Chebyshev Polynomial-Based Fog Computing Scheme Supporting Pseudonym Revocation for 5G-Enabled Vehicular Networks
Abstract
1. Introduction
- We present a fog computing technique for 5G-enabled vehicle networks, which is based on the Chebyshev polynomial and allows for the revocation of pseudonyms.
- We adapt fog computing in the proposed scheme to generate security parameters and check the validity of vehicles.
- We adapt the 5G technology to increase the communication range among vehicles and the system, which avoid the expensive RSU used.
- In order to stop an insider attack, we use fog computing. As soon as the fog server detects that a pseudonym-timestamp ID is about to expire, it will not renew the signature key.
- Our solutions not only pass all privacy and security tests but are also resistant to a wide range of common security assaults.
- In our study, we use the Chebyshev polynomial to sign messages and verify the signature, which results in lower overall performance costs.
2. Related Work
3. Background
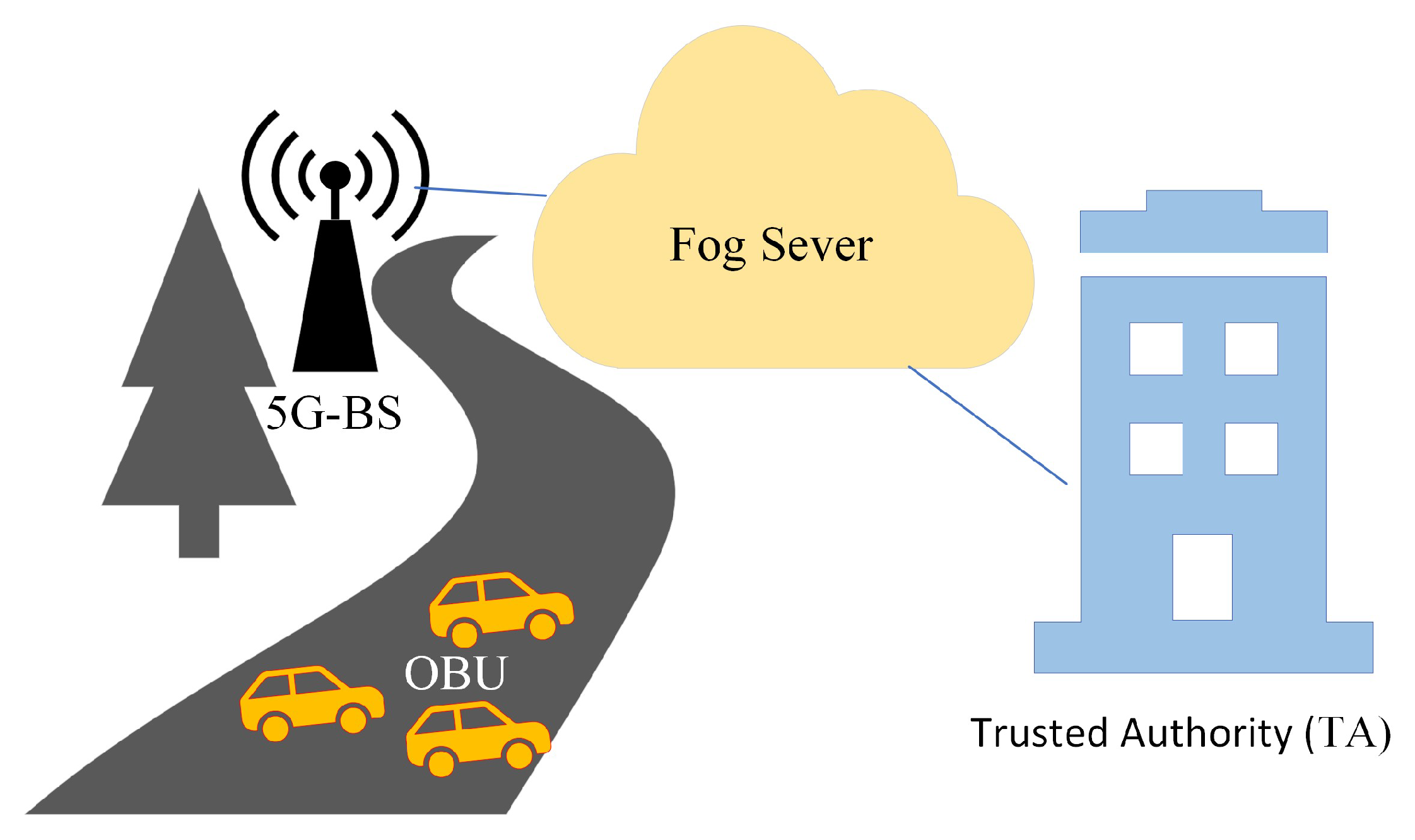
3.1. Architecture
- TA: TA is in charge of providing a valid computation and storage capacity for the main parameter of fog servers and OBUs within its authority. If the system contains incorrect or malicious information, the TA can trace and revoke the pseudonym-ID of the information source. In the vehicular network, all entities hold TA in high regard, and it is impossible to compromise TA.
