A Robust Medical Image Watermarking Scheme Based on Nature-Inspired Optimization for Telemedicine Applications
Abstract
1. Introduction
- The use of SLT and RSVD reduces the computational complexity and improves the robustness.
- The use of XOR encryption improves the security of inserted watermark.
- The FA provides a better optimized scaling factor in the least number of populations and iterations.
- We used the PSNR, SSIM, and NC values to design the fitness function for the FA, which improves the quality of both the embedded watermarked image and the extracted watermark.
2. Background and Motivation
3. Preliminaries
3.1. Slantlet Transform
3.2. Firefly Algorithm
- All fireflies are unisexual, so one firefly will be attracted to other fireflies regardless of their sex.
- Attractiveness is proportional to their brightness; thus, for any two flashing fireflies, the less bright one will move.
- If there are no fireflies brighter than a particular firefly, it will move randomly toward the brighter one.
| Algorithm 1: Firefly algorithm to optimize MSF. |
|
3.3. Randomized Singular Value Decomposition (RSVD)
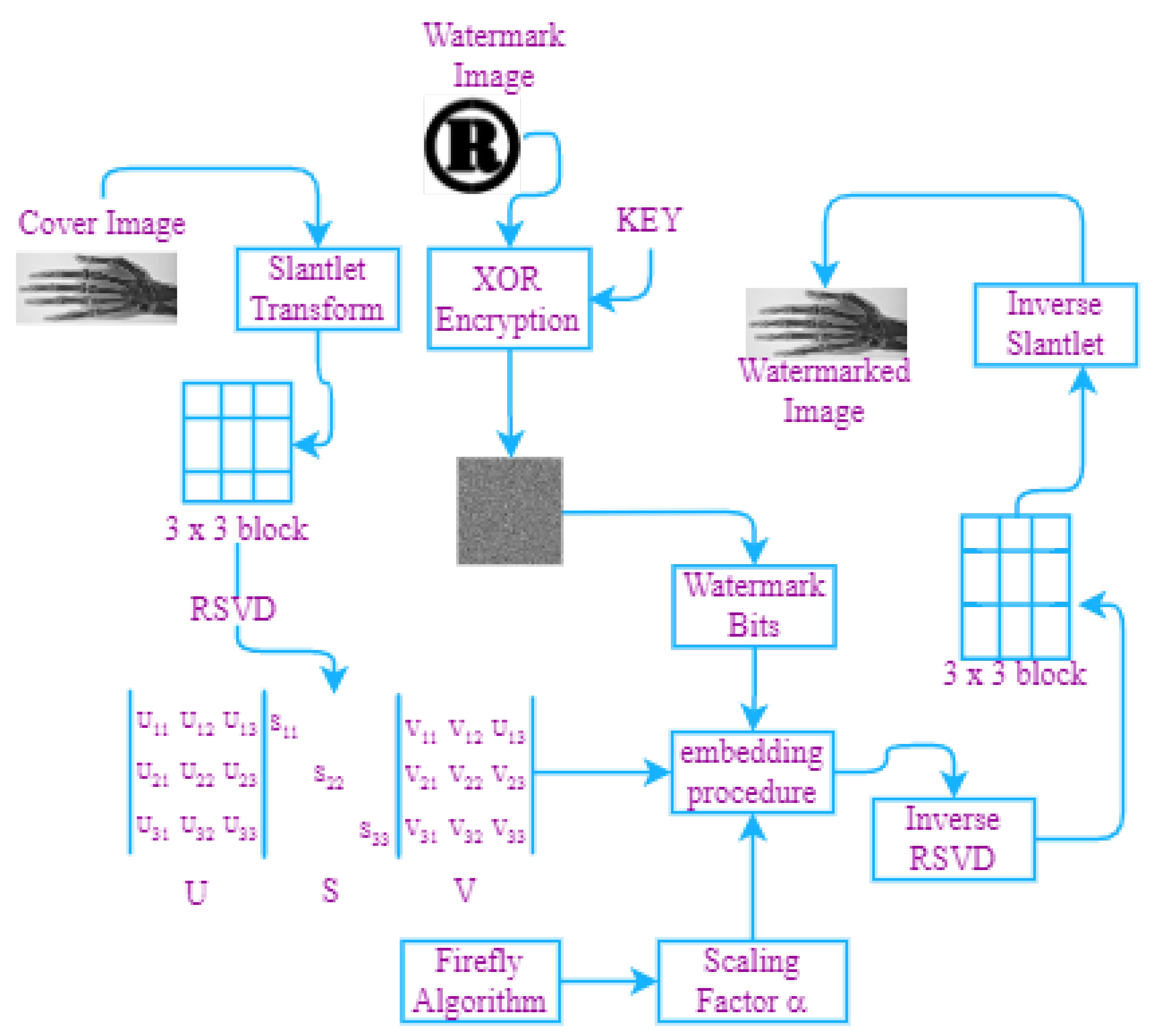
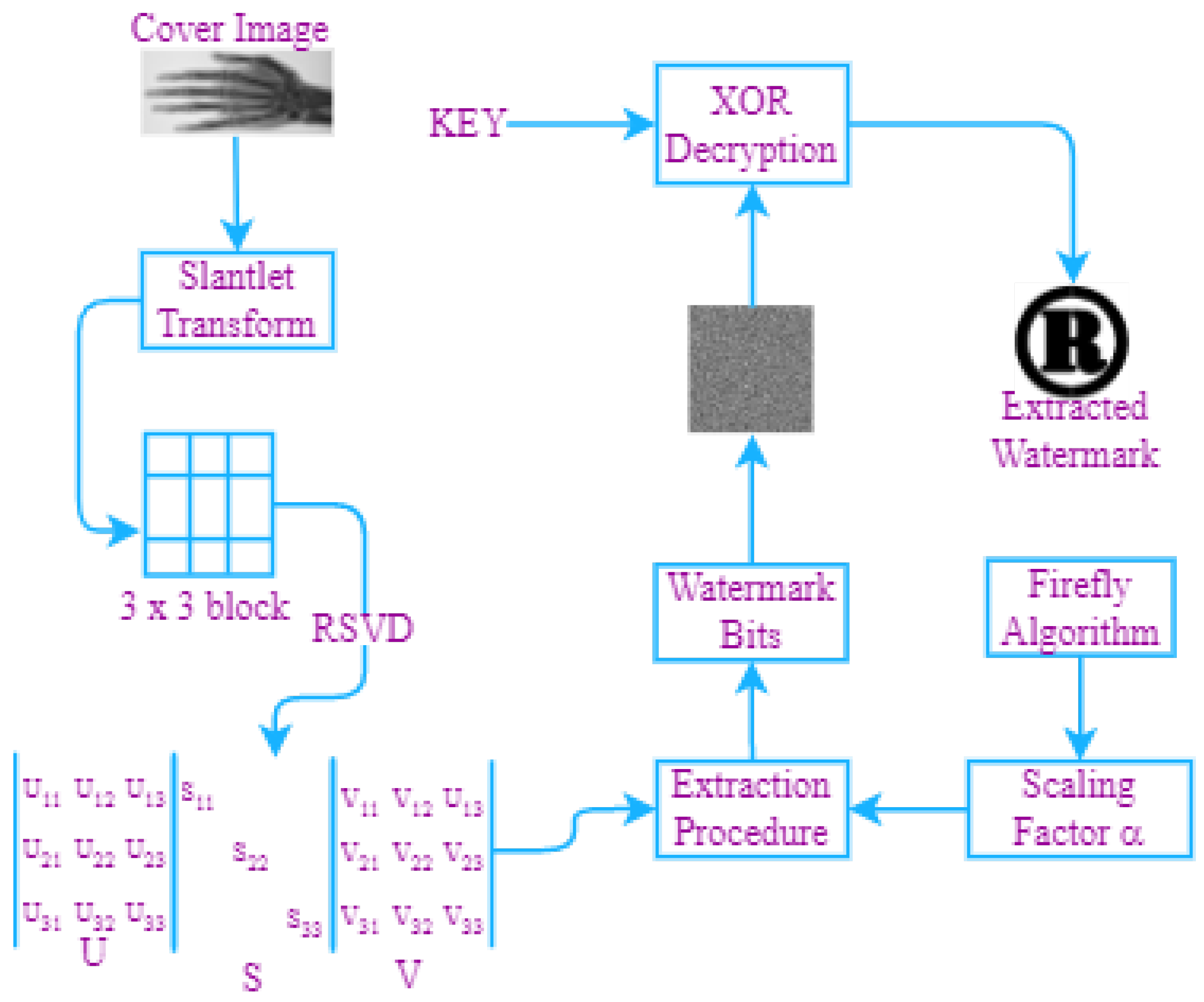
4. Proposed Work
4.1. Watermark Entrenching Scheme
| Algorithm 2: The step-wise process to entrench the watermark |
|
4.2. Watermark Extraction Scheme
| Algorithm 3: The step-wise process to extract the watermark |
|
4.3. Analysis of Imperceptibility Based on SSF
5. Results and Discussion
5.1. Robustness Analysis
5.2. Comparison of Proposed Scheme with Existing Schemes
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| SVD | Singular Value Decomposition |
| SLT | Slantlet Transform |
| RSVD | Randomized-Singular Value Decomposition |
| FA | Firefly Algorithm |
