Enabling Privacy-Preserving Data Sharing with Bilateral Access Control for Cloud
Abstract
:1. Introduction
- We suggest a data-sharing scheme for cloud services, derived from identity-based matchmaking encryption, named IBME-DS. The access policies in IBME-DS are specified by both the sender and receiver to achieve bilateral access control.
- To further improve the system efficiency, we design a privacy-preserving matching mechanism to delegate the matching process to the cloud server, which ensures user privacy and data confidentiality during the matching procedure.
- We formally define the system model, threat model, and security model of IBME-DS. Then, a comprehensive security analysis is to demonstrate that our proposed scheme meets the practical security requirements.
- Finally, we evaluate the performance of IBME-DS by conducting extensive experiments on a real-world dataset to show that IBME-DS is more efficient than relevant works.
2. Preliminary
- Bilinearity: The map e is bilinear, if , for , and .
- Non-degeneracy: There exists , where is the identity in .
- Computability: can be computed efficiently, for , .
2.1. Matchmaking Encryption
- Setup: Given the security parameter , the algorithm is to initialize the system and output a set of master keys, as master public/policy/secret key .
- : Given the sender’s attributes , and the master secret key , the algorithm is to generate the encryption key to the sender with attributes .
- : Given the receiver’s attributes , and the master secret key , the algorithm is to generate the decryption key to the sender with attributes .
- : Given the access policy , and the master policy key , the algorithm is to generate the decryption key for the access policy .
- : Given the encryption key , the access policy , and the message m, the algorithm is to generate the ciphertext c.
- or ⊥: Given the decryption key , the decryption key , and the ciphertext c, the algorithm is to output either the message m or ⊥.
2.2. Identity-Based Matchmaking Encryption
- Setup: Given the security parameter , the algorithm will output the master public/secret key .
- : Given the sender’s identity , and the master secret key , the algorithm will output the encryption key .
- : Given the receiver’s identity , and the master secret key , the algorithm will output the decryption key .
- : Given the target receiver’s identity , the master public key , the encryption key , and the message , and the algorithm will output the ciphertext c, associated to both and .
- or ⊥: Given the target sender’s identity , the master public key , the decryption key , and the ciphertext c, the algorithm will compute and output either the message m or ⊥.
3. Definition and System Model
3.1. System Model
- Key Generation Center: KGC is defined as the fully trusted party in the system, to initialize system parameters and generate master public/secret keys for users. By taking the identity from users as input, it secretly outputs the encryption key and decryption key to senders and receivers via the secure channel.
- Cloud Server: CS receives the information from users and performs matching. Then, it returns the successful matching results to the receiver.
- Sender: The sender has his/her own unique identity . Through the identity , the sender can be uniquely designated. In particular, the sender can specify the target receiver in the ciphertext. The sender’s identity will not be revealed even if the match fails.
- Receiver: The receiver also has his/her own unique identity . Similarly, the receiver can also specify the target sender.
- : Given the security parameter , the probabilistic algorithm will output the master public/secret key .
- : Given the sender’s identity and the master secret key , the probabilistic algorithm will output the encryption key .
- : Given the receiver’s identity and the master secret key , the probabilistic algorithm will output the decryption key .
- : Given the target receiver’s identity , the master public key , the encryption key , and the message , the probabilistic algorithm will output the ciphertext C.
- : Given the target sender’s identity , the master public key , the probabilistic algorithm will output the match tag .
- “accepted” or “failed”: Given the master public key , the ciphertext C, and the match tag , the deterministic algorithm will output “accepted”, if the match occurs. Otherwise, “failed”.
- : Given the target sender’s identity , the master public key , the decryption key , and the ciphertext C, the deterministic algorithm will recover the message m, if and .
3.2. Threat Model
3.3. Security Model
- Setup: The system is established with the input security parameter. Then, the challenger sets the master public/secret key .
- Hash Query: The adversary requests the hash oracle to get the corresponding hash values for polynomial times.
- KeyGen Query: The adversary requests the key generation oracle and for polynomial times to obtain the corresponding , respectively.
- Challenge: The adversary claims to be challenged, and provides two instances and . Then, the challenger chooses randomly. By running algorithm, the challenger can compute . Finally, will be sent to the adversary.
