Abstract
A microgrid generates a large amount of power data during daily operation, which needs to be safely transferred, stored, and deleted. In this paper, we propose a secure storage and deletion verification scheme that combines blockchain and edge computing for the problems of limited storage capacity of blockchain and unverifiable data deletion. Firstly, edge computing is used to preprocess power data to reduce the amount of data and to improve the quality of data. Secondly, a hybrid encryption method that combines the improved ElGamal algorithm and the AES-256 algorithm is used to encrypt outsourcing data, and a secure storage chain is built based on the K-Raft consensus protocol to ensure the security of data in the transmission process. Finally, after initiating a data deletion request and successfully deleting the data, a deletion proof is generated and stored in the chain built, based on the Streamlet consensus protocol. The experimental results illustrate that the basic computing cost, block generation time, and communication delay of this scheme are the most efficient; the efficiency of the improved ElGamal algorithm is three times that of the traditional algorithm; the transaction throughput of the the double-layer blockchain can reach 13,000 tps at most. This scheme can realize the safe storage of microgrid data, and can also realize the efficient deletion and verification of outsourcing data.
1. Introduction
An important development direction of renewable energy technology is to promote the proportion of distributed energy system in an energy system and to improve the permeability of new energy with the maturation and perfection of distributed clean energy resource-related technology equipment [1]. As a distributed energy system, a large amount of powerful data is generated in the process of daily operation of a microgrid. However, the large amount of power data brings difficulties associated with its storage, and also brings about challenges for the operators to ensure the requirements for safe and reliable data deletion. In December 2015, the Ukrainian power grid was attacked, and the virtual private network credentials of authorized users were stolen to carry out DoS attacks, resulting in massive power outages [2]. In November 2021, DMEA of the United States was attacked by the network. This attack resulted in 90% of its internal systems being paralyzed and 25 years of historical data being lost; Denmark Vestas Wind Systems suffered network attacks, resulting in unspecified data leakage. Data leakage and other privacy related issues are now receiving more and more attention. Therefore, ways to ensure the safe storage, deletion, and verification of microgrid data have become major problems to be solved.
Satoshi Nakamoto published a proposal for a new monetary system called Bitcoin [3]. The system provides a purely digital currency that is managed by a network of unknown and untrusted nodes, with no need for a trusted third party. Its underlying support technology is blockchain. With the popularity of Bitcoin, blockchain has gradually entered the public view. Using blockchain can ensure the security of power data and can solve the verification problem. However, due to limited storage capacity, further development of blockchain has been restricted [4].
Because edge devices are closer to the data source, edge computing can process a large amount of temporary data, and therefore, can reduce overall network traffic and become an option for processing power big data [5]. However, a large amount of data will be stored in the local intelligent edge terminal which will also bring serious security risks to the data [6].
Therefore, combining edge computing with blockchain by using the powerful big data processing capability of edge computing to preprocess power big data can reduce the data scale and can improve data quality [7]. Using blockchain and using its data security, transparency, and traceability features to ensure the safety of edge devices [8], we can fully combine the advantages of both to achieve safe and efficient management of microgrid data. In the edge computing environment, a secure storage and deletion verification scheme of microgrid data based on blockchain is proposed, which can meet the scalability requirements of blockchain, and can also solve the problem that the deletion of outsourced data cannot be verified. Specifically, as compared with traditional data security storage and deletion verification schemes, the contributions of this article are elaborated as follows:
- (1)
- By integrating edge computing and blockchain, a microgrid data framework based on four-tier architecture is designed. It is an efficient and enhanced structure. The edge computing is used to preprocess power big data which can reduce data scale and improve data quality.
- (2)
- In order to effectively improve the speed of encryption and decryption and to provide more secure privacy protection, this scheme proposes a hybrid encryption method combining the improved ElGamal algorithm and the AES-256 algorithm, which has the characteristics of low computational cost, fast encryption and decryption, and good security.
- (3)
- Combining the Kademlia consensus protocol and the Raft consensus protocol, a new K-Raft consensus protocol with high throughput and high scalability is used to build a secure storage chain.
