Abstract
In the 802.11 protocol, the fundamental medium access mechanism is called Distributed Coordination Function (DCF). In DCF, before making any transmission attempt, the nodes count down a timer with a value randomly selected from the Contention Window (CW) size. If the transmitted packet is involved in a collision, the node increases the CW size in an attempt to reduce the collision rate. Conversely, if the packet is transmitted successfully, the node reduces the CW size in order to increase the frequency of the transmission attempts. The growth or reduction in the CW size has a critical effect on the network performance. Several backoff algorithms have been proposed to improve the system throughput. However, none of these methods enable the system to approach the theoretical maximum throughput possible under DCF. Accordingly, this study proposes the Rapidly Adaptive Collision Backoff (RACB) algorithm, in which the CW size is adjusted dynamically based on the collision rate, as analyzed by a mathematical model. Notably, RACB requires no knowledge of the number of nodes in the wireless network and is applicable to both lightly loaded and heavily loaded networks. The numerical results show that, by adjusting the CW size such that the collision rate is maintained at a value close to 0.1, RACB enables the system throughput to approach the maximum DCF throughput in wireless environments containing any number of nodes.
1. Introduction
The IEEE 802.11 [1,2,3,4] protocol is one of the most commonly deployed wireless access technologies around the world and provides a detailed specification of the Medium Access Control (MAC) layer and Physical Layer (PHY) of WLANs. The MAC specification defines two medium access coordination functions, namely the Point Coordination Function (PCF) and the Distributed Coordination Function (DCF). PCF is a centralized MAC protocol that supports collision-free and time-bounded services. By contrast, DCF is a contention-based scheme that employs the Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) protocol and the Binary Exponential Backoff (BEB) contention-resolution algorithm. In the IEEE 802.11 standard, DCF is the default medium access control method, while PCF is an optional function.
In a wireless network, collisions occur when two or more nodes transmit packets simultaneously. In order to avoid such collisions, DCF uses a random backoff period to force the nodes to defer their wireless channel access attempts for a short arbitrary period. In particular, the nodes randomly select a backoff period from the Contention Window (CW) size and then count this backoff period down before attempting to send their packets. During the countdown period, if another node transmits a packet, thereby causing the channel to become busy, the countdown process is frozen until the state of the channel returns to idle. The node then continues the countdown and attempts to transmit its packets once the counter reaches zero.
According to the discussions above, when the size of the CW is small, the average length of the backoff period is short. As a result, the waiting time before packet transmissions is also short. However, the probability of collisions is increased. Conversely, a larger CW size increases the waiting time before transmissions but reduces the collision probability. Accordingly, an appropriate setting of the CW size is essential for achieving an acceptable tradeoff between the channel collision rate and the waiting time before packet transmission.
In DCF, the variation in the CW size is determined by the BEB algorithm. More specifically, each time a node experiences a transmission collision, the size of the CW is doubled until it reaches the maximum value (CWmax) in order to reduce the probability of transmission collisions occurring again. By contrast, each time a packet is successfully transmitted, BEB restores the CW size to the minimum value (CWmin). However, in network environments containing a large number of nodes, all competing for the same wireless channel, such sudden large reductions in the CW size cause a severe degradation of the system throughput [5,6,7,8,9,10] since the shorter CW size results in a greater number of collisions after any successful transmission.
Song [11] attempted to resolve this problem using a modified backoff algorithm designated as Exponential Increase Exponential Decrease (EIED), in which the size of the CW was doubled after a collision (as in the original BEB scheme) but was only halved (rather than restored to the minimum value) after each successful transmission. Compared with BEB, EIED results in a significant improvement in the performance of the DCF mechanism in environments with a large number of contending nodes. However, in wireless networks containing many nodes, it is desirable to maintain the CW size as large as possible in order to avoid frequent collisions. Accordingly, Ye and Tseng [12] proposed an alternative backoff algorithm referred to as Linear Increase Linear Decrease (LILD), in which the CW size was increased and decreased linearly with an incremental step size of CWmin after each collision and successful transmission. Compared to BEB and EIED, the change in the CW size in LILD is more progressive, and, hence, LILD achieves a higher throughput than either BEB or EIED in networks containing a large number of nodes. However, EIED outperforms LILD in networks with a rapidly changing load due to the exponential change in the CW size. Accordingly, the present group [13] previously combined the respective advantages of EIED and LILD in a new backoff algorithm designated as Exponential-Linear Backoff Algorithm (ELBA). In the proposed algorithm, the channel was judged to be heavily loaded if the CW size exceeded a certain threshold value, and the size of the CW was adjusted linearly using the method prescribed in LILD. By contrast, when the CW size was smaller than this threshold value, the network was judged to be lightly loaded, and the CW size was adjusted exponentially, as in EIED. The experimental results showed that ELBA outperformed BEB, EIED and LILD under both light and heavy network loads.
Although the algorithms described above achieve better system throughput than DCF with BEB, their performance regarding system throughput is still not achieving theoretical maximum throughput [14]. According to the analysis results presented in [5,14], the optimal size of the CW varies with the number of nodes in the network. However, in practical networks, the individual nodes are unaware of the total number of nodes contending for the channel [15]. Thus, they are unable to determine the optimal CW size. Accordingly, the present study proposes a new backoff algorithm, referred to hereafter as the Rapidly Adaptive Collision Backoff (RACB) algorithm, which allows the system throughput to approach the maximum theoretical throughput in [14] with no knowledge of the number of wireless nodes in the network. In the proposed algorithm, the wireless nodes adjust the CW size directly based on their own observed collision rate, where the relationship between the optimal CW size and the collision rate is determined mathematically [5,14]. When the collision rate exceeds a certain threshold value, the nodes increase the CW size. By contrast, when the collision rate falls below the threshold value, the nodes reduce the CW size. Notably, the CW size is increased/decreased exponentially or linearly depending on the distance of the collision rate from the specified threshold value. Importantly, RACB enables the CW size to be adjusted adaptively in such a way that the system throughput approaches the maximum throughput without requiring any knowledge of the total number of nodes in the network.
