Secure Modern Wireless Communication Network Based on Blockchain Technology
Abstract
:1. Introduction
2. Survey of the Literature
Problem Statement
3. Research Method
3.1. Dataset
3.2. Transaction Verification Denied Conflict with Spurious Node (TVDCSN)
3.2.1. Conflict Rules
- ▪
- If node x broadcasts a WELCOME message with HN(y), node v must verify that none of the nodes indicated by x are one of HN (v). Nodes b and c must be present in HN2(y); therefore, y should choose MPRs that would enable it to connect to them. Nevertheless, y may pretend to wish to select v as MPR for taking care of a and b;
- ▪
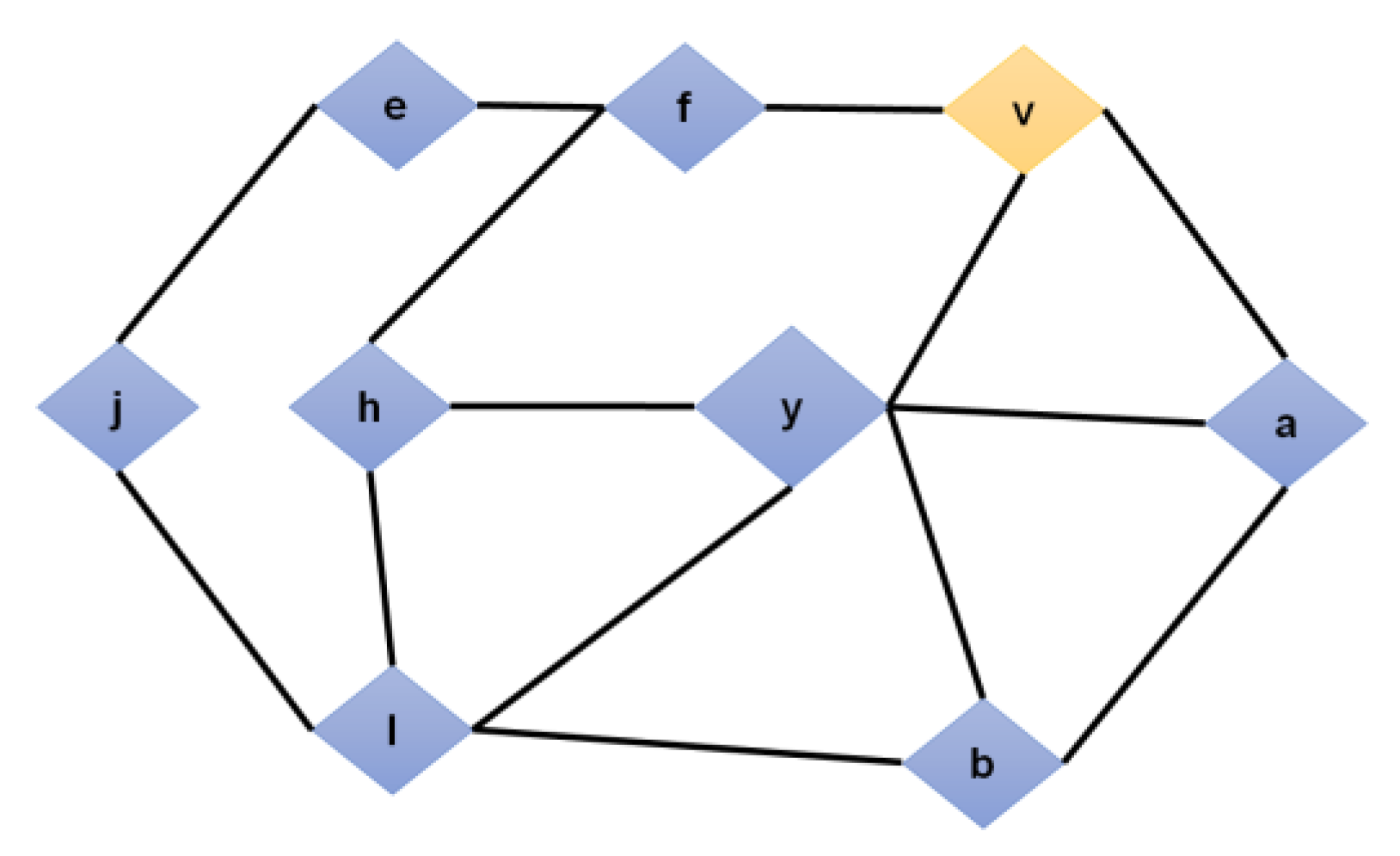
- If a node y is named in a Welcome text, node v must check to determine if there is a node u HN(y) that is (a) not referenced in the recipient’s WELCOME text and (b) at least three hops distant from node v. If such criteria are met, a secondary assessment is required: (c) has w been designated as MPR to fill in for u by y? Figure 2 shows the finding of conflicts to prevent attacks.