- (4)
- A deletion verification chain is constructed based on a minimalist lightweight Streamlet consensus protocol, which can greatly simplify the consensus reaching process, and therefore, reduce the delay.
- (5)
- The scheme builds a double-layer blockchain for safe storage and data deletion of microgrid data. This design further strengthens the system security.
2. Related Work
In terms of secure data storage, Fu et al. [9] designed a fog-assisted privacy-preserving cloud data storage and retrieval system for the Industrial Internet of Things (IIoT). Data users could search for encrypted data with identifiers, and could also search encrypted data based on monitored objects with certain functions, ensuring the confidentiality of the data and considering the addition and deletion of the characteristics of monitored objects, which met the requirements of scalability. However, the edge nodes were considered to be honest which was impractical, the authenticity of user equipment was ignored, and the computational overhead was difficult to evaluate. Sun et al. [10] proposed a healthcare information security storage solution based on hyperledger fabric and the attribute-based access control framework. The scheme stores medical information in the blockchain, and medical information can be protected and tamper proofed by formulating corresponding smart contracts. In addition, the solution also combines IPFS to relieve the storage pressure of the blockchain. H. Han et al. [11] proposed the double chain model, and combined off chain storage technology with data deduplication technology to optimize a blockchain storage model. Ren et al. [12] proposed a mechanism that combined blockchain and regeneration coding to improve the security and reliability of stored data under edge computing. The terminal was selected according to the remaining energy of the node, and the recovered data were repaired through regeneration coding. Therefore, the resources of each device under edge computing could be fully developed, and the waste of resources could be avoided. Nizamuddin et al. [13] proposed a blockchain-based document sharing and version control framework, which could facilitate multi-user collaboration, change and track documents in a secure and trusted environment, and could store files in the Inter Planetary File System (IPFS), and therefore, the security of documents was guaranteed. However, it adopted the traditional Proof of Work (PoW) consensus protocol, and the efficiency of data processing was low. Li et al. [14] proposed a blockchain-based Internet of Things (IoT) decentralized data storage scheme. A blockchain network was formed by adding edge nodes. The encrypted calculations and collected data from IoT devices were performed by edge nodes. In addition, certificateless cryptography technology was used to simplify the authentication process in the blockchain network. However, the computing power of the network was not considered in this scheme, and therefore, it remained to be tested in practical applications. Rui et al. [15] proposed a method to realize the distributed data storage and tamper resistance in blockchain, and improved the practical Byzantine fault tolerance (PBFT) consensus protocol to store IoT data securely.
In terms of data deletion verification, Yang et al. [16] proposed a new blockchain-based data deletion scheme, which used blockchain to ensure that any malicious deletion operation could be verified, and therefore, the deletion operation was more transparent. A special timestamp server was used as the trusted authority to provide the necessary information to the cloud sever for making data deletion proof. The existing threat model assumed that the semi-honest server was part of its analysis, but it could not resist the clock step which attacked against the protocol. Yu et al. [17] proposed a scheme to realize outsourced data access control by using attribute-based encryption, and deleted the data through interactive verification. However, this scheme could not carry out public verification and responsibility tracking, and the cost of the scheme based on bilinear construction was relatively high. Xue et al. [18] proposed a secure deletion scheme that supported fine-grained access control. Using key policy attribute-based encryption technology to encrypt data realized the secure deletion of cloud data, but the calculation cost was high and a trusted third-party was required to generate a re-encryption key, therefore, its security was difficult to be guaranteed. Cheng et al. [19] proposed a new modifiable blockchain structure based on Lagrange interpolation to make up for the defects of most existing hash-based blockchain, which could support the modification of records and data blocks. The data segments were organized by the Lagrange interpolation method in each block, and the polynomial function was used to maintain the order of blocks. The polynomial-based blockchain structure realized the purpose of modification, and also supported the differential control strategy of modification difficulty. Yang et al. [20] proposed a cloud storage data deletion verifiable scheme supporting efficient tracking. The Merkle Tree was used to realize public verification in outsourced data deletion without any trusted third-party. At the same time, this scheme realized effective data leakage source tracking to prevent data owners and cloud servers from repudiating each other.
