Abstract
We explore the influence of cooperative jamming on covert communication for integrated satellite–terrestrial relay networks (ISTRN) in this article, where one full-duplex relay is utilized to support communications and acts as a jammer to confuse eavesdroppers. A cooperative scheme is first proposed to efficiently achieve covert communication in this specific scenario. Further, the probability of detection error (PDE) is derived. Subsequently, the minimum PDE is calculated using the optimal detection threshold. Moreover, a closed-form expression of outage probability (OP) is acquired to quantify the system’s covert performance. Based on this, we design a power optimization algorithm to enhance the effective covert rate under covertness constraints. Lastly, numerical simulation results are given to verify the efficiency of our cooperative jamming scheme when interrupting the eavesdroppers. Notably, an optimal power allocation factor can be obtained, leading to a higher effective covert rate.
1. Introduction
Satellite communication (SatCom) has received a great deal of attention in recent years [1], due to its wide coverage and free from geographical conditions. It is helpful for achieving global communication and has been an indispensable part of the fifth-generation (5G) wireless communication system. Moreover, because of the complementarity of SatCom and traditional terrestrial communication, it has become one of the hot topics in the field of wireless communication to combine SatCom and traditional terrestrial communication [2]. The integrated satellite–terrestrial relay networks (ISTRN) can not only achieve global coverage but also realize the interconnection between satellites and terrestrial base stations.
In addition, it is able to obtain, transmit and process satellite–terrestrial information in real-time [3]. On the premise of ensuring service quality, the ISTRN has clear advantages in bandwidth, power loss, spectrum utilization and comprehensive service [4]. Nevertheless, due to the openness of wireless communication and the wide coverage of satellite beams, the secure environment of wireless communication in the ISTRN is increasingly severe [5]. In the search for effective secure communication technology and to analyze its performance in this network, we present the related research.
1.1. Related Work
SatCom has developed rapidly and become one of the critical components of future wireless communication networks in recent years [6]. This has many advantages, such as wide coverage, improved flexibility and enhanced quality of service (QoS) and can be employed as a potent supplement for terrestrial communication [7]. Based on this, one of the defining features of 6G wireless communication networks will be the integration of SatCom and terrestrial networks.
Further, the ISTRN absorbs the merits of SatCom and terrestrial networks [8], and thus can not only satisfy gradually expanding communication demands but also diversify communication ways. Many scholars have conducted extensive and in-depth research. In [7], the authors provided a comprehensive study of emerging technologies for 6G-oriented integrated satellite–terrestrial networks, further including an analysis of the component architectures, a discussion of typical applications and a presentation of potential future challenges.
Similarly, the authors of [9] explored how to design and implement a 6G-oriented integrated satellite–terrestrial network. The communication performance of the ISTRN with multi-antenna terrestrial relays was analyzed after considering hardware impairments and the effects of interference on relays and destinations in [10]. In [11], the authors introduced cognitive radio (CR) and non-orthogonal multiple access (NOMA) techniques into the ISTRN in order to significantly improve the spectrum utilization efficiency and studied the system performance in a multi-user scenario based on this.
Furthermore, the authors of [12] investigated the impact of channel estimation errors (CEE) and hardware losses (HI) on the security performance of the above-mentioned ISTRN with CR and NOMA techniques. Considering the demands of different users for spectral efficiency in the ISTRN, two antenna selection strategies were proposed to balance the effectiveness and complexity of the system in [13]. In addition, the joint problem of user association and spectrum allocation in ISTRN was studied in [14,15].
However, owing to the broadcast characters of the satellite beams and the openness of wireless communication, secrecy problems always exist in ISTRN [16]. Without loss of generality, ensuring that malicious eavesdroppers are unaware of communication behavior between legitimate parties may be the most direct and effective method of secure communication. As an emerging security technique, covert communication aims to achieve secure and reliable wireless communication with a low probability of being detected [17]. Moreover, there are various applications for this, such as secret combat operations, intelligent reflecting surfaces and unmanned aerial vehicle (UAV) networks [18].
In previous pioneering works, the authors illustrated the limits of covert communication [19,20], such as the square root law. To enhance its effectiveness, the work by Sobers used an uninformed jammer, which generated artificial noise for the eavesdroppers [21]. Moreover, the authors of [22] utilized the inherent uncertainty of channels to realize covert transmission in relay networks. In [23], the feasibility and achievable performance of covert communication were examined in amplify-and-forward (AF) relay networks. To further improve the system’s covert performance, an optimization strategy for the system capacity was proposed in [24].
