A Secure Data Flow Forwarding Method Based on Service Ordering Management
Abstract
1. Introduction
2. Related Work
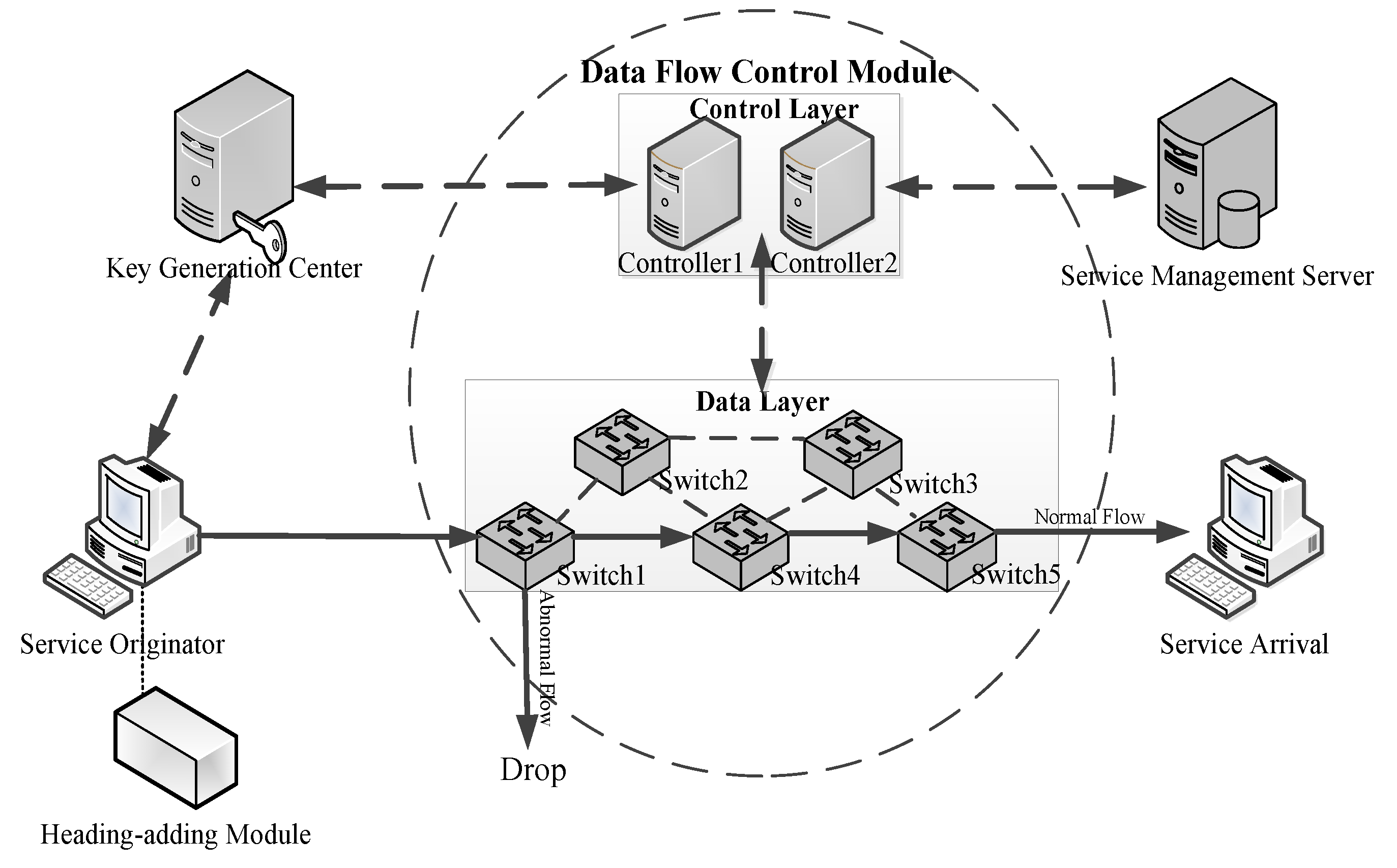
3. Secure Data Flow Forwarding Model Based on Service Ordering Management
- (1)
- Key generation center (KGC): It is responsible for key generation and information distribution during the digital signature process, providing the secret signature key to the service originator and providing the public system parameters to the controller in the data flow control module for signature verification.