To sum up, whether it is the secure storage of data or deletion verification, although the research on it is very extensive, there are still some problems more or less. These problems are mainly reflected in the limited storage capacity, high computational cost, excessive reliance on trusted third-parties, centralized storage, and inefficient data processing. Therefore, in view of the above problems, a secure storage and deletion verification scheme of microgrid data based on blockchain is designed within an edge computing environment, which can realize the distributed secure storage of data, and can also ensure the efficiency of data processing and support the deletion verification of data.
3. Scheme Framework
The scheme is mainly composed of microgrid nodes, edge servers, cloud servers, and blockchains. Therefore, it can be divided into four layers, which are the data layer, the edge layer, the storage layer, and the consensus layer. The overall architecture of the scheme is shown in Figure 1, and the specific functions of each part are as follows:
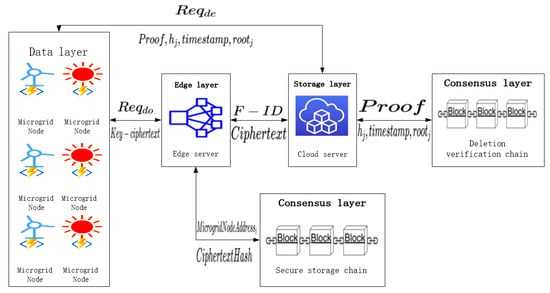
Figure 1.
Scheme framework.
- (1)
- The microgrid nodes are included in the data layer, which is the source of data generation. It mainly completes the collection and upload of data, and can also generate some data requests and verify responses.
- (2)
- The edge layer is mainly composed of edge servers, which can process big data generated by microgrid nodes, upload the processed data to the cloud server for storage, and can maintain the normal operation of the secure storage chain.
- (3)
- The storage layer is mainly composed of cloud servers, which are responsible for storing the microgrid data processed by the edge server, responding to some data requests generated by the microgrid nodes, and maintaining the normal operation of the deletion verification chain.
- (4)
- Two blockchains are included in the consensus layer, which are secure storage chain and deletion verification chain. The former is responsible for receiving and storing valid information uploaded from the edge server, and the latter is responsible for receiving and storing the deletion proof generated by the cloud server.
In this scheme, first, the power big data generated during the operation of microgrid nodes are uploaded to the edge server for preprocessing, to reduce the data scale and to improve the data quality. Secondly, the processed data are encrypted by the edge server, and the encrypted data packet is uploaded to the cloud server for storage. The hash value of the encrypted data, timestamp, and the information of microgrid node are uploaded to the secure storage chain for storage. Then, when the data are needed, it can send a data download request to the edge server. After the verification is passed by the edge server, it returns the ciphertext to the microgrid node, and then the ciphertext can be decrypted to obtain the required data. Finally, when the microgrid node no longer needs the data, it can directly send a data deletion request to the cloud server. After the verification is passed by the cloud server, it deletes the data and generates a deletion proof, and then uploads the deletion proof to the deletion verification chain for storage. At the same time, it returns the deletion proof to the microgrid node for verification.
4. Scheme Design
The blockchain can be divided into a public chain, a consortium chain, and a private chain, according to its degree of decentralization [21]. When the blockchain is applied to the microgrid, each node needs to be authorized to join or exit. Otherwise, the excessively open system allows each node to join or exit freely, which can create chaos in the system and can make management of the system more difficult. Thus, it is more appropriate to choose the consortium chain to build the system.
