Augmenting Vehicular Ad Hoc Network Security and Efficiency with Blockchain: A Probabilistic Identification and Malicious Node Mitigation Strategy
Abstract
:1. Introduction
- High Vehicle Mobility: The highly dynamic nature of VANETs, which are characterized by vehicles moving at high speeds, results in frequent changes in network nodes. This demands an authentication system that is capable of rapidly adapting to changes in network topology without compromising on security or performance.
- Resource Limitations in Vehicles: Despite being equipped with advanced technologies, modern vehicles still face limitations in terms of processing power and storage capacity. An efficient authentication system must operate within these resource constraints, thereby ensuring light computational loads.
- Anonymity and Privacy Needs: Given the sensitive nature of vehicular data, such as location and movement patterns, ensuring user anonymity and privacy is paramount. Achieving this without significantly increasing the computational burden adds complexity to system design.
- Diversity and Scalability: VANETs support a wide array of applications, from road safety to infotainment services, each with its unique security requirements. The authentication system must be versatile enough to cater to these diverse needs and scalable to handle the increasing number of connected vehicles.
- Resistance to Attacks and Frauds: Authentication systems in VANETs must be robust against various security threats, including impersonation attacks, Sybil attacks, and data manipulation. Designing a system that can effectively counter these threats without imposing excessive computational demands is a significant challenge.
- Architecture of Security for VANET: Our proposed architecture leverages blockchain technology to significantly enhance the security of VANET systems. It provides a robust framework for secure and reliable communication among vehicles.
- Generation of Secure Hashes for Vehicular Interactions: We introduce a novel method for generating secure hashes for each vehicular interaction. This method ensures the integrity and authenticity of the interactions, thereby contributing to a safer and more reliable network.
- Network-Wide Verification and Mitigation of Illegal Activities: Our architecture enables each node in the VANET network to verify the interactions through the generated hashes. This decentralized verification process bolsters the overall security of the system, thereby effectively minimizing the potential for illegal activities.
- Enhanced Security: The architecture significantly elevates the security level in VANETs by leveraging a dual-layer blockchain approach, thereby ensuring the authenticity and integrity of vehicular communications, which is critical for applications like emergency response and traffic management.
- Improved Efficiency: By reducing the observation errors in reputation assessment [24], the system enhances the overall network efficiency, which is crucial for real-time applications such as collision avoidance systems and dynamic traffic light control.
- Scalability: The architecture is designed to be scalable, thus making it capable of accommodating the growing number of connected vehicles and diverse data transactions within VANETs, thereby making it suitable for the expanding scope of smart city projects.
