Robust Zero Watermarking Algorithm for Medical Images Based on Improved NasNet-Mobile and DCT
Abstract
1. Introduction
- (1)
- Proposed a zero-watermarking algorithm for medical images based on improved NasNet-Mobile and DCT.
- (2)
- Double encryption of the watermark using Chen chaos mapping and Arnold transform dislocation.
- (3)
- Changing the NasNet-Mobile network structure to train the medical image dataset and extract robust features.
- (4)
- The proposed algorithm can withstand most of the conventional and geometric attacks and the algorithm is robust.
2. Fundamental Principles
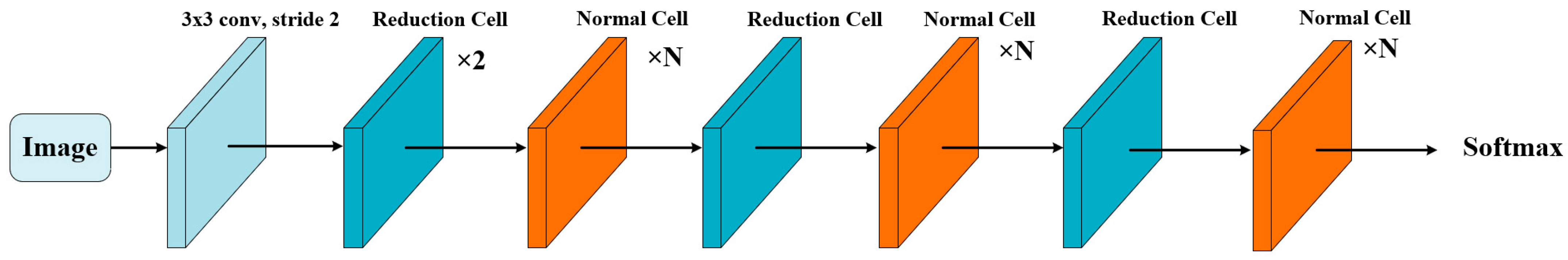
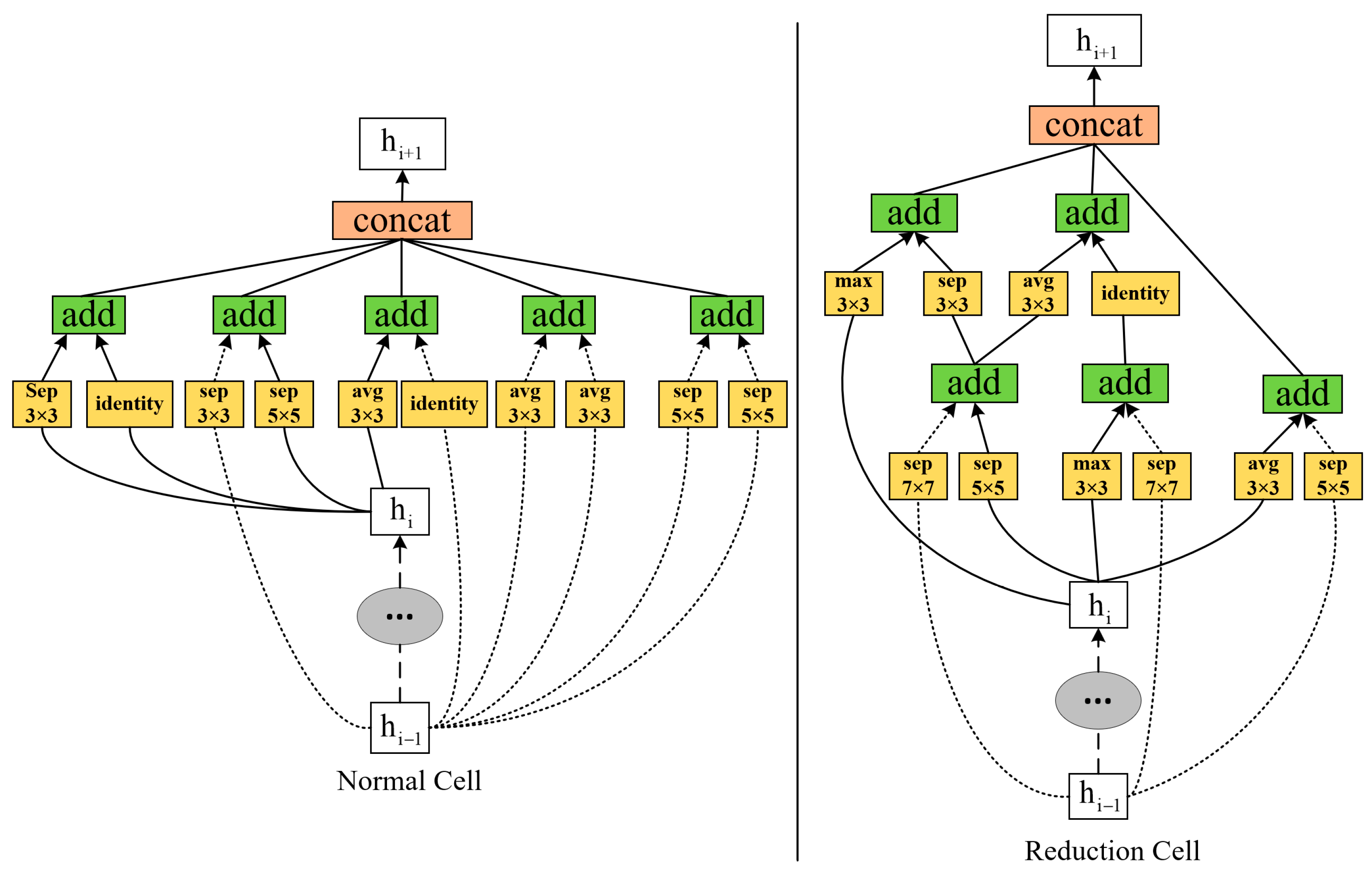
2.1. NasNet-Mobile Convolutional Neural Network
2.2. Discrete Cosine Transform (DCT)
2.3. Chen Chaotic System
2.4. Arnold Mapping
3. Zero Watermark Algorithm
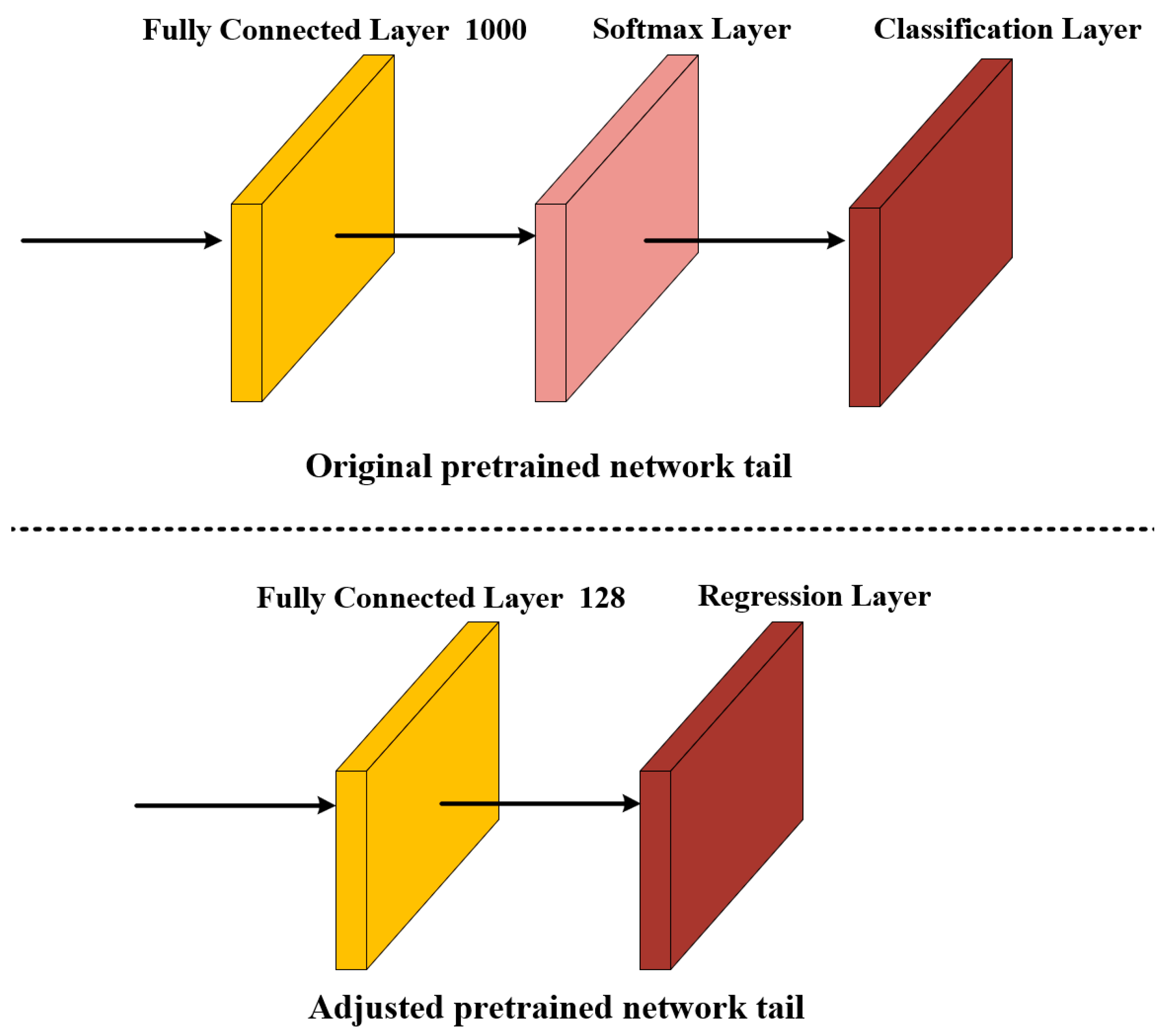
3.1. NasNet-Mobile Pre-Trained Network Migration Learning
3.1.1. NasNet-Mobile Network Restructuring
3.1.2. Dataset Creation
3.1.3. Training Network
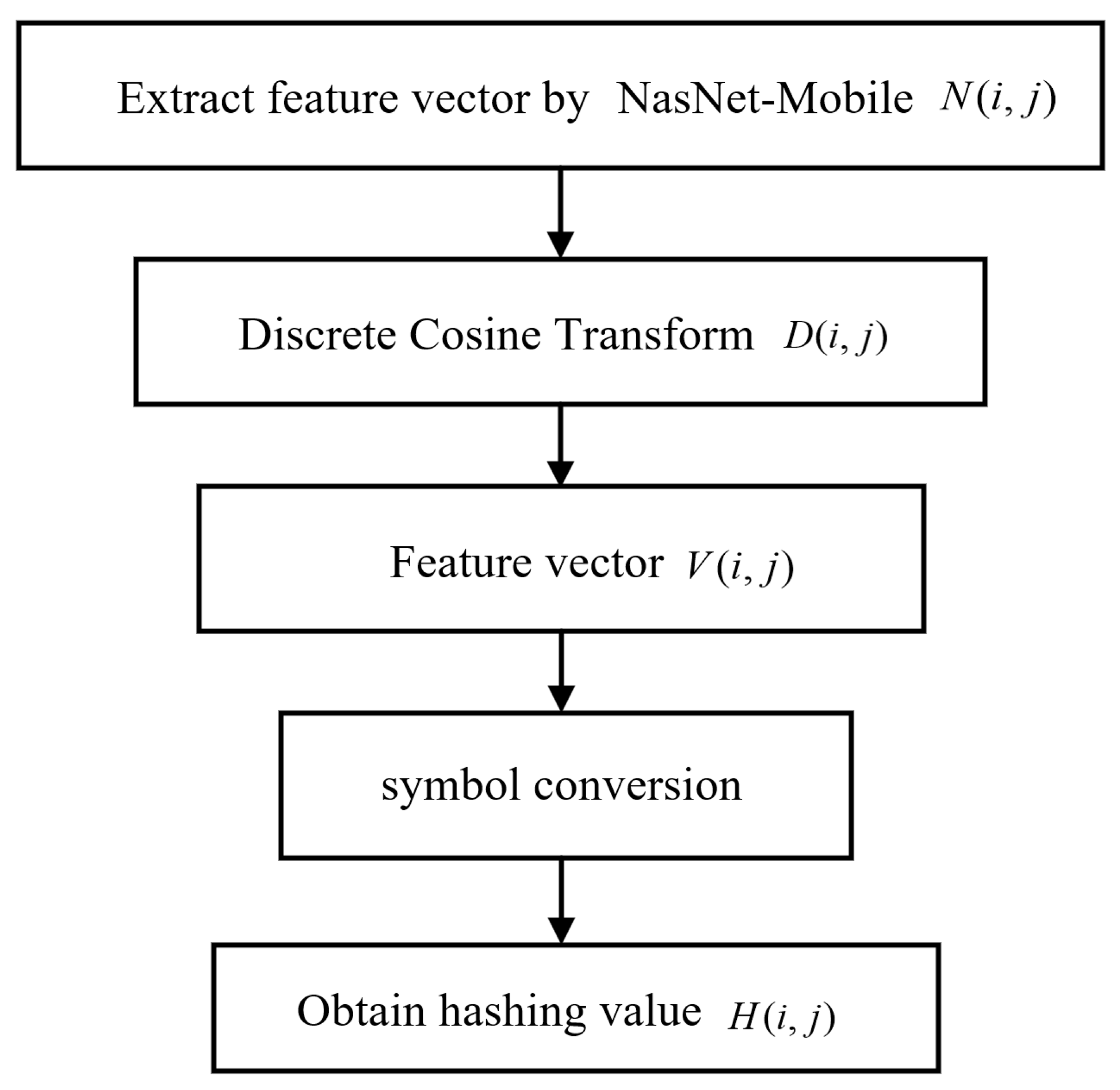
3.2. NasNet-Mobile Feature Extraction
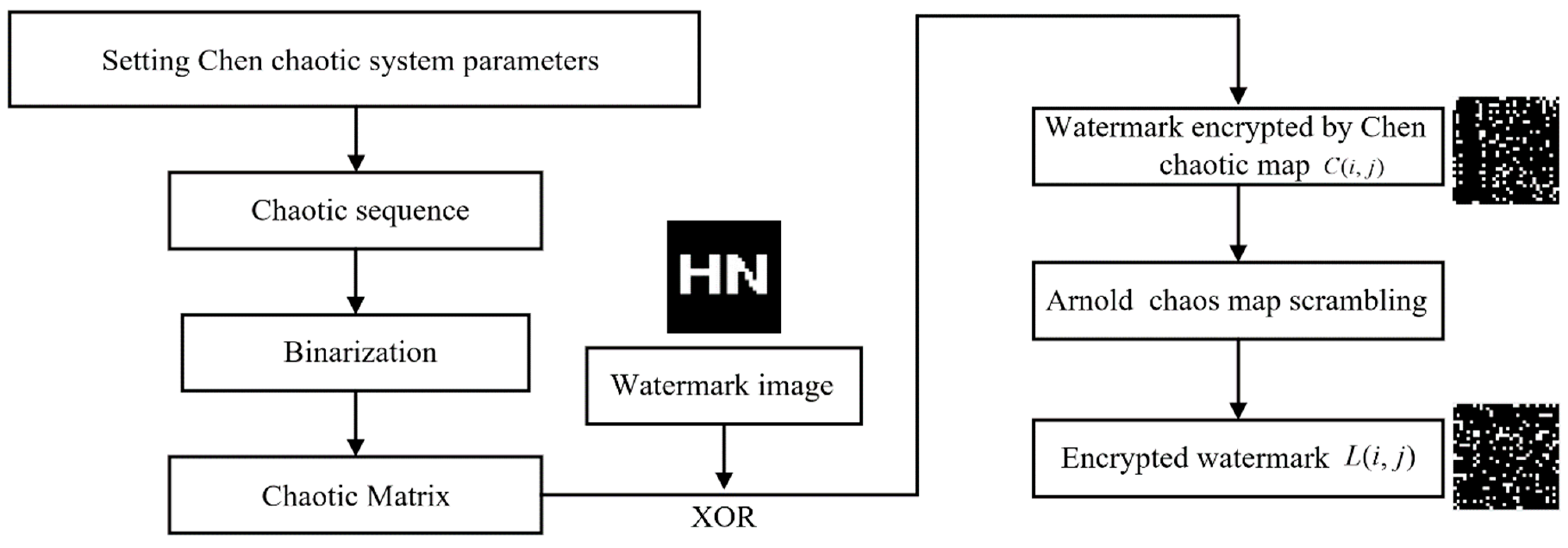
3.3. Watermark Encryption
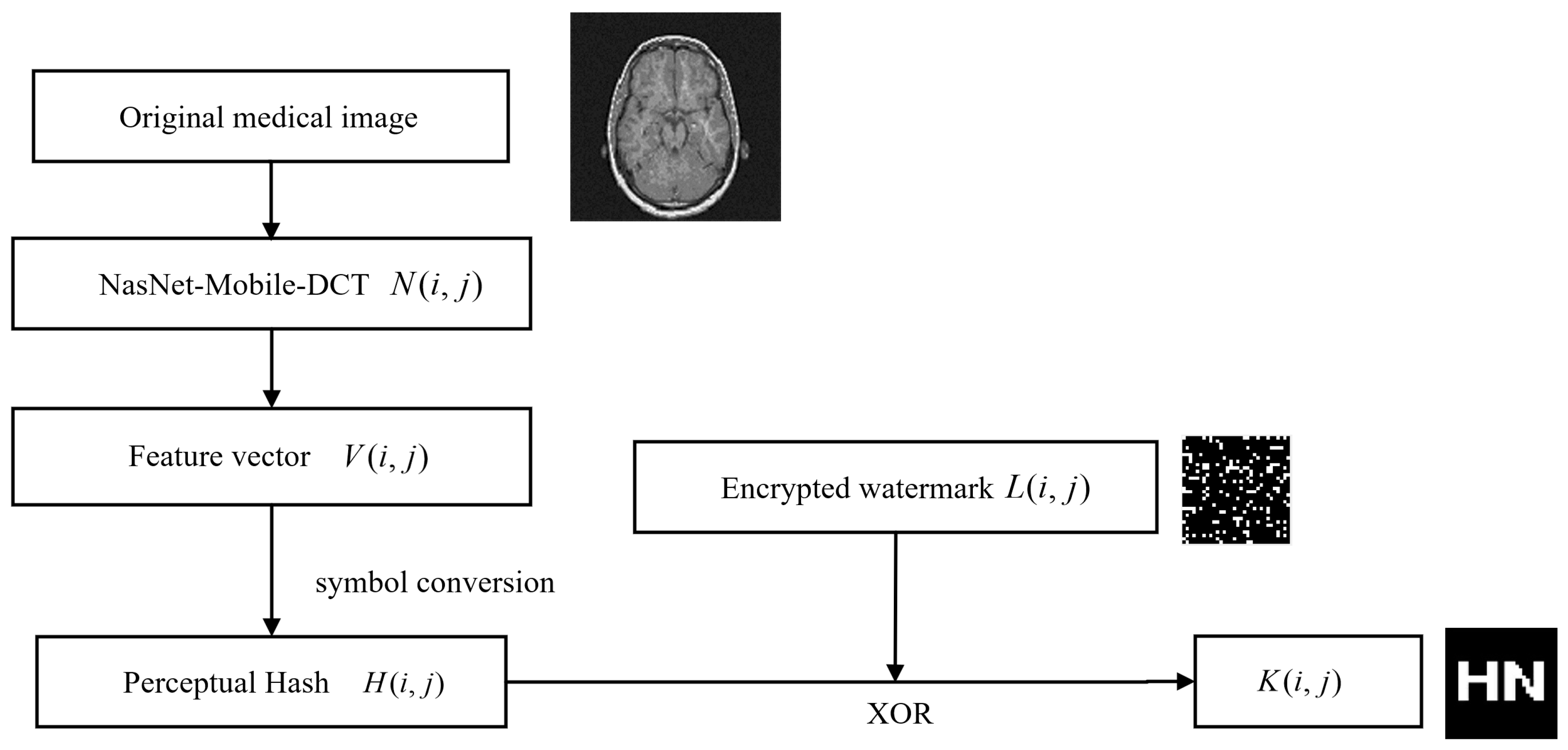
3.4. Embedding Watermarks
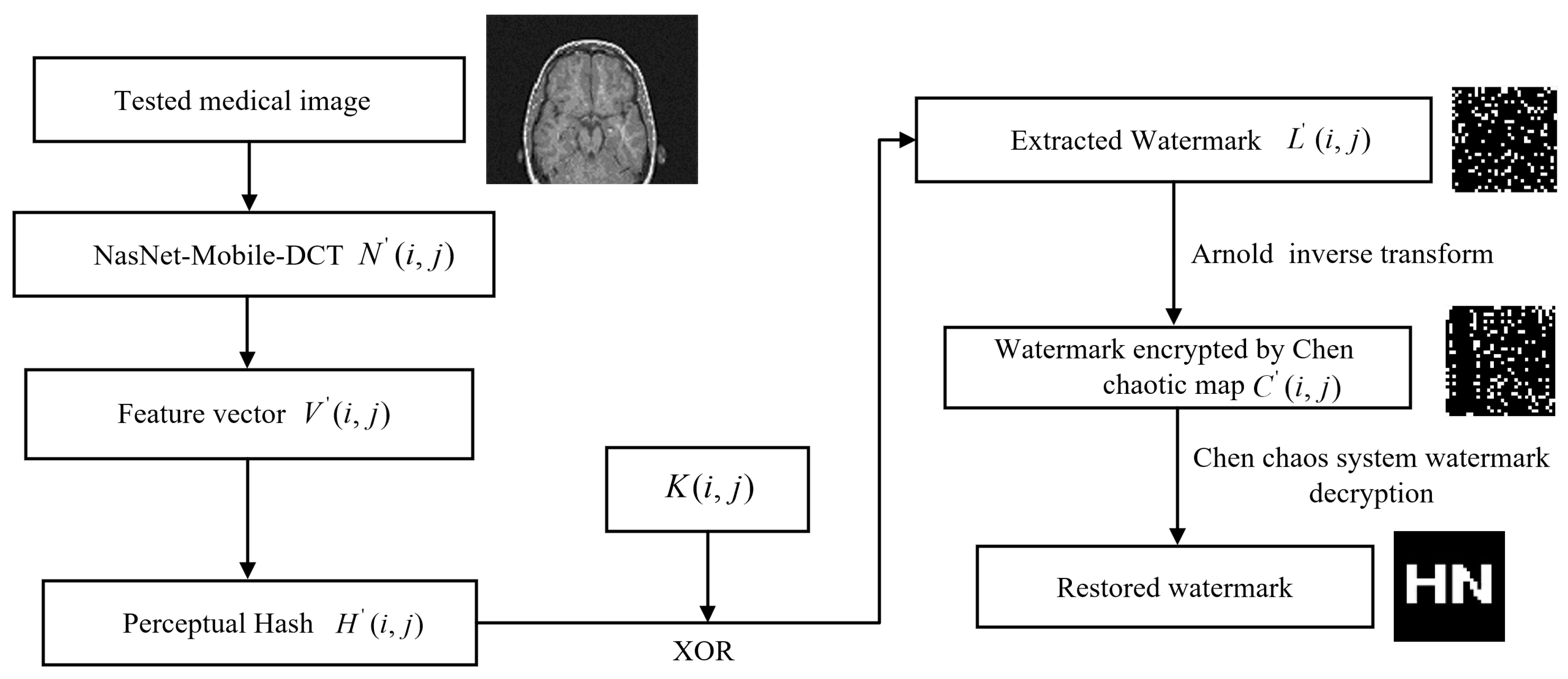
3.5. Watermark Extraction and Decryption
4. Experiments and Results
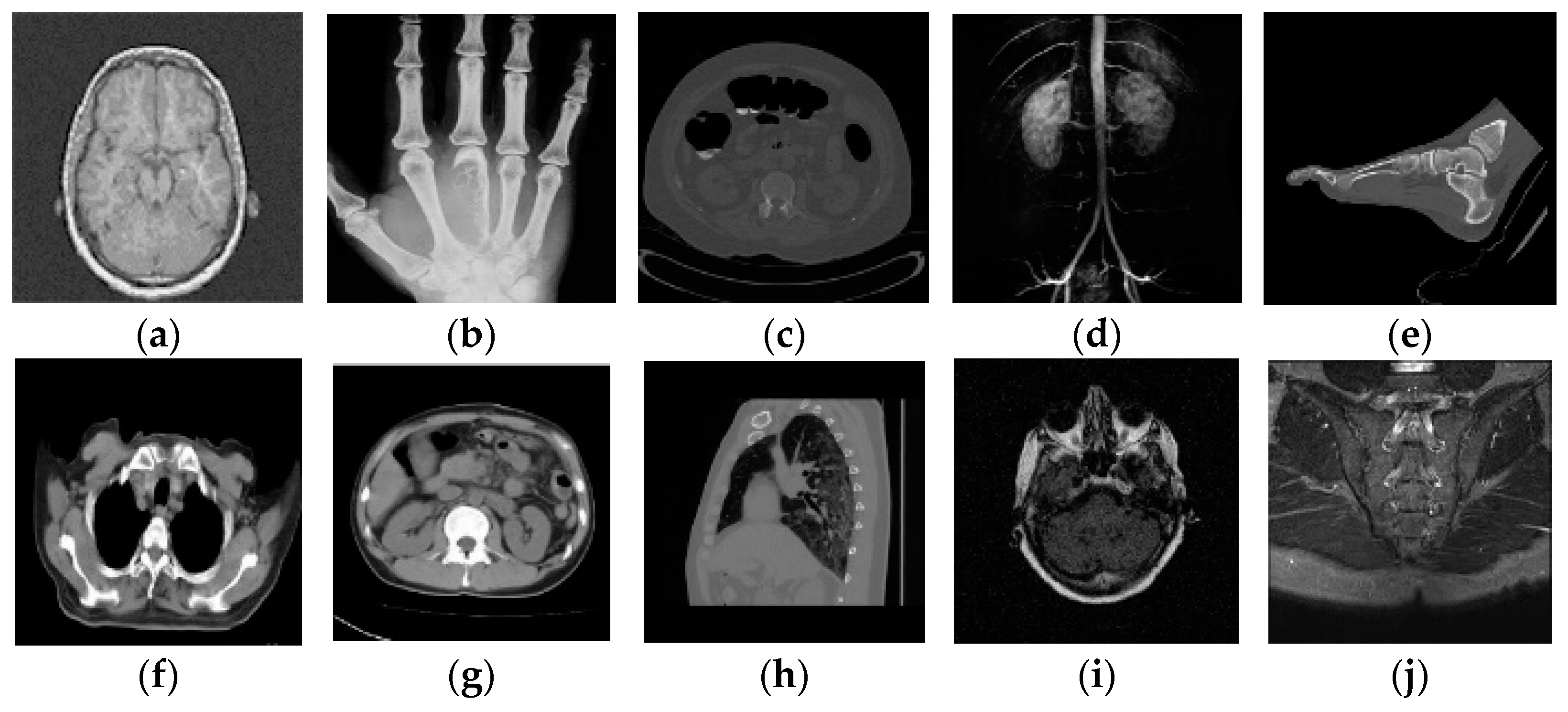
4.1. Testing Different Images
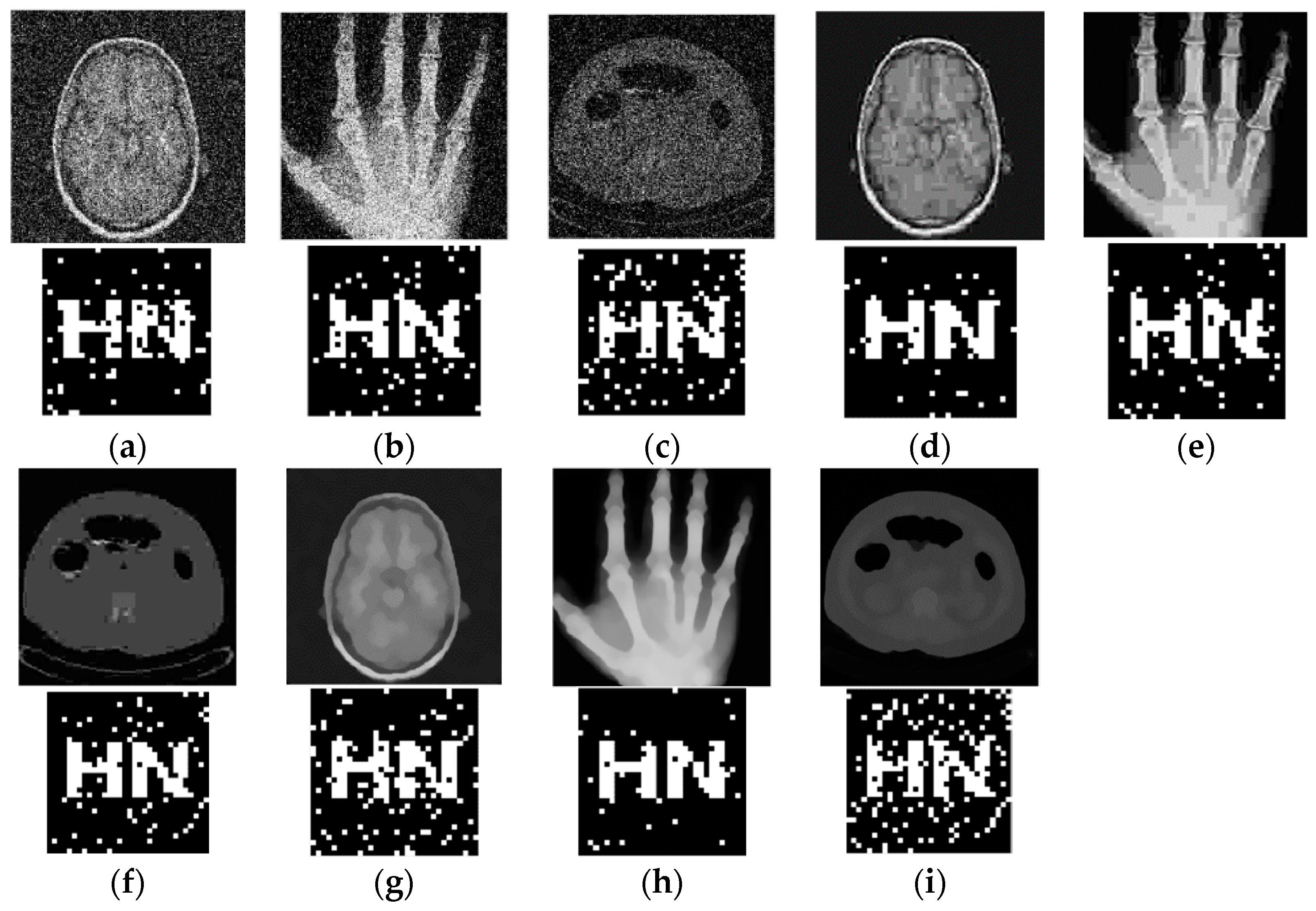
4.2. Conventional Attacks
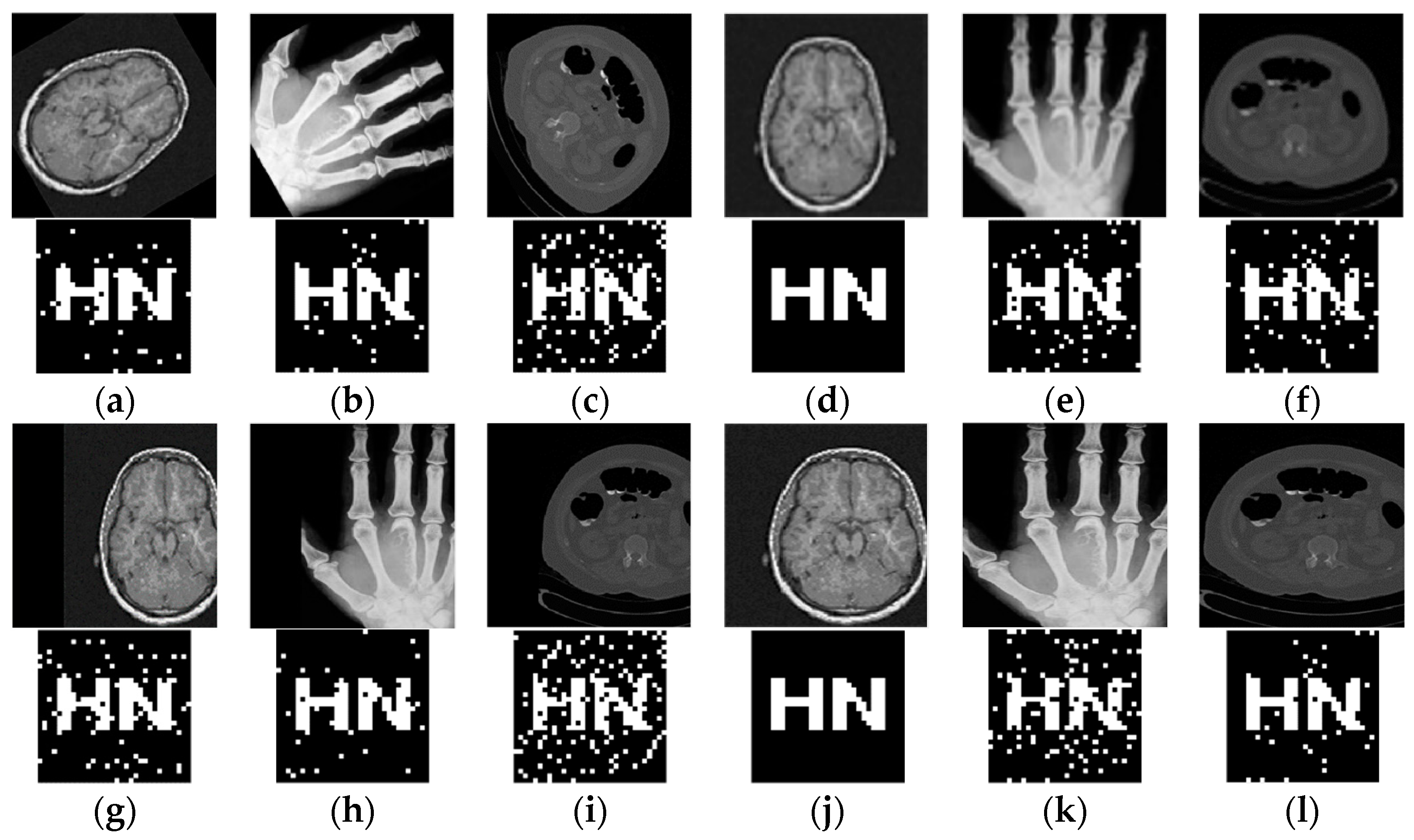
4.3. Geometric Attacks
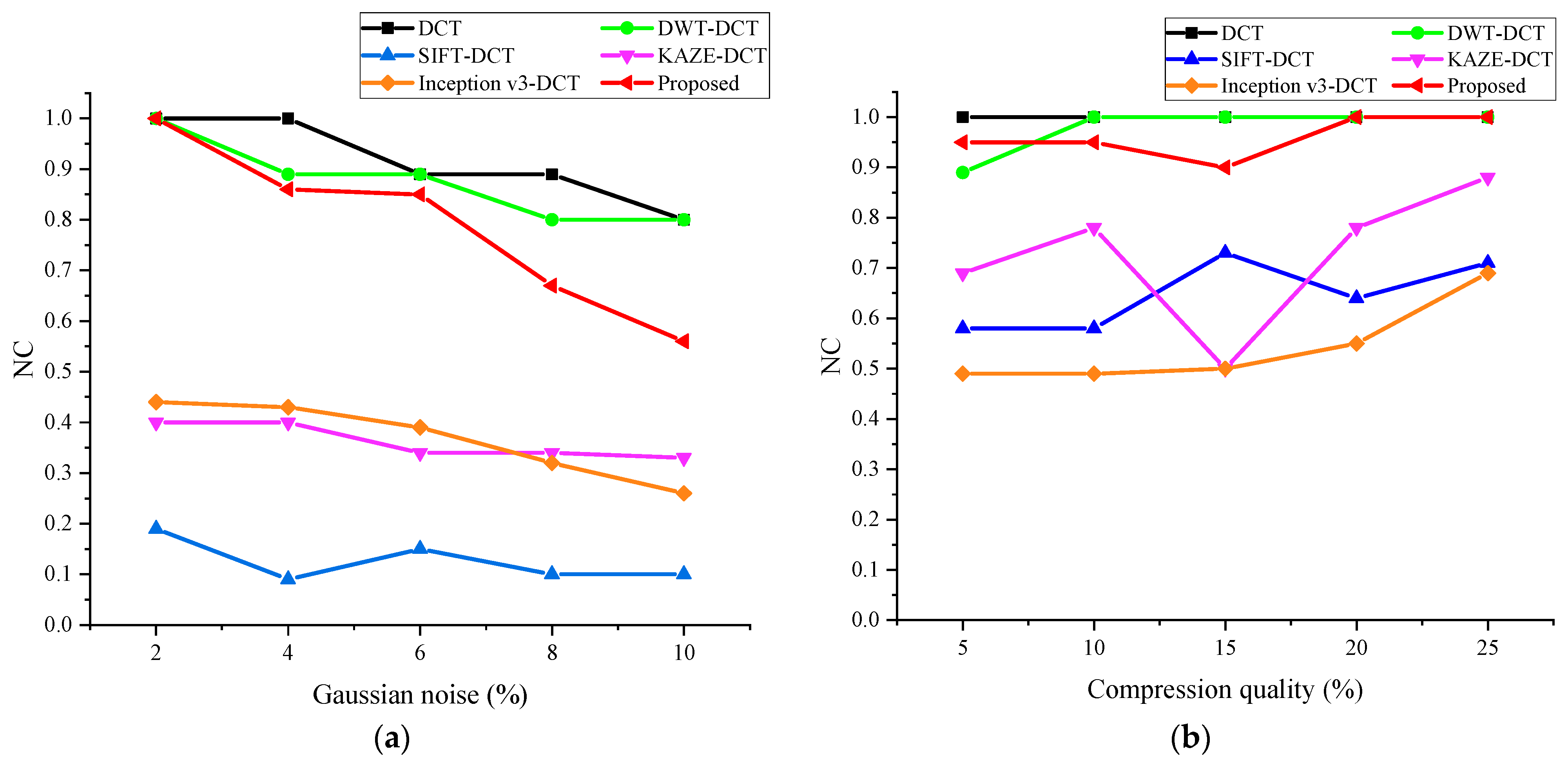
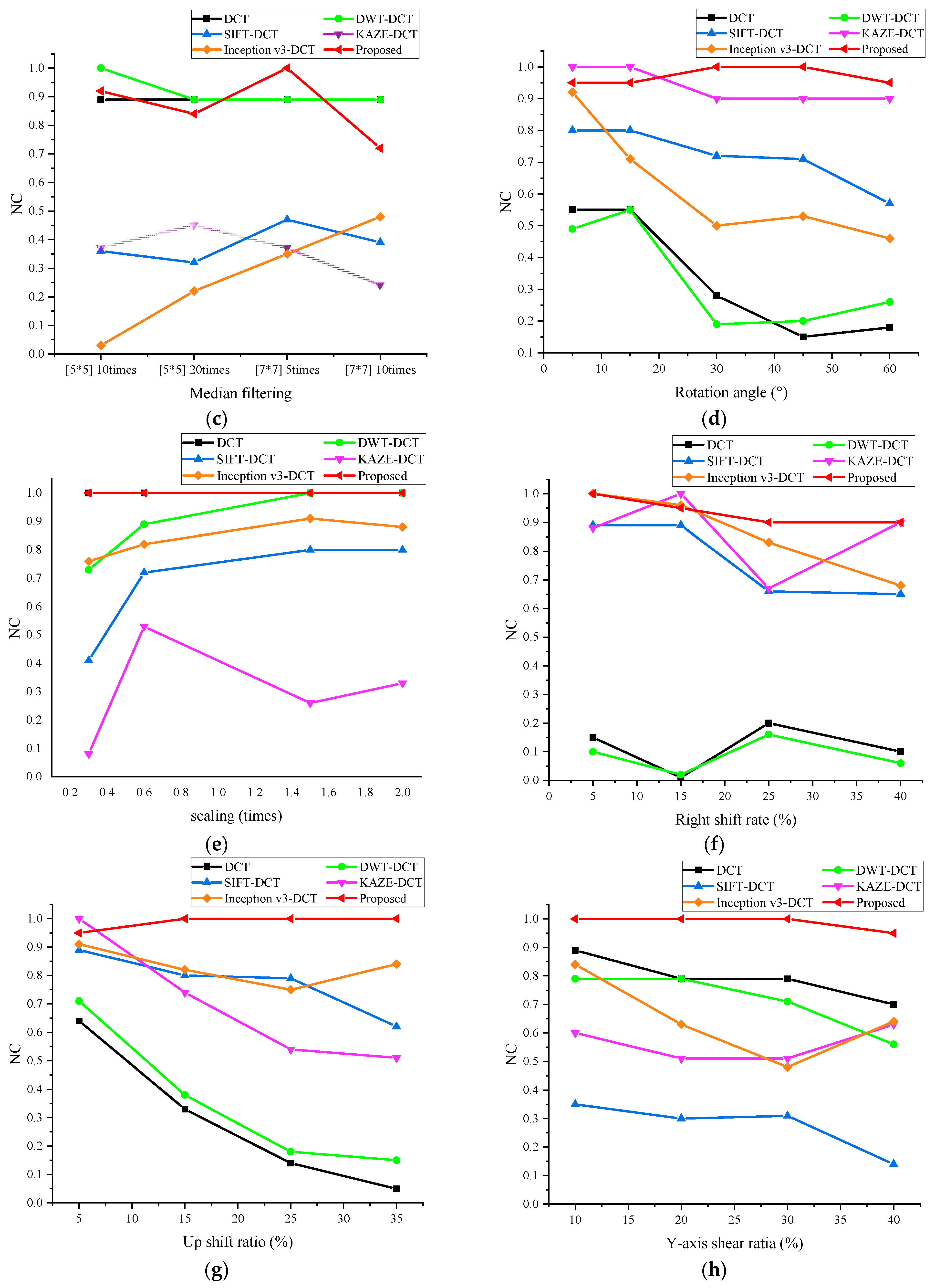
4.4. Algorithm Comparison
