ID-Based Deniable Authentication Protocol with Key Agreement and Time-Bound Properties for 6G-Based WBAN Healthcare Environments
Abstract
1. Introduction
1.1. Research Motivations
1.2. Research Contributions
- ID-Based public key systems: This simplifies key and certificate management and reduces the complexity to decrease the risks of bandwidth and vulnerabilities but still increases the security level.
- Scalablility for 6G WBAN: It manages this expansion without sacrificing the quality of service, maintaining high security and performance levels even under heavy network loads.
- Key Agreement for securing WBAN communication: It protects all entities from the risk of a third-party intercepting or compromising the key.
- Deniability of authentication for protecting user privacy: It lets the users communicate securely without leaving any trace of their conversation, even if their messages are intercepted and decrypted by an attacker. The verifier cannot convince the third party of the authentication by releasing the communication messages.
- Time-bound authentication service for secure access control: It allows authorized users to access specific resources within a limited time frame, ensuring that only authorized users can access the resources and reducing the risk of unauthorized access.
1.3. Paper Structures
2. Related Works
3. Technical Preliminaries
3.1. Elliptic Curve Cryptography (ECC)
- A specific point O is on an elliptic curve, E; nonetheless, the point O is not on the elliptic curve, E. The point O is an additive identity that is regarded as the point of infinity or a zero point.
- There is a point P with coordinates (x, y) on the elliptic curve, E. The point P is reflected across the x-axis and mapped onto a point, −P (negative P). Hence, the coordinates of the point, −P, are (x, −y).
- While q is the prime order of the point, P, the qP = O, and q is an integer.