The authors of [25] used a full-duplex receiver to transmit a jamming signal to confuse the eavesdropper while receiving the information sent by the transmitter. In [26], the authors performed a similar investigation, differing from the previous study in that a delay constraint was also considered. The covert performance of a wireless relay communication system consisting of a transmitter, receiver, relay and eavesdropper was investigated in [27], where the relay could operate in full-duplex mode or convert to half-duplex mode.
The authors of [28] studied whether a self-sustained relay could forward source information while secretly transmitting covert information of it. In that paper, its feasibility was demonstrated, and the performance limits as well as associated costs were obtained. Moreover, not only covert communication between terrestrial nodes but also UAV-based air-terrestrial covert communication has been widely investigated [29,30,31].
Inspired by the above works, we note that covert communication with positive rate is usually achieved by various uncertainties inherent in the system or the assistance of the jammer. In view of better controllability and performance, jammer-assisted approaches to achieve covert communication have been widely adopted and studied. Nevertheless, almost all the previous works of others have been based on independent terrestrial networks. Moreover, existing assisted jamming schemes mainly allow transmitters or receivers to be equipped with full duplex antennas as jamming nodes or deploy specific jammers to emit artificial noise to confuse eavesdroppers. Although all of the above mainstream approaches can better achieve covert communication, they inevitably have the following shortcomings:
- The artificial noise can degrade the quality of legitimate communication.
- Legitimate communication resources are tied up or costly to achieve.
- It is easy to arouse the suspicion of eavesdroppers.
Based on this, the relay cooperative scheme is proposed. Given its own characteristics, it can partially or completely solve the above problems and has been considered as one of the key means to achieve effective covert communication. In addition, the introduction of a relay can also increase the diversity of channel uncertainty, which can bring gains to the covert performance of the system. Thus far, the performance of covert communication with relay-assisted cooperative jamming, particularly for the ISTRN, has not been reported.
Therefore, this article aims to study the impact of cooperative jamming on covert communication for the ISTRN, where the relay is employed to aid information transmission and acts as a jammer to cheat the eavesdropper. Further, the probability of detection error (PDE) of the eavesdropper is deduced. In addition, we propose a cooperative scheme to realize efficient covert communication in the ISTRN. To quantify the system’s covert performance, the closed-form expression of outage probability (OP) and effective covert rate are derived. Lastly, we obtain the optimal power allocation factor, leading to the maximum effective covert rate under covert constraints.
1.2. Motivation and Contributions
Recently, the security of wireless communications in the ISTRN has gradually gained attention from scholars. In this article, we select the covert communication technique to solve the above problem, which is more direct and effective. Nevertheless, the existing related works are mostly based on terrestrial networks or use an individually deployed jammer. This motivated us to explore the covert performance of the ISTRN with relay-assisted cooperative jamming. Notably, the main features and contributions of this article are summarized as follows:
- Covert communication in the ISTRN with relay-assisted cooperative jamming is studied for the first time, where one full-duplex terrestrial relay is utilized to support communications and acts as a jammer to confuse eavesdroppers.
- Based on the above, the closed-form expression of the PDE and the effective covert rate are deduced to quantify the system’s covert performance.
- Moreover, a power optimization algorithm is designed to explore how to enhance the effective covert rate under covertness constraints.
- Subsequently, numerical simulation results are presented to observe the influence of relevant parameters on the covert performance. Finally, the observation results are analyzed and summed up in detail.
2. System Model and Problem Formulation
Primarily, we propose a specific covert system model. Then, the related signal model is explored. Last, based on the above, the problem we research is formulated.
2.1. System Description
In Figure 1, we establish the ISTRN with cooperative jamming, including one satellite equipped with a multi-beam antenna; a legitimate user ; one full-duplex terrestrial relay , which has a set of transceiver antennas and adopts the AF model; and one eavesdropper , which is located near the R. S utilizes the fixed spot beam to communicate with B, directly covering R and adjacent E.
