GFRX: A New Lightweight Block Cipher for Resource-Constrained IoT Nodes
Abstract
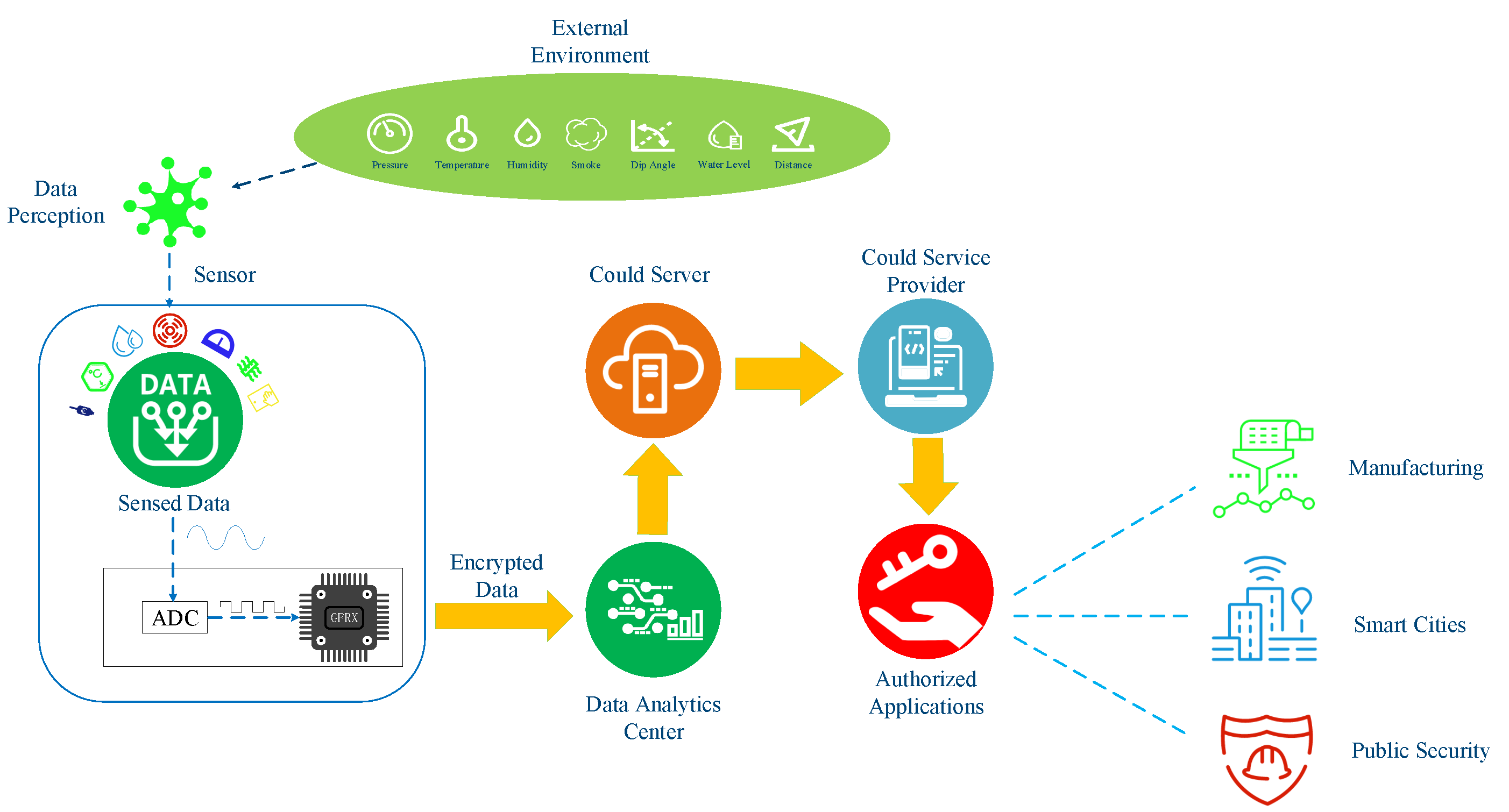
:1. Introduction
- To improve the diffusion effect of the traditional Feistel structure, a new variant of the generalized Feistel structure GFRX is proposed. In GFRX, two ARX structures with different linear components are used to deal with all branches of the generalized Feistel structure to enhance diffusion and confusion.
- To reduce the cost of hardware implementation, the decryption process of the proposed GFRX is similar to its encryption process, so significant additional resources are not required. Meanwhile, the encryption structure is reused in the key extension to minimize the additional resource consumption.
- To improve the flexibility and efficiency of hardware implementation, different levels of serialization implementation are proposed to ensure efficiency under different hardware and throughput requirements.