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Evsutin, O.; Melman, A.; Meshcheryakov, R. Digital Steganography and Watermarking for Digital Images: A Review of Current Research Directions. IEEE Access 2020, 8, 166589–166611. [Google Scholar] [CrossRef]
- Tian, Y.; Fu, S. A Descriptive Framework for the Field of Deep Learning Applications in Medical Images. Knowl.-Based Syst. 2020, 210, 106445. [Google Scholar] [CrossRef]
- Amine, K.; Fares, K.; Redouane, K.M.; Salah, E. Medical Image Watermarking for Telemedicine Application Security. J. Circuits Syst. Comput. 2022, 31, 2250097. [Google Scholar] [CrossRef]
- Venkateswarlu, I.B. Fast Medical Image Security Using Color Channel Encryption. Braz. Arch. Biol. Technol. 2020, 63, e20180473. [Google Scholar] [CrossRef]
- Thabit, R. Review of Medical Image Authentication Techniques and Their Recent Trends. Multimed. Tools Appl. 2021, 80, 13439–13473. [Google Scholar] [CrossRef]
- Raj, N.R.N.; Shreelekshmi, R. A Survey on Fragile Watermarking Based Image Authentication Schemes. Multimed. Tools Appl. 2021, 80, 19307–19333. [Google Scholar] [CrossRef]
- Verma, V.S.; Jha, R.K. An Overview of Robust Digital Image Watermarking. IETE Tech. Rev. (Inst. Electron. Telecommun. Eng. India) 2015, 32, 479–496. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, B.K. Entropy Based Spatial Domain Image Watermarking and Its Performance Analysis. Multimed. Tools Appl. 2021, 80, 9315–9331. [Google Scholar] [CrossRef]
- Wang, H.; Su, Q. A Color Image Watermarking Method Combined QR Decomposition and Spatial Domain. Multimed. Tools Appl. 2022, 81, 37895–37916. [Google Scholar] [CrossRef]
- Basha, S.H.; Jaison, B. A Novel Secured Euclidean Space Points Algorithm for Blind Spatial Image Watermarking. EURASIP J. Image Video Process. 2022, 2022, 21. [Google Scholar] [CrossRef]