- Section 2 provides a critique of the current solutions and underscores their limitations. This section delves into the myriad of security challenges in VANETs, thereby elucidating the predominant types of attacks that these networks are susceptible to. Additionally, it explores a range of proposed security measures designed to mitigate such attacks, thus presenting an insightful overview of the security landscape in VANETs [25]. In addition, this section offers a detailed taxonomy of the security solutions tailored for VANETs, thereby dissecting various types of security measures that have been proposed. It thoroughly evaluates the advantages and drawbacks of these solutions, thereby providing an extensive guide for researchers and practitioners in the field [26]. These mechanisms include various trust management methods in VANETs, thus elucidating their respective strengths and weaknesses and offering a balanced perspective on the topic [27].
- Section 3 dives into our proposed system, thus offering a detailed overview of the algorithm, methodology, and its unique benefits. It discusses the shortcomings of the existing systems and demonstrates how our proposal effectively addresses them.
- Section 4 provides a comprehensive evaluation of our prototype, thus examining its performance and scalability metrics.
- Section 5 concludes the paper by recapping the key contributions and exploring potential directions for future research.
2. Related Work
2.1. Blockchain Solutions for VANETs, Trust Models, Cyber Attacks, and Mitigation Strategies
- Rapid Change of Context: The fast-paced environment can outpace the PKI’s ability to update and validate certificates, thereby leading to delays or errors in authentication.
- Scalability Concerns: The sheer volume of high-frequency interactions requires a PKI system to handle a significant number of certificate validations within a minimal time frame, which can form a scalability bottleneck.
- Latency in Certificate Revocation: The time-sensitive nature of revoking compromised certificates can be at odds with the quick interaction times, thereby potentially allowing unauthorized access.
- Decentralization: The blockchain operates on a peer-to-peer network that inherently supports the dynamic and decentralized nature of VANETs, thereby facilitating faster and more efficient verifications.
- Immediate Validation: Transactions and communications in a blockchain network can be validated in real time, which aligns well with the high-speed requirements of VANETs.
- Immutable Ledger: The blockchain ledger [36] provides a tamper-proof record of all transactions, including authentications and data exchanges, thereby enhancing trust in vehicular communications.
2.2. Advantages and Benefits of the Proposed Technology
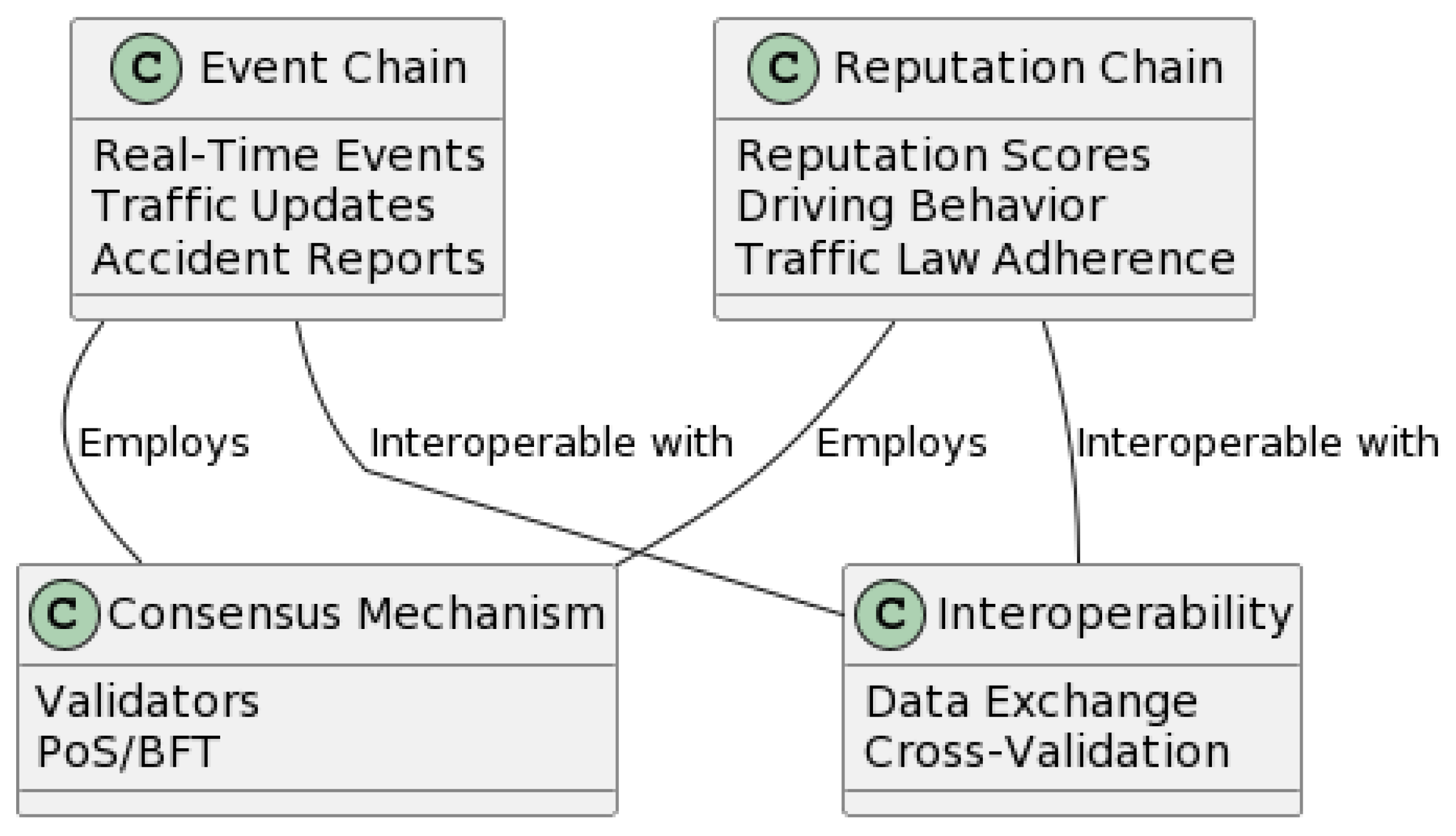
3. Blockchain-Enhanced Security and Operational Efficiency in VANETs
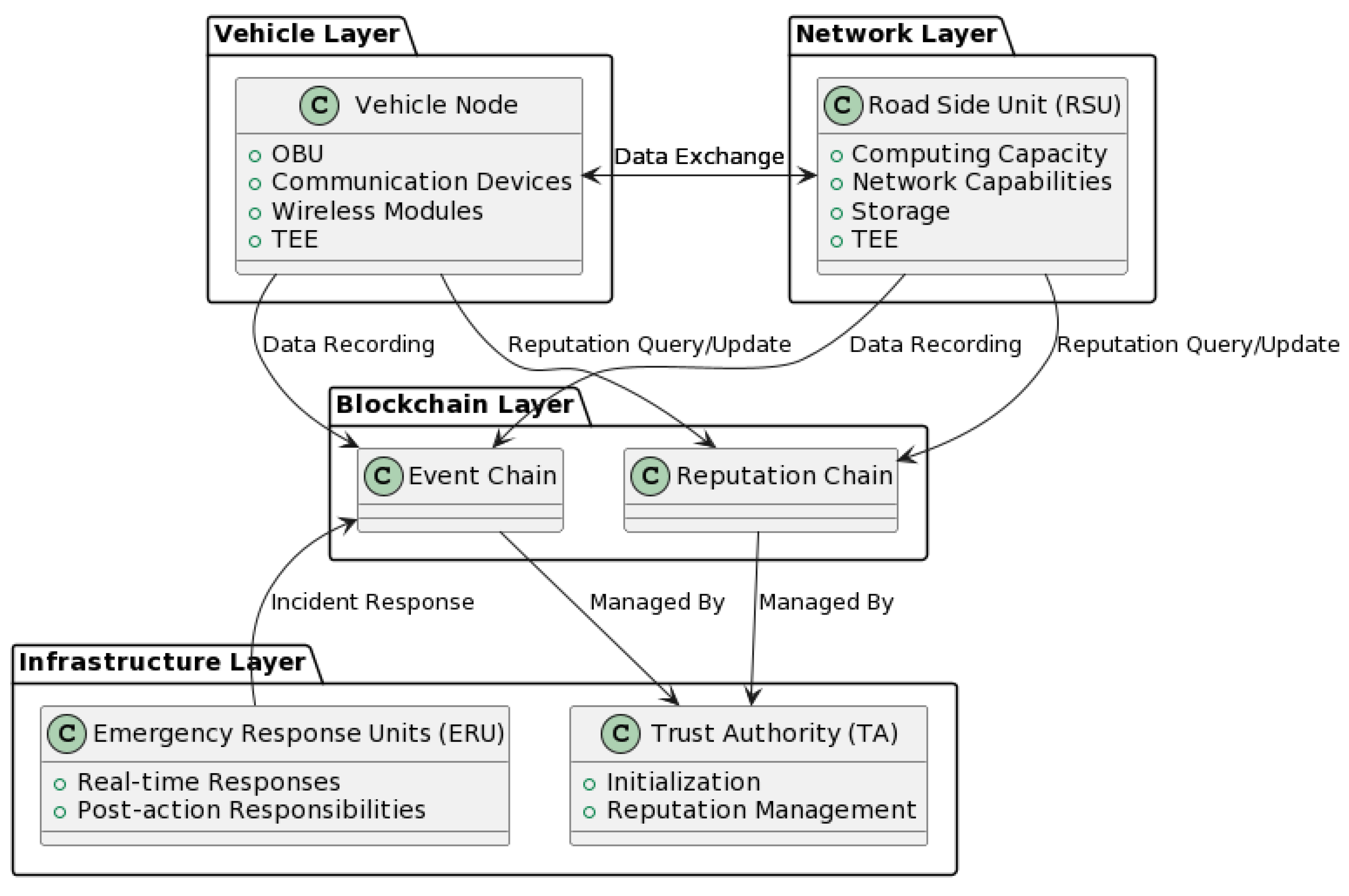
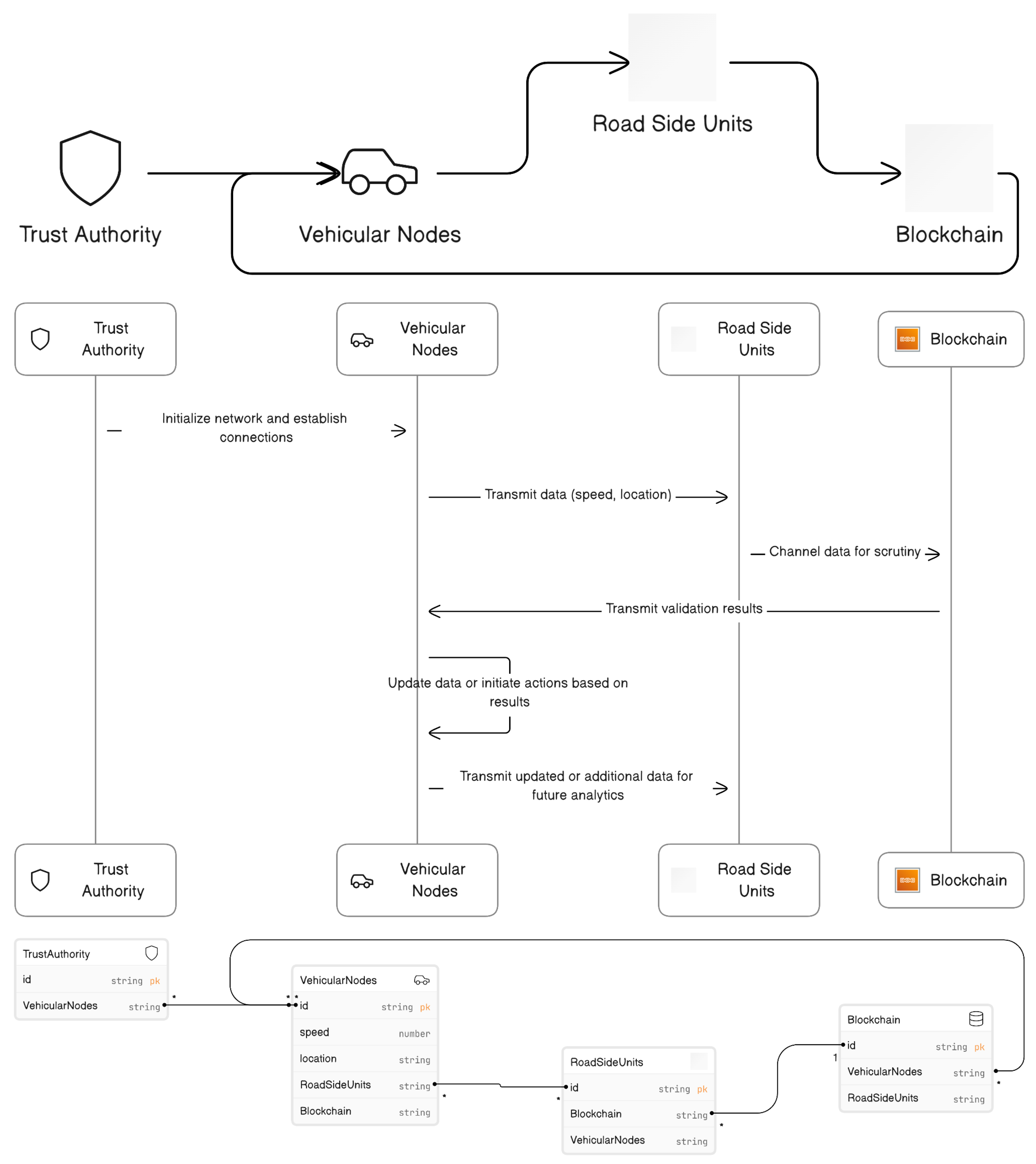
3.1. Architecture Overview
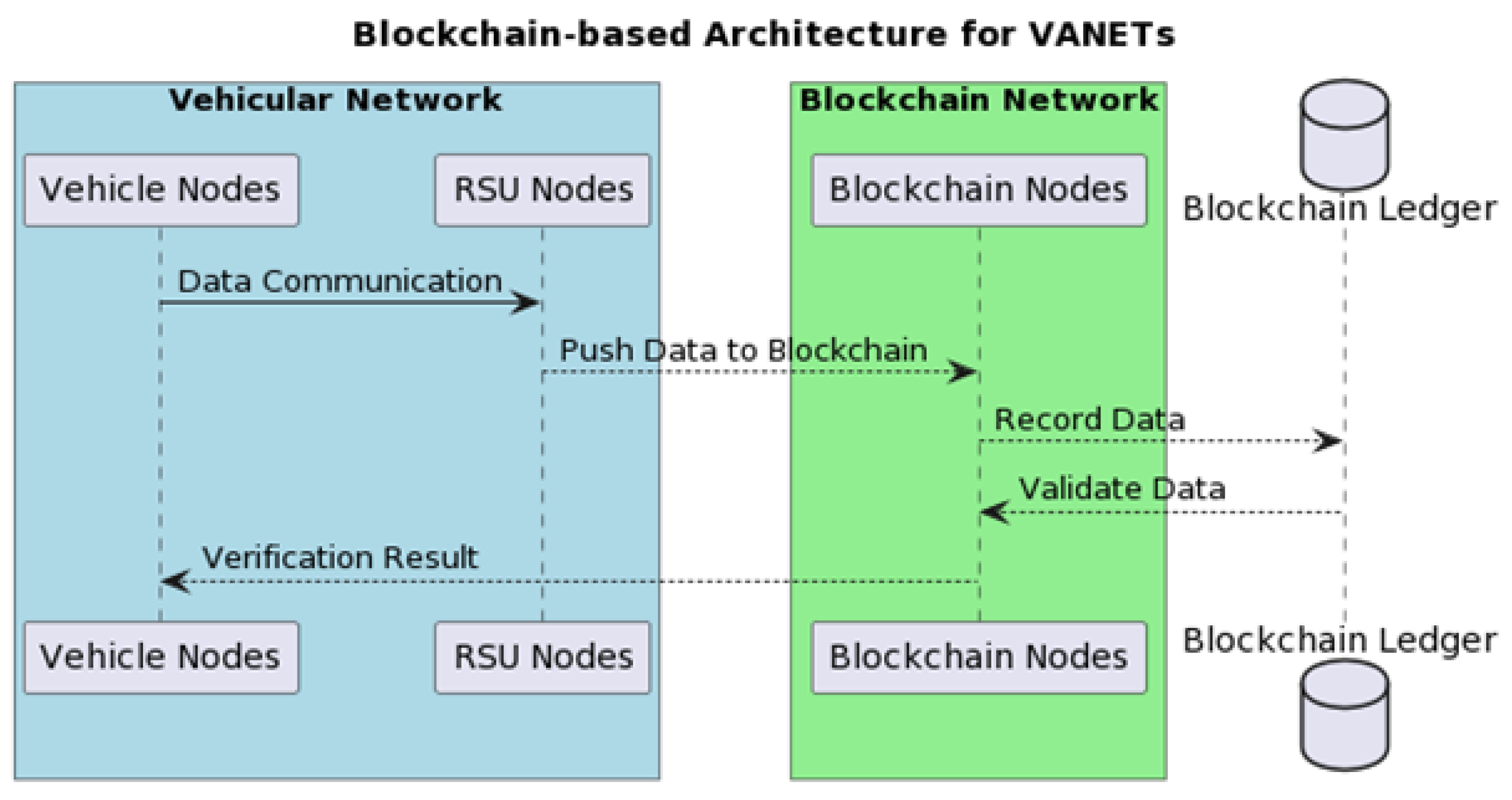
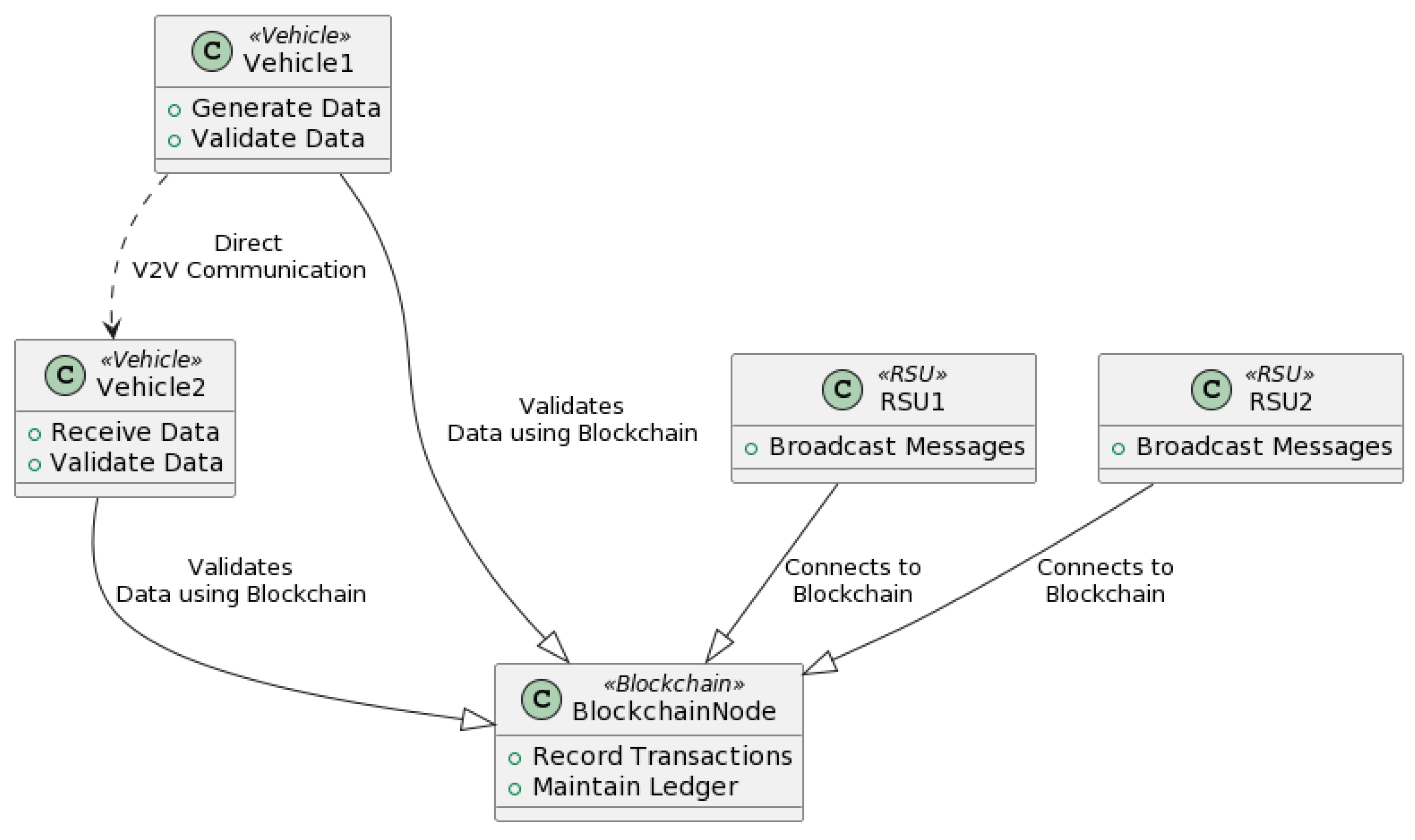
- Vehicle-To-Vehicle (V2V) Validation: When a vehicle receives data from another vehicle, it first performs a basic V2V validation check. This check includes verifying the data signature, expiration date, and consistency with the vehicle’s own knowledge of the world.