| MRI | Magnetic Resonance Imaging |
| CT | Computed Tomography |
| DICOM | Digital Imaging and Communications in Medicine |
| JPEG | Joint Photographic Experts Group |
| SSIM | Structural Similarity Index Metric |
| PSNR | Peak Signal-to-Noise Ratio |
| NC | Normalized Correlation |
| NIA | Nature Inspired Algirthm |
| MSF | Multi-Valued Scaling Factor |
| SSF | Single-Valued Scaling Factor |
| LWT | Lifting Wavelet Transform |
| IWT | Integer Wavelet Transform |
| PSO | Particle Swarm Optimization |
| MRI | Magnetic Resonance Imaging |
| GA | Genetic Algorithm |
| ABC | Artificial Bee Colony Algorithm |
| DWT | Discrete Wavelet Transform |
| MAC | Media Access Control |
| HD | Hessenberg Decomposition |
References
- Kumar, L.; Singh, K.U. Color Ultrasound Image Watermarking Scheme Using FRT and Hessenberg Decomposition for Telemedicine Applications. JUCS J. Univers. Comput. Sci. 2022, 28, 882–897. [Google Scholar] [CrossRef]
- Altay, Ş.Y.; Ulutaş, G. Self-adaptive step firefly algorithm based robust watermarking method in DWT-SVD domain. Multimed. Tools Appl. 2021, 80, 23457–23484. [Google Scholar] [CrossRef]
- Favorskaya, M.; Savchina, E.; Gusev, K. Feature-based synchronization correction for multilevel watermarking of medical images. Procedia Comput. Sci. 2019, 159, 1267–1276. [Google Scholar] [CrossRef]
- Liu, X.; Lou, J.; Fang, H.; Chen, Y.; Ouyang, P.; Wang, Y.; Zou, B.; Wang, L. A Novel Robust Reversible Watermarking Scheme for Protecting Authenticity and Integrity of Medical Images. IEEE Access 2019, 7, 76580–76598. [Google Scholar] [CrossRef]
- Mousavi, S.M.; Naghsh, A.; Abu-Bakar, S.A.R. Watermarking techniques used in medical images: A survey. J. Digit. Imaging 2014, 27, 714–729. [Google Scholar] [CrossRef]
