E-ReInForMIF Routing Algorithm Based on Energy Selection and Erasure Code Tolerance Machine
Abstract
:1. Introduction
2. E-ReInForMIF Algorithm Principle
2.1. EC Fault-Tolerant Machine Based on the Quantitative Evaluation Mechanism of Node Energy Consumption
- (1)
- is the energy consumption from node Nj to the sink node. The path from Nj to the sink node is estimated according to the minimum number of jumps.
- (2)
- is the transmission of energy consumption from the node to the neighbor node .
- (3)
- is the overall energy consumption of the node sending data to the sink node through .
2.2. Residual Energy of Nodes
3. E-ReInForMIF Algorithm Steps
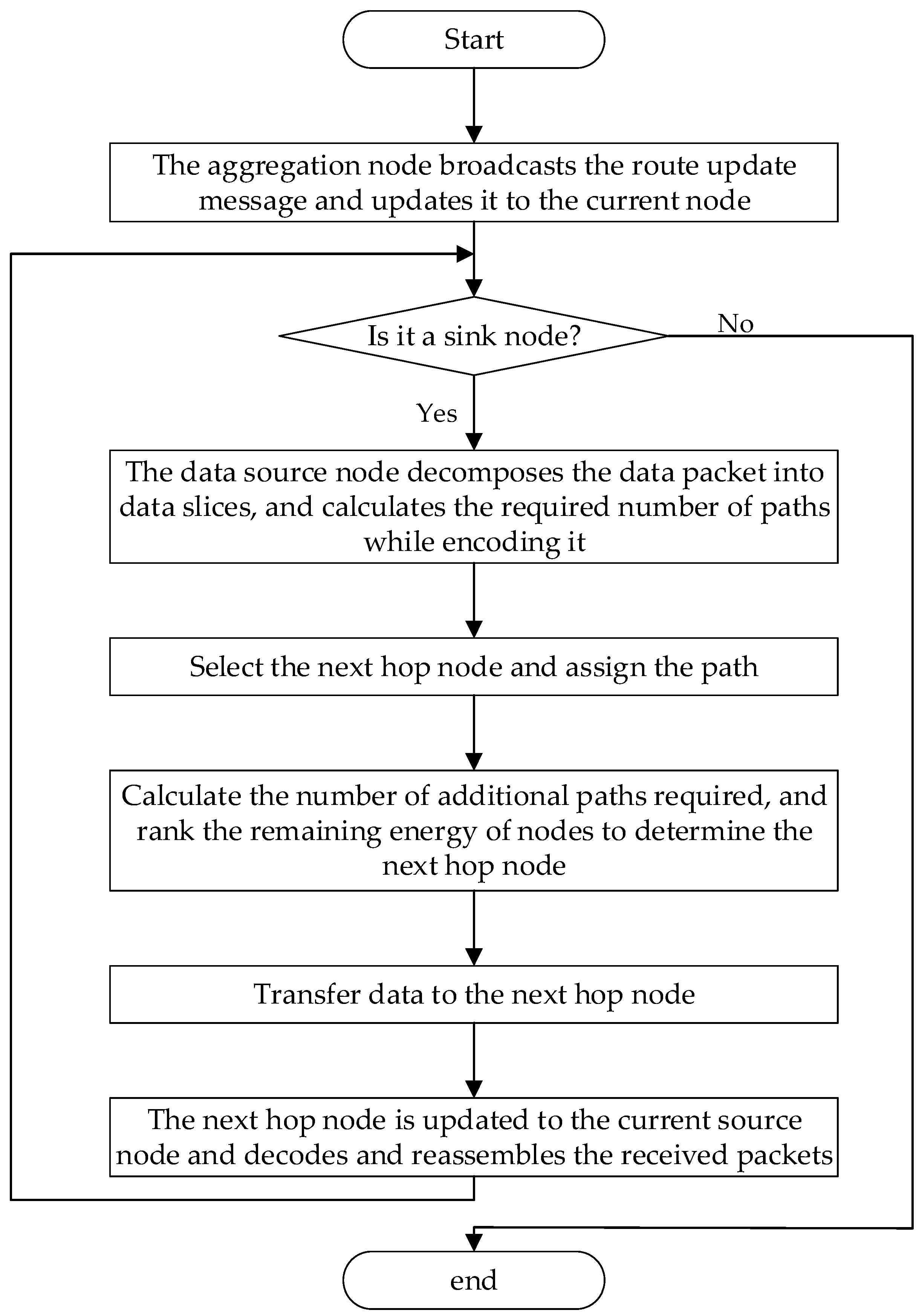
3.1. E-ReInForMIF Algorithm Flow
3.2. Specific Steps of the E-ReInForMIF Algorithm
- (1)
- The sink node broadcasts the updated content selected by the entire path node to each other node periodically. Each node adjusts its hop count based on the received message and broadcasts the message to other neighboring nodes. In the path, each node knows the jump to the sink node by itself and its surrounding nodes;
- (2)
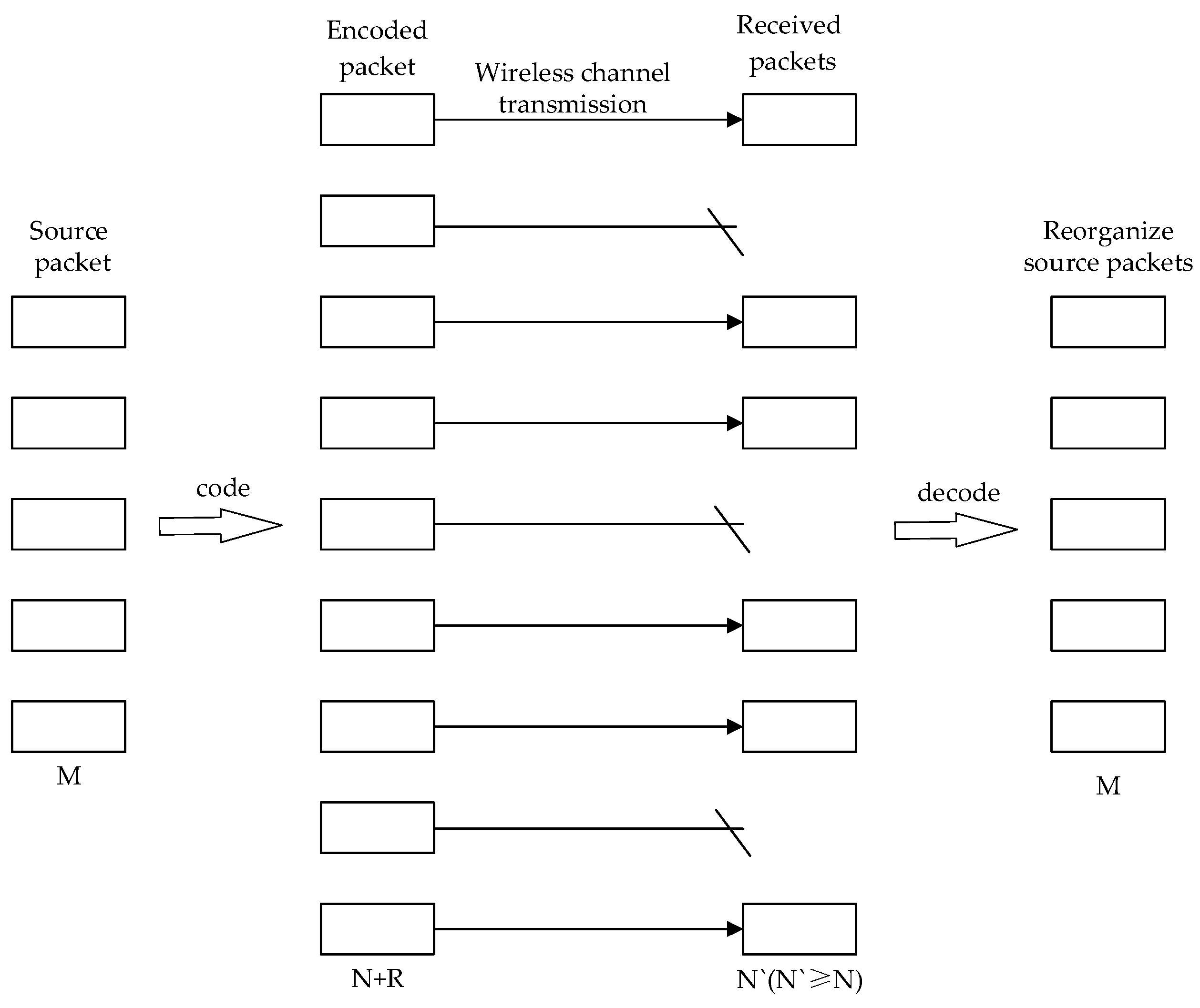
