1. Introduction
Communication-induced checkpointing (hereafter, CIC) is a rollback recovery technique that requires no explicit synchronization procedure with other processes upon checkpointing and that precludes the occurrence of the domino-effect phenomenon [
1]. These features can be realized by having every process piggyback on each sent message, some control information of other processes as well as itself. In addition, if needed before message delivery, additional checkpoints, called forced checkpoints, can be taken based on the local variables of the process and the information piggybacked on the messages [
2]. Most CIC protocols [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15] with these advantages have the following common behavioral features. If each process recognizes the delivery of a message may make any other local checkpoint of another process, called a basic checkpoint, become useless, the protocols make the process take a forced checkpoint.
CIC protocols are classified into two types, model-based CIC and timestamp-based CIC [
1]. Although model-based protocols [
3,
4] may be transformed to their corresponding timestamp-based ones [
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15], the overhead of the first, in its eagerness to break suspicious message exchange patterns, can be considerably higher than that of the second in terms of the number of forced checkpoints [
1]. Timestamp-based protocols have continuously advanced with their protocol-specific checkpoint timestamping schemes using Lamport’s logical clock to decrease the number of forced checkpoints in the following manner. Early-stage CIC protocols [
5,
6] make each process take a forced checkpoint if their timestamp-increasing flow condition is not satisfied when comparing its local timestamp with the one piggybacked on each message received. However, this may cause a large number of unnecessary forced checkpoints due to the inaccuracy in decisions about the uselessness of basic checkpoints of other processes. To cut back on the overhead as much as possible, improved protocols [
7,
8,
11,
12,
13,
14,
15] have been designed to utilize more information piggybacked on each message, including the most recent checkpoint timestamp of every other process. In particular, among them, a representative protocol [
7], HMNR, attempts to lower the forced checkpointing overhead by narrowing the condition inducing forced checkpoints with the help of the control information contained in each message received. A recently enhanced version of HMNR, LazyHMNR [
8], is designed to balance the growing rates of checkpoint timestamps of processes by temporarily ceasing to increase the timestamps taken of outliers.
However, despite efforts to decrease the frequency of forced checkpointing, these previous protocols have a much greater number of forced checkpoints than basic checkpoints, highly increasing additional execution time and the stable storage size required [
16]. This results in the negative effect of slower acquisition of the most recent timestamps of the next checkpoints of other processes when receiving each message. Accurate situation awareness with diversified information conveyance paths is needed to make the number of unnecessary forced checkpoints taken as low as possible.
Although developed to operate based on a reliable first-in, first-out (hereafter, FIFO) communication channel, most traditional CIC protocols [
3,
4,
5,
6,
7,
8,
10,
11,
12,
13,
14,
15] do not use this advantageous feature to lessen this sort of forced checkpointing overhead. A previous CIC protocol [
9] attempted to decrease the number of forced checkpoints by obtaining the up-to-date local clock of the next checkpoint of every other process based on performing sender-based message logging earlier than before. However, the protocol may not only generate a few extra control messages but may also greatly lengthen the latency of message sending. In addition, it has a critical limitation that, due to its usage of message logging, the applicable process execution model can be piecewise deterministic only. Another most recent CIC protocol [
10] is designed to use pessimistic message logging to cut down on the forced checkpointing frequency. The protocol can overcome the constraint of the piecewise deterministic model by recognizing which execution point is deterministic in each checkpoint interval. However, it has the same limitation as the traditional ones [
3,
4,
5,
6,
7,
8,
11,
12,
13,
14,
15] mentioned above—that is, the slow gathering of the most recent local timestamp of the next checkpoint of every other process. In addition, if non-deterministic events that cannot be logged often occur in the execution of processes, the performance gain may be greatly diminished.
This paper proposes a scalable CIC protocol to considerably cut down the possibility of performing unnecessary forced checkpointing by exploiting the beneficial feature of reliable communication channels generally assumed in the research field, namely, rollback recovery with checkpointing and message logging. This protocol enables each process sending a message to attain the most recent timestamp-related information of the next checkpoint of its receiver as fast as possible and accelerate the spread of the information to others with little overhead. For this purpose, the information is piggybacked on the acknowledgment of each application message essential to ensuring communication reliability, which requires no additional control message. In addition, it allows each process to perform actual message sending operations right after receiving messages without any delay, unlike the existing protocols [
9]. Moreover, the protocol is never constrained by the piecewise deterministic execution model because it does not utilize message logging.
3. The Scalable CIC Protocol
The proposed CIC protocol, LightweightCIC, is designed to substantially decrease the possibility of making wrong decisions when performing forced checkpointing, as follows:
The protocol enables each process sending a message to attain the most recent timestamp information of the next checkpoint of its receiver as fast as possible and accelerate the spread of the information to others in a lightweight manner.
It incurs neither additional control message nor delay in the completion of application message send operations executed right after each message is received.
It can always be operated under the non-deterministic execution model.
The protocol can meet the third requirement because it is a checkpoint-only protocol using no message logging technique unlike our previous one [
9]. Then, to combine the first and second requirements together, it exploits the beneficial feature of reliable communication channels, as follows. The protocol has each process
r receiving a message
from another process
q piggyback its current timestamp (
(
r)) upon acknowledgment of
, denoted by
. Then, it propagates the information,
.
, not only to its sender
q but also to others in an effective manner. With this immediate update of the information, the protocol identifies whether
q should take a forced checkpoint upon receipt of a message
based on Equations (
4) and (
5), unlike the HMNR protocols [
7,
8,
14,
15]:
Compared with Equation (
3), Equation (
5) can greatly enhance the up-to-dateness of the two important variables of each process
q,
and
, and speed up their dissemination to other processes. This improvement may greatly boost the accuracy of both
and (
>
) in
. With this feature, the protocol can greatly reduce the possibility of taking unnecessary forced checkpoints compared to the existing protocols [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15]. We proved the superiority of Equation (
5) over Equation (
3) in Lemma 1 in terms of the number of forced checkpoints taken.