- Guess: After receiving from the challenger, the adversary outputs a guess on b.
- Setup: The system is established with the input security parameter. Then, the challenger sets the master public/secret key .
- Hash Query: The adversary requests the hash oracle to get the corresponding hash values for polynomial times.
- SKGen Query: The adversary requests the SKGen oracle by inputting , the challenger returns the sender’s encryption key.
- RKGen Query: The adversary requests the RKGen oracle by inputting , the challenger returns the receiver’s decryption key.
- Forgery: The adversary sends the tuple to the challenger, in which has never been input to the SKGen oracle. The challenger generates by executing the algorithm. Then, the challenger computes the message m from the ciphertext C by executing the algorithm.
3.4. Design Goal
- Security. The security is to ensure the system is with semantic security under the attack launched by any PPT adversary. The security is the basic demand of the data-sharing scheme in cloud services, which ensures the message m is unknown to others.
- Privacy. The privacy is aimed at preventing the stored data and access policy from being revealed to the cloud, even in the matching phase.
- Authenticity. The authenticity means that a valid ciphertext under identity can only be generated by a valid encryption key from KGC. In other words, it guarantees that if a sender with the proper identity can produce a ciphertext, the ciphertext can be decrypted correctly.
- Bilateral Access Control. The bilateral access control ensures that the access policy is designed by both the sender and receiver. Compared to the existing access control scheme, of which the policy is only designed by one side, bilateral access control is a practical requirement for data sharing to cloud services.
4. Concrete Construction
4.1. Workflow of IBME-DS
4.2. IB-ME-Based Data-Sharing Scheme
- Setup: The system runs this probabilistic algorithm. Taking in the security parameter , the system sets , where . Then, it selects two hash functions as , and , and a padding function , where is efficiently invertible. Additionally, the system chooses four random numbers and sets , and . The system publishes the master public key . The master secret key keeps secretly.
- : KGC runs this probabilistic algorithm. Taking in the sender’s identity , and the master secret key , KGC computes the encryption key . Then, KGC sends to the sender with the identity .
Algorithm 1 SKGen Input: the sender’s identity , the master secret key .
Output: the sender’s encryption key .
Compute .
return the sender’s encryption key - : KGC runs this probabilistic algorithm. Taking in the receiver’s identity , and the master secret key , KGC computes the decryption key , as Equation (3):Then, KGC sends to the receiver with the identity .
Algorithm 2 RKGen Input: the receiver’s identity , the master secret key .
Output: the receiver’s decryption key .
Compute .
return the receiver’s decryption key . - : The sender runs this probabilistic algorithm. Taking in the target receiver’s identity , the master public key , the sender’s encryption key , and the message , the sender conducts as the following steps:
- 1.
- Select .
- 2.
- Compute .
- 3.
- Compute .
- 4.
- Compute Equation (4)
- 5.
- Compute
- 6.
- Output ciphertext .
Algorithm 3 Enc Input: the target receiver’s identity , the master public key , the sender’s encryption key , and the message m.
Output: ciphertext C.
Select random numbers .
Compute .
Compute .
Compute
Compute .
return ciphertext . - : The receiver runs this probabilistic algorithm. Taking in the target sender’s identity , the master public key , the receiver computes the auxiliary information as the match tag when the matching is delegated to the CS. The receiver chooses randomly . It computes Equation (5) as follows:The detailed computations on are as Equation (6):The receiver sends to the CS.
Algorithm 4 MatchTag Input: the target sender’s identity , the master public key .
Output: the match tag .
Choose randomly .
Let .
Compute
Compute .
return the match tag . - : CS runs this deterministic algorithm. Taking in the master public key , the ciphertext C, and the match tag , CS executes check Equation (7)If the equation holds, CS outputs “accepted”, to indicate the match occurs. Otherwise, “failed”.
Algorithm 5 Match - : The receiver runs this deterministic algorithm. Taking in the target sender’s identity , master public key , the decryption key , and the ciphertext C, the receiver conducts the following operations:
- 1.
- Parse C as .
- 2.
- Compute
- 3.
- Compute .
- 4.