2. Related Work
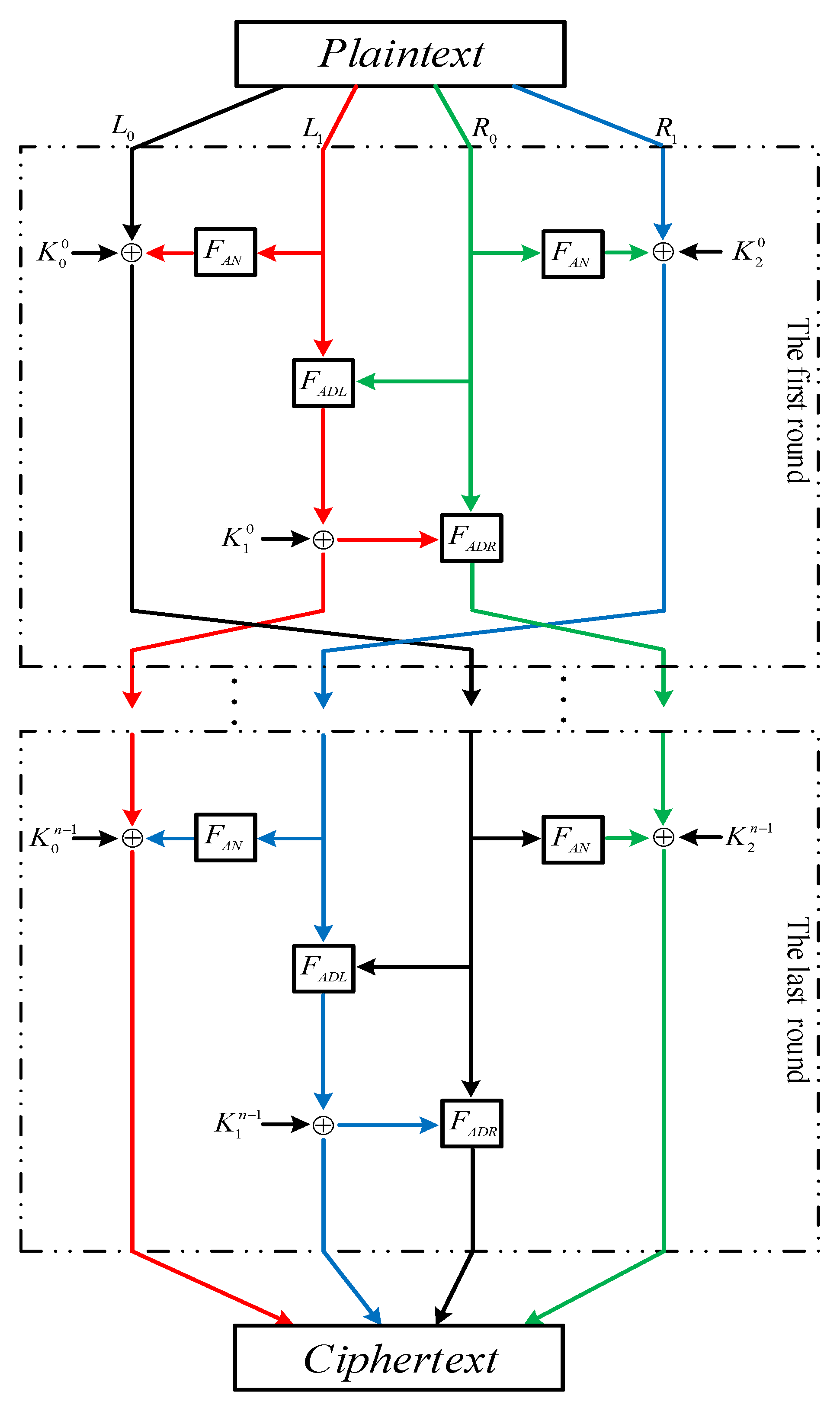
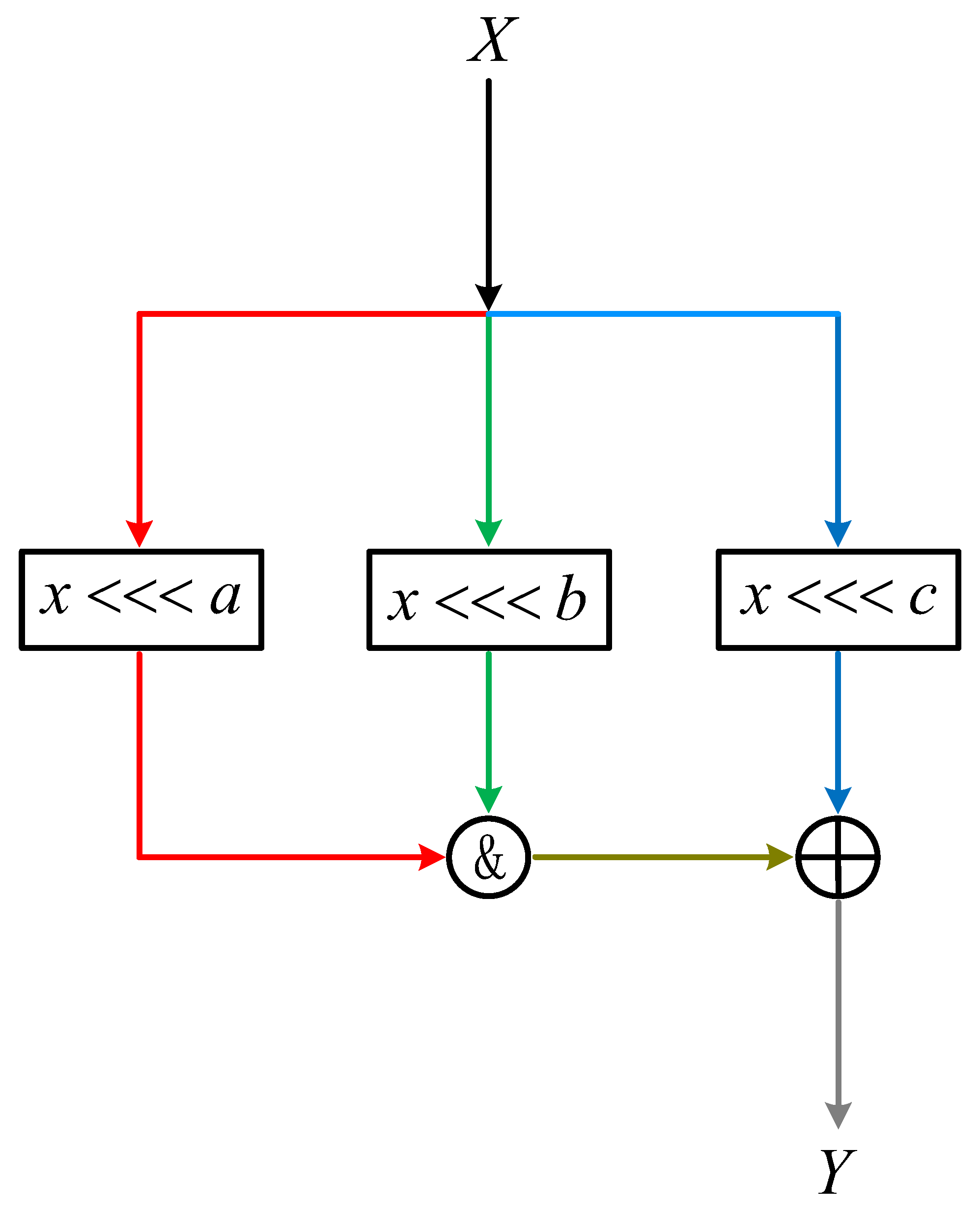
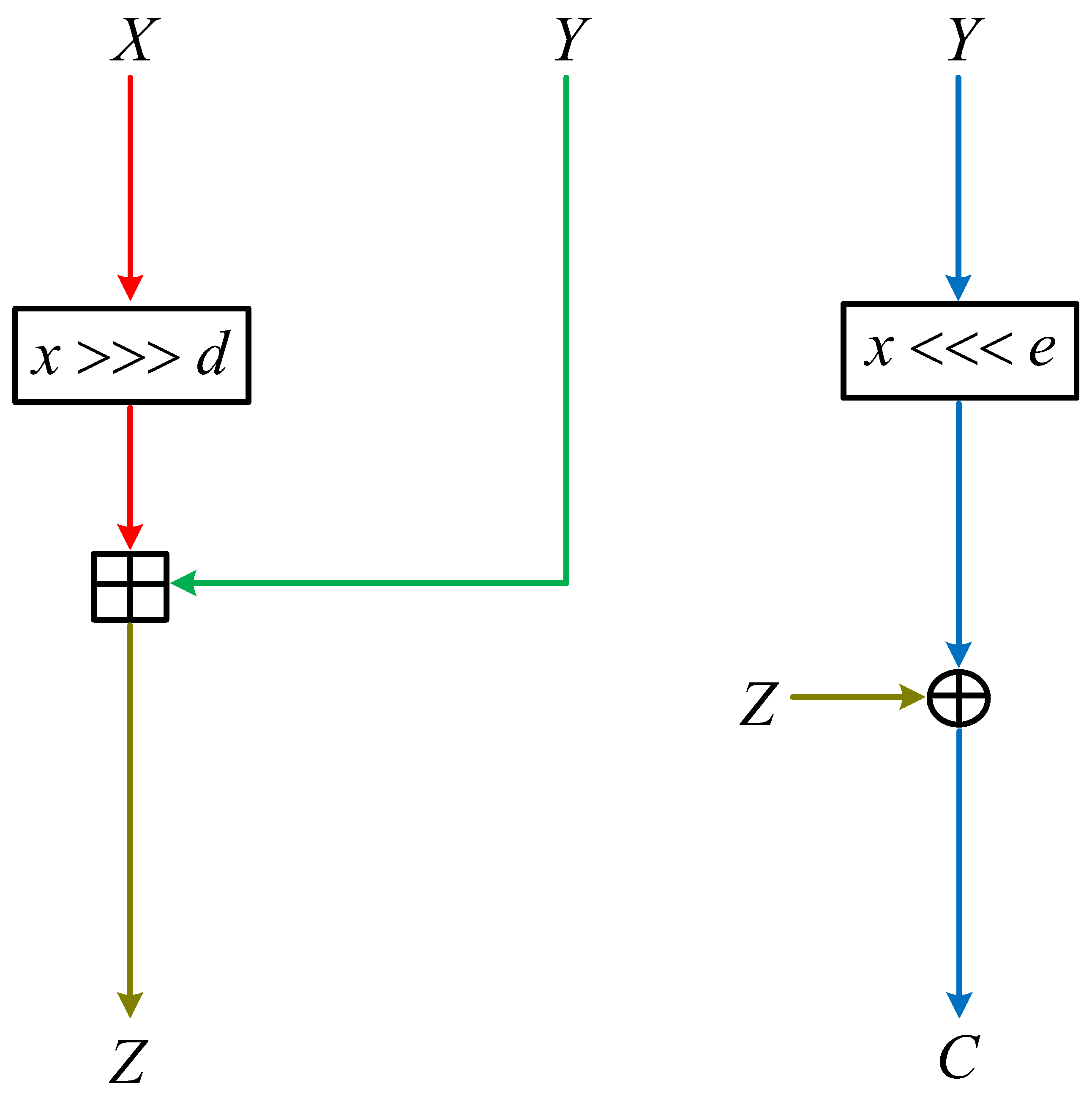
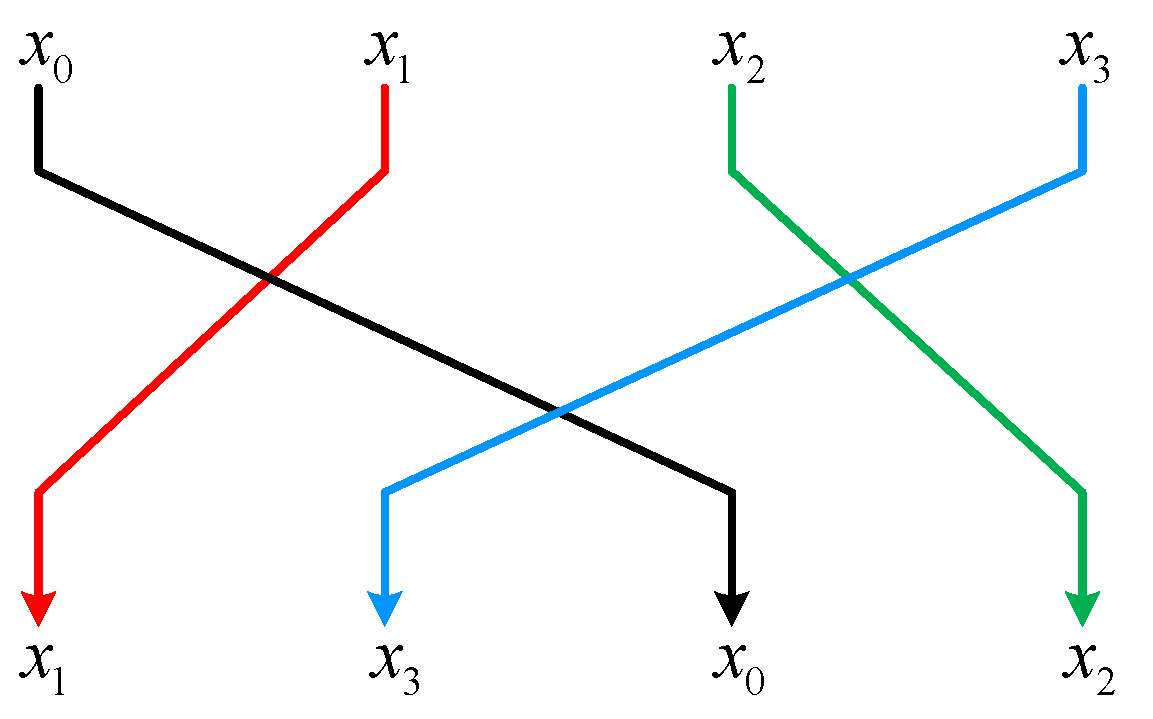
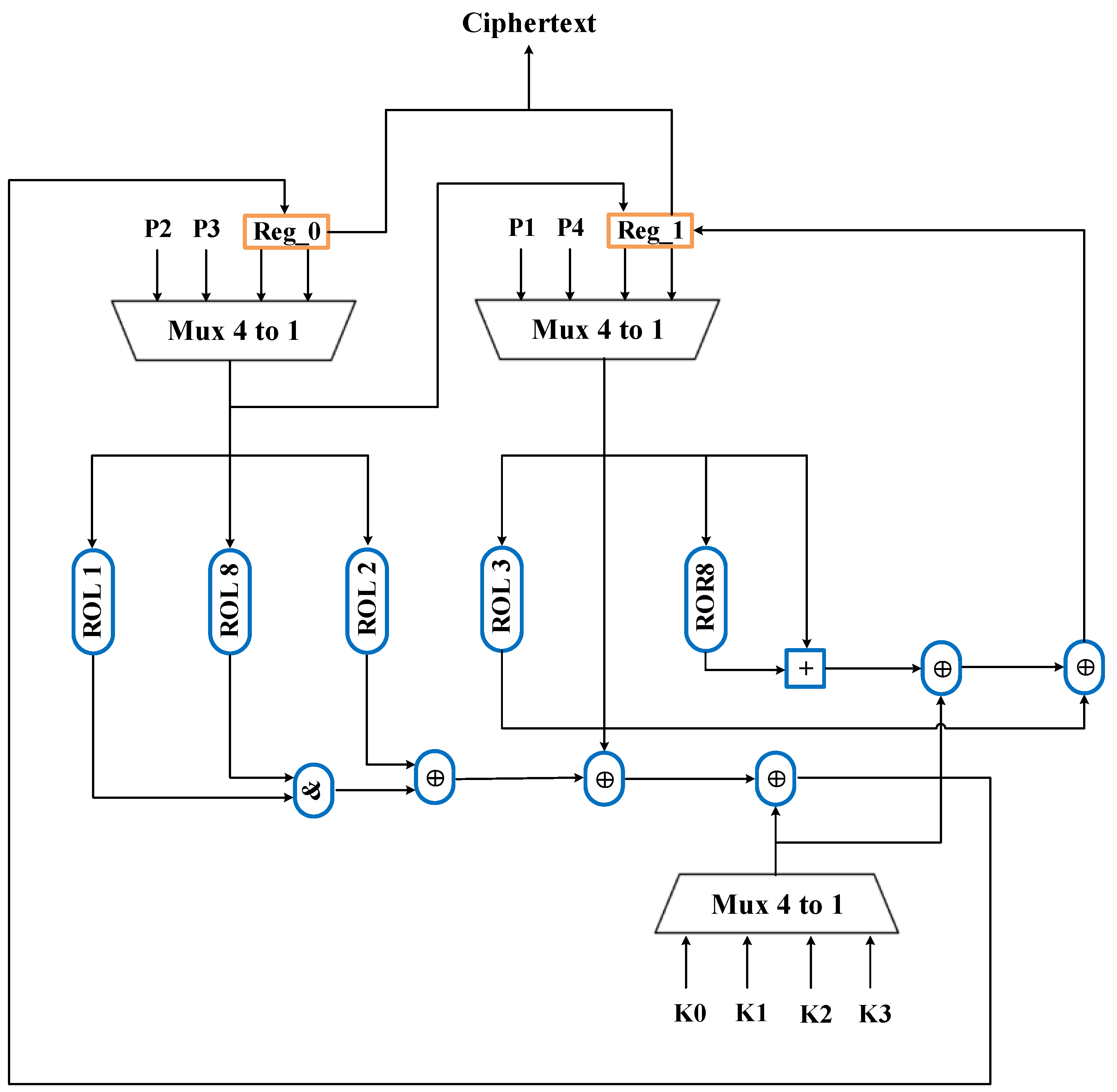
3. Specification of the GFRX
3.1. Encryption
| Algorithm 1 GFRX Encryption. | |
| Input: Plaintext, key | |
| Output: Ciphertext | |
| 1: | ← Plaintext |
| 2: | for r=1 to RN do |
| 3: | |
| 4: | |
| 5: | |
| 6: | |
| 7: | |
| 8: | |
| 9: | |
| 10: | |
| 11: | return Ciphertext ← |
3.2. Key Extension
3.3. Decryption
4. Security Analysis
4.1. Overall Structure Analysis
4.2. Differential and Linear Analysis
5. Performance Evaluation
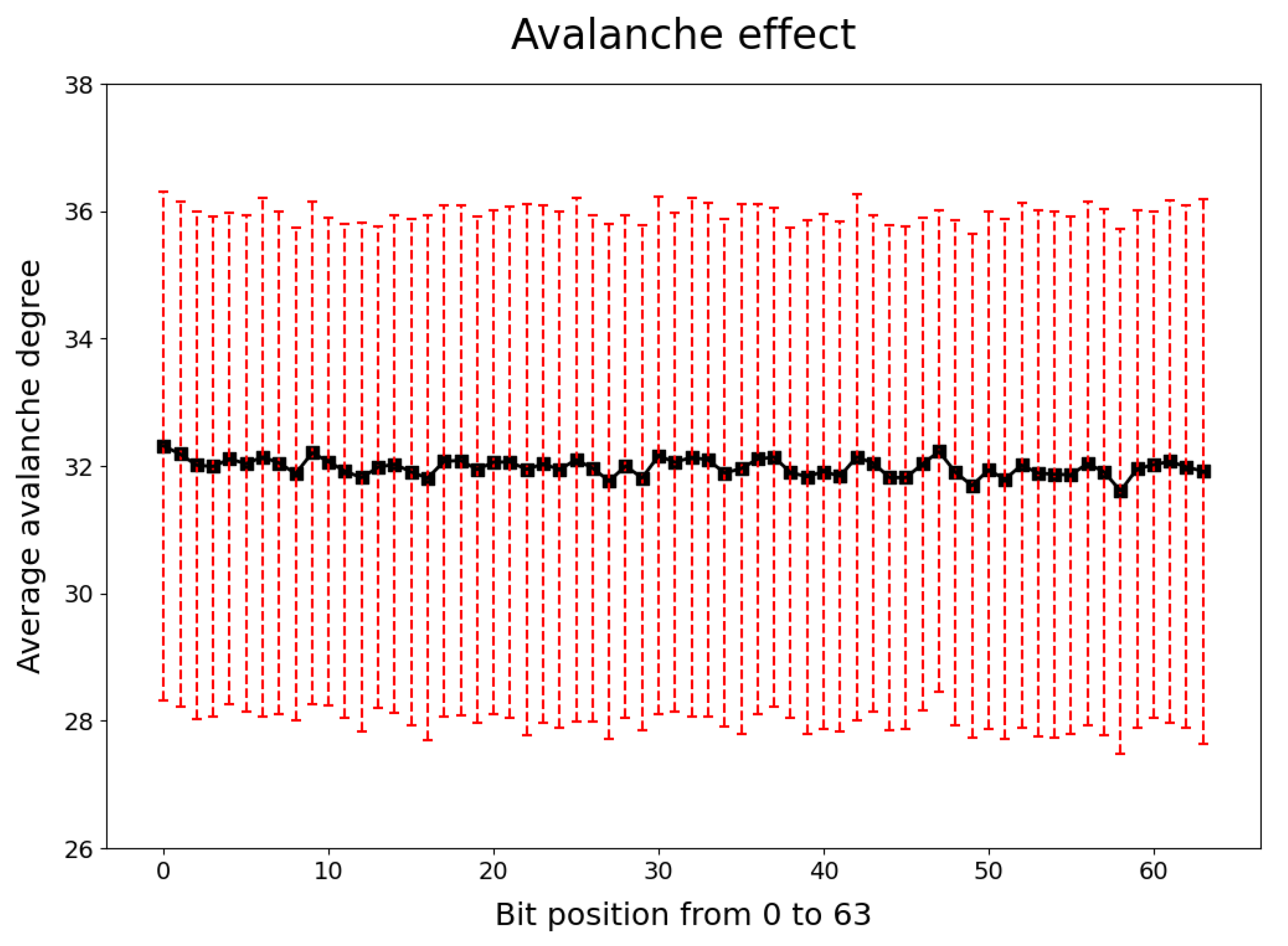
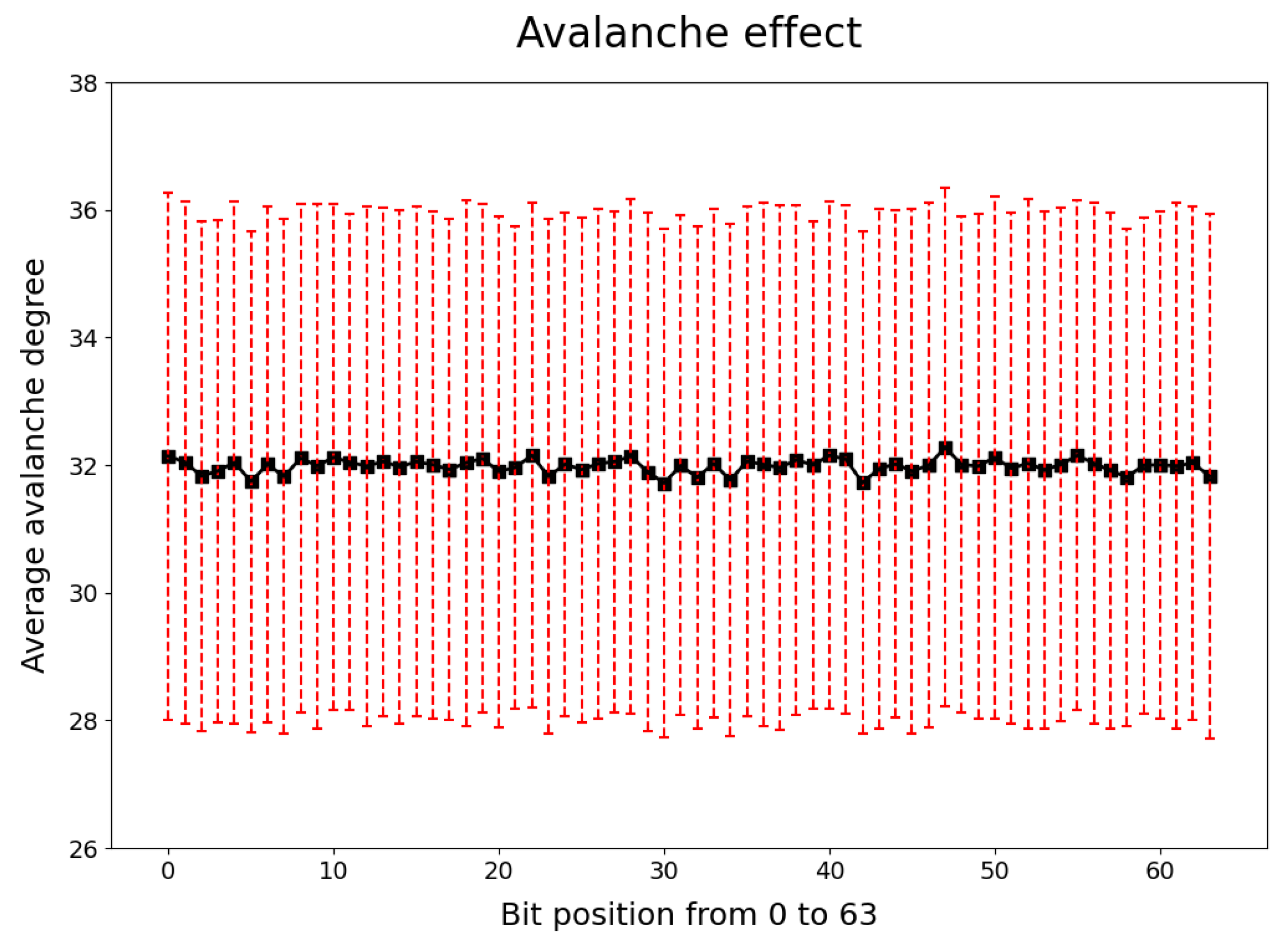
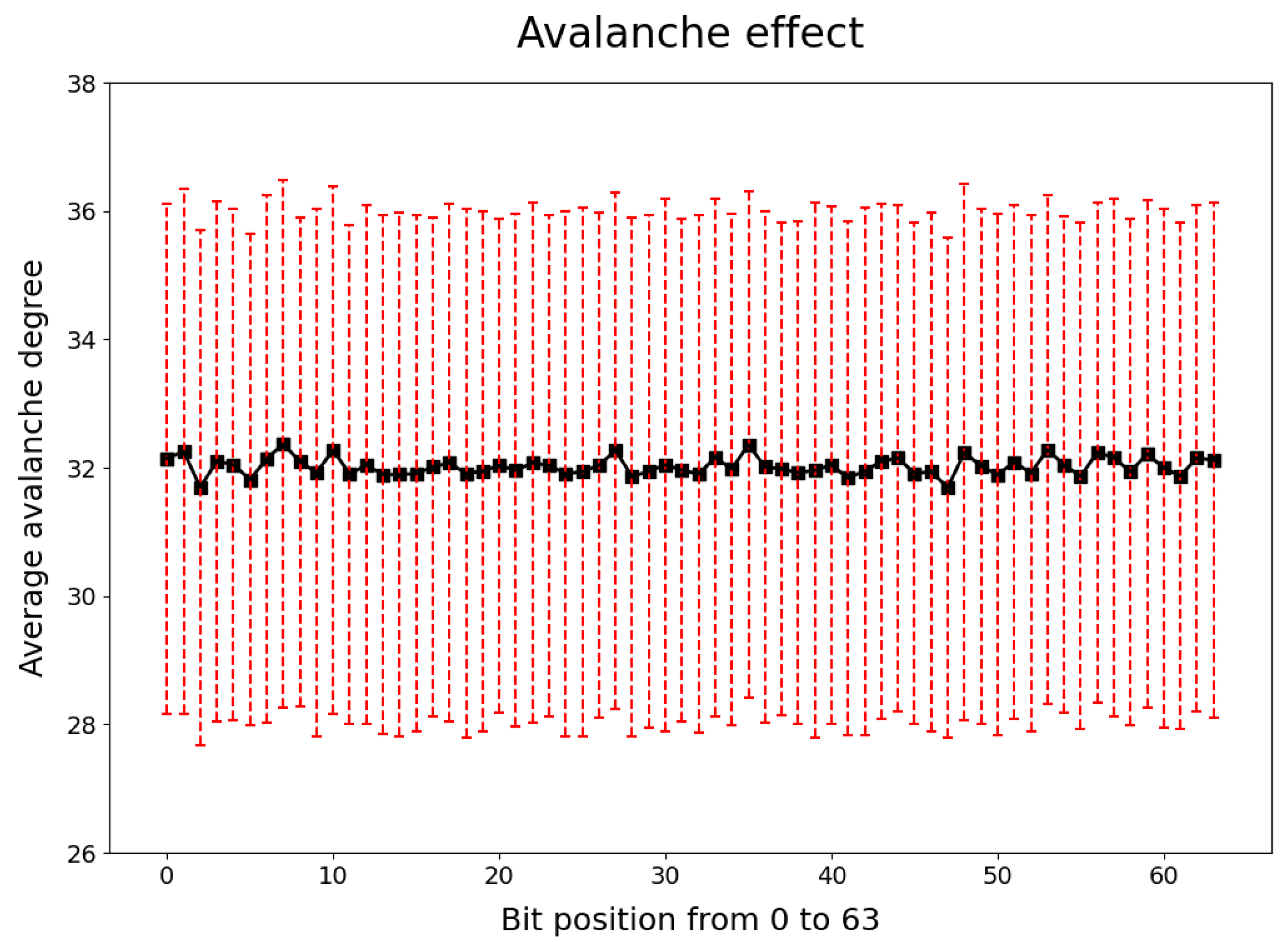
5.1. Avalanche Effect
- A set of keys K is fixed randomly, then a set of plaintexts P is selected randomly.
- After encryption, the initial ciphertext C is obtained.
- The first bit of the plaintext is reversed and the rest of the bits remain unchanged; then the algorithm is input together with the key.
- After encryption, the ciphertext is obtained.
- The Hamming weight of represents the avalanche degree of the first bit in the plaintext.
- Repeat the above steps to find the avalanche degree on all bits of P.
- Repeat the preceding steps 1000 times. Each time, P is random and K is the initial fixed key.
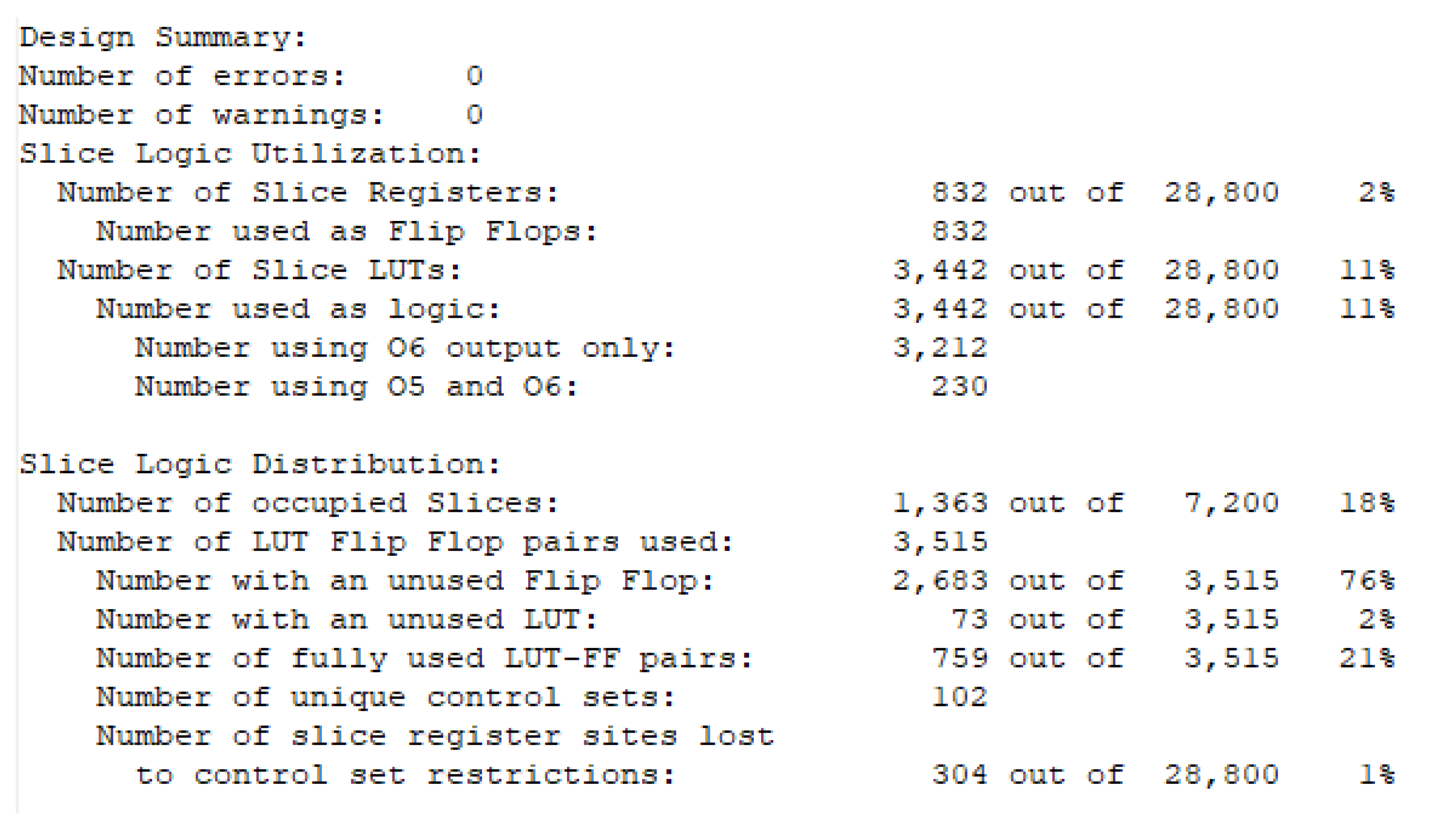
5.2. Hardware Implementation
5.2.1. FPGA Implementation