- In the finite field , all of the points on the elliptic curve E are called E().
3.2. Bilinear Pairing [33]
- Bilinear: , where and .
- Nondegenerate: , while .
- Computable: Given , there is an efficient algorithm to compute .
3.3. Brief Review of Time-Bound Method of Chien’s Group-Oriented Range-Bound Key Agreement Protocol [18]
3.4. Security Assumptions
3.4.1. Computational Diffie–Hellman Problem (CDHP) [34]
3.4.2. Decisional Diffie–Hellman Problem (DDHP) [34,35]
3.4.3. One-Way Hash Function (OWHF) [36]
3.4.4. Time-Bound Method of Chien’s Protocol [19]
4. Our Proposed Protocol
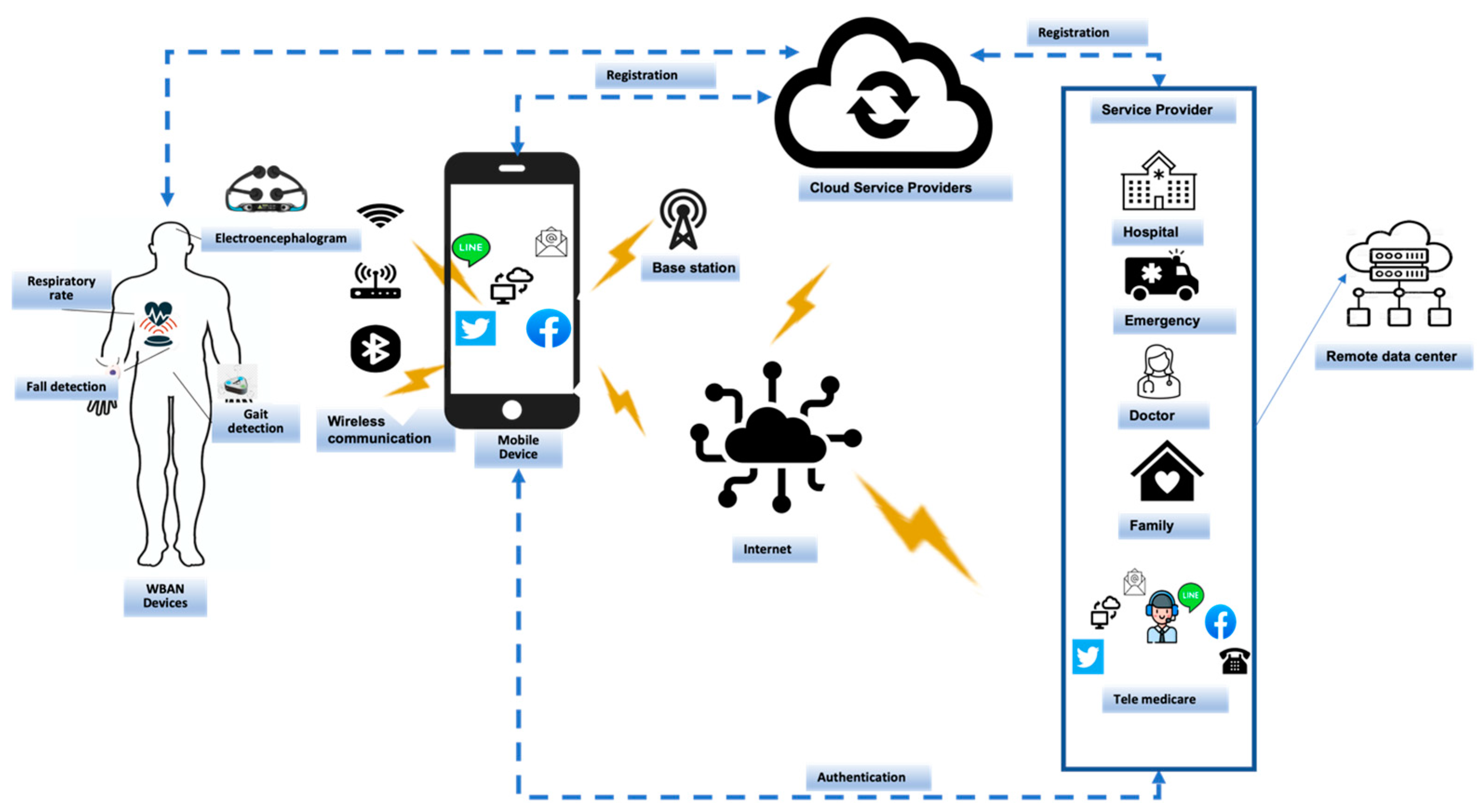
4.1. Problem Statement
4.2. System Model
- Simplified key and certificate management, reducing complexity and increasing security.
- Scalability for 6G WBAN without compromising quality of service.
- Key agreement for secure WBAN communication, protecting against interception.
- Deniability of authentication, ensuring user privacy and non-repudiation.
- Time-bound authentication service for secure access control.
- Improved efficiency with lower computational overheads compared to existing protocols.
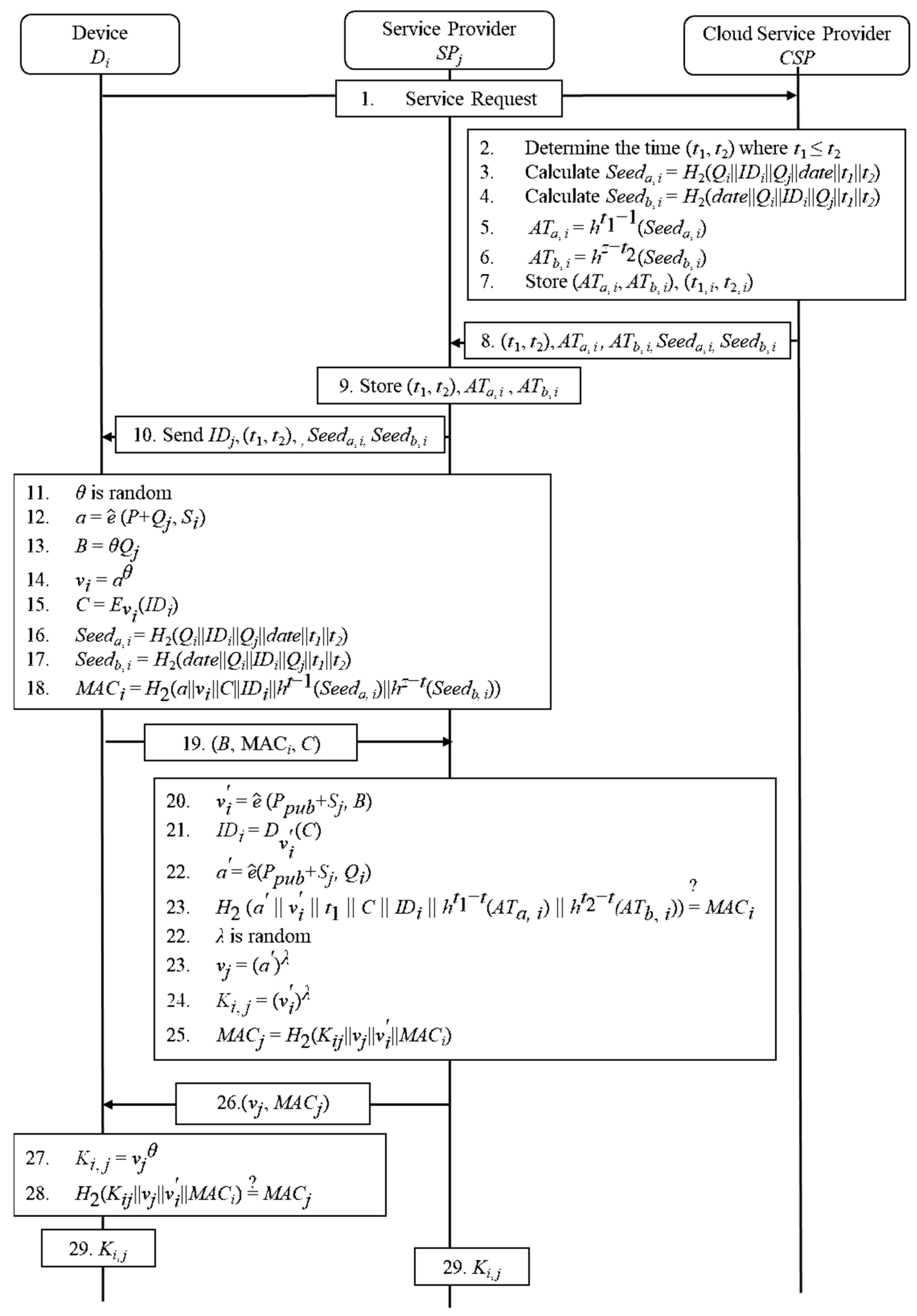
4.3. Proposed Protocol
| Algorithm 1: Setup |
| Output: The public parameters Pub_params = and the private parameters Priv_params = s. |
| Algorithm: |
|
|
|
|
|
|
|
| Algorithm 2: KeyGen | |
| Input: The identity and the identity | |
| Algorithm: | |
| |
| |
| |
| |
| (6) | |
| (7) | |
| |
| (8) | |
| (9) | |
|

| Algorithm 3: AuthID | |
| |
| |
| (10) | |
| (11) | |
| (12) | |
| |
| |
| |
| (13) | |
| (14) | |
| (15) | |
| |
| (16) | |
| (17) | |
| (18) | |
| (19) | |
| (20) | |
| |
| (21) | |
| |
| |
| (22) | |
| = | (23) |
| (24) | |
| |
| (25) | |
| If equals to , it implies that the integrity of the message authentication code is valid. Otherwise, the request from the device will be dropped, and the Algorithm will be terminated. | |