- ▪
- Accessing the Topology management (TM) table might be used to perform assessments (a) and (b). There is a conflict if there isn’t an element carrying the MPR that x selected and that enables it to go from x to z in just two hops. Keep in mind that if either condition (a) or (b) is not met, conflicts cannot be found. A TM text must exist where either y has chosen u or u has chosen x as MPR for (c) to be verified. To do this, v must check each u 2 U, where U HN2(y) is dependent on y’s text. Algorithm 1 illustrates the testing of the criterion when the TM message’s structure is “latest (location), dest (location)”;
- ▪
- A WELCOME text with all Hn(v) must be viewed by v as a threat, and necessary action must be taken.
| Algorithm 1: Testing criterion |
| Testing–criterion For each If r.last If r.dest do For each If u For each For each do If Consider y as a malicious node Else Consider y as a trustworthy MPR |
- ▪
- When all nodes in HN2 (v) HN (v) imply that the separation between y and u is less than three-hops, every node v must incorporate a spurious node;
- ▪
- Sv HN(v);
- ▪
- New node u promotes Fu by nature before rule 1 is calculated;
- ▪
- Then, the spurious node is removed when rule (1) is falsifiable;
- ▪
- Regular inspection must be carried out (every spurious verification period).
3.2.2. Block Configuration
3.2.3. Block Maintenance
4. Results and Discussion
4.1. Detection Accuracy (%)
4.2. Attack Prevention (%)
4.3. Security (%)
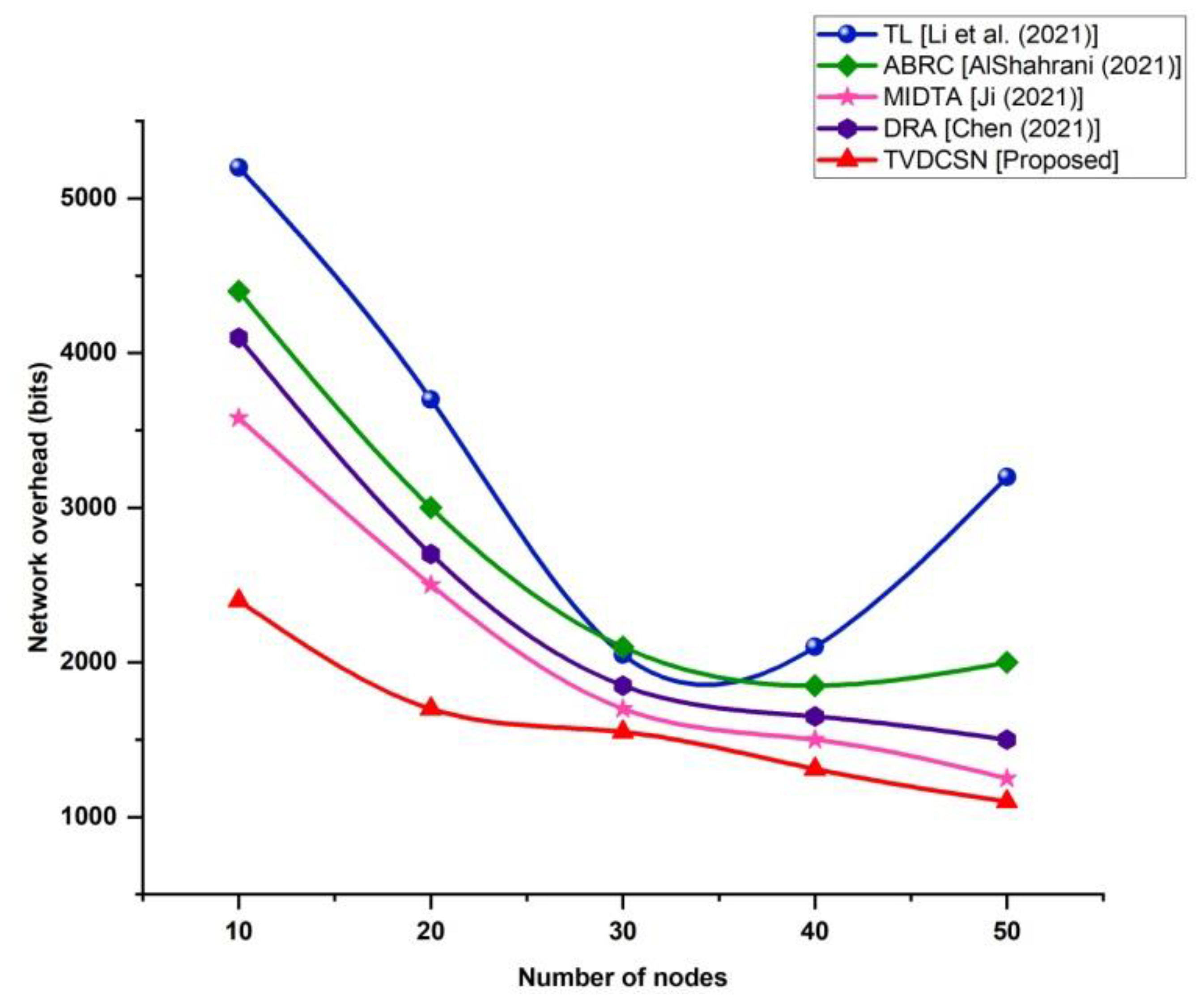