5.2.2. ASIC Implementation and Comprehensive Performance Evaluation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ray, P.P.; Dash, D.; De, D. Edge computing for internet of things: A survey, e-healthcare case study and future direction. J. Netw. Comput. Appl. 2019, 140, 1–22. [Google Scholar] [CrossRef]
- Goyal, P.; Sahoo, A.K.; Sharma, T.K.; Singh, P.K. Internet of things: Applications, security and privacy: A survey. Mater. Today Proc. 2021, 34, 752–759. [Google Scholar] [CrossRef]
- Kakkar, L.; Gupta, D.; Tanwar, S.; Saxena, S.; Alsubhi, K.; An, D.; Noya, I.D.; Goyal, N. A secure and efficient signature scheme for iot in healthcare. Cmc-Comput. Mater. Contin. 2022, 73, 6151–6168. [Google Scholar] [CrossRef]
- Rana, A.; Sharma, S.; Nisar, K.; Ibrahim, A.A.A.; Dhawan, S.; Chowdhry, B.; Hussain, S.; Goyal, N. The rise of blockchain internet of things (biot): Secured, device-to-device architecture and simulation scenarios. Appl. Sci. 2022, 12, 7694. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. Aes proposal: Rijndael. AES Propos. 1999, 2, 1–45. [Google Scholar]
- Basu, S. International data encryption algorithm (idea)—A typical illustration. J. Glob. Res. Comput. Sci. 2011, 2, 116–118. [Google Scholar]
- Al-Aali, Y.; Boussakta, S. Lightweight block ciphers for resource-constrained devices. In Proceedings of the 2020 12th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2020; pp. 1–6. [Google Scholar]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.; Seurin, Y.; Vikkelsoe, C. Present: An Ultra-Lightweight Block Cipher; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- Banik, S.; Pandey, S.K.; Peyrin, T.; Sasaki, Y.; Sim, S.M.; Todo, Y. Gift: A Small Present; Springer: Berlin/Heidelberg, Germany, 2017; pp. 321–345. [Google Scholar]
