1. Introduction
Dynamic and shared-spectrum-access techniques are among the most challenging approaches in advanced modern wireless communication. Examples of technologies implementing dynamic spectrum spatial capabilities are 5th-Generation New-Radio (5G-NR)-Heterogeneous-Network (HetNet) [
1,
2], 6th-Mobile-Generation [
3], and Wi-Fi-6,7,8 802.11.ax-be. Moreover, dealing with multi-interference signals, Over-the-Air (OTA) in the domains of space, time, and frequency, or coping with jamming attacks that strongly correlate with transmission signals, and simultaneously integrating the application of modern MIMO techniques poses challenging issues. Existing solutions to these problems include: intelligent access [
4,
5], intelligent SIC [
6,
7,
8,
9,
10,
11], smart management sharing systems, and dynamic-cognitive-radio-spectra [
12,
13,
14].
More and more systems in both the civilian and military fields are required to deal with multi-path phenomena and diverse sources of interference in conjunction with ultra-reliability and low-air transport requirements [
2]. In the advanced modern communication field, several users per urban area and the number of mobile operators conducting Stand-Alone (SA) unlicensed communications are massive and intensifying. This process of congestion leads to the destruction of wireless channels, causing bad conditions for wave propagation [
15], scattering phenomena [
16], and interference-jamming problems [
17,
18,
19]. The meaning of the destruction of wireless channels is that there is a strong correlation between the desired signal and the interference signal that causes a significant reduction in the complex power gain of the wireless links. In designing next-generation communication systems, it is necessary to consider these decoding and fairness problems in addition to dealing with these destructive effects.
Two main approaches have been developed in recent years to deal with the challenges of offsetting the destructive effects of various sources of interference. The capabilities of those approaches combine spatial selectivity and wireless communication techniques that increase the channel’s capacity and bring about accurate and fast decoding processes. The two main approaches can be classified as follows: classical conventional and non-conventional analog–digital-SIC approach [
7,
20] or None-Orthogonal-Multiple-Access (NOMA) techniques [
21,
22,
23], and advanced MIMO-beamforming techniques such as analog–digital hybrid-beamforming structure [
24,
25,
26], and multi-layer-precoding full-dimensional massive MIMO systems [
14,
27].
The first approach includes three different families of decoders incorporating interference offset algorithms. The first family has algorithms such as classical analog–digital-SIC [
7,
20,
28], zero forcing-interference cancellation (ZF-IC) [
29], MGSTC [
29,
30,
31], and SIC based on machine-learning/deep-learning algorithms such as SICnet [
28] and-deepSIC [
7]. The main advantage of these techniques is the absence of the requirement for physical feedback between the receiver and the transmitter to share the information evaluation of the wireless channel with the transmitter (e.g., the Channel-State-Information-at-the-Transmitter (CSIT)). The common denominator of this family is based on serial process decoders designed for the spatial separation of a block of information intended for a specific user from a system of simultaneously transmitted blocks. The coalition of the remaining blocks considered internal interferences are serially offset to decode the desired block. These methods are limited in dealing with interference processes from external interferers, such as neighboring users who produce a strong correlation with the signals of the desired transmitter or an intelligent jammer activated in the same geographic-spatial space. The reason for this weakness is that the external disturbance process causes a violation of the legality of the internal offset process predefined in the SIC algorithm. This process damages the iterative decoding process and significantly damages the system’s performance (as we prove in the next section).
The second family is the NOMA technique. The NOMA is based on multi-carrier power control, which allows identifying each user’s reception power values or power coefficients according to their differences in power-multiplexing. This method is also vulnerable to external interference from outside the network or from the source of an intelligent jammer. These interferences disrupt the spatial separation process, which is based on differentiating the reception power of each user.
The third family is based on minimum-mean-square detection interference-rejection combiner (MMSE-IRC) [
32]. The conventional MMSE-IRC enables spatial selectivity, as well as dealing with neighboring users who produce complex disturbances within the legal framework of the network, a high order of diversity, and advanced spatial pluralism. The MMSE-IRC is limited in the aspect of eliminating the outsourcing of dynamic interference and dealing with destructive wireless effects because the construction of the system mechanisms is heavily based on None-Stand-Alone (NSA) networks or on network-based regulation protocols, with the help of Physical-Upload-Share-Channel (PUSHC), and auxiliary Demodulation-Reference-Signals (DM-RS) [
1,
2].
The second approach is high-resolution beamforming techniques [
33], hybrid beamforming [
4,
24], analog–digital-beamforming, and multi-layer-precoding full-dimensional massive MIMO systems [
34]. This approach’s disadvantage is that the receiver must share with the transmitter CSIT via physical feedback that might be vulnerable. As a result, the ability of an intelligent jammer or a general disturbance to damage the CSIT is natural and exists in physical reality. The balance between the need to develop systems without closed feedback and the development of advanced feedback-based methods is derived from considerations of the need to implement real-time communication, communication with minimal computational overhead, and constraints of physical conditions that cannot connect physical feedback between the receiver and the transmitter. Examples of such systems with physical constraints and limitations are satellite communication systems, critical wireless links (for example, medical systems based on wireless communication), and autonomous vehicles.