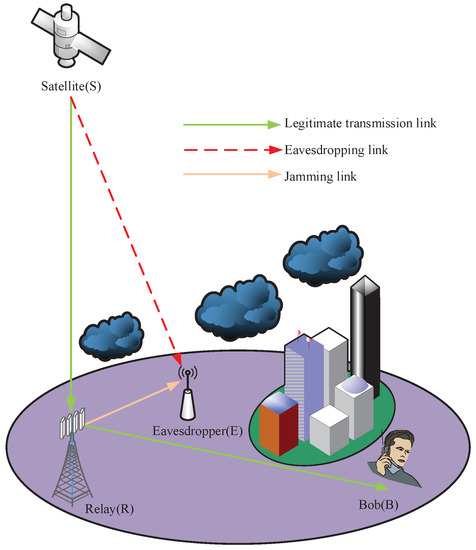
Figure 1.
The ISTRN with relay-assisted cooperative jamming.
In the considered system model, the satellite S always transmits source information to B via relaying. The direct link from S to B is unreachable because of the bad weather, building blocks and other heavy fading. E attempts to detect and confirm whether the transmission from S to B is on or off. Therefore, a cooperative jamming scheme for the terrestrial relay is proposed to achieve efficient covert communication.
R uses the full-duplex mode, which not only receives the signals from S as a relay but also generates jamming signals for confusing E in the first time slot. Then, the re-transmission enables source information to be obtained by B covertly in the second time slot. We consider the worst case, namely, that E is aware of the possible time when S may send its source information and owns all the knowledge of the system. (If it owns all the knowledge of the system, E is able to reduce the uncertainty and enhance its accuracy of detection significantly. The assumption here is the worst case, which enables our model credible and universal [32]).
Moreover, for the link , we define its channel coefficient as . This is an independent, zero-mean circularly symmetric complex Gaussian random variable with unit variance. A block fading environment is considered, implying that discrete-time channel coefficients are unchanged in one block but vary independently between blocks. Lastly, we deem that R, E and B are all constantly disturbed by additive white Gaussian noise (AWGN).
2.2. Signal Model
In the first time slot, S randomly selects the transmission model between two models: Model one, something transmission with power ; and Model zero, nothing transmission. Moreover, whatever model S chooses, R always confuses E by transmitting the jamming signals with power so as to achieve reliable covert communication between S and B. Moreover, we note that the corresponding self-interference cancellation technique of R enables its self-interference to be removed partially. Hence, the received signal of R in the first time slot can be given by
where and represent that S chooses Model one and Model zero, respectively. denotes the normalized signal from S; ; n is the number of channel used in each time slot; and . Moreover, represents the AWGN at R and . To simplify the subsequent analysis, it is assumed that for . In addition, represents the residual self-interference derived from the jamming signal , which also meets . Moreover, , and denotes the residual factor.
Then, is amplified by R with the coefficient G when is true in the second time slot. It is worth noting that R always employs automatic gain control to guarantee that its transmit power is , where the gain . Even if S stops working or remains silent, R still forwards the jamming signals continuously. Moreover, it is assumed that B is aware of the jamming code book. Therefore, the continuous jamming signals can be successfully decoded and eliminated at B.
2.3. Problem Formulation
Since R always sends either the re-transmission or the jamming signals in the second time slot, we primarily pay attention to the first time slot. At this time, E attempts to use the related detection device to judge whether S transmits its source information to B. Therefore, two types of detection error will occur inevitably, which are expressed as
where and are the missed detection and false alarm probabilities, respectively.Clearly, represents E judges that no transmission at S, and is the opposite.
Without loss of generality, no matter what strategy E adopts, we can only realize the reliable covert communication if the following constraint is satisfied [32], namely
where denotes any sufficiently small constant that satisfies and represents the requirement of covert communication, and denotes PDE. The reliability of covert communication depends on whether (3) can be satisfied. For E, both types of detection error are intolerable. On the contrary, S, R and B tend to confuse E as much as possible to degrade its detection ability.
In this letter, we pay attention to obtaining the maximum effective covert rate to fight against E, which can be defined as
where denotes the required rate between S and B, and represents the OP for the ISTRN.
Furthermore, we present a practical and effective scheme of power allocation for the ISTRN. We define the total transmitted power as , which is fixed in our relay system, where S and R are treated as a whole. One variable factor is set. , , and . Moreover, to ensure covertness, we should also consider the constraint of (3). Thus, we describe the optimization problem as
3. Performance Analysis
We mainly focus on covert performance for the ISTRN with relay-assisted cooperative jamming in this section. First, the related channels’ statistical characteristics are derived. Moreover, the closed-form solution of PDE is obtained. Further, we calculate the minimum PDE of E using the optimal detection threshold. To measure the system covert performance, the closed-form expression of OP is derived. Finally, our scheme of power allocation is employed to optimize the effective covert rate under the covertness constraint.