- Blockchain-Based Validation: If the data passes the V2V validation check, the vehicle then broadcasts it to the blockchain. The blockchain then performs a global validation check. This check includes verifying that the data have not been previously broadcast and that they are consistent with the data that other vehicles have broadcast to the blockchain.
3.1.1. Vehicle and Network Layer
- Vehicle Node: Vehicles are furnished with an onboard unit (OBU) containing advanced communication devices, wireless transmission modules, and a trusted execution environment (TEE). These vehicles have adequate computational power to perform rudimentary calculations, such as road condition monitoring and trust evaluation based on received data [74,75]. Furthermore, they can partake in blockchain consensus mechanisms and execute queries on the blockchain.
- RSU: RSUs facilitate communication among vehicle nodes within their operational domain. They are endowed with significant computational power, networking capabilities, and ample storage, which are all bolstered by a TEE.
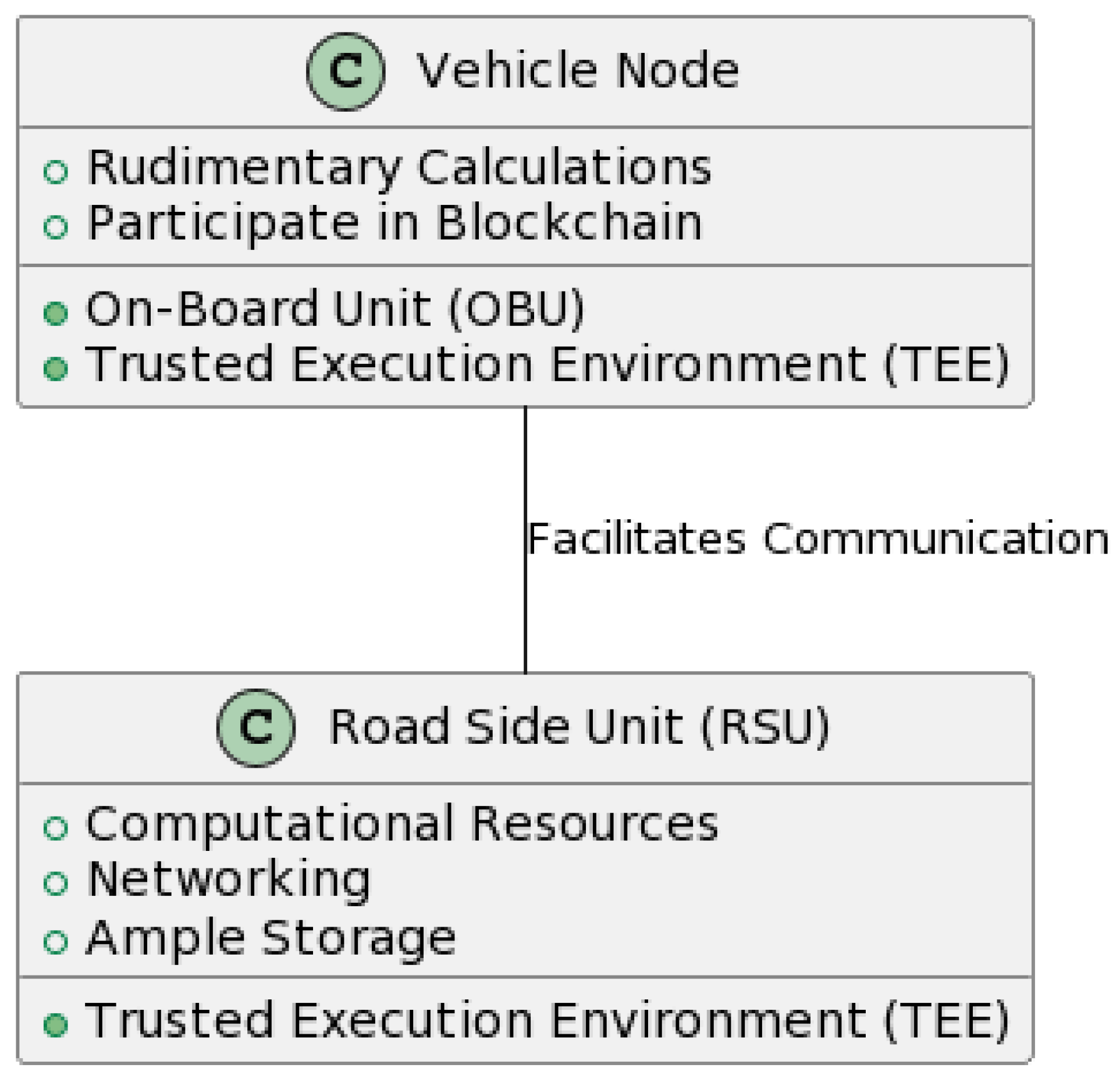
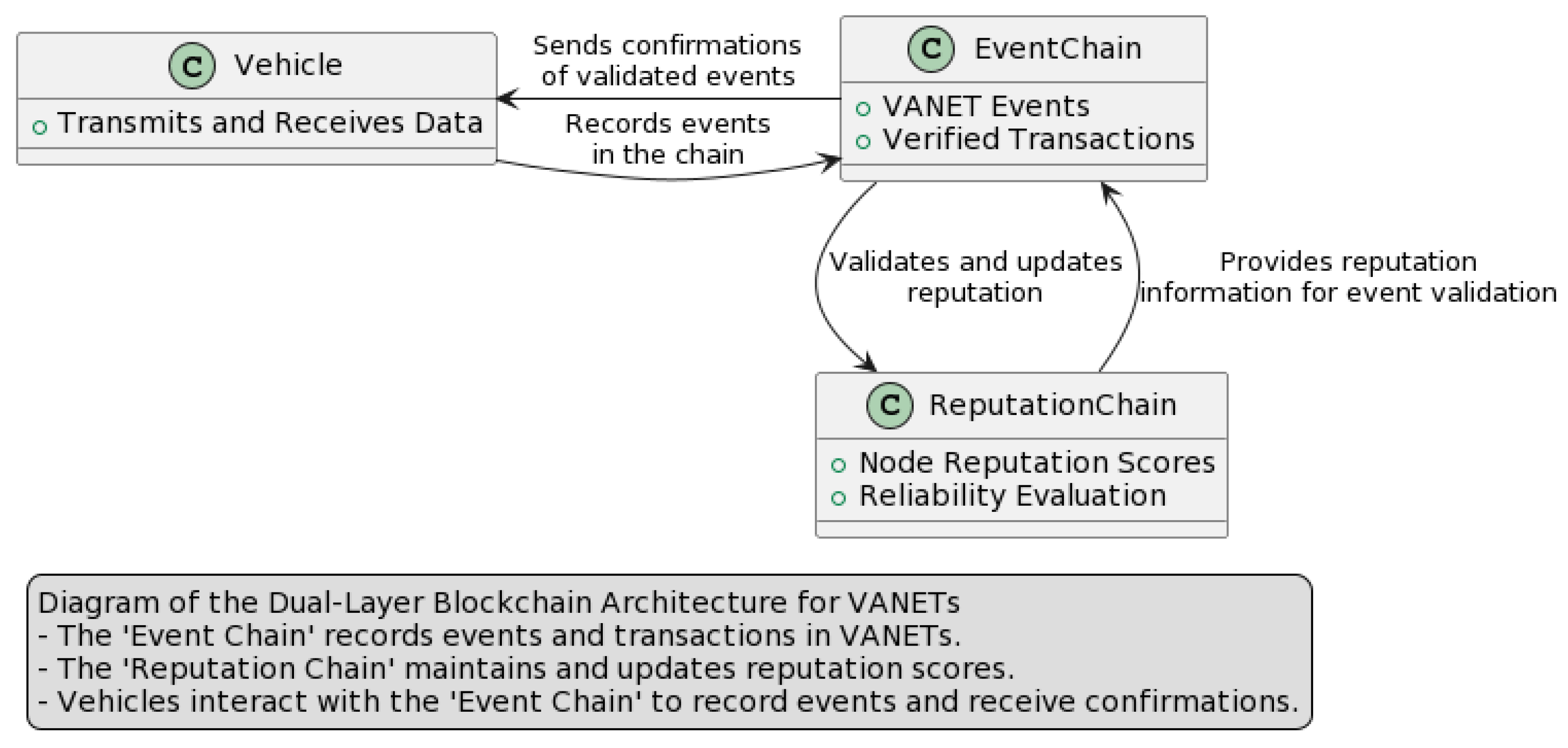
3.1.2. Blockchain Layer
- Optimized Block Generation and Hashing Mechanisms: A cornerstone of our adapted blockchain platform is the optimized block generation protocol. Each vehicular transaction is encapsulated into blocks, which are structured via a consensus algorithm tailored for high-frequency, low-latency vehicular data. The SHA-256 cryptographic hash function is employed to ensure the integrity of these blocks, thus creating an unbreakable chain of data that is resistant to tampering and fraud [19]. The blockchain platform is equipped with an advanced data retrieval system that interfaces seamlessly with the distributed ledger. This system maintains the uprightness of data, with each node validating and mirroring the complete blockchain ledger, thus ensuring the highest level of data veracity and redundancy [11].
- Customized Smart Contracts: To cater to the dynamic nature of VANETs, the blockchain platform incorporates smart contracts designed to automate and streamline vehicular processes such as real-time traffic data sharing, automated toll collection, and vehicular status reporting [9]. These smart contracts execute autonomously, with their conditions predefined by consensus among network participants, thereby enhancing trust [78,79] and efficiency within the network. Our blockchain platform is specifically enhanced to handle the extensive throughput demanded by real-time vehicular communication. It supports rapid transaction processing and block generation, which are crucial for the instantaneous nature of vehicular communications [12].
