A Novel Cloud Enabled Access Control Model for Preserving the Security and Privacy of Medical Big Data
Abstract
:1. Introduction
1.1. Contributions of the Study
- A comprehensive overview of the role of big data in medical care is presented.
- An overview of privacy and security implications of medical big data is presented.
- A comprehensive examination of strategies and techniques for addressing security and privacy challenges in medical big data, along with key components based on the available literature, is provided.
- A comparison of similar research is highlighted.
- Designed a novel access control model for improving the security and privacy of medical big data, which can be used as a primary base to build safe medical big data solutions.
1.2. Outline of the Study
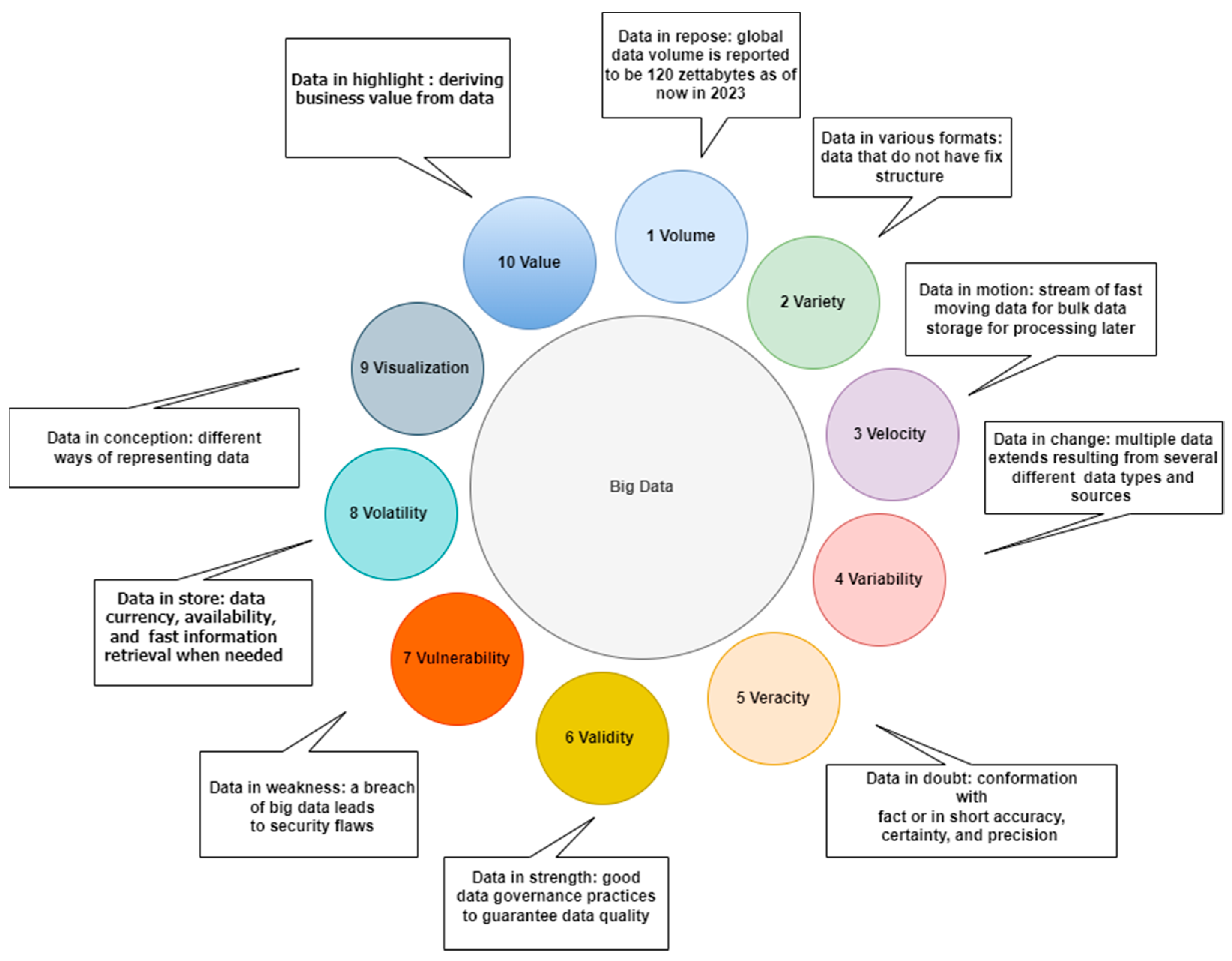
2. Big Data
2.1. Characteristics of Big Data
2.2. Big Data Applications
2.3. The Role of Big Data in Healthcare
2.4. Sources of Medical Big Data
- Medical devices (sensors/machine-generated) data
- Human-generated data
- Social media and behavioral data
- Biometric data
- Epidemiological data
- Public health surveillance data
