Architectural Threats to Security and Privacy: A Challenge for Internet of Things (IoT) Applications
Abstract
1. Introduction
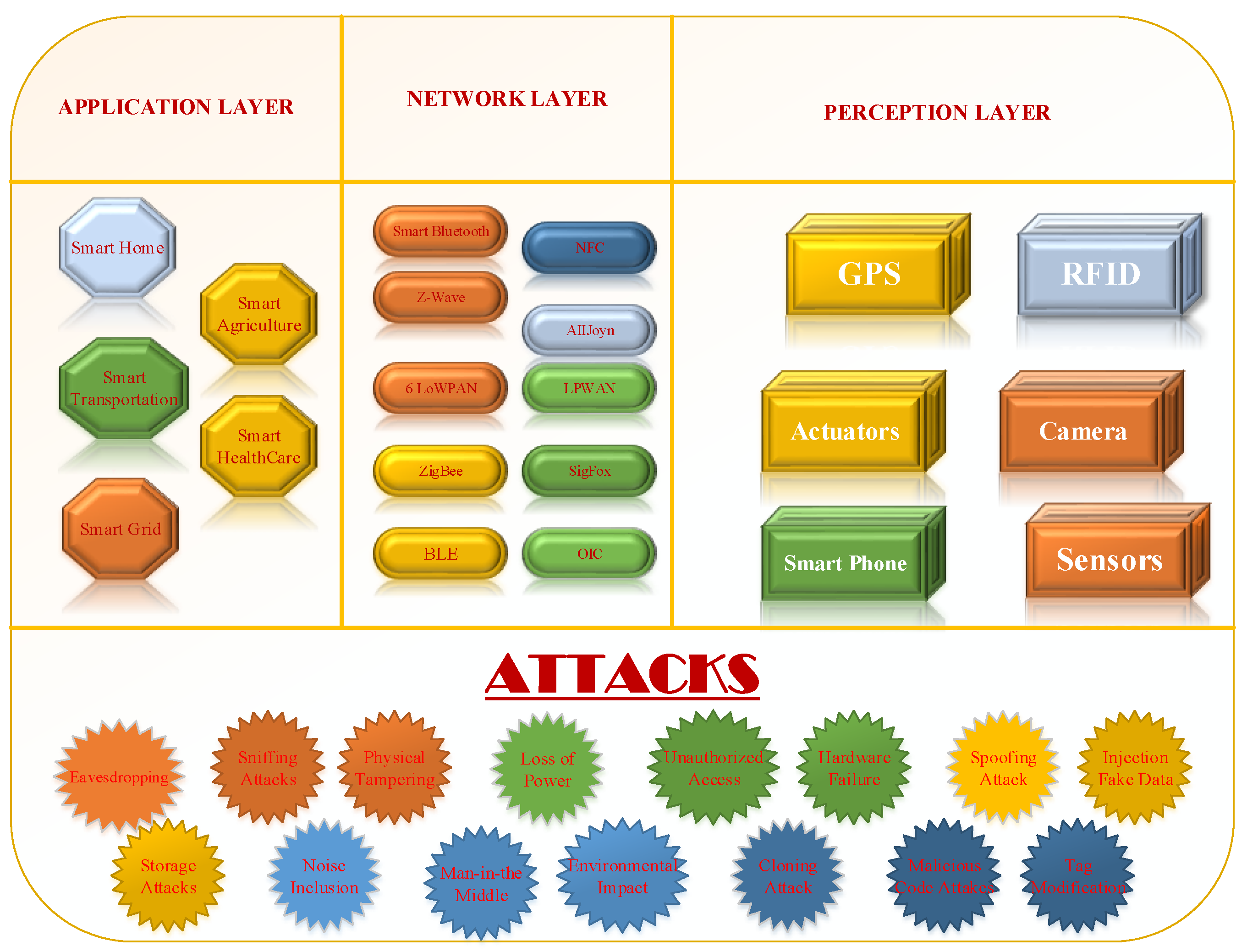
2. Internet of Things (IoT) Architecture
2.1. Sensing Layer
2.2. Communication Layer
2.3. Application Layer
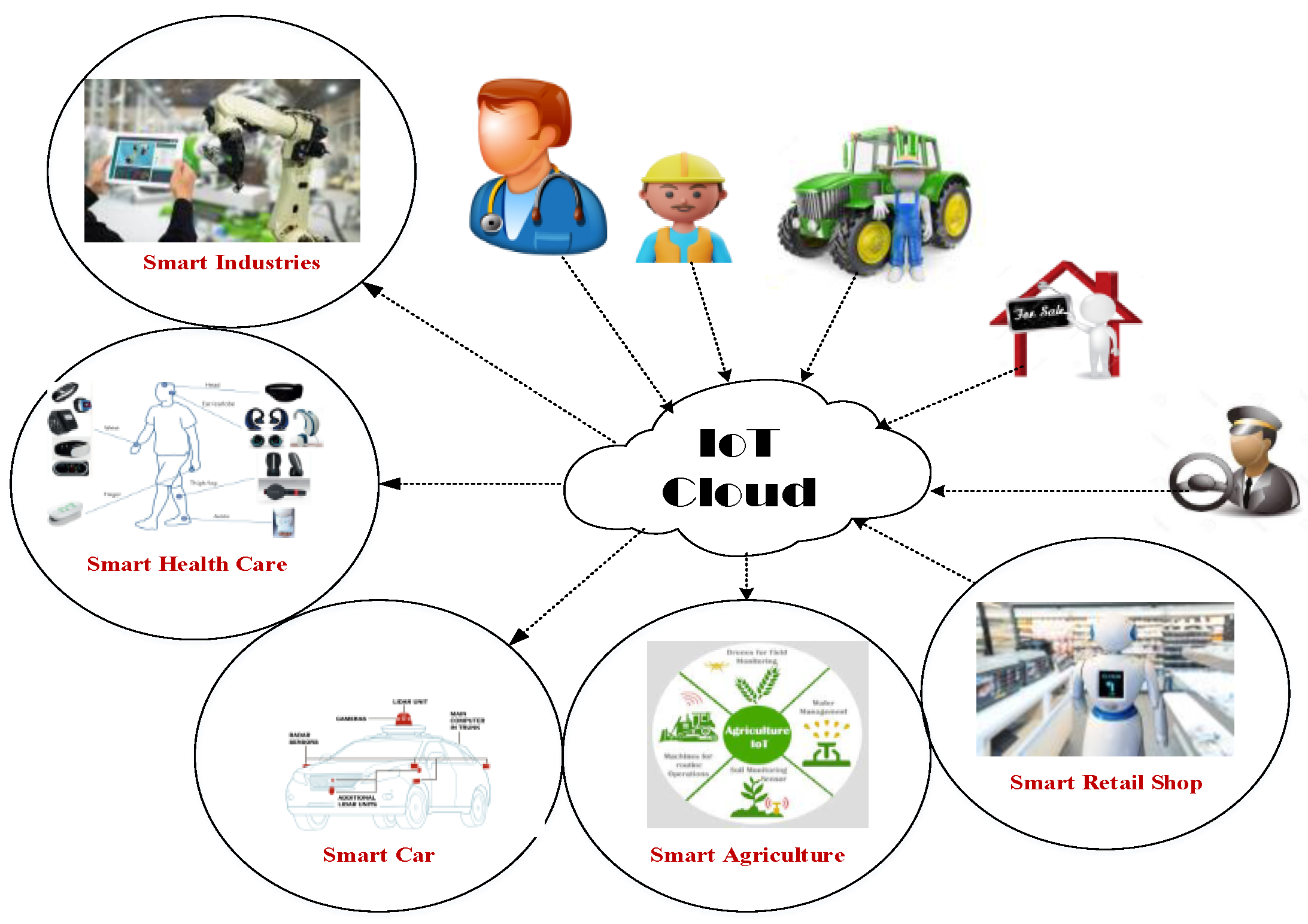