- Recover the message m by the reversibility of .
Algorithm 6 Dec Input: the target sender’s identity , the master public key , the decryption key , and the ciphertext C.
Output: the message m.
Parse C as ;
Compute
Compute .
return the message .
5. Security Analysis
- 1.
- If query has been requested before, that the query can be found in , returns . Otherwise, generates a coin , .
- 2.
- If , chooses and computes . Then, add to . Otherwise, sets , and adds to , where x is unknown to .
- 3.
- Return .
- 1.
- queries and . Let and , it means that .
- 2.
- selects a random .
- 3.
- sends to .
- 1.
- If query has been requested before, that the query can be found in , returns . Otherwise, generates a coin randomly, .
- 2.
- If , randomly selects and computes . Otherwise, computes . Then, add to .
- 3.
- Finally, send to .
- 1.
- If query has been requested before, then the query can be found in , returns . Otherwise, generates a coin randomly, .
- 2.
- If , randomly selects and computes . Otherwise, computes . Then, add to .
- 3.
- Finally, send to .
- 1.
- queries and .
- 2.
- If both the tuples and without and , aborts. If not, , , , where , and .
- 3.
- parses C as , computes and selects a random tuple .
- 4.
- Return .
6. Theoretical Analysis and Performance Evaluation
6.1. Theoretical Analysis
6.2. Experimental Setting
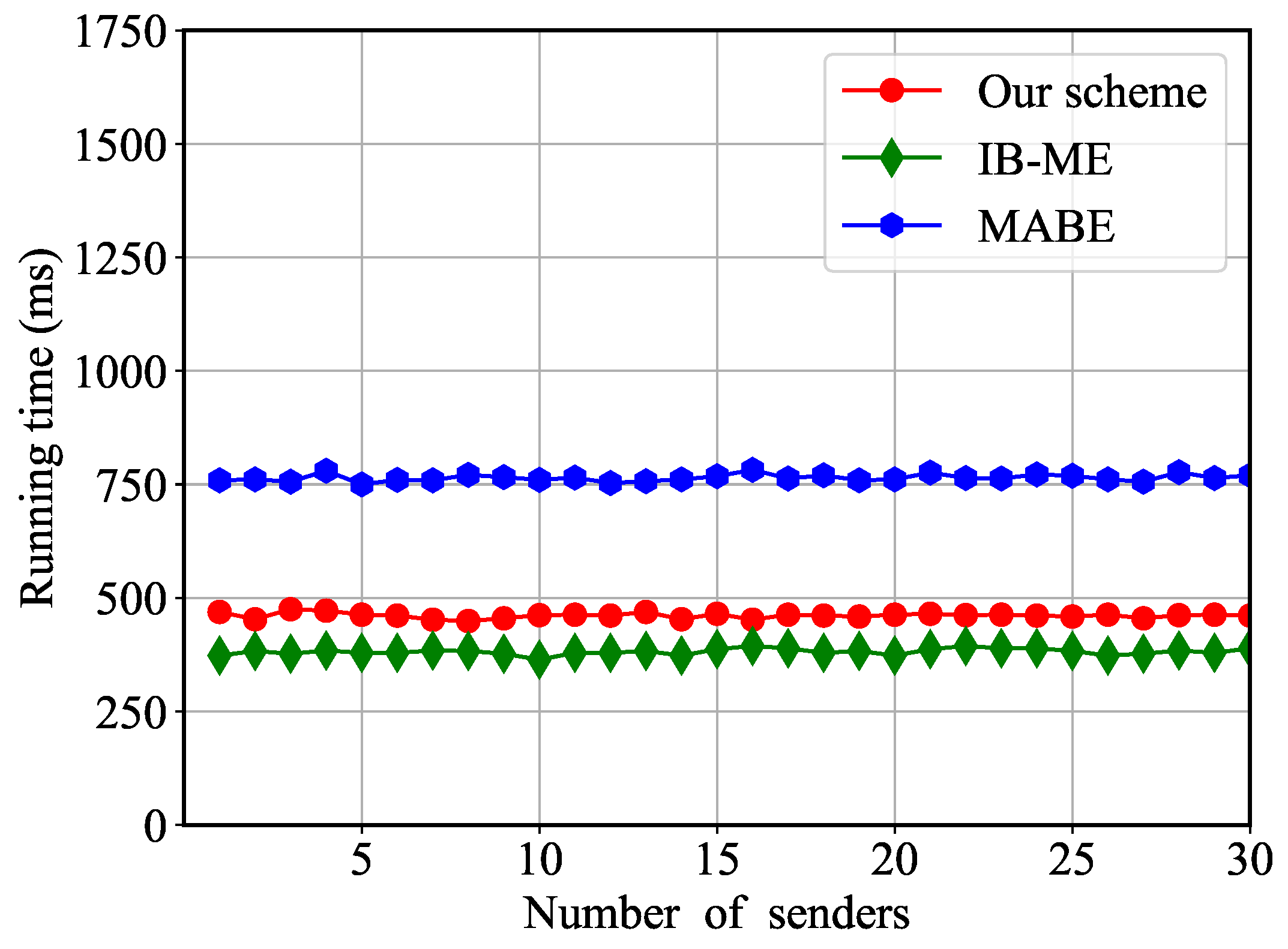
6.3. Computational Cost
6.4. Communication Overhead
7. Related Work
7.1. Access Control
7.2. Matchmaking Encryption
8. Discussion
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ganapathy, D.N.; Joshi, K.P. A Semantically Rich Framework to Automate Cloud Service Level Agreements. IEEE Trans. Serv. Comput. 2022, 16, 53–64. [Google Scholar] [CrossRef]
- Zhang, C.; Zhu, L.; Xu, C.; Ni, J.; Huang, C.; Shen, X. Location privacy-preserving task recommendation with geometric range query in mobile crowdsensing. IEEE Trans. Mob. Comput. 2021, 21, 4410–4425. [Google Scholar] [CrossRef]
- Mahmoud, M.M.; Rodrigues, J.J.; Ahmed, S.H.; Shah, S.C.; Al-Muhtadi, J.F.; Korotaev, V.V.; De Albuquerque, V.H.C. Enabling technologies on cloud of things for smart healthcare. IEEE Access 2018, 6, 31950–31967. [Google Scholar] [CrossRef]
- Rajeswari, S.; Suthendran, K.; Rajakumar, K. A smart agricultural model by integrating IoT, mobile and cloud-based big data analytics. In Proceedings of the 2017 International Conference on Intelligent Computing and Control (I2C2), Coimbatore, India, 23–24 June 2017; pp. 1–5. [Google Scholar]