Lemma 1. Equation (5) causes fewer or the same forced checkpoints as Equation (3) to be taken. Proof. We prove the correctness of the lemma by contradiction. It is assumed that Equation (
5) may lead to more forced checkpoints being taken than Equation (
3), meaning the first equation cannot detect the situations where forced checkpointing need not be performed more accurately than the latter, as Theorem 2 is satisfied. Suppose two consecutive messages
and
form an NC-pattern where sending
to
r after Ck
before Ck
precedes receiving
from
p after Ck
before Ck
in the same checkpoint interval CI
. There are two cases that can happen, as follows:
Case 1: . ≤ ..
In this case, as Ck. ≤ . < Ck., both equations enable q to skip performing a forced checkpointing action when q receives .
Case 2: . > ..
In this case, we should consider two subcases, as follows:
Case 2.1: . ≥ (r) right after .
In this case, as Ck. ≮ Ck., both equations cause a forced checkpoint to be taken when q receives .
Case 2.2: . < (r) right after .
In this case, we should consider the following two subcases:
Case 2.2.1: . > (r) right after .
In this case, as Ck. ≮ Ck., both equations force q to decide to perform a forced checkpointing action when q receives .
Case 2.2.2: . ≤ (r) right after .
In this case, Ck
.
≤
.
< Ck
.
. Equation (
5) can detect this situation because
.
is equal to
(
r) right after
and results in no forced checkpoint being taken when
q receives
. However, Equation (
3) cannot identify this situation without the help of a C-path starting with
and bringing
(
r) to
q before
q actually delivers
. Due to this limitation, Equation (
3) may exclude this situational possibility to skip taking a forced checkpoint.
Therefore, Equation (
5) leads to fewer or the same number of forced checkpoints to be taken as in Equation (
3). This contradicts the hypothesis. □
Figure 7 shows the formal description of five modules of the proposed protocol for each process
p. The first module,
Initialize(), initializes all the variables that
p should maintain and takes its initial checkpoint. The second module,
Local-Checkpointing(), increments both its checkpoint timestamp and the number of checkpoints taken by
p from the beginning of its execution by one. Then, it resets several other variables used for deciding whether the value of
is true and records its current state with the first two variables in the stable storage. The third module,