- Cao, H.; Hu, F.; Sun, Y.; Chen, S.; Su, Q. Robust and Reversible Color Image Watermarking Based on DFT in the Spatial Domain. Optik 2022, 262, 169319. [Google Scholar] [CrossRef]
- Chopra, A.; Gupta, S.; Dhall, S. Analysis of Frequency Domain Watermarking Techniques in Presence of Geometric and Simple Attacks. Multimed. Tools Appl. 2020, 79, 501–554. [Google Scholar] [CrossRef]
- Tian, C.; Wen, R.-H.; Zou, W.-P.; Gong, L.-H. Robust and Blind Watermarking Algorithm Based on DCT and SVD in the Contourlet Domain. Multimed. Tools Appl. 2020, 79, 7515–7541. [Google Scholar] [CrossRef]
- Tang, M.; Zhou, F. A Robust and Secure Watermarking Algorithm Based on DWT and SVD in the Fractional Order Fourier Transform Domain. Array 2022, 15, 100230. [Google Scholar] [CrossRef]
- Liu, J.; Li, J.; Cheng, J.; Ma, J.; Sadiq, N.; Han, B.; Geng, Q.; Ai, Y. A Novel Robust Watermarking Algorithm for Encrypted Medical Image Based on DTCWT-DCT and Chaotic Map. Comput. Mater. Contin. 2019, 61, 889–910. [Google Scholar]
- Jose, A.; Subramaniam, K. Comparative Analysis of Reversible Data Hiding Schemes. IET Image Process. 2020, 14, 2064–2073. [Google Scholar] [CrossRef]
- Lowe, D.G. Distinctive Image Features from Scale-Invariant Keypoints. Int. J. Comput. Vis. 2004, 60, 91–110. [Google Scholar] [CrossRef]
- Bay, H.; Ess, A.; Tuytelaars, T.; Van Gool, L. Speeded-Up Robust Features (SURF). Comput. Vis. Image Underst. 2008, 110, 346–359. [Google Scholar] [CrossRef]
- Alcantarilla, P.F.; Bartoli, A.; Davison, A.J. KAZE Features. In Proceedings of the Computer Vision—ECCV 2012, Florence, Italy, 7–13 October 2012; Fitzgibbon, A., Lazebnik, S., Perona, P., Sato, Y., Schmid, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 214–227. [Google Scholar]
