Design of a Decentralized Identifier-Based Authentication and Access Control Model for Smart Homes
Abstract
1. Introduction
- An innovative authentication and access control model for smart homes is proposed in this paper, leveraging the decentralized nature of decentralized identifiers (DIDs) to effectively address the issue of single points of failure in traditional solutions. This model enables multiple smart homes to connect to the same blockchain network, allowing users to register once and access across households, thereby overcoming the complexity of authentication processes in traditional solutions and enhancing user experience.
- To accommodate the proposed system model, we have improved the capability-based access control scheme and introduced two types of tokens for authorization. This approach leverages the advantages of decentralized identifiers while ensuring high security and responsiveness.
- A thorough analysis of the proposed model is conducted through experiments, comparing it with other approaches. The results demonstrate the lightweight, secure, and reliable nature of the proposed solution, making it highly suitable for addressing security requirements in smart home environments.
2. Relevant Information
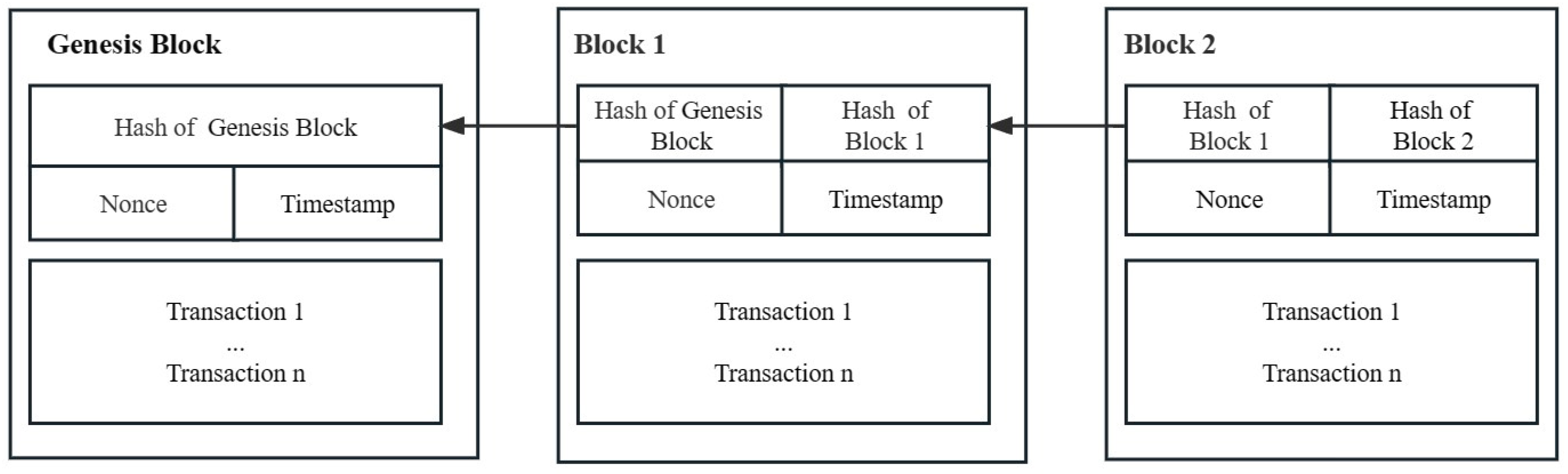
2.1. Blockchain
2.2. Decentralized Identifiers
2.3. Capability-Based Access Control
2.4. Elliptic Curve Cryptography
3. System Model
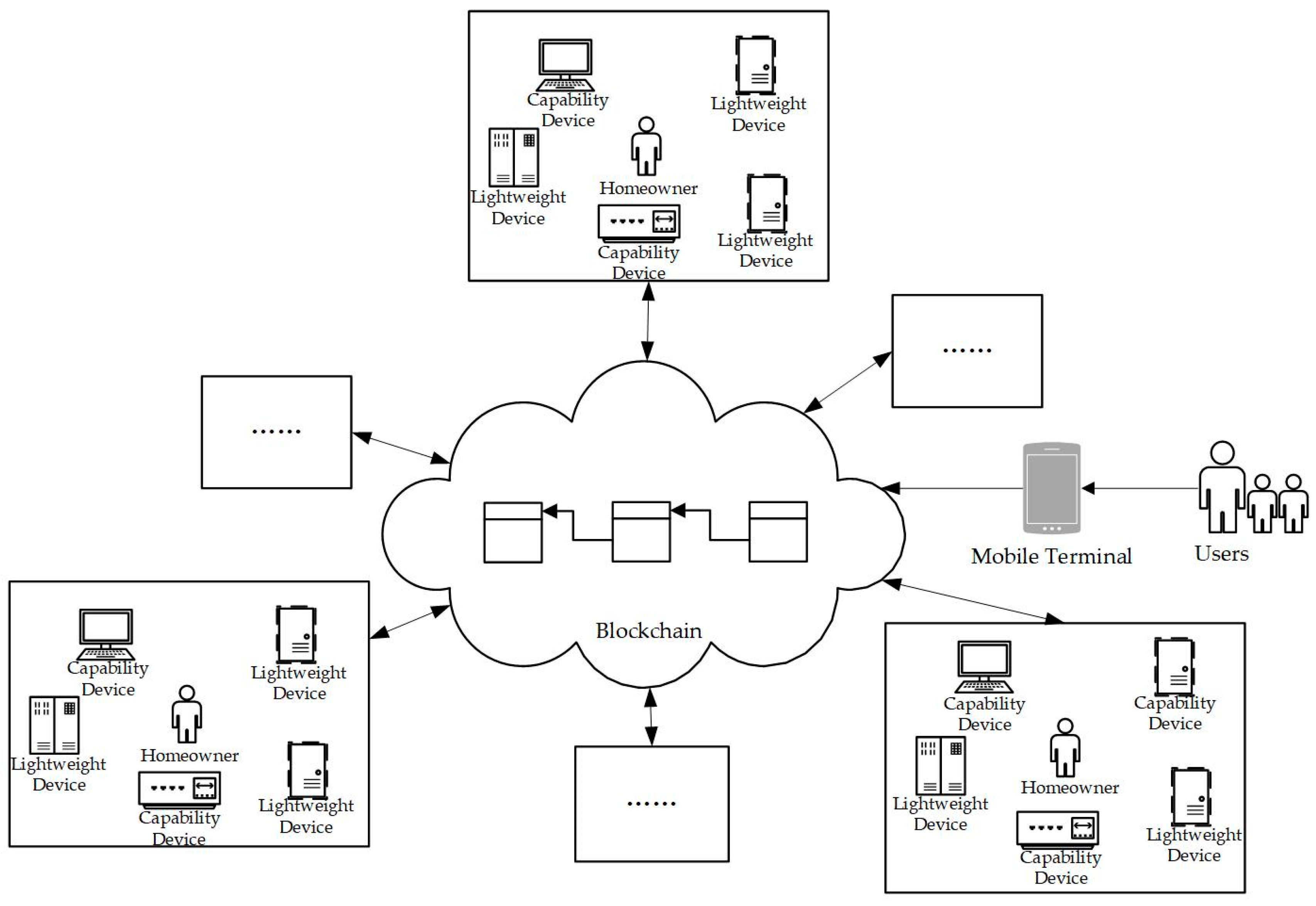
3.1. Overall Architecture
- Lightweight devices: Typically, these are sensor devices in smart homes, such as smart meters and surveillance devices. These devices have limited resources, which is why we collectively refer to them as lightweight devices in this paper. The primary responsibility of lightweight devices is to provide services when accessed by users.
