An Approach towards Designing Logic Locking Using Shape-Perpendicular Magnetic Anisotropy-Double Layer MTJ
Abstract
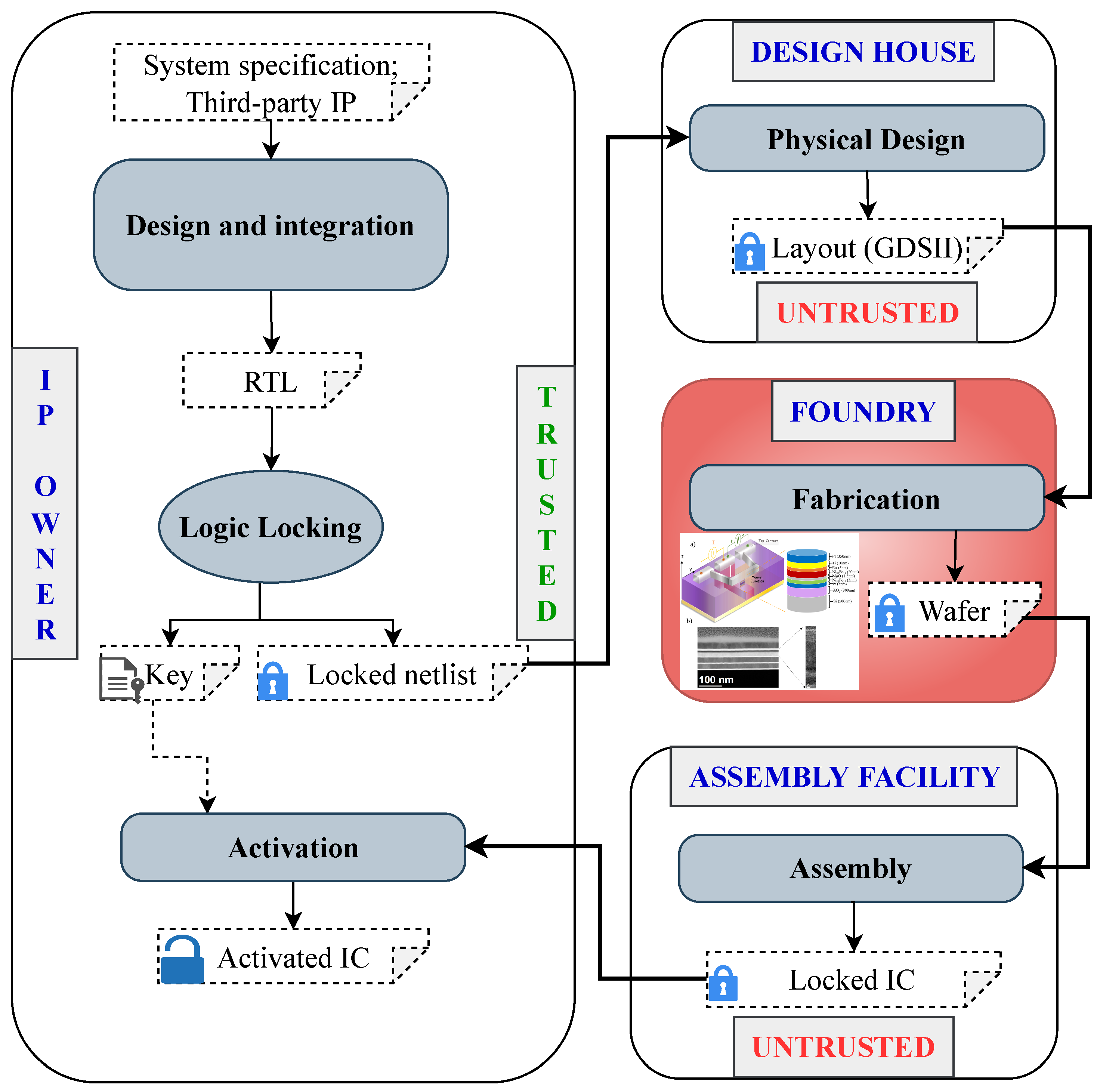
1. Introduction
2. Background
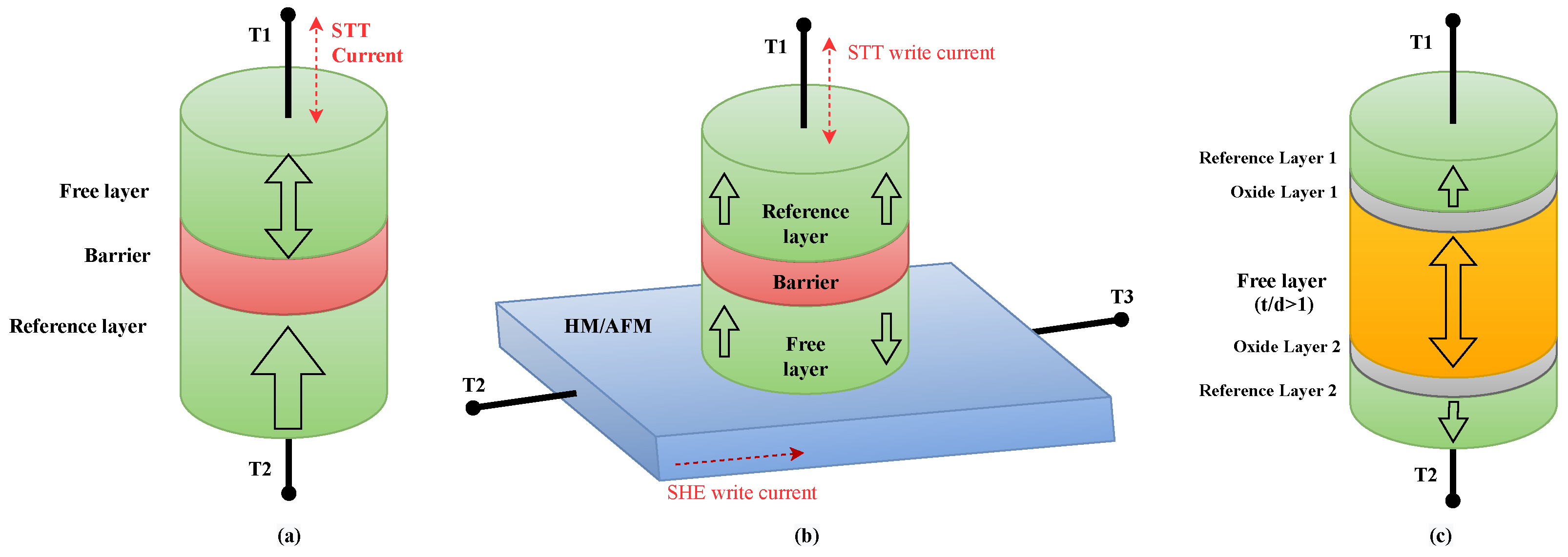
2.1. s-PMA Double Barrier MTJ
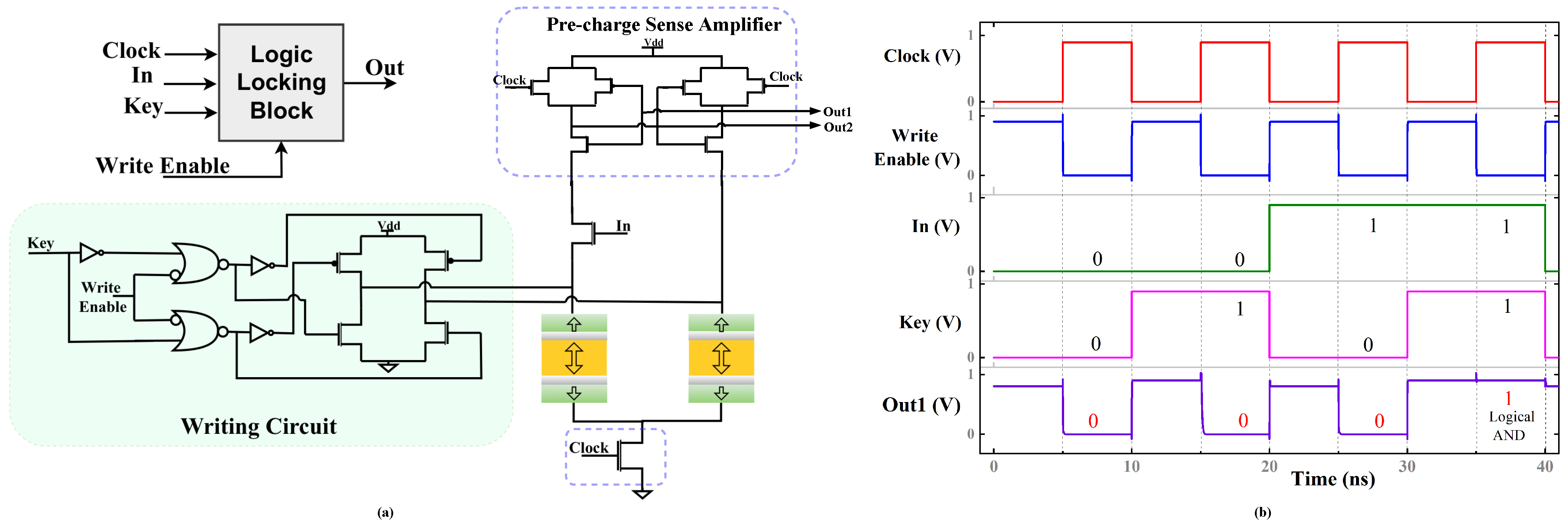
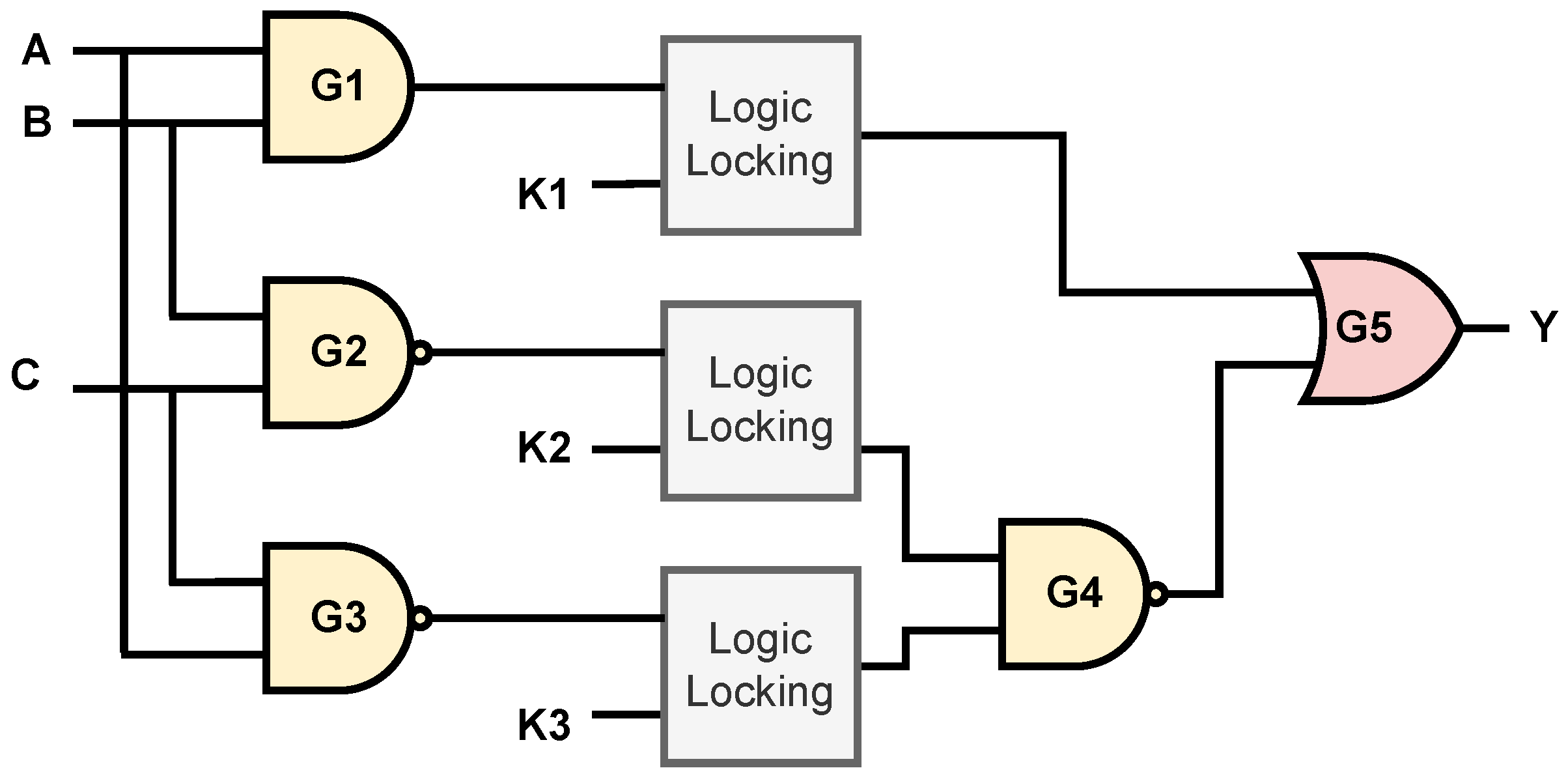
2.2. Design of LL Block Using s-PMA DMTJ
3. Simulation Setup
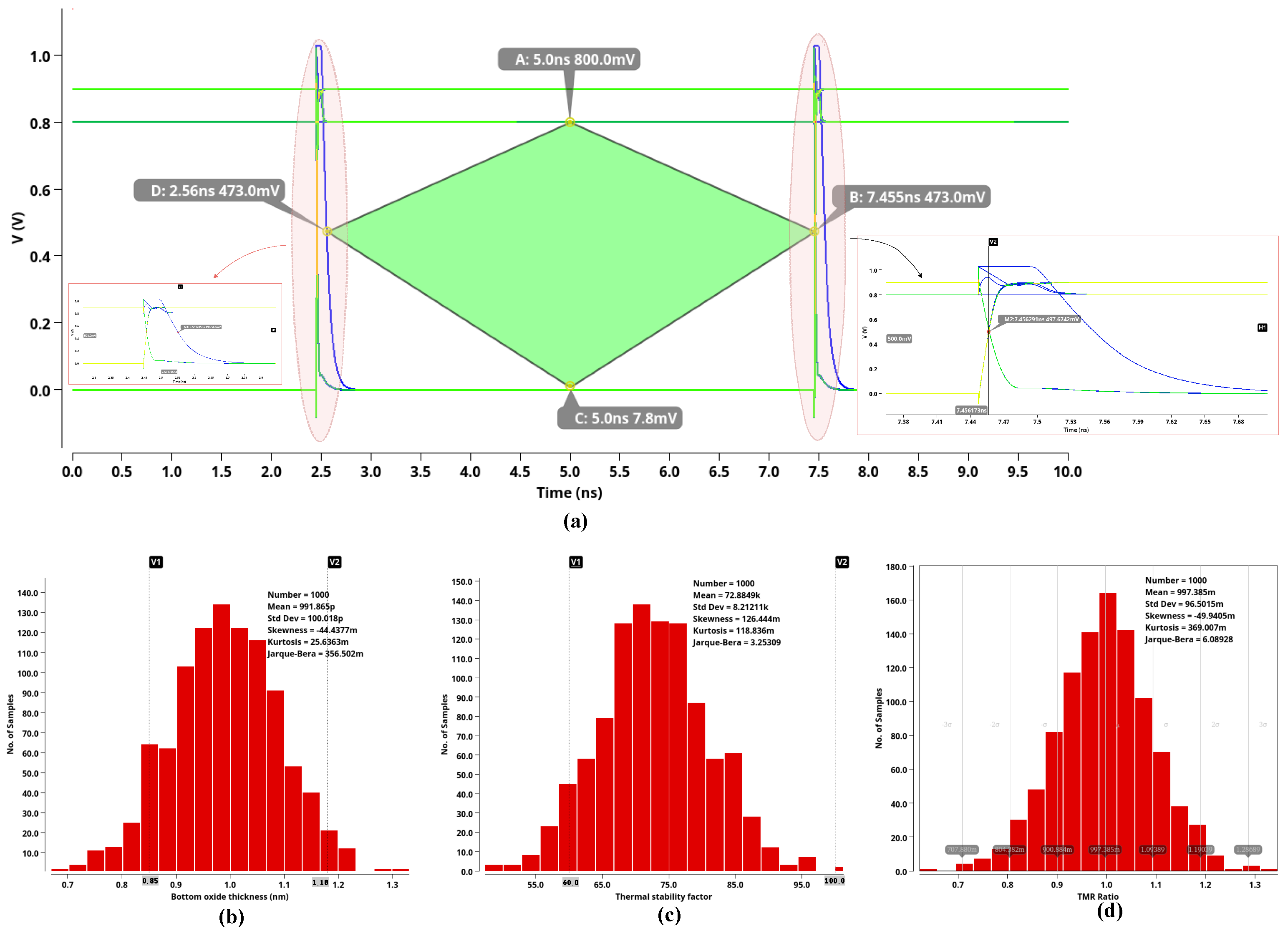
3.1. Eye Diagram Test for Signal Integrity at High Data Rates
3.2. Transient Measurement
3.3. Monte Carlo Simulations
3.4. Spectrum Analysis
4. Simulation Results
4.1. Logic Locking Block
4.1.1. Parametric Sweep and Performance Evaluation
4.1.2. Eye Diagram Mask and Monte Carlo Simulation
4.2. Test Circuit
5. Security Aspect and Challenges of s-DMTJ Based LL
5.1. Layout Camouflaging
5.2. Output Corruption Measurements for Logic Locking
5.3. Current Challenges in s-DMTJ Based LL
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hu, W.; Chang, C.-H.; Sengupta, A.; Bhunia, S.; Kastner, R.; Li, H. An Overview of Hardware Security and Trust: Threats, Countermeasures, and Design Tools. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2021, 40, 1010–1038. [Google Scholar] [CrossRef]
- Chakraborty, A.; Jayasankaran, N.G.; Liu, Y.; Rajendran, J.; Sinanoglu, O.; Srivastava, A.; Xie, Y.; Yasin, M.; Zuzak, M. Keynote: A Disquisition on Logic Locking. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2020, 39, 1952–1972. [Google Scholar] [CrossRef]