- Liu, B.-T.; Li, L.; Wu, R.-X.; Xie, M.-M.; Li, Q.P. Loong: A family of involutional lightweight block cipher based on spn structure. IEEE Access 2019, 7, 136023–136035. [Google Scholar] [CrossRef]
- Jha, P.; Zorkta, H.Y.; Allawi, D.; Al-Nakkar, M.R. Improved lightweight encryption algorithm (ILEA). In Proceedings of the 2020 International Conference for Emerging Technology (INCET), Belgaum, India, 5–7 June 2020; pp. 1–4. [Google Scholar]
- Guo, Y.; Li, L.; Liu, B. Shadow: A lightweight block cipher for iot nodes. IEEE Internet Things J. 2021, 8, 13014–13023. [Google Scholar] [CrossRef]
- Nyberg, K. Generalized feistel networks. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 6–10 December 1996; pp. 91–104. [Google Scholar]
- Aboushosha, B.; Ramadan, R.A.; Dwivedi, A.D.; El-Sayed, A.; Dessouky, M.M. Slim: A lightweight block cipher for internet of health things. IEEE Access 2020, 8, 203747–203757. [Google Scholar] [CrossRef]
- Chen, S.; Fan, Y.; Sun, L.; Fu, Y.; Zhou, H.; Li, Y.; Wang, M.; Wang, W.; Guo, C. Sand: An and-rx feistel lightweight block cipher supporting s-box-based security evaluations. Des. Codes Cryptogr. 2022, 90, 155–198. [Google Scholar] [CrossRef]
- Izadi, M.; Sadeghiyan, B.; Sadeghian, S.S.; Khanooki, H.A. Mibs: A new lightweight block cipher. In Proceedings of the International Conference on Cryptology and Network Security, Kanazawa, Japan, 12–14 December 2009; pp. 334–348. [Google Scholar]