- Capability devices: These devices in smart homes possess sufficient computing, storage, and communication resources, including gateways, computers, and smart voice assistants. Capability devices not only provide services to users but also have the responsibility of maintaining the blockchain ledger.
- Blockchain: The blockchain is collectively maintained by all capability devices in the network. It deploys smart contracts and maintains lists, such as the decentralized identifier (DID) management table and the blockchain account address table. Each device in the network is assigned a blockchain account to record its activities within the system.
- Homeowners: Referring to the owners of smart homes, homeowners have higher security requirements in this model. They are primarily responsible for actions such as applying for DIDs for smart devices and issuing tokens. Homeowners possess a blockchain account and can perform corresponding operations using their account.
- Users: This refers to household members and visitors who may have resource demands on smart devices within the smart home.
- Mobile terminal app: This is a terminal application through which users interact with the blockchain network and request device services. This application enables convenient control and management of smart devices while ensuring system security.
3.2. Smart Contract Module
- DID Registration Contract: This contract enables users to apply for the generation of corresponding DDO documents based on their blockchain account address and attribute information, which are then stored in the DID management table. In the system proposed in this paper, there are two main types of DDOs, namely device DDOs and user DDOs, as illustrated in Figure 3.
- Account Application Contract: This contract allows devices, users, or homeowners to apply for a blockchain ledger key, which, when hashed, can generate a blockchain account address. Each account address will be stored in the blockchain account address list for other contracts to recognize and invoke. The contract ensures that each entity has a unique account address and enables quick lookup and access through the account address list.
- DID Query Contract: This contract provides users with a convenient encapsulated interface for querying the DID of the target device. Through this contract, users can input the device’s name or other identifiers and obtain the corresponding DID. This contract facilitates users in finding the desired devices more easily and accelerates the overall system interaction process.
- DID Resolver Contract: When it is necessary to obtain the target information of an entity for an interaction, the DDO of the target DID can be acquired through this contract. Any malicious requests attempting to manipulate the DDO of others will be rejected, as only the DID owner can use this contract to obtain their DDO. This contract ensures that only authorized entities can access the information of other entities.
- DDO Update Contract: This contract allows entities to update their information when necessary, such as changing ownership, adding new features, or fixing defects. Only the owner of the DID can use the contract to update their DDO. The updating of Device DDOs falls under the rights of their respective owners. Through this contract, the system can ensure the accuracy and integrity of device information and prevent unauthorized modifications.
- DID Revocation Contract: If necessary, this contract can be used to delete the corresponding DDO and mark the DID as revoked. This functionality can also help protect information within the system. For instance, in the event of device theft or loss, the contract can be used to delete the device’s DID, thereby safeguarding the device’s information from unauthorized access.
- Token Issuance Contract: This contract allows the account owner to issue user tokens to users and permits the capability device (see Section 4.1) to issue device capability tokens to users. These tokens will be used to authenticate the identities and permissions of users and devices. The token issuance contract requires the authentication of the user issuing the token and determines the type and validity period of the token based on the user’s identity and permissions.
- Token Verification Contract: This contract is utilized to verify the legitimacy of user and device tokens. When a user makes an access request to a device, the token validation contract needs to parse the token, examine its validity and permissions, and based on the examination results, determine whether to permit the operation. If the token is invalid or lacks sufficient permissions, the request will be denied.
4. Solution Design
4.1. System Initialization Phase
4.2. Registration Phase
4.2.1. Special Registration
4.2.2. Device Registration
- (a)
- generates a random number and a public key , which is then sent to the registering device.
- (b)
- The registering device generates a random number and computes and . Subsequently, it sends to .
- (c)
- determines the shared secret as follows:
- (d)
- The registering device uses its own blockchain account private key . First, it calculates the blockchain account address using the SHA256 hash function. Then, it encrypts with the shared secret , resulting in , which is sent to .
- (e)
- Upon receiving the message, decrypts using the shared secret . It then invokes the contract to query whether the homeowner’s blockchain account address is present in the blockchain account address list. If it exists, proceeds to register the for the registering device using the DID registration contract and stores the corresponding in the DID management list. Otherwise, the request is rejected, and the connection is terminated.
4.2.3. User Registration
- (a)
- Dc generates a random number and computes the public key , then sends to the user.
- (b)
- The user generates a random number , and computes and . Subsequently, the user sends to .
- (c)
- determines the shared secret key as follows:
- (d)
- The user applies for a blockchain account private key through the account application contract to the blockchain, and the blockchain account address is stored in the blockchain account address list.