- Khan, M.N.I.; Ghosh, S. Comprehensive Study of Security and Privacy of Emerging Non-Volatile Memories. J. Low Power Electron. Appl. 2021, 11, 36. [Google Scholar] [CrossRef]
- Mishra, R.; Yang, H. Emerging Spintronics Phenomena and Applications. IEEE Trans. Magn. 2021, 57, 1–34. [Google Scholar] [CrossRef]
- Srinivasan, S.; Sarkar, A.; Behin-Aein, B.; Datta, S. All-Spin Logic Device with Inbuilt Nonreciprocity. IEEE Trans. Magn. 2011, 47, 4026–4032. [Google Scholar] [CrossRef]
- Shreya, S.; Jain, A.; Kaushik, B.K. Computing-in-Memory Architecture Using Energy-Efficient Multilevel Voltage-Controlled Spin-Orbit Torque Device. IEEE Trans. Electron Devices 2020, 67, 1972–1979. [Google Scholar] [CrossRef]
- Shen, S.Q. Spintronics and spin current. AAPPS Bull. 2008, 18, 29. [Google Scholar]
- Ghosh, S. Spintronics and Security: Prospects, Vulnerabilities, Attack Models, and Preventions. Proc. IEEE 2016, 104, 1864–1893. [Google Scholar] [CrossRef]
- Onizawa, N.; Mukaida, S.; Tamakoshi, A.; Yamagata, H.; Fujita, H.; Hanyu, T. High-Throughput/Low-Energy MTJ-Based True Random Number Generator Using a Multi-Voltage/Current Converter. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2020, 28, 2171–2181. [Google Scholar] [CrossRef]
- Divyanshu, D.; Kumar, R.; Khan, D.; Amara, S.; Massoud, Y. Physically Unclonable Function using GSHE driven SOT assisted p-MTJ for next generation hardware security applications. IEEE Access 2022, 10, 93029–93038. [Google Scholar] [CrossRef]