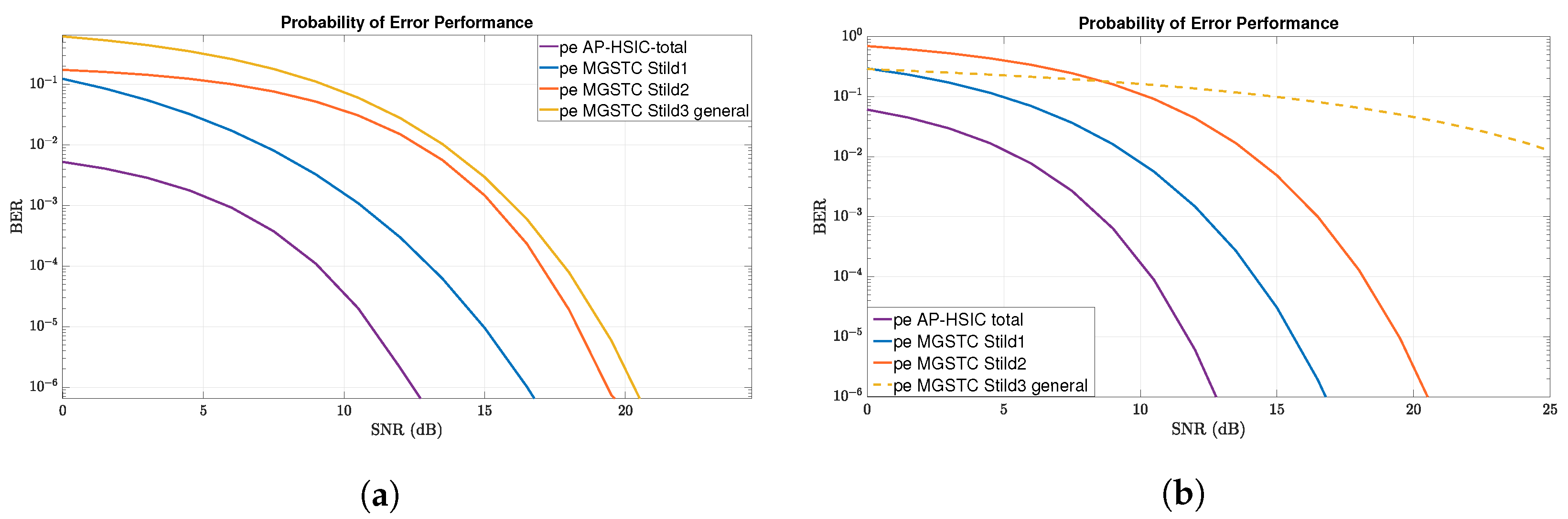
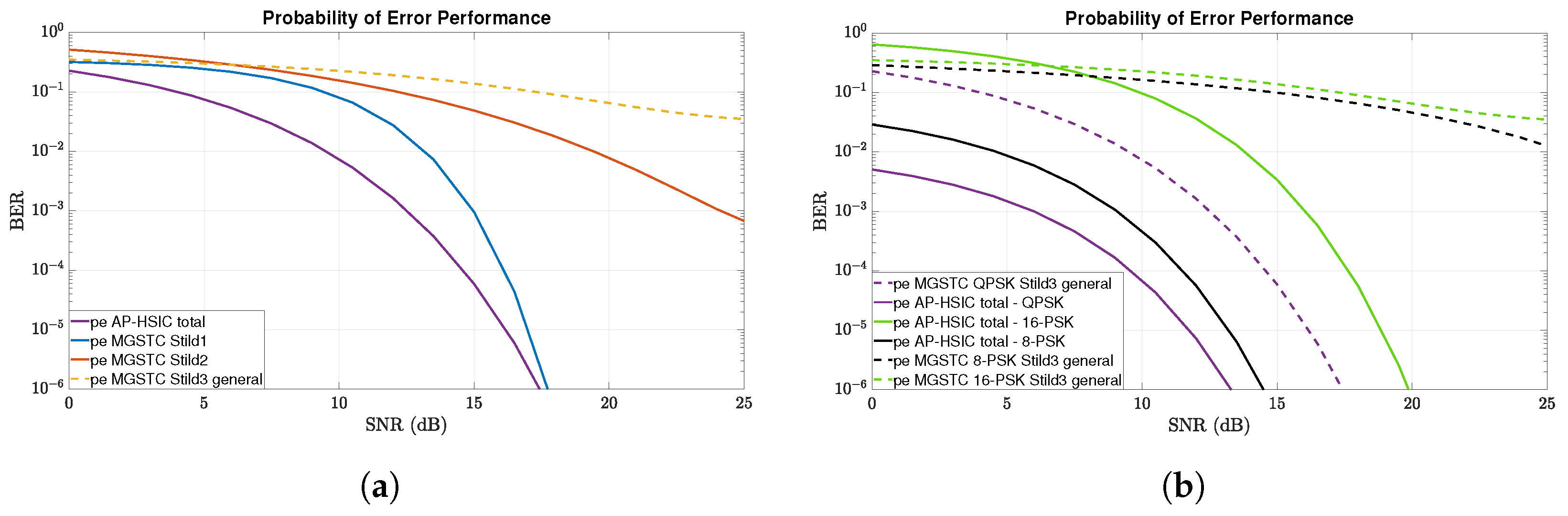
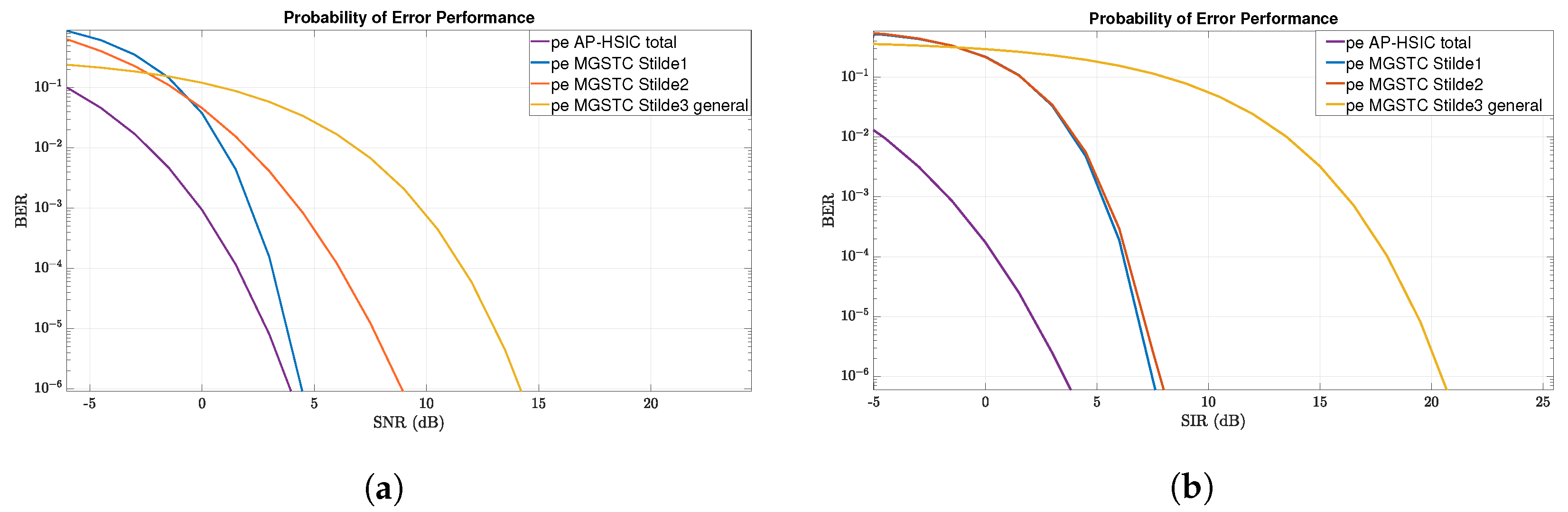
In this paper, we propose a new digital interference cancellation algorithm—the AP-HSIC—that only requires the Channel-State-Information-at-the-Receiver (CSIR) assumption and generates computational feedback at the receiver. This computational feedback can overcome the effects of random scatters in a multi-path fading channel and quasi-static Flat-Rayleigh-Fading MIMO channels, combined with high-level AWGN and general interference scenarios. We compare the MGSTC decoding algorithm’s performance based on the MIMO array’s serial-decoding mode and the proposed algorithm, AP-HSIC, which combines parallel processing decoding methods in the MIMO array. This comparison was conducted in an environment of different interferers. The comparison is reflected in the performance levels of Bit–Error Ratio (BER) vs. the Signal-to-Noise Ratio (SNR) or BER vs. Signal-to-Interference Ratio (SIR).
The analysis considers different constellation orders (Quadrature Phase Shift Keying (QPSK); 8-PSK; and 16-PSK) and challenges the two systems under scenarios of high-level AWGN and two kinds of interference: Partial Band Noise (PBN) [
35] and general interference [
1]. The presence of general interfering signals can be associated with neighboring users or jamming attacks [
17].
The proposed AP-HSIC can generate significant capabilities for successfully canceling digital interference. The AP-HSIC offers flexibility regarding stand-alone (SA) networks without the request to control a sharing channel that statistically measures the spatial domain. The receiver also does not require any control or physical feedback from the transmitter. In addition, AP-HSIC can decode symbols in a parallel MIMO mode in real-time without slowing down the decoding process and simultaneously with the interference cancellation process. These features are significant in applying ultra-bit-rate and heavy-capacity channel requirements. It has the ability to discern between the original channel response matrix and interfering factors. The next section defines these factors as the interrupting part, , where we show how to calculate an approximation to and perform an online update to the general MIMO channel response matrix. The computation of allows a total offset of the interference signal. The result is that the