3.1. Statistical Properties of Channels
Considering the actual scenario and referring to the relevant study [5], it is generally believed that terrestrial channels obey the independent identically distributed (i.i.d.) Rayleigh fading. Thus, the probability distribution function (PDF) and cumulative distribution function (CDF) of are obtained, respectively, as
where is the received signal-to-noise ratio (SNR), represents the average gain of channel, and .
Moreover, it is inevitable to use multi-beam technology to improve the spectral efficiency in SatCom, which should be considered in the establishment of a channel model [33]. However, in the previous system description, we assumed that the relay and the eavesdropper are in close proximity and under the same beam coverage. Therefore, the subsequent formula derivation and analysis are based on the specific single beam. In addition, the channels of satellite–terrestrial links are generally modeled as shadowed Rician (SR) fading channels. Therefore, the coefficient can be shown as
where is the SR coefficient, and represents the loss that depends on the radio frequency, including the free space loss and antenna gain. Therefore, can be written as
where represents the carrier wavelength of the transmitted signal, s denotes the distance from the terrestrial station to the center of the satellite beam, and 35,786 km. is the satellite beam gain, and is the relevant antenna gain.
In addition, for parabolic antenna [34], the can be expressed as
where represents the upper limit of the relevant antenna gain, and denotes the deflection angle of S. Moreover, is the angle from the terrestrial station to the center of the satellite beam, and denotes the satellite beam’s 3 dB angle. Thus, the beam gain of S is shown as [35]
where , denotes the maximum of , , and are the order 1 and 3 first-kind Bessel functions, respectively. Generally, to gain the system’s best performance, —namely, , and further, .
From [36], the PDF of is given by
where denotes the fading severity parameter, represents the line of sight (LOS) link’s average power, and is half of the average power of the multi-path links. In addition, , , and .
Generally, is an integer. Through utilizing [37], we can obtain the confluent hyper-geometric function
Thus, the above Formula (12) is rewritten as
and
where is a Pochhammer function [37], and .
3.2. Probability of Detection Error
In the first time slot, the likelihood ratio test is utilized by E, which further employs radiometry to perform the binary detection [21]. Moreover, we obtain the signal received at E as
where . Furthermore, it should be noted that E is usually unaware of the code book for the signal .
Based on (16), denotes the average received power, which is used as the test statistic by E, namely
where represents the detection threshold of E. Relying on the strong law of large numbers and (2), the false alarm probabilities of E are written as
where .
By means of (6), we can obtain the as
where .
Moreover, the probability of missed detection at E is derived as
With the help of (6) and (14), the can be rewritten as
By utilizing the specific combination function of exponential and rational in [37], namely
where
and , , .
Therefore, the PDE for a preset can be given by
According to , a new constraint can be obtained, which can be expressed as
which implies that there is a new range for the .
On the other hand, since E aims to minimize the PDE, it will never select the case of , which represents an absolute incorrect detection. Therefore, the optimal detection threshold for E, defined as , occurs only when . It can be calculated by , which has been solved and shown in numerical simulation. Furthermore, under the prescribed optimal detection threshold , the minimum PDE at E should be expressed as
3.3. Effective Covert Rate
When S forwards its source information, the signal received by B from the AF relay should be expressed as
Through a series of derivations, the equivalent instantaneous end-to-end SNR of B is expressed as
where , and further, . In the noise-limited system, the outage probability denotes the probability that , which represents the actual system capacity, falls below the required transmission rate . Consequently, the OP should be written as
To facilitate the derivations of the (29), can be approximately equivalent to by its upper boundary as
Based on this, a closed-form lower bound of can be rewritten as
where , , and .
By combining Equations (4) and (31), a closed form of effective covert rate is derived as
From derivation and discussion, we note that the monotonically increases with the rising and , where their sum is fixed. This indicates that we can employ , the optimal factor for power allocation, to obtain the maximum . However, based on the optimization function (5), even if acquiring the absolute by (32), we should further discuss whether it is in the feasible region derived from covertness constraints—namely, and (25). After that, the global optimum power allocation solution will be obtained to maximize the effective covert rate , which was solved and is shown subsequently.