4.4. Network Overhead (Bits)
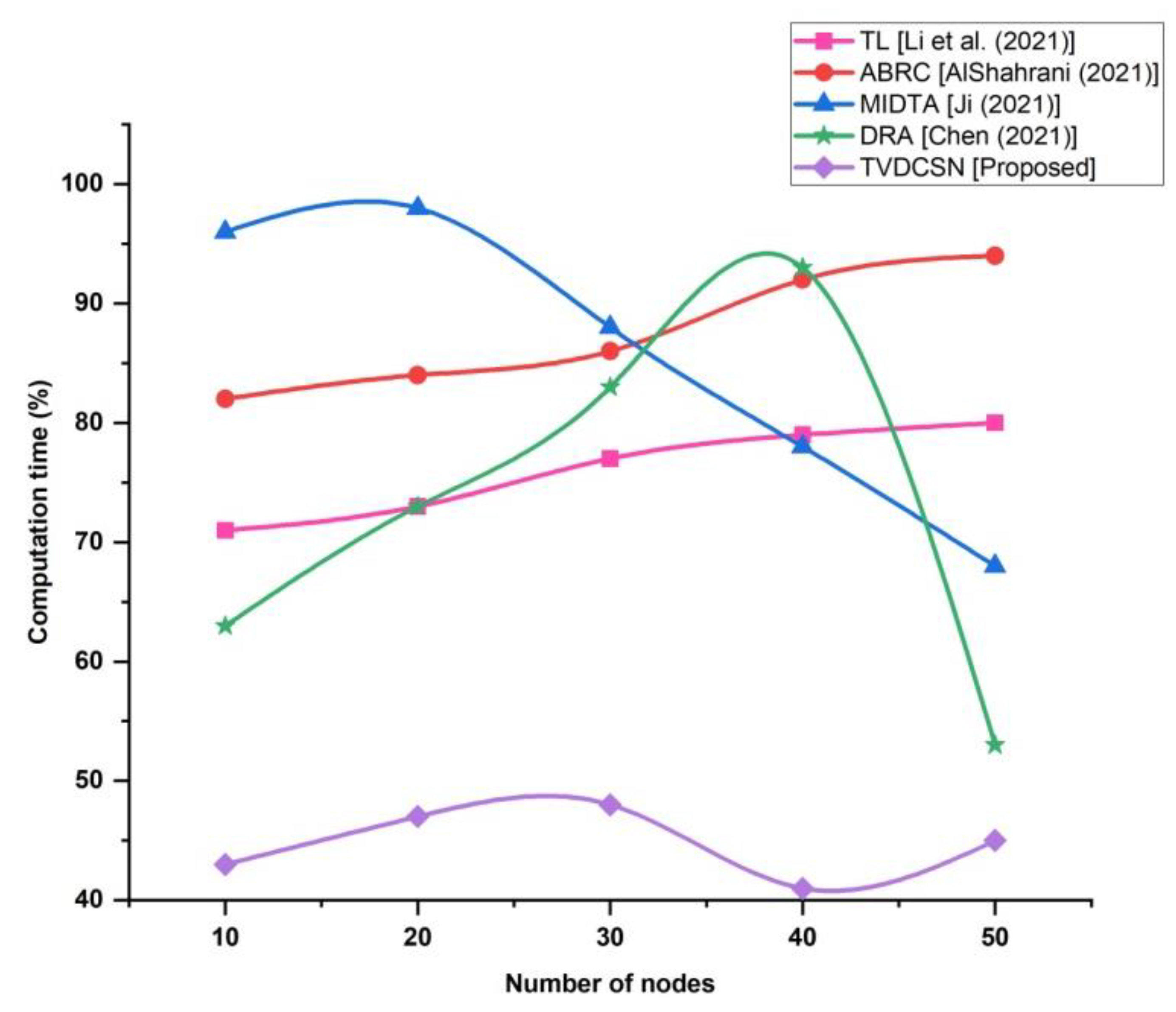
4.5. Computation Time (%)
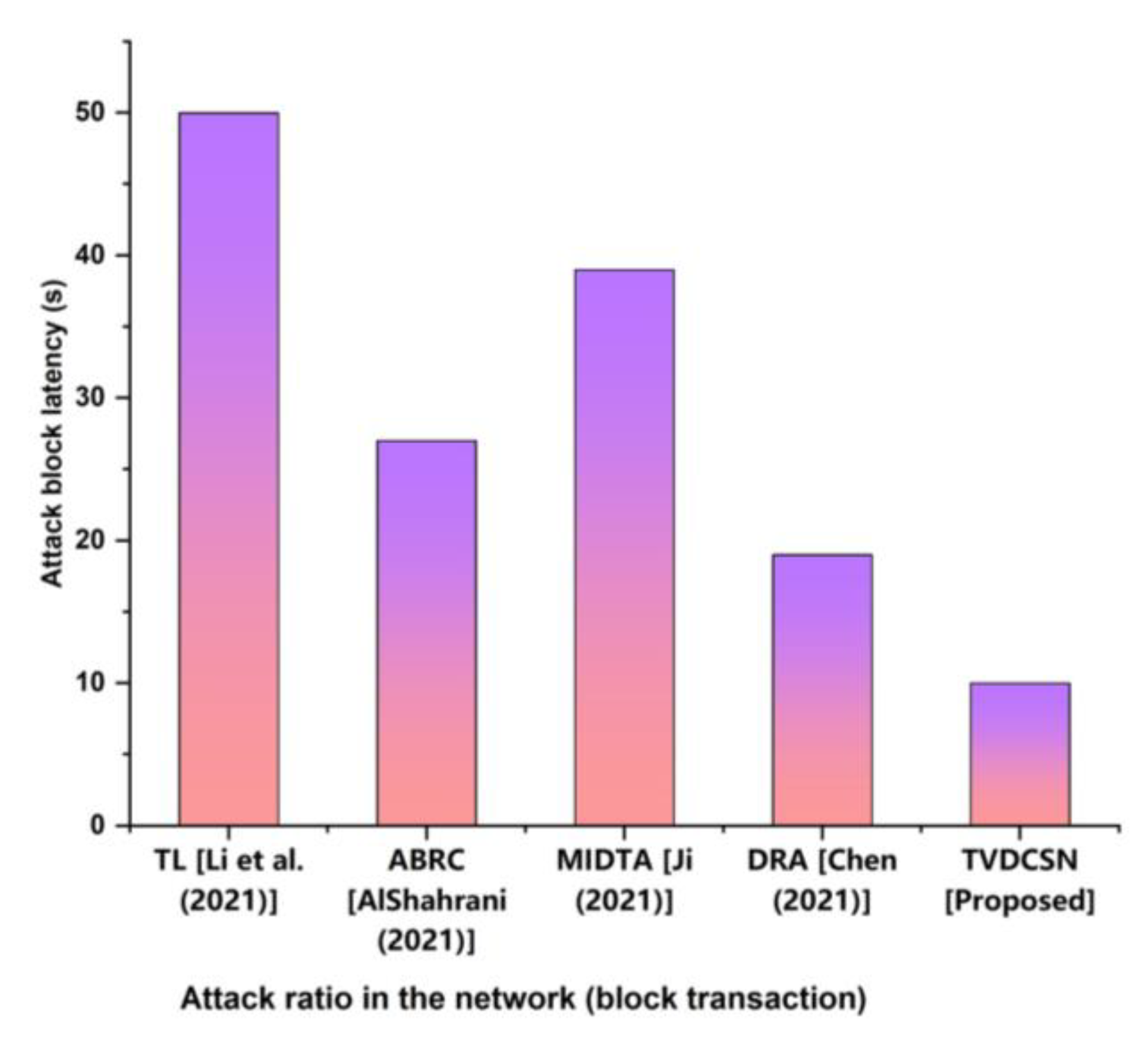
4.6. Block Latency
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Hasan, M.K.; Jang, Y.M. The Role of Optical Wireless Communication Technologies in 5G/6G and IoT Solutions: Prospects, Directions, and Challenges. Appl. Sci. 2019, 9, 4367. [Google Scholar] [CrossRef]
- Jin, L.; Hu, X.; Lou, Y.; Zhong, Z.; Sun, X.; Wang, H.; Wu, J. Introduction to wireless endogenous security and safety: Problems, attributes, structures and functions. China Commun. 2021, 18, 88–99. [Google Scholar] [CrossRef]
- Parvathy, K.; Rajalakshmi, S. A Review on Network Layer Attacks in Wireless Sensor Networks. Int. J. Comput. Sci. Eng. 2021, 9, 45–48. [Google Scholar]
- Srinivasu, P.N.; Bhoi, A.K.; Nayak, S.R.; Bhutta, M.R.; Woźniak, M. Blockchain Technology for Secured Healthcare Data Communication among the Non-Terminal Nodes in IoT Architecture in 5G Network. Electronics 2021, 10, 1437. [Google Scholar] [CrossRef]
- Ramasamy, L.K.; KP, F.K.; Imoize, A.L.; Ogbebor, J.O.; Kadry, S.; Rho, S. Blockchain-Based Wireless Sensor Networks for Malicious Node Detection: A Survey. IEEE Access 2021, 9, 128765–128785. [Google Scholar] [CrossRef]
- Ramesh, S.; Yaashuwanth, C.; Prathibanandhi, K.; Basha, A.R.; Jayasankar, T. An optimized deep neural network based DoS attack detection in wireless video sensor network. J. Ambient. Intell. Humaniz. Comput. 2021, 1–14. [Google Scholar] [CrossRef]
