Sobhanayak, S. Blockchain technology: A survey on applications and security privacy challenges. Internet Things 2019, 8, 100107. [Google Scholar] [CrossRef]
- Kochovski, P.; Gec, S.; Stankovski, V.; Bajec, M.; Drobintsev, P.D. Trust management in a blockchain based fog computing platform with trustless smart oracles. Future Gener. Comput. Syst. 2019, 101, 747–759. [Google Scholar] [CrossRef]
- Ichikawa, D.; Kashiyama, M.; Ueno, T. Tamper-resistant mobile health using blockchain technology. JMIR mHealth uHealth 2017, 5, e7938. [Google Scholar] [CrossRef]
- Hughes, L.; Dwivedi, Y.K.; Misra, S.K.; Rana, N.P.; Raghavan, V.; Akella, V. Blockchain research, practice and policy: Applications, benefits, limitations, emerging research themes and research agenda. Int. J. Inf. Manag. 2019, 49, 114–129. [Google Scholar] [CrossRef]
- Zhou, P.; Du, Y.; Li, B.; Li, Y.; Li, S.; Ji, Z.; Su, X.; Yu, W.; Chen, J.; Tang, X.; et al. China blockchain technology and application development white paper. In Proceedings of the China Blockchain Technology and Application Forum, Beijing, China, 18 October 2016. [Google Scholar]
- Bhaskar, P.; Tiwari, C.K.; Joshi, A. Blockchain in education management: Present and future applications. Interact. Technol. Smart Educ. 2020, 18, 1–17. [Google Scholar] [CrossRef]
- Guo, J.; Li, C.; Zhang, G.; Sun, Y.; Bie, R. Blockchain-enabled digital rights management for multimedia resources of online education. Multimed. Tools Appl. 2020, 79, 9735–9755. [Google Scholar] [CrossRef]
- Zhang, L.; Ma, Z.; Ji, X.; Wang, C. Blockchain: Application in the System of Teaching Informatization Management of Higher Education. In Proceedings of the 2020 3rd International Conference on Smart BlockChain (SmartBlock), Zhengzhou, China, 23–25 October 2020; pp. 185–190. [Google Scholar]
- Turkanović, M.; Hölbl, M.; Košič, K.; Heričko, M.; Kamišalić, A. EduCTX: A blockchain-based higher education credit platform. IEEE Access 2018, 6, 5112–5127. [Google Scholar] [CrossRef]
- Li, Z.; Gao, S.; Peng, Z.; Guo, S.; Yang, Y.; Xiao, B. B-DNS: A secure and efficient DNS based on the blockchain technology. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1674–1686. [Google Scholar] [CrossRef]
- Gao, S.; Peng, Z.; Tan, F.; Zheng, Y.; Xiao, B. SymmeProof: Compact zero-knowledge argument for blockchain confidential transactions. IEEE Trans. Dependable Secur. Comput. 2022. [Google Scholar] [CrossRef]
- Peng, Z.; Xu, J.; Hu, H.; Chen, L.; Kong, H. BlockShare: A Blockchain empowered system for privacy-preserving verifiable data sharing. Bull. IEEE Comput. Soc. Tech. Comm. Data Eng. 2022, 1, 14–24. [Google Scholar]
- Wang, H.; Xu, C.; Zhang, C.; Xu, J.; Peng, Z.; Pei, J. vChain+: Optimizing verifiable blockchain boolean range queries. In Proceedings of the 2022 IEEE 38th International Conference on Data Engineering (ICDE), Kuala Lumpur, Malaysia, 9–12 May 2022; pp. 1927–1940. [Google Scholar]
- Peng, Z.; Zhang, Y.; Xu, Q.; Liu, H.; Gao, Y.; Li, X.; Yu, G. NeuChain: A fast permissioned blockchain system with deterministic ordering. Proc. VLDB Endow. 2022, 15, 2585–2598. [Google Scholar] [CrossRef]
- Ozili, P.K. Blockchain finance: Questions regulators ask. In Disruptive Innovation in Business and Finance in the Digital World; Emerald Publishing Limited: Bingley, UK, 2019. [Google Scholar]
- Truong, N.B.; Sun, K.; Lee, G.M.; Guo, Y. Gdpr-compliant personal data management: A blockchain-based solution. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1746–1761. [Google Scholar] [CrossRef]