The remainder of this paper is organized as follows. Section 2 introduces the basic operation of DCF and its related backoff algorithms. Section 3 analyzes the performance of DCF and examines the relationship between the maximum system throughput and the optimal CW size. Section 4 introduces the proposed RACB algorithm. Section 5 describes the experimental settings and presents the numerical results. Finally, Section 6 provides some brief concluding remarks and indicates the proposed direction of future research.
2. Background and Related Works
2.1. IEEE 802.11 DCF
Figure 1 [1] illustrates the basic operation of the CSMA/CA protocol in DCF. Before a wireless node transmits a new packet to the network, it first senses the activity of the channel. If the channel is sensed idle for an interval greater than the DIFS (Distributed Inter-frame Spacing), the node transmits the packet immediately. Conversely, if the channel is sensed busy, the node defers transmission until the end of the ongoing transmission. Once the channel becomes idle, the node initializes its backoff timer with a randomly selected backoff period with a duration greater than zero and less than the CW size. The node senses the channel as it waits and decrements the timer each time it senses the channel to remain idle for a DIFS. If the channel is still idle when the timer expires, the node transmits its packet. However, if another node starts to transmit during the countdown period, the node freezes its timer until the channel becomes idle for a DIFS once again, at which point it restarts the timer and transmits its packet once the timer expires.
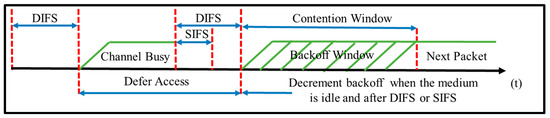
Figure 1.
Operation of IEEE 802.11 DCF [1].
DCF adopts the BEB algorithm [1] to control the variation in the CW size. As shown in Figure 2 [1], the minimum value (CWmin) and maximum value (CWmax) of the CW size are set as 32 and 1024, respectively. In the first transmission attempt, BEB sets the CW equal to CWmin, and the node selects a random value for its backoff timer in the range of [0, CWi−1]. Note that CW is the size of the contention window, CWi is the current CW size and i is the number of failed transmission attempts thus far. After each unsuccessful transmission, CW is doubled, i.e., CWi = 2 * CWi−1 = 2i * CWmin, until it reaches the maximum value, CWmax = 2m * CWmin. (Note that m is the maximum number of backoff stages in the BEB algorithm.) Once CWi reaches CWmax, it remains at this value until a successful transmission occurs, at which point it is reset to CWmin.
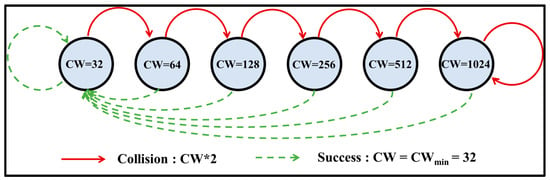
Figure 2.
Markov chain model for BEB algorithm [1].
BEB is an asymmetric backoff algorithm; i.e., the CW size decreases drastically after a successful transmission. As a result, it causes a large number of collisions after any successful transmission, particularly in networks containing a large number of nodes, and degrades the system throughput accordingly [5].
2.2. Related Works
2.2.1. Exponential Increase Exponential Decrease (EIED)
Several modifications have been proposed to address the problems caused by the asymmetric nature of BEB [8,9,10,11,12,13]. For example, the Exponential Increase Exponential Decrease (EIED) method in [11] aims to reduce the CW size more slowly after successful transmissions by using an exponential reduction strategy. As shown in Figure 3 [11], the CW size is set initially to CWmin and is then doubled (CWi = 2 * CWi−1) after each unsuccessful transmission until the current CW reaches CWmax. The CW size is maintained at this value until a successful transmission occurs, at which point the current CW is halved (CWi = CWi−1/2). The CW size continues to be halved until it reaches CWmin, where it remains until an unsuccessful transition occurs.
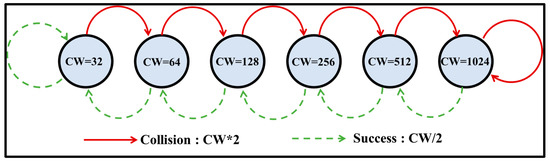
Figure 3.
Markov chain model for EIED algorithm [11].
By decreasing the CW size exponentially rather than asymmetrically, EIED achieves a better DCF performance (i.e., a higher system throughput) than that obtained using BEB. For wireless networks containing a large number of wireless nodes, the CW size should be maintained as large as possible in order to avoid frequent collisions. However, the CW size may vary widely in EIED, particularly in networks with a large number of nodes. Consequently, EIED may be too sensitive to adapt to changes in the condition of the wireless network.
2.2.2. Linear Increase Linear Decrease (LILD)
The Linear Increase Linear Decrease (LILD) algorithm [12] aims to overcome this drawback of EIED by decreasing the CW size linearly rather than exponentially following a successful transmission. As shown in Figure 4, the CW size is set initially as CWmin. After each unsuccessful transmission, CW is incremented by CWmin (CWi = CWi−1 + CWmin) until it reaches CWmax. The CW is then decreased linearly by CWmin (CWi = CWi−1 − CWmin) each time a successful transmission occurs until it reaches CWmin.
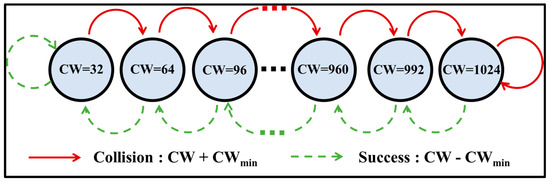
Figure 4.