system can decode the originally transmitted symbols without increasing the power and re-transmitting. We may assume statistical dependence between the general interference (or the jamming signal) and the user signal, as well as statistical dependence between the AWGN and the user signal. Furthermore, with the knowledge of the CSIR, we can distinguish between a signal that transmits data from an interference signal without changing to pilot symbols, changing modulation, or increasing the transmission power.
The common denominator of advanced wireless communication systems that include interference offset techniques and innovative parallel decoding algorithms is that the network operates in Time-Division-Duplex (TDD) communication mode. A significant advantage of this mode is in the abstraction of the ability to evaluate the wireless channel and reduce the information overhead between the transmitter and the receiver. The significant and growing problem with this mode is that it is weak against interference or neighboring users in the space. The considerable advantages of the proposed algorithm are not only that it allows information to be decoded in a parallel manner at the same time as the offset of the interferers without the need for physical feedback between the transmitter and the receiver, but it also allows applicability to communication systems that are unable to produce physical feedback due to considerations of system architecture, critical response time, etc. Examples of this applicability are satellite systems, autonomous vehicles, and ultra-low latency wireless systems. The proposed algorithm allows these systems to transmit high data rates in a high order of modulations and simultaneously decode them under diverse interfering scenarios and under TDD mode.
The remainder of the paper is organized as follows:
Section 2 presents the proposed communication MIMO model under various interference scenarios.
Section 3 presents the AP-HSIC algorithm, where we prove its correctness, prove its convergence, and analyze its complexity.
Section 4 describes the real-time simulations and numerical results based on SIMULINK and MATLAB platforms and provides a comparison of the performances of both systems: the MGSTC and the AP-HSIC. In
Section 5, we derive conclusions and a vision for further research on efficient solutions to communication system problems under interfering scenarios.