- Administrative claims data
- Genomics data
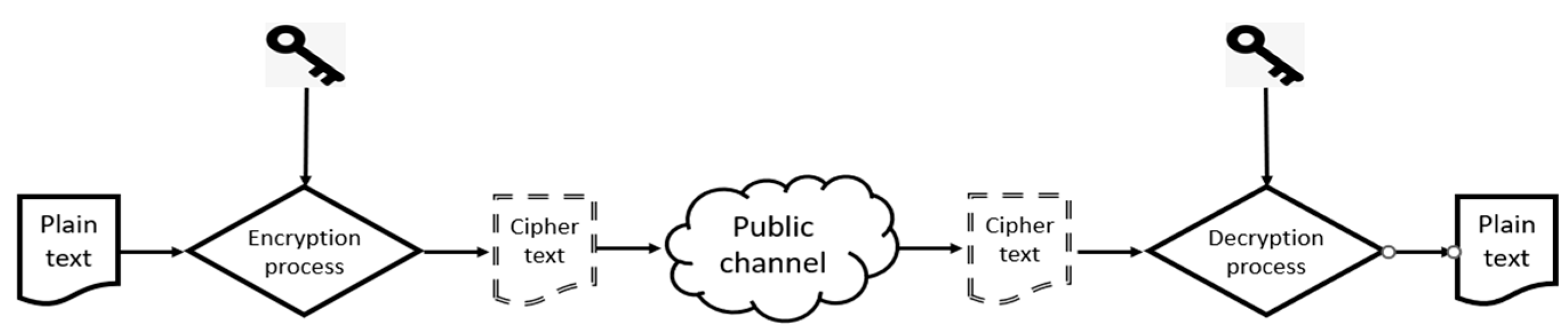
3. Preamble on Security and Privacy of Big Data
- Data collection
- Data transfer
- Data storage
- Data consumption and sharing
3.1. Big Data: Privacy and Security Protection Mechanisms
- Encryption
- Implementation of Access Control mechanisms
- Data auditing
- Mechanisms for network layer protection
- Data governance
- Authentication
- Data minimization
- Real-time security analytics
3.2. Related Work and Discussion
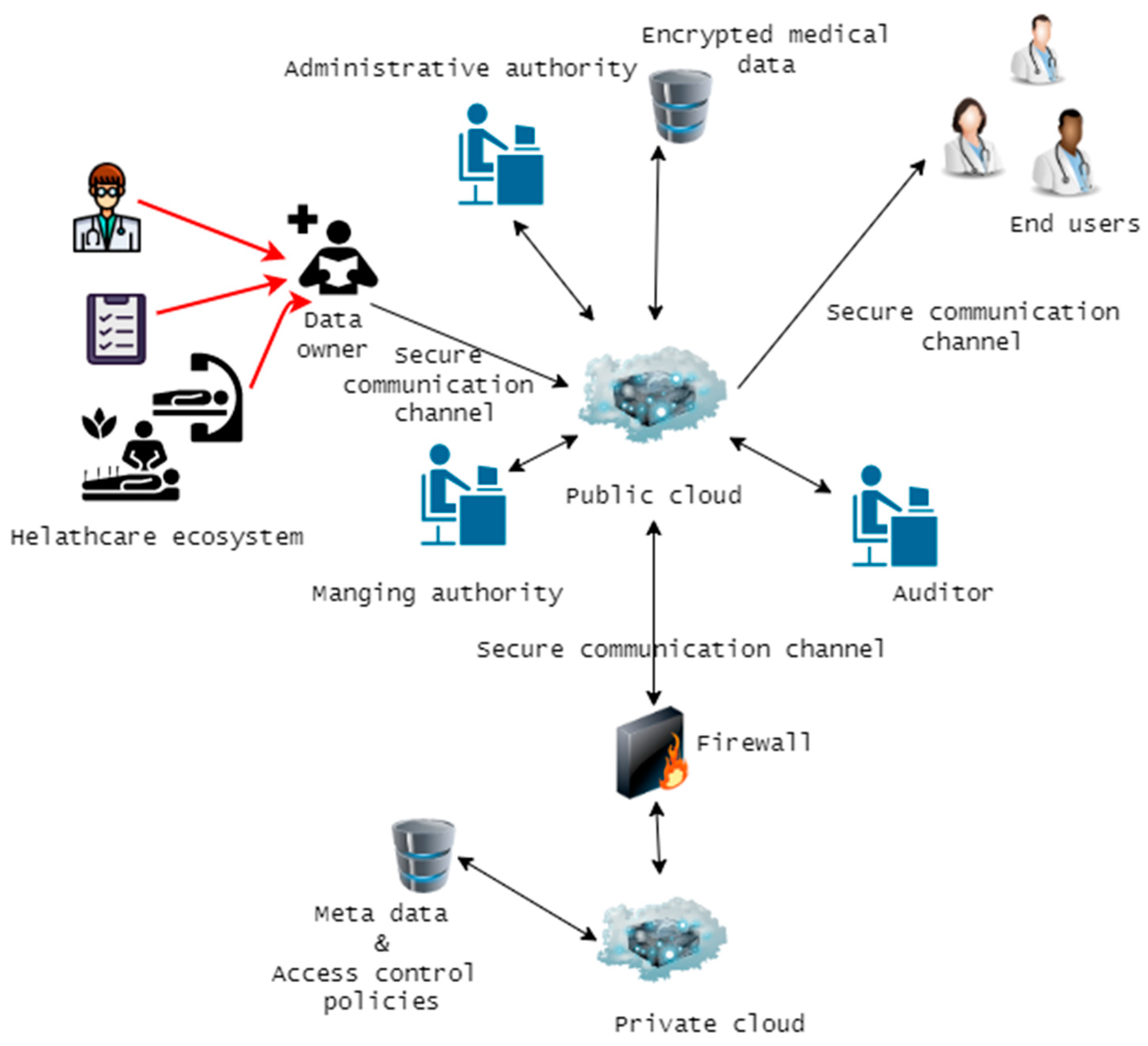
4. System Design and Implementation
- Public cloud
- Private cloud
- Administrative authority
- Managing authority
- Data owners
- End user
- Auditor
- Override user
Role Based Encryption (RBE)
5. Implementation Results and Discussion
5.1. Performance Testing
5.2. Data Integrity Testing
5.3. Security Implication Testing
- Initial Reconnaissance
- Port and service scanning,
- Vulnerability analysis
- Open ports: Port 80 (TCP) and Port 443 (TCP)
- Server information: Microsoft IIS server 8.0
- SSL certificate information: Public key encrypted SSL connection that uses 2048 bits key.