4. Numerical Simulation Results
Numerical simulation results are given for exploring the impact of the system parameters on the covert performance of the ISTRN there. In our simulation, we set the W, the noise power dB and the required transmission rate bps/Hz. Moreover, the system parameters are shown in Table 1 [35], and Table 2 gives a series of parameters based on the SR fading channel [36].

Table 1.
The system parameters.

Table 2.
The channel parameters.
Figure 2 plots the PDE versus with diverse detection thresholds, where , and under ILS. Clearly, when , the eavesdropper can minimize its PDE. Moreover, it is clear that the rise of may create more randomness and can better hide source signals, which causes a larger detection error probability at E. Furthermore, when , approaches 1. In addition, it should be noted that there is an upper limit to the .
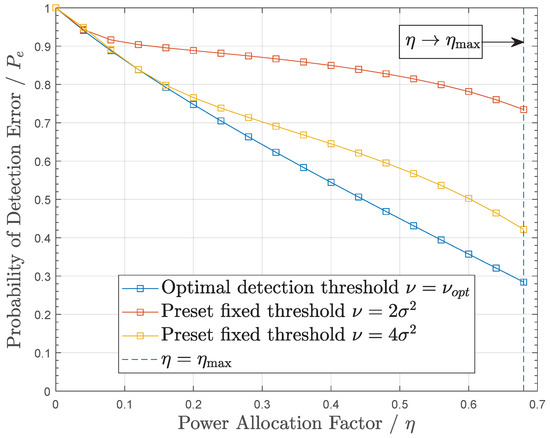
Figure 2.
PDE versus under different detection thresholds.
Figure 3 shows the PDE with optimal detection thresholds versus under different shadowing types. Compared with the above, this illustrates that, with the worsening of channel shadowing, increases continuously. This is because the E is interfered by not only the R but also the channel uncertainty. Additionally, the value interval of varies with the change of fading type, which verifies Formula (25). For the jamming performance, the above two figures show a similar pattern—namely, as the jamming power decreases, the jamming performance gradually weakens, and the eavesdropper is able to detect the presence of legitimate communications increasingly accurately.
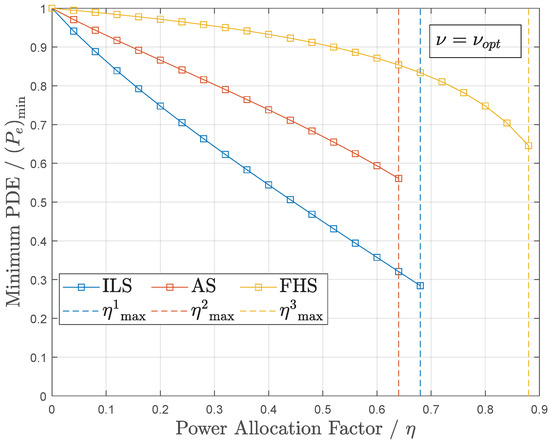
Figure 3.
Minimum PDE versus under different fading types.
Therefore, in order to ensure system covertness, sufficiently high jamming power is necessary. However, higher jamming power is not better. Excessive jamming power can produce more pronounced jamming noise at the receiver, which is not conducive to effectively achieving covert communication. Thus, how to balance the relationship between the transmission power and jamming power is the key to strengthening the jamming performance.
Figure 4 depicts the versus for diverse , which shows the effectiveness of the proposed scheme by us. It should be noted that, when continues rising, increases first and then stabilizes, which implies that, as the value of rises, the requirement for covertness decreases, allowing higher communication rates. Moreover, when is small, the global optimum power allocation factor varies with its increase, which enables the to increase. However, as continues to rise, the optimal and global will be unchanged. We list the when reaches the stable maximum value. Furthermore, it should be noted that the worse channel shadowing contributes to the rise of but also inevitably causes the decrease of . Lastly, we can see that, as increases, the effective covert rate improves significantly.