3. Applications of the Internet of Things
3.1. Smart Home
3.2. Smart Agriculture
3.3. Smart Transportation
3.4. Smart Healthcare
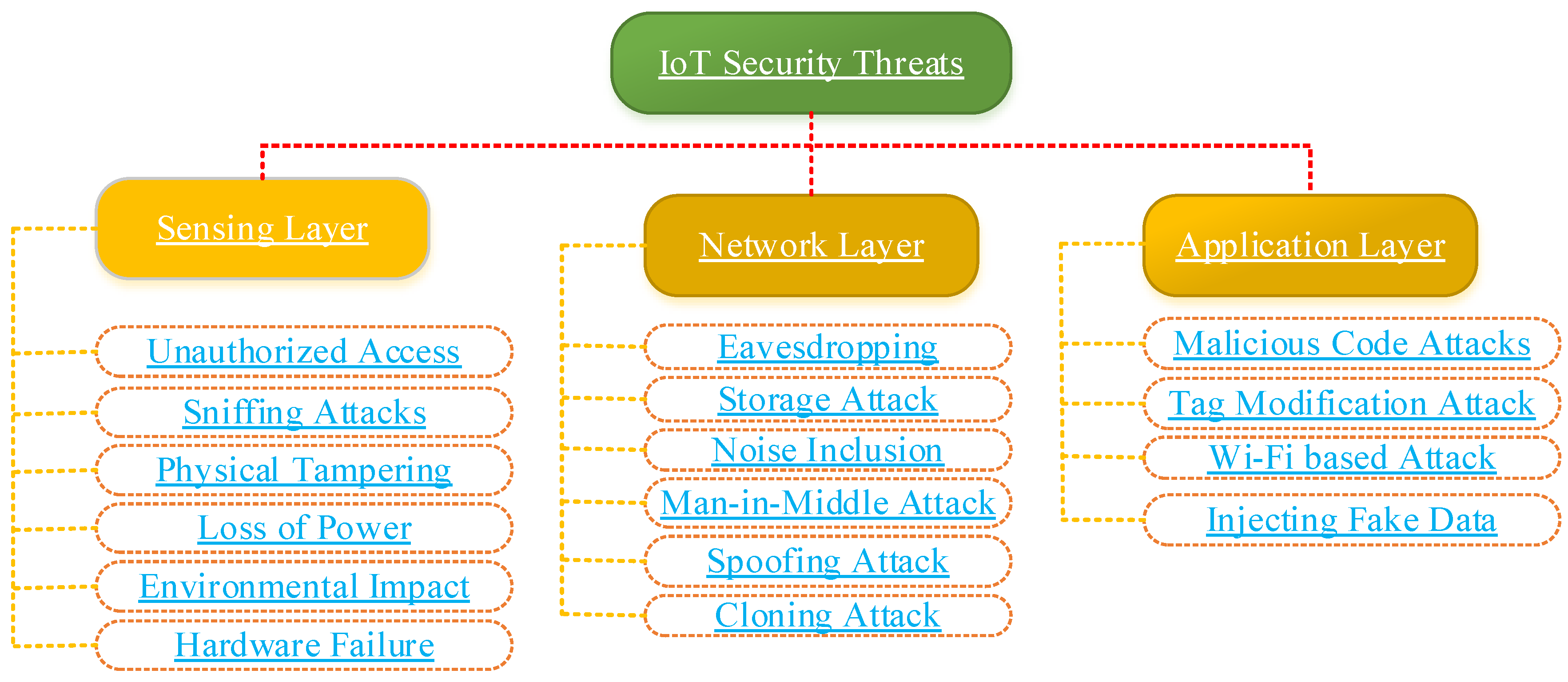
4. Security Threats and Vulnerabilities in IoT
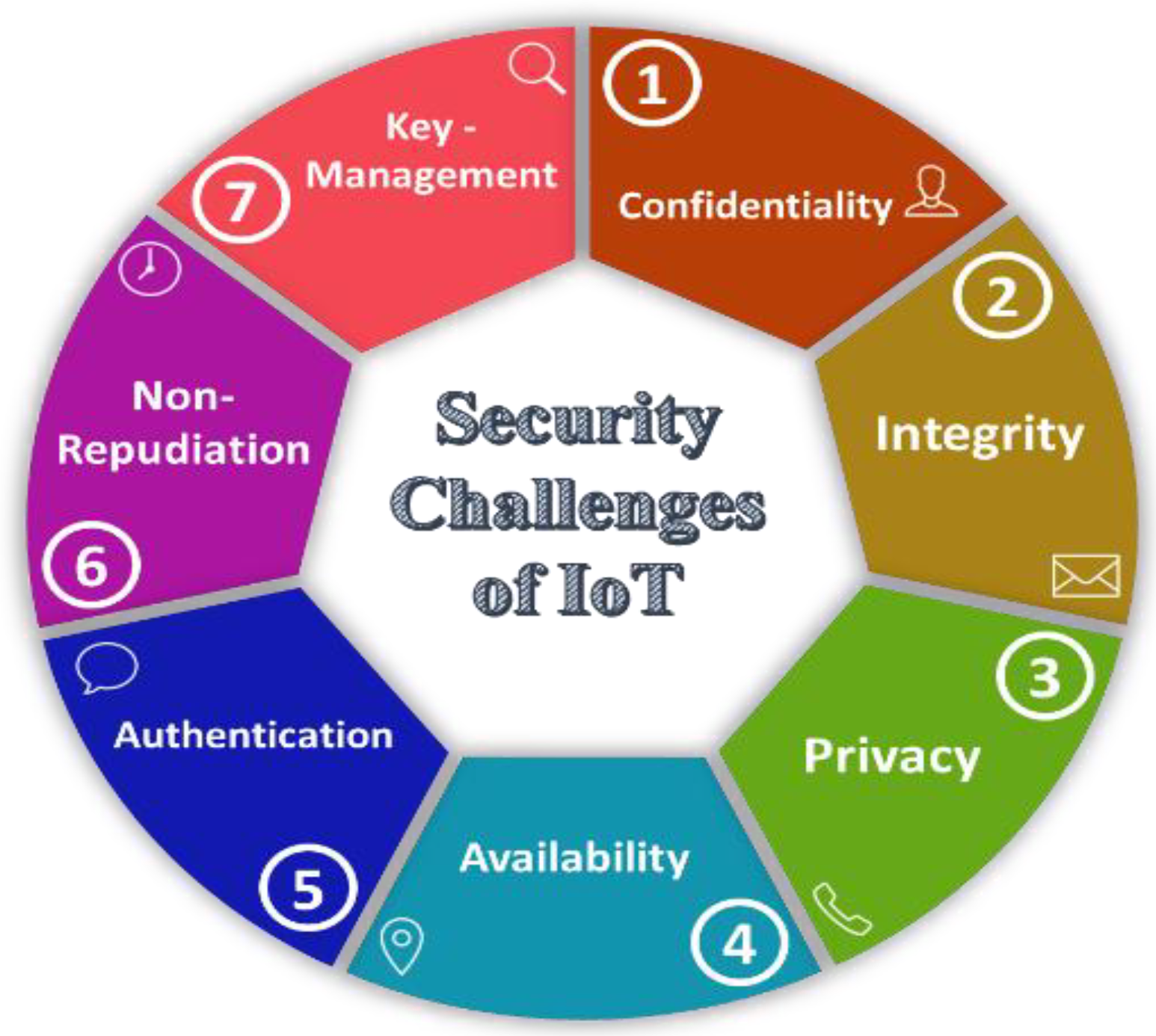
5. Classification of Security Challenges of the Internet of Things
- I.