- (2)
- Header-addition module: Before sending the data flow from the service originator, the header-add module inserts the service header into the front end of the original data message, which provides the basis for secure and orderly data flow forwarding. The structure of the service header is detailed in Section 3.1.
- (3)
- Service management server: It is responsible for formulating rules for the services in the network and sending the rules to the controller of the data flow control module, providing the basis for matching and forwarding data flows. The generation of the service rules is detailed in Section 3.2.
- (4)
- Data flow control module: It consists of the control layer and the data layer. The controller in the control layer controls the generation of the flow table according to the service rules in the service management server and sends the flow table to the switches in the data layer. The switches in the data layer perform service header-based data flow control and forwarding according to the flow table information. Only data flows that meet the service rules are allowed, and those violating the rules are discarded. The specific process that implements the orderly forwarding of data flows is described in Section 3.3. Meanwhile, the entry switch verifies the signature of the matches in the received data flow to ensure their correctness and tamperproof nature. The process of verifying the data flow matches is described in Section 3.4.
3.1. Service Header Structure
- (1)
- ID (16 bits): It stores the identity of the data flow originator.
- (2)
- Matches (128 bits): It stores the characteristic information describing the data flow, which may include the type of service, the type of originator role of the service, the type of source host, and the destination host type. Fine-grained control and forwarding of data flows can be achieved on the basis of the Matches field, which ensures the secure and orderly transmission of data flows in the network.
- (3)
- Signature (768 bits): It guarantees the authenticity and unforgeability of the Matches field.
- (4)
- Next_Type (8 bits): It stores the type of header that the switch will need to parse next, providing a logical relationship between multiple headers for the switch.
3.2. Generation of Service Rules
- (1)
- Service library: It stores the set of service types in the network.
- (2)
- Authentication module: It authenticates the parties (users and hosts) who use the services. When a user or host on the network wants to qualify for a certain type of service, it applies to the authentication module, which then establishes a logical relationship between the authenticated role and host information and that type of service, and then sends it to the rule generation module.