- Sjöstrand, T.; Mrenna, S.; Skands, P. A Brief Introduction to PYTHIA 8.1. Comput. Phys. Commun. 2008, 178, 852–867. [Google Scholar] [CrossRef]
- Rublee, E.; Rabaud, V.; Konolige, K.; Bradski, G. ORB: An Efficient Alternative to SIFT or SURF. In Proceedings of the 2011 International Conference on Computer Vision, Barcelona, Spain, 6–13 November 2011; pp. 2564–2571. [Google Scholar]
- Leutenegger, S.; Chli, M.; Siegwart, R.Y. BRISK: Binary Robust Invariant Scalable Keypoints. In Proceedings of the 2011 International Conference on Computer Vision, Barcelona, Spain, 6–13 November 2011; pp. 2548–2555. [Google Scholar]
- Hamidi, M.; El Haziti, M.; Cherifi, H.; El Hassouni, M. A Hybrid Robust Image Watermarking Method Based on Dwt-Dct and Sift for Copyright Protection. J. Imaging 2021, 7, 218. [Google Scholar] [CrossRef]
- Soualmi, A.; Alti, A.; Laouamer, L. An Imperceptible Watermarking Scheme for Medical Image Tamper Detection. Int. J. Inf. Secur. Priv. 2022, 16, 18. [Google Scholar] [CrossRef]
- Zeng, C.; Liu, J.; Li, J.; Cheng, J.; Zhou, J.; Nawaz, S.A.; Xiliang, X.; Bhatti, U.A. Multi-Watermarking Algorithm for Medical Image Based on KAZE-DCT. J. Ambient. Intell. Humaniz. Comput. 2022, 1–9. [Google Scholar] [CrossRef]
- Meng, R.; Cui, Q.; Yuan, C. A Survey of Image Information Hiding Algorithms Based on Deep Learning. CMES Comput. Model. Eng. Sci. 2018, 117, 425–454. [Google Scholar] [CrossRef]
- Bao, Z.; Xue, R. Survey on Deep Learning Applications in Digital Image Security. Opt. Eng. 2021, 60, 120901. [Google Scholar] [CrossRef]