Markov chain model for LILD algorithm [12].
The CW size in LILD changes more slowly than in EIED and BEB, and, hence, LILD is better suited to networks with a large number of nodes. However, it is impractical for networks with variable loads because of the linear change in the CW size.
2.2.3. Exponential-Linear Backoff Algorithm (ELBA)
From the discussions above, EIED is suitable for networks with a light load, while LILD is more suitable for networks with a heavy load. Thus, the ELBA algorithm [13] aims to combine the respective advantages of EIED and LILD to improve the throughput in wireless networks with a variable load. In particular, ELBA sets a threshold referred to as the Contention Window Threshold, CWThreshold, as an index against which to judge the network status. When the CW size is less than this threshold, the network load is assumed to be light, and the CW size is tuned exponentially as in EIED. By contrast, when the CW size is larger than this threshold value, the network is assumed to be heavily loaded, and the CW size is tuned linearly as in LILD. As shown in Figure 5, the CW size is initialized as CWmin. After each unsuccessful transmission, the CW is doubled (CWi = CWi−1 * 2) until it reaches CWThreshold. After each subsequent unsuccessful transmission, the CW size is increased exponentially by CWmin (CWi = CWi−1 + CWmin) until it reaches CWmax. Following each successful transmission with the current CW size between CWmin and CWThreshold, the CW is halved (CWi = CWi−1/2) until it reaches CWmin. By contrast, for current CW sizes in the range of CWThreshold to CWmax, the CW is decreased exponentially by CWmin (CWi = CWi−1 − CWmin) until it reaches CWThreshold.
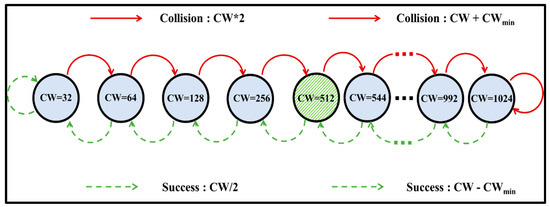
Figure 5.
Markov chain model for ELBA algorithm [13].
In accordance with the IEEE 802.11 standard, ELBA sets CWmin and CWmax as 32 and 1024, respectively, and assigns the Contention Window Threshold as half of CWmax, i.e., 512. Notably, the adaptive approach of ELBA reduces the collision rate (and improves the system throughput) compared to BEB, EIED and LILD in both lightly loaded and heavily loaded networks.
2.3. Maximum Throughput in Wireless Networks
The authors in [14] devised an analytical model for maximizing the throughput in wireless networks by optimizing the CW size in accordance with the number of nodes (see Table 1). However, the model assumed that each node is able to determine the number of competing nodes in the network and can set the optimal CW accordingly, which is unreasonable in real-world wireless networks.

Table 1.
Maximum throughput versus optimal CW size [14].
2.4. Contributions of Present Study
The present study proposes a Rapidly Adaptive Collision Backoff (RACB) algorithm for improving the system throughput over WLANs. RACB maximizes the system throughput by adjusting the CW size based on the collision rate of the nodes, where the relationship between the collision rate and the optimal CW size is described using a mathematical model. Notably, RACB requires no knowledge of the number of nodes in the wireless network and is applicable to both lightly loaded and heavily loaded networks.
3. Performance Analysis of DCF
3.1. Maximum System Throughput under DCF
In the present study, the throughput performance of DCF was investigated using a self-written simulator implemented in NS-2 tool [16]. The simulations commenced by examining the relationship between the maximum system throughput and the CW size in networks with different numbers of wireless nodes. In accordance with the IEEE 802.11 standard, the CW size was varied in the range of 32 to 1024. Furthermore, the network was assumed to contain 10, 20, 30, 40 or 50 nodes.
As shown in Figure 6, for all the simulated environments, the system throughput increases rapidly as the CW size first increases. However, at a certain optimal value of the CW size, the throughput saturates, or reduces slightly as a result of low channel utilization. For the smallest wireless network with 10 competing nodes, the maximum system throughput reaches 84.5% for a CW size of 160. For the network with 30 nodes, the maximum system throughput reduces slightly to 84% with an optimal CW size of 512. In Figure 6, the maximum system throughput of different number of nodes can be mapped to the different optimal CW size. The simulation results match the analysis in [14].
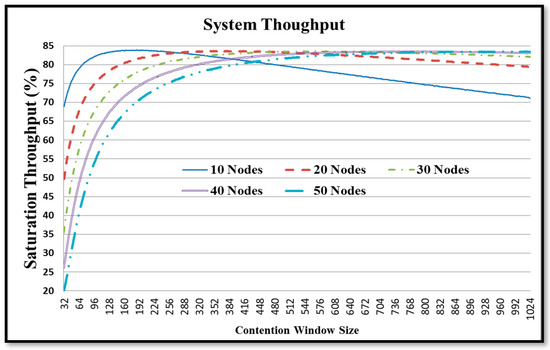
Figure 6.
System throughput of DCF for different CW sizes.
Figure 7 shows the simulation results obtained for the variation in the saturation throughput with the number of network nodes under different backoff algorithms. As shown, ELBA outperforms DCF, EIED and LILD for all the considered networks. However, the system throughput still fails to meet the maximum value in [14] due to the non-optimal setting of the CW size. Moreover, as the number of nodes increases, the performance gap between ELBA and the maximum saturation throughput increases.