| |
| (26) | |
| (27) | |
| (28) | |
| |
| |
| (29) | |
| |
| (30) | |
| If equals to , it implies that the integrity of the message authentication code is valid. Otherwise, the request from the service provider will be dropped and the algorithm will be terminated. |
5. Security Analysis
5.1. Security Proof
5.1.1. Security of Private Keys
5.1.2. Mutual Authentication
5.1.3. Key Confirmation
5.1.4. Deniability
5.1.5. Forward Security
5.2. A Formal Security Verification Using AVISPA
5.3. Performance Analysis
6. Conclusions
- Our proposed protocol is based on ID-based public key systems. It simplifies key and certificate management and reduces the complexity to decrease the risks of bandwidth and vulnerabilities, but still increases the security level.
- Our proposed protocol can achieve scalablility for 6G WBAN. It manages this expansion without sacrificing the quality of service, maintaining high security and performance levels even under heavy network loads.
- Our proposed protocol can achieve key agreement for securing WBAN communication. It protects all entities from the risk of a third party intercepting or compromising the key.
- Our proposed protocol can achieve deniability of authentication for protecting user privacy. It lets the users communicate securely without leaving any trace of their conversation, even if their messages are intercepted and decrypted by an attacker. The verifier cannot convince the third party of the authentication by releasing the communication messages.
- Our proposed protocol can achieve time-bound authentication service for secure access control. It allows authorized users to access specific resources within a limited time frame, ensuring that only authorized users can access the resources and reducing the risk of unauthorized access.