- Yeoh, W.Z.; Teh, J.S.; Sazali, M.I.S.B.M. μ2: A lightweight block cipher. In Proceedings of the Computational Science and Technology, Cagliari, Italy, 1–4 July 2020; pp. 281–290. [Google Scholar]
- Patil, J.; Bansod, G.; Kant, K.S. Lici: A new ultra-lightweight block cipher. In Proceedings of the 2017 International Conference on Emerging Trends & Innovation in ICT (ICEI), Pune, India, 3–5 February 2017; pp. 40–45. [Google Scholar]
- Shibutani, K.; Isobe, T.; Hiwatari, H.; Mitsuda, A.; Akishita, T.; Shirai, T. Piccolo: An ultra-lightweight blockcipher. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Nara, Japan, 28 September–1 October 2011; pp. 342–357. [Google Scholar]
- Suzaki, T.; Minematsu, K.; Morioka, S.; Kobayashi, E. Twine: A Lightweight Block Cipher for Multiple Platforms; Springer: Berlin/Heidelberg, Germany, 2012; pp. 339–354. [Google Scholar]
- Lang, L.; Botao, L.; Hui, W. Qtl: A new ultra-lightweight block cipher. Microprocess. Microsystems 2016, 45, 45–55. [Google Scholar]
- Ferguson, N.; Schneier, B.; Kohno, T. Block Cipher Modes; Wiley Online Library: Hoboken, NJ, USA, 2015; pp. 63–76. [Google Scholar]
- Biham, E.; Shamir, A. Differential Cryptanalysis of the Data Encryption Standard; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Matsui, M. Linear cryptanalysis of the data encryption standard. In Proceedings of the EUROCRYPT 1993, Lofthus, Norway, 23–27 May 1993; pp. 386–397. [Google Scholar]