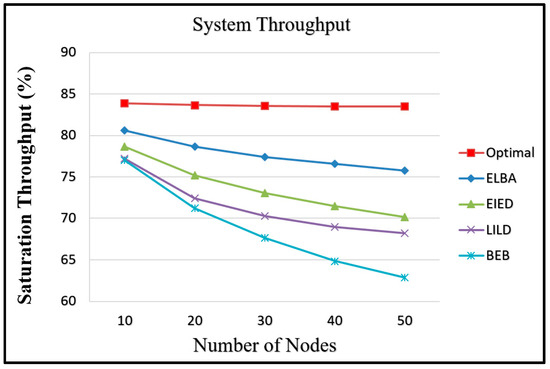
Figure 7.
Saturation throughput of DCF under different backoff algorithms.
3.2. DCF Performance Analysis for Different CW Sizes
The optimal CW size, i.e., the CW size that achieves the maximum DCF throughput, can be obtained using the analytical model in [14]. However, as described in Section 2.3, this model is based on the unrealistic assumption that the nodes in the network are able to determine the number of competing nodes for the channel. Accordingly, the aim of the present study is to establish a more realistic approach for determining the optimal CW size. In practice, the throughput of wireless networks is closely related to the collision rate. Moreover, in backoff algorithms, the collision rate increases as the CW size reduces. Therefore, a further series of simulations was performed to investigate the relationship between the collision rate, the system throughput and the CW size in typical IEEE 802.11 environments with DCF. Figure 8, Figure 9, Figure 10, Figure 11 and Figure 12 show the corresponding results for networks containing 10, 20, 30, 40 and 50 nodes, respectively.
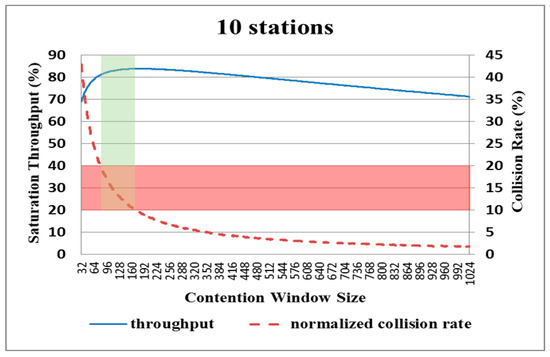
Figure 8.
Variation in system throughput and collision rate with CW size for network with 10 nodes.
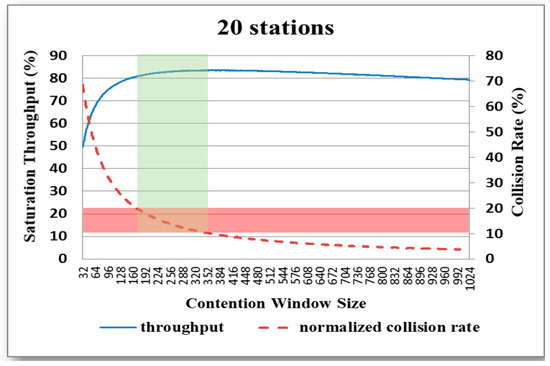
Figure 9.
Variation in system throughput and collision rate with CW size for network with 20 nodes.
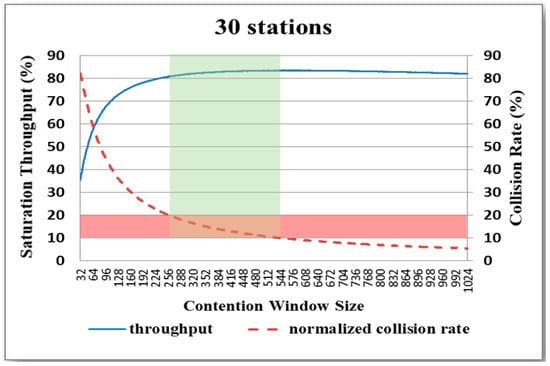
Figure 10.
Variation in system throughput and collision rate with CW size for network with 30 nodes.
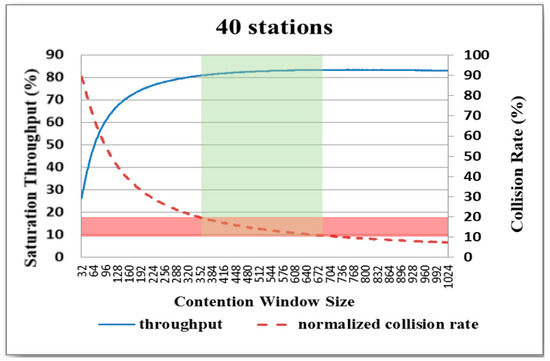
Figure 11.
Variation in system throughput and collision rate with CW size for network with 40 nodes.
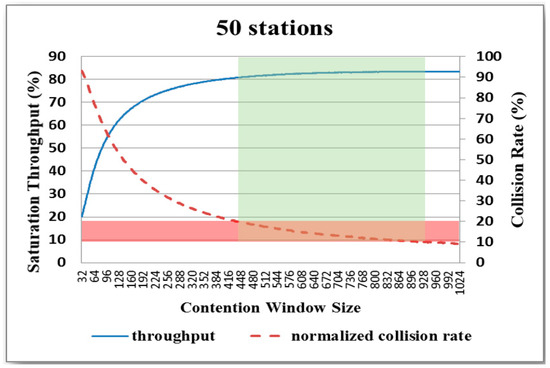
Figure 12.
Variation in system throughput and collision rate with CW size for network with 50 nodes.
For each network, the collision rate decreases as the CW size increases. Thus, as described above in Figure 6, the system throughput generally improves with an increasing CW size, particularly as the CW size first increases. An inspection of Figure 8, Figure 9, Figure 10, Figure 11 and Figure 12 shows that, for each of the considered networks, the maximum system throughput occurs for collision rates in the range of 0.1–0.2. Importantly, in WLANs, each node is able to determine the collision rate for itself by counting the transmission results. Therefore, as described in the following section, the present study proposes a backoff algorithm in which the system throughput is maximized by controlling the CW size in such a way that the collision rate remains in the interval of 0.1–0.2.