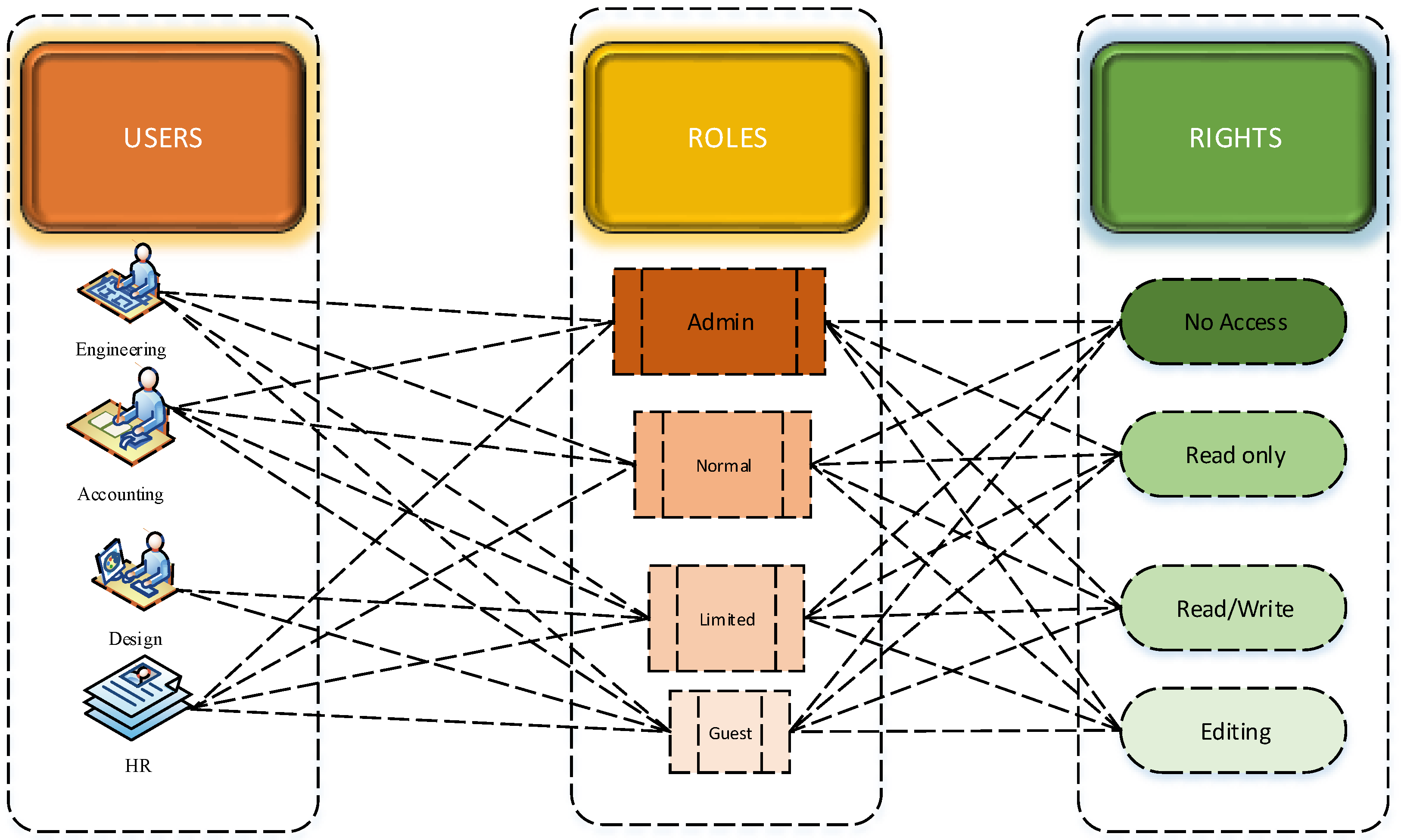
- In the context of business scenarios, data are a valuable asset to remain competitive in the market. The traditional treatment through “confidentiality” algorithms is not adequate to handle resource scarcity, heterogeneity, and scalability of data. To ensure the confidentiality of the IoT system, access control, authentication, and supervision of the network need strict compliance. Confidentiality of the data is compulsory to predict and estimate real-world problems. An IoT-based earlier warning system for tsunamis or earthquakes has a significant role in the evacuation of the population at risk to safeguard human life. The data obtained from the system must be accessible only to the pertinent body and disaster management department that issues necessary guidelines from time to time. The indiscriminate spread of such sensitive information may cause panic, unrest, hazards, public disorder, and law and order situations among a large group of people that may become out of control in some cases. Likewise, food company data of biosensors on bacterial composition must safely be stored and remain confidential. The leakage of the data may severely damage a firm’s reputation and competitive advantage over competitors. The confidentiality of IoT data cannot directly be dealt with by customer solutions, due to scalability and changing access rights. To manage knowledge systems, trust-based techniques remain effective to handle the sheer amount of IoT data, out of which Role-Based-Access-Control is standard and has emerged as successful as compared to traditional access control, as illustrated in Figure 5. Each departmental user has different roles and permissions; however, access rights can be altered by dynamically modifying role assignments. In the context of the IoT as compared to a static database, the entire stream in real-time can be accessed through RBAC, termed a data stream management system [90].
- II.
- The second challenge associated with the security of the IoT is “Integrity”, which means ensuring the data received to/from the perception layer are actual and pure from any kind of alteration. Further processing of manipulated data from sensors will give out erroneous results and, therefore, must not be trusted. The integrity is to be ensured for the internet of things system in general and data in particular [92]. The characteristics of integrity are extremely difficult phenomena to determine that data are received from the first and actual device. Moreover, the protection of information is not possible with the implementation of a password policy. This requires a sophisticated algorithm to establish integrity among devices and their data. In addition, advanced operating systems and configuration patterns support the algorithm. To fully implement integrity, an IoT system has three different states of information to consider that is either in motion, at rest, or in the processing stage. While traveling from the perception layer to communication channels to cloud computers for storage, the information must be protected against any modification in it. In the second stage of integrity, i.e., at the resting stage, the verification of information is carried out during the booting process. During the process in the third stage of integrity, periodic checks are conducted at operations at start-up and end. The sole purpose of a checksum of data during integrity is to make sure neither outer physical interference nor any cybercrime is committed [93]. In this connection, the uniqueness of contents and removal of errors from the data are ensured through CRC (Cyclic Redundancy Check) or Checksum techniques in caparison to traditional approaches of mathematical techniques such as SHA (Secure Hash Algorithm). Previously, the SHA technique was frequently applied; however, abusers arrange to modify the data, and the hash is recalculated; therefore, it becomes ineffective and obsolete [94]. In this connection, the internet of things system is shielded from Man-in-Middle assails after ensuring that data are unaltered and safely received. The framework in this context is also determined in research endeavors conducted in [95].
- III
- The third security challenge is “Privacy” in which data intended for a specific user can only be accessed. Privacy can be preserved in the internet of health things by exchanging sensitive information between patients and systems. Most of the exchange of data of IoT systems is performed through wireless communication technologies that are always vulnerable to threats and present numerous issues of privacy violations. Some common attacks in this respect are masking and eavesdropping attacks. Hence, the adoption of the IoT is strong for the resolution of privacy-related matters. Multiple models have been proposed to curtail the privacy problems of the IoT, for instance, Kaos, Tropos, NFR, GPRAM, and PRIS [96].
- IV.
- The fourth security challenge is “Availability”, which is alternatively used for reliability and defined as the probability of performance of an element of the network system to give the desired output at a specific time under specific environmental conditions. Availability is particularly used to calculate the performance of any component of a system that becomes operational after recovering from a faulty status. It is worth mentioning that failure in the large-scale internet of things can be disastrous to operations when encountering an emergency in public facilities. It is pivotal to ensure resilience, reliability, and availability in large IoT public network deployment, and this must be included in future research directions [97]. To make reliable internet of things systems, significant numbers of IoT elements are required to be connected to design a large complex network. In addition, the objects should to mobile, and the dynamics and configuration are subject to change as per the network requirements. As the mentioned network is constituted of smart but heterogeneous objects, the interoperability and coordination among them, the environment, the platforms, and the supporting software are to be taken into special consideration. Specific hardware standards have been developed to ensure the reliability of the network of the IoT; the first attempt in this regard was conducted in the military manual and termed MIL-HDBK-217, adopted by the majority of the engineering fraternity for the calculation of commercial and industrial reliability standards [98]. In contrast, software reliability is performed with numerous models that are not all acceptable, due to the non-specification of requirements, especially in the IoT. Safety and reliability are used in combination for the realization of the mutual goal defined for the software. Another terminology considered with availability is maintainability to obtain the optimal cost of the IoT life-cycle that should be taken into account even in the design phase. In the case of failure, and maintainability of the internet of things, the problematic components should easily be replaced without interruption of service and provide seamless connectivity. A highly maintainable system must produce effective, efficient, and satisfactory output [99].
- V.