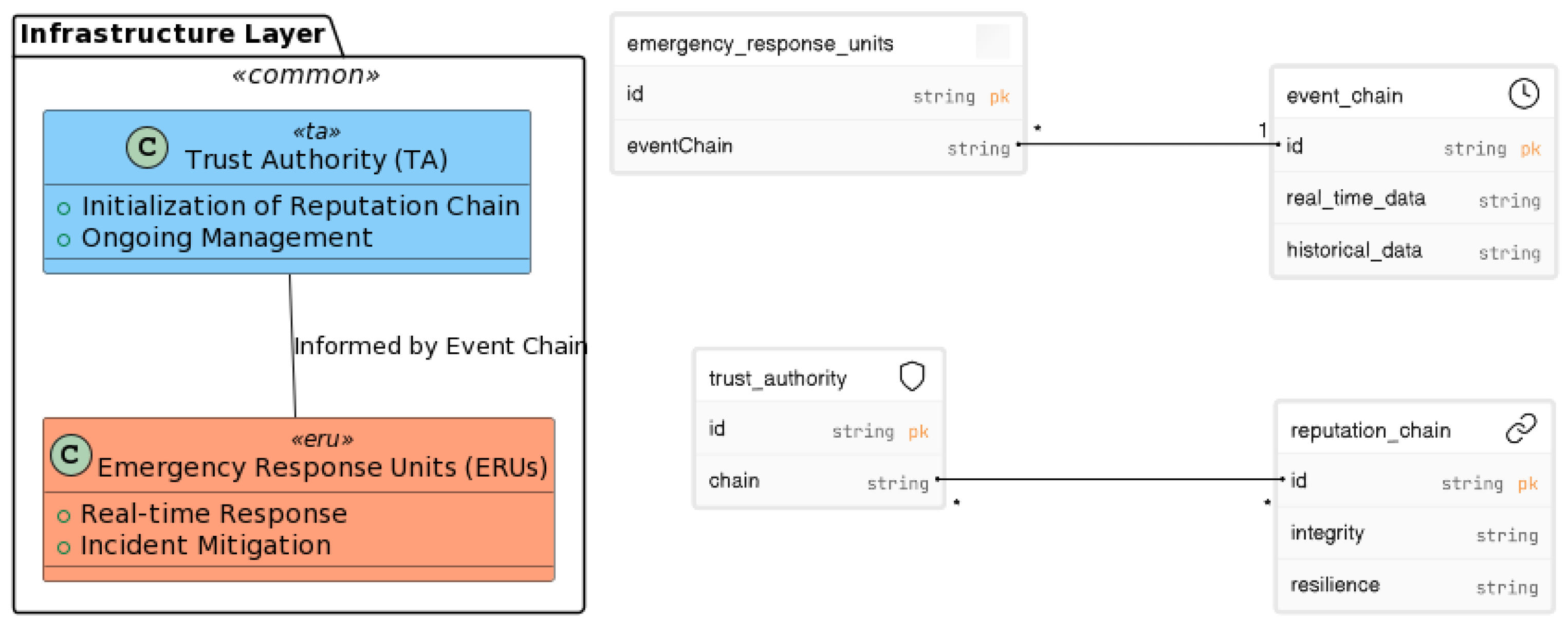
3.1.3. Infrastructure Layer
- Trust Authority (TA): Operating as the architectural cornerstone of the reputation chain, the trust authority is vested with the task of initializing the chain and orchestrating its ongoing management. By so doing, the TA not only assures the chain’s integrity, but also underwrites its resilience against adversarial attacks, thereby fostering a secure and reliable ecosystem for reputation management.
- Emergency Response Units (ERUs): These units serve as indispensable assets in the VANET infrastructure, which are tasked with promptly responding to vehicular incidents based on real-time and historical data. Informed by the event chain, ERUs are capable of executing expeditious countermeasures, as well as formulating postincident strategies to mitigate risk and enhance operational efficiency.
3.2. Reputation Models and Calculation
3.2.1. Reputation Evaluation through a Bayesian Approach
- Historical Data Analysis: The history of a node’s actions and interactions within the VANET plays a pivotal role. This includes data on previous communications, transactions, and behavioral patterns.
- Node Interaction Frequency and Nature: The frequency and nature of a node’s interactions with other nodes are scrutinized. Regular, positive interactions contribute to a higher reputation score.
- Responses from Other Nodes: The feedback or responses that a node receives from others in the network are crucial. Positive endorsements from other reputable nodes can enhance a node’s reputation.
- Recent Behavior Analysis: More recent actions of a node are given greater weight, as they more accurately reflect the node’s current status and intentions.
- Initial Probability Estimation: Each node starts with an initial reputation score based on a predefined trust level.
- Evidence Accumulation: As nodes interact within the VANET, evidence regarding their behavior accumulates. This includes data from the factors mentioned above.
- Probabilistic Updating: The reputation score of a node is updated probabilistically, thereby considering the new evidence. Bayesian inference calculates the posterior probability of a node being trustworthy given the accumulated evidence.
- Dynamic Adaptation: The system continuously adapts the reputation scores based on the latest interactions and feedback, thereby ensuring that the scores are reflective of the current behavior and reliability of the nodes (1). represents the posterior probability of a node being trustworthy given the new evidence. This approach allows for a nuanced and evidence-based reputation management system in VANETs, thus enhancing the overall security and reliability of the network.
3.2.2. Probabilistic Reputation Framework
- signifies the newly updated reputation value.
- represents the aggregated reputation score from the preceding time interval.
- T is the quantified trust metric derived from the event report .
- is a measure that incorporates various social factors affecting trust.
- represents the weighting factors.
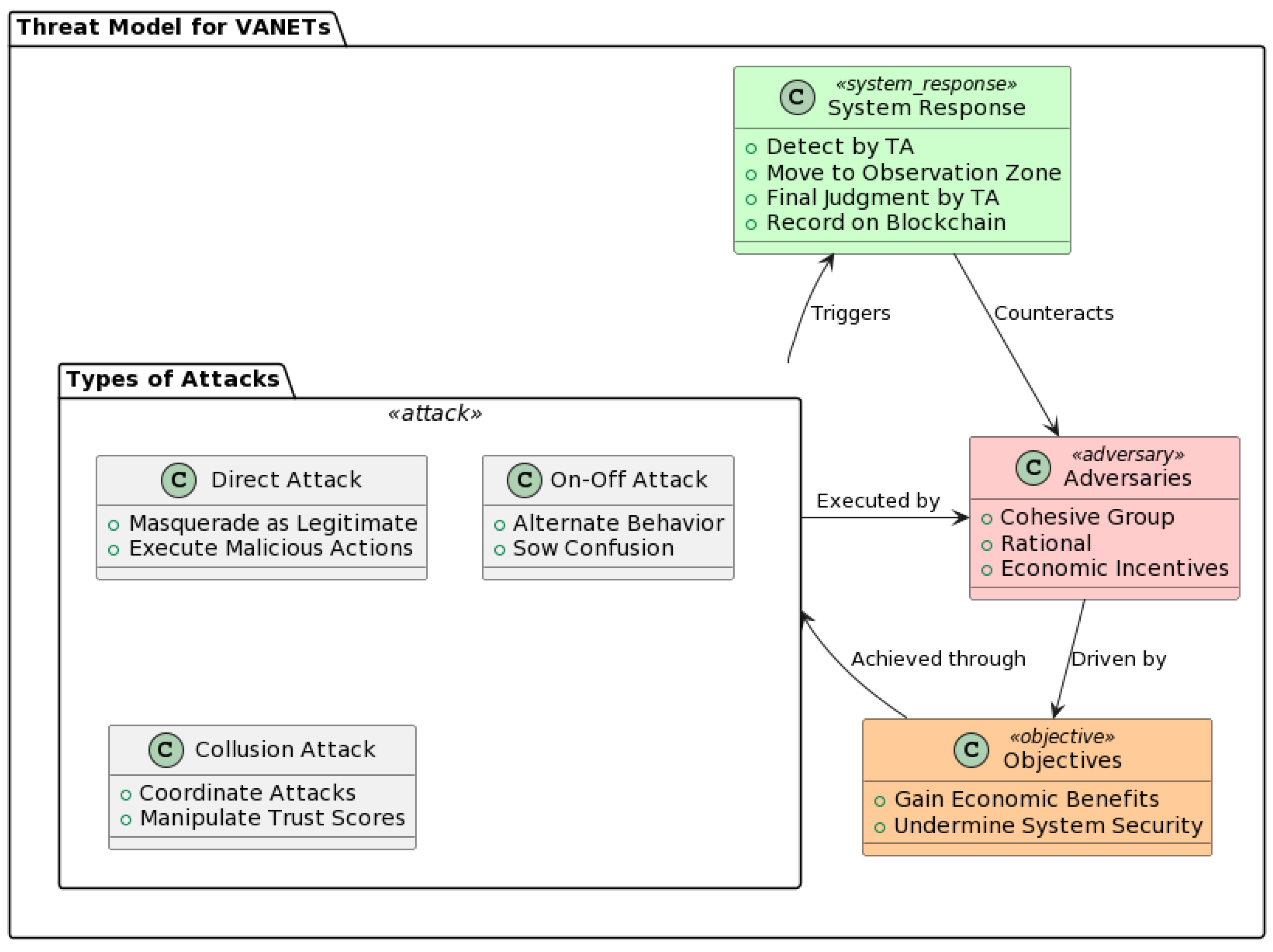
3.3. Threat Model
- Direct Attack: In this scenario, adversaries initially masquerade as legitimate network participants to amass a positive reputation. Upon reaching a critical reputation threshold, they deviate from normative behavior to execute malicious actions. This type of attack poses significant challenges in terms of detection, as the malicious entities maintain a semblance of normalcy for substantial periods.
- On–Off Attack: Here, adversaries alternate between conforming and deviating from expected behavior throughout their activity cycles. Such erratic conduct aims to sow confusion among other network participants, including roadside units (RSUs). Although less covert than direct attacks, the on–off modality presents its own set of detection challenges due to its intermittent nature.
- Collusion Attack: In its most insidious form, multiple adversaries collaborate to launch coordinated attacks against specific targets or events. Their tactics may involve manipulating trust scores, not only by artificially lowering the scores of genuine nodes, but also by inflating trust metrics within the colluding group. The orchestrated nature of these attacks makes them particularly difficult to detect and counter.
3.4. System Operational Behavior
- Network Initiation and Trust Configuration: The trust authority, an overarching entity vested with the authority to oversee the issuance and management of cryptographic keys and credentials, orchestrates the foundational phase of the VANET’s operation. It meticulously authenticates the vehicular nodes and establishes encrypted communication conduits, thereby underpinning a secure operational milieu. In the initialization phase, vehicular nodes entering the network for the first time are mandated to communicate their identifying credentials to the trust authority (TA). Upon successfully verifying the provided information, the TA responds by issuing a pseudonym and a corresponding digital certificate to the vehicular node. Furthermore, it generates a public–private cryptographic key pair using elliptic curve cryptography. All these constituents collectively facilitate the formal registration of the vehicle’s identity within the system. This comprehensively assembled information is then immutably recorded in the blockchain ledger in the form of a cryptographic transaction.
- Vehicular Data Dissemination: The vehicular nodes, epitomizing the network’s mobile units, collate an array of pertinent data. Subsequently, these nodes disseminate the amassed data to the strategically positioned roadside units (RSUs), thus facilitating a confluence of vehicular information streams.
- Data Collection by RSUs: The RSUs, stationed as pivotal nodal points within the network, aggregate vehicular data. They act as intermediaries that channel the vehicular data into the Blockchain stratum, thereby ensuring the data’s subsequent validation and indelible recording.
- Blockchain Data Verification: Upon acquisition of the data, the blockchain infrastructure executes a stringent validation protocol. Leveraging the prowess of advanced consensus algorithms and the automation afforded by smart contracts, the infrastructure meticulously ascertains the data’s veracity and integrity.
- Validation Response to Vehicular Nodes: Consequent to the Blockchain’s validation process, the vehicular nodes receive feedback. This feedback, indicative of the blockchain’s scrutiny, prompts the nodes to refine their data reporting protocols in alignment with the validation outcomes.
- Ongoing Data Procurement: In a perpetual state of vigilance, the RSUs persist in their endeavor to procure updated vehicular data. This unceasing data acquisition undergirds a spectrum of analytical and decision-making paradigms, which is quintessential for the holistic management of vehicular dynamics. The ongoing activities of the vehicular nodes within the network can be segmented into four major categories:
- (a)
- Event Observation: Upon detecting a relevant event, the vehicular node captures the pertinent information and relays it to the nearest roadside unit (RSU). The RSU, in turn, disseminates this information to proximal vehicular nodes for further observation and verification.
- (b)
- Observation Report Generation: Vehicles then produce observational reports by integrating multivariable data, which are normalized through cosine similarity measures. The direct trust score is subsequently inferred using Bayesian statistical methods.
- (c)
- Trust Exchange: Nodes within the network partake in cooperative communication to exchange direct trust metrics, which are then construed as indirect trust indicators.
- (d)
- Composite Trust Calculation: The cumulative trust level of a target vehicle is calculated by assimilating both the direct and indirect trust metrics.
On the other hand, RSUs within the network are responsible for two main functions:- (a)
- Query and Verification: Upon receipt of an event observation report from a vehicular node, the RSU engages in rigorous data queries and verification protocols.
- (b)
- Reputation Value Recalculation: Once the trust scores are received from the cooperative vehicular nodes, the RSU consults the historical reputation and social trust of the target vehicle stored in the reputation blockchain. The new comprehensive reputation score is then calculated through weighted integration.