4. Rapidly Adaptive Collision Backoff (RACB) Algorithm
4.1. Analytical Model for Relationship between Optimal CW Size and Collision Rate
To simplify the mathematical analysis, the following assumptions are undertaken: (1) the wireless network operates at saturation conditions; (2) the wireless channel is an error-free medium and (3) the hidden node problem does not exist. Table 2 summarizes the notations used in the mathematical analysis.

Table 2.
Notations used in mathematical analysis.
In the proposed model, the system throughput (S) is defined as
In other words, S is defined as the fraction of time for which the channel is sensed busy due to the successful transmission of payload packets. S can be elaborated as follows:
where PS is the probability of a successful transmission over the wireless channel, E[P] is the average packet payload size, TS is the average time for which the channel is sensed busy due to a successful transmission and PI is the probability that the channel is sensed idle. In addition, σ is the slot time, PC is the probability of a channel collision and TC is the average time for which the channel is sensed busy due to a collision.
TS and TC can be formulated as shown in Equation (3), where P* is the average length of the longest packet payload involved in a collision.
In calculating the system throughput, the model assumes that the network contains n nodes and each node has a transmission probability of τ. The probability of none of the nodes transmitting over the wireless channel, PI, is thus provided as
Meanwhile, the probability PS that only one of the n nodes transmits over the wireless channel, while the remaining n-1 nodes remain idle, can be described as
Finally, the probability PC of more than one node attempting to transmit over the wireless channel at the same time is provided by
Probabilities PI, PS and Pc are calculated from the system perspective. From the node perspective, the equivalent probabilities are denoted as pi, ps and pc, where pi is the probability that the node is in an idle state (Equation (7)), ps is the probability that the node achieves a successful transmission (Equation (8)) and pc is the probability that the node transmission collides in the wireless channel (Equation (9)).
In DCF, the size of the CW changes after each transmission attempt. The variation in the backoff window size is shown by the Markov chain model in Figure 13.
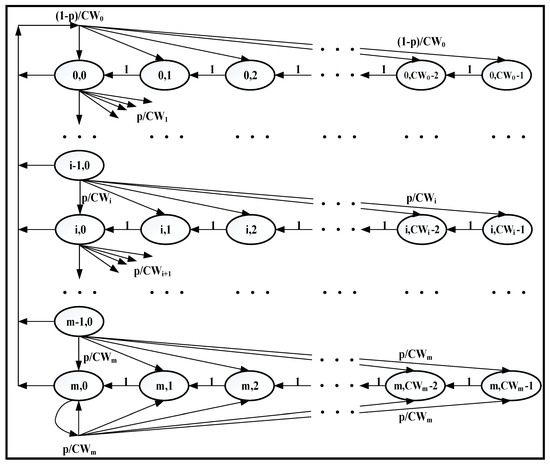
Figure 13.
Markov chain model for variation in backoff window size in DCF [5].
In Figure 13, p is the collision probability, CWi is the CW size after i collisions, m is the maximum number of backoff stages and bi, CWi−x is the probability that the node is in a certain state b after i collisions and the remaining value of the backoff timer is CWi−x. In other words, bi,0 is the probability that the node is in state b after i collisions and the backoff timer is equal to zero. Mathematically, the probability bi,k can be formulated as
Owing to the chain regularities, for each , it follows that
By combining Equation (10) and , Equation (11) can be rewritten as
Furthermore, by combining Equations (10) and (12), can be expressed as a function of and p as
Equation (13) can be simplified to
The probability τ that a node transmits when the value of the backoff timer is equal to zero can be expressed as
Taking the CW size as a constant value, Equation (15) can be simplified by setting m = 0 as
In other words, for a given value of CW, the transmission probability τ has a constant value. Accordingly, the relationship between the optimal CW size and the maximum system throughput for different numbers of nodes can be obtained as shown in Figure 14. Furthermore, from Equation (16), the relationships between the optimal CW size and the transmission probability, and the transmission probability and the collision rate, respectively, can be obtained as a function of the number of nodes in the network, as shown in Figure 15 and Figure 16.
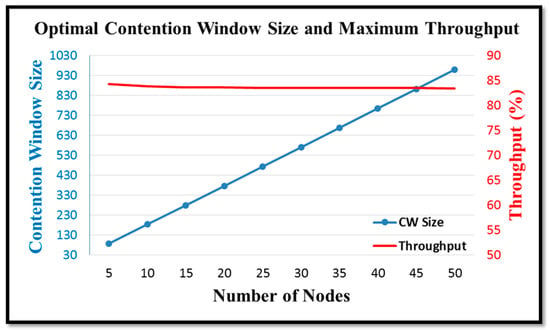
Figure 14.
Relationship between optimal CW size and maximum throughput in networks with different numbers of nodes.
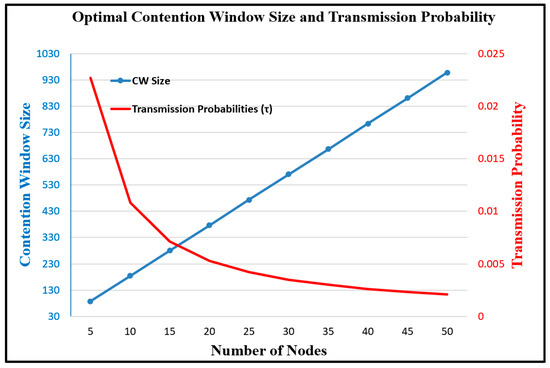
Figure 15.
Relationship between optimal CW size and transmission probability in networks with different numbers of nodes.