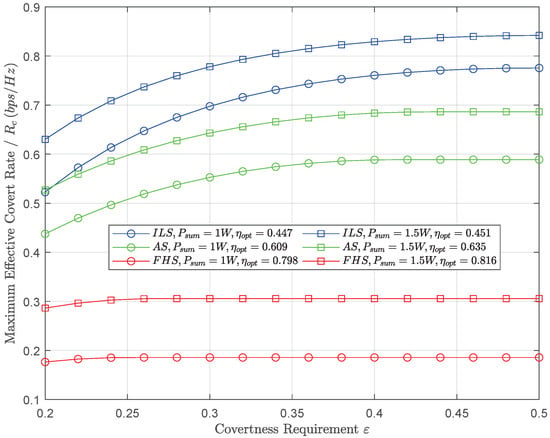
Figure 4.
The maximum versus covertness requirement for different values of the total transmission power.
5. Conclusions
As shown in Table 3, we compare this article with some current research on covert communication and briefly summarize its innovations. Furthermore, the main work and contribution are elaborated as follows. In this article, we primarily studied the covert performance in ISTRN with cooperative jamming. Primarily, we proposed a specific system model of covert communication, which was based on ISTRN. Our work aimed to maximize the effective covert rate under a covertness constraint. To improve the system’s effectiveness, a relay cooperative scheme was presented. Based on this, the probability of detection error at the eavesdropper and the outage probability of legitimate communication were obtained to quantify the system’s covert performance.

Table 3.
Comparative analysis with the current research on covert communication.
Further, in order to explore the impacts of transmission power and jamming power on covert communication and to enhance the covert performance, a power optimization algorithm was presented. Through the numerical simulation results, it was clear that, as the transmission power increased and the jamming power decreased, the probability of detection error declined continuously as the legitimate communication signal was more easily detected by the eavesdropper, which suffered less interference at the same time—namely, its detection became more accurate.
Moreover, as the transmission power rose, there was a gain in the effective covert rate. However, in order to meet the covertness, higher jamming power was also required, which brought heavy interference to the legitimate communication. Based on this, we designed the power allocation factor and found that an optimal power allocation factor, which effectively balanced the information and jamming power, could be obtained to achieve system covertness. Lastly, the numerical simulation results also implied that a higher covert rate was allowed when the covertness requirement was weakened.
Author Contributions
Z.W., K.G. and S.Z. conceived and designed the experiments; Z.W. performed the experiments; K.G. analyzed the data; S.Z. contributed analysis tools; and Z.W. wrote the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Science Foundation of China under Grants 62001517, 61901502 and 61971474 and by the National Postdoctoral Program for Innovative Talents under Grant BX20200101.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AF | Amplify and forward |
| AWGN | Additive white Gaussian noise |
| CDF | Cumulative distribution function |
| CEE | Channel estimation errors |
| CR | Cognitive radio |
| GEO | Geosynchronous earth orbit |
| HI | Hardware losses |
| ISTRN | Integrated satellite–terrestrial relay networks |
| LOS | Line of sight |
| NOMA | Non-orthogonal multiple access |
| OP | Outage probability |
| PDE | Probability of detection error |
| Probability distribution function | |
| QoS | Quality of service |
| SatCom | Satellite communication |
| SNR | Signal-to-noise ratio |
| SR | Shadowed Rician |
| TDMA | Time division multiple access |
| UAV | Unmanned aerial vehicle |
References
- Zhu, S.; Yang, X.; Xiao, N.; Liu, D. Overview of 5G and satellite hybrid network development. In Proceedings of the International Conference on Wireless Communications and Smart Grid (ICWCSG), Hangzhou, China, 13–15 August 2021; pp. 360–366. [Google Scholar]
- Wu, Z.; Liu, R.; Shuai, H.; Zhu, S.; Li, C. Covert performance for integrated satellite multiple terrestrial relay networks with partial relay selection. Sensors 2022, 22, 5524. [Google Scholar] [CrossRef]