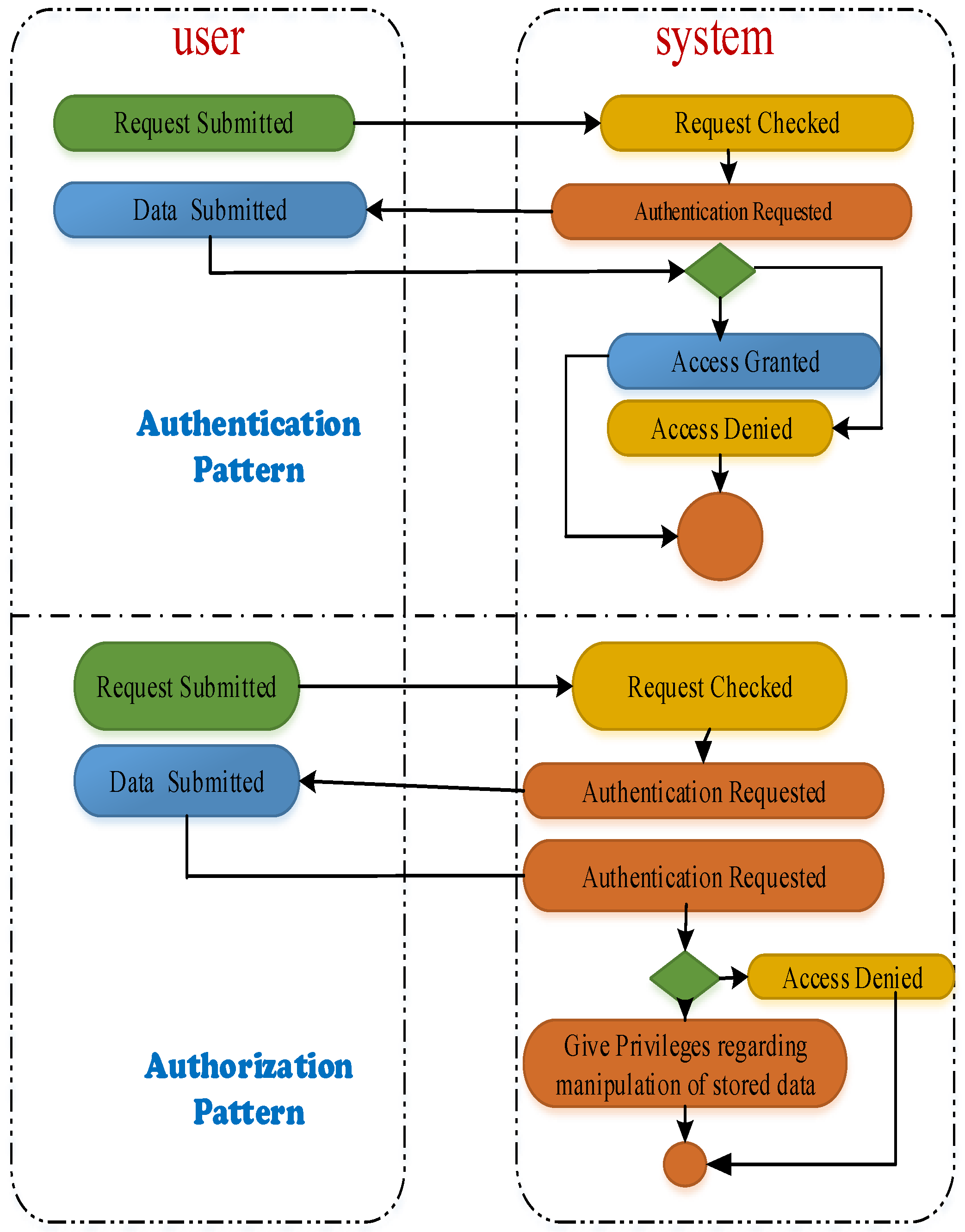
- The fifth security challenge is that “Authentication” is solely required in the internet of things to prevent intrusion into the system and the theft of private information. Normally, the heterogeneous devices connected to the network communicate with the local gateway for the outward provisioning of information. The local gateway obtains necessary permission from the cloud computing system to send the required information to the outside world. To filter out unauthorized persons, application request information must first authenticate to gain access into the network. The phenomenon of approving any smart object or user to grant permission for the collection of network information or data is called authorization, illustrated in detail in Figure 7. It comprises identification, putting requests by the user to the gateway or cloud platform, followed by authorization and authentication. Without following the requisite process, access will not be granted and authentication will fail.
- VI.
- The sixth security challenge is “non-Repudiation”, which is the computational settling of the dispute between the sender and receiver in a case when the sender refuses to send the message and the receiver declines to receive the message. Numerous protocols have been designed to minimize the denying phenomena [106]. In this situation, the distrusted parties may overall create an ineffective way of communication and a lack of promising service provision that unnecessarily causes concerns and anxiety among prime stakeholders. Some traditional non-repudiation mechanisms have been developed and divided into TTP (trusted party)-based approaches and non-TTP-based schemes to determine another way to control impediments to acceptance and development. In the former scenario, TTP plays the role of middleman between the client and service provider and helps to facilitate the exchange of information and acknowledgment of receiving the message [107]. Another method of activation of an off-line TTP service is where the sender provides encrypted data with a TTP key so that the receiver acquires the decrypted service only after obtaining acknowledgment [108]. These phenomena experience performance bottlenecks and single-point failure in distributed IoT systems because of the unavailability of third parties. It is dominated by a non-TTP-based approach in which the service provider manages to forward the message in encrypted form and then provide the true and fake password for attempting multiple iterations. If the response is not received from the client side, the service provider terminates the process. One of the drawbacks of this scheme is that clients can cheat based on a true password [109]. The process has been further refined by proposing a protocol where the server furnishes part of the decryption key to run a series of iterations. Some disadvantages on the part of non-TTP-based schemes are lacking fairness, the high cost, and the performance issues to iterate for confirmations, which is certainly not possible for the internet of things technology. Currently, reliability and trustworthiness have been enhanced in terms of the security of industrial and transportation IoT by applying a non-repudiation mechanism in electronic events [110]. Furthermore, the non-repudiation mechanisms are digital signature (service provider sends private key and receiver verifies its authenticity), digital watermarking [111] (embedded with unique code for distribution to claim the ownership), sign-encryption [112] (signed by the originator and then encrypted), public key cryptography [113] (integrity and authentication), and certificate cryptography [114] (custody of user’s secret key).
- VII.
- The seventh security challenge is “Key Management”, which is an integral part of security infrastructure that is responsible for the management of numerous tasks of IoT systems. The key management may be asymmetric, as shown in Figure 9, or symmetric. In this connection, a symmetric-shared key [115] ensures safe and secure communication in resource-constrained IoT devices. The keys generated for the security of the entire system are generated and stored; however, the real issue confronted in the mobile system is their distribution [116]. Various standards and protocols are developed for IoT applications to redress security threats. Although MQTT (message queuing telemetry transport) and CoAPs (constrained application protocols) are frequently used by an IoT that lacks security mechanisms, the security services of SSL (Secure Socket Shell) are utilized [117].