- Chacko, A.; Chacko, S. Deep Learning-Based Robust Medical Image Watermarking Exploiting DCT and Harris Hawks Optimization. Int. J. Intell. Syst. 2022, 37, 4810–4844. [Google Scholar] [CrossRef]
- Fan, Y.; Li, J.; Bhatti, U.A.; Shao, C.; Gong, C.; Cheng, J.; Chen, Y. A Multi-Watermarking Algorithm for Medical Images Using Inception V3 and DCT. Comput. Mater. Contin. 2023, 74, 1279–1302. [Google Scholar]
- Zhang, W.; Li, J.; Bhatti, U.A.; Liu, J.; Zheng, J.; Chen, Y.-W. Robust Multi-Watermarking Algorithm for Medical Images Based on GoogLeNet and Henon Map. Comput. Mater. Contin. 2023, 75, 565–586. [Google Scholar] [CrossRef]
- Zoph, B.; Vasudevan, V.; Shlens, J.; Le, Q.V. Learning Transferable Architectures for Scalable Image Recognition. In Proceedings of the 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Salt Lake City, UT, USA, 18–23 June 2018; IEEE: New York, NY, USA, 2018; pp. 8697–8710. [Google Scholar]
- Liu, Y.L.; Li, J.B. DCT and Logistic Map Based Multiple Robust Watermarks for Medical Image. Appl. Res. Comput. 2013, 30, 3430–3433. [Google Scholar]
- Liu, Y.; Li, J. The Medical Image Watermarking Algorithm Using DWT-DCT and Logistic. In Proceedings of the 2012 7th International Conference on Computing and Convergence Technology (ICCCT), Seoul, Republic of Korea, 3–5 December 2012; pp. 599–603. [Google Scholar]
- Fang, Y.; Liu, J.; Li, J.; Cheng, J.; Hu, J.; Yi, D.; Xiao, X.; Bhatti, U.A. Robust Zero-Watermarking Algorithm for Medical Images Based on SIFT and Bandelet-DCT. Multimed. Tools Appl. 2022, 81, 16863–16879. [Google Scholar] [CrossRef]

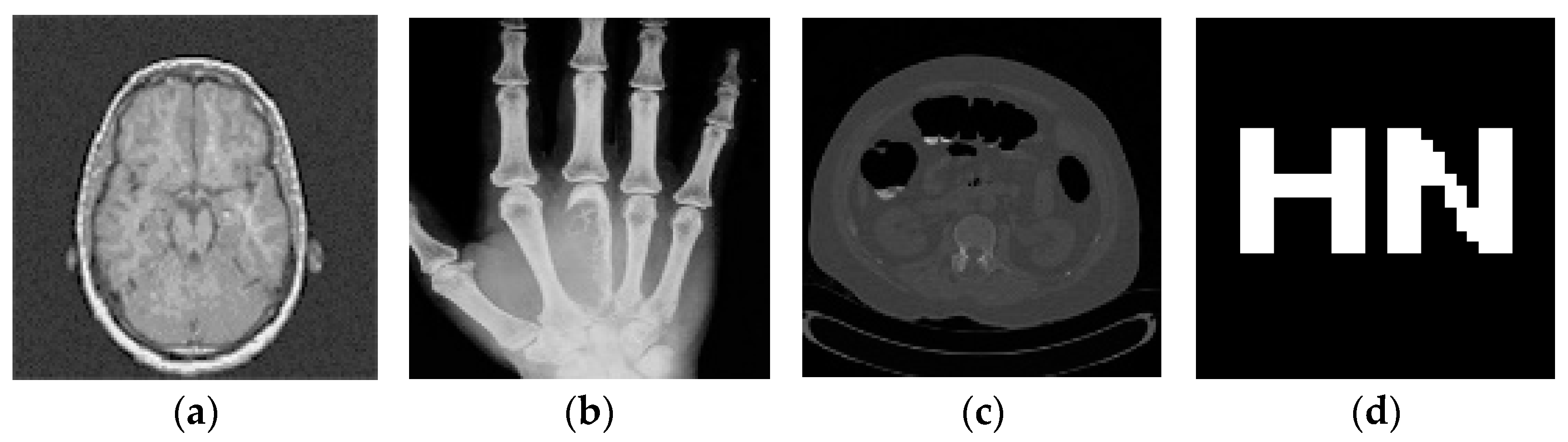
| Enhanced Type | Intensity | Number of New Images |
|---|---|---|
| JPEG compression (%) | 5, 10, 15, 20 | 4 |
| Gaussian noise (%) | 2, 4, 6, 8, 10, 12, 14, 16 | 8 |