- Kumar, R.; Divyanshu, D.; Khan, D.; Amara, S.; Massoud, Y. Spin Orbit Torque-Assisted Magnetic Tunnel Junction-Based Hardware Trojan. Electronics 2022, 11, 1753. [Google Scholar] [CrossRef]
- Divyanshu, D.; Kumar, R.; Khan, D.; Amara, S.; Massoud, Y. Logic Locking Using Emerging 2T/3T Magnetic Tunnel Junctions for Hardware Security. IEEE Access 2022, 10, 102386–102395. [Google Scholar] [CrossRef]
- Wang, H.; Kang, W.; Zhang, Y.; Zhao, W. Modeling and Evaluation of Sub-10-nm Shape Perpendicular Magnetic Anisotropy Magnetic Tunnel Junctions. IEEE Trans. Electron Devices 2018, 65, 5537–5544. [Google Scholar] [CrossRef]
- Chun, K.C.; Zhao, H.; Harms, J.D.; Kim, T.-H.; Wang, J.-P.; Kim, C.H. A Scaling Roadmap and Performance Evaluation of In-Plane and Perpendicular MTJ Based STT-MRAMs for High-Density Cache Memory. IEEE J. Solid-State Circuits 2013, 48, 598–610. [Google Scholar] [CrossRef]
- Garzon, E.; De Rose, R.; Crupi, F.; Trojman, L.; Lanuzza, M. Assessment of STT-MRAM performance at nanoscaled technology nodes using a device-to-memory simulation framework. Microelectron. Eng. 2019, 215, 111009. [Google Scholar] [CrossRef]
- Wang, Z.; Zhao, W.; Deng, E.; Klein, J.O.; Chappert, C. Perpendicular-anisotropy magnetic tunnel junction switched by spin-Hall-assisted spin-transfer torque. J. Phys. D Phys. 2015, 48, 065001. [Google Scholar] [CrossRef]
- Zhang, K.; Zhang, D.; Wang, C.; Zeng, L.; Wang, Y.; Zhao, W. Compact Modeling and Analysis of Voltage-Gated Spin-Orbit Torque Magnetic Tunnel Junction. IEEE Access 2020, 8, 50792–50800. [Google Scholar] [CrossRef]