3.5. Invalid or Fraudulent Data Management
- Immediacy in Decision Making: The high-stakes nature of VANETs demands a system architecture that supports split-second decision making. The storage of invalid data could introduce latency that is antithetical to the need for prompt response times, thereby potentially affecting the safety-critical functions of the network.
- Strategic Data Storage Management: The sheer scale of data generated by vehicles and infrastructure in VANETs necessitates a selective approach to data retention. Our strategy prioritizes the storage of authentic and operationally pertinent data to ensure the optimal use of finite storage capabilities.
- Enhancement of Network Throughput: The exclusion of invalid data from storage is also a strategic decision to maximize network throughput. This ensures that network bandwidth is conserved for the transmission and processing of legitimate and relevant data, thereby enhancing network performance.
- Mitigation of Security Threats: The potential exploitation of stored invalid data by nefarious actors cannot be overlooked. Our proactive approach to discard such data immediately serves as a deterrent to the execution of security exploits that could compromise network integrity.
3.5.1. Special Cases: Node Disconnection and Re-Entry
3.5.2. Special Cases: Blockchains in Fraud Recognition in VANETs
4. Experiments and Results: Performance Analysis
4.1. An Overview of Network Simulator ns-3 Validation Suite
4.2. Experimental Methodology: ns-3 Simulations
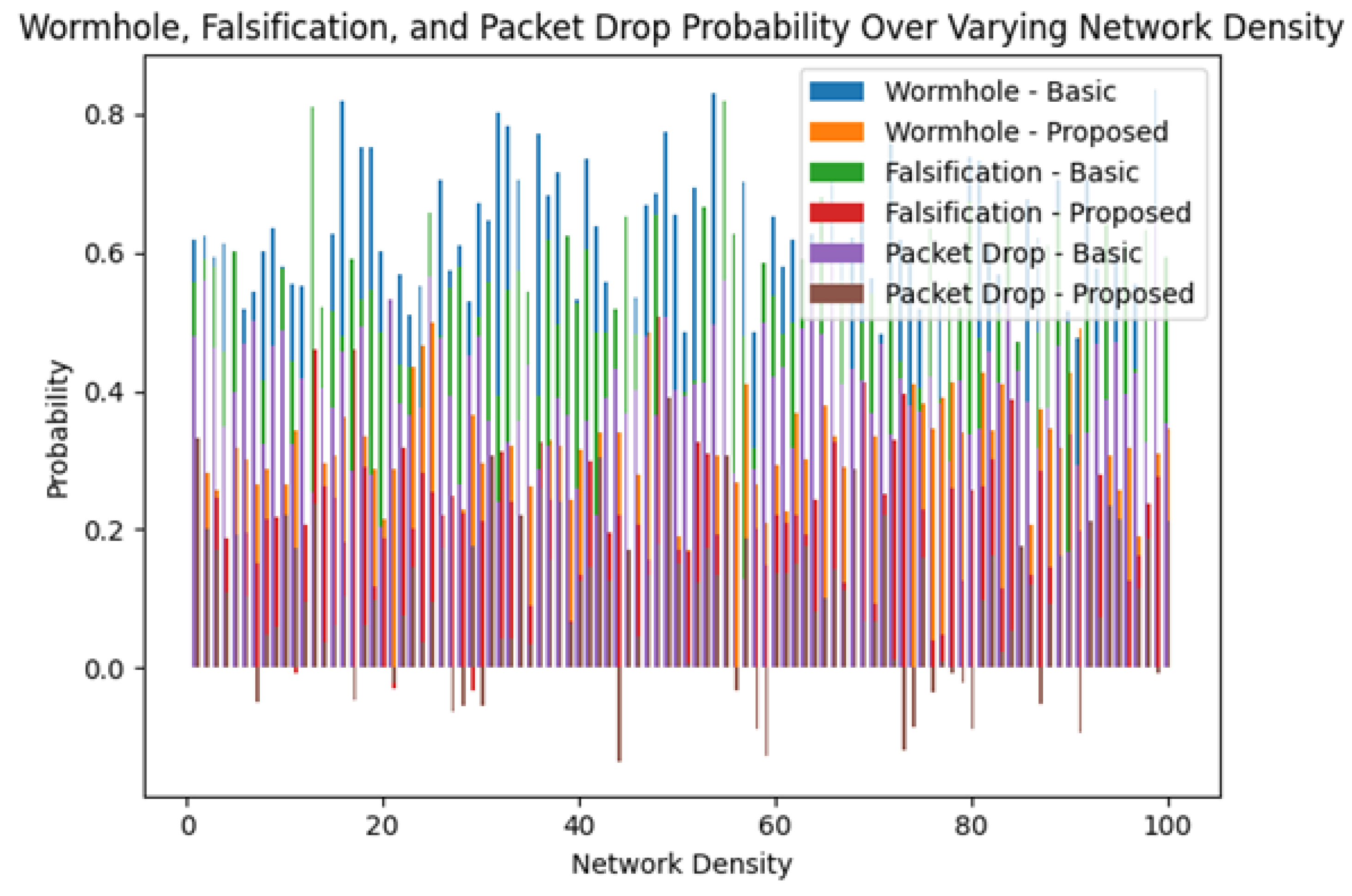
- The probability of successful detection of falsification assaults: This metric quantifies the system’s ability to identify and prevent counterfeit information from being injected into the network.
- The probability of successful detection of wormhole intrusions: This metric assesses the system’s effectiveness in detecting and thwarting clandestine tunnels that manipulate the spatial distribution of network traffic.