5.4. Functional Requirement Analysis
- Least Privilege principle
- 2.
- Separation of duties
- 3.
- Scalability
- 4.
- Auditing
- 5.
- Policy management
- 6.
- Flexibility of configuration
- 7.
- Delegation of capabilities
- 8.
- Hybrid cloud architecture
- 9.
- Role hierarchy management
5.5. Discussion
- Healthcare data should be sufficiently safeguarded and secured as security and privacy risks are imminent.
- When studying big data in healthcare, tools that assure maximum protection for underlying big data need to be employed.
- Healthcare data should be protected throughout its life cycle by adopting the above-mentioned and discussed security mechanisms.
- The adoption of an audit trail system should be an added advantage, as all the transactions can be traced.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kaur, P.; Sharma, M.; Mittal, M. Big Data and Machine Learning Based Secure Healthcare Framework. Procedia Comput. Sci. 2018, 132, 1049–1059. [Google Scholar] [CrossRef]
- Jiang, R.; Shi, M.; Zhou, W. A Privacy Security Risk Analysis Method for Medical Big Data in Urban Computing. IEEE Access 2019, 7, 143841–143854. [Google Scholar] [CrossRef]
- al Hamid, H.A.; Rahman, S.M.M.; Hossain, M.S.; Almogren, A.; Alamri, A. A Security Model for Preserving the Privacy of Medical Big Data in a Healthcare Cloud Using a Fog Computing Facility with Pairing-Based Cryptography. IEEE Access 2017, 5, 22313–22328. [Google Scholar] [CrossRef]
- Mae, R. 22 Big Data Applications & Examples|Built in. 2022. Available online: https://builtin.com/big-data/big-data-examples-applications (accessed on 4 February 2023).
- David, T. What Is Big Data? Introduction, Types, Characteristics, Examples. 2023. Available online: https://www.guru99.com/what-is-big-data.html (accessed on 4 February 2023).
- Batko, K.; Ślęzak, A. The use of Big Data Analytics in healthcare. J. Big Data 2022, 9, 1–24. [Google Scholar] [CrossRef]
- Christo, P. 25+ Impressive Big Data Statistics for 2023. 2023. Available online: https://techjury.net/blog/big-data-statistics/#gref (accessed on 4 February 2023).
- Abouelmehdi, K.; Beni-Hessane, A.; Khaloufi, H. Big healthcare data: Preserving security and privacy. J. Big Data 2018, 5, 1–18. [Google Scholar] [CrossRef] [Green Version]
- Siddique, M.; Mirza, M.A.; Ahmad, M.; Chaudhry, J.; Islam, R. A survey of big data security solutions in healthcare. In Security and Privacy in Communication Networks: 14th International Conference, SecureComm 2018, Singapore, 8–10 August 2018, Proceedings, Part II; Springer International Publishing: Cham, Switzerland, 2018; Volume 255, pp. 391–406. [Google Scholar] [CrossRef]
- Youssef, A.E. A Framework for Secure Healthcare Systems Based on Big Data Analytics in Mobile Cloud Computing Environments. Int. J. Ambient. Syst. Appl. 2014, 2, 1–11. [Google Scholar] [CrossRef]
- Manogaran, G.; Thota, C.; Lopez, D.; Sundarasekar, R. Big Data Security Intelligence for Healthcare Industry 4.0. In Cybersecurity for Industry 4.0; Springer: Cham, Switzerland, 2017; pp. 103–126. [Google Scholar] [CrossRef]
- Manogaran, G.; Thota, C.; Lopez, D.; Vijayakumar, V.; Abbas, K.M.; Sundarsekar, R. Big Data Knowledge System in Healthcare. Stud. Big Data 2017, 23, 133–157. [Google Scholar] [CrossRef] [Green Version]
- Jee, K.; Kim, G.H. Potentiality of Big Data in the Medical Sector: Focus on How to Reshape the Healthcare System. Health Inf. Res. 2013, 19, 79–85. [Google Scholar] [CrossRef] [Green Version]
- Karatas, M.; Eriskin, L.; Deveci, M.; Pamucar, D.; Garg, H. Big Data for Healthcare Industry 4.0: Applications, challenges and future perspectives. Expert Syst. Appl. 2022, 200, 116912. [Google Scholar] [CrossRef]
- Miah, S.J.; Camilleri, E.; Vu, H.Q. Big Data in Healthcare Research: A survey study. J. Comput. Inf. Syst. 2021, 62, 480–492. [Google Scholar] [CrossRef]
- Pranjal Bora. Big Data in Healthcare: All You Need to Know. Digital Authority Partners (DAP). 2022. Available online: https://www.digitalauthority.me/resources/big-data-in-healthcare/ (accessed on 11 February 2023).