MSG-Send(), indicates that
p sends a message
m to the receiver of
m after its most recent checkpoint. Then,
p sends the message with the variables for making a decision about whether the receiver is forced to take a checkpoint before delivering
m. The fourth module,
MSG-Recv(), first checks whether the received message may make useless checkpoints. If so,
p performs a forced checkpointing by calling
Local-Checkpointing(). Then,
p sends an acknowledgment with its checkpoint timestamp and
. Next, it updates its local variables related to the decision-making condition according to the values of the piggybacked variables and delivers the contents of the message to its target application. The last module,
Ack-Recv(), updates its checkpoint timestamp and
according to the value of the checkpoint timestamp piggybacked on the acknowledgment.
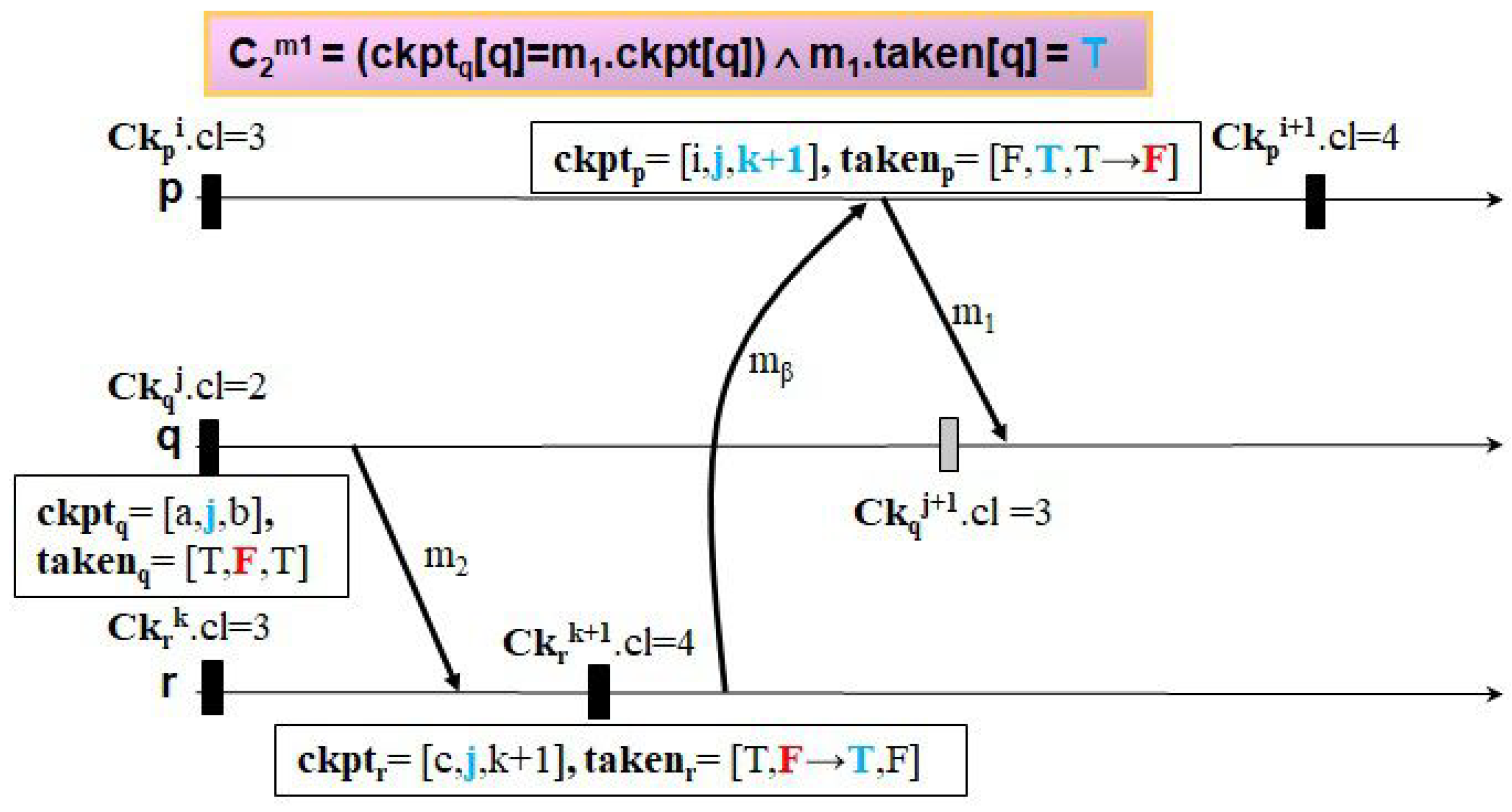
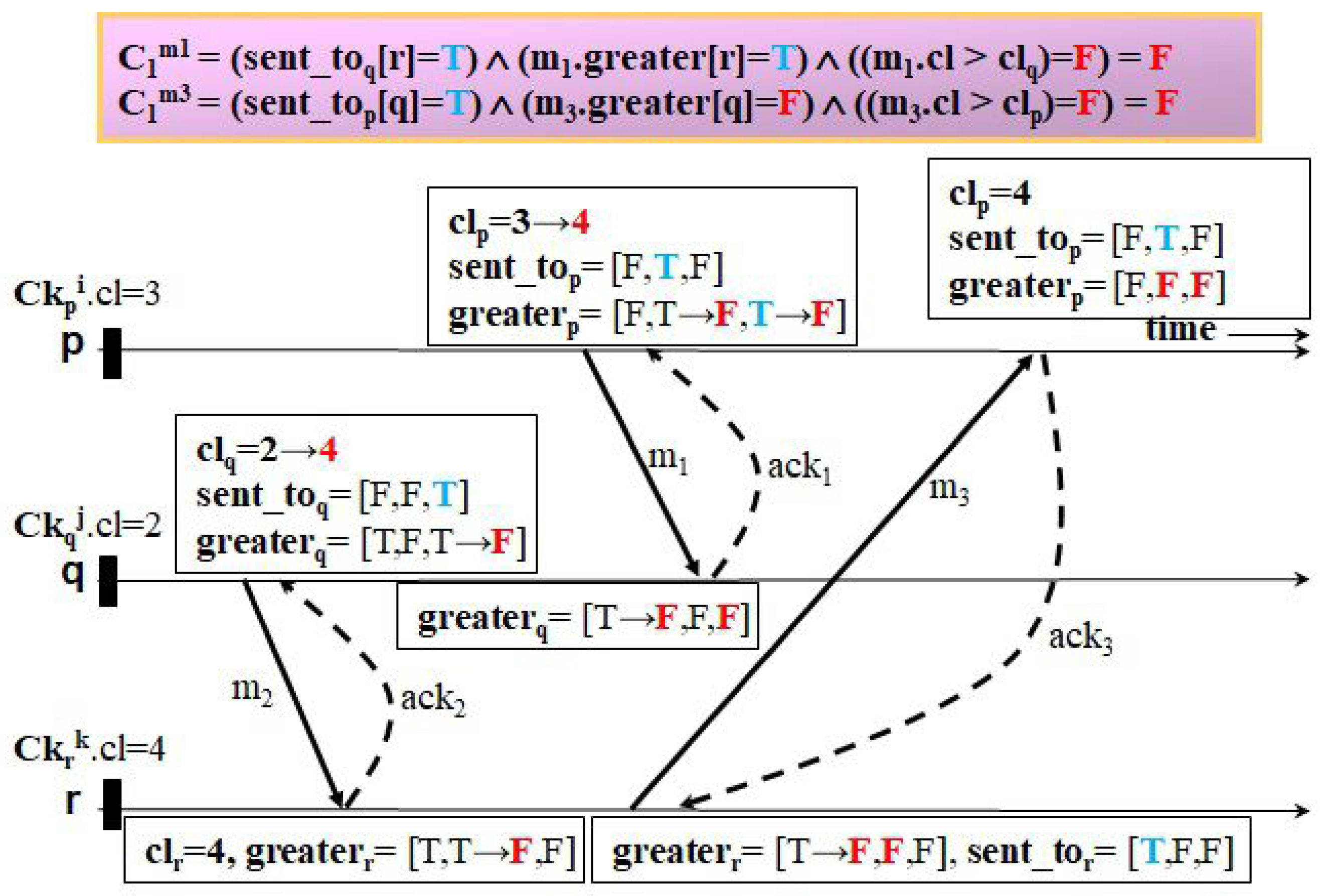
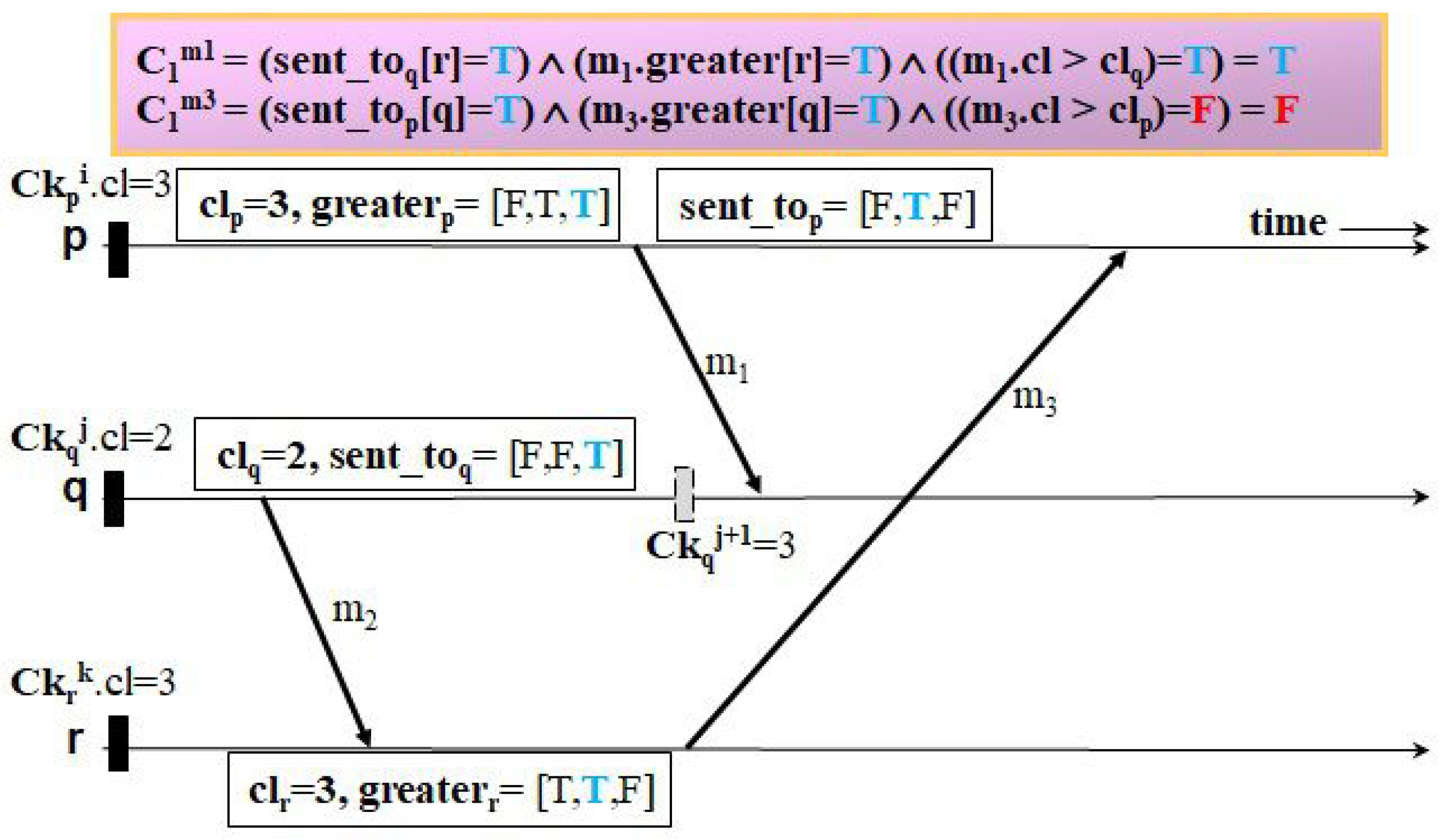
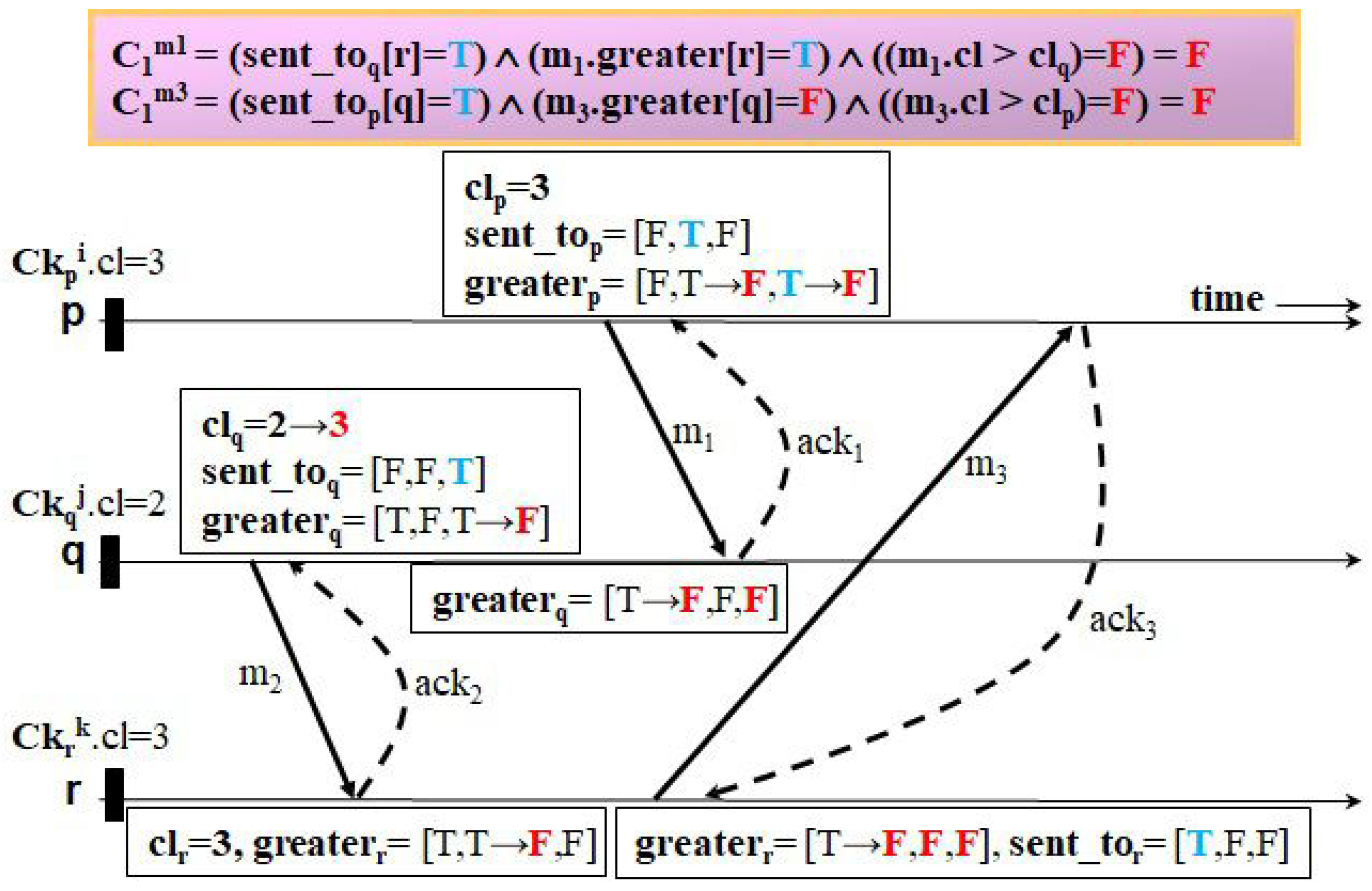
Let us examine how our protocol can fulfill both requirements with the beneficial feature unlike a representative useless checkpoint-free CIC protocol, HMNR, using several examples of checkpointing and communication patterns.