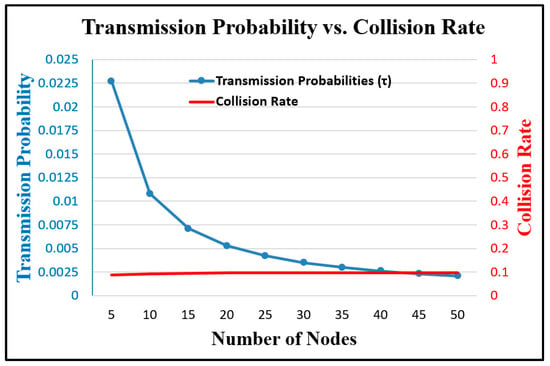
Figure 16.
Relationship between transmission probability and collision rate in networks with different numbers of nodes.
Overall, the results presented in Figure 14, Figure 15 and Figure 16 show that the optimal CW size causes the collision rate to approach 0.1 for any number of nodes in the network. Therefore, by adjusting the CW size in such a way that the collision rate of the nodes remains close to 0.1, the system throughput approaches the maximum DCF throughput [14], irrespective of the size of the network.
4.2. CW Size Adjustment in Rapidly Adaptive Collision Backoff (RACB) Algorithm
As in all existing backoff algorithms [1,7,8,9,10,11,12,13], the RACB algorithm proposed in the present study adjusts the CW size after each transmission. However, while existing algorithms adjust the CW size based on the transmission outcome (i.e., success or collision), RACB adjusts the CW size based on the collision rate of the nodes.
RACB combines the respective advantages of EIED and LILD. In particular, as shown in Figure 17, when the collision rate is much higher or much lower than a specified index value, α, the CW size is adjusted exponentially such that the current collision rate of the node is rapidly restored to the target value (i.e., α = 0.1). Conversely, when the collision rate of the node falls between a high threshold value () and a low threshold value (), the CW size is already close to the optimal value. Thus, the CW size is adjusted linearly (rather than exponentially) in order to maintain the collision rate within this interval and maximize the system throughput accordingly.
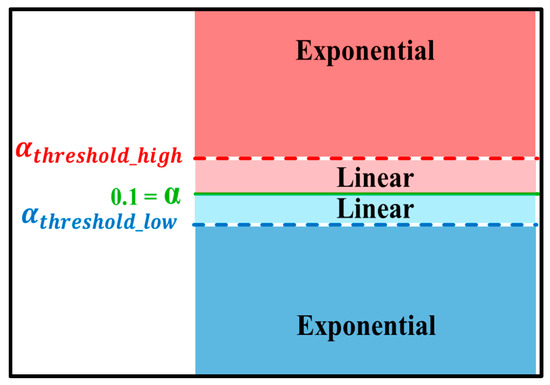
Figure 17.
Variation in CW size in RACB algorithm.
The collision rate is a statistical value obtained after several transmissions. In other words, a collision rate of 0.1 indicates that one transmission failed within the past 10 transmissions. Consequently, to adjust the CW size, RACB adopts a Collision Rate Index (CRI) as the current collision rate. Let WT be the weight of the current collision rate and () be the weight of the historical collision rate. The CRI is then formulated as
where collision is the transmission result and has a value of 0 for a successful transmission and 1 for a collision.
Figure 18 presents the pseudo code of the RACB algorithm. As shown, the CRI value is updated after each transmission. If CRIT is higher than , the CW size is doubled (CWi = CWi−1 * 2) until it reaches CWmax. By contrast, if CRIT is lower than , the CW size is halved (CWi = CWi−1/2) until it reaches CWmin. If CRIT lies between and α, the CW size is increased by CWmin (CWi = CWi−1 + CWmin). Finally, if CRIT lies between α and , the CW is decreased by CWmin (CWi = CWi−1 − CWmin).
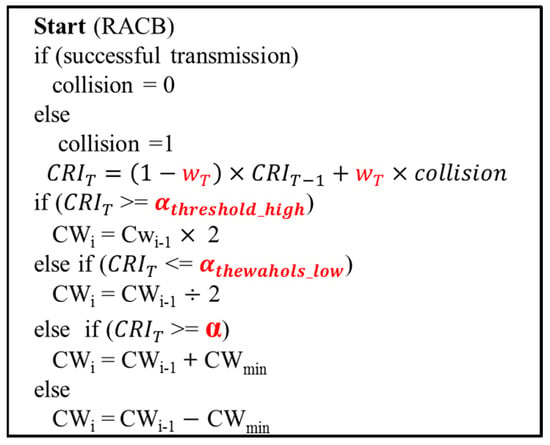
Figure 18.
Pseudo code for Rapidly Adaptive Collision Backoff algorithm.
5. Performance Evaluation
5.1. Experimental Environment and Parameter Settings
The performance of the proposed RACB algorithm was compared with that of four existing backoff algorithms (DCF, EIED, LILD and ELBA). The simulations considered the wireless topology shown in Figure 19 with n nodes operating at saturation conditions in an error-free medium with no hidden node problem. The 802.11 WLAN (PHY: DSSS) parameters were assigned the same values as those used in [5] (Table 3).
Figure 19.
Network topology.

Table 3.
Simulation parameters.
5.2. Numerical Results
Figure 20 and Figure 21 show the simulation results obtained for the variations in the collision rate and system throughput, respectively, with the number of nodes in the network under five different backoff algorithms (BEB, LILD, EIED, ELBA and RACB). Among the existing algorithms, ELBA achieves the lowest collision rate and the highest normalized throughput. However, the throughput still does not approach the ideal maximum value in [14] due to the non-optimality of the CW size.