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Pourghebleh, B.; Wakil, K.; Navimipour, N.J. A comprehensive study on the trust management techniques in the Internet of Things. IEEE Internet Things J. 2019, 6, 9326–9337. [Google Scholar] [CrossRef]
- Young, S.-J.; Chiou, C.-L. Synthesis and optoelectronic properties of Ga-doped ZnO nanorods by hydrothermal method. Microsyst. Technol. 2018, 24, 103–107. [Google Scholar] [CrossRef]
- Wei, L.; Wu, J.; Long, C. Blockchain-enabled trust management in service-oriented internet of things: Opportunities and challenges. In Proceedings of the 2021 The 3rd International Conference on Blockchain Technology, Shanghai, China, 26–28 March 2021; pp. 90–95. [Google Scholar]
- Das, R.; Prasad, A. Survey of Blockchain Techniques for IoT Device Security. In Blockchain Technology; CRC Press: Boca Raton, FL, USA, 2022; pp. 57–72. [Google Scholar]
- Li, S.; Tryfonas, T.; Li, H. The Internet of Things: A security point of view. Internet Res. 2016, 26, 337–359. [Google Scholar] [CrossRef]
- Choo, K.R.; Dehghantanha, A.; Parizi, R.M. Blockchain Cybersecurity, Trust and Privacy; Advances in Information Security; Springer: Berlin/Heidelberg, Germany, 2020; Volume 79, pp. 28–29. [Google Scholar]
- Souri, A.; Hussien, A.; Hoseyninezhad, M.; Norouzi, M. A systematic review of IoT communication strategies for an efficient smart environment. Trans. Emerg. Telecommun. Technol. 2022, 33, 3736. [Google Scholar] [CrossRef]
- Gajewski, M.; Batalla, J.M.; Mastorakis, G.; Mavromoustakis, C.X. Anomaly traffic detection and correlation in smart home automation IoT systems. Trans. Emerg. Telecommun. Technol. 2020, 33, e4053. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context-aware computing for the internet of things: A survey. IEEE Commun. Surv. Tutor. 2013, 16, 414–454. [Google Scholar] [CrossRef]
- Tamrakar, A.; Shukla, A.; Kaliifullah, A.; Reegu, F.; Shukla, K. extended review on internet of things (IoT) and its characterization. Int. J. Health Sci. 2022, 10, 234. [Google Scholar]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low power wide area networks: An overview. IEEE Commun. Surv. Tutor. 2017, 19, 855–873. [Google Scholar] [CrossRef]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Internet Things J. 2016, 4, 1–20. [Google Scholar] [CrossRef]
- Kim, H.; Choi, H.; Kang, H.; An, J.; Yeom, S.; Hong, T. A systematic review of the smart energy conservation system: From smart homes to sustainable smart cities. Renew. Sustain. Energy Rev. 2021, 140, 110755. [Google Scholar] [CrossRef]
- Bakhshi, K.K.; Rahmani, A.M.; Sabbagh Molahosseini, A. A fault-tolerant architecture for internet-of-things based on software-defined networks. Telecommun. Syst. 2021, 77, 155–169. [Google Scholar] [CrossRef]
- Hong, J.; Shin, J.; Lee, D. Strategic management of next-generation connected life: Focusing on smart key and car-home connectivity. Technol. Forecast. Soc. Chang. 2016, 103, 11–20. [Google Scholar] [CrossRef]
- Khedekar, D.C.; Truco, A.C.; Oteyza, D.A.; Huertas, G.F. Home automation—A fast-expanding market. Thunderbird Int. Bus. Rev. 2017, 59, 79–91. [Google Scholar] [CrossRef]
- Coughlan, T.; Mackley, K.L.; Brown, M.; Martindale, S.; Schlögl, S.; Mallaband, B.; Arnott, J.; Hoonhout, J.; Szostak, D.; Brewer, R.; et al. Current issues and future directions in methods for studying technology in the home. PsychNology J. 2013, 11, 159–184. [Google Scholar]
- Bhrugubanda, M.; Rao, S.L.A.; Shanmukhi, M.; Rao, A. Sustainable And Intelligent IoT Based Precision Agriculture–Smart Farming. Solid State Technol. 2020, 63, 17824–17833. [Google Scholar]
- Mankin, R.; Hagstrum, D.; Guo, M.; Eliopoulos, P.; Njoroge, A. Automated applications of acoustics for stored product insect detection, monitoring, and management. Insects 2021, 12, 259. [Google Scholar] [CrossRef]
- Joshi, V.; Adhikari, M.S. IoT-Based Technology for Smart Farming. In Electronic Devices and Circuit Design; Apple Academic Press: Palm Bay, FL, USA, 2022; pp. 223–242. [Google Scholar]
- Pisman, T.I.; Erunova, M.G.; Botvich, I.Y.; Emelyanov, D.V.; Kononova, N.A.; Bobrovsky, A.V.; Kryuchkov, A.A.; Shpedt, A.A.; Shevyrnogov, A.P. Information Content of Spectral Vegetation Indices for Assessing the Weed Infestation of Crops Using Ground-Based and Satellite Data. Izv. Atmos. Ocean. Phys. 2021, 57, 1188–1197. [Google Scholar] [CrossRef]
- Islam, N.; Rashid, M.M.; Pasandideh, F.; Ray, B.; Moore, S.; Kadel, R. A review of applications and communication technologies for internet of things (IoT) and unmanned aerial vehicle (UAV) based sustainable smart farming. Sustainability 2021, 13, 1821. [Google Scholar] [CrossRef]
- Mukhopadhyay, S.C.; Nag, A.; Gooneratne, C. Printed and flexible sensors: A review of products and techniques. In Printed and Flexible Sensor Technology; IOPscience: Bristol, UK, 2021; p. 11. [Google Scholar]
- Garcia, A.P.; Umezu, C.K.; Polania, E.C.M.; Neto, A.F.D.; Rossetto, R.; Albiero, D. Sensor-Based Technologies in Sugarcane Agriculture. Sugar Tech. 2022, 24, 679–698. [Google Scholar] [CrossRef]
- Brown, S.; Wagner-Riddle, C.; Debruyn, Z.; Jordan, S.; Berg, A.; Ambadan, J.T.; Congreves, K.A.; Machado, P.V.F. Assessing variability of soil water balance components measured at a new lysimetric facility dedicated to the study of soil ecosystem services. J. Hydrol. 2021, 603, 127037. [Google Scholar] [CrossRef]
- Kumar, A.; Bhatia, A.; Fagodiya, R.K.; Malyan, S.K.; Meena, B.L. A Promising Technique for Greenhouse Gases Measurement Eddy Covariance Flux Tower. Adv. Plants Agric. Res. 2017, 7, 337–340. [Google Scholar]
- Murray, S.C. Optical sensors advancing precision in agricultural production. Photon. Spectra 2018, 51, 48. [Google Scholar]
- Povh, F.P.; Anjos, W.d.G.d.; Yasin, M.; Harun, S.W.; Arof, H. Optical sensors applied in agricultural crops. In Optical Sensors-New Developments and Practical Applications; IntechOpen: London, UK, 2014; pp. 141–163. [Google Scholar]
- Upendar, K.; Agrawal, K.N.; Vinod, K.S. The Role of Sensing Techniques in Precision Agriculture. In Machine Vision for Industry 4.0; CRC Press: Boca Raton, FL, USA, 2022; pp. 63–78. [Google Scholar]
- Gómez Álvarez-Arenas, T.; Gil-Pelegrin, E.; Cuello, J.E.; Fariñas, M.D.; Sancho-Knapik, D.; Burbano, D.A.C.; Peguero-Pina, J.J. Ultrasonic sensing of plant water needs for agriculture. Sensors 2016, 16, 1089. [Google Scholar] [CrossRef]
- Sharma, V.; Tripathi, A.K.; Mittal, H. Technological revolutions in smart farming: Current trends, challenges & future directions. Comput. Electron. Agric. 2022, 13, 107217. [Google Scholar]
- Savickas, D.; Steponavičius, D.; Domeika, R. Analysis of Telematics Data of Combine Harvesters and Evaluation of Potential to Reduce Environmental Pollution. Atmosphere 2021, 12, 674. [Google Scholar] [CrossRef]
- Jaafar, H.H.; Woertz, E. Agriculture as a funding source of ISIS: A GIS and remote sensing analysis. Food Policy 2016, 64, 14–25. [Google Scholar] [CrossRef]
- Yalew, S.G.; van Griensven, A.; Mul, M.L.; van der Zaag, P. Land suitability analysis for agriculture in the Abbay basin using remote sensing, GIS and AHP techniques. Model. Earth Syst. Environ. 2016, 2, 101. [Google Scholar] [CrossRef]
- Ramu, P.; Santosh, B.S.; Chalapathi, K. Crop-land suitability analysis using geographic information system and remote sensing. Prog. Agric. Eng. Sci. 2022, 36, 77–94. [Google Scholar] [CrossRef]