- 5G-BS: A 5G-BS is a piece of roadway infrastructure that is permanently installed. Through the 5G protocol and secure wired connections, the 5G-BS can communicate with the vehicle’s OBU and the TA within a large range of communication.
- Fog Server: The fog server is in charge of providing the signature key of participating vehicles during joining through 5G-BS. The fog server saves the system’s master key to validate and authenticate the vehicle. We trust the fog server implicitly to help TA reveal the signers’ identities.
- OBU: The vehicle is equipped with an OBU that supports the dedicated short-range communication (DSRC) protocol and 5G protocol. The OBU sends a traffic-related message to the other OBUs or fog servers on a regular basis, informing them of traffic statuses, such as speed, location, and danger warnings.
3.2. Design Goals
- Authentication and Integrity: The authenticity of the owner and validity of the message must be fulfilled to avoid any modification from the attacker.
- Identity Privacy: The true identity of the vehicle should be hidden in pseudonym-ID of the message.
- Traceability: The TA can trace any insider attacker by revealing the true identity of the vehicle.
- Pseudonym Revocation: The TA has the ability to revoke insider attackers to use services.
- Unlinkability: The attacker cannot link several signatures sent by the same owner.
- Resistance to Security Attacks: Our proposal must resist the security attacks, such as replay, forgery, modify, and man-in-the-middle attacks.
- Efficient: Our proposal must lower performances costs in terms of communication and computational overheads.
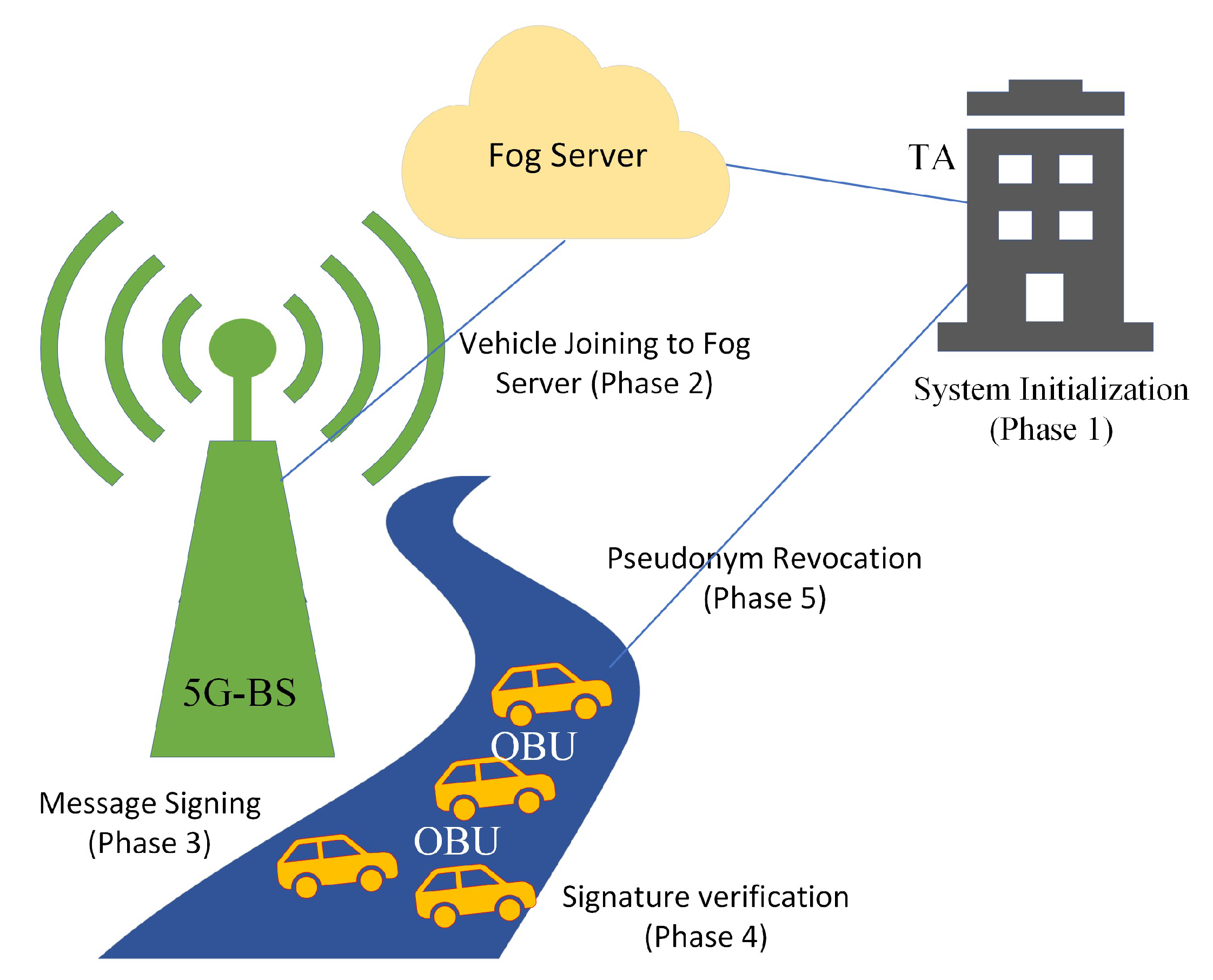
3.3. Proposed Framework
- System Initialization (Phase 1): In our work, the TA is in charge of setting up the security parameters and registering vehicles and fog servers.