- Qasim, A.F.; Meziane, F.; Aspin, R. Digital watermarking: Applicability for developing trust in medical imaging workflows state of the art review. Comput. Sci. Rev. 2018, 27, 45–60. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Hybrid Nature-Inspired Optimization and Encryption-Based Watermarking for E-Healthcare. IEEE Trans. Comput. Soc. Syst. 2022, 1–8. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Watermarking techniques for medical data authentication: A survey. Multimed. Tools Appl. 2021, 80, 30165–30197. [Google Scholar] [CrossRef]
- Ali, M.; Ahn, C.W.; Pant, M.; Siarry, P. An image watermarking scheme in wavelet domain with optimized compensation of singular value decomposition via artificial bee colony. Inf. Sci. 2015, 301, 44–60. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. RDWT-SVD-Firefly Based Dual Watermarking Technique for Medical Images (Workshop Paper). In Proceedings of the 2020 IEEE Sixth International Conference on Multimedia Big Data (BigMM), New Delhi, India, 24–26 September 2020; pp. 366–372. [Google Scholar] [CrossRef]
- Yang, X.S. Nature-Inspired Metaheuristic Algorithms; Luniver Press: Frome, UK, 2008. [Google Scholar]
- Zhang, Y.; Wu, L. Rigid Image Registration based on Normalized Cross Correlation and Chaotic Firefly Algorithm. Int. J. Digit. Content Technol. Its Appl. 2012, 6, 129–140. [Google Scholar]
- Hassanzadeh, T.; Vojodi, H.; Moghadam, A.M.E. An image segmentation approach based on maximum variance Intra-cluster method and Firefly algorithm. In Proceedings of the 2011 Seventh International Conference on Natural Computation, Shanghai, China, 26–28 July 2011; Volume 3, pp. 1817–1821. [Google Scholar] [CrossRef]
- Kanimozhi, T.; Latha, K. An integrated approach to region based image retrieval using firefly algorithm and support vector machine. Neurocomputing 2015, 151, 1099–1111. [Google Scholar] [CrossRef]