2. Proposed Communication MIMO Model under Various Interference
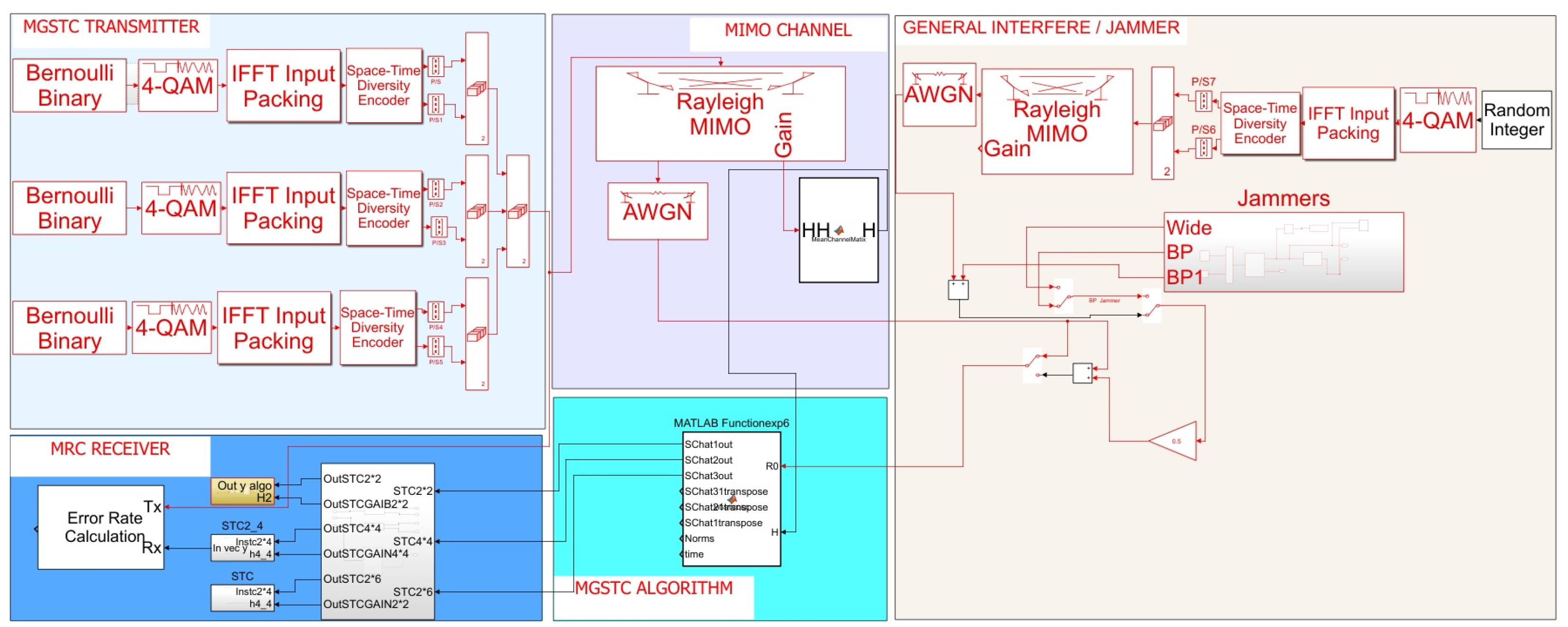
This section describes and analyzes a proposed communication MIMO model under various interference scenarios for two different architectures. The first architecture includes a transmitter based on the MGSTC scheme, including the diversity-transmitting technique-OSTBC. The receiver is based on the MGSTC decoding algorithm. This architecture is described in [
29]. The MGSTC has the property of interference cancellation and decoding capability with the ability to separate a single symbol information block from a set of transmitted blocks and combines an error-reducing mechanism. The MGSTC technique works by iterating a serial decoding mode in the receiver. It includes the parallel transmission of a series of blocks in space and, on the receiver side, a serial decoding capability that separates the various transmitted blocks.
In this architecture, as we mentioned, the MGSTC decoding algorithm decodes and de-multiplexes the individual data streams in a specific user from the other streams and creates, through serial iterations (i.e., multi-stage decoding), a communication mode capable of offsetting the noise part (a sum of AWGN with the rest of the broadcast blocks). This process is performed by utilizing the accuracy of a single decoding stream relative to the last decoding iteration.
There are two distinct advantages of the MGSTC decoding algorithm. The first one is based on the fact that, at the end of each iteration, when we move to the next group order, the MGSTC scheme produces a diversity gain for every matrix of OSTBC transmission modulation symbols, ( included MGSTC component-block as ). The diversity gain is increased by when the i is the iteration number and is the number of transmission antennas in the i’th group, while , and are the number of total receiver antennas and the number of total transmission antennas, respectively.
Having the ability to raise the diversity order means being able to reduce the average power transmission of each group inversely to the diversity order of each group; for example, the average power per symbol transmission at antennas 1 and 2 in the first group is defined as , and the diversity order is 4, the average power per symbol at antennas 3 and 4 will be , with diversity order of 8. The second advantage is based on the fact that in each given iteration, as the iteration process continues forward, the decoding accuracy increases, a process that results in the elimination of the noise part in relation to the previous iteration.
The challenging issue in the MGSTC and in multi-stage decoding, in general, is that the advantages become disadvantages in several communication scenarios. Those advantages, as mentioned above, at the same time, lead to disadvantages for MGSTC systems when interference cases are present in the same spatial domain. The disadvantages, reflected in the SIC process of the MGSTC, are based on it being a serial decoding mode of data blocks. Every error accumulated in a given SIC process is dragged into the next iteration and amplified. Another significant weakness of the MGSTC is the wireless links between the antenna couples in the descending order of the antenna array of the transmitter (e.g., antennas 5 and 6 in our simulation) to all antenna arrays of the receiver. The weakness arises from the fact that these paths are more attenuated in terms of the SNR or SIR and because of the reliance on diversity gain. Thus, in the presence of interfering signals, fading effects, or high levels of AWGN that hit these paths, an imbalance in the trade-off between a higher diversity gain and lower SNR occurs, leading to increased values of BER.