- Joon, D.; Chopra, K. Hybrid Deep Learning Prediction Model for Blackhole Attack Protection in Wireless Communication. Nveo-Nat. Volatiles Essent. Oils J.|NVEO 2021, 8, 10228–10243. [Google Scholar]
- Mughaid, A.; AlZu’bi, S.; Alnajjar, A.; AbuElsoud, E.; Salhi, S.E.; Igried, B.; Abualigah, L. Improved dropping attacks detecting system in 5g networks using machine learning and deep learning approaches. Multimedia Tools Appl. 2022, 1–23. [Google Scholar] [CrossRef]
- Marriwala, N.; Punj, H.; Panda, S.; Kaur, I.; Rathore, D. An Authentication Based Approach for Prevention of Spectrum Sensing Data Falsification Attacks in Cognitive Radio Network. Wirel. Pers. Commun. 2022, 124, 119–145. [Google Scholar] [CrossRef]
- Hanif, M.; Ashraf, H.; Jalil, Z.; Jhanjhi, N.Z.; Humayun, M.; Saeed, S.; Almuhaideb, A.M. AI-Based Wormhole Attack Detection Techniques in Wireless Sensor Networks. Electronics 2022, 11, 2324. [Google Scholar] [CrossRef]
- Yang, H.; Zhang, X.; Cheng, F. A Novel Algorithm for Improving Malicious Node Detection Effect in Wireless Sensor Networks. Mob. Networks Appl. 2021, 26, 1564–1573. [Google Scholar] [CrossRef]
- Pang, B.; Teng, Z.; Sun, H.; Du, C.; Li, M.; Zhu, W. A Malicious Node Detection Strategy Based on Fuzzy Trust Model and the ABC Algorithm in Wireless Sensor Network. IEEE Wirel. Commun. Lett. 2021, 10, 1613–1617. [Google Scholar] [CrossRef]