- The probability of successful detection of packet dropping attacks: This metric evaluates the system’s capability in recognizing and mitigating malicious node behavior that involves intentionally discarding incoming packets.
- The average latency under various attack scenarios: This metric measures the impact of different attack types on the network’s latency performance.
- Falsification Assaults: In this adversarial model, the compromised node injects counterfeit information into the network. Our framework incorporates advanced cryptographic verification procedures, thus elevating the likelihood of detecting such disinformation campaigns.
- Wormhole Intrusions: Here, an adversarial node may craft a clandestine tunnel, thereby manipulating the spatial distribution of network traffic. To counteract such illicit activities, our architecture integrates spatiotemporal analytics that facilitate the timely detection of unauthorized tunneling mechanisms.
- Packet-Dropping Attacks: This type of attack represents a more surreptitious but equally pernicious threat, where a malicious node intentionally discards incoming packets. Such actions contribute to data loss and degraded network performance.
Simulation Setup
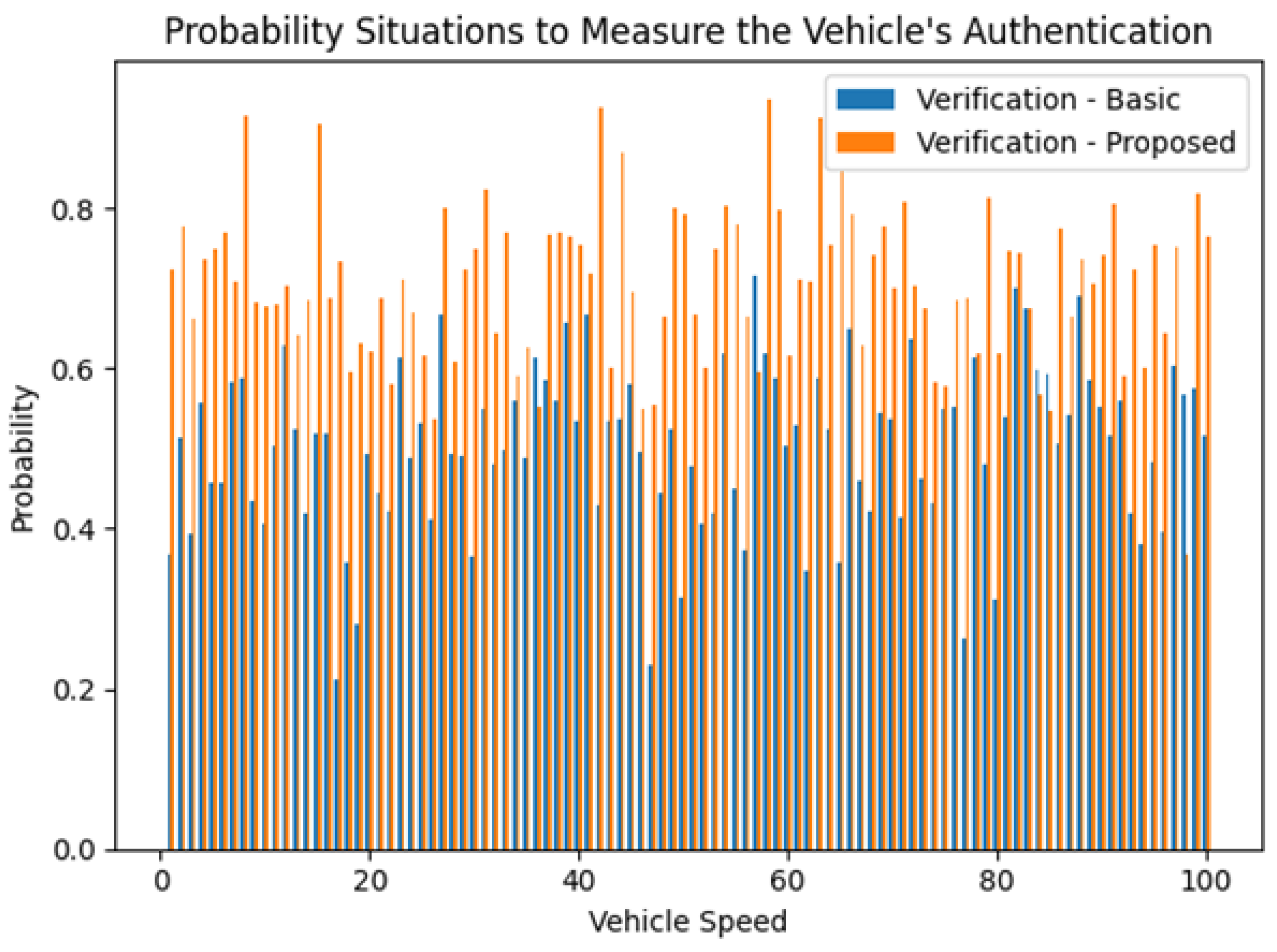
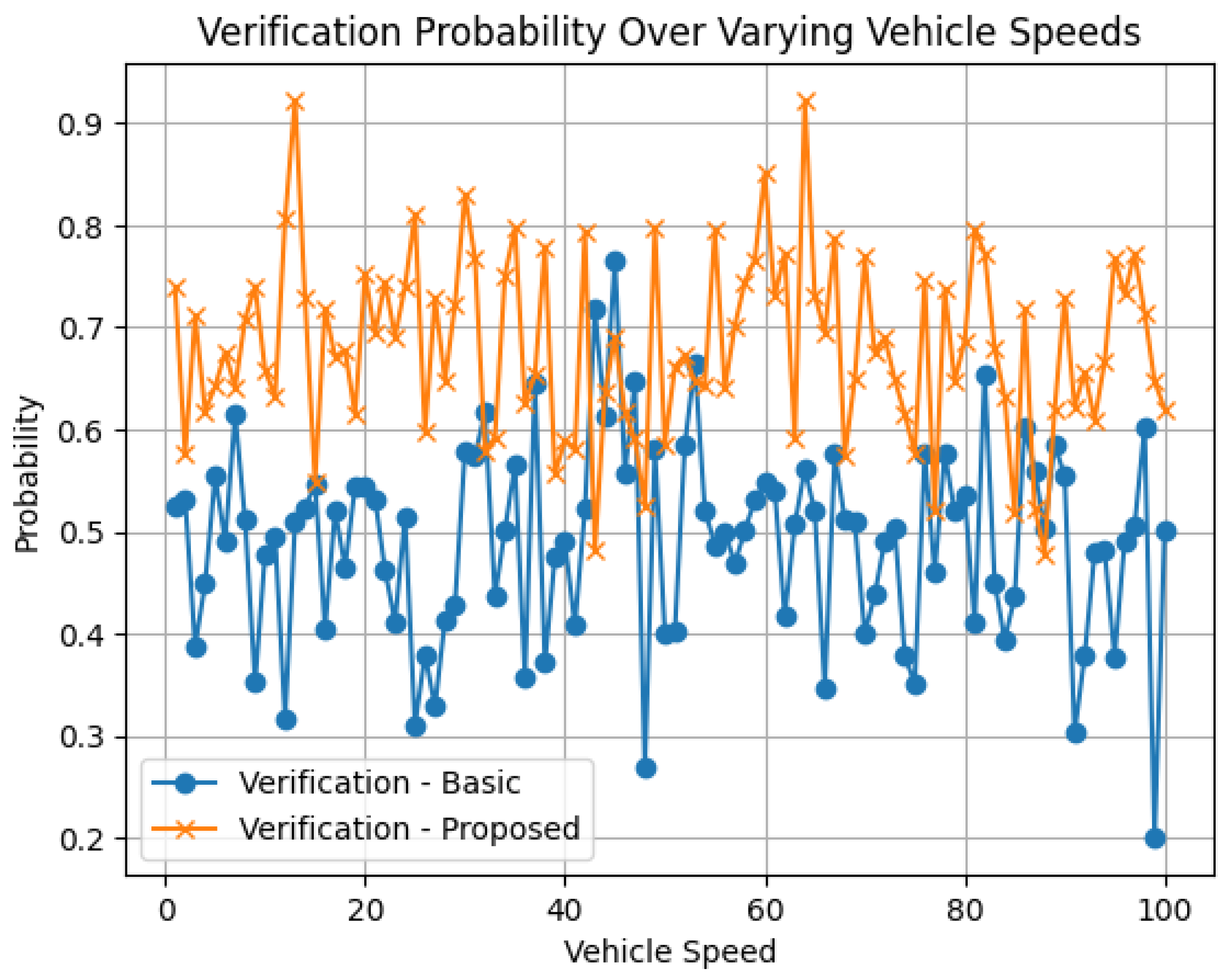
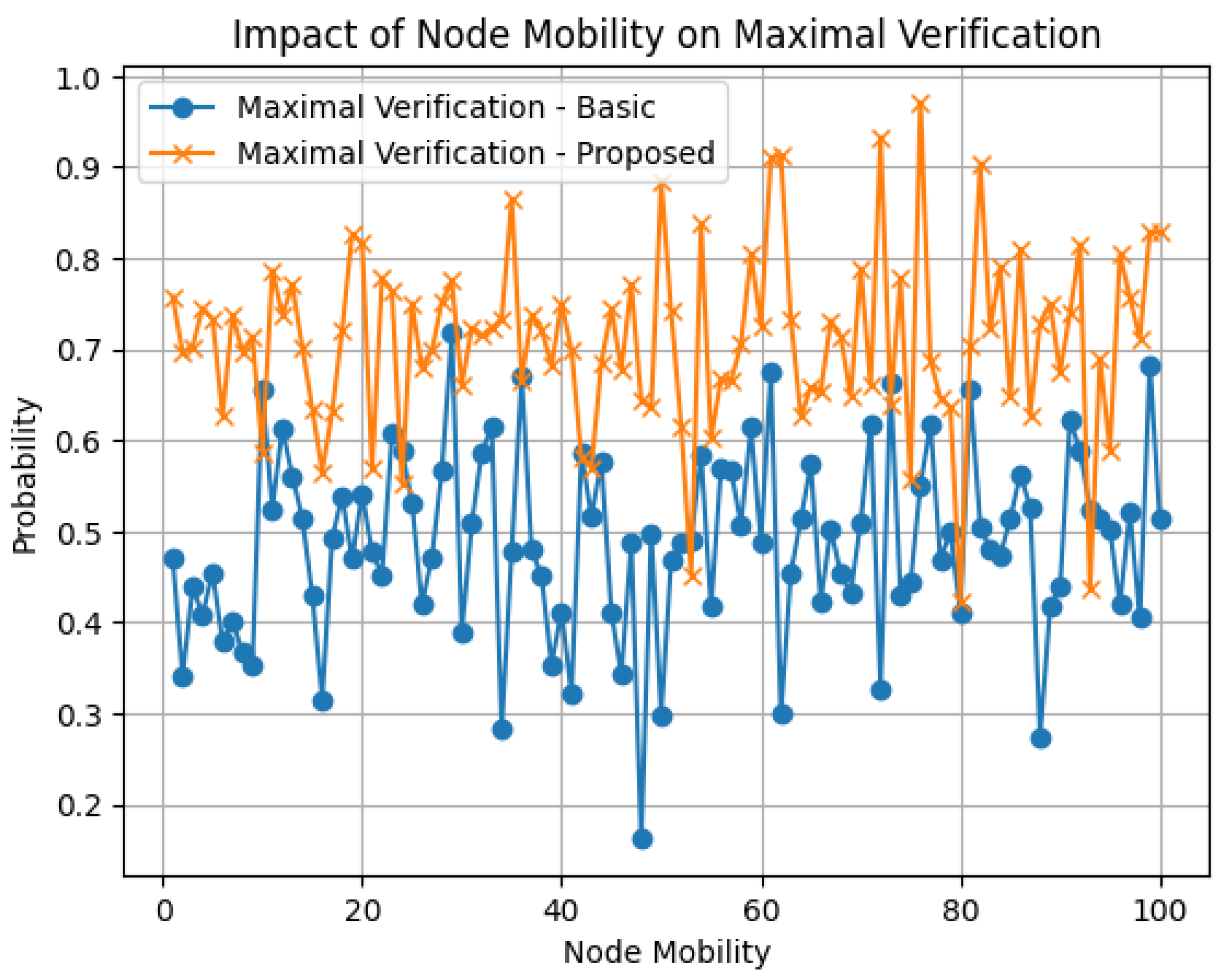
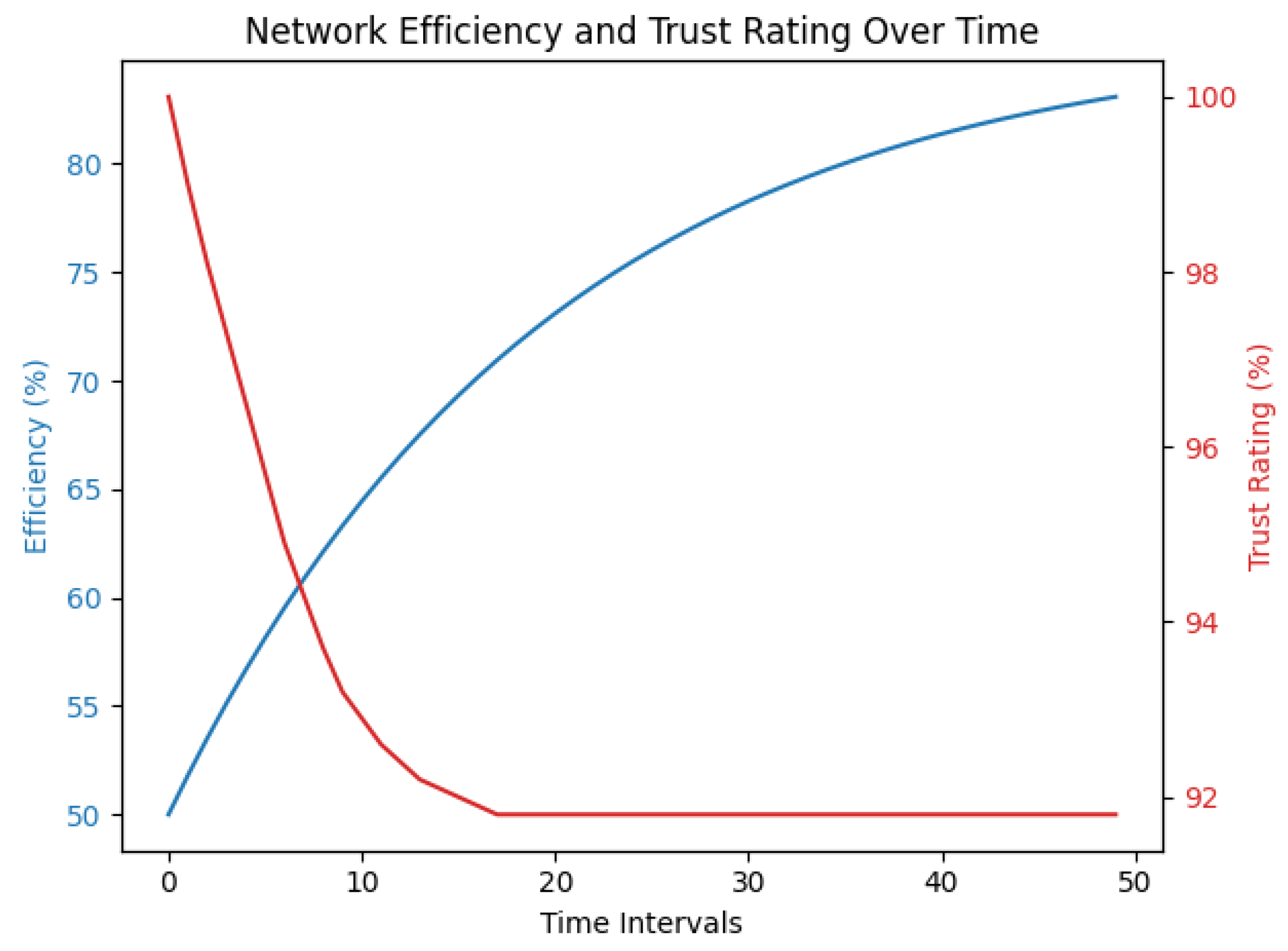
4.3. Simulation Results
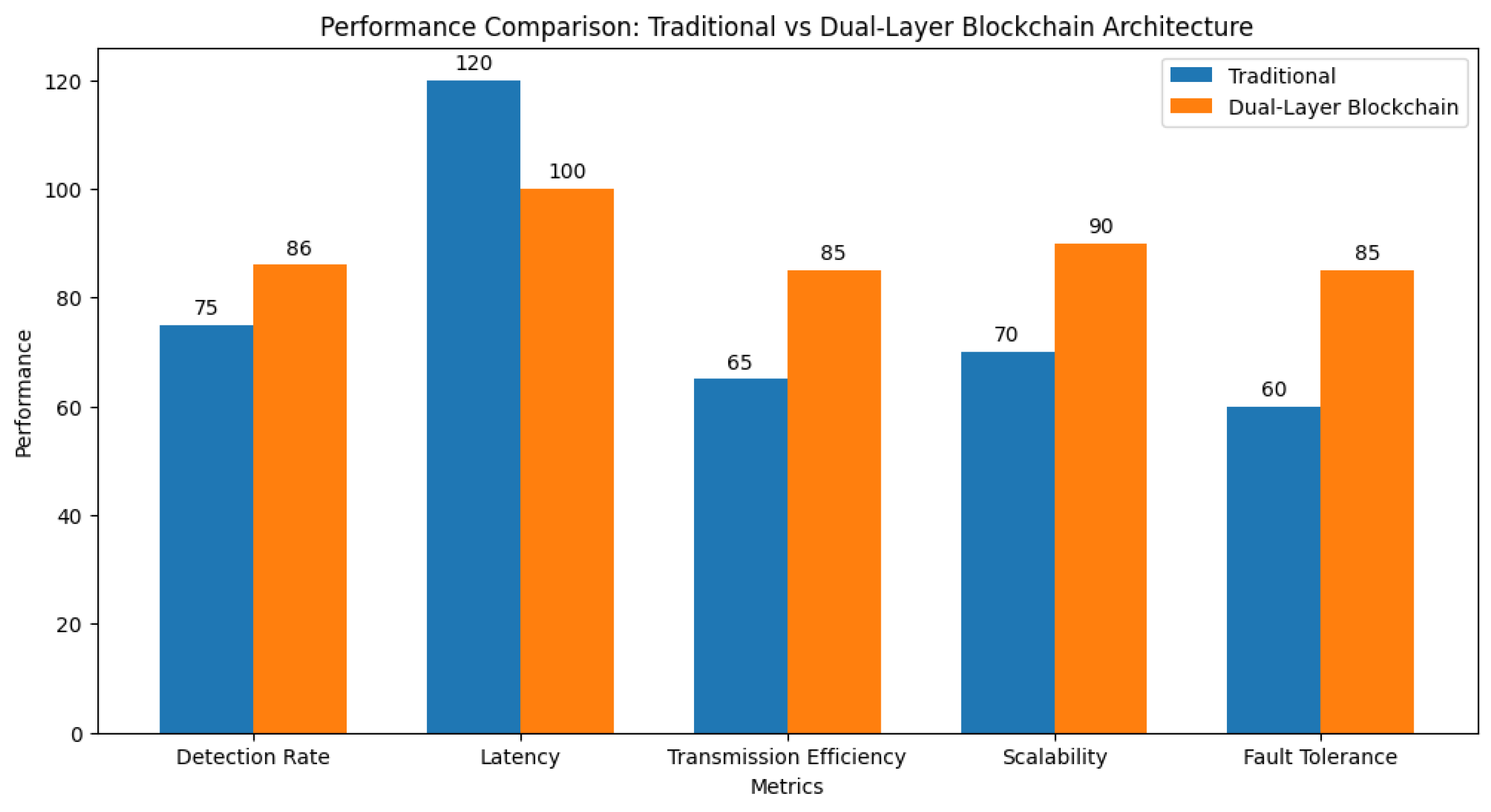
4.3.1. In-Depth Comparative Analysis of Dual-Layer Blockchain versus Traditional VANET Architectures: A Quantitative Performance Evaluation
4.3.2. Discussions: Real-World Applicability, Scalability, and Privacy Concerns
5. Conclusions and Future Work
- Latency: The latency measurements underscore a remarkable reduction, thereby substantially enhancing the responsiveness of vehicular communication channels.