- Vehicle Joining to Fog Server (Phase 2): When a vehicle joins the covered area of the fog server through 5G-BS, it should be validated and authenticated to that fog server to share messages according to the parameters of the fog server. When a vehicle enters the covered area of the new fog server or its pseudonym-ID is expired, it should be joined to the fog server area and obtains the signature key and pseudonym-ID from the fog server.
- Message Signing (Phase 3): Before messages can be transmitted between vehicles on 5G-enabled networks, the linked vehicle must sign them using its signature key.
- Signature Verification (Phase 4): Before proceeding with the message , the receiver-enrolled vehicle must verify the authenticity of the final-tuple {, , , , , }.
- Pseudonym Revocation (Phase 5): Prior to the adversary broadcasting counterfeit messages to disrupt the 5G-enabled vehicular networks, we are able to track down the fraudulently registered car and revoke its pseudonym-ID during the pseudonym revocation phase.
3.4. Mathematics Used
- Elliptic Curve: Number theorists place a premium on elliptic curves, and this topic is currently a hotspot for study, for instance, Andrew Wiles’s demonstration of Fermat’s Last Theorem relied on elliptic curves. Elliptic curve cryptography (ECC) and integer factorization are two other areas where they are useful. Some studies [29,30] based on elliptic curve.
- Bilinear Pair: Ingenious systems for one-round three-party key negotiation, identity-based encryption, and aggregate signatures have all been developed using bilinear pairings. For certain selected elliptic curves, the Tate pairing can be used to generate appropriate bilinear pairings. Some studies [31,32,33] based on bilinear pair.
4. Proposed Scheme
4.1. System Initialization (Phase 1)
- Let P and be the large prime and generated values regarding Chebyshev polynomial, respectively.
- TA chooses a random number as its master secret key.
- Let be one-way hash function according to Chebyshev polynomial.
- Let {, x, P, h} be the security parameters.
- TA chooses a random number as secret parameter.
- Let = be an authentication code.
- TA preloads an authentication code and the security parameters { , x, P, h} in each vehicle.
- TA preloads the master key and the security parameters { , x, P, h} in each fog server.
4.2. Vehicle Joining to Fog Server (Phase 2)
- The vehicle chooses random number and computes parameter mod P and calculates pseudonym-ID , where is a vehicle’s true identity and is a newness timestamp.
- The vehicle sends the first-tuple to TA through 5G-BS by assisting fog server, where .
- The TA then reveals vehicle’s true identity by computing , where is an authentication code.
- Once checking the validity and authenticity of the vehicle’s true identity , the TA sends to the fog server via the secure channel.
- The fog server selects the signature key as the following Equation.
- The fog server encrypts the signature key as the following Equation.
- The fog server sends the second-tuple to vehicle, where and is a valid timestamp obtained from fog server.
- After checking the freshness of timestamp , the vehicle decrypts the signature key as the following Equation.
4.3. Message Signing (Phase 3)
- The vehicle signs the message , where is current timestamp.
- A signature of the communication is calculated by the vehicle as .
- The vehicle then uses V2V communication on 5G-enabled vehicular networks to broadcast the final-tuple {, , , , , } to other cars.
4.4. Signature Verification (Phase 4)
- Upon receiving the final-tuple {, , , , , }, the checker initially tests the newness of timestamp as Equation (1).
- The checker then computes the parameter .