- Watanabe, K.; Jinnai, B.; Fukami, S.; Sato, H.; Ohno, H. Shape anisotropy revisited in single-digit nanometer magnetic tunnel junctions. Nat. Commun. 2018, 9, 663. [Google Scholar] [CrossRef]
- Perrissin, N.; Lequeux, S.; Strelkov, N.; Chavent, A.; Vila, L.; Buda-Prejbeanu, L.D.; Auffret, S.; Sousa, R.C.; Prejbeanu, I.L.; Dieny, B. A highly thermally stable sub-20 nm magnetic random-access memory based on perpendicular shape anisotropy. Nanoscale 2018, 10, 12187. [Google Scholar] [CrossRef] [PubMed]
- Wang, M.; Zhang, Y.; Zhao, X.; Zhao, W. Tunnel Junction with Perpendicular Magnetic Anisotropy: Status and Challenges. Micromachines 2015, 6, 1023–1045. [Google Scholar] [CrossRef]
- Limaye, N.; Kalligeros, E.; Karousos, N.; Karybali, I.G.; Sinanoglu, O. Thwarting All Logic Locking Attacks: Dishonest Oracle with Truly Random Logic Locking. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2021, 40, 1740–1753. [Google Scholar] [CrossRef]
- Zhang, Y.; Yan, B.; Kang, W.; Cheng, Y.; Klein, J.O.; Zhang, Y.; Chen, Y.; Zhao, W. Compact Model of Subvolume MTJ and Its Design Application at Nanoscale Technology Nodes. IEEE Trans. Electron Devices 2015, 62, 2048–2055. [Google Scholar] [CrossRef]
- Kang, W.; Ran, Y.; Zhang, Y.; Lv, W.; Zhao, W. Modeling and Exploration of the Voltage-Controlled Magnetic Anisotropy Effect for the Next,-Generation Low-Power and High-Speed MRAM Applications. IEEE Trans. Nanotechnol. 2017, 16, 387–395. [Google Scholar] [CrossRef]