- Jitter: The measured jitter remained within the confines of operational tolerance, thus reinforcing the reliability and stability of the vehicular network.
- Packet Delivery Ratio (PDR): A superior PDR, eclipsing the 95th percentile, affirms the robustness of the data transmission protocols under our blockchain-enabled regime.
- Energy Efficiency: The framework’s commendable energy efficiency metrics herald a new epoch of sustainable VANET architectures, thereby paving the way for greener intelligent transportation systems.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Menouar, H.; Guvenc, I.; Akkaya, K.; Uluagac, A.S.; Kadri, A.; Tuncer, A. UAV-enabled intelligent transportation systems for the smart city: Applications and challenges. IEEE Commun. Mag. 2017, 55, 22–28. [Google Scholar] [CrossRef]
- Asra, S.A. Security Issues of Vehicular Ad Hoc Networks (VANET): A Systematic Review. TIERS Inf. Technol. J. 2022, 3, 17–27. [Google Scholar] [CrossRef]
- Afzal, Z.; Kumar, M. Security of vehicular ad-hoc networks (VANET): A survey. J. Phys. Conf. Ser. 2020, 1427, 012015. [Google Scholar] [CrossRef]
- Sweeney, L. k-anonymity: A model for protecting privacy. Int. J. Uncertain. Fuzziness Knowl.-Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Li, R.; Song, T.; Mei, B.; Li, H.; Cheng, X.; Sun, L. Blockchain for large-scale internet of things data storage and protection. IEEE Trans. Serv. Comput. 2018, 12, 762–771. [Google Scholar] [CrossRef]
- Wang, L.; Zheng, D.; Guo, R.; Hu, C.; Jing, C. A blockchain-based privacy-preserving authentication scheme with anonymous identity in vehicular networks. Int. J. Netw. Secur. 2020, 22, 981–990. [Google Scholar]
- Wang, X.; Xu, C.; Zhou, Z.; Yang, S.; Sun, L. A survey of blockchain-based cybersecurity for vehicular networks. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 740–745. [Google Scholar]
- Diallo, E.H.; Dib, O.; Al Agha, K. A scalable blockchain-based scheme for traffic-related data sharing in VANETs. Blockchain Res. Appl. 2022, 3, 100087. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Guan, Y.L.; Yuen, C.; Sun, S.; Lam, K.-Y.; Koh, L.H. Blockchain for the internet of vehicles towards intelligent transportation systems: A survey. IEEE Internet Things J. 2020, 8, 4157–4185. [Google Scholar] [CrossRef]
- Mikavica, B.; Kostić-Ljubisavljević, A. Blockchain-based solutions for security, privacy, and trust management in vehicular networks: A survey. J. Supercomput. 2021, 77, 9520–9575. [Google Scholar] [CrossRef]
- Javaid, U.; Aman, M.N.; Sikdar, B. DrivMan: Driving trust management and data sharing in VANETS with blockchain and smart contracts. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–5. [Google Scholar]
- Yeh, L.Y.; Shen, N.X.; Hwang, R.H. Blockchain-based privacy-preserving and sustainable data query service over 5g-vanets. IEEE Trans. Intell. Transp. Syst. 2022, 23, 15909–15921. [Google Scholar] [CrossRef]
- Guehguih, B.; Lu, H. Blockchain-based privacy-preserving authentication and message dissemination scheme for vanet. In Proceedings of the 2019 5th International Conference on Systems, Control and Communications, Wuhan, China, 21–23 December 2019; pp. 16–21. [Google Scholar]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. An efficient and anonymous blockchain-based data sharing scheme for vehicular networks. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar]
- Guo, Z.; Wang, G.; Li, Y.; Ni, J.; Du, R.; Wang, M. Accountable Attribute-Based Data-Sharing Scheme Based on Blockchain for Vehicular Ad Hoc Network. IEEE Internet Things J. 2022, 10, 7011–7026. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. Secure authentication and key management with blockchain in VANETs. IEEE Access 2019, 8, 2482–2498. [Google Scholar] [CrossRef]
- Xie, L.; Ding, Y.; Yang, H.; Wang, X. Blockchain-based secure and trustworthy Internet of Things in SDN-enabled 5G-VANETs. IEEE Access 2019, 7, 56656–56666. [Google Scholar] [CrossRef]
- Joshi, G.P.; Perumal, E.; Shankar, K.; Tariq, U.; Ahmad, T.; Ibrahim, A. Toward blockchain-enabled privacy-preserving data transmission in cluster-based vehicular networks. Electronics 2020, 9, 1358. [Google Scholar] [CrossRef]
- Li, B.; Liang, R.; Zhu, D.; Chen, W.; Lin, Q. Blockchain-based trust management model for location privacy preserving in VANET. IEEE Trans. Intell. Transp. Syst. 2020, 22, 3765–3775. [Google Scholar] [CrossRef]
- Mokhtar, B.; Azab, M. Survey on security issues in vehicular ad hoc networks. Alex. Eng. J. 2015, 54, 1115–1126. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Yan, K.; Zeng, P.; Wang, K.; Ma, W.; Zhao, G.; Ma, Y. Reputation consensus-based scheme for information sharing in internet of vehicles. IEEE Trans. Veh. Technol. 2023, 72, 13631–13636. [Google Scholar] [CrossRef]
- Malhi, A.K.; Batra, S.; Pannu, H.S. Security of vehicular ad-hoc networks: A comprehensive survey. Comput. Secur. 2020, 89, 101664. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Abdullah, A.H.; Hassan, W.H.; Anisi, M.H.; Goudarzi, S.; Rezazadeh Baee, M.A.; Mandala, S. Trust management in vehicular ad hoc network: A systematic review. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 146. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Das, A.K.; Leung, M.T.; Choo, K.K.R.; Vollala, S. Blockchain-based vehicular ad-hoc networks: A comprehensive survey. Ad Hoc Netw. 2022, 137, 102980. [Google Scholar] [CrossRef]
- Zhang, J.; Zheng, K.; Zhang, D.; Yan, B. AATMS: An anti-attack trust management scheme in VANET. IEEE Access 2020, 8, 21077–21090. [Google Scholar] [CrossRef]
- Eziama, E.; Tepe, K.; Balador, A.; Nwizege, K.S.; Jaimes, L.M. Malicious node detection in vehicular ad-hoc network using machine learning and deep learning. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Sheikh, M.S.; Liang, J.; Wang, W. A survey of security services, attacks, and applications for vehicular ad hoc networks (vanets). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef]
- Sedar, R.; Kalalas, C.; Vázquez-Gallego, F.; Alonso, L.; Alonso-Zarate, J. A comprehensive survey of v2x cybersecurity mechanisms and future research paths. IEEE Open J. Commun. Soc. 2023, 4, 325–391. [Google Scholar] [CrossRef]
- Yu, R.; Kang, J.; Huang, X.; Xie, S.; Zhang, Y.; Gjessing, S. MixGroup: Accumulative pseudonym exchanging for location privacy enhancement in vehicular social networks. IEEE Trans. Dependable Secur. Comput. 2015, 13, 93–105. [Google Scholar] [CrossRef]
- Lo, N.W.; Tsai, J.L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans. Intell. Transp. Syst. 2015, 17, 1319–1328. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 October 2023).