- Hoang, V.T.; Rogaway, P. On Generalized Feistel Networks; Springer: Berlin/Heidelberg, Germany, 2010; pp. 613–630. [Google Scholar]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The simon and speck lightweight block ciphers. In Proceedings of the 52nd Annual Design Automation Conference, San Francisco, CA, USA, 7–11 June 2015; pp. 1–6. [Google Scholar]
- Abed, F.; List, E.; Lucks, S.; Wenzel, J. Cryptanalysis of the speck family of block ciphers. Cryptology ePrint Archive 2013. [Google Scholar]
- Alkhzaimi, H.A.; Lauridsen, M.M. Cryptanalysis of the simon family of block ciphers. Cryptology ePrint Archive 2013. [Google Scholar]
- Abed, F.; List, E.; Lucks, S.; Wenzel, J. Differential and linear cryptanalysis of reduced-round simon. Cryptology ePrint Archive 2013. [Google Scholar]
- Alex, B.; Vesselin, V. Automatic search for differential trails in arx ciphers. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 25–28 February 2014; pp. 227–250. [Google Scholar]
- Biryukov, A.; Roy, A.; Velichkov, V. Differential analysis of block ciphers simon and speck. In Proceedings of the International Workshop on Fast Software Encryption, Istanbul, Turkey, 8–11 March 2015; pp. 546–570. [Google Scholar]
- Alizadeh, J.; Alkhzaimi, H.A.; Aref, M.R.; Bagheri, N.; Gauravaram, P.; Kumar, A.; Lauridsen, M.M.; Sanadhya, S.K. Cryptanalysis of simon variants with connections. In Proceedings of the International Workshop on Radio Frequency Identification: Security and Privacy Issues, New York, NY, USA, 23–24 June 2015; pp. 90–107. [Google Scholar]