- The checker then uses the signature of the final-tuple {, , , , , } to validate the message , where . The checker accepts the message when Equation (5) holds. If the message does not meet these requirements, it will be rejected
4.5. Pseudonym Revocation (Phase 5)
- Upon the malicious registered vehicle broadcasting the final-tuple {, , , , , }, the fog server computes the vehicle’s true identity as Equation (6).
- The fog server then sends to the TA through a secure channel.
- The TA checks the data stored about it in the vehicle registration list and deletes it.
- The TA sends to all fog servers for revoking process.
- Once the valid timestamp is close to expiring, the malicious vehicle requests a new signature key from the fog server.
- After checking the in the revocation list, the fog server rejects the request because it is revoked.
5. Result
5.1. Security Analysis
- Authentication and Integrity: The checker in our work can verify the legality and integrity of the final-tuple {, , , , , } by verifying whether Equation (5) holds. Thus, the legality and integrity of our work are satisfied.
- Identity Privacy: In a 5G-enabled vehicular network, the vehicle’s true identity of is involved in the pseudonym-ID of the final-tuple {, , , , , } generated by the vehicle. Hence, no attacker can obtain the true identity of the vehicle through the . Thus, our work satisfies the identity privacy requirement.
- Traceability: The true identity of the vehicle is hidden in the generated by the vehicle, where . By using an authentication code , the TA or fog server computes by calculating . Hence, our work provides a traceability requirement.
- Pseudonym Revocation: Once the process of traceability is done, the TA has the ability to revoke the pseudonym of the vehicle as shown in Section 4.5. Hence, our work provides a pseudonym revocation requirement.
- Unlinkability: The vehicle uses a pseudonym-ID to create the final-tuple {, , , , , }. Once the valid timestamp is close to expiring, the vehicle creates a new pseudonym-ID to request a new signature for completing the joining process. Our work also utilizes the freshness timestamp to compute the signature . Any attacker who tries to link multiple final-tuples {, , , , , } may not succeed because of changes in their pseudonym-ID and timestamp. Nevertheless, no linkability issue arises in our work.
- Resistance to Replay Attacks: The newness timestamp is included in the final-tuple {, , , , , }. Before accepting the message , the verifier checks whether the inequality holds. If it is valid, the verifier accepts the message to be checked further; otherwise, the message is rejected. Therefore, the resistance to replay attacks is satisfied in our work.