- (3)
- Path generation module: It generates the service transmission path in the network according to the type of service. Currently, network forwarding devices only forward data flows through IP or MAC addresses, making it difficult to manage network services and prevent attacks. Therefore, it is essential to arrange data flows by service type by regulating service transmission paths in the network. The method of generating the service transmission path is described below.
- (4)
- Rule generation module: It generates the service rule table for the services in the service library based on the results obtained from the authentication and path generation modules.
- (5)
- Update module: It is responsible for ensuring the update of information on the service management server. When information is added or excluded in the service library and other modules, the update module notifies the corresponding modules to update accordingly.
- (6)
- Service rule table: It records the management rules for each type of service, including the set of users and hosts allowed to use a certain type of service and the service transmission paths in the network. The service rule table acts as the basis for performing orderly and secure data flow forwarding by the service control module.
- (1)
- All hosts that have been cleared by the authentication module must be connected to the destination host via a path, as in Equation (1).
- (2)
- The path length between hosts that need to communicate with each other should be minimized to avoid excessive traffic and improve the efficiency of service transmission. Assuming that the distances between host and route or between routes are not considered, the number of routing address hops can be used to describe the path length. The ordered transmission path length of the service T is denoted by and expressed as
| Algorithm 1. Path topology generation algorithm. |
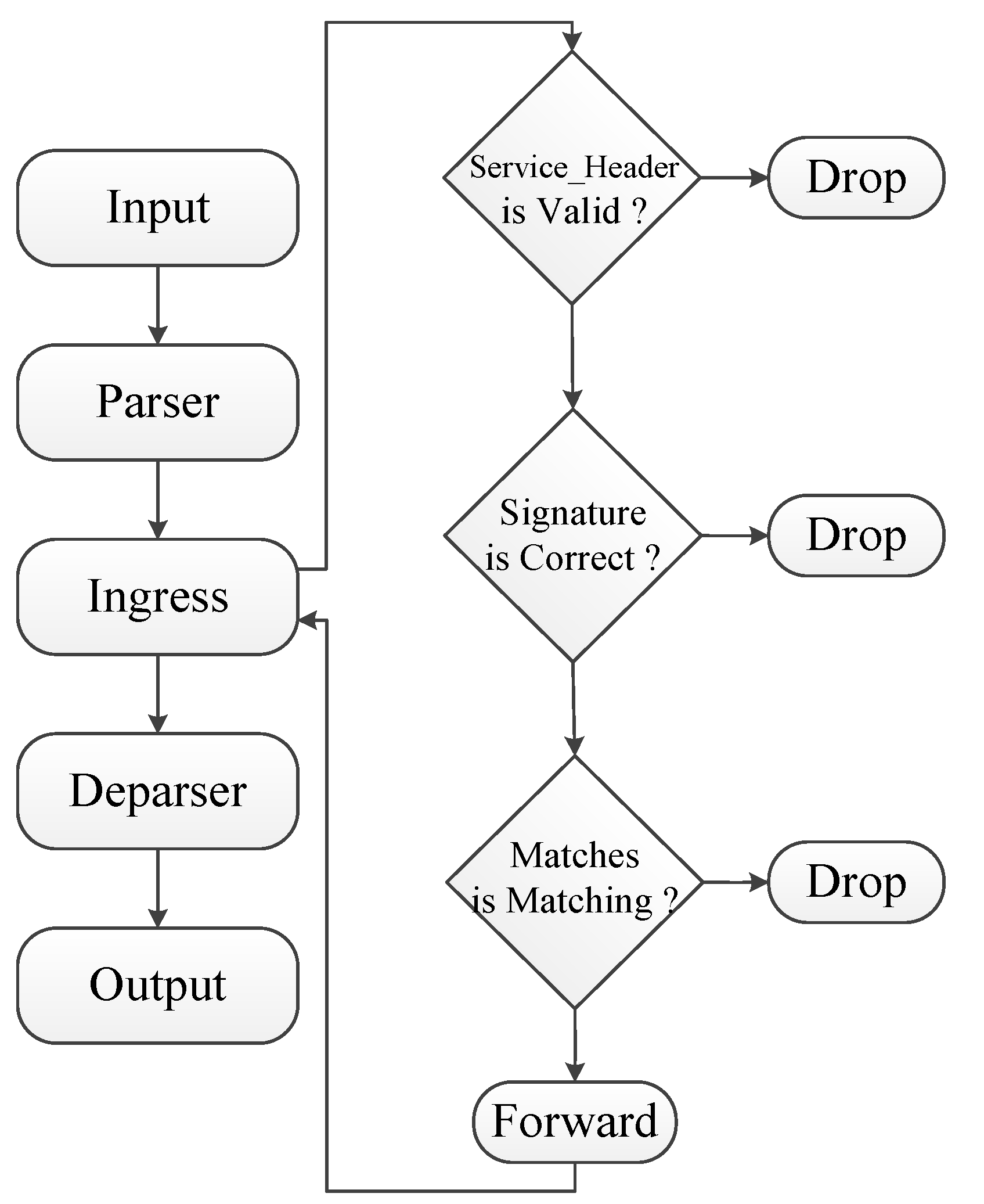
3.3. Ordered Forwarding of Data Flows
| Algorithm 2. Control and forwarding of data flow. |
3.4. Identity-Based Match Signature
- (1)
- It is safe against an attacker, who initiates an attack by randomly selecting a message and identity . In other words, the signature generated by , and cannot pass signature verification.
- (2)
- It is based on the difficulties of discrete logarithms. For example, suppose is a positive integer; it is difficult to solve even if we have in .