- Jiang, D. The construction of smart city information system based on the Internet of Things and cloud computing. Comput. Commun. 2020, 150, 158–166. [Google Scholar] [CrossRef]
- Wang, X.; Li, Z. Traffic and Transportation Smart with Cloud Computing on Big Data. Int. J. Comput. Sci. Appl. 2016, 13, 1–16. [Google Scholar]
- Meixner, F.; Buettner, R. Trust as an integral part for success of cloud computing. In Proceedings of the International Conference on Internet and Web Applications and Services, Stuttgart, Germany, 27 May–1 June 2012; pp. 207–214. [Google Scholar]
- Esposito, C.; Castiglione, A.; Martini, B.; Choo, K.K.R. Cloud manufacturing: Security, privacy, and forensic concerns. IEEE Cloud Comput. 2016, 3, 16–22. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Li, H.; Yang, K.; Zhou, J.; Lin, X. HealthDep: An efficient and secure deduplication scheme for cloud-assisted eHealth systems. IEEE Trans. Ind. Inform. 2018, 14, 4101–4112. [Google Scholar] [CrossRef]
- Zhou, Y.; Zheng, S.; Wang, L. Privacy-preserving and efficient public key encryption with keyword search based on CP-ABE in cloud. Cryptography 2020, 4, 28. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Liu, X.; Li, X.; Jiang, Q.; Zhang, J. Attribute-based keyword search over hierarchical data in cloud computing. IEEE Trans. Serv. Comput. 2017, 13, 985–998. [Google Scholar] [CrossRef]
- Zhang, C.; Zhao, M.; Zhu, L.; Zhang, W.; Wu, T.; Ni, J. FRUIT: A blockchain-based efficient and privacy-preserving quality-aware incentive scheme. IEEE J. Sel. Areas Commun. 2022, 40, 3343–3357. [Google Scholar] [CrossRef]
- Chatterjee, A.; Sengupta, I. Sorting of fully homomorphic encrypted cloud data: Can partitioning be effective? IEEE Trans. Serv. Comput. 2017, 13, 545–558. [Google Scholar] [CrossRef]
- Xu, C.; Wang, N.; Zhu, L.; Sharif, K.; Zhang, C. Achieving searchable and privacy-preserving data sharing for cloud-assisted E-healthcare system. IEEE Internet Things J. 2019, 6, 8345–8356. [Google Scholar] [CrossRef]
- Wang, N.; Yang, W.; Wang, X.; Wu, L.; Guan, Z.; Du, X.; Guizani, M. A blockchain based privacy-preserving federated learning scheme for Internet of Vehicles. Digit. Commun. Netw. 2022; in press. [Google Scholar] [CrossRef]
- Nasiraee, H.; Ashouri-Talouki, M. Anonymous decentralized attribute-based access control for cloud-assisted IoT. Future Gener. Comput. Syst. 2020, 110, 45–56. [Google Scholar] [CrossRef]
- Ateniese, G.; Francati, D.; Nuñez, D.; Venturi, D. Match me if you can: Matchmaking encryption and its applications. J. Cryptol. 2021, 34, 1–50. [Google Scholar] [CrossRef]