- Jagadeeswari, V.; Subramaniyaswamy, V.; Logesh, R.; Vijayakumar, V. A study on medical Internet of Things and Big Data in personalized healthcare system. Health Inf. Sci. Syst. 2018, 6, 14. [Google Scholar] [CrossRef] [PubMed]
- Kankanhalli, A.; Hahn, J.; Tan, S.; Gao, G. Big data and analytics in healthcare: Introduction to the special section. Inf. Syst. Front. 2016, 18, 233–235. [Google Scholar] [CrossRef] [Green Version]
- Price, W.N.; Cohen, I.G. Privacy in the age of medical big data. Nat. Med. 2019, 25, 37–43. [Google Scholar] [CrossRef] [PubMed]
- Olaronke, I.; Oluwaseun, O. Big data in healthcare: Prospects, challenges and resolutions. In Proceedings of the FTC 2016—Proceedings of Future Technologies Conference, San Francisco, CA, USA, 6–7 December 2016; pp. 1152–1157. [Google Scholar] [CrossRef]
- Sarkar, B.K. Big data for secure healthcare system: A conceptual design. Complex Intell. Syst. 2017, 3, 133–151. [Google Scholar] [CrossRef] [Green Version]
- Thilakarathne, N.N.; Kagita, M.K.; Gadekallu, T.R. The Role of the Internet of Things in Health Care: A Systematic and Comprehensive Study. SSRN Electron. J. 2020. [Google Scholar] [CrossRef]
- Thilakarathne, N.N. Review on the Use of ICT Driven Solutions Towards Managing Global Pandemics. J. ICT Res. Appl. 2021, 14, 207–225. [Google Scholar] [CrossRef]
- Arvind, K.S.; Vanitha, S.; Suganya, K.S. Pandemic Management Using Internet of Things and Big Data—A Security and Privacy Perspective. In IoT and Big Data Analytics for Smart Cities; Chapman and Hall: London, UK; CRC: Boca Raton, FL, USA, 2022; pp. 159–173. [Google Scholar] [CrossRef]
- Hulsen, T.; Jamuar, S.S.; Moody, A.R.; Karnes, J.H.; Varga, O.; Hedensted, S.; Spreafico, R.; Hafler, D.A.; McKinney, E.F. From big data to precision medicine. Front. Med. 2019, 6, 34. [Google Scholar] [CrossRef] [Green Version]
- Kavidopoulou, A.; Syrigos, K.N.; Makrogkikas, S.; Dlamini, Z.; Hull, R.; Marima, R.; Skepu, A.; Koumoulos, E.P.; Bakas, G.; Vamvakaris, I.; et al. AI and Big Data for Drug Discovery. In Trends of Artificial Intelligence and Big Data for E-Health; Springer International Publishing: Cham, Switzerland, 2022; pp. 121–138. [Google Scholar] [CrossRef]
- Raghupathi, W.; Raghupathi, V. Big data analytics in healthcare: Promise and potential. Health Inf. Sci. Syst. 2014, 2, 1–10. [Google Scholar] [CrossRef]
- Patel, S.; Patel, A. A big data revolution in health care sector: Opportunities, challenges and technological advancements. Int. J. Inf. Sci. Technol. 2016, 6, 155–162. [Google Scholar] [CrossRef]
- Kim, M.-J.; Yu, Y.-S. Development of Real-time Big Data Analysis System and a Case Study on the Application of Information in a Medical Institution. Int. J. Softw. Eng. Its Appl. 2015, 9, 93–102. Available online: https://www.earticle.net/Article/A251363 (accessed on 5 February 2023). [CrossRef]
- Chawla, N.V.; Davis, D.A. Bringing big data to personalized healthcare: A patient-centered framework. J. Gen. Intern. Med. 2013, 28, 660–665. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kuriyan, J.; Cobb, N. Forecasts of Cancer and Chronic Patients: Big Data Metrics of Population Health. arXiv 2013, arXiv:1307.3434. [Google Scholar]
- Abinaya, K. Data Mining with Big Data e-Health Service Using Map Reduce. Int. J. Adv. Res. Comput. Commun. Eng. 2015, 123–127. [Google Scholar] [CrossRef]
- Wang, L.; Alexander, C.A. Big data analytics as applied to diabetes management. Eur. J. Clin. Biomed. Sci. 2016, 2, 29–38. [Google Scholar] [CrossRef]
- Shinde, K.V. A real time monitoring system in healthcare with hadoop. Res. Journey’Int. Multidiscip. E-Res. J. 2016. Available online: https://researchjourney.net/upload/April-May-June%202016/3-K%20.V.%20SHINDE%20-%20Suplementary%20Issue-international%20conference-Cover%20page%20-Editorial%20Board%20-Index.pdf (accessed on 5 February 2023).
- Luo, J.; Wu, M.; Gopukumar, D.; Zhao, Y. Big data application in biomedical research and health care: A literature review. Biomed. Inform. Insights 2016, 8, BII.S31559. [Google Scholar] [CrossRef] [Green Version]
- Balladini, J.; Rozas, C.; Frati, E.; Vicente, N.; Lima, C.O.L. Big Data Analytics in Intensive Care Units: Challenges and applicability in an Argentinian Hospital. J. Comput. Sci. Technol. 2015, 15, 61–67. Available online: http://www.merriam-webster.com/dictionary/continuous (accessed on 11 February 2023).