- Our proposed protocol can gain better efficiency than previously proposed protocols in terms of computational overheads.
- Our proposed protocol can gain better security than previously proposed protocols by applying the AVISPA tool to give a formal security verification.
Author Contributions
Funding
Conflicts of Interest
References
- Bhatti, D.S.; Saleem, S.; Imran, A.; Iqbal, Z.; Alzahrani, A.; Kim, H.; Kim, K.-I. A Survey on Wireless Wearable Body Area Networks: A Perspective of Technology and Economy. Sensors 2022, 22, 7722. [Google Scholar] [CrossRef]
- Hasan, K.; Biswas, K.; Ahmed, K.; Nafi, N.S.; Islam, M.S. A comprehensive review of wireless body area network. J. Netw. Comput. Appl. 2019, 143, 178–198. [Google Scholar] [CrossRef]
- Le, T.-V.; Lu, C.-F.; Hsu, C.-L.; Do, T.K.; Chou, Y.-F.; Wei, W.-C. A novel three-factor authentication protocol for multiple service providers in 6G-aided intelligent healthcare systems. IEEE Access 2022, 10, 28975–28990. [Google Scholar] [CrossRef]
- Alabdulatif, A.; Khalil, I.; Saidur Rahman, M. Security of Blockchain and AI-Empowered Smart Healthcare: Application-Based Analysis. Appl. Sci. 2022, 12, 11039. [Google Scholar] [CrossRef]
- Alsaeed, N.; Nadeem, F. Authentication in the Internet of Medical Things: Taxonomy, Review, and Open Issues. Appl. Sci. 2022, 12, 7487. [Google Scholar] [CrossRef]
- Hsu, C.-L.; Chuang, Y.-H.; Hung, M.-T. An Efficient Deniable Authentication Protocol from Pairings to Protect Users’ Privacy. Chiang Mai J. Sci. 2014, 41, 1384–1391. [Google Scholar]
- Di Raimondo, M.; Gennaro, R. New Approaches for Deniable Authentication. In Proceedings of the 12th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 7–11 November 2005; pp. 112–121. [Google Scholar]
- Lee, W.-B.; Wu, C.-C.; Tsaur, W.-J. A novel deniable authentication protocol using generalized ElGamal signature scheme. Inf. Sci. 2007, 177, 1376–1381. [Google Scholar] [CrossRef]
- Shao, Z. Efficient deniable authentication protocol based on generalized ElGamal signature scheme. Comput. Stand. Interfaces 2004, 26, 449–454. [Google Scholar] [CrossRef]
- Rasmussen, K.; Gasti, P. Weak and Strong Deniable Authenticated Encryption: On Their Relationship and Applications. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–10. [Google Scholar]
- Zarour, M.; Alenezi, M.; Ansari, M.T.J.; Pandey, A.K.; Ahmad, M.; Agrawal, A.; Kumar, R.; Khan, R.A. Ensuring data integrity of healthcare information in the era of digital health. Healthc. Technol. Lett. 2021, 8, 66–77. [Google Scholar] [CrossRef]
- Mavridis, I.; Georgiadis, C.; Pangalos, G. Access-rule certificates for secure distributed healthcare applications over the Internet. Health Inform. J. 2002, 8, 127–137. [Google Scholar] [CrossRef]
- Alezabi, K.A.; Hashim, F.; Hashim, S.J.; Ali, B.M. An Efficient Authentication and Key Agreement Protocol for 4G (LTE) Networks. In Proceedings of the 2014 IEEE Region 10 Symposium, Kuala Lumpur, Malaysia, 14–16 April 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 502–507. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Li, F.; Xiong, P.; Jin, C. Identity-based deniable authentication for ad hoc networks. Computing 2014, 96, 843–853. [Google Scholar] [CrossRef]
- Zhu, H.; Zhang, Y.; Zhang, Y.; Li, H. A Novel and Provable Authenticated Key Agreement Protocol with Privacy Protection Based on Chaotic Maps towards Mobile Network. Int. J. Netw. Secur. 2016, 18, 116–123. [Google Scholar]
- Tzeng, W.-G. A time-bound cryptographic key assignment scheme for access control in a hierarchy. IEEE Trans. Knowl. Data Eng. 2002, 14, 182–188. [Google Scholar] [CrossRef]
- Chien, H.-Y. Group-oriented range-bound key agreement for Internet of Things scenarios. IEEE Internet Things J. 2018, 5, 1890–1903. [Google Scholar] [CrossRef]