| Median filter [3 × 3] (times) | 5, 10, 15, 20 | 4 |
| Median filter [5 × 5] (times) | 5, 10, 15, 20 | 4 |
| Median filter [7 × 7] (times) | 5, 10, 15, 20 | 4 |
| Clockwise rotation (°) | 5, 10, 15, 20, 25, 30, 35, 40, 45, 50, 55, 60 | 12 |
| Anticlockwise rotation (°) | 5, 10, 15, 20, 25, 30, 35, 40, 45, 50, 55, 60 | 12 |
| Y-axis shear (%) | 5, 10, 15, 20, 25, 30, 35, 40 | 8 |
| Scaling | 0.2, 0.4, 0.6, 0.8, 1.0, 1.2, 1.4, 1.6, 1.8, 2.0 | 10 |
| Right-shift (%) | 5, 10, 15, 20, 25, 30, 35, 40 | 8 |
| Left-shift (%) | 5, 10, 15, 20, 25, 30, 35, 40 | 8 |
| Down-shift (%) | 5, 10, 15, 20, 25, 30, 35, 40 | 8 |
| X-axis shear (%) | 5, 10, 15, 20, 25, 30, 35, 40 | 8 |
| Up-shift (%) | 5, 10, 15, 20, 25, 30, 35, 40 | 8 |
| Image | (a) | (b) | (c) | (d) | (e) | (f) | (g) | (h) | (i) | (j) |
|---|---|---|---|---|---|---|---|---|---|---|
| (a) | 1.00 | |||||||||
| (b) | 0.14 | 1.00 | ||||||||
| (c) | 0.42 | 0.25 | 1.00 | |||||||
| (d) | 0.39 | 0.22 | 0.37 | 1.00 | ||||||
| (e) | 0.18 | 0.30 | 0.33 | 0.34 | 1.00 | |||||
| (f) | 0.41 | 0 | 0.41 | 0.41 | 0.27 | 1.00 | ||||
| (g) | 0.43 | 0.07 | 0.05 | 0.24 | 0.07 | 0.10 | 1.00 | |||
| (h) | 0.23 | 0.29 | 0.27 | 0.21 | 0.43 | 0.38 | 0.32 | 1.00 | ||
| (i) | 0.39 | 0.03 | 0.17 | 0.35 | 0.06 | 0.18 | 0.33 | 0.39 | 1.00 | |
| (j) | 0.30 | 0.03 | 0.14 | 0.10 | 0.03 | 0.23 | 0.31 | 0.23 | 0.32 | 1.00 |
| Conventional Attacks | PSNR (dB) | NC | |||||
|---|---|---|---|---|---|---|---|
| Intensity | Img1 | Img2 | Img3 | Img1 | Img2 | Img3 | |
| Gaussian noise | 0.02 | 17.81 | 16.76 | 17.29 | 1.00 | 0.93 | 0.94 |
| 0.04 | 15.12 | 14.06 | 14.55 | 0.86 | 0.93 | 0.89 | |
| 0.06 | 13.65 | 12.55 | 13.04 | 0.85 | 0.88 | 0.82 | |