- Kandel, R. Provenance-Based Malicious Node Detection in Wireless Sensor Network Using Bloom Filter. Doctoral Dissertation, Pulchowk Campus, Lalitpur, Nepal, 2021. [Google Scholar]
- Kumar, M.; Mukherjee, P.; Verma, K.; Verma, S.; Rawat, D.B. Improved Deep Convolutional Neural Network Based Malicious Node Detection and Energy-Efficient Data Transmission in Wireless Sensor Networks. IEEE Trans. Netw. Sci. Eng. 2021, 9, 3272–3281. [Google Scholar] [CrossRef]
- Jagadeesan, S.; Manjula, R.; Johnpeter, T. December. In A Cross-Layer based Hidden Marko (C-HMM) Model for Detection and Prevention of Malicious Attacks in Wireless Ad-hoc Networks. In Proceedings of the 2021 IEEE International Conference on Mobile Networks and Wireless Communications (ICMNWC), Tumkur, India, 3–4 December 2021; IEEE: Piscataway, NJ, USA; pp. 1–5. [Google Scholar]
- Gowri, S.; Srinivasulu, S.; Jabez, J.; Vimali, J.S.; Sivasangari, A. Discovery of localized malicious attack in wireless networks. In Smart Computing Techniques and Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 207–216. [Google Scholar] [CrossRef]
- Sharma, T.; Mohapatra, A.K.; Tomar, G. SDBMND: Secure Density-Based Unsupervised Learning Method with Malicious Node Detection to Improve the Network Lifespan in Densely Deployed WSN. Wirel. Commun. Mob. Comput. 2022, 2022, 1–15. [Google Scholar] [CrossRef]
- Ali, F.; El-Sappagh, S.; Islam, S.R.; Ali, A.; Attique, M.; Imran, M.; Kwak, K.-S. An intelligent healthcare monitoring framework using wearable sensors and social networking data. Futur. Gener. Comput. Syst. 2021, 114, 23–43. [Google Scholar] [CrossRef]