- Sharma, A.; Chaturvedi, R.; Bhargava, A. A novel opposition based improved firefly algorithm for multilevel image segmentation. Multimed. Tools Appl. 2022, 81, 15521–15544. [Google Scholar] [CrossRef]
- Draa, A.; Benayad, Z.; Djenna, F.Z. An opposition-based firefly algorithm for medical image contrast enhancement. Int. J. Inf. Commun. Technol. 2015, 7, 385–405. [Google Scholar] [CrossRef]
- Ali, M.; Ahn, C.W. Comments on ‘Optimized gray-scale image watermarking using DWT–SVD and Firefly Algorithm’. Expert Syst. Appl. 2015, 42, 2392–2394. [Google Scholar] [CrossRef]
- Mishra, A.; Agarwal, C.; Sharma, A.; Bedi, P. Optimized gray-scale image watermarking using DWT–SVD and Firefly Algorithm. Expert Syst. Appl. 2014, 41, 7858–7867. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K.; Lv, Z.; Bhatnagar, G. Compression-Then-Encryption-Based Secure Watermarking Technique for Smart Healthcare System. IEEE Multimed. 2020, 27, 133–143. [Google Scholar] [CrossRef]
- Chaturvedi, A.K.; Shukla, P.K. Effective watermarking technique using optimal discrete wavelet transform and sanitization technique. Multimed. Tools Appl. 2020, 79, 13161–13177. [Google Scholar] [CrossRef]
- Baba Ahmadi, S.B.; Zhang, G.; Jelodar, H. A robust hybrid SVD-based image watermarking scheme for color images. In Proceedings of the 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 17–19 October 2019; pp. 0682–0688. [Google Scholar] [CrossRef]
- Pandey, M.K.; Parmar, G.; Gupta, R.; Sikander, A. Lossless robust color image watermarking using lifting scheme and GWO. Int. J. Syst. Assur. Eng. Manag. 2020, 11, 320–331. [Google Scholar] [CrossRef]