- (e)
- The user computes using the SHA256 hash function and encrypts with the shared key , resulting in . Subsequently, the user sends it to .
- (f)
- Upon receiving the message, decrypts using and checks if the blockchain account address is present in the blockchain account address list. If it exists, registers a decentralized identifier UDID for the account owner by invoking the DID registration contract and stores the corresponding DDO in the DID management list. Otherwise, rejects the request and terminates the connection.
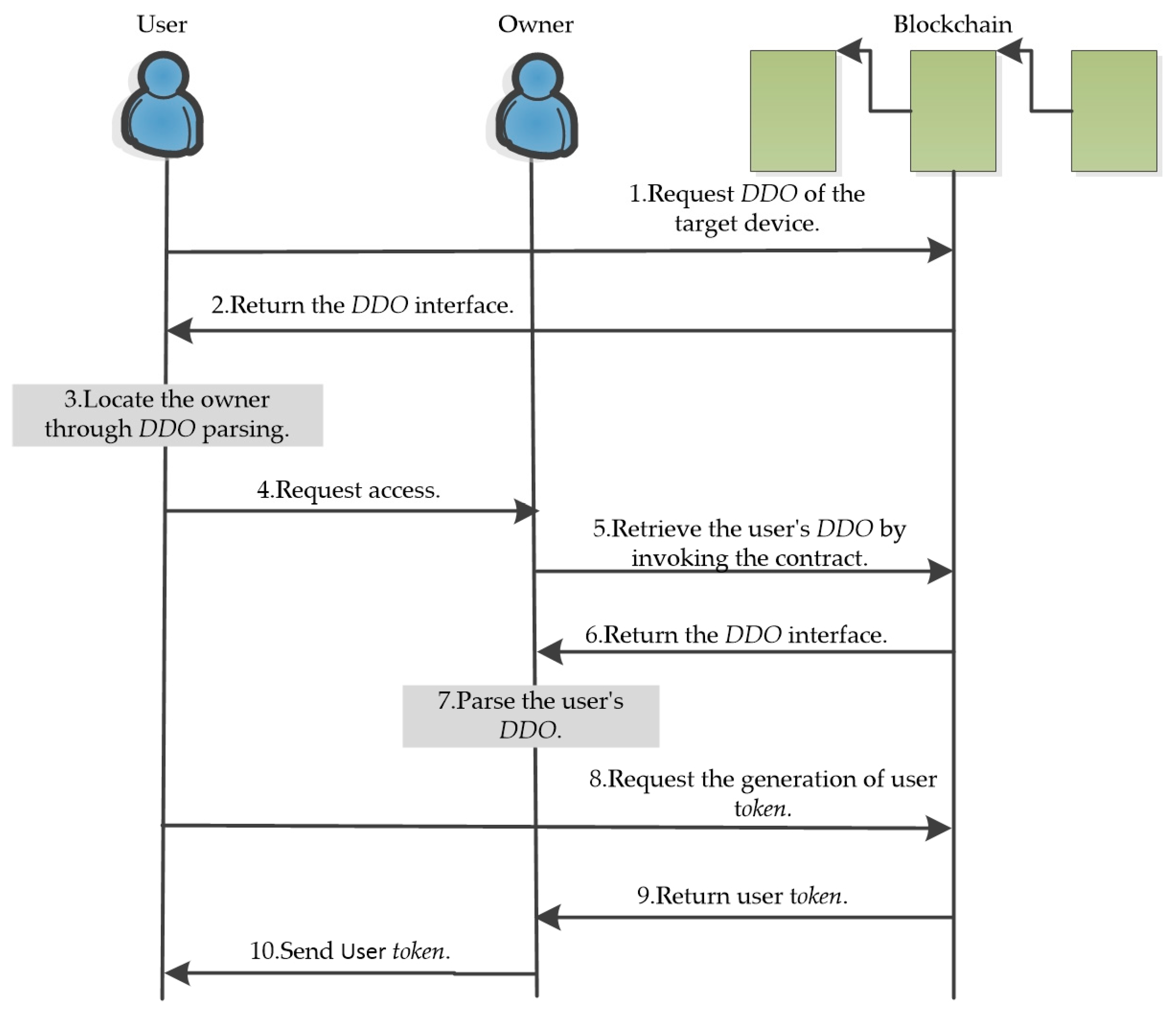
4.3. Identity Authentication Phase
- (a)
- Users enter the blockchain network through a mobile terminal app and invoke the DID query contract to locate the target device’s
- (b)
- The DID resolution contract is called to obtain the DDO identified by the Users can initiate an access request to the homeowner of the smart home where the device is located.