- Boukenze, B.; Mousannif, H.; Haqiq, A. A conception of a predictive analytics platform in healthcare sector by using data mining techniques and Hadoop. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2016. [Google Scholar]
- Herland, M.; Khoshgoftaar, T.M.; Wald, R. A review of data mining using big data in health informatics. J. Big Data 2014, 1, 2. [Google Scholar] [CrossRef] [Green Version]
- Belle, A.; Thiagarajan, R.; Soroushmehr, S.M.R.; Navidi, F.; Beard, D.A.; Najarian, K. Big data analytics in healthcare. Biomed. Res. Int. 2015, 2015. [Google Scholar] [CrossRef] [Green Version]
- Salerno, J.; Knoppers, B.M.; Lee, L.M.; Hlaing, W.W.M.; Goodman, K.W. Ethics, big data and computing in epidemiology and public health. Ann. Epidemiol. 2017, 27, 297–301. [Google Scholar] [CrossRef] [PubMed]
- Vayena, E.; Salathé, M.; Madoff, L.C.; Brownstein, J.S. Ethical Challenges of Big Data in Public Health. PLoS Comput. Biol. 2015, 11, e1003904. [Google Scholar] [CrossRef] [Green Version]
- Pastorino, R.; De Vito, C.; Migliara, G.; Glocker, K.; Binenbaum, I.; Ricciardi, W.; Boccia, S. Benefits and challenges of Big Data in healthcare: An overview of the European initiatives. Eur. J. Public Health 2019, 29, 23–27. [Google Scholar] [CrossRef] [Green Version]
- Kalinaki, K.; Thilakarathne, N.N.; Mubarak, H.R.; Malik, O.A.; Abdullatif, M. Cybersafe Capabilities and Utilities for Smart Cities. In Cybersecurity for Smart Cities; Springer: Cham, Switzerland, 2023; pp. 71–86. [Google Scholar]
- Martin-Sanchez, F.; Verspoor, K. Big data in medicine is driving big changes. Yearb. Med. Inf. 2014, 9, 14–20. [Google Scholar] [CrossRef] [Green Version]
- Alli, A.A.; Kassim, K.; Mutwalibi, N.; Hamid, H.; Ibrahim, L. Secure Fog-Cloud of Things: Architectures, Opportunities and Challenges. In Secure Edge Computing, 1st ed.; Ahmed, M., Haskell-Dowland, P., Eds.; CRC Press: Boca Raton, FL, USA, 2021; pp. 3–20. [Google Scholar]
- Thilakarathne, N.N.; Kagita, M.K.; Gadekallu, T.R.; Maddikunta, P.K.R. The Adoption of ICT Powered Healthcare Technologies towards Managing Global Pandemics. arXiv 2020, arXiv:2009.05716. [Google Scholar]
- Mahendran, R.K.; Velusamy, P. A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of Medical Things. Comput. Commun. 2020, 153, 545–552. [Google Scholar] [CrossRef]
- Uchibeke, U.U.; Schneider, K.A.; Kassani, S.H.; Deters, R. Blockchain Access Control Ecosystem for Big Data Security. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1373–1378. [Google Scholar] [CrossRef] [Green Version]
- Benjelloun, F.-Z.; Lahcen, A.A. Big Data Security. In Web Services: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2019; pp. 25–38. [Google Scholar] [CrossRef]
- Kuo, M.H.; Sahama, T.; Kushniruk, A.W.; Borycki, E.M.; Grunwell, D.K. Health big data analytics: Current perspectives, challenges and potential solutions. Int. J. Big Data Intell. 2014, 1, 114. [Google Scholar] [CrossRef]
- Rao, S.; Suma, S.N.; Sunitha, M. Security Solutions for Big Data Analytics in Healthcare. In Proceedings of the 2015 2nd IEEE International Conference on Advances in Computing and Communication Engineering, ICACCE 2015, Dehradun, India, 1–2 May 2015; pp. 510–514. [Google Scholar] [CrossRef]
- Patil, H.K.; Seshadri, R. Big data security and privacy issues in healthcare. In Proceedings of the 2014 IEEE International Congress on Big Data, BigData Congress, Anchorage, AK, USA, 27 June–2 July 2014; pp. 762–765. [Google Scholar] [CrossRef]
- Iadarola, G.; Poli, A.; Spinsante, S. Compressed Sensing of Skin Conductance Level for IoT-based wearable sensors. In Proceedings of the 2022 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Ottawa, ON, Canada, 16–19 May 2022; IEEE: Piscataway, NJ, USA; pp. 1–6. [Google Scholar]
- Iadarola, G.; Disha, D.; De Santis, A.; Spinsante, S.; Gambi, E. Global Positioning System measurements: Comparison of IoT wearable devices. In Proceedings of the 2022 IEEE 9th International Workshop on Metrology for AeroSpace (MetroAeroSpace), Pisa, Italy, 27–29 June 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 213–218. [Google Scholar]
- Casaccia, F.; Iadarola, G.; Poli, A.; Spinsante, S. CS-Based Decomposition of Acoustic Stimuli-Driven GSR Peaks Sensed by an IoT-Enabled Wearable Device. In IoT Technologies for Health Care: 8th EAI International Conference, HealthyIoT 2021, Virtual Event, 24–26 November 2021; Springer International Publishing: Cham, Switzerland, 2021; pp. 166–179. [Google Scholar]
- Ramya Devi, R.; Vijaya Chamundeeswari, V. Triple DES: Privacy Preserving in Big Data Healthcare. Int. J. Parallel. Program. 2020, 48, 515–533. [Google Scholar] [CrossRef]
- Abiodun, M.K.; Awotunde, J.B.; Ogundokun, R.O.; Adeniyi, E.A.; Arowolo, M.O. Security and Information Assurance for IoT-Based Big Data. Stud. Comput. Intell. 2021, 972, 189–211. [Google Scholar] [CrossRef]
- Ramachandra, M.N.; Rao, M.S.; Lai, W.C.; Parameshachari, B.D.; Babu, J.A.; Hemalatha, K.L. An Efficient and Secure Big Data Storage in Cloud Environment by Using Triple Data Encryption Standard. Big Data Cogn. Comput. 2022, 6, 101. [Google Scholar] [CrossRef]
- Sarosh, P.; Parah, S.A.; Bhat, G.M.; Muhammad, K. A Security Management Framework for Big Data in Smart Healthcare. Big Data Res. 2021, 25, 100225. [Google Scholar] [CrossRef]