| 0.08 | 12.66 | 11.42 | 12.04 | 0.67 | 0.87 | 0.76 | |
| 0.10 | 11.86 | 10.67 | 11.21 | 0.56 | 0.85 | 0.63 | |
| JPEG compression | 25% | 33.39 | 32.03 | 34.27 | 1.00 | 1.00 | 1.00 |
| 20% | 32.51 | 31.17 | 33.39 | 1.00 | 1.00 | 1.00 | |
| 15% | 31.25 | 30.03 | 32.37 | 0.90 | 0.94 | 1.00 | |
| 10% | 29.26 | 28.39 | 30.65 | 0.95 | 1.00 | 0.88 | |
| 5% | 26.46 | 25.16 | 27.68 | 0.95 | 0.86 | 0.88 | |
| Median filtering [5 × 5] | 5 (times) | 25.13 | 27.00 | 28.35 | 1.00 | 0.86 | 0.83 |
| 10 (times) | 24.29 | 25.99 | 27.60 | 0.92 | 0.92 | 0.83 | |
| 15 (times) | 23.86 | 25.48 | 27.24 | 0.89 | 0.92 | 0.83 | |
| 20 (times) | 23.56 | 25.09 | 27.07 | 0.84 | 0.92 | 0.75 | |
| Median filtering [7 × 7] | 5 (times) | 22.49 | 24.75 | 26.61 | 1.00 | 0.86 | 0.83 |
| 10 (times) | 21.77 | 23.14 | 25.70 | 0.72 | 0.86 | 0.83 | |
| Geometric Attacks | PSNR (dB) | NC | |||||
|---|---|---|---|---|---|---|---|
| Intensity | Img1 | Img2 | Img3 | Img1 | Img2 | Img3 | |
| Rotation (clockwise) | 5° | 18.36 | 14.63 | 22.50 | 0.95 | 0.94 | 0.94 |
| 15° | 15.05 | 10.06 | 19.58 | 0.95 | 0.87 | 0.94 | |
| 30° | 14.56 | 9.14 | 18.11 | 1.00 | 0.86 | 1.00 | |
| 45° | 13.99 | 8.24 | 17.72 | 1.00 | 0.80 | 0.93 | |
| 60° | 13.68 | 7.44 | 17.03 | 0.95 | 0.94 | 0.83 | |
| Scaling | 0.3 | 20.97 | 21.32 | 25.67 | 1.00 | 0.88 | 0.88 |
| 0.6 | 27.13 | 27.25 | 29.70 | 1.00 | 1.00 | 0.94 | |
| 1.5 | 46.44 | 43.72 | 45.19 | 1.00 | 1.00 | 0.93 | |
| 2.0 | 46.40 | 43.61 | 44.94 | 1.00 | 1.00 | 0.93 | |
| Right translation | 5% | 14.60 | 10.37 | 19.13 | 1.00 | 1.00 | 0.93 |
| 15% | 12.98 | 8.12 | 16.04 | 0.95 | 0.92 | 0.89 | |
| 25% | 11.34 | 6.62 | 15.25 | 0.90 | 0.92 | 0.75 | |
| 40% | 10.11 | 5.75 | 14.50 | 0.90 | 0.80 | 0.82 | |