- (c)
- Upon receiving the access request, the homeowner invokes the DID query contract to find the user’s and then calls the DID resolution contract to learn about the user’s specific details. The homeowner can choose whether to agree to provide access services. If agreed, the token issuance contract is called to issue a , as shown below:
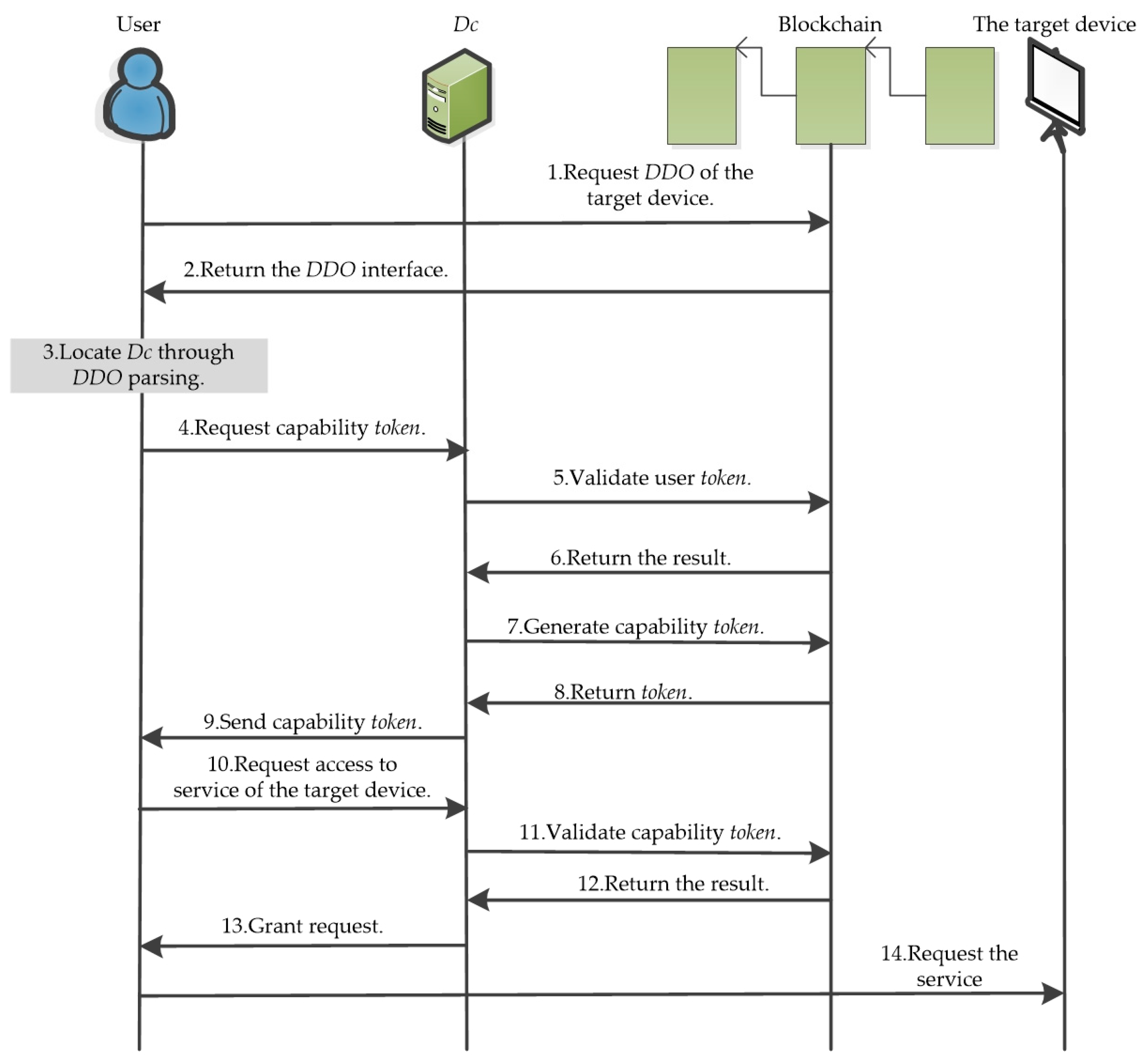
4.4. Authorized Access Phase
5. Experimental Analysis
5.1. Security Analysis
- Replay Attack Resistance: In this system, generates a new key pair for each session request, which is used for encrypting response messages and computing messages. Since the generated key pair is always up to date, it can withstand any replay attacks. Additionally, during the authentication and authorization access phase, timestamps are included in the user token and device capability token, ensuring full resistance against replay attacks.
- Impersonation Attack Resistance: The system adopts a decentralized identifier (DID) to authorize legitimate user access, and due to the uniqueness of each object’s DID, it is impossible for any unauthorized user to impersonate others.
- Man-in-the-Middle Attack Resistance: Decentralized identifiers (DIDs) are distributed across multiple nodes, eliminating the reliance on a single centralized authority and significantly reducing the risk of unauthorized interception and manipulation of communication. The process of storing and verifying DIDs involves rigorous identity authentication, leveraging cryptographic techniques such as digital signatures and public-key encryption. These measures effectively prevent impersonation by intermediaries, ensuring the integrity and authenticity of the communication channels.
- Denial-of-Service (DoS) Attack Resistance: Due to the token verification contract performing token expiration and validity checks for each request, the system can avoid DoS attacks and ensure smooth operation.
- Malicious Node Attack Resistance: The system is implemented using blockchain technology, guaranteeing the immutability and decentralization of the distributed ledger, which effectively mitigates attacks from malicious nodes.
- Tamper Resistance: Firstly, without a valid token, attackers are unable to access data through access requests. Secondly, all data stored on the blockchain are formed into a Merkle tree to create a hash value, and the blocks are linked together through hash values, contributing to the robust tamper-resistant capability of the blockchain. Both types of tokens are stored on the blockchain, which prevents unauthorized modification by attackers.
- Traceability: All critical information is preserved in an immutable distributed ledger on the blockchain, enabling the tracing of any malicious activities and reducing improper behavior by malicious users.
- Confidentiality: The services provided by the devices are protected and accessed only by two parties: the homeowner and the user. It is at the discretion of the homeowner to issue user tokens to specific individuals, and unauthorized individuals are prohibited from using the smart device services without the homeowner’s approval.
- Integrity: Hash functions possess irreversibility, uniqueness, and collision resistance, significantly reducing the possibility of data forgery and enabling the precise tracking and verification of recorded data. All DIDs, DDOs, and tokens are stored on the blockchain, preventing arbitrary manipulation and ensuring the integrity of the system.