- The sending node processes the bM byte data packets, arranges them into M data slices of b bytes, and encodes them;
- (3)
- Calculate the transmission path: according to the source node data reliability parameter , channel error rate , and hop count , use the following formula:prepare for reliable data transmission through calculation and analysis;
- (4)
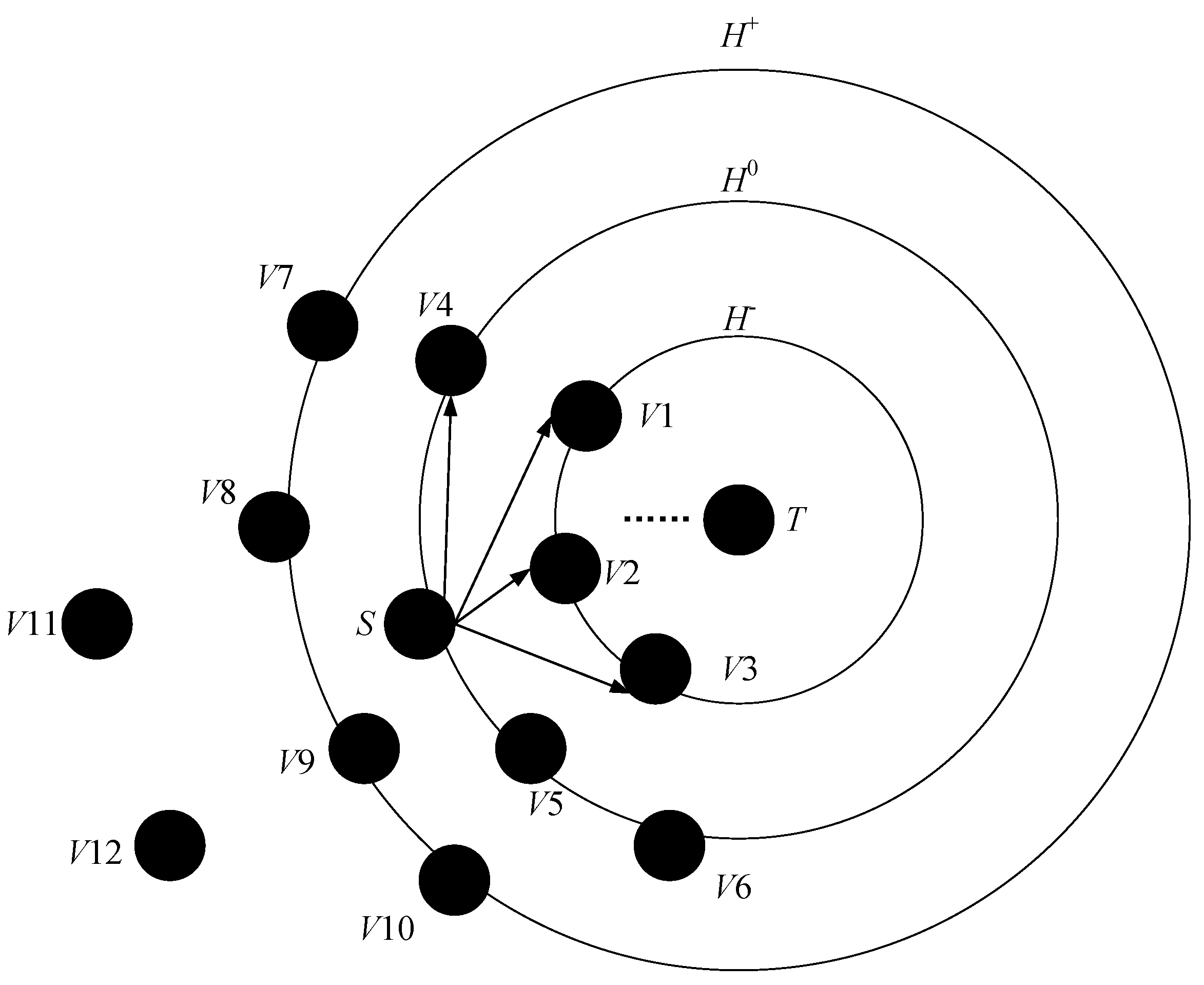
- Compare the energy consumption of each neighbor node transmitting data packets with the energy consumption of the source node to the sink node hop. According to the comparison between the former and the latter, they are classified into three categories: less 1, the same, and more 1. The corresponding combinations are H−, H0, and H+. The incremental ordering of each aggregation node is determined by the calculation of each node in the transmission path;
- (5)
- Select the next hop node from three sets according to the data transmission energy consumption requirements. The source node first selects the next hop node at H−. If is smaller than the calculated number of paths, additional paths need to be added when the source node transmits data. The additional number of paths is:
- (6)