- Lai, C.C.; Tsai, C.C. Digital Image Watermarking Using Discrete Wavelet Transform and Singular Value Decomposition. IEEE Trans. Instrum. Meas. 2010, 59, 3060–3063. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Cloud based secure watermarking using IWT-Schur-RSVD with fuzzy inference system for smart healthcare applications. Sustain. Cities Soc. 2021, 75, 103398. [Google Scholar] [CrossRef]
- Xu, D. Commutative Encryption and Data Hiding in HEVC Video Compression. IEEE Access 2019, 7, 66028–66041. [Google Scholar] [CrossRef]
- Selesnick, I. The slantlet transform. IEEE Trans. Signal Process. 1999, 47, 1304–1313. [Google Scholar] [CrossRef]
- Zhang, J.; Erway, J.; Hu, X.; Zhang, Q.; Plemmons, R. Randomized SVD Methods in Hyperspectral Imaging. J. Electr. Comput. Eng. 2012, 2012, 409357. [Google Scholar] [CrossRef]
- Cox, I.; Kilian, J.; Leighton, F.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef] [PubMed]
- Loukhaoukha, K. Optimal Image Watermarking Algorithm Based on LWT-SVD via Multi-objective Ant Colony Optimization. J. Inf. Hiding Multimed. Signal Process. 2011, 2, 303–319. [Google Scholar]
- Wang, Z.; Bovik, A.C.; Sheikh, H.R. Structural similarity based image quality assessment. In Digital Video Image Quality and Perceptual Coding; CRC Press: Boca Raton, FL, USA, 2017; pp. 225–242. [Google Scholar]
- Thakur, S.; Singh, A.K.; Kumar, B.; Ghrera, S.P. Improved DWT-SVD-Based Medical Image Watermarking Through Hamming Code and Chaotic Encryption. In Proceedings of the Advances in VLSI, Communication, and Signal Processing; Dutta, D., Kar, H., Kumar, C., Bhadauria, V., Eds.; Springer: Singapore, 2020; pp. 897–905. [Google Scholar]
- Guo, Y.; Li, B.Z.; Goel, N. Optimised blind image watermarking method based on firefly algorithm in DWT-QR transform domain. IET Image Process. 2017, 11, 406–415. [Google Scholar] [CrossRef]