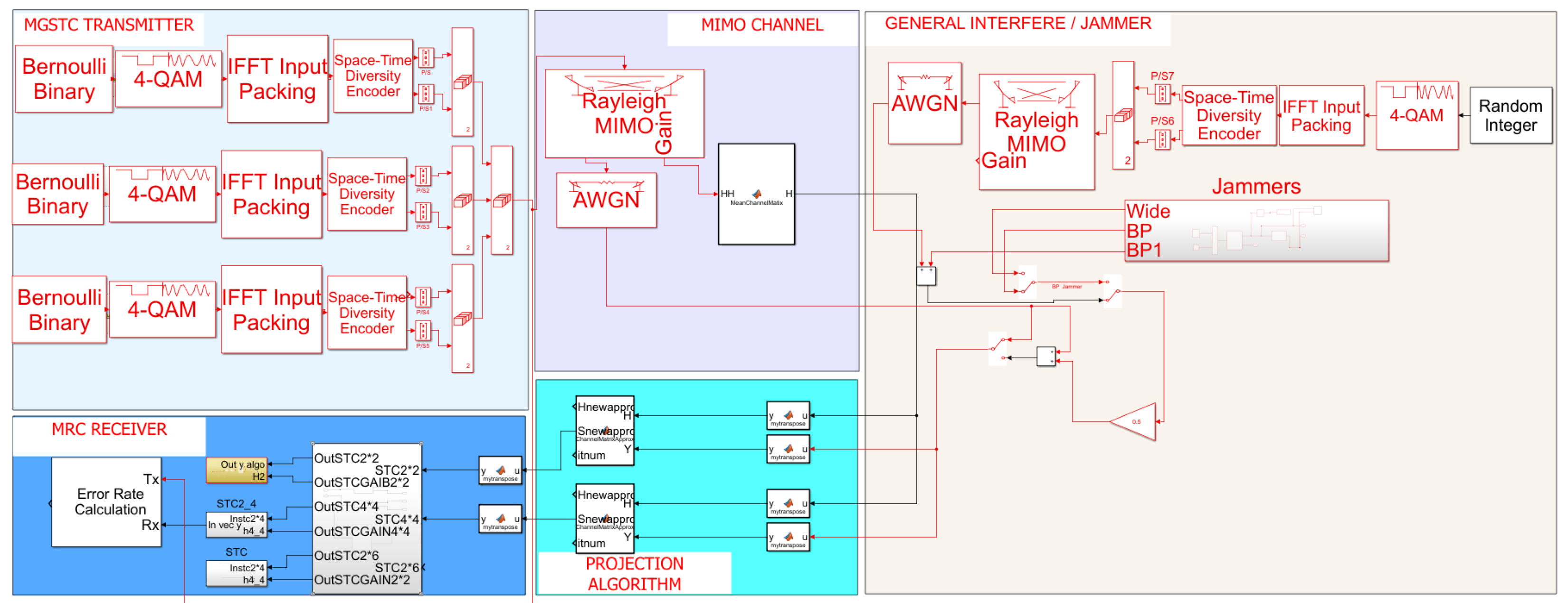
We propose the second architecture using the MGSTC-OSTBC at the transmitter and the AP-HSIC scheme at the receiver instead of the MGSTC decoding algorithm. This proposed hybrid scheme produces immunity against various interference scenarios, as can be seen in the simulation results below. In addition, a more efficient and accurate process of parallel spatial decoding of the series of simultaneously transmitted symbols blocks is achieved in this scheme compared to the first scheme we described.
We separately analyze and simulate the two architectures under three challenging interference scenarios acting in the same spatial domain. The first interference scenario is a high-leveled AWGN. The second scenario is PBN, and the third scenario is a general interference simulating a smart jamming device or a neighboring user.
We start the first and essential analysis with the general interference case. In that case, the communication standard ideal model
changes to (see [
29]):
where
Y is the received signal, with dimensions
,
is the number of receiver antennas, and
k is the number of sample symbols per frame. The MIMO channel response matrix between the transmitter and receiver is
, with dimensions
, where
is the number of transmission antennas. The MIMO channel-response matrix between the interference and the receiver is defined by
, with dimensions
, where
is the number of interference transmission antennas.
is the matrix of OSTBC transmission modulation symbols of the desired transmission, with dimensions
and
is the matrix of OSTBC interference modulation symbols, with dimensions
. Finally, the
is the signal interference ratio,
P is the total transmission power, and
Z is the independent complex Gaussian random variable noise. The model communication is described in
Figure 1.
For the MGSTC decoding algorithm, in the presence of the interference signal,
, [
29] becomes:
where
is the receive-matrix for decoding the first symbol-block,
.
is the null space matrix relative to the decoding process of
, and
is the independent complex Gaussian random variable noise multiplied with the null space matrix,
.
The second part of this equation, the interference that is received as an additive factor to the MGSTC decoding algorithm, produces the most destructive effects as it destroys the orthogonality of
relative to the other part of the MIMO channel-response matrix–destruction that the MGSTC algorithm cannot deal with (see [
36]).
In order to solve the problem of interference estimation and digital interference cancellation in the presence of general interference by using self-computational feedback at the receiver, we describe two main approaches with different assumptions to model the interference intervention. The first approach is based on the assumption that the number of interference transmission antennas and the number of legitimate transmission antennas are different, implying that there exists no correlating matrix
such that
, and therefore we do not have any information about the interference tactic. The second approach is applied under the assumption that there exists a correlation unknown matrix
such that
. Under the most general assumption, writing
, we can decompose (
1) into:
where
is the Moore–Penrose pseudo-inverse of
S. Multiplying from the right by
, we obtain:
since
(which implies
, see Remark 1) and since
.