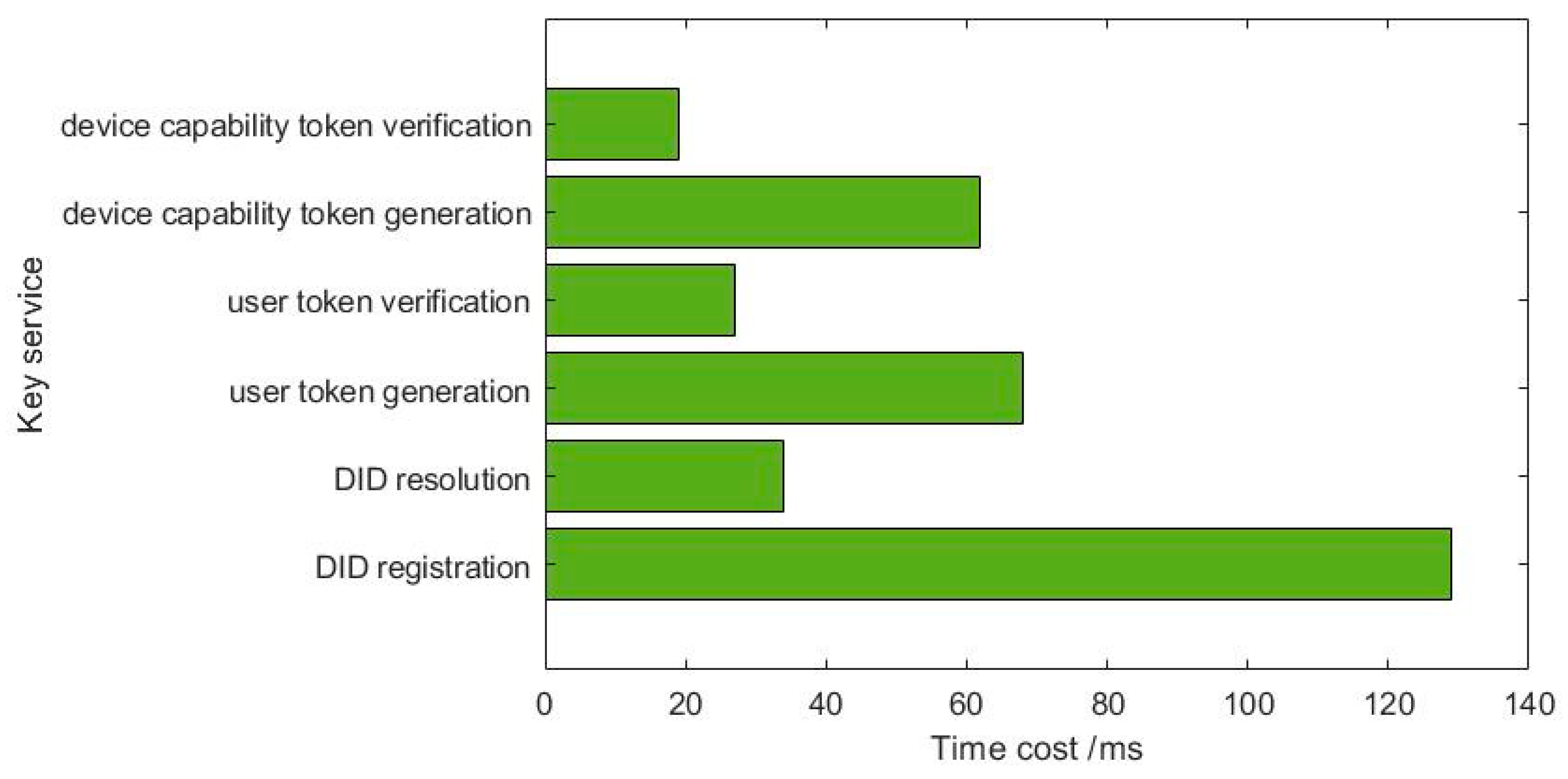
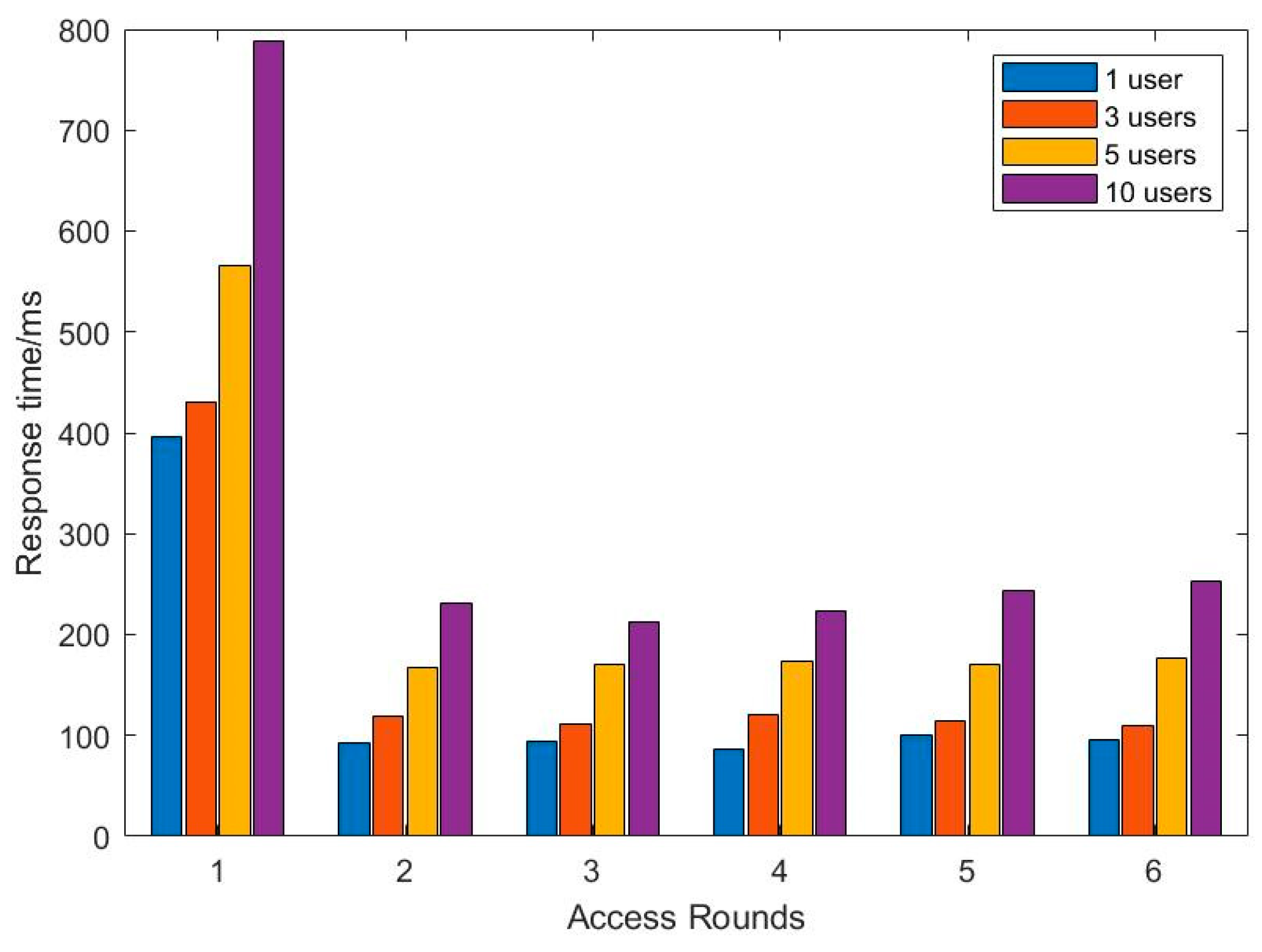
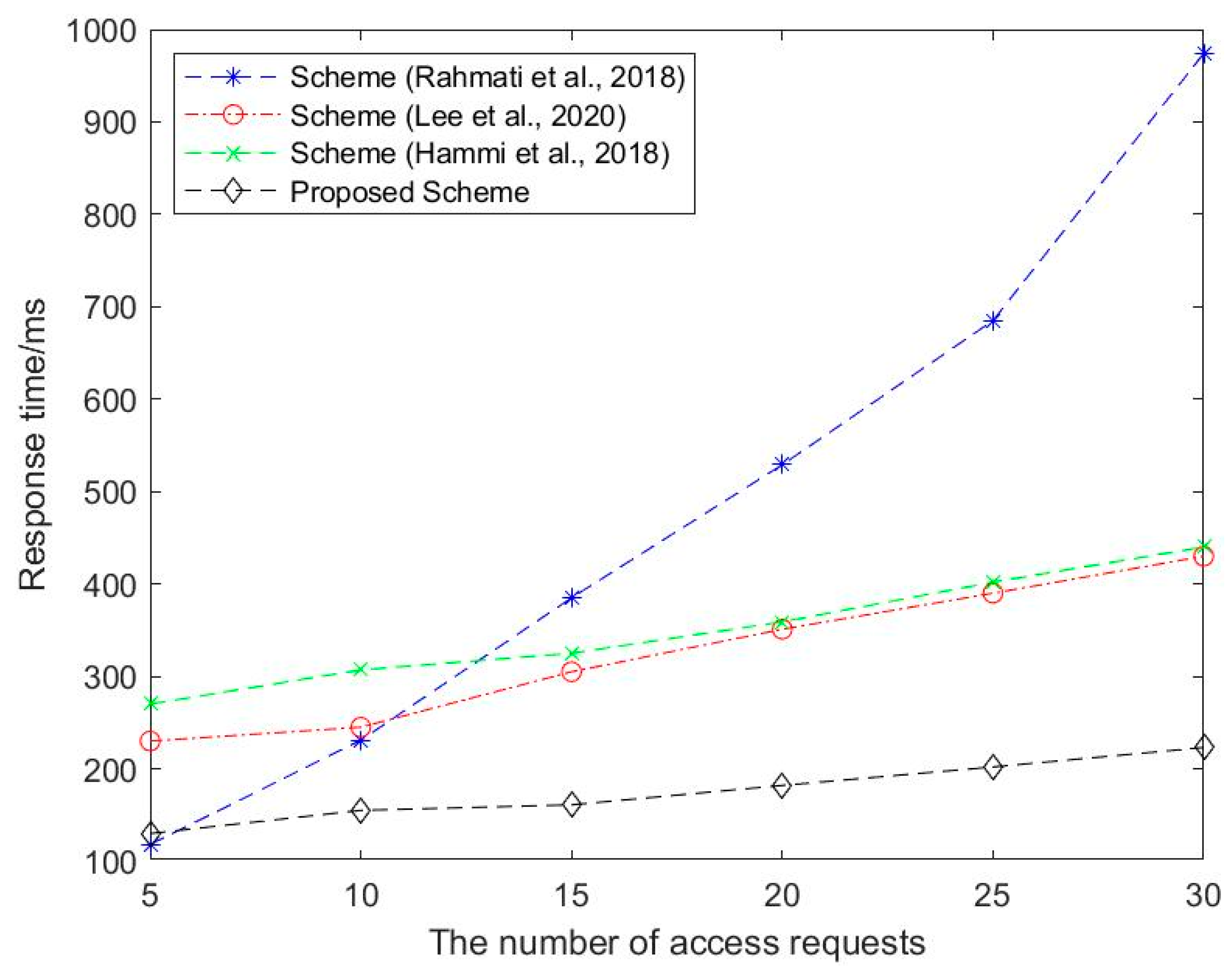
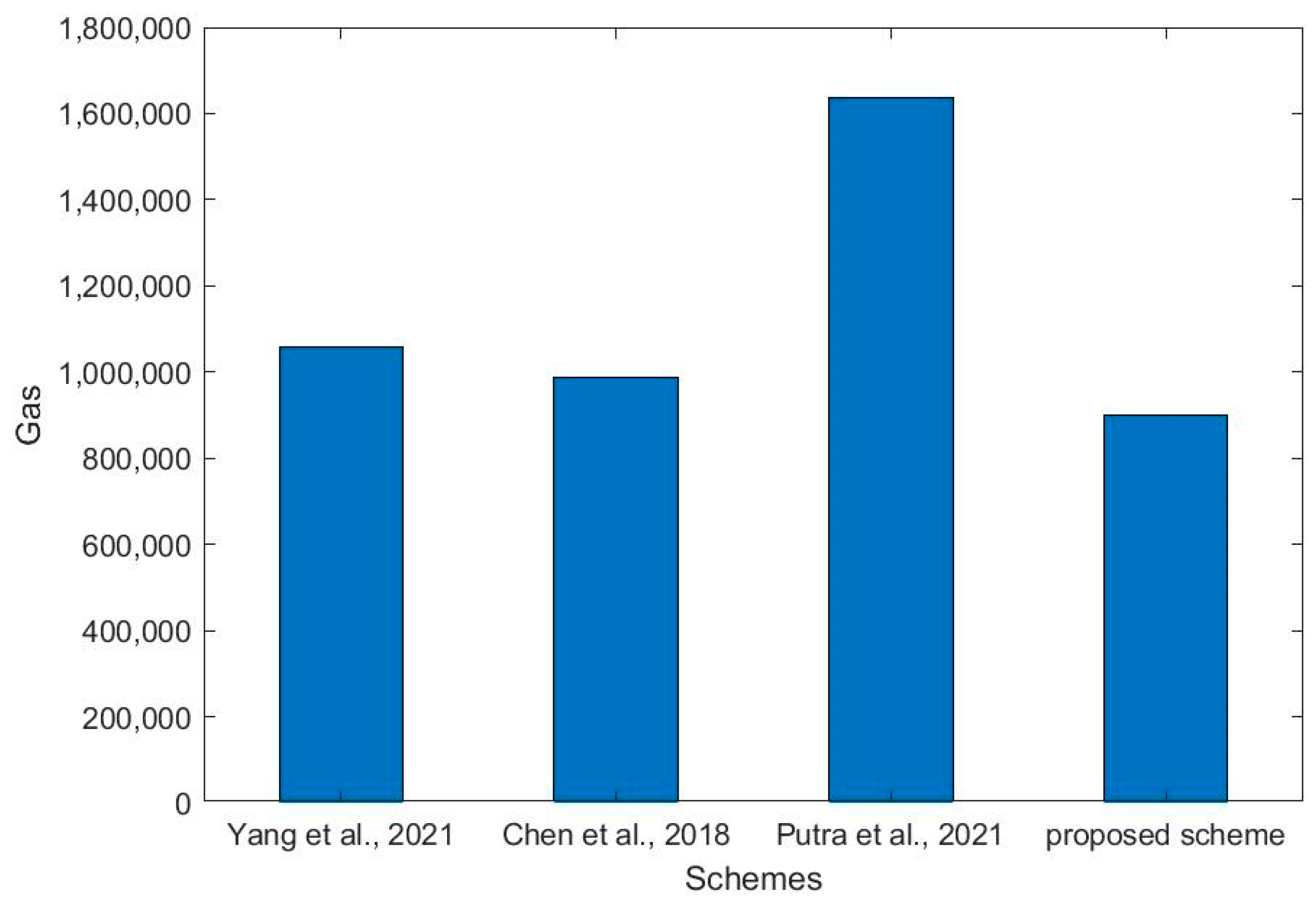
5.2. Performance Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar]
- da Ponte, F.R.; Gomes, R.L.; Celestino, J.; Madeira, E.R.; Patel, A. IoT device programmable language customization for home automation. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 168–173. [Google Scholar]
- Padmanaban, S.; Nasab, M.A.; Shiri, M.E.; Javadi, H.H.S.; Nasab, M.A.; Zand, M.; Samavat, T. The role of internet of things in smart homes. In Artificial Intelligence-based Smart Power Systems; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2023; pp. 259–271. [Google Scholar]
- Kavallieratos, G.; Chowdhury, N.; Katsikas, S.; Gkioulos, V.; Wolthusen, S. Threat Analysis for Smart Homes. Future Internet 2019, 11, 207. [Google Scholar] [CrossRef]
- Schiansky, P.; Kalb, J.; Sztatecsny, E.; Roehsner, M.-C.; Guggemos, T.; Trenti, A.; Bozzio, M.; Walther, P. Demonstration of quantum-digital payments. arXiv 2023, arXiv:2305.14504. [Google Scholar]
- Yin, H.-L.; Fu, Y.; Li, C.-L.; Weng, C.-X.; Li, B.-H.; Gu, J.; Lu, Y.-S.; Huang, S.; Chen, Z.-B. Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 2023, 10, nwac228. [Google Scholar] [PubMed]
- Pereira, M.; Currás-Lorenzo, G.; Navarrete, Á.; Mizutani, A.; Kato, G.; Curty, M.; Tamaki, K. Modified BB84 quantum key distribution protocol robust to source imperfections. Phys. Rev. Res. 2023, 5, 023065. [Google Scholar]
- Gu, J.; Cao, X.-Y.; Fu, Y.; He, Z.-W.; Yin, Z.-J.; Yin, H.-L.; Chen, Z.-B. Experimental measurement-device-independent type quantum key distribution with flawed and correlated sources. Sci. Bull. 2022, 67, 2167–2175. [Google Scholar]
- Kang, W.M.; Moon, S.Y.; Park, J.H. An enhanced security framework for home appliances in smart home. Hum. -Centric Comput. Inf. Sci. 2017, 7, 6. [Google Scholar]