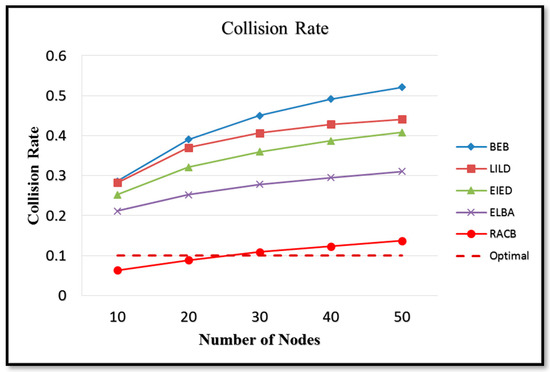
Figure 20.
Variation in collision rate with number of nodes under different backoff algorithms.
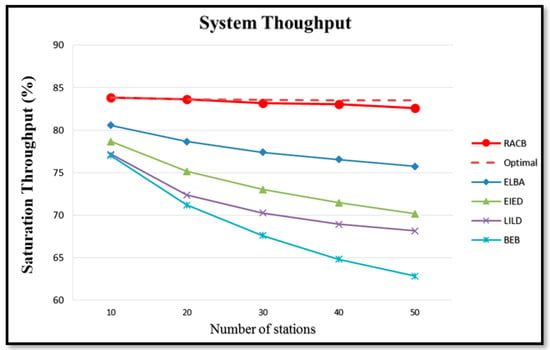
Figure 21.
Variation in throughput with number of nodes under different backoff algorithms.
Among all the algorithms considered in Figure 20 and Figure 21, the RACB algorithm achieves the lowest collision rate and the maximum normalized throughput. For all values of n, the normalized throughput is close to the ideal maximum value. As a result, the effectiveness of the RACB algorithm in maximizing the system throughput by adjusting the CW size in such a way as to maintain a collision rate close to 0.1 is confirmed.
6. Conclusions
This study has derived a mathematical model to describe the relationship between the CW size and the collision rate in IEEE 802.11 wireless networks. It has been shown that the system throughput approaches the ideal maximum value for DCF when the collision rate of the network is close to 0.1. Accordingly, a Rapidly Adaptive Collision Backoff (RACB) algorithm has been proposed in which the CW size is adjusted after each transmission in such a way as to maintain the collision rate close to the ideal value of 0.1. Notably, the proposed algorithm can be deployed in both lightly loaded and heavily loaded networks and requires no knowledge of the number of nodes competing for the wireless channel. Furthermore, RACB combines the respective advantages of EIED and LILD in rapidly adjusting the CW size such that it remains close to the optimal size after each transmission. The numerical results have shown that RACB achieves a higher system throughput than the BEB, EIED, LILD and ELBA algorithms proposed in the literature. Future studies will explore the effects of the analytical model assumptions, namely an error-free medium and no hidden node problem, on the system throughput and collision rate [17,18,19,20,21,22,23,24,25,26,27,28,29].
Author Contributions
Conceptualization, C.-H.L. and W.-S.H.; methodology, C.-H.L., M.-H.C. and W.-S.H.; software, C.-K.S. and Y.-H.W.; validation, C.-H.L. and W.-S.H.; formal analysis, C.-H.L. and M.-H.C.; investigation, C.-K.S. and Y.-H.W.; resources, C.-K.S. and W.-S.H.; data curation, C.-H.L. and W.-S.H.; writing—original draft preparation, C.-H.L. and M.-H.C.; writing—review and editing, C.-H.L., M.-H.C. and Y.-H.W.; visualization, C.-H.L. and M.-H.C.; supervision, C.-K.S. and W.-S.H.; project administration, C.-K.S. and W.-S.H.; funding acquisition, C.-K.S. and W.-S.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Science and Technology Council, grant number MOST 108-2221-E-242-001, MOST 110-2221-E-992-029-MY2. Further, the APC was supported in part by Fooyin University Research Project with the grant number FYU1300-111-04.
Data Availability Statement
The data used to support the findings of this study are available from the corresponding author upon request.
Acknowledgments
We thank the anonymous reviewers for their constructive comments, which helped in improving the quality of this paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- IEEE Standard 802.11; IEEE Standard for Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: Piscataway, NJ, USA, 1999.
- Wang, K.; Zhang, B.; Alenezi, F.; Li, S. Communication-efficient surrogate quantile regression for non-randomly distributed system. Inf. Sci. 2022, 588, 425–441. [Google Scholar] [CrossRef]
- Wu, H.; Han, X.; Zhu, H.; Chen, C.; Yang, B. An Efficient Opportunistic Routing Protocol with Low Latency for Farm Wireless Sensor Networks. Electronics 2022, 11, 1936. [Google Scholar] [CrossRef]
- Vedula, V.; Lama, P.; Boppana, V.R.; Trejo, A.L. On the Detection of Low-Rate Denial of Service Attacks at Transport and Application Layers. Electronics 2021, 10, 2105. [Google Scholar] [CrossRef]
- Song, N.O.; Kwak, B.J.; Miller, L.E. Analysis of EIED backoff algorithm for the IEEE 802.11 DCF. In Proceedings of the IEEE Vehicular Technology Conference, Dallas, TX, USA, 28–28 September 2005. [Google Scholar]
- Xu, S.; Dai, H.; Feng, L.; Chen, H.; Chai, Y.; Zheng, W.X. Fault Estimation for Switched Interconnected Nonlinear Systems with External Disturbances via Variable Weighted Iterative Learning. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 2011–2015. [Google Scholar] [CrossRef]
- Hu, J.; Wu, Y.; Li, T.; Ghosh, B.K. Consensus Control of General Linear Multiagent Systems with Antagonistic Interactions and Communication Noises. IEEE Trans. Autom. Control 2019, 64, 2122–2127. [Google Scholar] [CrossRef]