- Resistance to Forgery Attacks: The attacker cannot forge a valid final-tuple {, , , , , } in our work. This is because the checker can verify the authenticity of the final-tuple {, , , , , } by computing whether the equation holds. If it is valid, the checker accepts the message ; otherwise, it is rejected. Therefore, the resistance to forgery attacks is satisfied in our work.
- Resistance to Modify Attacks: The attacker cannot easily modify a valid final-tuple {, , , , , }, where . The checker can check the validity of the final-tuple {, , , , , } by computing whether the equation holds. If it is so, the checker accepts the message ; otherwise, it is rejected. Therefore, the resistance to modify attacks is satisfied in our work.
- Resistance to Man-In-The-Middle Attacks: The investigation of the node authenticity and message validity above proves that it is necessary to verify that the relation between the signer and the checker should be verified and that a real message cannot be modified and fabricated. Therefore, the resistance to man-in-the-middle attacks is satisfied in our work.
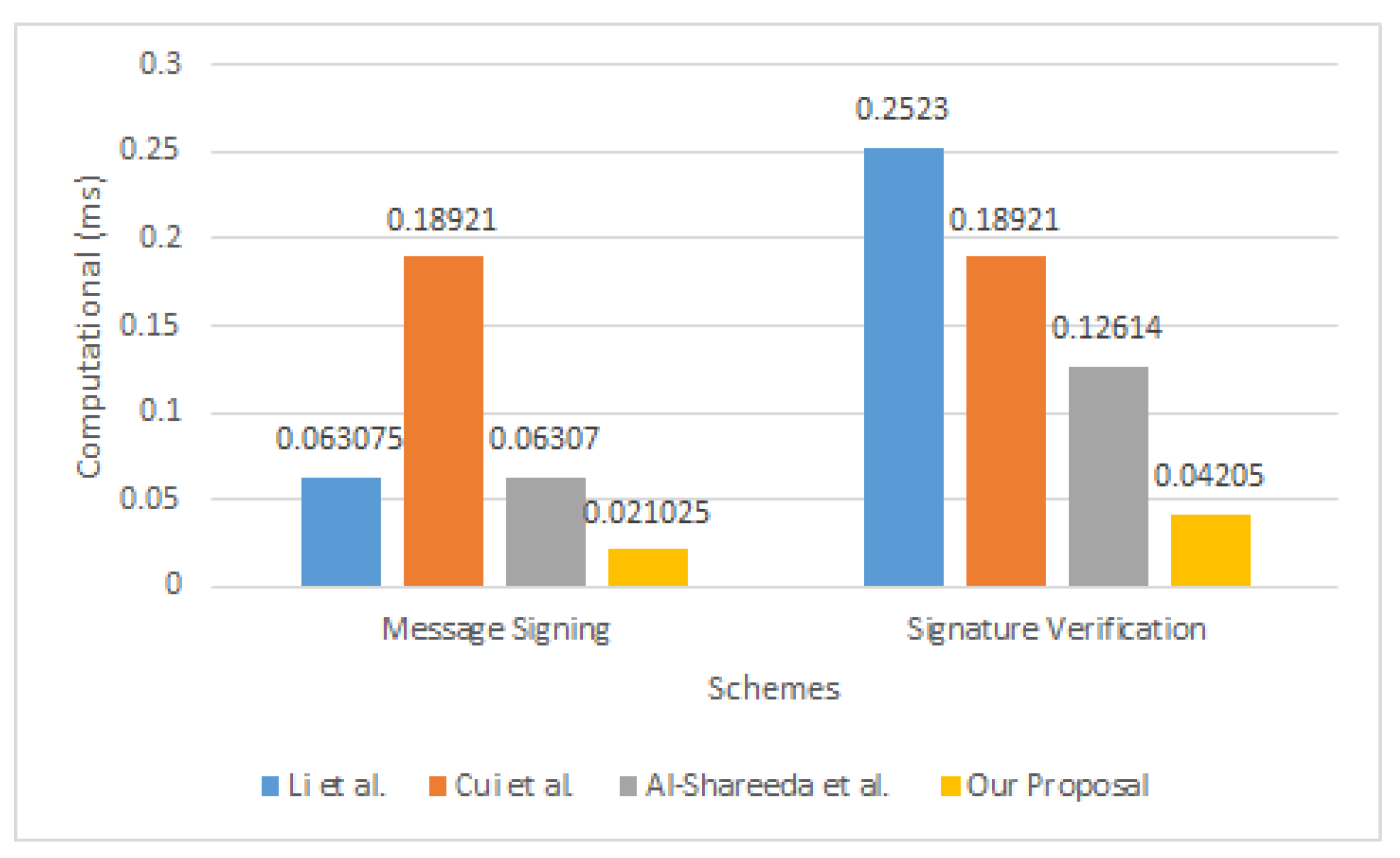
5.2. Performance Evaluation
5.2.1. Overhead of Computational
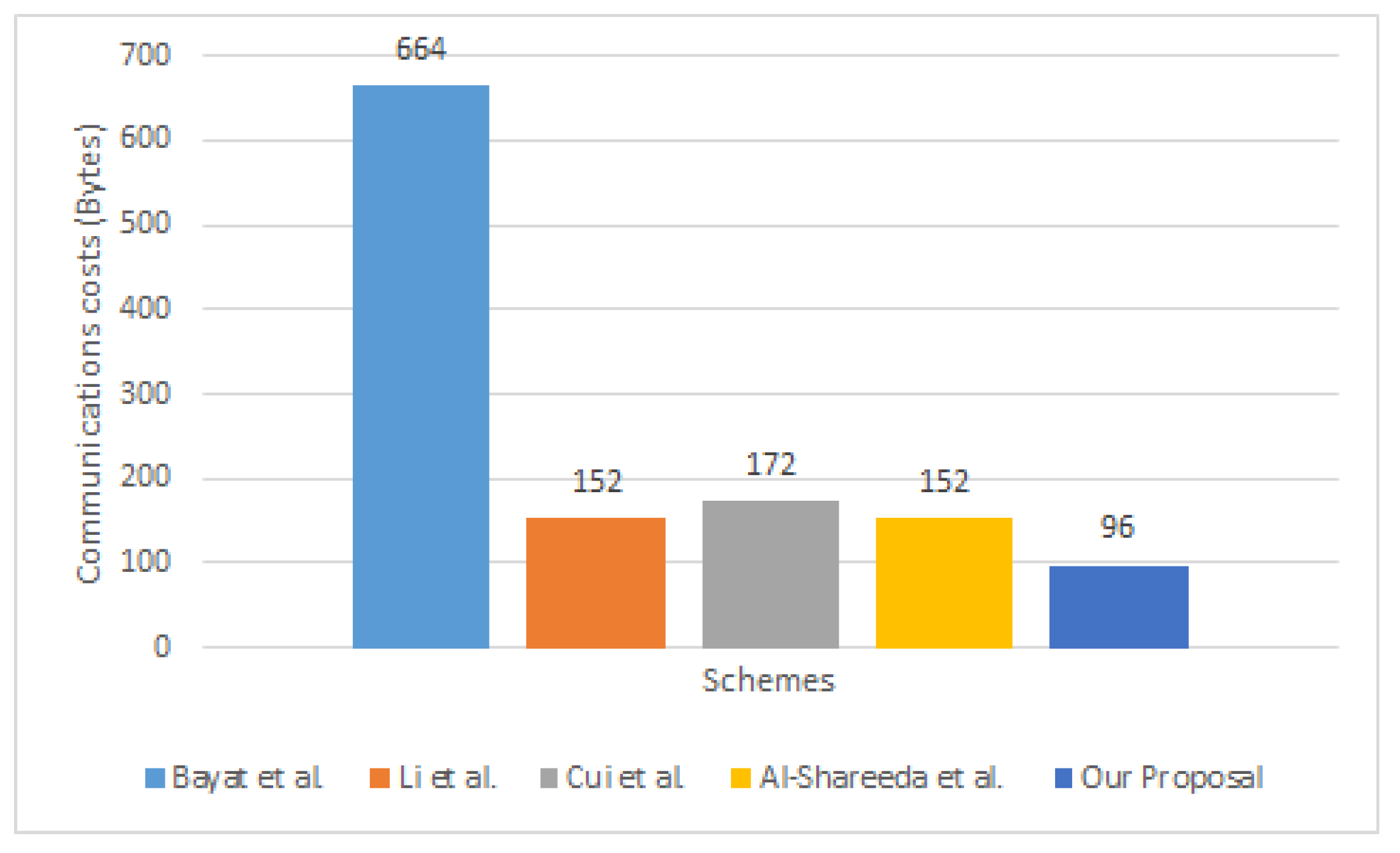
5.2.2. Overhead of Communication
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhang, J.; Zhong, H.; Cui, J.; Tian, M.; Xu, Y.; Liu, L. Edge computing-based privacy-preserving authentication framework and protocol for 5G-enabled vehicular networks. IEEE Trans. Veh. Technol. 2020, 69, 7940–7954. [Google Scholar] [CrossRef]
- Lai, C.; Lu, R.; Zheng, D.; Shen, X. Security and privacy challenges in 5G-enabled vehicular networks. IEEE Netw. 2020, 34, 37–45. [Google Scholar] [CrossRef]
- Cheng, X.; Zhang, R.; Chen, S.; Li, J.; Yang, L.; Zhang, H. 5G enabled vehicular communications and networking. China Commun. 2018, 15, iii–vi. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Naik, R.P.; Jang, J.W.; Chung, W.Y. Software-Defined Small Cell-Linked Vehicular Networks: Architecture and Evaluation. Electronics 2023, 12, 304. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S. COVID-19 Vehicle Based on an Efficient Mutual Authentication Scheme for 5G-Enabled Vehicular Fog Computing. Int. J. Environ. Res. Public Health 2022, 19, 15618. [Google Scholar] [CrossRef] [PubMed]
- Wymeersch, H.; Seco-Granados, G.; Destino, G.; Dardari, D.; Tufvesson, F. 5G mmWave positioning for vehicular networks. IEEE Wirel. Commun. 2017, 24, 80–86. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S. MSR-DoS: Modular Square Root-based Scheme to Resist Denial of Service (DoS) Attacks in 5G-enabled Vehicular Networks. IEEE Access 2022, 10, 120606–120615. [Google Scholar] [CrossRef]
- Chiti, F.; Fantacci, R.; Giuli, D.; Paganelli, F.; Rigazzi, G. Communications protocol design for 5G vehicular networks. In 5G Mobile Communications; Springer: Berlin/Heidelberg, Germany, 2017; pp. 625–649. [Google Scholar]