- Wu, T.-Y.; Meng, Q.; Chen, Y.-C.; Kumari, S.; Chen, C.-M. Toward a Secure Smart-Home IoT Access Control Scheme Based on Home Registration Approach. Mathematics 2023, 11, 2123. [Google Scholar] [CrossRef]
- Haseeb-ur-Rehman, R.M.A.; Liaqat, M.; Aman, A.H.M.; Almazroi, A.A.; Hasan, M.K.; Ali, Z.; Ali, R.L. LR-AKAP: A Lightweight and Robust Security Protocol for Smart Home Environments. Sensors 2022, 22, 6902. [Google Scholar]
- Rahmati, A.; Fernandes, E.; Eykholt, K.; Prakash, A. Tyche: Risk-based permissions for smart home platforms. arXiv 2018, arXiv:1801.04609. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar]
- Yakubu, B.M.; Khan, M.I.; Bhattarakosol, P. IPChain: Blockchain-Based Security Protocol for IoT Address Management Servers in Smart Homes. J. Sens. Actuator Netw. 2022, 11, 80. [Google Scholar] [CrossRef]
- Singh, S.; Ra, I.-H.; Meng, W.; Kaur, M.; Cho, G.H. SH-BlockCC: A secure and efficient Internet of things smart home architecture based on cloud computing and blockchain technology. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719844159. [Google Scholar] [CrossRef]
- Menon, S.; Anand, D.; Kavita; Verma, S.; Kaur, M.; Jhanjhi, N.Z.; Ghoniem, R.M.; Ray, S.K. Blockchain and Machine Learning Inspired Secure Smart Home Communication Network. Sensors 2023, 23, 6132. [Google Scholar]
- She, W.; Gu, Z.-H.; Lyu, X.-K.; Liu, Q.; Tian, Z.; Liu, W. Homomorphic consortium blockchain for smart home system sensitive data privacy preserving. IEEE Access 2019, 7, 62058–62070. [Google Scholar]
- Zeng, Y.; Wei, L.; Cheng, Y.; Zhang, H.; Sun, W.; Wang, B. Blockchain-Enabled Intelligent Dispatching and Credit-Based Bidding for Microgrids. Electronics 2023, 12, 2868. [Google Scholar] [CrossRef]
- Liu, Y.; Lu, Q.; Chen, S.; Qu, Q.; O’Connor, H.; Choo, K.-K.R.; Zhang, H. Capability-based IoT access control using blockchain. Digit. Commun. Netw. 2021, 7, 463–469. [Google Scholar] [CrossRef]