- Divyanshu, D.; Kumar, R.; Khan, D.; Amara, S.; Massoud, Y. Design of VGSOT-MTJ-Based Logic Locking for High-Speed Digital Circuits. Electronics 2022, 11, 3537. [Google Scholar] [CrossRef]
- Azriel, L.; Ginosar, R.; Mendelson, A. Sok: An overview of algorithmic methods in IC reverse engineering. In Proceedings of the 3rd ACM Workshop on Attacks and Solutions in Hardware Security Workshop, London, UK, 15 November 2019; pp. 65–74. [Google Scholar]
- Subramanyan, P.; Tsiskaridze, N.; Li, W.; Gascón, A.; Tan, W.Y.; Tiwari, A.; Shankar, N.; Seshia, S.A.; Malik, S. Reverse engineering digital circuits using structural and functional analyses. IEEE Trans. Emerg. Top. Comput. 2013, 1, 63–80. [Google Scholar] [CrossRef]
- Rajendran, J.; Sam, M.; Sinanoglu, O.; Karri, R. Security analysis of integrated circuit camouflaging. In Proceedings of the ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 709–720. [Google Scholar]
- Zhang, H.; Kang, W.; Wang, L.; Wang, K.L.; Zhao, W. Stateful Reconfigurable Logic via a Single-Voltage-Gated Spin Hall-Effect Driven Magnetic Tunnel Junction in a Spintronic Memory. IEEE Trans. Electron Devices 2017, 64, 4295–4301. [Google Scholar] [CrossRef]
- Rajendran, J.; Zhang, H.; Zhang, C.; Rose, G.S.; Pino, Y.; Sinanoglu, O.; Karri, R. Fault Analysis-Based Logic Encryption. IEEE Trans. Comput. 2015, 64, 410–424. [Google Scholar] [CrossRef]