- Al-Shareeda, M.A.; Manickam, S.; Laghari, S.A.; Jaisan, A. Replay-Attack Detection and Prevention Mechanism in Industry 4.0 Landscape for Secure SECS/GEM Communications. Sustainability 2022, 14, 15900. [Google Scholar] [CrossRef]
- Prasad, K.S.V.; Hossain, E.; Bhargava, V.K. Energy efficiency in massive MIMO-based 5G networks: Opportunities and challenges. IEEE Wirel. Commun. 2017, 24, 86–94. [Google Scholar] [CrossRef]
- Zhang, J.; Zhong, S.; Wang, T.; Chao, H.C.; Wang, J. Blockchain-based systems and applications: A survey. J. Internet Technol. 2020, 21, 1–14. [Google Scholar]
- Ge, X.; Li, Z.; Li, S. 5G software defined vehicular networks. IEEE Commun. Mag. 2017, 55, 87–93. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. SE-CPPA: A Secure and Efficient Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. Sensors 2021, 21, 8206. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Yang, Y.; Wang, T.; Sherratt, R.S.; Zhang, J. Big data service architecture: A survey. J. Internet Technol. 2020, 21, 393–405. [Google Scholar]
- Wang, J.; Han, H.; Li, H.; He, S.; Sharma, P.K.; Chen, L. Multiple strategies differential privacy on sparse tensor factorization for network traffic analysis in 5G. IEEE Trans. Ind. Inform. 2021, 18, 1939–1948. [Google Scholar] [CrossRef]
- Al-Mekhlafi, Z.G.; Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Qtaish, A. Lattice-Based Lightweight Quantum Resistant Scheme in 5G-Enabled Vehicular Networks. Mathematics 2023, 11, 399. [Google Scholar] [CrossRef]
- Pu, B.; Li, K.; Li, S.; Zhu, N. Automatic fetal ultrasound standard plane recognition based on deep learning and IIoT. IEEE Trans. Ind. Inform. 2021, 17, 7771–7780. [Google Scholar] [CrossRef]
- Cui, J.; Yu, J.; Zhong, H.; Wei, L.; Liu, L. Chaotic Map-Based Authentication Scheme Using Physical Unclonable Function for Internet of Autonomous Vehicle. IEEE Trans. Intell. Transp. Syst. 2022, 1–15. [Google Scholar] [CrossRef]
- Wang, J.; Jin, C.; Tang, Q.; Xiong, N.; Srivastava, G. Intelligent ubiquitous network accessibility for wireless-powered MEC in UAV-assisted B5G. IEEE Trans. Netw. Sci. Eng. 2020, 8, 2801–2813. [Google Scholar] [CrossRef]
- Abassi, R.; Ben Chehida Douss, A.; Sauveron, D. TSME: A trust-based security scheme for message exchange in vehicular Ad hoc networks. Hum.-Centric Comput. Inf. Sci. 2020, 10, 1–19. [Google Scholar] [CrossRef]
- Zhang, J.; Jiang, Y.; Cui, J.; He, D.; Bolodurina, I.; Zhong, H. DBCPA: Dual Blockchain-Assisted Conditional Privacy-Preserving Authentication Framework and Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Mob. Comput. 2022, 1–15. [Google Scholar] [CrossRef]