| Algorithm 3. Packet signature algorithm. |
| Algorithm 4. Packet signature verification algorithm. |
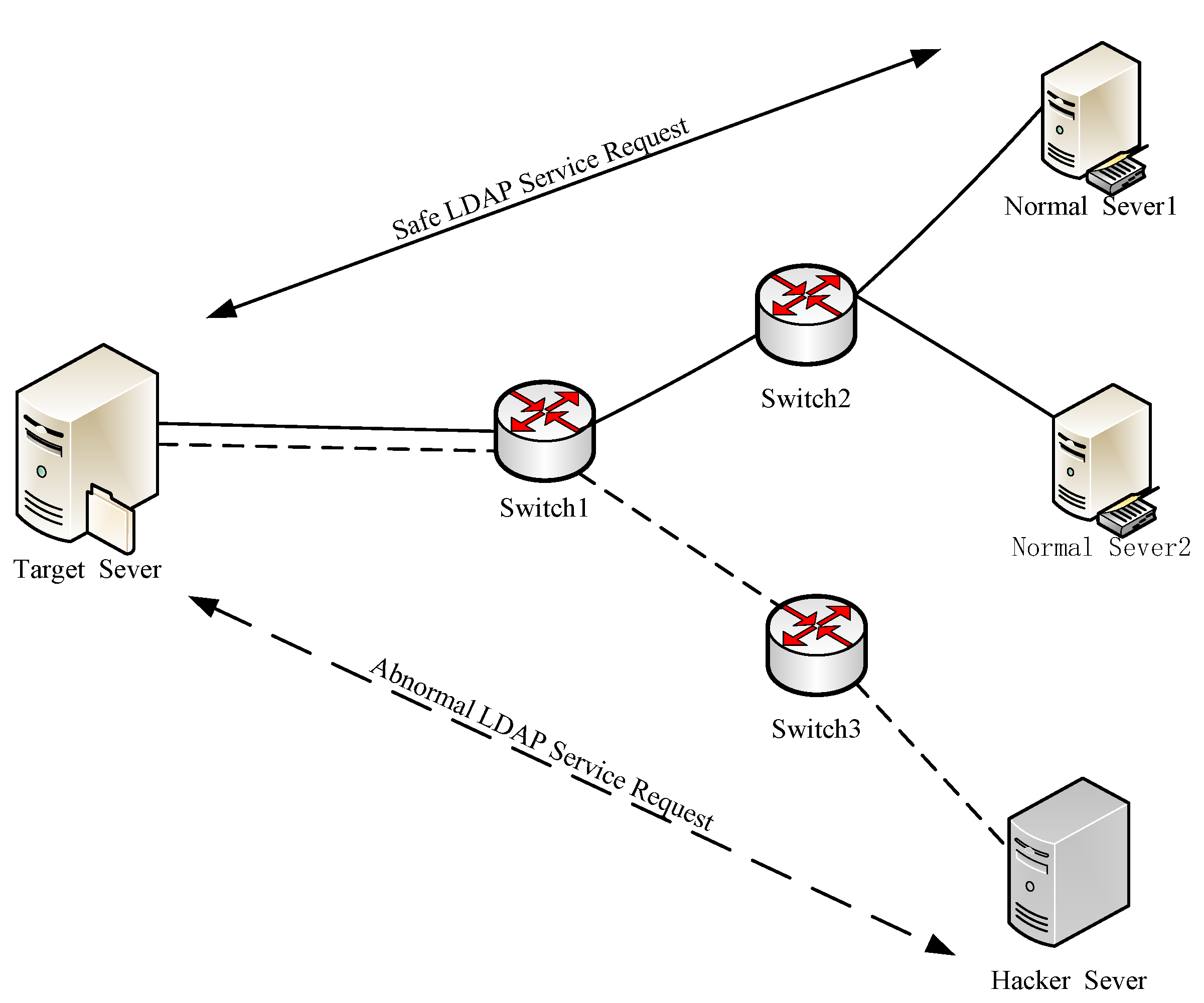
4. Experiment and Analysis
4.1. Experiment Environment
4.2. Validity Analysis
4.3. Protection against Network Attacks
- (1)
- MS08–067 vulnerability attack
- (2)
- Apache Log4j2 vulnerability attack
4.4. Performance Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Greene, K. Software-Defined Networking; MIT Technology Review: Cambridge, Massachusetts, 2009; pp. 30–32. [Google Scholar]
- Chica, J.C.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Gao, S.; Li, Z.; Xiao, B.; Wei, G. Security threats in the data plane of software-defined networks. IEEE Netw. 2018, 32, 108–113. [Google Scholar] [CrossRef]
- Rana, D.S.; Dhondiyal, S.A.; Chamoli, S.K. Software Defined Networking (SDN) Challenges, issues and Solution. Int. J. Comput. Sci. Eng. 2019, 7, 884–889. [Google Scholar] [CrossRef]
- Zhang, X.; Cui, L.; Wei, K.; Tso, F.P.; Ji, Y.; Jia, W. A survey on stateful data plane in software defined networks. Comput. Netw. 2021, 184, 107597. [Google Scholar] [CrossRef]
- Lara, A.; Kolasani, A.; Ramamurthy, B. Network innovation using openflow: A survey. IEEE Commun. Surv. Tutor. 2013, 16, 493–512. [Google Scholar] [CrossRef]
- Kaur, S.; Kumar, K.; Aggarwal, N. A review of Security Threats in Software-Defined Networking. In Intelligent Computing and Communication Systems: Algorithms for Intelligent Systems; Singh, B., Coello, C.A., Jindal, P., Verma, P., Eds.; Springer: Berlin, Germany, 2021; pp. 123–131. [Google Scholar]
- Bosshart, P.; Daly, D.; Gibb, G.; Izzard, M.; McKeown, N.; Rexford, J.; Schlesinger, C.; Talayco, D.; Vahdat, A.; Varghese, G. P4: Programming protocol-independent packet processors. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–95. [Google Scholar] [CrossRef]