- Sengupta, A.; Nabeel, M.; Limaye, N.; Ashraf, M.; Sinanoglu, O. Truly Stripping Functionality for Logic Locking: A Fault-based Perspective. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. (TCAD) 2020, 39, 4439–4452. [Google Scholar] [CrossRef]
- Sanchez Hazen, D.; Teixeira, B.M.S.; Salomoni, D.; Auffret, S.; Vila, L.; Sousa, R.C.; Prejbeanu, I.L.; Buda-Prejbeanu, L.D.; Dieny, B. Real time investigation of double magnetic tunnel junction with a switchable assistance layer for high efficiency STT-MRAM. APL Mater. 2022, 10, 031104. [Google Scholar] [CrossRef]
- McPherson, J.W. Time dependent dielectric breakdown physics-Models revisited. Microelectron. Reliab. 2012, 52, 1753–1760. [Google Scholar] [CrossRef]
- Lv, H.; Leitao, D.C.; Hou, Z.; Freitas, P.P.; Cardoso, S.; Kämpfe, T.; Müller, J.; Langer, J.; Wrona, J. Barrier Breakdown Mechanism in Nano-Scale Perpendicular Magnetic Tunnel Junctions with Ultrathin MgO Barrier. AIP Adv. 2018, 8, 055908. [Google Scholar] [CrossRef]
- Van Beek, S.; Martens, K.; Roussel, P.; Couet, S.; Souriau, L.; Swerts, J.; Kim, W.; Rao, S.; Mertens, S.; Lin, T.; et al. Impact of Processing and Stack Optimization on the Reliability of Perpendicular STT-MRAM. In Proceedings of the 2017 IEEE International Reliability Physics Symposium (IRPS), Monterey, CA, USA, 2–6 April 2017. [Google Scholar]



| Parameter | Value |
|---|---|
| Diameter (D) | 10 nm |
| Free Layer Thickness (t) | 14 nm |
| Top Oxide Thickness | 0.2 nm |
| Bottom Oxide Thickness | 1 nm |
| TMR Ratio at zero bias | 1 |
| Damping Coefficient | 0.005 |
| Saturation Magnetization () | 1.2 × 10 A/m |