- Kaufman, M.; Heister, S.; Yuthas, K. Consortium Capabilities for Enterprise Blockchain Success. J. Br. Blockchain Assoc. 2021, 27744. [Google Scholar] [CrossRef]
- Yang, D.; Long, C.; Xu, H.; Peng, S. A review on scalability of blockchain. In Proceedings of the 2020 The 2nd International Conference on Blockchain Technology, Hilo, HI, USA, 12–14 March 2020; pp. 1–6. [Google Scholar]
- Walsh, C.; O’Reilly, P.; Gleasure, R.; McAvoy, J.; O’Leary, K. Understanding manager resistance to blockchain systems. Eur. Manag. J. 2021, 39, 353–365. [Google Scholar] [CrossRef]
- Peng, Z.; Xu, J.; Chu, X.; Gao, S.; Yao, Y.; Gu, R.; Tang, Y. Vfchain: Enabling verifiable and auditable federated learning via blockchain systems. IEEE Trans. Netw. Sci. Eng. 2021, 9, 173–186. [Google Scholar] [CrossRef]
- Wu, H.; Peng, Z.; Guo, S.; Yang, Y.; Xiao, B. VQL: Efficient and verifiable cloud query services for blockchain systems. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 1393–1406. [Google Scholar] [CrossRef]
- Dinh, T.T.A.; Wang, J.; Chen, G.; Liu, R.; Ooi, B.C.; Tan, K.L. Blockbench: A framework for analyzing private blockchains. In Proceedings of the 2017 ACM International Conference on Management of Data, Chicago, IL, USA, 14–19 May 2017; pp. 1085–1100. [Google Scholar]
- Yang, R.; Wakefield, R.; Lyu, S.; Jayasuriya, S.; Han, F.; Yi, X.; Yang, X.; Amarasinghe, G.; Chen, S. Public and private blockchain in construction business process and information integration. Autom. Constr. 2020, 118, 103276. [Google Scholar] [CrossRef]
- Aswin, A.; Kuriakose, B. An Analogical Study of Hyperledger Fabric and Ethereum. In Intelligent Communication Technologies and Virtual Mobile Networks; Springer: Berlin/Heidelberg, Germany, 2019; pp. 412–420. [Google Scholar]
- Nasir, Q.; Qasse, I.; Talib, M.A.; Nassif, A. Performance analysis of Hyperledger Fabric platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef]
- Alexandridis, A.; Al-Sumaidaee, G.; Alkhudary, R.; Zilic, Z. Making Case for Using RAFT in Healthcare Through Hyperledger Fabric. In Proceedings of the 2021 IEEE International Conference on Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021; pp. 2185–2191. [Google Scholar]
- Hu, J.; Liu, K. Raft consensus mechanism and the applications. J. Phys. Conf. Ser. 2020, 1544, 012079. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 1–11. [Google Scholar] [CrossRef]
- Kabra, N.; Bhattacharya, P.; Tanwar, S.; Tyagi, S. MudraChain: Blockchain-based framework for automated cheque clearance in financial institutions. Future Gener. Comput. Syst. 2020, 102, 574–587. [Google Scholar] [CrossRef]
- Babu, E.S.; Rao, M.S.; Naganjaneyulu, S.; Sai, M.S.S.; Ganiya, R.K. Secure exchange and effectual verification of educational academic records using hyperledger fabric block chain system. Int. J. Ad Hoc Ubiquitous Comput. 2022, 40, 194–213. [Google Scholar] [CrossRef]
- Wang, S. Performance evaluation of hyperledger fabric with malicious behavior. In Blockchain–ICBC 2019: Second International Conference, Held as Part of the Services Conference Federation, SCF 2019, San Diego, CA, USA, 25–30 June 2019, Proceedings 2; Springer: Berlin/Heidelberg, Germany, 2019; pp. 211–219. [Google Scholar]
- Fu, W.; Wei, X.; Tong, S. An improved blockchain consensus algorithm based on raft. Arab. J. Sci. Eng. 2021, 46, 8137–8149. [Google Scholar] [CrossRef]
- Wang, C.; Chu, X. Performance characterization and bottleneck analysis of hyperledger fabric. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 1281–1286. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).