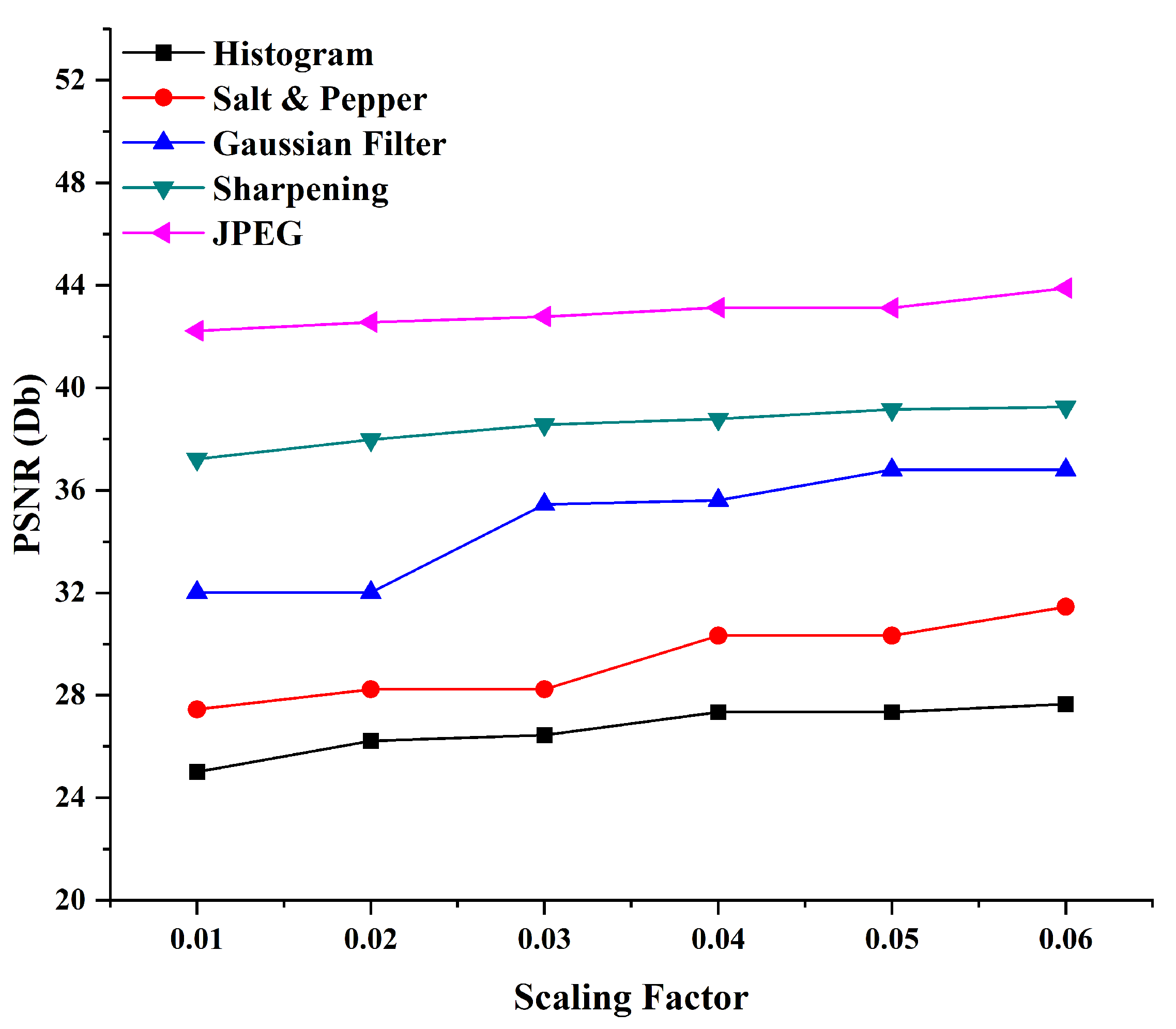
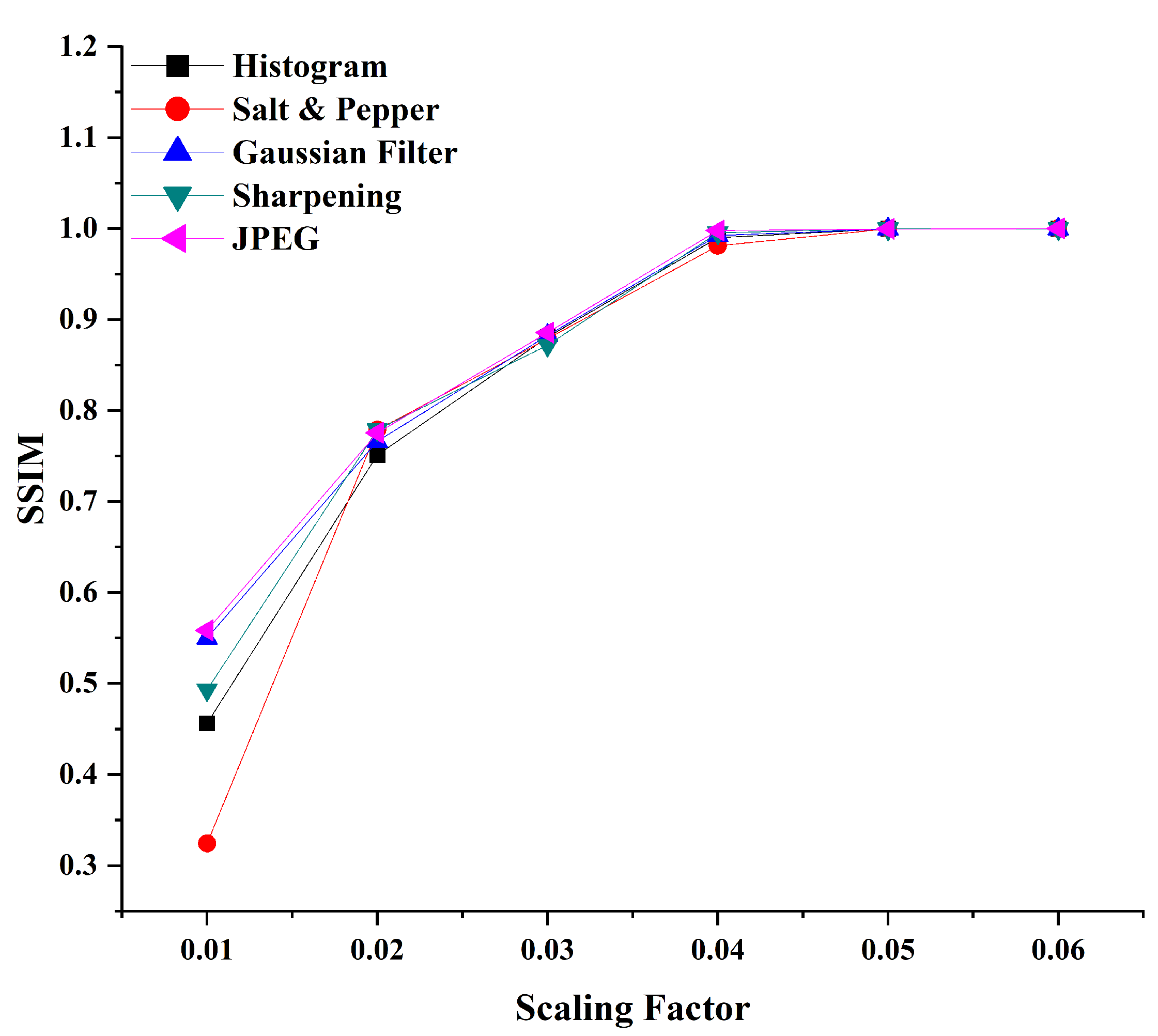
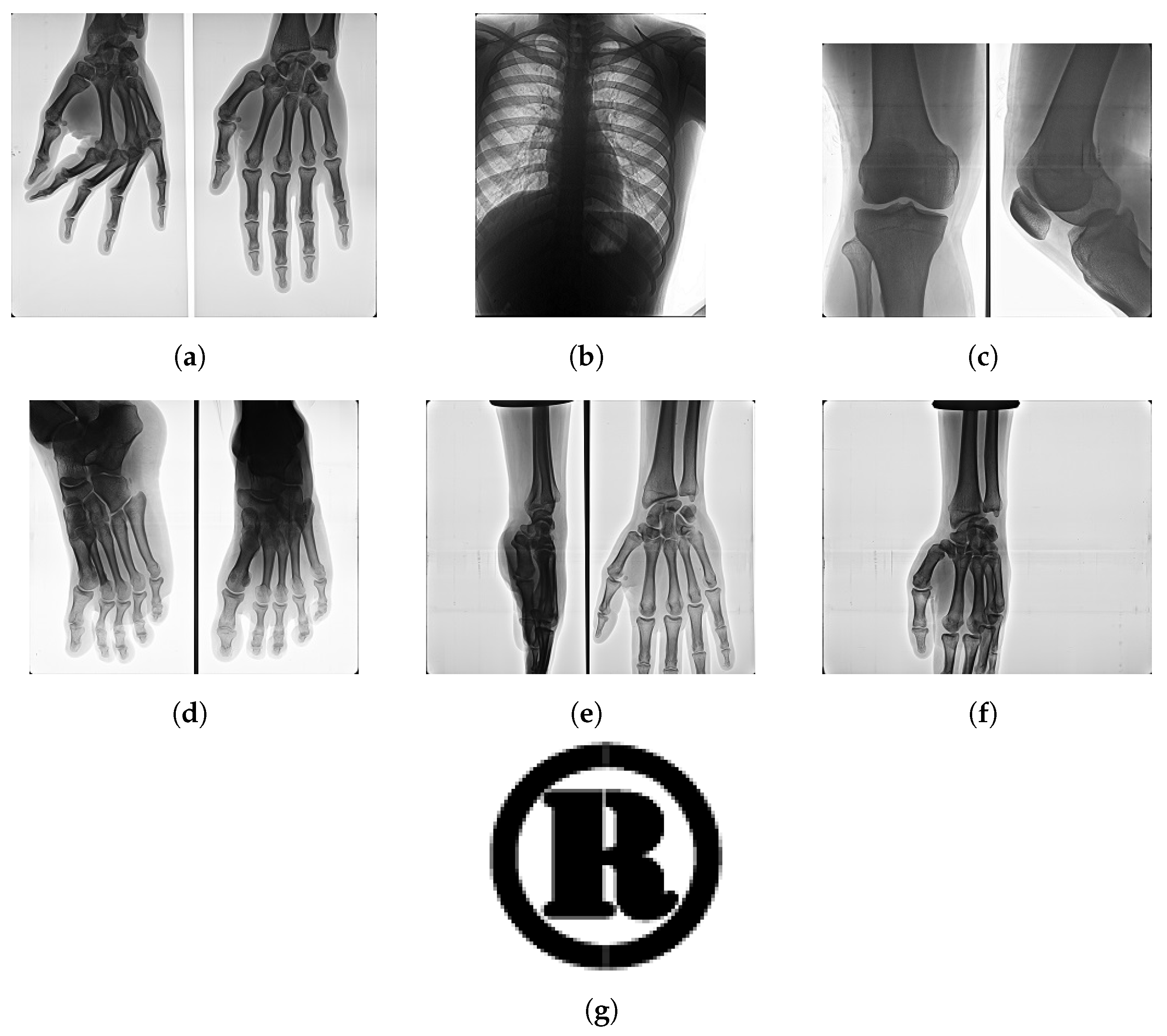


| SF | Histogram | Salt and Pepper | Gaussian Filter | Sharpening | JPEG |
|---|---|---|---|---|---|
| 0.01 | 25.0125 | 27.4512 | 32.0125 | 37.2235 | 42.2234 |
| 0.02 | 26.2323 | 28.2356 | 32.0126 | 37.9815 | 42.5678 |
| 0.03 | 26.4512 | 28.2365 | 35.4589 | 38.5642 | 42.7787 |
| 0.04 | 27.3521 | 30.3312 | 35.6201 | 38.7886 | 43.1256 |
| 0.05 | 273528 | 30.3312 | 36.8011 | 39.1563 | 43.1187 |
| 0.06 | 27.6621 | 31.4589 | 36.8011 | 39.2563 | 43.8920 |
| SF | Histogram | Salt and Pepper | Gaussian Filter | Sharpening | JPEG |
|---|---|---|---|---|---|
| 0.01 | 0.4563 | 0.3245 | 0.5501 | 0.4933 | 0.5586 |
| 0.02 | 0.7512 | 0.7789 | 0.7663 | 0.7789 | 0.7756 |
| 0.03 | 0.8809 | 0.8791 | 0.8828 | 0.8719 | 0.8856 |
| 0.04 | 0.9901 | 0.9812 | 0.9923 | 0.9956 | 0.9979 |
| 0.05 | 0.9998 | 0.9998 | 0.9996 | 0.9998 | 0.9997 |
| 0.06 | 1.0000 | 1.0000 | 0.9997 | 0.9999 | 1.0000 |
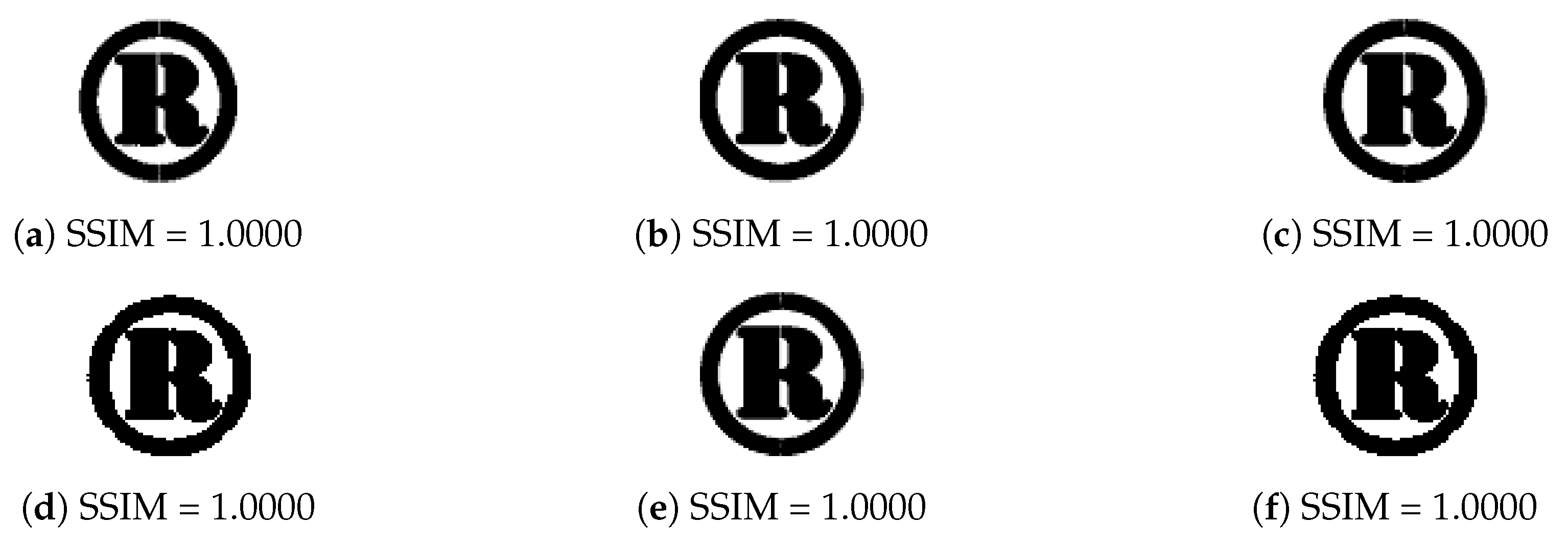
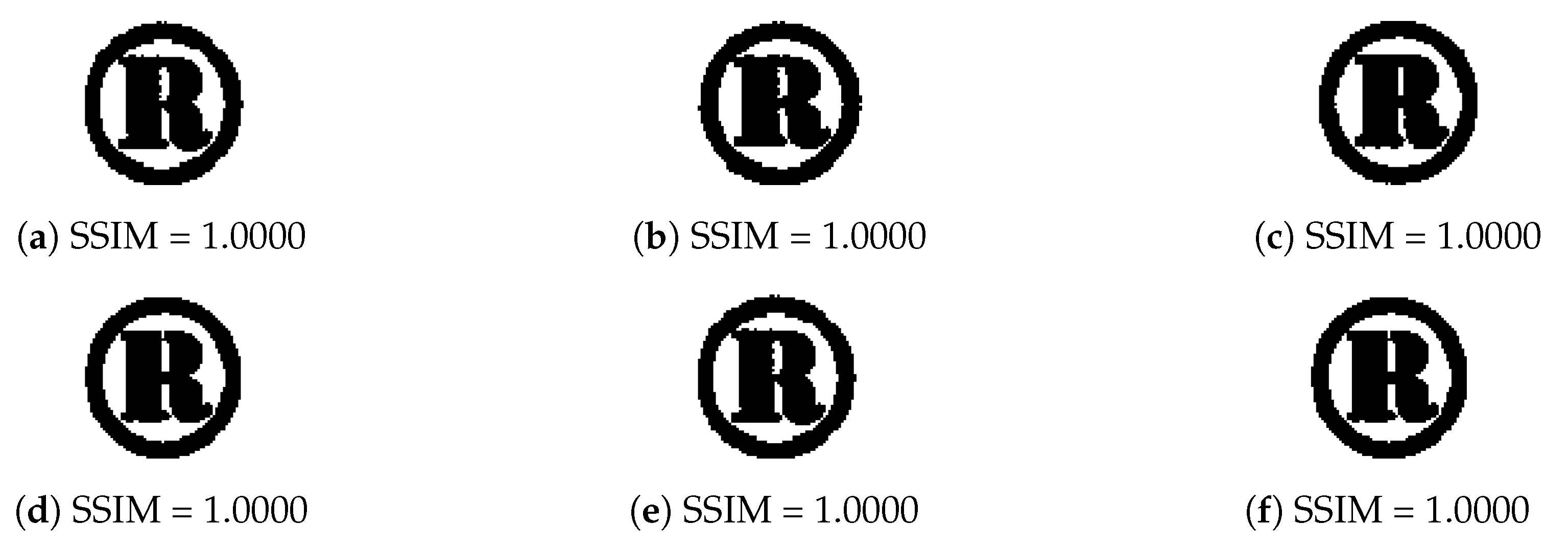
| Evaluation Matrics | (a) | (b) | (c) | (d) | (e) | (f) | (g) |
|---|---|---|---|---|---|---|---|
| Watermarked Image | PSNR | 58.6123 | 58.6122 | 58.6122 | 58.6118 | 58.6121 | 58.6121 |
| SSIM | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | |
| NC | 0.9991 | 0.9991 | 0.9992 | 0.9991 | 0.9993 | 0.9991 | |
| Extracted Watermark | SSIM | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 |
| NC | 0.9988 | 0.9989 | 0.9987 | 0.9988 | 0.9986 | 0.9987 |
| Image Name | ||||||
|---|---|---|---|---|---|---|
| SF | (a) | (b) | (c) | (d) | (e) | (f) |
| 0.01 | 0.4563 | 0.4553 | 0.4563 | 0.4534 | 0.4566 | 0.4566 |
| 0.02 | 0.7512 | 0.7512 | 0.7522 | 0.7532 | 0.7522 | 0.7512 |