- Odelu, V. A Dynamic Time-Bound Access Control for Secure Hierarchical Content Sharing. TechRxiv 2023. [Google Scholar] [CrossRef]
- Hsu, C.-L.; Le, T.-V.; Lu, C.-F.; Lin, T.-W.; Chuang, T.-H. A privacy-preserved E2E authenticated key exchange protocol for multi-server architecture in edge computing networks. IEEE Access 2020, 8, 40791–40808. [Google Scholar] [CrossRef]
- Kobayashi, S.; Kane, T.B.; Paton, C. The privacy and security implications of open data in healthcare. Yearb. Med. Inform. 2018, 27, 041–047. [Google Scholar] [CrossRef]
- Yi, X. Identity-based fault-tolerant conference key agreement. IEEE Trans. Dependable Secur. Comput. 2004, 1, 170–178. [Google Scholar]
- Xu, C.; Li, Z.; Mu, Y.; Guo, H.; Guo, T. Affiliation-hiding authenticated asymmetric group key agreement. Comput. J. 2012, 55, 1180–1191. [Google Scholar] [CrossRef]
- Li, M.; Xu, X.; Guo, C.; Tan, X. AD-ASGKA–authenticated dynamic protocols for asymmetric group key agreement. Secur. Commun. Netw. 2016, 9, 1340–1352. [Google Scholar] [CrossRef]
- Wu, T.-Y.; Tseng, Y.-M.; Tsai, T.-T. A revocable ID-based authenticated group key exchange protocol with resistant to malicious participants. Comput. Netw. 2012, 56, 2994–3006. [Google Scholar] [CrossRef]
- Choi, K.Y.; Hwang, J.Y.; Lee, D.H. Efficient ID-based group key agreement with bilinear maps. In Proceedings of the Public Key Cryptography–PKC 2004: 7th International Workshop on Theory and Practice in Public Key Cryptography, Singapore, 1–4 March 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 130–144. [Google Scholar]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J.; Qin, B.; Dong, Z. Round-efficient and sender-unrestricted dynamic group key agreement protocol for secure group communications. IEEE Trans. Inf. Secur. 2015, 10, 2352–2364. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of Elliptic Curves in Cryptography; Springer: Berlin/Heidelberg, Germany, 1986. [Google Scholar]
- Barker, E.; Barker, W. Recommendation for Key Management, Part 2: Best Practices for Key Management Organization; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018.
- Jablon, D. IEEE P1363 Standard Specifications for Public-Key Cryptography. In Proceedings of the IEEE NIST Key Management Workshop CTO Phoenix Technologies Treasurer, Gaithersburg, MD, USA, 1–2 November 2001; pp. 1–26. [Google Scholar]
- Cremers, C.; Horvat, M. Improving the ISO/IEC 11770 Standard for Key Management Techniques. In Proceedings of the Security Standardisation Research: First International Conference, SSR 2014, London, UK, 16–17 December 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 215–235. [Google Scholar]
- Miller, V.S. The Weil pairing, and its efficient calculation. J. Cryptol. 2004, 17, 235–261. [Google Scholar] [CrossRef]
- Joux, A.; Nguyen, K. Separating decision Diffie–Hellman from computational Diffie–Hellman in cryptographic groups. J. Cryptol. 2003, 16, 239–247. [Google Scholar] [CrossRef]
- Boneh, D. The Decision Diffie-Hellman Problem. In Proceedings of the Algorithmic Number Theory: Third International Symposiun, ANTS-III, Portland, OR, USA, 21–25 June 1998; Springer: Berlin/Heidelberg, Germany, 2006; pp. 48–63. [Google Scholar]
- Winternitz, R.S. Producing a One-Way Hash Function from DES. In Advances in Cryptology: Proceedings of Crypto 83; Springer: Berlin/Heidelberg, Germany, 1984; pp. 203–207. [Google Scholar]
- Nayak, S.; Patgiri, R. 6G communication technology: A vision on intelligent healthcare. Health Inform. A Comput. Perspect. Healthc. 2021, 932, 1–18. [Google Scholar]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Paoletti, E.; Zoppi, P.; Geli, S.; Dioniso, P. How 6G Technology Can Change the Future Wireless Healthcare. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Suraci, C.; Pizzi, S.; Molinaro, A.; Araniti, G. Business-Oriented Security Analysis of 6G for eHealth: An Impact Assessment Approach. Sensors 2023, 23, 4226. [Google Scholar] [CrossRef]