- Kaur, R.; Kaur, A. Digital Signature. In Proceedings of the 2012 International Conference on Computing Sciences, Phagwara, India, 14–15 September 2012; pp. 295–301. [Google Scholar]
- Hess, F. Efficient Identity Based Signature Schemes Based on Pairings. In Proceedings of the International Workshop on Selected Areas in Cryptography, St. John’s, NF, Canada, 15–16 August 2002; pp. 310–324. [Google Scholar]
- Topolski, R. NebuAd and Partner ISPs: Wiretapping, Forgery and Browser Hijacking; Free Press: Washington, DC, USA, 2008. [Google Scholar]
- Hirani, M.; Jones, S.; Read, B. Global DNS Hijacking Campaign: DNS Record Manipulation at Scale. 2019. Available online: https://www.fireeye.com/blog/threat-research/2019/01/global-dns-hijacking-campaign-dns-record-manipulation-at-scale.html (accessed on 9 January 2019).
- Shrivastava, R.K.; Mishra, S.; Archana, V.; Hota, C. Preventing Data Tampering in IoT Networks. In Proceedings of the 2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, 16–19 December 2019; pp. 1–6. [Google Scholar]
- Ahmed, M.R.; Islam, S.; Shatabda, S.; Islam, A.K.M.M.; Robin, M.T.I. Intrusion detection system in software-defined networks using machine learning and deep learning techniques–a comprehensive survey. TechRxiv 2021. [Google Scholar] [CrossRef]
- Song, Z.; Liu, Z. Abnormal detection method of industrial control system based on behavior model. Comput. Secur. 2019, 84, 166–178. [Google Scholar]
- Ding, P.; Li, J.; Wang, L.; Wen, M.; Guan, Y. HYBRID-CNN: An efficient scheme for abnormal flow detection in the SDN-Based Smart Grid. Secur. Commun. Netw. 2020, 2020, 8850550. [Google Scholar] [CrossRef]
- Chen, J. Network intrusion detection based on convolutional neural networks with LSTM. Cyber Secur. Data Gov. 2021, 40, 42–46. [Google Scholar]