| Spin Polarization | 0.57 |
| Interfacial anisotropy density () | 2.2 × 10 KJ/m |
| Gyromagnetic Ratio () | 2.21 × 10 m/ (A.s) |
| Eye-Parameters | PMA-STT | Pre-VCMA STT | s-DMTJ |
|---|---|---|---|
| Level 0, 1: Mean | 290.6 nV, 1 V | 293.7 nV, 1 V | 64.36 V, 1 V |
| Level 0, 1: SD | 26.98 pV, 1.909 nV | 3.088 nV, 4.893 nV | 15.45 V, 12.54 V |
| Eye Amplitude & Height | 1 V, 1 V | 1 V, 1 V | 999.9 mV, 999.8 mV |
| Eye Width | 4.8 ns | 4.266 ns | 3.795 ns |
| Eye Rise & Fall Time | 4.758 ps, 7.462 ps | 4.687 ps, 16.18 ps | 1.195 ps, 127.6 ps |
| Random Jitter | 20.6 ps | 77.41 ps | 126 ps |
| Deterministic Jitter | 71.64 ps | 269.2 ps | 448.7 ps |
| A | B | C | Y | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | |||
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 0 | 1 | 1 |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | 1 | 0 | 1 | 0 | 1 | 0 | 1 | 0 | 1 |
| 1 | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 |
| 1 | 1 | 1 | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 1 |
| Parameter | PMA STT | Pre-VCMA | s-DMTJ |
|---|---|---|---|
| Amplitude (RMS) | 874.7 mV | 880 mV | 881.4 mV |
| Minimum Delay | 100.6 ps | 298.7 ps | 462.7 ps |
| Duty Cycle | 50.72% | 52.72% | 54.24% |
| Minimum Fall Time | 12.70 ps | 25.93 ps | 47.2 ps |
| Minimum Rise Time | 8.295 ps | 7.724 ps | 41.58 ps |
| Parameters | PMA STT | Pre-VCMA | s-DMTJ |
|---|---|---|---|
| ENOB | −0.286 (bits) | −1.159 (bits) | −0.455 (bits) |
| SNR | 0.033 (dB) | −5.222 (dB) | −0.980 (dB) |