- Nemati, A.; Feizi, S.; Ahmadi, A.; Makki, V.A.-d. A low-cost and flexible fpga implementation for speck block cipher. In Proceedings of the 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), Rasht, Iran, 8–10 September 2015; pp. 42–47. [Google Scholar]
- Mace, F.; Standaert, F.X.; Quisquater, J.J. Asic implementations of the block cipher sea for constrained applications. In Proceedings of the Third International Conference on RFID Security-RFIDSec, Amherst, MA, USA, 26–28 June 2007; Volume 2007, pp. 103–114. [Google Scholar]
- Rolfes, C.; Poschmann, A.; Leander, G.; Paar, C. Ultra-lightweight implementations for smart devices–security for 1000 gate equivalents. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, London, UK, 8–11 September 2008; pp. 89–103. [Google Scholar]
- Manifavas, C.; Hatzivasilis, G.; Fysarakis, K.; Rantos, K. Lightweight Cryptography for Embedded Systems—A Comparative Analysis; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]

| Block Size | Key Size | ||||
|---|---|---|---|---|---|
| 96 | 128 | 144 | 192 | 256 | |
| 64 | 26 | 27 | - | - | - |
| 96 | 28 | - | 29 | - | - |
| 128 | - | 32 | - | 33 | 34 |
| Algorithm | Block Size | Key Size | Average Avalanche | Average Uncertainty | Avalanche Threshold |
|---|---|---|---|---|---|
| SIMON | 64 | 128 | 31.970015 | 3.996816 | 12 |
| SPECK | 64 | 128 | 32.013781 | 4.000526 | 8 |
| GFRX | 64 | 128 | 32.005156 | 4.010121 | 6 |
| NOT | NAND | AND | OR | XOR | XNOR | 4-1 MUX | D-Flip-Flop | 1-Full-Adder |