- After receiving the data slice, the neighbor node decodes the data; the entire encoding and decoding process is performed using a system encoding method;
- (7)
- At this point, consider the neighbor node as the source node, calculate the number of new transmission paths again, and cycle through the previous operations until the data is transmitted to the sink node.
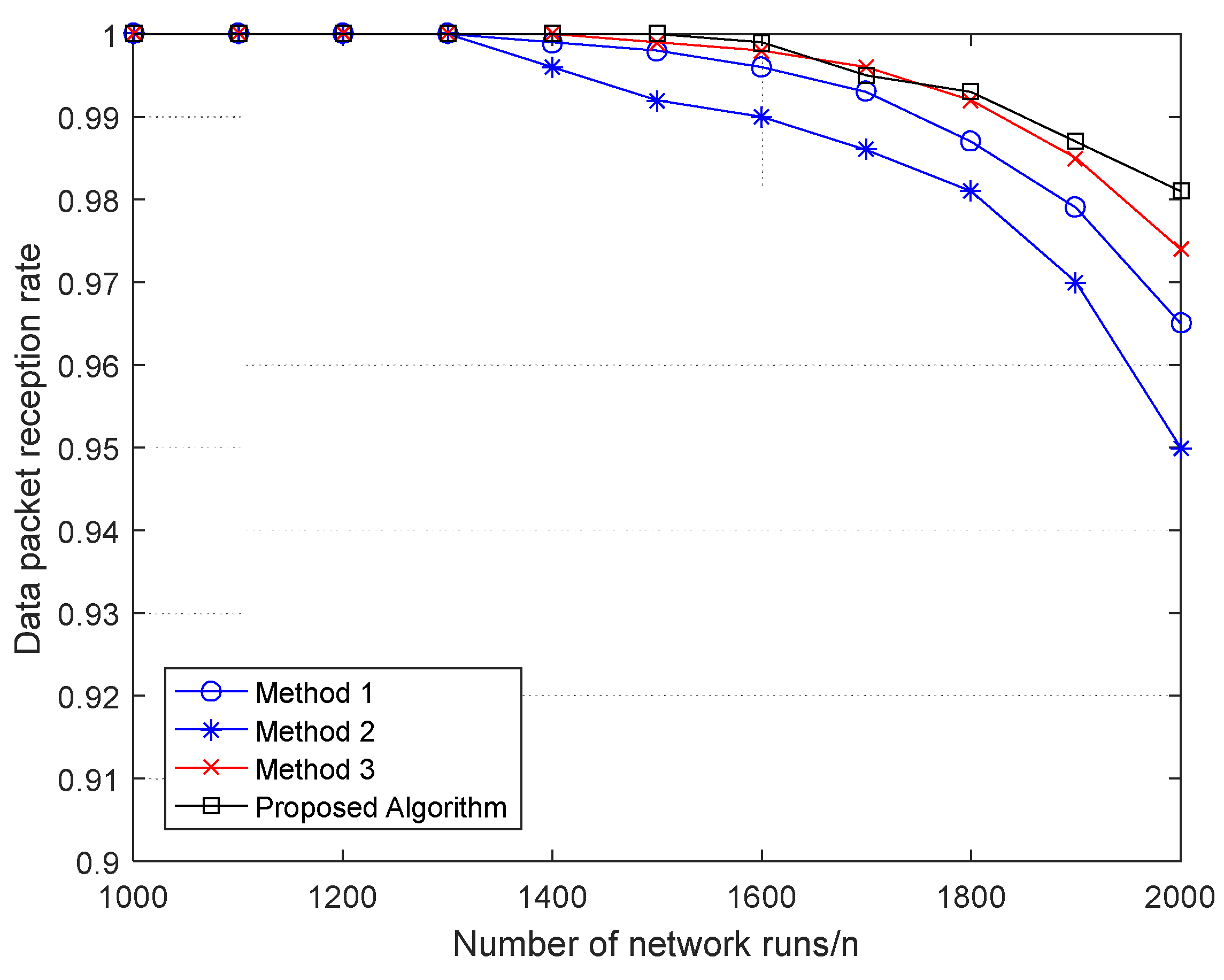
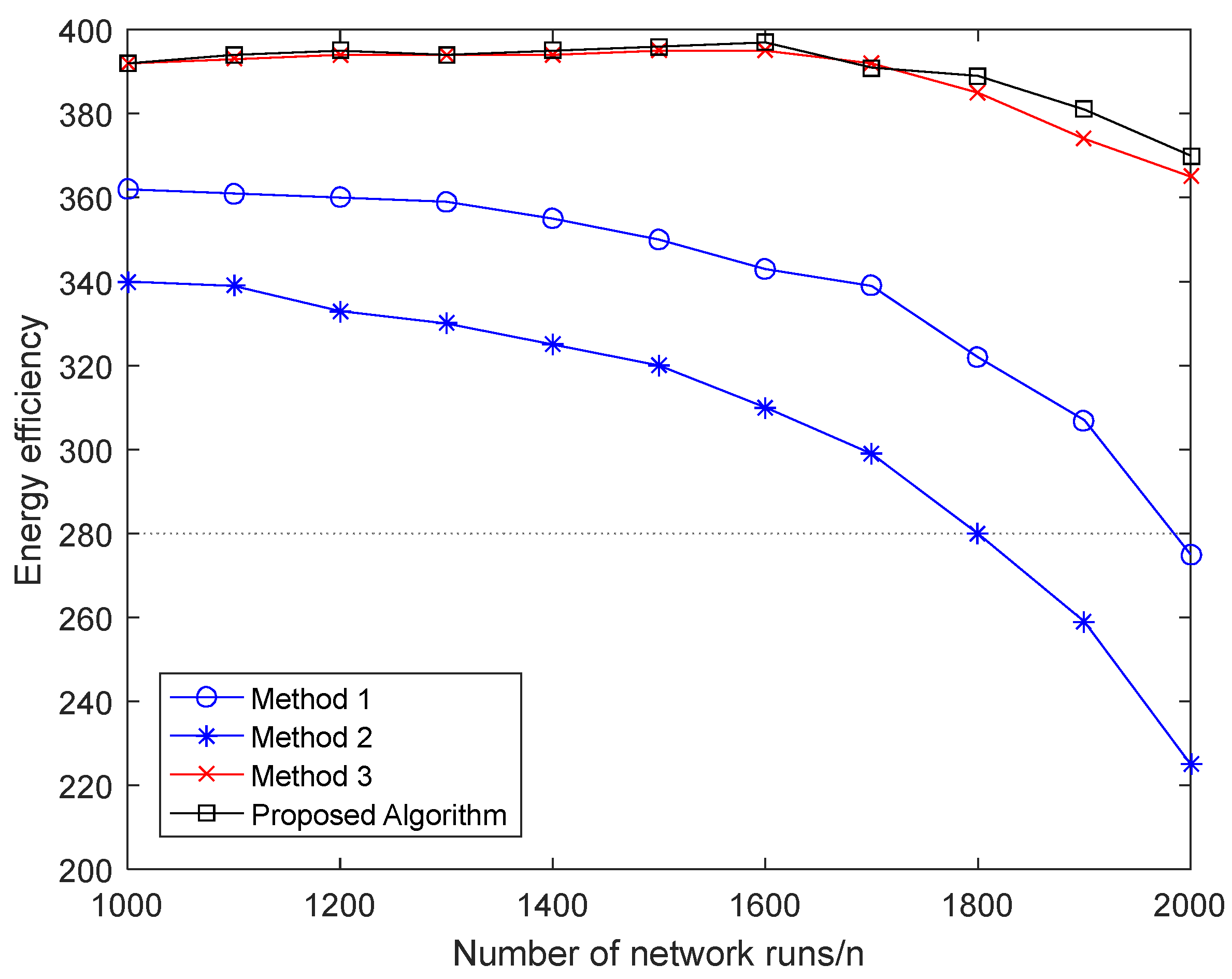
4. Experimental Simulation Result
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Ahmed, S.; Ahmed, I.; Walid, O.; Ahmed, M.K. Compressive sensing based secure data aggregation scheme for IoT based WSN applications. PLoS ONE 2021, 16, 10160–10187. [Google Scholar]
- Nouf, A.; Tahani, G. A Novel Security Architecture for WSN-Based Applications in Smart Grid. Smart Cities 2022, 5, 633–649. [Google Scholar]
- Lavanya, S.; Prasanth, A.; Jayachitra, S.; Shenbagarajan, A. A Tuned classification approach for efficient heterogeneous fault diagnosis in IoT-enabled WSN applications. Measurement 2021, 183, 109771–109787. [Google Scholar] [CrossRef]