- Xu, S.; Ning, J.; Li, Y.; Zhang, Y.; Xu, G.; Huang, X.; Deng, R.H. Match in my way: Fine-grained bilateral access control for secure cloud-fog computing. IEEE Trans. Dependable Secur. Comput. 2020, 19, 1064–1077. [Google Scholar] [CrossRef]
- Damgård, I.; Haagh, H.; Orlandi, C. Access control encryption: Enforcing information flow with cryptography. In Proceedings of the Theory of Cryptography: 14th International Conference, Beijing, China, 31October–3 November 2016; pp. 547–576. [Google Scholar]
- Yuan, E.; Tong, J. Attributed based access control (ABAC) for web services. In Proceedings of the IEEE International Conference on Web Services (ICWS’05), Orlando, FL, USA, 11–15 July 2005. [Google Scholar]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Advances in Cryptology–EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Zheng, Q.; Xu, S.; Ateniese, G. VABKS: Verifiable attribute-based keyword search over outsourced encrypted data. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 522–530. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Huang, X.; Pang, H.H.; Deng, R.H. Expressive bilateral access control for internet-of-things in cloud-fog computing. In Proceedings of the 26th ACM Symposium on Access Control Models and Technologies, Virtual, 16–18 June 2021; pp. 143–154. [Google Scholar]
- Sun, J.; Yuan, Y.; Tang, M.; Cheng, X.; Nie, X.; Aftab, M.U. Privacy-preserving bilateral fine-grained access control for cloud-enabled industrial IOT healthcare. IEEE Trans. Ind. Inform. 2021, 18, 6483–6493. [Google Scholar] [CrossRef]
- Chen, B.; Xiang, T.; Ma, M.; He, D.; Liao, X. CL-ME: Efficient certificateless matchmaking encryption for internet of things. IEEE Internet Things J. 2021, 8, 15010–15023. [Google Scholar] [CrossRef]
- Li, T.; Li, X.; Liu, X. An efficient privacy-preserving bidirectional friends matching scheme in mobile social networks. In Proceedings of the 2019 International Conference on Networking and Network Applications (NaNA), Daegu, Republic of Korea, 10–13 October 2019; pp. 51–57. [Google Scholar]
- Francati, D.; Guidi, A.; Russo, L.; Venturi, D. Identity-based matchmaking encryption without random oracles. In Proceedings of the Progress in Cryptology–INDOCRYPT 2021: 22nd International Conference on Cryptology in India, Jaipur, India, 12–15 December 2021; Proceedings 22. Springer: Berlin/Heidelberg, Germany, 2021; pp. 415–435. [Google Scholar]
- Wu, A.; Weng, J.; Luo, W.; Yang, A.; Liu, J.N.; Jiang, Z. Cross-domain identity-based matchmaking encryption. Cryptol. ePrint Arch. 2022. Available online: https://eprint.iacr.org/2022/085 (accessed on 20 November 2023).