- Wu, Y.; Jiang, B.; Pan, R.; Liu, Y. A SDN access control mechanism based on zero trust. Netinfo Secur. 2020, 8, 37–46. [Google Scholar]
- Chuang, P.J.; Wu, K.L. Employing On-Line Training in SDN Intrusion Detection. J. Inf. Sci. Eng. 2021, 37, 483–496. [Google Scholar]
- Qin, X.; Tang, G.; Chang, C. SDN security control and forwarding method based on cipher identification. J. Commun. 2018, 39, 31–42. [Google Scholar]
- Maleh, Y.; Qasmaoui, Y.; El Gholami, K.; Sadqi, Y.; Mounir, S. A comprehensive survey on SDN security: Threats, mitigations, and future directions. J. Reliab. Intell. Environ. 2022, 1–39. [Google Scholar] [CrossRef]
- Skowyra, R.; Xu, L.; Gu, G.; Dedhia, V.; Hobson, T.; Okhravi, H.; Landry, J. Effective Topology Tampering Attacks and Defenses in Software-Defined Networks. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Luxembourg, 25–28 June 2018; pp. 374–385. [Google Scholar]
- Dargahi, T.; Caponi, A.; Ambrosin, M.; Bianchi, G.; Conti, M. A survey on the security of stateful SDN data planes. IEEE Commun. Surv. Tutor. 2017, 19, 1701–1725. [Google Scholar] [CrossRef]
- Huang, T.; Yu, F.R.; Zhang, C.; Liu, J.; Zhang, J.; Liu, Y. A survey on large-scale software defined networking (SDN) testbeds: Approaches and challenges. IEEE Commun. Surv. Tutor. 2016, 19, 891–917. [Google Scholar] [CrossRef]
- Yao, G.; Bi, J.; Xiao, P. Source Address Validation Solution with OpenFlow/NOX Architecture. In Proceedings of the 19Th IEEE International Conference on Network Protocols, Vancouver, BC, Canada, 17–20 October 2011; pp. 7–12. [Google Scholar]
- Casado, M.; Freedman, M.J.; Pettit, J.; Luo, J.; McKeown, N.; Shenker, S. Ethane: Taking control of the enterprise. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 1–12. [Google Scholar] [CrossRef]