Let the interference factor be defined by:
Furthermore, let
and
.
Now,
, where
, which implies that
. We therefore have
since
and
(whatever the coding modulation is, using the fact that
is Hermitian with simple eigenvalues from the set
). The last implies that we reduce the noise part by multiplying with
, assuming that
k is large enough.
Note that when a correlation matrix
exists such that
, then
and (3) is equivalent to
which we write as:
where
.
In order to compute
and
S from (
7) or from (
9), we can start with the standard ideal model to obtain a first approximation for
S, using the known channel response matrix
H. Then, we iterate on (
7) or on (
9) to compute the best approximations for
and for
S, as explained in
Section 3. In [
36], it has been proven and demonstrated through simulations that the worst-case scenario is where a rotation correlation matrix
exists such that
. Thus, our analysis includes the case where
are correlated. Note that
. Therefore:
This implies that
, if
. Thus, continuing with (
9) does not lose the generality, as (
7) can be solved by the same algorithm, with the error threshold
instead of
.
A more simplified case is when
(although it is not simple for the jammer to generate
S exactly). Practical examples of intelligent jammers (or neighboring users with the same modulation order), where
or
, were considered in [
17,
36,
37].
Note that, in view of (
2), the part
, which is orthogonal to
(in the Frobenius inner-product
) is simply canceled by multiplication with
from the right. However, the part
, which is in the direction of
, cannot be canceled without intervening in the channel-state by using some feedback. This explains why, in the aforementioned papers, the simplified cases appear as the most challenging interferences. Mathematically, these resemble simple cases or mathematical simplification, but physically, these cases create disturbances in terms of nonlinear distortions in the constellation or duplication of symbols in the constellation, as described in [
36].
In the following, we present computational feedback that cancels
by computing
and using it to reliably decode
S and update the new MIMO channel-response matrix to be
without the need to update the transmitter. The next interference scenario is the PBN case. The PBN case represents the noise energy caused by a jammer, a neighboring user under the same operator, or a user from a neighboring operator that leaks energy across a specific portion of the system’s target bandwidth. The noise power bandwidth of the PBN may be less than that of the user, but the power amplitude of the PBN can be much higher than the user’s received signal. The last scenario is a high-leveled AWGN that is added to the existing noise part,
Z, as described in [
38].
3. The Alternating Projections HSIC Algorithm
In this section, we write for the number of transmission antennas and for the number of receiver antennas for the simplicity of presentation. Let A be any matrix. Then, we denote the Moore–Penrose pseudoinverse by . Let an singular value decomposition (S.V.D.) of A be denoted by , where U is an unitary matrix, V is an unitary matrix, and is an rectangular diagonal matrix with non-negative entries, i.e., , where are the singular values of A. Then, , where is just the diagonal matrix with on its main diagonal. Note that, for , as above, we have , where are the first ℓ columns of , respectively. Therefore, .
Remark 1. Note that . Therefore, if A is a random matrix, and Almost Surely (A.S.), then always exists and, A.S. In that case, we have: and , as well as and . Let and . Then, and , where and are self-adjoined with simple eigenvalues in the set . Furthermore, and are self-adjoined with simple eigenvalues in the set .
Let
z be a random
complex vector. Then, we write
if the p.d.f. of
z is
, where
is an
complex vector, and
is a positive-definite
complex matrix. Let
Z be a random
complex matrix. Let
denote the function transforming the matrix
Z into a vector by aligning its columns into a single
column vector. We write
for
Z having the Probability Distribution Function (P.D.F.):
where
is a complex
matrix,
V is a positive-definite complex
matrix, and
U is a positive-definite complex
matrix. One can show that
if and only if
. Note that, if
, then
. Also note that if
, then
, and
. The latter implies that
Therefore, if
, then,
. The following lemma can be easily proven.
Lemma 1. Let and . The matrix equation has solutions if and only if (i.e., ). In that case, the set of all solutions is given by:where is an arbitrary matrix. Moreover, we have , implying that a minimal Frobenius-norm solution is . Moreover, even when the condition is not satisfied, is still a minimal Frobenius-norm solution to the problem . The following theorem would be useful for turning our non-convex problem into a convex one:
Theorem 1. The set of full-rank matrices is dense in the set of all matrices, i.e., for any and any , there exists a full-rank matrix such that .
The proof of this theorem and of the following theorems is given in the
Appendix A.
Under the assumptions mentioned above, the standard ideal MIMO model is described by:
where
S is an
OSTBC symbol matrix of signals. We assume that
. The
matrix
H is the channel matrix (random with the unknown p.d.f., but assumed to be stationary) and
, which is equivalent to
Theorem 2. Assume that the communication is made with some modulation not containing 0 and let be the radius of the modulation point with minimal radius. Assume that and let be the OSTBC symbol matrix of signals, where and each is , chosen such that for , and is an arbitrary matrix. In addition, we also assume that S is known to the receiver. Let . Then, is a random matrix such that:Moreover, since is bounded above, by taking , it follows that , implying that A.S. holds. In view of Remark 1, A.S. implies that A.S., from which we can conclude that , and that . Now, when S is unknown, when we search for S that minimizes , by Lemma 1, we need to take . However, as H is random and Y is random, is random, while the true S that was sent by the transmitter is not random. However, as it is almost sure that , we can take as an approximation for S. Note that is still a random matrix, but it would give us what is needed, as is expressed in the following theorem.
Theorem 3. Let be an matrix as in Theorem 2, and further assume that and that is full-rank. Let S denote an unknown signal matrix that is sent by the transmitter and let be the signal measured by the receiver. Let (note that is a random variable matrix, while S is not random). Then, The following theorem connects the expectation of the square error between the approximated computed symbol matrix and the real symbol matrix S, in terms of the transmission power, the number of antennas, and the SNR level. This would give us a new formula for the BER, as we will see in the simulations section.