- Fatima, S.; Hussain, S.; Shahzadi, N.; Din, B.U.; Sajjad, W.; Saleem, Y.; Aun, M. A Secure Framework for IoT Healthcare Data Using Hybrid Encryption. In Proceedings of the 2022 International Conference on Emerging Trends in Electrical, Control, and Telecommunication Engineering (ETECTE), Lahore, Pakistan, 2–4 December 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Gadde, S.; Amutharaj, J.; Usha, S. A security model to protect the isolation of medical data in the cloud using hybrid cryptography. J. Inf. Secur. Appl. 2023, 73, 103412. [Google Scholar] [CrossRef]
- Sharma, K.; Agrawal, A.; Pandey, D.; Khan, R.A.; Dinkar, S.K. RSA based encryption approach for preserving confidentiality of big data. J. King Saud. Univ.-Comput. Inf. Sci. 2022, 34, 2088–2097. [Google Scholar] [CrossRef]
- Sharma, D.; Kawatra, R. Security Techniques Implementation on Big Data Using Steganography and Cryptography. Lect. Notes Netw. Syst. 2023, 517, 279–302. [Google Scholar] [CrossRef]
- Jayasankar, T.; Bhavadharini, R.M.; Nagarajan, N.R.; Mani, G.; Ramesh, S. Securing Medical Data using Extended Role Based Access Control Model and Twofish Algorithms on Cloud Platform. Eur. J. Mol. Clin. Med. 2021, 8, 2021. Available online: https://ejmcm.com/article_6677_f9876c57ebfe46bd9508546774432d82.pdf (accessed on 18 February 2023).
- Nayak, L.; Jayalakshmi, V. A Study of Securing Healthcare Big Data using DNA Encoding based ECC. In Proceedings of the 6th International Conference on Inventive Computation Technologies, ICICT 2021, Coimbatore, India, 20–22 January 2021; pp. 348–352. [Google Scholar] [CrossRef]
- Sreedevi, A.G.; Harshitha, T.N.; Sugumaran, V.; Shankar, P. Application of cognitive computing in healthcare, cybersecurity, big data and IoT: A literature review. Inf. Process. Manag. 2022, 59, 102888. [Google Scholar] [CrossRef]
- Jiang, R.; Han, S.; Yu, Y.; Ding, W. An access control model for medical big data based on clustering and risk. Inf. Sci. 2023, 621, 691–707. [Google Scholar] [CrossRef]
- Ahtesham, M. Bigdata Applications in Healthcare: Security and Privacy Challenges. Lect. Notes Netw. Syst. 2022, 455, 231–240. [Google Scholar] [CrossRef]
- el Azzaoui, A.; Sharma, P.K.; Park, J.H. Blockchain-based delegated Quantum Cloud architecture for medical big data security. J. Netw. Comput. Appl. 2022, 198, 103304. [Google Scholar] [CrossRef]
- Marichamy, V.S.; Natarajan, V. Blockchain based Securing Medical Records in Big Data Analytics. Data Knowl. Eng. 2023, 144, 102122. [Google Scholar] [CrossRef]
- Nair, A.K.; Sahoo, J.; Raj, E.D. Privacy preserving Federated Learning framework for IoMT based big data analysis using edge computing. Comput. Stand Interfaces 2023, 86, 103720. [Google Scholar] [CrossRef]
- Kashyap, R.; Piersson, A.D. Big Data Challenges and Solutions in the Medical Industries. In Handbook of Research on Pattern Engineering System Development for Big Data Analytics; IGI Global: Hershey, PA, USA, 2018; pp. 1–24. [Google Scholar] [CrossRef]
- Kalejahi, B.K.; Meshgini, S.; Yariyeva, A.; Ndure, D.; Maharramov, U.; Farzamnia, A. Big Data Security Issues and Challenges in Healthcare. arXiv 2019. [Google Scholar] [CrossRef]
- Esposito, C.; de Santis, A.; Tortora, G.; Chang, H.; Choo, K.K.R. Blockchain: A Panacea for Healthcare Cloud-Based Data Security and Privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- Khaloufi, H.; Abouelmehdi, K.; Beni-Hssane, A.; Saadi, M. Security model for Big Healthcare Data Lifecycle. Procedia Comput. Sci. 2018, 141, 294–301. [Google Scholar] [CrossRef]
- Jain, P.; Gyanchandani, M.; Khare, N. Big data privacy: A technological perspective and review. J. Big Data 2016, 3, 1–25. [Google Scholar] [CrossRef] [Green Version]
- Thilakarathne, N.N.; Priyashan, W.D.M.; Premarathna, C.P. Artificial Intelligence-Enabled IoT for Health and Wellbeing Monitoring. In Proceedings of the 2021 12th International Conference on Computing Communication and Networking Technologies, ICCCNT 2021, Kharagpur, India, 6–8 July 2021. [Google Scholar] [CrossRef]
- Thilakarathne, N.N.; Weerasinghe, H.D.; Welhenge, A.; Kagita, M.K. Privacy Dilemma in Healthcare: A Review on Privacy Preserving Medical Internet of Things. In Proceedings of the 2021 12th International Conference on Computing Communication and Networking Technologies, ICCCNT 2021, Kharagpur, India, 6–8 July 2021. [Google Scholar] [CrossRef]
- Wang, B.; Li, L. Research Progress in Biomedical Big Data. Prog. China Epidemiol. 2022, 391–400. [Google Scholar] [CrossRef]













| Domain | Applications |
|---|---|
| Healthcare | Disease prediction, medical research, providing quality medical care, cost reduction of medical treatments, identity the diseases at early stages and identifying the best possible treatment plans, and pandemic surveillance |
| Public sector | Surveillance, environmental protection, power generation and consumption (smart grid), tax reduction, public welfare |
| Education | Track student performance, improve student learning, and provide student guidance. |
| Entertainment | Manage content for a target audience, measure the performance, and measure the feedback. |
| Banking | Analyzing business, customer habit analysis, prognostic analytics |
| Industry | Improve the manufacturing process, improve the quality of products, and reduce errors. |
| Transportation | Intelligent transport systems, traffic control, traffic congestion management, identifying the best possible route (Google Maps), revenue management. |
| Technique | Tools |
|---|---|
| Map Reduce | Oozie, Flume, Pig, Hive |
| NoSQL | Cassandra |