- Bayat, M.; Barmshoory, M.; Pournaghi, S.M.; Rahimi, M.; Farjami, Y.; Aref, M.R. A new and efficient authentication scheme for vehicular ad hoc networks. J. Intell. Transp. Syst. 2020, 24, 171–183. [Google Scholar] [CrossRef]
- Li, J.; Choo, K.K.R.; Zhang, W.; Kumari, S.; Rodrigues, J.J.; Khan, M.K.; Hogrefe, D. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar] [CrossRef]
- Cui, J.; Chen, J.; Zhong, H.; Zhang, J.; Liu, L. Reliable and Efficient Content Sharing for 5G-Enabled Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1247–1259. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Password-Guessing Attack-Aware Authentication Scheme Based on Chinese Remainder Theorem for 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 1383. [Google Scholar] [CrossRef]
- Yang, J.; Deng, J.; Xiang, T.; Tang, B. A Chebyshev polynomial-based conditional privacy-preserving authentication and group-key agreement scheme for VANET. Nonlinear Dyn. 2021, 106, 2655–2666. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Al-Mekhlafi, Z.G.; Qtaish, A.; Alzahrani, A.J.; Alshammari, G.; Sallam, A.A.; Almekhlafi, K. Chebyshev Polynomial-Based Scheme for Resisting Side-Channel Attacks in 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 5939. [Google Scholar] [CrossRef]
- Zhang, L.; Zhu, Y.; Ren, W.; Wang, Y.; Choo, K.K.R.; Xiong, N.N. An energy-efficient authentication scheme based on Chebyshev chaotic map for smart grid environments. IEEE Internet Things J. 2021, 8, 17120–17130. [Google Scholar] [CrossRef]
- Alazzawi, M.; Lu, H.; Yassin, A.; Chen, K. Efficient Conditional Anonymity with Message Integrity and Authentication in a Vehicular Ad hoc Network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Alazzawi, M.A.; Al-behadili, H.A.; Srayyih Almalki, M.N.; Challoob, A.L.; Al-shareeda, M.A. ID-PPA: Robust identity-based privacy-preserving authentication scheme for a vehicular ad-hoc network. In Proceedings of the Advances in Cyber Security: Second International Conference, ACeS 2020, Penang, Malaysia, 8–9 December 2020; Revised Selected Papers 2. Springer: Berlin/Heidelberg, Germany, 2021; pp. 80–94. [Google Scholar]
- Ali, I.; Li, F. An efficient conditional privacy-preserving authentication scheme for Vehicle-To-Infrastructure communication in VANETs. Veh. Commun. 2020, 22, 100228. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Zahednejad, B.; Bayat, M.; Farjami, Y. NECPPA: A novel and efficient conditional privacy-preserving authentication scheme for VANET. Comput. Netw. 2018, 134, 78–92. [Google Scholar] [CrossRef]
- Bayat, M.; Pournaghi, M.; Rahimi, M.; Barmshoory, M. NERA: A new and efficient RSU based authentication scheme for VANETs. Wirel. Netw. 2020, 26, 3083–3098. [Google Scholar] [CrossRef]
- Roychoudhury, P.; Roychoudhury, B.; Saikia, D.K. Provably secure group authentication and key agreement for machine type communication using Chebyshev’s polynomial. Comput. Commun. 2018, 127, 146–157. [Google Scholar] [CrossRef]