- Mustafa, A.S.; Ismail, B.; Abdelhafid, A.; Pascal, L. Enhanced efficient outlier detection and classification approach for WSNs. Simul. Model. Pract. Theory 2022, 120, 102618–102635. [Google Scholar]
- He, C.B.; Qin, Q.; Li, M.Z. Variable Factor Based Non Uniform Clustering Routing Protocol for WSNs. Inf. Comput. 2022, 34, 11–13. [Google Scholar]
- Zhao, F.; Wei, K.; Chen, H.B. A data aggregation node selection algorithm based on average residual energy in sensor networks. Comput. Appl. Res. 2012, 29, 3096–3098. [Google Scholar]
- Elsway, A.A.; Khedr, A.M.; Oruba, A.; Walid, O. Energy-aware disjoint dominating sets-based whale optimization algorithm for data collection in WSNs. J. Supercomput. 2022, 79, 10227–10249. [Google Scholar] [CrossRef]
- Xu, J.Q.; Ding, Y.G.; Zhao, H.; Zhang, X.Y.; Bi, F.W. Energy Balanced Reliable Routing Metrics in Wireless Sensor Networks. Comput. Eng. 2009, 35, 87–89. [Google Scholar]
- Zhuang, Y.; Shen, J. ReInForm-CS routing algorithm for CS based wireless sensor networks. Comput. Syst. Appl. 2012, 21, 140–144. [Google Scholar]
- Wang, D.D.; Chai, Q.L.; Cai, X.J. Research and Simulation of ReInForM Routing Algorithm Based on Energy Selection. Comput. Simul. 2011, 28, 174–177. [Google Scholar]