| 0.03 | 08809 | 0.8811 | 0.8809 | 0.8811 | 0.8809 | 0.8809 |
| 0.04 | 0.9901 | 0.9901 | 0.9901 | 0.9901 | 0.9901 | 0.9901 |
| 0.05 | 0.9998 | 0.9998 | 0.9998 | 0.9998 | 0.9998 | 0.9998 |
| 0.06 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 |
| Image Name | ||||||
|---|---|---|---|---|---|---|
| SF | (a) | (b) | (c) | (d) | (e) | (f) |
| 0.01 | 0.3245 | 0.3234 | 0.3242 | 0.3298 | 0.3245 | 0.3235 |
| 0.02 | 0.7789 | 0.7799 | 0.7783 | 0.7789 | 0.7799 | 0.7788 |
| 0.03 | 0.8791 | 0.8796 | 0.8789 | 0.8795 | 0.8797 | 0.8792 |
| 0.04 | 0.9812 | 0.9823 | 0.9823 | 0.9825 | 0.9823 | 0.9812 |
| 0.05 | 0.9998 | 0.9998 | 0.9998 | 0.9998 | 0.9998 | 0.9998 |
| 0.06 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 |
| Image Name | ||||||
|---|---|---|---|---|---|---|
| SF | (a) | (b) | (c) | (d) | (e) | (f) |
| 0.01 | 0.5501 | 0.5501 | 0.5501 | 0.5501 | 0.5501 | 0.5501 |
| 0.02 | 0.7663 | 0.7663 | 0.7663 | 0.7663 | 0.7663 | 0.7663 |
| 0.03 | 0.8828 | 0.8828 | 0.8828 | 0.8828 | 0.8828 | 0.8828 |
| 0.04 | 0.9923 | 0.9923 | 0.9923 | 0.9923 | 0.9923 | 0.9923 |
| 0.05 | 0.9996 | 0.9996 | 0.9996 | 0.9996 | 0.9996 | 0.9996 |
| 0.06 | 0.9997 | 0.9997 | 0.9997 | 0.9997 | 0.9997 | 0.9997 |
| Image Name | ||||||
|---|---|---|---|---|---|---|
| SF | (a) | (b) | (c) | (d) | (e) | (f) |
| 0.01 | 0.5586 | 0.5591 | 0.5587 | 0.5586 | 0.5586 | 0.5588 |
| 0.02 | 0.7756 | 0.7759 | 0.7756 | 0.7751 | 0.7756 | 0.7758 |
| 0.03 | 0.8856 | 0.8855 | 0.8857 | 0.8851 | 0.8856 | 0.8856 |
| 0.04 | 0.9979 | 0.9971 | 0.9969 | 0.9979 | 0.9969 | 0.9979 |
| 0.05 | 0.9997 | 0.9997 | 0.9997 | 0.9997 | 0.9997 | 0.9997 |
| 0.06 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 | 1.0000 |
| Proposed Work | [7] | [10] | [31] | [32] | |
|---|---|---|---|---|---|