- Li, S.; Pang, J.; Wu, Q.; Yao, N.; Yuan, W. Transfer learning based attack detection for wireless communication networks. Concurr. Comput. Pr. Exp. 2021, 33, e6461. [Google Scholar] [CrossRef]
- AlShahrani, B.M.M. Classification of cyber-attack using Adaboost regression classifier and securing the network. Turk. J. Comput. Math. Educ. (TURCOMAT) 2021, 12, 1215–1223. [Google Scholar]
- Ji, K. Malicious Intrusion Data Mining Algorithm of Wireless Personal Communication Network Supported by Legal Big Data. Wirel. Commun. Mob. Comput. 2021, 2021, 1–7. [Google Scholar] [CrossRef]
- Chen, J. An identification method of malicious nodes in wireless communication based on dynamic reputation algorithm. Int. J. Inf. Commun. Technol. 2021, 19, 343–355. [Google Scholar] [CrossRef]
- Bargarai, F.A.M.; AbdulAzeez, A.M.; Tiryaki, V.M.; Zeebaree, D.Q. Management of Wireless Communication Systems Using Artificial Intelligence-Based Software Defined Radio. Int. J. Interact. Mob. Technol. (iJIM) 2020, 14, 107–133. [Google Scholar] [CrossRef]
- Beritelli, F.; Capizzi, G.; Sciuto, G.L.; Napoli, C.; Tramontana, E.; Wozniak, M. Reducing interferences in wireless communication systems by mobile agents with recurrent neural networks-based adaptive channel equalization. In Photonics Applications in Astronomy, Communications, Industry, and High-Energy Physics Experiments; SPIE: Washington, DC, USA, 2015; Volume 9662, pp. 497–505. [Google Scholar] [CrossRef]