- Suraci, C.; Pizzi, S.; Molinaro, A.; Araniti, G. MEC and D2D as Enabling Technologies for a Secure and Lightweight 6G eHealth System. IEEE Internet Things J. 2021, 9, 11524–11532. [Google Scholar] [CrossRef]
- Liu, H.; Zhou, Y.; Zhu, N. A novel elliptic curve scalar multiplication algorithm against power analysis. Math. Probl. Eng. 2013, 2013, 862508. [Google Scholar] [CrossRef]
- Robert, J.-M.; Negre, C.; Plantard, T. Efficient Fixed-base exponentiation and scalar multiplication based on a multiplicative splitting exponent recoding. J. Cryptogr. Eng. 2019, 9, 115–136. [Google Scholar] [CrossRef]









| Protocol Symbol | HLPSL Notations | Description |
|---|---|---|
| IDD, IDSP | The identification of the entity x, where x = {i, j}. | |
| D, SP, CSP | D, SP, CSP | The abbreviations of Device, Service Provider, and Cloud Service Provider individually. |
| UPPERQD, UPPERQSP | The public key of the entity x, where x = {i, j}. | |
| DS, SPS | The private key of the entity x, where x = {i, j}. | |
| MACI, MACJ | The authentication code for entity x, where x = {i, j}. | |
| THETA | A random number. | |
| Pub_parameter | The public parameter of the system. | |
| Priv_parameter | The private parameter of the system. | |
| G1, G2 | The generators are based on the cyclic additive group, which is generated by P. | |
| P | P | A point from the generator with a prime. |
| q | LOWERQ | A large prime. |
| s | S | The system secret value. |
| (), () | H2, H3 | The one-way hash algorithm. |
| C | CIPHER | The ciphertexts. |
| k | SKcspd, SKcspsp | The symmetric encryption key |
| KIJ | The shared key. | |
| {m}_k | A message is encrypted by the symmetric encryption key k. | |
| {m}_k | The message is decrypted by the symmetric encryption key k. | |
| ATA, ATB | Two secret tokens which are generated by CSP and published to the Service Provider. |
| Functions | [22] | [23] | [24] | [25] | [26] | [27] | [40] | [3] | Ours |
|---|---|---|---|---|---|---|---|---|---|
| Provide 6G-based intelligent healthcare environment | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ |
| Provide key agreement authentication | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Provide deniability authentication | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ |
| Provide ID-based mutual authentication | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ |
| Provide time-bound authentication | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ |
| Notation | Descriptions | Time Overheads |
|---|---|---|
| TBP | The bilinear pairing operation | 13.909 ms |
| TSM | The scalar multiplication operation in | 6.869 ms |
| TEXP | The exponentiation operation in | 0.140 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hsu, C.-L.; Nguyen, A.-T.; Cheng, G.-L. ID-Based Deniable Authentication Protocol with Key Agreement and Time-Bound Properties for 6G-Based WBAN Healthcare Environments. Electronics 2023, 12, 2682. https://doi.org/10.3390/electronics12122682
Hsu C-L, Nguyen A-T, Cheng G-L. ID-Based Deniable Authentication Protocol with Key Agreement and Time-Bound Properties for 6G-Based WBAN Healthcare Environments. Electronics. 2023; 12(12):2682. https://doi.org/10.3390/electronics12122682
Chicago/Turabian StyleHsu, Chien-Lung, Anh-Tuan Nguyen, and Guan-Lin Cheng. 2023. "ID-Based Deniable Authentication Protocol with Key Agreement and Time-Bound Properties for 6G-Based WBAN Healthcare Environments" Electronics 12, no. 12: 2682. https://doi.org/10.3390/electronics12122682
APA StyleHsu, C.-L., Nguyen, A.-T., & Cheng, G.-L. (2023). ID-Based Deniable Authentication Protocol with Key Agreement and Time-Bound Properties for 6G-Based WBAN Healthcare Environments. Electronics, 12(12), 2682. https://doi.org/10.3390/electronics12122682