| SSIM | 1.0000 | 0.9961 | - | - | - |
| NC | 0.9988 | 0.9985 | 0.9993 | 0.9869 | 1.0000 |
| Attack | Proposed Work | [7] | [10] | [31] | [32] | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| SSIM | NC | SSIM | NC | SSIM | NC | SSIM | NC | SSIM | NC | |
| Histogram Equalization | 1.0000 | 0.6221 | 0.9961 | 0.5650 | - | 0.7223 | - | - | - | - |
| Salt and Pepper | 1.0000 | 0.9879 | 0.9923 | 0.9981 | - | 09251 | - | 0.9938 | 0.9260 | 0.9997 |
| Gaussian Noise | 0.9997 | 0.9889 | 0.9816 | 0.9920 | - | 0.5918 | - | 0.9738 | 0.9314 | 0.9997 |
| JPEG Compression | 1.0000 | 0.9941 | 0.9910 | 0.9825 | - | - | - | - | 0.9314 | 0.9997 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pallaw, V.K.; Singh, K.U.; Kumar, A.; Singh, T.; Swarup, C.; Goswami, A. A Robust Medical Image Watermarking Scheme Based on Nature-Inspired Optimization for Telemedicine Applications. Electronics 2023, 12, 334. https://doi.org/10.3390/electronics12020334
Pallaw VK, Singh KU, Kumar A, Singh T, Swarup C, Goswami A. A Robust Medical Image Watermarking Scheme Based on Nature-Inspired Optimization for Telemedicine Applications. Electronics. 2023; 12(2):334. https://doi.org/10.3390/electronics12020334
Chicago/Turabian StylePallaw, Vijay Krishna, Kamred Udham Singh, Ankit Kumar, Teekam Singh, Chetan Swarup, and Anjali Goswami. 2023. "A Robust Medical Image Watermarking Scheme Based on Nature-Inspired Optimization for Telemedicine Applications" Electronics 12, no. 2: 334. https://doi.org/10.3390/electronics12020334
APA StylePallaw, V. K., Singh, K. U., Kumar, A., Singh, T., Swarup, C., & Goswami, A. (2023). A Robust Medical Image Watermarking Scheme Based on Nature-Inspired Optimization for Telemedicine Applications. Electronics, 12(2), 334. https://doi.org/10.3390/electronics12020334