- Evans, B.; Werner, M.; Lutz, E.; Bousquet, M.; Corazza, G.E.; Maral, G.; Rumeau, R. Integration of satellite and terrestrial systems in future multimedia communications. IEEE Wirel. Commun. 2005, 12, 72–80. [Google Scholar] [CrossRef]
- Chen, S.; Sun, S.; Kang, S. System integration of terrestrial mobile communication and satellite communication—The trends, challenges and key technologies in B5G and 6G. China Commun. 2020, 17, 156–171. [Google Scholar] [CrossRef]
- Guo, K.; An, K.; Zhang, B.; Huang, Y.; Guo, D. Physical layer security for hybrid satellite terrestrial relay networks with joint relay selection and user scheduling. IEEE Access 2018, 6, 55815–55827. [Google Scholar] [CrossRef]
- Guo, K.; An, K.; Zhang, B.; Huang, Y.; Tang, X.; Zheng, G.; Tsiftsis, T.A. Physical layer security for multi-user satellite communication systems with threshold-based scheduling scheme. IEEE Trans. Veh. Technol. 2020, 69, 5129–5141. [Google Scholar] [CrossRef]
- Zhu, X.; Jiang, C. Integrated satellite-terrestrial networks toward 6G: Architectures, applications, and challenges. IEEE Internet Things J. 2022, 9, 437–461. [Google Scholar] [CrossRef]
- Wang, W.; Chen, T.; Ding, R.; Seco-Granados, G.; You, L.; Gao, X. Location-based timing advance estimation for 5G integrated LEO satellite communications. IEEE Trans. Veh. Technol. 2021, 70, 6002–6017. [Google Scholar] [CrossRef]
- Zhu, X.; Jiang, C. Creating efficient integrated satellite-terrestrial networks in the 6G era. IEEE Wirel. Commun. 2022, 29, 154–160. [Google Scholar] [CrossRef]
- Guo, K.; Lin, M.; Zhang, B.; Wang, J.B.; Wu, Y.; Zhu, W.P.; Cheng, J. Performance analysis of hybrid satellite-terrestrial cooperative networks with relay selection. IEEE Trans. Veh. Technol. 2020, 69, 9053–9067. [Google Scholar] [CrossRef]
- Liu, R.; Guo, K.; An, K.; Zhu, S.; Shuai, H. NOMA-based integrated satellite-terrestrial relay networks under spectrum sharing environment. IEEE Wirel. Commun. Lett. 2021, 10, 1266–1270. [Google Scholar] [CrossRef]
- Guo, K.; Dong, C.; An, K. NOMA-based cognitive satellite terrestrial relay network: Secrecy performance under channel estimation errors and hardware impairments. IEEE Internet Things J. 2022, 9, 17334–17347. [Google Scholar] [CrossRef]
- Shuai, H.; Guo, K.; An, K.; Huang, Y.; Zhu, S. Transmit antenna selection in NOMA-based integrated satellite-HAP-terrestrial networks with imperfect CSI and SIC. IEEE Wirel. Commun. Lett. 2022, 11, 1565–1569. [Google Scholar] [CrossRef]
- Qiu, W.; Liu, A.; Han, C.; Lu, A. Joint user association and spectrum allocation in satellite-terrestrial integrated networks. IEICE Trans. Commun. 2022, E105B, 1063–1077. [Google Scholar] [CrossRef]
- Qiu, W.; Liu, A.; Han, C. Joint down-link spectrum allocation and user association for satellite-terrestrial integrated networks. In Proceedings of the IEEE 14th International Conference on Advanced Information Technology (ICAIT), Chongqing Univ, Chongqing, China, 8–11 October 2021; pp. 19–24. [Google Scholar]
- Jin, L.; Hu, X.; Lou, Y.; Zhong, Z.; Sun, X.; Wang, H.; Wu, J. Introduction to wireless endogenous security and safety: Problems, attributes, structures and functions. China Commun. 2021, 18, 88–99. [Google Scholar] [CrossRef]
- Yan, S.; Zhou, X.; Hu, J.; Hanly, S.V. Low probability of detection communication: Opportunities and challenges. IEEE Wirel. Commun. 2019, 26, 19–25. [Google Scholar] [CrossRef]
- Zhou, X.; Yan, S.; Hu, J.; Sun, J.; Li, J.; Shu, F. Joint optimization of a UAV’s trajectory and transmit power for covert communications. IEEE Trans. Signal Process. 2019, 67, 4276–4290. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D. Limits of reliable communication with low probability of detection on AWGN channels. IEEE J. Sel. Areas Commun. 2013, 31, 1921–1930. [Google Scholar] [CrossRef]