- Kouhalvandi, L.; Shayea, I.; Ozoguz, S.; Mohamad, H. Overview of evolutionary algorithms and neural networks for modern mobile communication. Trans. Emerg. Telecommun. Technol. 2022, 33, e4579. [Google Scholar] [CrossRef]
- Janjua, K.; Shah, M.A.; Almogren, A.; Khattak, H.A.; Maple, C.; Din, I.U. Proactive forensics in IoT: Privacy-aware log-preservation architecture in fog-enabled-cloud using holo-chain and containerization technologies. Electronics 2020, 9, 1172. [Google Scholar] [CrossRef]


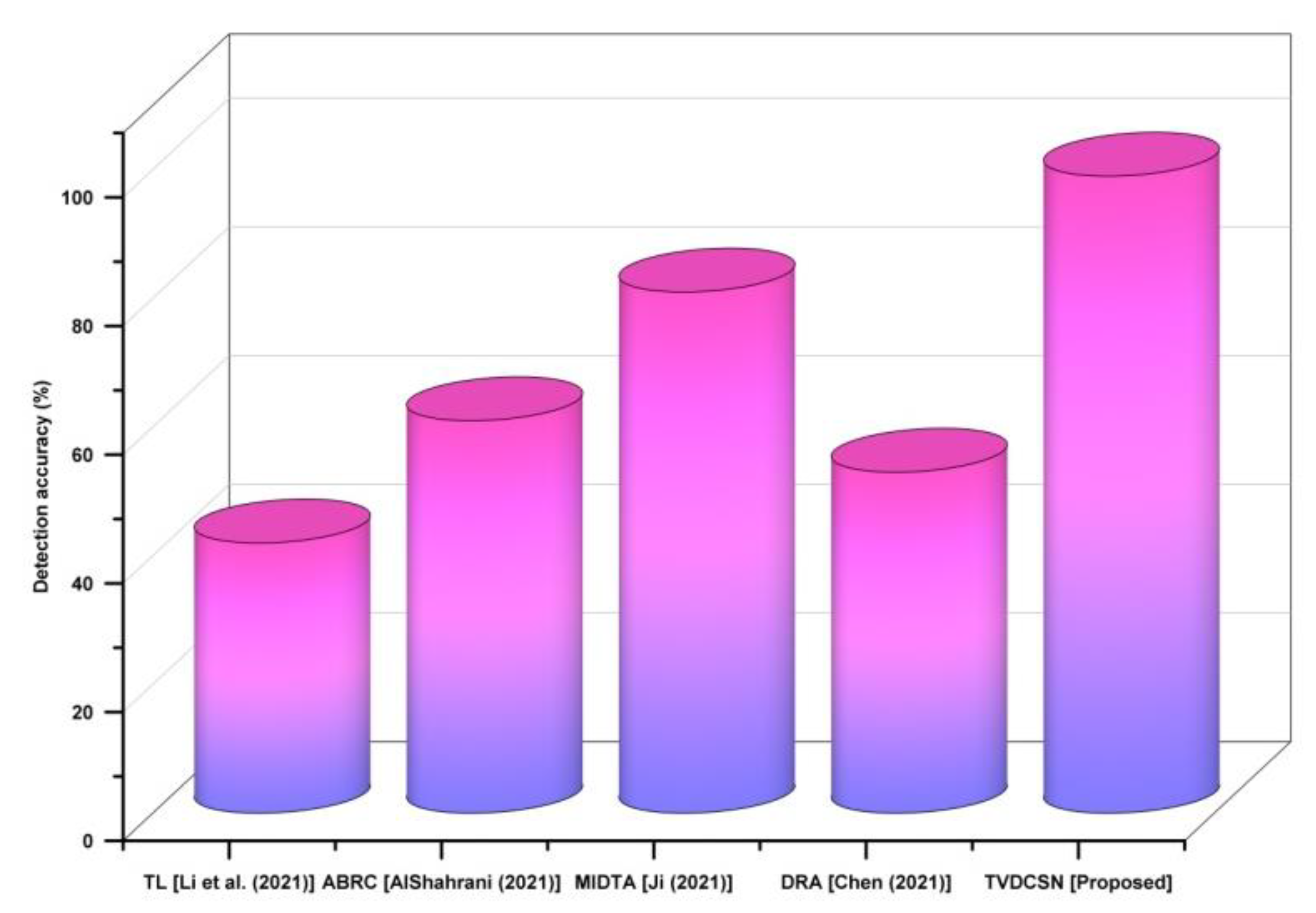


| Methods | Detection Accuracy (%) |
|---|---|
| TL (Li et al. (2021)) | 42 |
| ABRC (AlShahrani (2021)) | 61 |
| MIDTA (Ji (2021)) | 81 |
| DRA (Chen (2021)) | 53 |
| TVDCSN (Proposed) | 99 |
| Methods | Attack Prevention (%) |
|---|---|
| TL (Li et al. (2021)) | 63 |
| ABRC (AlShahrani (2021)) | 81 |
| MIDTA (Ji (2021)) | 52 |
| DRA (Chen (2021)) | 43 |
| TVDCSN (Proposed) | 98 |
| Methods | Security (%) |
|---|---|
| TL (Li et al. (2021)) | 52 |
| ABRC (AlShahrani (2021)) | 71 |
| MIDTA (Ji (2021)) | 81 |
| DRA (Chen (2021)) | 62 |
| TVDCSN (Proposed) | 97 |
| Number of Nodes | Network Overhead (Bits) | ||||
|---|---|---|---|---|---|
| TL (Li et al. (2021)) | ABRC (AlShahrani (2021)) | MIDTA (Ji (2021)) | DRA (Chen (2021)) | TVDCSN (Proposed) | |
| 10 | 5200 | 4400 | 3580 | 4100 | 2400 |
| 20 | 3700 | 3000 | 2500 | 2700 | 1700 |
| 30 | 2050 | 2100 | 1700 | 1850 | 1550 |
| 40 | 2100 | 1850 | 1500 | 1650 | 1310 |