- Zou, S.; Xi, J.; Wang, S.; Lu, Y.; Xu, G. Reportcoin: A novel blockchain-based incentive anonymous reporting system. IEEE Access 2019, 7, 65544–65559. [Google Scholar] [CrossRef]
- Yuan, Y.; Wang, F.Y. Towards blockchain-based intelligent transportation systems. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 2663–2668. [Google Scholar]
- Li, W.; Song, H. ART: An attack-resistant trust management scheme for securing vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2015, 17, 960–969. [Google Scholar] [CrossRef]
- Ahmad, F.; Kurugollu, F.; Kerrache, C.A.; Sezer, S.; Liu, L. Notrino: A novel hybrid trust management scheme for internet-of-vehicles. IEEE Trans. Veh. Technol. 2021, 70, 9244–9257. [Google Scholar] [CrossRef]
- Oubabas, S.; Aoudjit, R.; Rodrigues, J.J.; Talbi, S. Secure and stable vehicular ad hoc network clustering algorithm based on hybrid mobility similarities and trust management scheme. Veh. Commun. 2018, 13, 128–138. [Google Scholar] [CrossRef]
- Yang, Q.; Wang, H. Toward trustworthy vehicular social networks. IEEE Commun. Mag. 2015, 53, 42–47. [Google Scholar] [CrossRef]
- Siddiqui, S.A.; Mahmood, A.; Zhang, W.E.; Sheng, Q.Z. Machine learning based trust model for misbehaviour detection in internet-of-vehicles. In Proceedings of the Neural Information Processing: 26th International Conference, ICONIP 2019, Sydney, NSW, Australia, 12–15 December 2019; pp. 512–520. [Google Scholar]
- Fang, W.; Zhang, W.; Liu, Y.; Yang, W.; Gao, Z. BTDS: Bayesian-based trust decision scheme for intelligent connected vehicles in VANETs. Trans. Emerg. Telecommun. Technol. 2020, 31, e3879. [Google Scholar] [CrossRef]
- Halabi, T.; Zulkernine, M. Trust-based cooperative game model for secure collaboration in the internet of vehicles. In Proceedings of the ICC 2019–2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Raya, M.; Papadimitratos, P.; Gligor, V.D.; Hubaux, J.P. On data-centric trust establishment in ephemeral ad hoc networks. In Proceedings of the IEEE INFOCOM 2008-The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1238–1246. [Google Scholar]
- Mármol, F.G.; Pérez, G.M. TRIP, a trust and reputation infrastructure-based proposal for vehicular ad hoc networks. J. Netw. Comput. Appl. 2012, 35, 934–941. [Google Scholar] [CrossRef]
- Guleng, S.; Wu, C.; Chen, X.; Wang, X.; Yoshinaga, T.; Ji, Y. Decentralized trust evaluation in vehicular Internet of Things. IEEE Access 2019, 7, 15980–15988. [Google Scholar] [CrossRef]
- Xu, S.; Guo, C.; Hu, R.Q.; Qian, Y. Blockchain-inspired secure computation offloading in a vehicular cloud network. IEEE Internet Things J. 2021, 9, 14723–14740. [Google Scholar] [CrossRef]
- Zhang, H.; Bian, X.; Xu, Y.; Xiang, S.; He, X. Blockchain-assisted vehicle reputation management method for VANET. J. Xidian Univ. 2022, 49, 49–59. [Google Scholar]
- Fei, Z.; Liu, K.; Huang, B.; Zheng, Y.; Xiang, X. Dirichlet process mixture model based nonparametric bayesian modeling and variational inference. In Proceedings of the 2019 Chinese Automation Congress (CAC), Hangzhou, China, 22–24 November 2019; pp. 3048–3051. [Google Scholar]
- Gurung, S.; Lin, D.; Squicciarini, A.; Bertino, E. Information-oriented trustworthiness evaluation in vehicular ad-hoc networks. In Proceedings of the Network and System Security: 7th International Conference, NSS 2013, Madrid, Spain, 3–4 June 2013; Springer: Berlin/Heidelberg, Germany; pp. 94–108. [Google Scholar]
- Sugumar, R.; Rengarajan, A.; Jayakumar, C. Trust based authentication technique for cluster based vehicular ad hoc networks (VANET). Wirel. Netw. 2018, 24, 373–382. [Google Scholar] [CrossRef]
- Dahmane, S.; Kerrache, C.A.; Lagraa, N.; Lorenz, P. WeiSTARS: A weighted trust-aware relay selection scheme for VANET. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Zhou, M.; Zhang, R.; Xie, W.; Qian, W.; Zhou, A. Security and privacy in cloud computing: A survey. In Proceedings of the 2010 Sixth International Conference on Semantics, Knowledge and Grids, Beijing, China, 1–3 November 2010; pp. 105–112. [Google Scholar]
- Golle, P.; Greene, D.; Staddon, J. Detecting and correcting malicious data in VANETs. In Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks, Philadelphia, PA, USA, 1 October 2004; pp. 29–37. [Google Scholar]
- Diffie, W.; Hellman, M.E. New directions in cryptography. In Democratizing Cryptography: The Work of Whitfield Diffie and Martin Hellman; Association for Computing Machinery: New York, NY, USA, 2022; pp. 365–390. [Google Scholar]
- Narayanan, A.; Bonneau, J.; Felten, E.; Miller, A.; Goldfeder, S. Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction; Princeton University Press: Princeton, NJ, USA, 2016. [Google Scholar]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An efficient decentralized key management mechanism for VANET with blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5836–5849. [Google Scholar] [CrossRef]
- Feng, J.; Wang, Y.; Wang, J.; Ren, F. Blockchain-based data management and edge-assisted trusted cloaking area construction for location privacy protection in vehicular networks. IEEE Internet Things J. 2020, 8, 2087–2101. [Google Scholar] [CrossRef]
- Zhu, X.; Jiang, S.; Wang, L.; Li, H. Efficient privacy-preserving authentication for vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2013, 63, 907–919. [Google Scholar] [CrossRef]
- Su, J.; Ren, R.; Li, Y.; Lau, R.Y.; Shi, Y. Trusted blockchain-based signcryption protocol and data management for authentication and authorization in VANETs. Wirel. Commun. Mob. Comput. 2022, 2022, 9572992. [Google Scholar] [CrossRef]
- Grover, J. Security of Vehicular Ad Hoc Networks using blockchain: A comprehensive review. Veh. Commun. 2022, 34, 100458. [Google Scholar] [CrossRef]
- Zhang, X.; Li, R.; Cui, B. A security architecture of VANET based on blockchain and mobile edge computing. In Proceedings of the 2018 1st IEEE International Conference on Hot Information-Centric Networking (HotICN), Shenzhen, China, 15–17 August 2018; pp. 258–259. [Google Scholar]
- Disterer, G. ISO/IEC 27000, 27001 and 27002 for information security management. J. Inf. Secur. 2013, 4, 92–100. [Google Scholar] [CrossRef]
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Fernando, N.; Loke, S.W.; Rahayu, W. Mobile cloud computing: A survey. Future Gener. Comput. Syst. 2013, 29, 84–106. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Kshetri, N. Can blockchain strengthen the internet of things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Bonneau, J.; Miller, A.; Clark, J.; Narayanan, A.; Kroll, J.A.; Felten, E.W. Sok: Research perspectives and challenges for bitcoin and cryptocurrencies. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 104–121. [Google Scholar]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium blockchain for secure energy trading in industrial internet of things. IEEE Trans. Ind. Inform. 2017, 14, 3690–3700. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, K.; Benslimane, A. Challenges and solutions in autonomous driving: A blockchain approach. IEEE Netw. 2020, 34, 218–226. [Google Scholar] [CrossRef]
- Yang, Z.; Zheng, K.; Yang, K.; Leung, V.C. A blockchain-based reputation system for data credibility assessment in vehicular networks. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Huang, X.; Yu, R.; Kang, J.; Zhang, Y. Distributed reputation management for secure and efficient vehicular edge computing and networks. IEEE Access 2017, 5, 25408–25420. [Google Scholar] [CrossRef]
- Liu, G.; Yang, Q.; Wang, H.; Wu, S.; Wittie, M.P. Uncovering the mystery of trust in an online social network. In Proceedings of the 2015 IEEE Conference on Communications and Network Security (CNS), Florence, Italy, 28–30 September 2015; pp. 488–496. [Google Scholar]
- Jayasinghe, U.; Lee, G.M.; Um, T.W.; Shi, Q. Machine learning based trust computational model for IoT services. IEEE Trans. Sustain. Comput. 2018, 4, 39–52. [Google Scholar] [CrossRef]
- Mahmood, A.; Zhang, W.E.; Sheng, Q.Z.; Siddiqui, S.A.; Aljubairy, A. Trust management for software-defined heterogeneous vehicular ad hoc networks. In Security Privacy and Trust in the IoT Environment; Springer: Cham, Switzerland, 2019; pp. 203–226. [Google Scholar]
- Bendechache, M.; Saber, T.; Muntean, G.M.; Tal, I. Application of blockchain technology to 5g-enabled vehicular networks: Survey and future directions. In Proceedings of the 18th International Symposium on High Performance Mobile Computing & Wireless Networks for HPC (MCWN 2020), Barcelona, Spain, 10–14 December 2020. [Google Scholar]
- Fernandes, C.P.; Montez, C.; Adriano, D.D.; Boukerche, A.; Wangham, M.S. A blockchain-based reputation system for trusted vanet nodes. Ad Hoc Netw. 2023, 140, 103071. [Google Scholar] [CrossRef]
- Fan, N.; Shen, S.; Wu, C.Q.; Yao, J. A hybrid trust model based on communication and social trust for vehicular social networks. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221097588. [Google Scholar] [CrossRef]
- Kerrache, C.A.; Lagraa, N.; Hussain, R.; Ahmed, S.H.; Benslimane, A.; Calafate, C.T.; Cano, J.-C.; Vegni, A.M. TACASHI: Trust-aware communication architecture for social internet of vehicles. IEEE Internet Things J. 2018, 6, 5870–5877. [Google Scholar] [CrossRef]
- Hou, B.; Xin, Y.; Zhu, H.; Yang, Y.; Yang, J. VANET Secure Reputation Evaluation & Management Model Based on Double Layer Blockchain. Appl. Sci. 2023, 13, 5733. [Google Scholar]
- Gazdar, T.; Belghith, A.; Abutair, H. An enhanced distributed trust computing protocol for VANETs. IEEE Access 2017, 6, 380–392. [Google Scholar] [CrossRef]
- Gu, X.; Tang, L.; Han, J. A social-aware routing protocol based on fuzzy logic in vehicular ad hoc networks. In Proceedings of the 2014 International Workshop on High Mobility Wireless Communications, Beijing, China, 1–3 November 2014; pp. 12–16. [Google Scholar]
- Campanile, L.; Gribaudo, M.; Iacono, M.; Marulli, F.; Mastroianni, M. Computer network simulation with ns-3: A systematic literature review. Electronics 2020, 9, 272. [Google Scholar] [CrossRef]
- Pratama, R.A.; Rosselina, L.; Sulistyowati, D.; Sari, R.F.; Harwahyu, R. Performance evaluation on vanet routing protocols in the way road of central jakarta using ns-3 and sumo. In Proceedings of the 2020 International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 19–20 September 2020; pp. 280–285. [Google Scholar]
- Liu, Y. Vanet routing protocol simulation research based on ns-3 and sumo. In Proceedings of the 2021 IEEE 4th International Conference on Electronics Technology (ICET), Chengdu, China, 7–10 May 2021; pp. 1073–1076. [Google Scholar]
- Malnar, M.; Jevtić, N. A framework for performance evaluation of VANETs using NS-3 simulator. Promet–Traffic Transp. 2020, 32, 255–268. [Google Scholar] [CrossRef]






| Parameter | Value |
|---|---|
| Grid Dimension | 5000 m × 5000 m |
| Number of Nodes in VANET | 50, 500 |
| Size of Data or User Request | 512 Bytes |
| Physical Layer | PHY 802.11p |
| Transmission Range | 250 m |
| Node Speed | 10–30 m/s |
| Simulation Time | 300 s |
| Virtual Machine (VM) | Compromised Nodes | Transmitting Nodes | Miners |
|---|---|---|---|
| Node 1 | 10 | 50 | 20 |
| Node 2 | 90 | 200 | 100 |
| Node 3 | 300 | 300 | 200 |
| Action | Probabilities |
|---|---|
| Malicious Node Addition | 5% |
| Compromised Node | 10% |
| Virtual Machine (VM) | Average Jitter | Maximum Jitter | Minimum Jitter |
|---|---|---|---|
| Node 1 | 1.2 ms | 2.3 ms | 0.4 ms |
| Node 2 | 1.5 ms | 2.5 ms | 0.3 ms |
| Node 3 | 1.4 ms | 2.4 ms | 0.5 ms |
| Virtual Machine (VM) | Average Latency | Maximum Latency | Minimum Latency |
|---|---|---|---|
| Node 1 | 15 ms | 25 ms | 5 ms |
| Node 2 | 18 ms | 28 ms | 6 ms |
| Node 3 | 16 ms | 26 ms | 5 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Juárez, R.; Bordel, B. Augmenting Vehicular Ad Hoc Network Security and Efficiency with Blockchain: A Probabilistic Identification and Malicious Node Mitigation Strategy. Electronics 2023, 12, 4794. https://doi.org/10.3390/electronics12234794
Juárez R, Bordel B. Augmenting Vehicular Ad Hoc Network Security and Efficiency with Blockchain: A Probabilistic Identification and Malicious Node Mitigation Strategy. Electronics. 2023; 12(23):4794. https://doi.org/10.3390/electronics12234794
Chicago/Turabian StyleJuárez, Rubén, and Borja Bordel. 2023. "Augmenting Vehicular Ad Hoc Network Security and Efficiency with Blockchain: A Probabilistic Identification and Malicious Node Mitigation Strategy" Electronics 12, no. 23: 4794. https://doi.org/10.3390/electronics12234794
APA StyleJuárez, R., & Bordel, B. (2023). Augmenting Vehicular Ad Hoc Network Security and Efficiency with Blockchain: A Probabilistic Identification and Malicious Node Mitigation Strategy. Electronics, 12(23), 4794. https://doi.org/10.3390/electronics12234794