- Lee, Y.; Rathore, S.; Park, J.H.; Park, J.H. A blockchain-based smart home gateway architecture for preventing data forgery. Hum. Centric Comput. Inf. Sci. 2020, 10, 9. [Google Scholar]
- Matsumoto, N.; Kotani, D.; Okabe, Y. Capability Based Network Access Control for Smart Home Devices. In Proceedings of the 2022 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Pisa, Italy, 21–25 March 2022; pp. 551–556. [Google Scholar]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar]
- Yang, X.; Yang, X.; Yi, X.; Khalil, I.; Zhou, X.; He, D.; Huang, X.; Nepal, S. Blockchain-based secure and lightweight authentication for Internet of Things. IEEE Internet Things J. 2021, 9, 3321–3332. [Google Scholar]
- Shao, S.-F.; Cao, X.-Y.; Xie, Y.-M.; Gu, J.; Liu, W.-B.; Fu, Y.; Yin, H.-L.; Chen, Z.-B. Experimental Phase-Matching Quantum Key Distribution without Intensity Modulation. arXiv 2023, arXiv:2303.11585. [Google Scholar]
- Chen, Y.-D.; Azhari, M.Z.; Leu, J.-S. Design and implementation of a power consumption management system for smart home over fog-cloud computing. In Proceedings of the 2018 3rd International Conference on Intelligent Green Building and Smart Grid (IGBSG), Yilan, Taiwan, 22–25 April 2018; pp. 1–5. [Google Scholar]
- Hossain, S.; Waheed, S.; Rahman, Z.; Shezan, S.; Hossain, M.M. Blockchain for the security of internet of things: A smart home use case using ethereum. Int. J. Recent Technol. Eng. 2020, 8, 4601–4608. [Google Scholar] [CrossRef]
- Ch, R.; Kumari, D.J.; Gadekallu, T.R.; Iwendi, C. Distributed-Ledger-Based Blockchain Technology for Reliable Electronic Voting System with Statistical Analysis. Electronics 2022, 11, 3308. [Google Scholar] [CrossRef]
- Liu, X.; Huang, Z.; Wang, Q.; Wan, B. An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System. Electronics 2023, 12, 2808. [Google Scholar] [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R.; Ignjatovic, A. Trust-based blockchain authorization for iot. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1646–1658. [Google Scholar] [CrossRef]