Theorem 4. Let , where H can be the ideal channel matrix or , the resulting channel matrix of the disrupted channel. Assume that the exact H (or the exact , respectively) is known to the receiver and assume that H (or , respectively) is constant for the current session. Let S be the true symbol matrix for the current session, and let be the approximated symbol matrix. Then, the distribution of (given the constant matrix H or , respectively) is:Moreover, the expectation of the square error satisfies: In the following, we propose an algorithm for the computational self-feedback of the receiver that identifies both
and an unknown matrix symbol
S. For this purpose, we regard
as
H and ignore the measurement noise
Z. Therefore, we write
. Assume that the system has undergone a jamming attack, and the new channel matrix is
. Now, the signal received by the receiver is:
In view of Theorem A1, we may assume w.l.o.g. that
is full-rank, i.e., has
, since we assume that
. Therefore,
, and (
16) implies that
Then, in view of Lemma 1, the general solution to the last equation is given by:
where
are arbitrary matrices with sizes
and
, respectively. Since
it follows that:
which is equivalent to:
which is more efficient from the complexity point of view since we assume that
. Note that the set (
21) is actually a subspace, that is the left kernel of
that we denote as
and is, therefore, closed and convex. Note that
and
leads to
and
, that is the best approximation for the true
S in terms of Lemma 1 and Theorem A3 when there is no interference.
Now, as (
21) might yield an infeasible point related to the symbol coding that is being used (here, we use QPSK, 8-PSK, and 16-PSK), letting
, we define a projection
by (
22) below with
, which actually projects any entry of the matrix
S onto the closest point in the
constellation (breaking ties arbitrarily). In the following experiments, we used Algorithm 1, also with 8-PSK and 16-PSK codings, for performance comparison with the QPSK coding. For this purpose, we defined the following general projections for
-PSK (for any
, including
-PSK=QPSK):
In order to use the following Algorithm 1, we need to encapsulate
in a relatively small closed convex set, for which projections can be conveniently calculated. Since any point in
has an absolute value
, we define by
the matrix-ball of all
matrices
S with
. Now, if
, then
implying that
, from which we conclude that
and moreover, that each such matrix is on the boundary of the matrix-ball.
| Algorithm 1: AP-HSIC: Receiver Self-Feedback Algorithm |
Require: An algorithm for computing Moore–Penrose Pseudoinverses and algorithms for computing , and .
Input: .
Output: and S such that , where .
- 1.
- 2:
- 3:
- 4:
- 5:
- 6:
- 7:
while do - 8:
- 9:
- 10:
- 11:
- 12:
end while - 13:
- 14:
- 15:
return
|
Let
and
and note that these sets are closed and convex sets in
.
We now need projections on
and on
such that any given point in
which is out of the set is projected to the closest point in the boundary of the set. Let
be defined by
, where:
The projection is realized in Algorithm 2.
For a given couple as above, let and let .
Let
be a directional matrix, which is with
and let
. Then, the directional derivative at
in the direction
U is defined by:
We compute:
from which we conclude that:
Now, a necessary condition for
to be a minimum point for
f is that
for any
as above. This implies that
which is equivalent to
Similarly, for
g, we have:
We compute:
from which we conclude that:
A necessary condition for
to be a minimum point for
g is that
for any
as above. This implies that
is equivalent to
Gathering (
28) and (
32), we obtain:
which, in view of Lemma 1, implies that the best approximation in terms of the Frobenius norm is:
Finally, we define the projection
by
, where:
where
are given by (
34). The projection
is realized in Algorithm 3.
Algorithm 1, as presented below, which we call the Alternating Projections Hard Successive Interference Cancellation (AP-HSIC), solves the problem of finding and S, such that , where , after which it uses (or the related modulation projection) in order to project S into as the final decision. In its main loop, it computes by applying to and next, by applying to the result, thus alternating between and until convergence to an intersection point (i.e., in ) is verified.
We can start from any couple; however, a good choice is needed in order to obtain faster convergence, which we took as with the last H known to the receiver, before the jamming attack began, which is a good starting point, as revealed by Theorem A3.
Remark 2. Note that with the true S implies thatLet be computed by Algorithm 1. Then,Therefore, by solving instead of , we do not lose the generality. | Algorithm 2:For |
Require: Matrix and Arithmetic Operations
Input: such that A is and B is .
Output: closest to .
- 1:
if then - 2:
- 3:
else - 4:
- 5:
end if - 6:
- 7.
return
|
| Algorithm 3:For |
Require: An algorithm for computing Moore–Penrose Pseudoinverses
Input: such that A is and B is and Y.
Output: closest to .
- 1:
- 2:
- 3:
- 4:
return
|
Algorithm Correctness, Convergence, and Complexity
The general problem that we need to solve here is the problem , for the unknowns and S, where . We assume that is known to the receiver; however, this is not a mandatory assumption since we can rename as an (unknown) H and solve the problem indifferently. The aforementioned general problem is non-convex since it involves the multiplication of two unknown variables and S, and is a discrete set (with elements) which is obviously non-convex. Indeed, the decision problem: “Given , does there exist such that ?” is NP-hard to solve, as one can prove the existence of a polynomial-time reduction from the SUBSET-SUM problem. Therefore, solving the problem where is also unknown, is harder, and under the widespread belief that NP≠P, it is not expected to have an efficient (i.e., polynomial-time) exact algorithm. Therefore, the proposed algorithm is an efficient algorithm as an approximation algorithm.