- Peng, Y.; Long, K.; Cheng, S.; Ma, J. Performance of reliable transport protocol over IEEE 802.11 wireless LAN: Analysis and enhancement. In Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies INFOCOM, New York, NY, USA, 23–27 June 2002. [Google Scholar]
- Vergados, D.J.; Amelina, N.; Jiang, Y.; Kralevska, K.; Granichin, O. Local voting: Optimal distributed node scheduling algorithm for multihop wireless networks. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; pp. 1014–1015. [Google Scholar]
- Cheng, M.H.; Hwang, W.S.; Wu, Y.J.; Lin, C.H.; Syu, J.S. An Effective Flow-Rule-Reducing Algorithm for Flow Tables in Software-Defined Networks. In Proceedings of the International Computer Symposium (ICS 2020), Tainan, Taiwan, 17–19 December 2020. [Google Scholar]
- Song, N.; Kwak, B.; Song, J.; Miller, L.E. Enhancement of IEEE 802.11 distributed coordination function with exponential increase exponential decrease backoff algorithm. In Proceedings of the 57th IEEE Semiannual Spring VTC, Jeju, Republic of Korea, 22–25 April 2003. [Google Scholar]
- Ye, S.R.; Tseng, Y.C. A multichain backoff mechanism for IEEE 802.11 WLANs. IEEE Trans. Veh. Technol. 2006, 55, 1613–1620. [Google Scholar] [CrossRef]
- Lin, C.H.; Shieh, C.K.; Hwang, W.S.; Ke, C.H. An exponential-linear backoff algorithm for contention-based wireless networks. In Proceedings of the International Conference on Mobile Technology, Applications, and Systems (ACM 2008), Yilan, Taiwan, 10–12 September 2008. [Google Scholar]
- Weng, C.E.; Chen, C.Y.; Chen, C.H.; Chen, C.H. Optimal performance study of IEEE 802.11 DCF with contention window. In Proceedings of the International Conference on Broadband and Wireless Computing, Communication and Applications (BWCCA 2011), Barcelona, Spain, 26–28 October 2011. [Google Scholar]
- Syed, I.; Roh, B. Adaptive Backoff Algorithm for Contention Window for Dense IEEE 802.11 WLANs. Mob. Inf. Syst. 2016, 2016, 8967281. [Google Scholar] [CrossRef]
- NS2 Learning Guide. Available online: https://csie1.nqu.edu.tw/smallko/ns2_old/ns2.htm (accessed on 30 May 2023).
- Yang, M.; Li, B. Survey and Perspective on Extremely High Throughput (EHT) WLAN—IEEE 802.11be. Mob. Netw. Appl. 2020, 25, 1765–1780. [Google Scholar] [CrossRef]
- Cho, L.; Chen, C.Y.; Hsu, C.Y. Improved ISR for IEEE 802.11ah Nonlinearity Compensation via Adjustable Constellation Borders. Electronics 2021, 10, 1573. [Google Scholar] [CrossRef]
- Zazhigina, E.; Yusupov, R.; Khorov, E.; Lyakhov, A. Analytical Study of Periodic Restricted Access Window Mechanism for Short Slots. Electronics 2021, 10, 549. [Google Scholar] [CrossRef]
- Tilwari, V.; Song, T.; Pack, S. An Improved Routing Approach for Enhancing QoS Performance for D2D Communication in B5G Networks. Electronics 2022, 11, 4118. [Google Scholar] [CrossRef]
- Mkongwa, K.G.; Liu, Q.; Wang, S. An adaptive backoff and dynamic clear channel assessment mechanisms in IEEE 802.15.4 MAC for wireless body area networks. Ad Hoc Netw. 2021, 120, 102554. [Google Scholar] [CrossRef]
- Lin, C.H.; Shieh, C.K.; Hwang, W.S.; Huang, W.T. Proportional bandwidth allocation with consideration of delay constraint over IEEE 802.11e-based wireless mesh networks. Wirel. Netw. 2018, 24, 1575–1592. [Google Scholar] [CrossRef]
- Zheng, Y.; Lu, K.; Wu, D.; Fang, Y. Performance analysis of IEEE 802.11 DCF in imperfect channels. IEEE Trans. Veh. Technol. 2006, 55, 1648–1656. [Google Scholar] [CrossRef]
- Cali, F.; Conti, M.; Gregori, E. IEEE 802.11 protocol: Design and performance evaluation of an adaptive backoff mechanism. IEEE J. Sel. Areas Commun. 2000, 18, 1774–1786. [Google Scholar] [CrossRef]
- Ni, Q.; Aad, L.; Barakat, C.; Turletti, T. Modeling and analysis of slow CW decrease IEEE 802.11 WLAN. In Proceedings of the 14th IEEE Proceedings on Personal, Indoor and Mobile Radio Communications, Beijing, China, 7–10 September 2003. [Google Scholar]
- Feng, L.; Yu, J.; Cheng, X.; Atiquzzaman, M. A novel contention-on-demand design for WiFi hotspots. Pers. Ubiquitous Comput. 2016, 20, 705–716. [Google Scholar] [CrossRef]
- Jiang, Y.; Liu, S.; Li, M.; Zhao, N.; Wu, M. A new adaptive co-site broadband interference cancellation method with auxiliary channel. Digit. Commun. Netw. 2022, in press. [Google Scholar] [CrossRef]
- Zhong, Q.; Han, S.; Shi, K.; Zhong, S.; Kwon, O.-M. Co-Design of Adaptive Memory Event-Triggered Mechanism and Aperiodic Intermittent Controller for Nonlinear Networked Control Systems. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 4979–4983. [Google Scholar] [CrossRef]
- Zhou, G.; Zhou, X.; Chen, J.; Jia, G.; Zhu, Q. LiDAR Echo Gaussian Decomposition Algorithm for FPGA Implementation. Sensors 2022, 22, 4628. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).