- Leelavathi, G.; Shaila, K.; Venugopal, K.R. Hardware performance analysis of RSA cryptosystems on FPGA for wireless sensor nodes. Int. J. Intell. Netw. 2021, 2, 184–194. [Google Scholar] [CrossRef]
- Chugh, B.; Thakur, S.; Singh, A.K.; Joany, R.M.; Rajendran, S.; Nguyen, T.A. Electrochemical sensors for agricultural application. In Nanosensors for Smart Agriculture; Elsevier: Amsterdam, The Netherlands, 2022; pp. 147–164. [Google Scholar]
- Qureshi, T.; Saeed, M.; Ahsan, K.; Malik, A.A.; Muhammad, E.S.; Touheed, N. Smart Agriculture for Sustainable Food Security Using Internet of Things (IoT). Wirel. Commun. Mob. Comput. 2022, 2022, 9608394. [Google Scholar] [CrossRef]
- del-Moral-Martínez, I.; Rosell-Polo, J.R.; Company, J.; Sanz, R.; Escolà, A.; Masip, J.; Martinez-Casasnovas, J.A.; Arnó, J. Mapping vineyard leaf area using mobile terrestrial laser scanners: Should rows be scanned on-the-go or discontinuously sampled? Sensors 2016, 16, 119. [Google Scholar] [CrossRef]
- Basri, M.A.M.; Adnan, M.A. Autonomous Agriculture Robot for Monitoring Plant using Internet of Things. ELEKTRIKA-J. Electr. Eng. 2022, 21, 14–19. [Google Scholar] [CrossRef]
- Khan, N.; Ray, R.L.; Sargani, G.R.; Ihtisham, M.; Khayyam, M.; Ismail, S. Current progress and future prospects of agriculture technology: Gateway to sustainable agriculture. Sustainability 2021, 13, 4883. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R. Enhancing smart farming through the applications of Agriculture 4.0 technologies. Int. J. Intell. Netw. 2022, 3, 150–164. [Google Scholar] [CrossRef]
- Al-Dweik, A.; Muresan, R.; Mayhew, M.; Lieberman, M. IoT-based multifunctional scalable real-time enhanced roadside unit for intelligent transportation systems. In Proceedings of the 2017 IEEE 30th Canadian Conference on Electrical and Computer Engineering (CCECE), Windsor, ON, Canada, 30 April–3 May 2017; pp. 1–6. [Google Scholar]
- Messaoud, S.; Ahmed, O.B.; Bradai, A.; Atri, M. Machine learning modeling-powered IoT systems for smart applications. In IoT-Based Intelligent Modelling for Environmental and Ecological Engineering; Springer: Berlin/Heidelberg, Germany, 2021; pp. 185–212. [Google Scholar]
- Jain, B.; Brar, G.; Malhotra, J.; Rani, S.; Ahmed, S.H. A cross-layer protocol for traffic management in Social Internet of Vehicles. Future Gener. Comput. Syst. 2018, 82, 707–714. [Google Scholar] [CrossRef]
- Wang, Z.; Wei, H.; Wang, J.; Zeng, X.; Chang, Y. Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey. Sustainability 2022, 14, 12409. [Google Scholar] [CrossRef]
- Ozbayoglu, M.; Kucukayan, G.; Dogdu, E. A real-time autonomous highway accident detection model based on big data processing and computational intelligence. In Proceedings of the 2016 IEEE International Conference on Big Data (Big Data), Washington, DC, USA, 5–8 December 2016; pp. 1807–1813. [Google Scholar]
- Kwon, D.; Park, S.; Baek, S.; Malaiya, R.K.; Yoon, G.; Ryu, J.-T. A study on the development of the blind spot detection system for the IoT-based smart connected car. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 12–14 January 2018; pp. 1–4. [Google Scholar]
- Devi, S.; Neetha, T. Machine Learning based traffic congestion prediction in an IoT based Smart City. Int. Res. J. Eng. Technol. 2017, 4, 3442–3445. [Google Scholar]
- Ghosh, A.; Chatterjee, T.; Samanta, S.; Aich, J.; Roy, S. Distracted driving: A novel approach towards accident prevention. Adv. Comput. Sci. Technol. 2017, 10, 2693–2705. [Google Scholar]
- Ryder, B.; Wortmann, F. Autonomously detecting and classifying traffic accident hotspots. In Proceedings of the 2017 ACM International Joint Conference on Pervasive and Ubiquitous Computing and Proceedings of the 2017 ACM International Symposium on Wearable Computers, Maui, HI, USA, 11–15 September 2017; pp. 365–370. [Google Scholar]
- Munoz-Organero, M.; Ruiz-Blaquez, R.; Sánchez-Fernández, L. Automatic detection of traffic lights, street crossings and urban roundabouts combining outlier detection and deep learning classification techniques based on GPS traces while driving. Comput. Environ. Urban Syst. 2018, 68, 1–8. [Google Scholar] [CrossRef]
- Amato, G.; Carrara, F.; Falchi, F.; Gennaro, C.; Meghini, C.; Vairo, C. Deep learning for decentralized parking lot occupancy detection. Expert Syst. Appl. 2017, 72, 327–334. [Google Scholar] [CrossRef]
- You, Z.; Yang, K.; Luo, W.; Lu, X.; Cui, L.; Le, X. Iterative Correlation-based Feature Refinement for Few-shot Counting. arXiv 2022, arXiv:2201.08959. [Google Scholar]
- Zantalis, F.; Koulouras, G.; Karabetsos, S.; Kandris, D. A review of machine learning and IoT in smart transportation. Future Internet 2019, 11, 94. [Google Scholar] [CrossRef]
- Gupta, A.; Kulkarni, S.; Jathar, V.; Sharma, V.; Jain, N. Smart car parking management system using IoT. Am. J. Sci. Eng. Technol. 2017, 2, 112–119. [Google Scholar]
- Rizvi, S.R.; Zehra, S.; Olariu, S. Aspire An agent-oriented smart parking recommendation system for smart cities. IEEE Intell. Transp. Syst. Mag. 2018, 11, 48–61. [Google Scholar] [CrossRef]
- Araújo, A.; Kalebe, R.; Giraõ, G.; Gonçalves, K.; Neto, B. Reliability analysis of an IoT-based smart parking application for smart cities. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 4086–4091. [Google Scholar]
- Egaji, O.A.; Evans, G.; Griffiths, M.G.; Islas, G. Real-time machine learning-based approach for pothole detection. Expert Syst. Appl. 2021, 184, 115. [Google Scholar] [CrossRef]
- Gopalakrishnan, K. Deep learning in data-driven pavement image analysis and automated distress detection: A review. Data 2018, 3, 28. [Google Scholar] [CrossRef]
- Kokilavani, M.; Malathi, A. Smart street lighting system using IoT. Int. J. Adv. Res. Appl. Sci. Technol. 2017, 3, 8–11. [Google Scholar]
- Tripathy, A.K.; Mishra, A.K.; Das, T.K. Smart lighting: Intelligent and weather adaptive lighting in street lights using IoT. In Proceedings of the 2017 International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), Kerala, India, 6–7 July 2017; pp. 1236–1239. [Google Scholar]
- Chowdhury, D.N.; Agarwal, N.; Laha, A.B.; Mukherjee, A. A vehicle-to-vehicle communication system using IoT approach. In Proceedings of the 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018; pp. 915–919. [Google Scholar]
- Naveed, Q.N.; Alqahtani, H.; Khan, R.U.; Almakdi, S.; Alshehri, M.; Abdul Rasheed, M.A.; Jain, B.; Brar, G. An intelligent traffic surveillance system using integrated wireless sensor network and improved phase timing optimization. Sensors 2022, 22, 3333. [Google Scholar] [CrossRef]
- Fan, X.; Liu, J.; Wang, Z.; Jiang, Y.; Liu, X. Crowdsourced road navigation: Concept, design, and implementation. IEEE Commun. Mag. 2017, 55, 126–128. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, Y. Research on intelligent medical big data system based on Hadoop and blockchain. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 7. [Google Scholar] [CrossRef]
- Merck, S.F. Chronic disease and mobile technology: An innovative tool for clinicians. Nurs. Forum 2017, 52, 298–305. [Google Scholar] [CrossRef] [PubMed]
- Sharp, L.K.; Biggers, A.; Perez, R.; Henkinsi, J.; Tilton, J.; Gerber, B.S. A Pharmacist and Health Coach–Delivered Mobile Health Intervention for Type 2 Diabetes: Protocol for a Randomized Controlled Crossover Study. JMIR Res. Protoc. 2021, 10, 171. [Google Scholar] [CrossRef] [PubMed]