- Zhang, K.L. Research and Implementation of Error Tolerant Mechanism for Erasure Codes in Distributed Systems. Comput. Mod. 2012, 8, 47–50. [Google Scholar]
- Zhang, Y.H.; Yan, L.J. Low energy routing protocol based on the remaining energy of all nodes. Microcomput. Appl. 2021, 37, 20–23. [Google Scholar]
- Pristupa, P.V.; Sushchenko, S.P.; Mikheev, P.A.; Moiseev, A.N. Efficiency Analysis of the Forward Error Correction at the Transport Protocol Level. Autom. Remote Control 2022, 83, 1059–1077. [Google Scholar] [CrossRef]
- Suelen, L.; Ricardo, M.; Carlos, M.; Francisco, V. Combining Network Coding and Retransmission Techniques to Improve the Communication Reliability of Wireless Sensor Network. Information 2021, 12, 184 . [Google Scholar] [CrossRef]
- Sun, C.L.; Wang, Z.Z.; Lu, D.W.; Cao, L.; Yue, Y.G.; Ding, H.H.; Hu, Z.Y. An Energy Efficient and Reliable Multipath Transmission Strategy for Mobile Wireless Sensor Networks. Comput. Intell. Neurosci. 2022, 80, 3804–3819. [Google Scholar] [CrossRef] [PubMed]
- Zhu, B.T.; Ebrahim, B.; Nguyen, H.H.; Robert, B.; Jerome, H. Improved Soft-k-Means Clustering Algorithm for Balancing Energy Consumption in Wireless Sensor Networks. IEEE Internet Things J. 2021, 8, 4868–4881. [Google Scholar] [CrossRef]