In the previous section, we have shown that we may assume that is full-rank, thus leading to the relaxed problem: , where . The constraint was replaced by a closed convex approximation envelope and the parametrization in terms of of all the solutions for was given. Next, the closed convex sets and were defined, and their related projections (of an outer point to its closest point in the related set) and were defined. We, therefore, need an intersection point, i.e., a point in .
For this purpose, we use the Alternating Projections (AP) algorithm, which is a known efficient algorithm that finds a point of intersection of a collection of closed convex sets, and was proven to have a linear rate of convergence globally (see [
39,
40]) and linear rate of convergence locally for non-convex sets (see [
41]). Let
denote the initial error, where
is the initial point in the search space and
is a solution to the problem
where
, which, in view of Remark 2, is a point of the intersection
. We may therefore take
to be the point of intersection
with
that is the closest to the initial point. Therefore, the algorithm converges to a point
of intersection
, where
is the closest to
.
Let denote the error after iteration t was executed. Then, the linearity of convergence means that for some . It follows that there exists such that , for any t. Therefore, for a given error threshold , implies that the needed number of iterations to achieve the goal is , that is , where is the final number of iterations. The complexity of a single iteration is due to matrix multiplications, matrix inversions, and pseudo-inversions. We conclude that the overall complexity of the proposed AP-HSIC algorithm is: .
Since the only constraint on
is that it should satisfy
, and
satisfy this constraint for any
t, we may assume that
, where
is the final iteration. Therefore,
, and using Theorem A4, we conclude that:
Or, in other words, if the given error threshold is
, then
will achieve the goal
. In this case, the needed SNR is:
Note that the monotone convergence of the AP algorithm implies that
is between
and
, and
is between
and
. It follows that
and
, from which we conclude that:
Therefore, if
, then
and we can break the whole loop (Algorithm 1 line 7) since the AP algorithm has converged. On the other hand, if
, then
means that the AP algorithm has not converged yet. This explains the condition in Algorithm 1 line 7.
Since we may assume that
are bounded, therefore the size of the matrices, and specifically
, enter the complexity of the proposed AP-HSIC algorithm as a constant multiplicative factor. Thus, in this case, the complexity would be dominated by the relation between
and
, which causes the algorithm to undergo several iterations that are shown in the following simulations to be decreasing as a function of the SNR at a rate that is proportional to
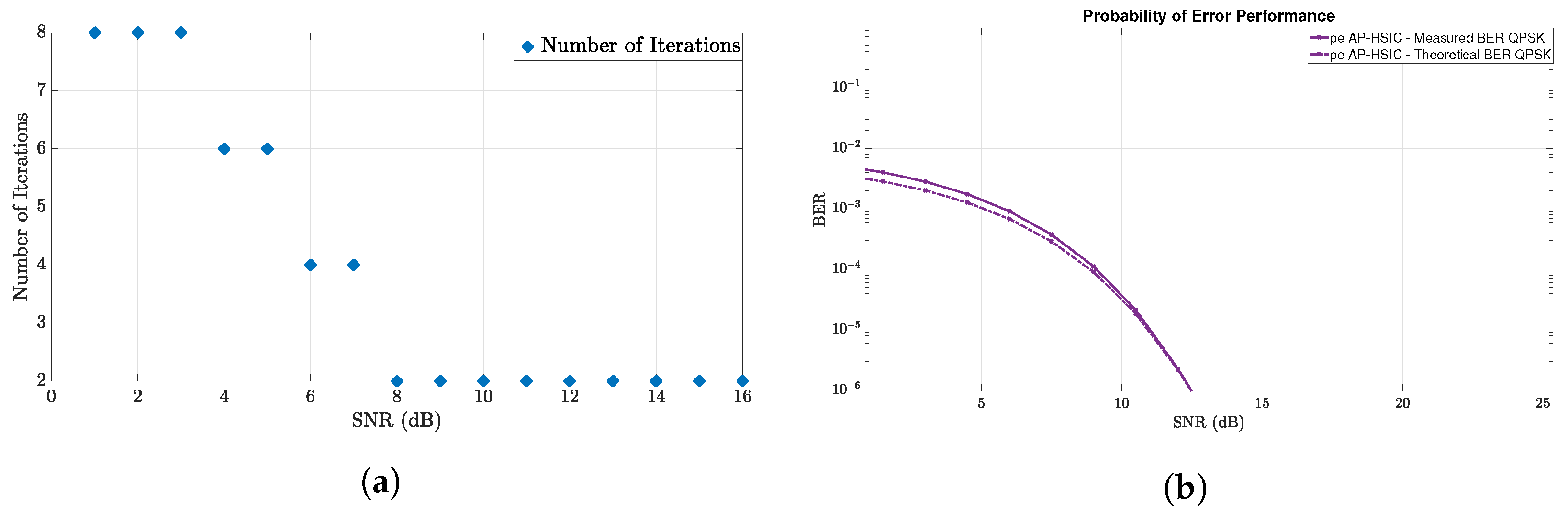
, thus assessing Theorem A4 and specifically (
A6). In the simulations, we have fixed the error threshold to be
, where each simulation period was fixed to
and where the symbol-time was fixed to
, which are custom values for the problem. In each simulation, the algorithm is shown to have no more than eight iterations (in the range
), where the convergence was achieved within the simulation period for all simulations.
If, in other scenarios or under different assumptions, the algorithm does not converge within the expected time period, it only means that more computational power is needed at the receiver side because, as noted earlier, the algorithm always converges (in a linear rate of convergence). Finally, note that the algorithm can work with other modulation orders, e.g., 16,32-QAM, since it only needs the definition of a relatively small closed convex set that contains all the possible symbol matrices (i.e., the modulation set) and a projection onto the modulation set that projects a general point onto the closest point in the modulation set.