| Storage | HDFS |
| Reference | Application | Description |
|---|---|---|
| [25,27,28,29] | Patient-centric care | In patient-centric care, big data is used to design personalized treatment plans based on the patient’s condition. |
| [30,31,32,33] | Predictive analysis | The application of predictive analytics allows clinicians, healthcare organizations, and health insurance providers to explain the possibility of their patients getting specific medical illnesses, such as heart difficulties or diabetes. |
| [34,35,36,37] | Real-time monitoring | Big data facilitates monitoring the state of patients with the use of medical equipment and the IoT and offers continuous real-time monitoring capabilities, which makes it feasible to begin therapy and intervention at an earlier stage. |
| [26,38,39] | Improving patient treatment | The collection and analysis of large amounts of data help medical professionals and relevant stakeholders to make better-informed choices regarding patient care and service provision. |
| Encryption Algorithm | Employed Technology | Details | References |
|---|---|---|---|
| Data Encryption Standard (DES) | Symmetric key encryption | DES is a symmetric encryption algorithm that uses the same key for both encryption and decryption processes. | [59] |
| Triple Data Encryption Standard (3DES) | Symmetric key encryption | Triple DES is an advanced version of DES, in which the encryption process passes three rounds during the execution time, as well as the decryption process, unlike in DES, which passes one round only. | [56,57,58] |
| Advanced Encryption Standard (AES) | Symmetric key encryption | The encryption and decryption processes use the same key, whereas the length of the key changes frequently in AES. | [60,61] |
| RSA Encryption | Asymmetric key encryption | This employs a public-key encryption algorithm, which uses two keys: a public key for the encryption process and a private key for the decryption process. | [62,63] |
| Twofish Encryption | Symmetric key encryption | This employs symmetric key encryption, which proved to be efficient with medical IoT devices with lower processing power. | [64] |
| Elliptic curve cryptography (ECC) | Asymmetric key encryption | This employs asymmetric key encryption, which is based on the Elliptic curve theory. This has been proven to be efficient in working with resource-constrained IoT devices owing to the low resource consumption nature, which results in improved security when dealing with IoT healthcare applications. | [60,65,66] |
| Reference | Survey/Review | Research | Focus on Security | Employed Technologies | Summary of the Scope of the Study |
|---|---|---|---|---|---|
| [1] | 🗶 | 🗸 | 🗸 | AI (Machine learning) | The authors present a brief overview of big data and its role in medical care in this study. Further, they also propose a design of a novel secure medical information system to handle medical data in a healthcare environment. |
| [2] | 🗶 | 🗸 | 🗸 | Cloud computing | In an urban computing environment, the researchers looked at the danger of security and privacy leaks across the life cycle of medical big data. |
| [3] | 🗶 | 🗸 | 🗸 | Fog computing, Cryptography | The researchers in this study focused on deploying a fog computing facility to secure confidential medical data in the cloud. |
| [8] | 🗸 | 🗸 | 🗸 | NA | The researchers examined the security and privacy aspects of medical big data, as well as potential solutions. |
| [9,68] | 🗸 | 🗶 | 🗸 | NA | As they analyze state-of-the-art security and privacy concerns about medical big data, the researchers focus on existing data privacy, data security, and users’ access control techniques. |
| [10] | 🗶 | 🗸 | 🗶 | Mobile computing, Cloud computing | The researchers presented a framework for a mobile cloud-based medical information system based on big data analytics. |
| [11,14] | 🗶 | 🗸 | 🗸 | IoT, Cryptography | The researchers discussed and proposed a secure industrial IoT architecture for processing the big data collated from sensors for medical applications. They further highlight how data privacy and security are poised to persist as a pivotal facet of healthcare within the IoT ecosystem. |
| [12] | 🗶 | 🗸 | 🗶 | NA | The researchers presented a management system based on big data to make appropriate healthcare judgments in this study. |
| [13] | 🗸 | 🗶 | 🗶 | NA | The researchers provide an overview of the current state of big data applications in medical care as well as the problems that governments and healthcare stakeholders face, and the opportunities and possibilities that medical big data presents. |
| [19] | 🗸 | 🗶 | 🗸 | NA | The researchers examine the legal and ethical problems that big data poses to patient privacy. |
| [69] | 🗶 | 🗸 | 🗸 | Blockchain, Cloud computing | The study presents a Quantum Cloud-as-a-service for an efficient, scalable, and secure solution for complex Smart Healthcare computations. Their novelty resides in the usage of Quantum Terminal Machines (QTM) and Blockchain technology to enhance the feasibility and security of the proposed architecture. |
| [20] | 🗸 | 🗶 | 🗸 | NA | The study investigated healthcare data fragmentation, ethical and usability challenges, as well as security and privacy concerns in terms of big data. |
| [70] | 🗶 | 🗸 | 🗸 | Blockchain, Cryptography | The study proposed a secure Block Chain based mechanism for managing and sharing Electronic Medical Records in medical Big Data using a cryptographic Hash Generator (CHG) in a Hadoop Distributed File System (HDFS) |