- Jiang, Y.; Wu, M. Research on Reliability of Data Transmission Based on Network Coding in WSN. Comput. Technol. Dev. 2013, 23, 148–151. [Google Scholar]




| Method | Advantage | Disadvantage |
|---|---|---|
| Energy balancing method | To balance the energy loss of nodes and extend the network life. | Data are easy to lose; reliability is not high. |
| ReInForM routing algorithm | High reliability to ensure the effective work of the network. | Uneven energy consumption of each node easily causes network breakdown. |
| ReInForM routing algorithm based on energy selection | Low energy loss and reliability. | The problem of data loss; the packet acceptance rate is low. |
| ReInForM Routing Algorithm with FEC Encoding | Improved packet reception rate and reduced energy consumption. | The accuracy of data packets is not high. |
| Parameter Type | Parameter Value |
|---|---|
| Number of network nodes | 100 |
| Node initial energy | 9900 J |
| Node residual energy | 9700 J |
| Transmitter amplifier energy consumption | 500 pj/bit/m2 |
| Destination node energy consumption | 8J |
| 250 J/bit | |
| Forwarding each data packet energy consumption | 2 J |
| Node maximum transmission distance | 100 m |
| Data packet length | 128 B |
| Control packet length | 64 bit |
| Expected reliability | 0.9 |
| Channel error rate | 0.4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Q.; Huang, H.; Lu, X.; Qu, J.; Gu, J.; Yang, C. E-ReInForMIF Routing Algorithm Based on Energy Selection and Erasure Code Tolerance Machine. Electronics 2023, 12, 2408. https://doi.org/10.3390/electronics12112408
Wu Q, Huang H, Lu X, Qu J, Gu J, Yang C. E-ReInForMIF Routing Algorithm Based on Energy Selection and Erasure Code Tolerance Machine. Electronics. 2023; 12(11):2408. https://doi.org/10.3390/electronics12112408
Chicago/Turabian StyleWu, Qiong, Hai Huang, Xinmiao Lu, Jiaxing Qu, Juntao Gu, and Cunfang Yang. 2023. "E-ReInForMIF Routing Algorithm Based on Energy Selection and Erasure Code Tolerance Machine" Electronics 12, no. 11: 2408. https://doi.org/10.3390/electronics12112408
APA StyleWu, Q., Huang, H., Lu, X., Qu, J., Gu, J., & Yang, C. (2023). E-ReInForMIF Routing Algorithm Based on Energy Selection and Erasure Code Tolerance Machine. Electronics, 12(11), 2408. https://doi.org/10.3390/electronics12112408