| Bayat et al. [22] | Li et al. [23] | Cui et al. [24] | Al-Shareeda et al. [25] | Our Work | |
|---|---|---|---|---|---|
| Authentication and Integrity | Yes | Yes | Yes | Yes | Yes |
| Identity Privacy | Yes | Yes | Yes | Yes | Yes |
| Traceability | Yes | Yes | Yes | Yes | Yes |
| Unlinkability | Yes | Yes | Yes | Yes | Yes |
| Resistance to Attacks | Yes | Yes | Yes | Yes | Yes |
| Pseudonyms Revocation | NO | NO | NO | NO | Yes |
| Efficient | NO | NO | NO | NO | Yes |
| Math Symbol | Definition |
|---|---|
| TA | Trusted Authority |
| 5G-BS | Fifth-Generation Base Station |
| Chebyshev Polynomial Parameters | |
| Pseudonym-IDs of Vehicle | |
| Signature Key | |
| h | One-Way Hash Function |
| Master’s Private Key | |
| Security Parameter | |
| Authentication Code | |
| Vehicle’s True Identity | |
| Current Timestamp | |
| || | Operations of Concatenation |
| ⊕ | Operation of X-OR |
| Operations | Definition | Times (ms) |
|---|---|---|
| The duration of the bilinear pairing cryptography (BPC) operation’s runtime. | 1.537 | |
| The scale multiplication operation’s runtime for the BPC. | 0.137 | |
| The scale multiplication operation’s runtime for the elliptic curve cryptography (ECC). | 0.063075 | |
| Chebyshev’s polynomial mapping operation’s runtime. | 0.021025 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Mekhlafi, Z.G.; Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Alreshidi, A.; Alazmi, M.; Alshudukhi, J.S.; Alsaffar, M.; Alsewari, A. Chebyshev Polynomial-Based Fog Computing Scheme Supporting Pseudonym Revocation for 5G-Enabled Vehicular Networks. Electronics 2023, 12, 872. https://doi.org/10.3390/electronics12040872
Al-Mekhlafi ZG, Al-Shareeda MA, Manickam S, Mohammed BA, Alreshidi A, Alazmi M, Alshudukhi JS, Alsaffar M, Alsewari A. Chebyshev Polynomial-Based Fog Computing Scheme Supporting Pseudonym Revocation for 5G-Enabled Vehicular Networks. Electronics. 2023; 12(4):872. https://doi.org/10.3390/electronics12040872
Chicago/Turabian StyleAl-Mekhlafi, Zeyad Ghaleb, Mahmood A. Al-Shareeda, Selvakumar Manickam, Badiea Abdulkarem Mohammed, Abdulrahman Alreshidi, Meshari Alazmi, Jalawi Sulaiman Alshudukhi, Mohammad Alsaffar, and Abdulrahman Alsewari. 2023. "Chebyshev Polynomial-Based Fog Computing Scheme Supporting Pseudonym Revocation for 5G-Enabled Vehicular Networks" Electronics 12, no. 4: 872. https://doi.org/10.3390/electronics12040872
APA StyleAl-Mekhlafi, Z. G., Al-Shareeda, M. A., Manickam, S., Mohammed, B. A., Alreshidi, A., Alazmi, M., Alshudukhi, J. S., Alsaffar, M., & Alsewari, A. (2023). Chebyshev Polynomial-Based Fog Computing Scheme Supporting Pseudonym Revocation for 5G-Enabled Vehicular Networks. Electronics, 12(4), 872. https://doi.org/10.3390/electronics12040872