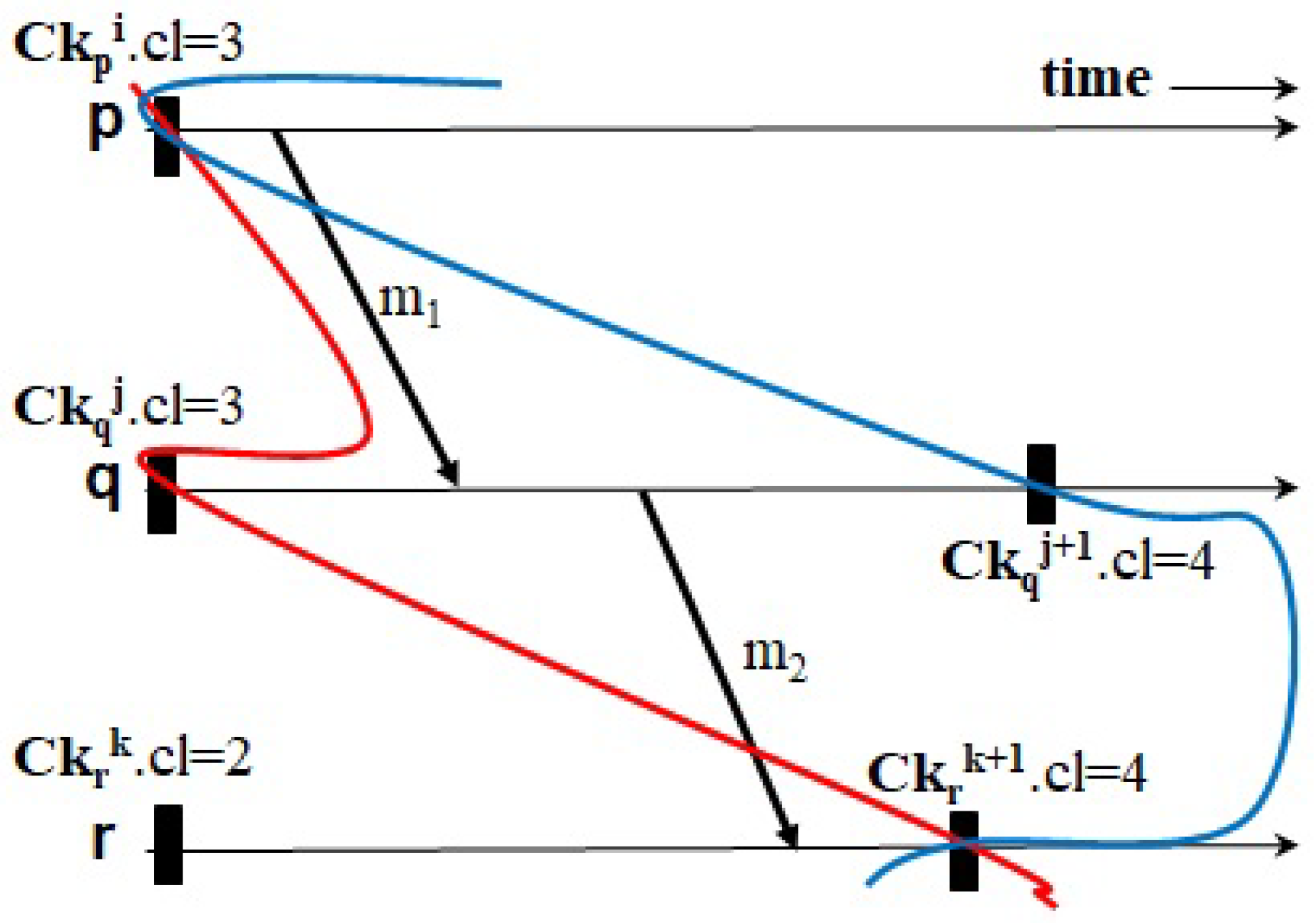
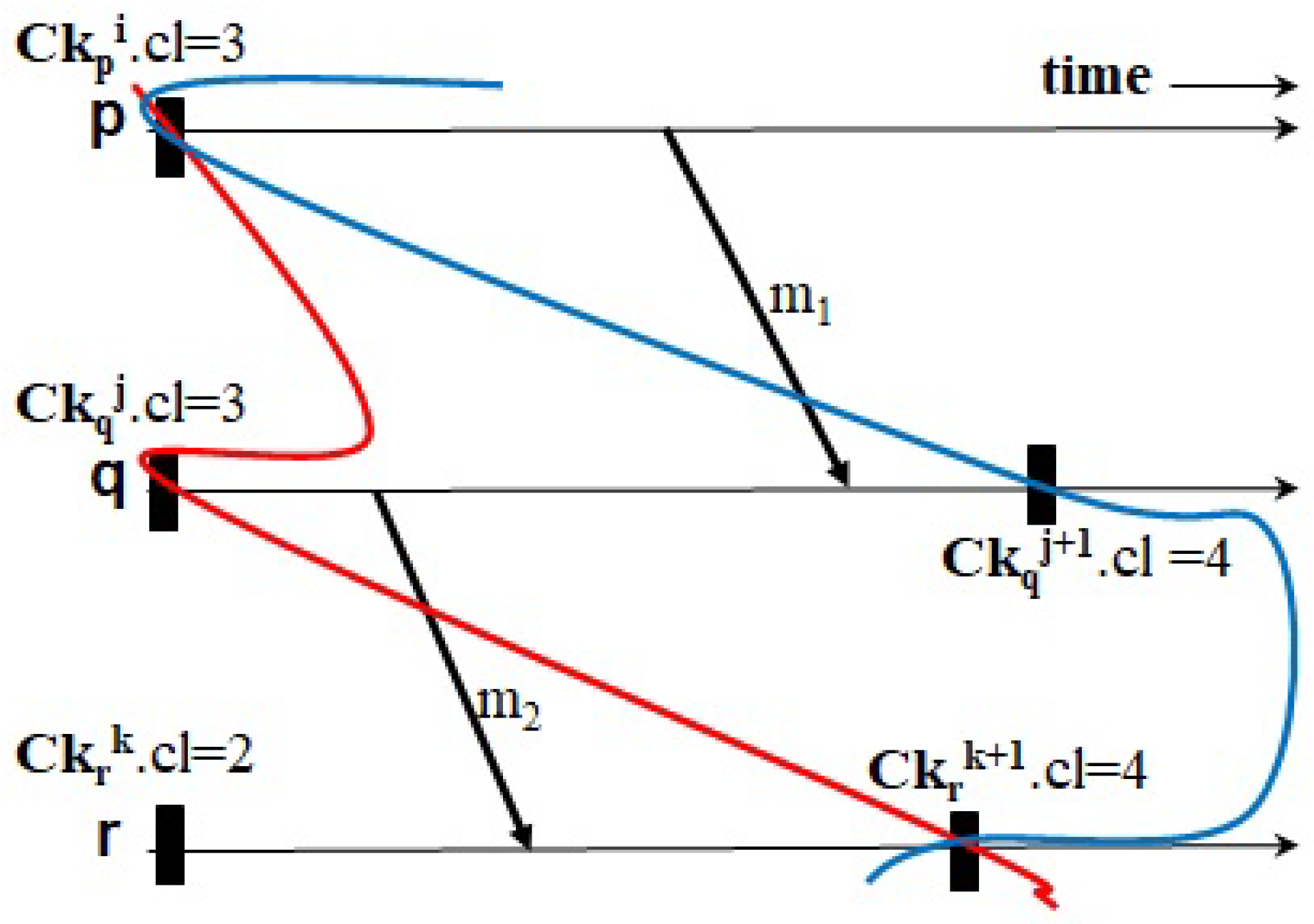
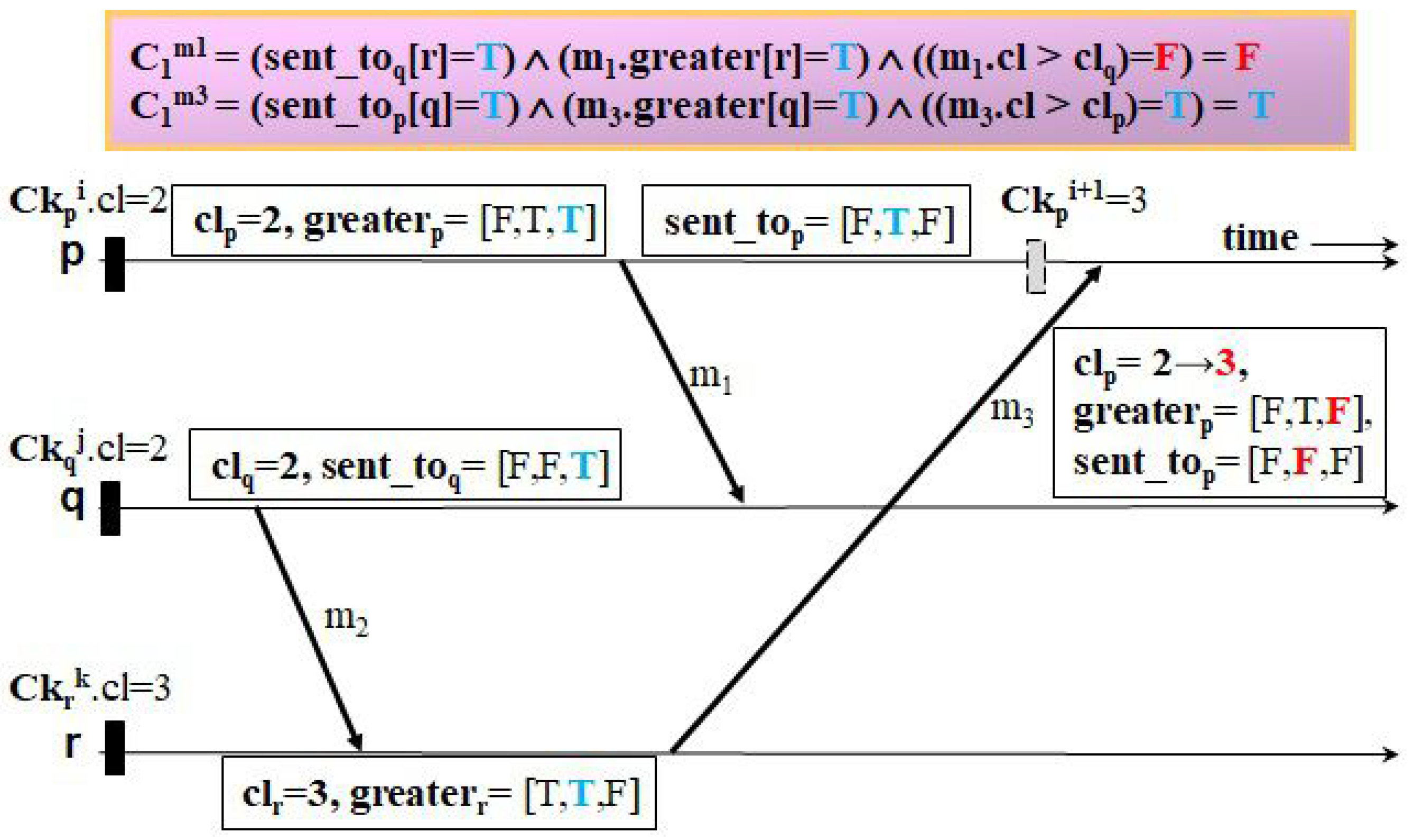
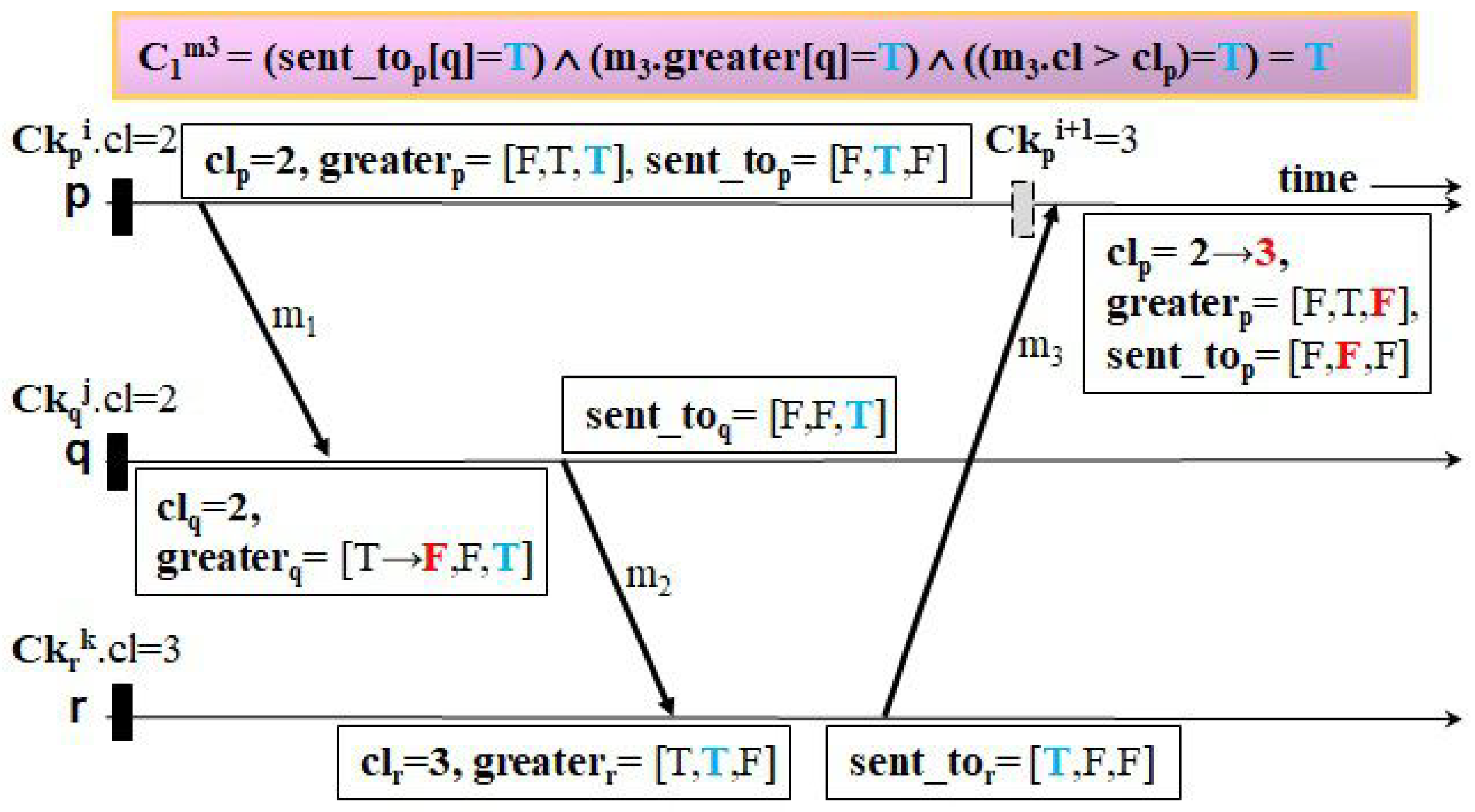
Figure 8,
Figure 9,
Figure 10,
Figure 11,
Figure 12 and
Figure 13 illustrate four examples to clarify how the two protocols trigger events of taking forced checkpoints with three messages,
,
, and
. The first example, shown in
Figure 8 and
Figure 9, shows the case where Ck
.
< Ck
.
< Ck
.