| 50 | 3200 | 2000 | 1250 | 1500 | 1100 |
| Number of Nodes | Computation Time (%) | ||||
|---|---|---|---|---|---|
| TL (Li et al. (2021)) | ABRC (AlShahrani (2021)) | MIDTA (Ji (2021)) | DRA (Chen (2021)) | TVDCSN (Proposed) | |
| 10 | 71 | 82 | 96 | 63 | 43 |
| 20 | 73 | 84 | 98 | 73 | 47 |
| 30 | 77 | 86 | 88 | 83 | 48 |
| 40 | 79 | 92 | 78 | 93 | 41 |
| 50 | 80 | 94 | 68 | 53 | 45 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chandan, R.R.; Balobaid, A.; Cherukupalli, N.L.S.; H L, G.; Flammini, F.; Natarajan, R. Secure Modern Wireless Communication Network Based on Blockchain Technology. Electronics 2023, 12, 1095. https://doi.org/10.3390/electronics12051095
Chandan RR, Balobaid A, Cherukupalli NLS, H L G, Flammini F, Natarajan R. Secure Modern Wireless Communication Network Based on Blockchain Technology. Electronics. 2023; 12(5):1095. https://doi.org/10.3390/electronics12051095
Chicago/Turabian StyleChandan, Radha Raman, Awatef Balobaid, Naga Lakshmi Sowjanya Cherukupalli, Gururaj H L, Francesco Flammini, and Rajesh Natarajan. 2023. "Secure Modern Wireless Communication Network Based on Blockchain Technology" Electronics 12, no. 5: 1095. https://doi.org/10.3390/electronics12051095
APA StyleChandan, R. R., Balobaid, A., Cherukupalli, N. L. S., H L, G., Flammini, F., & Natarajan, R. (2023). Secure Modern Wireless Communication Network Based on Blockchain Technology. Electronics, 12(5), 1095. https://doi.org/10.3390/electronics12051095