- Zuo, Z.; Chang, C.; Zhang, Y.; He, R.; Qin, X.; Yung, K.L. P4Label: Packet forwarding control mechanism based on P4 for software-defined networking. J. Ambient. Intell. Humaniz. Comput. 2020, 1–14. [Google Scholar] [CrossRef]
- Zhu, X.; Chang, C.; Xi, Q.; Zuo, Z. Attribute-guard: Attribute-based flow access control framework in software-defined networking. Secur. Commun. Netw. 2020, 2020, 6302739. [Google Scholar] [CrossRef]
- Sasaki, T.; Pappas, C.; Lee, T.; Hoefler, T.; Perrig, A. SDNsec: Forwarding Accountability for the SDN Data Plane. In Proceedings of the 2016 25th International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 1–10. [Google Scholar]
- Wu, P.; Chang, C.; Ma, Y. Port address overloading based packet forwarding. J. Commun. 2021, 42, 70–83. [Google Scholar]
- Galindo, D.; Garcia, F.D. A Schnorr-Like Lightweight Identity-Based Signature Scheme. In Proceedings of the International Conference on Cryptology in Africa, Gammarth, Tunisia, 21–25 June 2009; pp. 135–148. [Google Scholar]
- Schumacher, M.; Haul, C.; Hurler, M.; Buchmann, A. Data Mining in Vulnerability Databases. In Proceedings of the 7th Workshop ”Sicherheit in Vernetzten Systemen”, Hamburg, Germay, 22 March 2000. [Google Scholar]
- Sopariwala, S.; Fallon, E.; Asghar, M.N. Log4jPot: Effective Log4Shell Vulnerability Detection System. In Proceedings of the 2022 33rd Irish Signals and Systems Conference (ISSC), Cork, Ireland, 9–10 June 2022; pp. 1–5. [Google Scholar]
- Wang, S.; Li, Q.; Zhang, Y. LPV:Lightweight packet forwarding verification in SDN. Chin. J. Comput. 2019, 42, 176–189. [Google Scholar]
- Zuo, Z.; Chang, C.; Zhu, X. A software-defined networking packet forwarding verification mechanism based on programmable data plane. J. Electron. Inf. Technol. 2020, 42, 1110–1117. [Google Scholar]



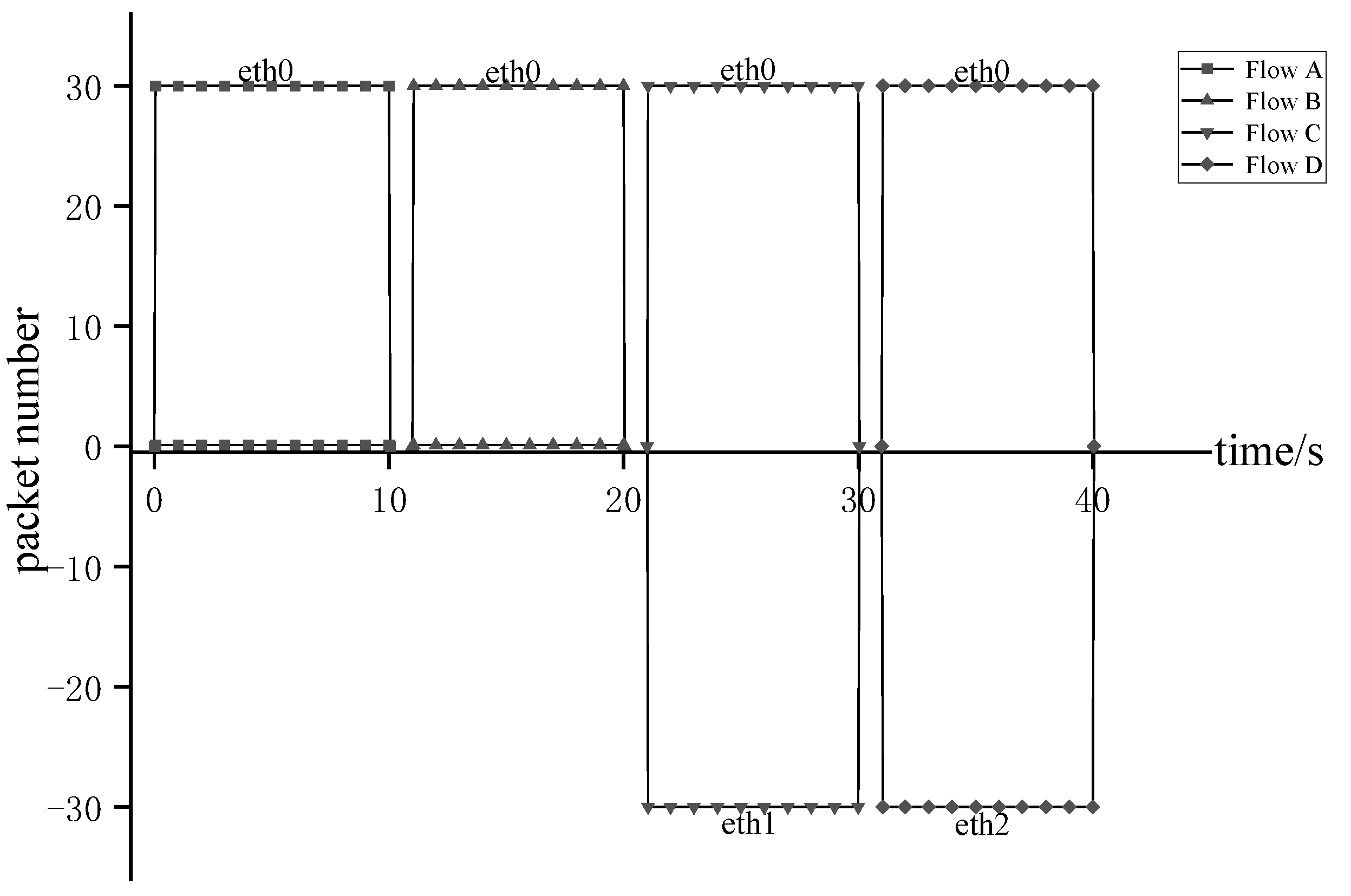