- Vijayalakshmi, A.; Jose, D.V.; Unnisa, S. Wearable Sensors for Pervasive and Personalized Health Care. In IoT in Healthcare and Ambient Assisted Living; Springer: Berlin/Heidelberg, Germany, 2021; pp. 123–143. [Google Scholar]
- Zhang, D.; Liu, Q. Biosensors and bioelectronics on smartphone for portable biochemical detection. Biosens. Bioelectron. 2016, 75, 273–284. [Google Scholar] [CrossRef] [PubMed]
- Akmandor, A.O.; Jha, N.K. Keep the stress away with SoDA: Stress detection and alleviation system. IEEE Trans. Multi-Scale Comput. Syst. 2017, 3, 269–282. [Google Scholar] [CrossRef]
- Haque, N.; Rahman, M.A.; Shahriar, M.H.; Khalil, A.A.; Uluagac, S. A novel framework for threat analysis of machine learning-based smart healthcare systems. arXiv 2021, arXiv:2103.03472. [Google Scholar]
- Esteva, A.; Kuprel, B.; Novoa, R.A.; Ko, J.; Swetter, S.M.; Blau, H.M.; Thrun, S. Dermatologist-level classification of skin cancer with deep neural networks. Nature 2017, 542, 115–118. [Google Scholar] [CrossRef]
- Kumar, S.; Lim, W.M.; Sivarajah, U.; Kaur, J. Artificial intelligence and blockchain integration in business: Trends from a bibliometric-content analysis. Inf. Syst. Front. 2022, 1–26. [Google Scholar] [CrossRef]
- Yamin, M.M.; Ullah, M.; Ullah, H.; Katt, B. Weaponized AI for cyber attacks. J. Inf. Secur. Appl. 2021, 57, 102722. [Google Scholar] [CrossRef]
- Peters, B.S.; Armijo, P.R.; Krause, C.; Choudhury, S.A.; Oleynikov, D. Review of emerging surgical robotic technology. Surg. Endosc. 2018, 32, 1636–1655. [Google Scholar] [CrossRef]
- Sood, S.K.; Rawat, K.S.; Kumar, D. A visual review of artificial intelligence and Industry 4.0 in healthcare. Comput. Electr. Eng. 2022, 101, 107948. [Google Scholar] [CrossRef]
- Winkler, E.C.; Wiemann, S. Findings made in gene panel to whole genome sequencing: Data, knowledge, ethics–and consequences? Expert Rev. Mol. Diagn. 2016, 16, 1259–1270. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Liu, Z.; Fan, F.; Hou, Y.; Yang, H.; Meng, X.; Zhang, Y.; Ren, F. Microfluidic chip and its application in autophagy detection. TrAC Trends Anal. Chem. 2019, 117, 300–315. [Google Scholar] [CrossRef]
- Zhang, J.Z.; Li, Y.K.; Cao, L.Y.; Zhang, Y. Research on the construction of smart hospitals at 424 homes and abroad. Chin. Hos. Manag. 2018, 38, 64–66. [Google Scholar]
- Wang, K.; Zhao, Y.; Gangadhari, R.K.; Li, Z. Analyzing the adoption challenges of the Internet of things (Iot) and artificial intelligence (ai) for smart cities in china. Sustainability 2021, 13, 10983. [Google Scholar] [CrossRef]
- White, R.W. Skill discovery in virtual assistants. Commun. ACM 2018, 61, 106–113. [Google Scholar] [CrossRef]
- Ortiz, C.L. Holistic conversational assistants. AI Mag. 2018, 39, 88–90. [Google Scholar] [CrossRef]
- Raghuvanshi, A.; Singh, U.K.; Joshi, C. A review of various security and privacy innovations for IoT applications in healthcare. In Advanced Healthcare Systems: Empowering Physicians with IoT-Enabled Technologies; Wiley: Hoboken, NJ, USA, 2022; pp. 43–58. [Google Scholar]
- Redfern, J. Smart health and innovation: Facilitating health-related behavior change. Proc. Nutr. Soc. 2017, 76, 328–332. [Google Scholar] [CrossRef]
- Zeevi, D.; Korem, T.; Zmora, N.; Israeli, D.; Rothschild, D.; Weinberger, A.; Ben-Yacov, O.; Lador, D.; Avnit-Sagi, T.; Lotan-Pompan, M.; et al. Personalized nutrition by prediction of glycemic responses. Cell 2015, 163, 1079–1094. [Google Scholar] [CrossRef]
- Kumar, A.; Jain, A.K. RFID Security issues, defenses, and security schemes. In Handbook of Research on Machine Learning Techniques for Pattern Recognition and Information Security; IGI Global: Hershey, PA, USA, 2021; pp. 293–310. [Google Scholar]
- Tu, Y.-J.; Kapoor, G.; Piramuthu, S. On Group Ownership Delegate Protocol for RFID Systems. Inf. Syst. Front. 2021, 1–8. [Google Scholar] [CrossRef]
- Parkinson, S.; Khan, S. A Survey on Empirical Security Analysis of Access Control Systems: A Real-World Perspective. ACM Comput. Surv. (CSUR) 2022, 98, 109–111. [Google Scholar] [CrossRef]
- Misra, S.; Roy, C.; Mukherjee, A. Introduction to Industrial Internet of Things and Industry 4.0; CRC Press: Boca Raton, FL, USA, 2021; pp. 86–89. [Google Scholar]
- Thilakarathne, N.N.; Kagita, M.K.; Priyashan, W.D. Green internet of things: The next generation energy efficient internet of things. In Applied Information Processing Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 391–402. [Google Scholar]
- Bhattacharjee, S.; Salimitari, M.; Chatterjee, M.; Kwiat, K.; Kamhoua, C. Preserving data integrity in IoT networks under opportunistic data manipulation. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 446–453. [Google Scholar]
- Zhang, G.; Kou, L.; Zhang, L.; Liu, C.; Da, Q.; Sun, J. A new digital watermarking method for data integrity protection in the perception layer of IoT. Secur. Commun. Netw. 2017, 2017, 3126010. [Google Scholar] [CrossRef]
- Meng, Y.; Li, J. Data sharing mechanism of sensors and actuators of industrial IoT based on blockchain-assisted identity-based cryptography. Sensors 2021, 21, 6084. [Google Scholar] [CrossRef] [PubMed]
- Bender, T.; Huesmainn, R.; Heinemann, A. Software Development Processes for ADs, SMCs and OSCs supporting Usability, Security, and Privacy Goals–an Overview. In Proceedings of the 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021; pp. 1–6. [Google Scholar]
- Zhu, Q.; Uddin, M.Y.S.; Venkatasubramanian, N.; Hsu, C.; Hong, H. Enhancing reliability of community internet-of-things deployments with mobility. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 1–2. [Google Scholar]
- Pokorni, S. Reliability prediction of electronic equipment: Problems and experience. In Proceedings of the 7th International Scientific Conference on Defensive Technologies OTEH, Belgrade, Serbia, 6–7 October 2016; pp. 695–700. [Google Scholar]
- Thomas, M.O.; Rad, B.B. Reliability evaluation metrics for internet of things, car tracking system: A review. Int. J. Inf. Technol. Comput. Sci. (IJITCS) 2017, 9, 1–10. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, L.D. Internet of Things (IoT) cybersecurity research: A review of current research topics. IEEE Internet Things J. 2018, 6, 2103–2115. [Google Scholar] [CrossRef]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef]
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Bashir, A.K. A survey of security and privacy issues in the Internet of Things from the layered context. Trans. Emerg. Telecommun. Technol. 2022, 33, 3935. [Google Scholar] [CrossRef]
- El-Hajj, M.; Chamoun, M.; Fadlallah, A.; Serhrouchni, A. Analysis of authentication techniques in Internet of Things (IoT). In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 10–20 October 2017; pp. 1–3. [Google Scholar]
- Chae, C.-J.; Choi, K.; Choi, K.; Yae, Y.; Shin, Y. The extended authentication protocol using e-mail authentication in OAuth 2.0 protocol for secure granting of user access. J. Internet Comput. Serv. 2015, 1, 21–28. [Google Scholar] [CrossRef]
- Xu, Y.; Ren, J.; Wang, G.; Zhang, C.; Yang, J.; Zhang, Y. A blockchain-based nonrepudiation network computing service scheme for industrial IoT. IEEE Trans. Ind. Inform. 2019, 6, 3632–3641. [Google Scholar] [CrossRef]