- Wang, L.; Wornell, G.W.; Zheng, L. Fundamental limits of communication with low probability of detection. IEEE Trans. Inf. Theory 2016, 62, 3493–3503. [Google Scholar] [CrossRef]
- Sobers, T.V.; Bash, B.A.; Guha, S.; Towsley, D.; Goeckel, D. Covert communication in the presence of an uninformed jammer. IEEE Trans. Wirel. Commun. 2017, 16, 6193–6206. [Google Scholar] [CrossRef]
- Wang, J.; Tang, W.; Zhu, Q.; Li, X.; Rao, H.; Li, S. Covert communication with the help of relay and channel uncertainty. IEEE Wirel. Commun. Lett. 2019, 8, 317–320. [Google Scholar] [CrossRef]
- Hu, J.; Yan, S.; Zhou, X.; Shu, F.; Li, J.; Wang, J. Covert communication achieved by a greedy relay in wireless networks. IEEE Trans. Wirel. Commun. 2018, 17, 4766–4779. [Google Scholar] [CrossRef]
- Zhang, Y.; He, W.; Li, X.; Peng, H.; Rabie, K.; Nauryzbayev, G.; ElHalawany, B.M.; Zhu, M. Covert communication in down-link NOMA systems with channel uncertainty. IEEE Sens. J. 2022, 22, 19101–19112. [Google Scholar] [CrossRef]
- Shahzad, K.; Zhou, X.; Yan, S.; Hu, J.; Shu, F.; Li, J. Achieving covert wireless communications using a full-duplex receiver. IEEE Trans. Wirel. Commun. 2018, 17, 8517–8530. [Google Scholar] [CrossRef]
- Shu, F.; Xu, T.; Hu, J.; Yan, S. Delay-constrained covert communications with a full-duplex receiver. IEEE Wirel. Commun. Lett. 2019, 8, 813–816. [Google Scholar] [CrossRef]
- Hu, J.; Yan, S.; Shu, F.; Wang, J. Covert rate maximization in wireless full-duplex relaying systems with power control. IEEE Trans. Commun. 2021, 69, 6198–6212. [Google Scholar]
- Hu, J.; Yan, S.; Shu, F.; Wang, J. Covert transmission with a self-sustained relay. IEEE Trans. Wirel. Commun. 2019, 18, 4089–4102. [Google Scholar] [CrossRef]
- Zhang, R.; Lu, R.; Cheng, X.; Wang, N.; Yang, L. A UAV-enabled data dissemination protocol with proactive caching and file sharing in V2X networks. IEEE Trans. Commun. 2021, 69, 3930–3942. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, R.; Zhang, J.; Yang, L. Cooperative jamming via spectrum sharing for secure UAV communications. IEEE Wirel. Commun. Lett. 2020, 9, 326–330. [Google Scholar] [CrossRef]
- Liu, B.; Zhu, X.; Jiang, Y.; Wei, Z.; Huang, Y. UAV and piece-wise convex approximation assisted localization with unknown path loss exponents. IEEE Trans. Veh. Technol. 2019, 68, 12396–12400. [Google Scholar] [CrossRef]
- Zhang, R.; Chen, X.; Liu, M.; Zhao, N.; Wang, X.; Nallanathan, A. UAV relay assisted cooperative jamming for covert communications over rician fading. IEEE Trans. Veh. Technol. 2022, 71, 7936–7941. [Google Scholar] [CrossRef]
- Arnau, J.; Christopoulos, D.; Chatzinotas, S.; Mosquera, C.; Ottersten, B. Performance of the multi-beam satellite return link with correlated rain attenuation. IEEE Trans. Wirel. Commun. 2014, 13, 6286–6299. [Google Scholar] [CrossRef]
- ITU-R. Prediction Procedure for the Evaluation of Interference between Stations on the Surface of the Earth at Frequencies above about 0.1 GHz, 1st ed.; ITU-R: Geneva, Switzerland, 2013; p. 452-15. [Google Scholar]
- An, K.; Liang, T.; Zheng, G.; Yan, X.; Li, Y.; Chatzinotas, S. Performance limits of cognitive-uplink FSS and terrestrial FS for Ka-band. IEEE Trans. Aerosp. Electron. Syst. 2019, 55, 2604–2611. [Google Scholar] [CrossRef]
- Miridakis, N.I.; Vergados, D.D.; Michalas, A. Dual-hop communication over a satellite relay and shadowed rician channels. IEEE Trans. Veh. Technol. 2015, 64, 4031–4040. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M.; Jeffrey, A.; Zwillinger, D. Table of Integrals, Series and Products, 7th ed.; Elsevier: Amsterdam, The Netherlands, 2007. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).