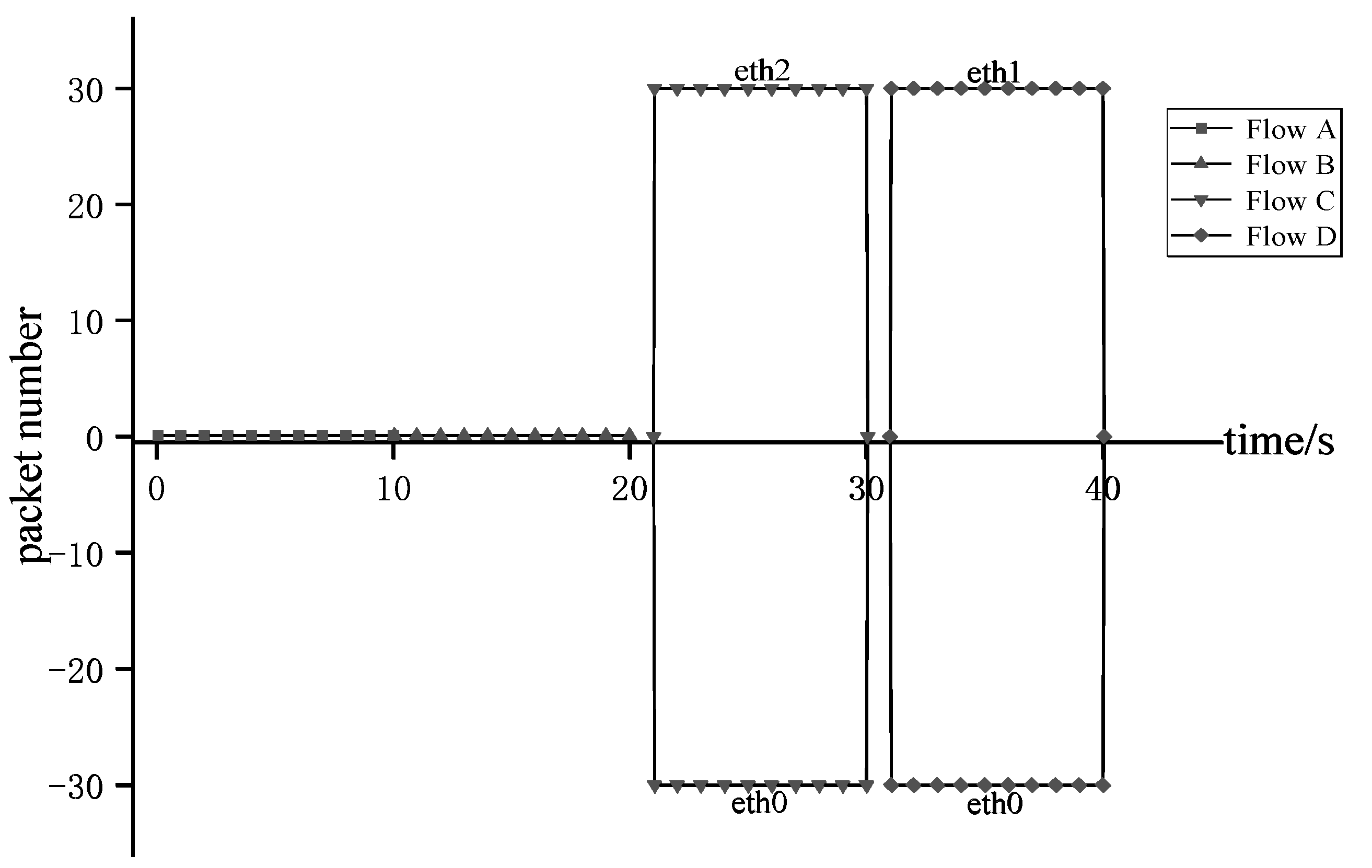



| Cycle Number | Service Type | Host Nodes | Path Length | Ordered Service Transmission Path |
|---|---|---|---|---|
| 1 | ||||
| 2 | ||||
| Scheme | Principle | Forwarding Device | Functionality | Delay Increase |
|---|---|---|---|---|
| Scheme 1 [34] | Sampling data flows at the first and last switches and checking the consistency of the message validation code | OpenFlow switch | Detecting and locating forged and tampered packets | 2.85 ms (three-layer tree structure, up to five switches) |
| Scheme 2 [35] | Sampling data flow at the entry switch and verifying the message validation code generated by the message | P4 switch | Detecting forged and tampered data packets | 0.09 ms (three switches) |
| Ours | Sampling data flow at the entry switch and verifying the matching signature | P4 switch | Ensure that matches were not tampered in the data flow forwarding process | 0.71 ms (three switches) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiao, J.; Chang, C.; Wu, P.; Ma, Y.; Lu, Z. A Secure Data Flow Forwarding Method Based on Service Ordering Management. Electronics 2022, 11, 4107. https://doi.org/10.3390/electronics11244107
Xiao J, Chang C, Wu P, Ma Y, Lu Z. A Secure Data Flow Forwarding Method Based on Service Ordering Management. Electronics. 2022; 11(24):4107. https://doi.org/10.3390/electronics11244107
Chicago/Turabian StyleXiao, Jingxu, Chaowen Chang, Ping Wu, Yingying Ma, and Zicong Lu. 2022. "A Secure Data Flow Forwarding Method Based on Service Ordering Management" Electronics 11, no. 24: 4107. https://doi.org/10.3390/electronics11244107
APA StyleXiao, J., Chang, C., Wu, P., Ma, Y., & Lu, Z. (2022). A Secure Data Flow Forwarding Method Based on Service Ordering Management. Electronics, 11(24), 4107. https://doi.org/10.3390/electronics11244107