- Adil, M.; Khan, M.K. Emerging IoT applications in sustainable smart cities for covid-19: Network security and data preservation challenges with future directions. Sustain. Cities Soc. 2021, 75, 103311. [Google Scholar] [CrossRef]
- Asokan, N.; Schunter, M.; Waidner, M. Optimistic protocols for fair exchange. In Proceedings of the 4th ACM Conference on Computer and Communications Security, Zurich, Switzerland, 1–4 April 1997; pp. 7–17. [Google Scholar]
- Markowitch, O.; Roggeman, Y. Probabilistic non-repudiation without trusted third party. In Proceedings of the Second Conference on Security in Communication Networks, Sydney, Australia, 9–11 November 1999; Volume 99, pp. 25–36. [Google Scholar]
- Chen, C.-L.; Deng, Y.; Weng, W.; Zhou, M.; Sun, H. A blockchain-based intelligent anti-switch package in tracing logistics system. J. Supercomput. 2021, 77, 7791–7832. [Google Scholar] [CrossRef]
- Singh, A.; Anand, A. Data leakage detection using cloud computing. Int. J. Eng. Comput. Sci. 2017, 6, 234. [Google Scholar] [CrossRef]
- Liu, J.; Ren, A.; Zhang, L.; Sun, R.; Du, X.; Guizani, M. A novel secure authentication scheme for heterogeneous internet of things. In Proceedings of the ICC 2019–2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Salman, A.; Diehl, W.; Kaps, J. A lightweight hardware/software co-design for pairing-based cryptography with low power and energy consumption. In Proceedings of the 2017 International Conference on Field Programmable Technology (ICFPT), Melbourne, Australia, 11–13 December 2017; pp. 235–238. [Google Scholar]
- Karati, A.; Fan, C.; Zhuang, E. Reliable data sharing by certificates encryption supporting keyword search against vulnerable KGC in the industrial internet of things. IEEE Trans. Ind. Inform. 2021, 18, 3661–3669. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Engels, D.W. A secure IoT architecture for smart cities. In Proceedings of the 2016 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 812–813. [Google Scholar]
- Shivraj, V.L.; Rajan, M.A.; Singh, M.; Balamuralidhar, P. One-time password authentication scheme based on elliptic curves for Internet of Things (IoT). In Proceedings of the 2015 5th National Symposium on Information Technology: Towards New Smart World (NSITNSW), Riyadh, Saudi Arabia, 17–19 February 2015; pp. 1–6. [Google Scholar]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Li, J.; Niyato, D.; Dobre, O.; Poor, H.V. 6G Internet of Things: A comprehensive survey. IEEE Internet Things J. 2021, 1, 234. [Google Scholar] [CrossRef]
- Choi, W.; Kim, J.; Lee, S.; Park, E. Smart home and internet of things: A bibliometric study. J. Clean. Prod. 2021, 301, 126908. [Google Scholar] [CrossRef]



| IoT Devices Installed at Smart Home | Purpose |
|---|---|
| Blood Pressure machine | Upgradation of Lifestyle and Health |
| Temperature sensor | |
| Glucose level machine | |
| Physiological signs monitor | |
| Heart rate | |
| EGG for an epileptic, sleep disorder, Seizure | |
| Infrared Sensors | |
| Wearable Accelerometer | |
| Wearable Sensors | |
| Tele-healthcare | |
| Kitchenware | Automation |
| Washing | |
| House Gates | Remotely controlled |
| Windows | |
| Garden | |
| Wardrobe | |
| TV | Smart Entertainment |
| Internet | |
| Laptop | |
| Heating and Ventilation | Comfortable environment |
| Electricity | |
| Gas |
| Smart Agriculture Sensors | Function | Application |
|---|---|---|
| Acoustic Sensor | Work on the changes in noise level | Pest identification and detection [17], seed classification [18] |
| Optoelectronic Sensor | Differentiation of plant type | Detect herbicides, weeds, and unwanted plants [19], differentiation of soil and vegetation based on reflection spectra [20] |
| Airflow Sensor | Measure the moisture contents and air permeability | Determine different soil characteristics, e.g., structure, moisture, and compaction [21] |
| SWLB (Soft-Water-Level-Based) Sensor | Determine hydrological behaviors | Measure the stream and water flow, rainfalls [22] |
| Electromagnetic Sensors | Record the electromagnetic response and electrical conductivity | Various chemicals such as organic matter and nitrates [23] |
| Mechanical Sensors | Soil mechanical resistance based on pressure | Different levels of compaction [24] |
| Eddy Covariance-Based Sensor | Determine continuous flux on a large part of land [25] | Gases exchange quantification, that is, carbon dioxide, methane, and water vapor [26] |
| Optical Sensor | Soil’s capability to the reflection of light [27] | Soil moisture, organic substance, and clay contents and minerals [28] |
| Ultrasonic Ranging Sensors | Work in association with the camera [29] | Uniform spray coverage, and tank and crop canopy monitoring [30] |
| Telematics Sensors | Collection of data from non-accessible points to avoid visits [31] | Reduce environmental effects through data management [32] |
| Remote Sensing | Management and manipulation of geographical data [33] | Identification of pests and plants, degradation mapping, land cover, and yield dates forecasting and modeling [34] |
| FPGA (Field-Programmable Gate Array based) Sensor | Real-time monitoring due to reconfiguration flexibility but high cost [35] | Transpiration, humidity, and irrigation [36] |
| Electrochemical Sensor | Chemical analysis of soil [37] | Soil characteristics are pH, salinity, and soil macro- and micronutrients [38] |
| LIDAR (Light Detection & Ranging) | Estimation of dynamic measurement of agriculture data [39] | Monitoring erosion, 3-D modeling, and land mapping and segmentation [40] |
| Mass Flow Sensors | Measure the quantity of grain flow [41] | Grain moisture contents [42] |
| Intelligent Transport | Features |
|---|---|
| Accident Prevention |
|
| Parking System |
|
| Road Condition | |
| Smart Street Light | |
| Transport Infrastructure |
|
| Optimization of Route |
|
| Intelligent Health Care | Features |
|---|---|
| Health Management |
|
| Diagnosis and Treatment |
|
| Drug Research | |
| Smart Hospital |
|
| Virtual Assistance | |
| Disease prevention and Risk Monitoring |
| IoT Layers | Security Challenges |
|---|---|
| Application Layer |
|
| Communication |
|
| Sensing Layer |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, Y.; Su’ud, M.B.M.; Alam, M.M.; Ahmad, S.F.; Salim, N.A.; Khan, N. Architectural Threats to Security and Privacy: A Challenge for Internet of Things (IoT) Applications. Electronics 2023, 12, 88. https://doi.org/10.3390/electronics12010088
Khan Y, Su’ud MBM, Alam MM, Ahmad SF, Salim NA, Khan N. Architectural Threats to Security and Privacy: A Challenge for Internet of Things (IoT) Applications. Electronics. 2023; 12(1):88. https://doi.org/10.3390/electronics12010088
Chicago/Turabian StyleKhan, Yasser, Mazliham Bin Mohd Su’ud, Muhammad Mansoor Alam, Sayed Fayaz Ahmad, Nur Agus Salim, and Nasir Khan. 2023. "Architectural Threats to Security and Privacy: A Challenge for Internet of Things (IoT) Applications" Electronics 12, no. 1: 88. https://doi.org/10.3390/electronics12010088
APA StyleKhan, Y., Su’ud, M. B. M., Alam, M. M., Ahmad, S. F., Salim, N. A., & Khan, N. (2023). Architectural Threats to Security and Privacy: A Challenge for Internet of Things (IoT) Applications. Electronics, 12(1), 88. https://doi.org/10.3390/electronics12010088