| [21] | 🗶 | 🗸 | 🗸 | Distributed computing | The researchers presented a brief overview of medical big data and proposed a distributed model for protecting patient data. |
| [52] | 🗸 | 🗶 | 🗸 | NA | The researchers present a brief review of security and privacy issues in terms of healthcare big data. |
| [51] | 🗸 | 🗶 | 🗸 | NA | In this study, the research highlights the viable security solutions for medical big data. |
| [50] | 🗸 | 🗶 | 🗶 | NA | The researchers explore the various use cases of medical big data in their study |
| [49] | 🗸 | 🗶 | 🗸 | NA | The researchers present a brief review of security challenges in terms of big data, including the solutions for protecting big data. |
| [71] | 🗶 | 🗸 | 🗸 | Federate learning | The authors put forth an innovative privacy-preserving framework that leverages federated learning to enable big data analysis in IoMT-based environments while ensuring the anonymity of users. |
| [48] | 🗶 | 🗸 | 🗸 | Blockchain | The researchers devised a blockchain access management method for safeguarding big data. |
| [72] | 🗸 | 🗶 | 🗶 | NA | The researchers have discussed the big data challenges in the study including the recent status of these challenges. |
| [73] | 🗸 | 🗶 | 🗶 | NA | The authors present a quick overview of big data in healthcare, as well as recent developments and difficulties. |
| [74] | 🗸 | 🗶 | 🗸 | NA | The researchers study the potential of blockchain technology for protecting healthcare data hosted within the cloud. |
| [75] | 🗸 | 🗶 | 🗸 | NA | In this study, the researchers focused on the security and privacy of big data and presented a brief overview of security and privacy requirements. |
| Our work | 🗶 | 🗸 | 🗸 | Cloud computing, Cryptography | The study presents a comprehensive overview of the role of big data in medical care with an evaluation of the privacy and security implications of such medical big data. Further, we also provide countermeasures summarizing the available literature, highlighting what has been achieved in recent years. On the other hand, we also present a novel access control model for improving the security and privacy of medical big data, which can be used as a base for developing such countermeasure solutions to safeguard from such security and privacy implications. |
| Access Control Model | Access is Granted | Access Permissions | Examples | Security Implications |
|---|---|---|---|---|
| DAC | Based on the identity of the user | Permissions are defined on the access control list. | Old versions of Windows/UNIX operating systems | Easily vulnerable to exploit |
| MAC | Given by the system administrator | The administrator has the full authority to change the security clearance of an object and users. | Most of the military applications | Vulnerable to exploit |
| RBAC | Based on the role assigned to an end user by the system administrator | An administrator offers a role to a user that includes pre-defined system rights and privileges. After a user has been allocated a role, he or she can only access system resources and complete specified duties described by the designated role. Further, the system administrator centrally manages the responsibilities allocated to users. | Google Cloud, Microsoft Azure/Most of the enterprise applications | More secure and resilient than the MAC and DAC models |
| Purpose | Tools/Components |
|---|---|
| Integrated development environment | Visual Studio 2019 |
| Programming languages | C#/ASP.NET |
| Public cloud | Microsoft Azure cloud instance |
| Private cloud | Azure SQL server instance |
| Software for data integrity testing | MD5 and SHA Checksum Utility |
| Tools used for initial reconnaissance | DNSenum and DMitry |
| Tools used for port and service scanning | Nmap |
| Tools used for vulnerability analysis | SPARTA, VEGA, and OWASP Zed Attack Proxy |
| Comparison Criteria | DAC | MAC | RBAC | Our Model |
|---|---|---|---|---|
| Least privilege principle | N | N | Y | Y |
| Separation of duties | N | N | Y | Y |
| Scalability | N | N | Y | Y |
| Auditing | Y | Y | Y | Y |
| Policy management | Y | N | Y | Y |
| Flexibility for configuration | N | N | Y | Y |
| Delegation of capabilities | Y | N | N | Y |
| Hybrid cloud architecture | N | N | N | Y |
| Role hierarchy management | N | N | Y | Y |
| Fine-grained access control | N | N | Y | Y |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alabdulatif, A.; Thilakarathne, N.N.; Kalinaki, K. A Novel Cloud Enabled Access Control Model for Preserving the Security and Privacy of Medical Big Data. Electronics 2023, 12, 2646. https://doi.org/10.3390/electronics12122646
Alabdulatif A, Thilakarathne NN, Kalinaki K. A Novel Cloud Enabled Access Control Model for Preserving the Security and Privacy of Medical Big Data. Electronics. 2023; 12(12):2646. https://doi.org/10.3390/electronics12122646
Chicago/Turabian StyleAlabdulatif, Abdullah, Navod Neranjan Thilakarathne, and Kassim Kalinaki. 2023. "A Novel Cloud Enabled Access Control Model for Preserving the Security and Privacy of Medical Big Data" Electronics 12, no. 12: 2646. https://doi.org/10.3390/electronics12122646
APA StyleAlabdulatif, A., Thilakarathne, N. N., & Kalinaki, K. (2023). A Novel Cloud Enabled Access Control Model for Preserving the Security and Privacy of Medical Big Data. Electronics, 12(12), 2646. https://doi.org/10.3390/electronics12122646