|---|---|---|---|---|---|---|---|---|
| 0.75 | 1.00 | 1.25 | 1.25 | 2.00 | 2.00 | 4.50 | 4.25 | 5.75 |
| Degree | Throughput (Kbps) | Area (GE) | FOM |
|---|---|---|---|
| 1-bit | 4.49 | 886.25 | 57.17 |
| 2-bit | 8.98 | 926.25 | 104.67 |
| 4-bit | 17.96 | 1006.25 | 177.38 |
| 8-bit | 35.92 | 1166.25 | 264.09 |
| 16-bit | 71.84 | 1486.25 | 325.22 |
| Algorithm | Throughput (Kbps) | Area (GE) | FOM |
|---|---|---|---|
| AES-128 | 12.40 | 3400 | 10.73 |
| DES | 44.40 | 2309 | 83.28 |
| DESL | 44.40 | 1848 | 130.00 |
| Hight-128 | 188.25 | 3048 | 202.63 |
| PRESENT-128 | 200.00 | 1886 | 562.27 |
| GFRX-128 | 206.45 | 1609 | 797.20 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, X.; Tang, S.; Li, T.; Li, X.; Wang, C. GFRX: A New Lightweight Block Cipher for Resource-Constrained IoT Nodes. Electronics 2023, 12, 405. https://doi.org/10.3390/electronics12020405
Zhang X, Tang S, Li T, Li X, Wang C. GFRX: A New Lightweight Block Cipher for Resource-Constrained IoT Nodes. Electronics. 2023; 12(2):405. https://doi.org/10.3390/electronics12020405
Chicago/Turabian StyleZhang, Xing, Shaoyu Tang, Tianning Li, Xiaowei Li, and Changda Wang. 2023. "GFRX: A New Lightweight Block Cipher for Resource-Constrained IoT Nodes" Electronics 12, no. 2: 405. https://doi.org/10.3390/electronics12020405
APA StyleZhang, X., Tang, S., Li, T., Li, X., & Wang, C. (2023). GFRX: A New Lightweight Block Cipher for Resource-Constrained IoT Nodes. Electronics, 12(2), 405. https://doi.org/10.3390/electronics12020405