- Lampson, B.W. Dynamic protection structures. In Proceedings of the November 18–20, Fall Joint Computer Conference, Las Vegas, NV, USA, 18–20 November 1969; pp. 27–38. [Google Scholar]
- Lu, Y.; Maharjan, S.; Zhang, Y. Adaptive edge association for wireless digital twin networks in 6G. IEEE Internet Things J. 2021, 8, 16219–16230. [Google Scholar] [CrossRef]






| Notation | Description |
|---|---|
| e | bilinear map |
| bilinear groups | |
| p | large prime |
| g | random number |
| hash functions | |
| padding function | |
| n | the length of message |
| master secret key | |
| master public key | |
| sender’s identity | |
| receiver’s identity | |
| target receiver’s identity | |
| sender’s encryption key | |
| receiver’s decryption key | |
| m | message |
| C | ciphertext |
| Scheme | Approach | SKGen | RKGen | Enc | Dec |
|---|---|---|---|---|---|
| Damgaard [19] | ACE | ||||
| Ateniese [17] | IB-ME | ||||
| Xu [18] | MABE | ||||
| Our scheme | IB-ME |
| Hardware Configuration | |
| CPU | Intel(R)Core(TM)i5-6200U@2.30 GHz |
| RAM | 8.00 GB |
| Software Configuration | |
| OS | 64-bit Windows 10 |
| Language | Java 14.0.2 |
| Library | JPBC-2.0.0 |
| Elliptic Curve | |
| Type | Type A |
| Security Level | AES-80 |
| Based Field Size | 512 bits |
| Group Order Size | 160 bits |
| Experimental Performance | ||||||
|---|---|---|---|---|---|---|
| Number of senders | 5 | 10 | 15 | 20 | 25 | 30 |
| Running time (ms) | 515 | 1010 | 1543 | 2047 | 2679 | 3058 |
| Scheme | Encryption Key | Decryption Key | Ciphertext |
|---|---|---|---|
| Ateniese19 [17] | 512 | 1536 | 1280 |
| Xu22 [18] | 3072 | 5120 | 7168 |
| Our scheme | 512 | 1536 | 2816 |
| Type of Scheme | Data Privacy | Sender Privacy | Outsource Match | Identity-Based Encryption | Access Control | |
|---|---|---|---|---|---|---|
| [20] | ABAC | × | × | × | × | one-way |
| [21,22,23] | ABE | √ | √ | × | × | one-way |
| [19] | ACE | √ | × | √ | × | bilateral |
| [17] | ME | √ | √ | × | × | bilateral |
| [24,25] | ME | √ | √ | √ | × | bilateral |
| [26] | CL-ME | √ | √ | × | √ | bilateral |
| [18,27] | AB-ME | √ | √ | √ | × | bilateral |
| [28,29] | IB-ME | √ | √ | × | √ | bilateral |
| Ours | IB-ME | √ | √ | √ | √ | bilateral |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, T.; Ma, X.; Yan, H. Enabling Privacy-Preserving Data Sharing with Bilateral Access Control for Cloud. Electronics 2023, 12, 4798. https://doi.org/10.3390/electronics12234798
Wu T, Ma X, Yan H. Enabling Privacy-Preserving Data Sharing with Bilateral Access Control for Cloud. Electronics. 2023; 12(23):4798. https://doi.org/10.3390/electronics12234798
Chicago/Turabian StyleWu, Tong, Xiaochen Ma, and Hailun Yan. 2023. "Enabling Privacy-Preserving Data Sharing with Bilateral Access Control for Cloud" Electronics 12, no. 23: 4798. https://doi.org/10.3390/electronics12234798
APA StyleWu, T., Ma, X., & Yan, H. (2023). Enabling Privacy-Preserving Data Sharing with Bilateral Access Control for Cloud. Electronics, 12(23), 4798. https://doi.org/10.3390/electronics12234798