| Up translation | 5% | 14.67 | 13.42 | 17.99 | 0.95 | 0.92 | 1.00 |
| 15% | 13.17 | 8.81 | 15.08 | 1.00 | 0.92 | 0.82 | |
| 25% | 11.97 | 7.08 | 14.32 | 1.00 | 0.73 | 0.82 | |
| 35% | 11.08 | 6.06 | 13.34 | 1.00 | 0.92 | 0.76 | |
| Y-axis cropping | 10% | 15.66 | 15.14 | 18.75 | 1.00 | 0.86 | 1.00 |
| 20% | 15.26 | 12.27 | 16.21 | 1.00 | 0.86 | 0.89 | |
| 30% | 14.95 | 11.29 | 15.02 | 1.00 | 0.86 | 0.83 | |
| 40% | 14.69 | 10.57 | 14.48 | 0.95 | 0.94 | 0.83 | |
| X-axis cropping | 10% | 14.70 | 10.00 | 19.52 | 1.00 | 0.94 | 1.00 |
| 20% | 13.14 | 8.80 | 18.07 | 1.00 | 0.81 | 0.94 | |
| 30% | 12.55 | 7.48 | 17.04 | 1.00 | 0.75 | 0.86 | |
| 40% | 12.14 | 7.70 | 16.67 | 1.00 | 0.81 | 0.88 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, F.; Li, J.; Bhatti, U.A.; Liu, J.; Chen, Y.-W.; Li, D. Robust Zero Watermarking Algorithm for Medical Images Based on Improved NasNet-Mobile and DCT. Electronics 2023, 12, 3444. https://doi.org/10.3390/electronics12163444
Dong F, Li J, Bhatti UA, Liu J, Chen Y-W, Li D. Robust Zero Watermarking Algorithm for Medical Images Based on Improved NasNet-Mobile and DCT. Electronics. 2023; 12(16):3444. https://doi.org/10.3390/electronics12163444
Chicago/Turabian StyleDong, Fangchun, Jingbing Li, Uzair Aslam Bhatti, Jing Liu, Yen-Wei Chen, and Dekai Li. 2023. "Robust Zero Watermarking Algorithm for Medical Images Based on Improved NasNet-Mobile and DCT" Electronics 12, no. 16: 3444. https://doi.org/10.3390/electronics12163444
APA StyleDong, F., Li, J., Bhatti, U. A., Liu, J., Chen, Y.-W., & Li, D. (2023). Robust Zero Watermarking Algorithm for Medical Images Based on Improved NasNet-Mobile and DCT. Electronics, 12(16), 3444. https://doi.org/10.3390/electronics12163444