| SFDR | 1.009 (dBc) | 1.995 (dBc) | 0.274 (dBc) |
| Signal Power | −7.376 (dB) | −10.925 (dB) | −8.095 (dB) |
| Noise Floor/Bin | −31.441 (dB) | −31.653 (dB) | −31.627 (dB) |
| Parameters | PMA STT | Pre-VCMA | s-DMTJ |
|---|---|---|---|
| MTJ area | High | High | Low |
| Signal Integrity | High | Medium | Medium |
| Transient | High | High | Medium |
| Spectrum | High | Medium | Medium |
| Thermal Stability | Medium | Medium | High |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Divyanshu, D.; Kumar, R.; Khan, D.; Amara, S.; Massoud, Y. An Approach towards Designing Logic Locking Using Shape-Perpendicular Magnetic Anisotropy-Double Layer MTJ. Electronics 2023, 12, 479. https://doi.org/10.3390/electronics12030479
Divyanshu D, Kumar R, Khan D, Amara S, Massoud Y. An Approach towards Designing Logic Locking Using Shape-Perpendicular Magnetic Anisotropy-Double Layer MTJ. Electronics. 2023; 12(3):479. https://doi.org/10.3390/electronics12030479
Chicago/Turabian StyleDivyanshu, Divyanshu, Rajat Kumar, Danial Khan, Selma Amara, and Yehia Massoud. 2023. "An Approach towards Designing Logic Locking Using Shape-Perpendicular Magnetic Anisotropy-Double Layer MTJ" Electronics 12, no. 3: 479. https://doi.org/10.3390/electronics12030479
APA StyleDivyanshu, D., Kumar, R., Khan, D., Amara, S., & Massoud, Y. (2023). An Approach towards Designing Logic Locking Using Shape-Perpendicular Magnetic Anisotropy-Double Layer MTJ. Electronics, 12(3), 479. https://doi.org/10.3390/electronics12030479