. In
Figure 8, HMNR takes two unnecessary forced checkpoints, as follows. When receiving
,
q decides to record a forced checkpoint state Ck
before
because it has a mistaken knowledge that Ck
.
is equal to that of the next checkpoint of
r (i.e., the value of
is true). Similarly, as
p receives
from
r, it performs forced checkpointing because it knows Ck
.
is equal to that of the next checkpoint of
q after having received
(i.e., the value of
is true). However, in
Figure 9, LightweightCIC triggers no events of forced checkpointing for the reasons mentioned below. On the receipt of
,
r knows its current logical clock value is greater than
piggybacked on
(on calling module
MSG-Recv()). Then, it conveys to
q the acknowledgment of
with
and
and indicates that the updated checkpoint timestamp of
q is equal to
(
[
q]←F). Afterwards,
q changes
and
to the current timestamp of
r piggybacked on the acknowledgment and
.
(on calling module
Ack-Recv()). When receiving
,
q can accurately recognize it is not necessary for
q to take a forced checkpoint as Ck
.
< Ck
.
(i.e., the value of
is false) (on calling module
MSG-Recv()). Then, as
q knows
is less than
, it immediately transmits the acknowledgment of
with
and
to
p and sets
[
p] to F. Upon receiving this message,
p updates
and every
[
i](
i≠
p) with
.
and
.
[
i], respectively, (on calling module
Ack-Recv()), like in
Figure 9. When receiving
, LightweightCIC restrains
p from performing forced checkpointing because it knows Ck
.
< Ck
.
(i.e., the value of
is false) (on calling module
MSG-Recv()). Upon the receipt of
,
r changes
[
p] to F. With this reduction in overhead, the proposed protocol requires no extra control message to quickly update the recovery information and has no delay on actually sending messages right after each message is received by their corresponding targets.
The second example, shown in
Figure 10 and
Figure 11, shows the case that Ck
.
< Ck
.
= Ck
.
. In
Figure 10, upon the receipt of
, HMNR takes one forced checkpoint, Ck
, before delivering
because
q wrongly believes Ck
.
= Ck
.
after
. On the other hand, it lets
p perform no forced checkpointing when receiving
, as it can recognize that Ck
.
is less than the timestamp of the next checkpoint of
q after
. However, in
Figure 11, LightweightCIC does not only have
p, but also
q does not perform forced checkpointing when receiving
because
q can see Ck
.
< Ck
.
after
according to the update of
upon receiving
.
The third example, shown in
Figure 12 and
Figure 13, illustrates the case that Ck
.
= Ck
.
< Ck
.
. When
q receives
in
Figure 12, HMNR does not need to record a forced checkpoint, as it can detect Ck
.
< Ck
.
after
. However, before delivering
, HMNR forces
p to perform forced checkpointing because
p cannot ensure the timestamp of the next checkpoint of
q after
is greater than Ck
.
. In contrast, after
q has received
in
Figure 13, LightweightCIC has
q piggyback
and
on
and has
p update
along with it. Thanks to this procedure, upon the receipt of
, LightweightCIC prohibits
p from performing forced checkpointing, as it can sense that Ck
.
< Ck
.
by checking
.
The fourth example, shown in
Figure 14 and
Figure 15, depicts the case of a different checkpointing and communication pattern in which a C-path,
, forms an NC-path,
. Receiving
in
Figure 14, HMNR has
p generate a forced checkpoint Ck
before
because
p recognizes Ck
.
≮ Ck
.
. On the other hand, when obtaining
in
Figure 15, LightweightCIC enables
q to change its current checkpoint timestamp and
to the most recent ones of
r with the piggybacked information. Thanks to this early update, by checking the information piggybacked on
,
p can see Ck
.
< Ck
.
, as
r already knew
after receiving
is equal to
before sending
(
[
q] = F);
p thus decides not to take a forced checkpoint.
Theorem 3. Our protocol always satisfies the property that no checkpoint becomes useless.
Proof. We prove the correctness of the theorem by contradiction. It is assume that some checkpoints become useless even after the protocol has been executed. When each process receives a message forming a Z-path, the protocol decides whether a forced checkpoint should be taken before delivering the message based on Equations (
4) and (
5). It was proven in HMNR [
7] that the property is always satisfied in all cases where Equation (
4) instructs each process not to take a forced checkpoint. Therefore, we only need to check all cases where each process decides not to take a forced checkpoint based on Equation (
5). There are two cases to consider:
Case 1: the Z-path is a C-path.
In this case, as the protocol uses a checkpoint timestamping function based on Lamport’s clock, the timestamp flow always goes up along any C-path. This behavioral feature makes Theorem 2 satisfied, meaning every C-path includes no Z-cycle at all times.
Case 2: the Z-path is an NC-path.
In this case, every NC-pattern in the NC-path should be checked in all cases presented in the proof of Lemma 1. Among them, we only need to examine two cases, Case 1 and Case 2.2.2, where the protocol allows each process to not take a forced checkpoint based on Equation (
5). Suppose two consecutive messages
and
form an NC-pattern, where sending
to
r after Ck
before Ck
precedes receiving
from
p after Ck
before Ck
in the same checkpoint interval CI
.
Case 2.1: . ≤ ..
In this case, as Ck. ≤ . < Ck., delivering does not make any checkpoint useless, even if a forced checkpointing action is not performed.
Case 2.2: . ≤ (r) right after .
In this case, as Ck. ≤ . < Ck., Theorem 2 is always satisfied, without taking any forced checkpoint.
Therefore, our protocol always prevents any checkpoint from being useless. This contradicts the hypothesis. □
Theorem 4. Our protocol results in fewer or the same number of forced checkpoints being taken as HMNR.
Proof. Our protocol instructs each process receiving a message to perform a forced checkpointing action based on Equations (
4) and (
5), while for HMNR, Equations (
3) and (
4) are used. As Equation (
4) is common to both our protocol and HMNR, Equations (
3) and (
5) need only be compared in terms of the number of forced checkpoints taken. Based on Lemma 1, Equation (
5) leads to fewer or the same number of forced checkpoints being taken as Equation (
3). Therefore, the protocol has each process generate fewer or the same number of forced checkpoints as HMNR. □