| Security Feature | [12] | [20] | [22] | Proposed Scheme |
|---|---|---|---|---|
| Confidentiality | √ | × | √ | √ |
| Tamper Resistance | × | √ | × | √ |
| Traceability | × | √ | × | √ |
| Scalability | × | × | √ | √ |
| Integrity | √ | √ | √ | √ |
| Software/Hardware | Parameter |
|---|---|
| Operating system | Ubuntu Linux 20.04LTS |
| CPU | AMD Ryzen 7 4800H with Radeon Graphics |
| Programming Language | solidity0.8.0 |
| Memory | 16 GB |
| Mnemonic | Gas Used | Notes |
|---|---|---|
| STOP | 0 | Halts execution. |
| ADD | 3 | Addition operation |
| MUL | 5 | Multiplication operation |
| SUB | 3 | Subtraction operation |
| DIV | 5 | Integer division operation |
| ADDMOD | 8 | Modulo addition operation |
| MULMOD | 8 | Modulo multiplication operation |
| BLOCKHASH | 20 | Get the hash of one of the 256 most recent complete blocks |
| BALANCE | 400 | Get balance of the given account |
| EXTCODESIZE | 700 | Get size of an account’s code |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, X.; Zhong, B.; Cui, Z. Design of a Decentralized Identifier-Based Authentication and Access Control Model for Smart Homes. Electronics 2023, 12, 3334. https://doi.org/10.3390/electronics12153334
Zhao X, Zhong B, Cui Z. Design of a Decentralized Identifier-Based Authentication and Access Control Model for Smart Homes. Electronics. 2023; 12(15):3334. https://doi.org/10.3390/electronics12153334
Chicago/Turabian StyleZhao, Xinyang, Bocheng Zhong, and Zicai Cui. 2023. "Design of a Decentralized Identifier-Based Authentication and Access Control Model for Smart Homes" Electronics 12, no. 15: 3334. https://doi.org/10.3390/electronics12153334
APA StyleZhao, X., Zhong, B., & Cui, Z. (2023). Design of a Decentralized Identifier-Based Authentication and Access Control Model for Smart Homes. Electronics, 12(15), 3334. https://doi.org/10.3390/electronics12153334