In view of the problems of difficult key management and distribution and low security when using a symmetric encryption algorithm alone [22], or the problems of long time-consuming, slow speed, and only suitable for a small amount of data encrypted when using asymmetric encryption algorithm alone [23], a hybrid encryption and decryption method that combines a symmetric encryption algorithm and an asymmetric encryption algorithm is adopted in this scheme. That is, when encrypting, the symmetric encryption algorithm is used to encrypt the plaintext so as to obtain the ciphertext, and then the public key of the asymmetric encryption algorithm is used to encrypt the key of the symmetric encryption algorithm to obtain the encrypted key ciphertext. When decrypting, the private key of the asymmetric encryption algorithm is used to decrypt the key ciphertext to obtain the key of the symmetric encryption algorithm, and then the key of the symmetric encryption algorithm is used to decrypt the ciphertext to obtain the plaintext. As compared with the symmetric encryption algorithm, the encryption and decryption of the asymmetric encryption algorithm take longer. Therefore, the traditional AES-256 algorithm is selected for the symmetric encryption algorithm, and an improved ElGamal algorithm is selected for the asymmetric encryption algorithm. This scheme combines the advantages of small computation and fast encryption speed of the symmetric encryption algorithm with the advantages of high security of an asymmetric encryption algorithm, and avoids the disadvantages of both.
4.1. Secure Storage
First of all, each microgrid node needs a unique account before storage, that is , which has been verified by the edge server and the cloud server. Secondly, each edge server has an identity , and each cloud server also has an identity . Then, the cloud server has a key pair of ElGamal, the edge server has the key of AES and the public key of ElGamal, and the microgrid node has the private key of ElGamal. Finally, each data file uploaded by a microgrid node also has an identity . The secure storage process is shown in Figure 2, and the specific process is as follows:
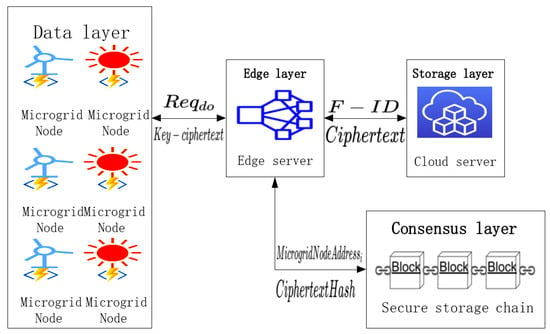
Figure 2.
Process of secure storage.
- (1)
- :
- The security parameters , , and are entered in this scheme, where is a sufficiently large prime number, is the primitive root of , and , is a positive integer, while also ensuring that .
- The exponent is -aryized, and is used as the private key of the improved ElGamal algorithm, and its public key is calculated by Equation (1):
- (2)
- :
- The recent transaction data are uploaded to the edge server, and then preprocessed to reduce the data size and improve the data quality by the microgrid node.
- The AES-256 algorithm is used to encrypt the preprocessed big data to obtain the ciphertext by the edge server, where is the plaintext.
- The public key of ElGamal is used to encrypt the key of AES to obtain the key ciphertext by the edge server. The specific encryption process is as follows:
① The plaintext is grouped, and its packet length is less than bits.
② An integer is selected randomly, and , and the ciphertext pair is calculated using Equation (2). The size of the ciphertext is twice that of the plaintext.
An improved ElGamal encryption algorithm is adopted in this scheme when encrypting data. The traditional encryption algorithm performs multiple iterations in the calculation process because the exponent sequence is too long. Using power residual calculations takes too much time, which causes the algorithm to operate inefficiently. The improved algorithm reduces the length of the exponential sequence by -ary of the index, and therefore reduces the number of iterations and improves the running speed [24]. The process of exponential -ary is defined as the function BR (), and the pseudo code of this function is shown in Algorithm 1.
| Algorithm 1: Function BR() | |
| Input: | |
| Output: | |
| 1 | |
| 2 | for to do |
| 3 | |
| 4 | |
| 5 | end for |
| 6 | return |
This process only needs to perform iterations, and store the result in a table. The table is only needed to be created once. When calculating the modulo operation of encryption and decryption, the result can be obtained by looking up the table.
- 4.
- The hash value of the ciphertext is calculated, and then the hash function is used to calculate the label .
- 5.
- The ciphertext is uploaded to the cloud server for storage. The key ciphertext is stored in the local edge server. The tag , the hash value of the ciphertext , the timestamp, and the microgrid account information are uploaded to the secure storage chain for storage.
For the storage process of data in the chain, in view of the problems of low throughput, poor scalability, and poor parallel performance in the traditional consensus protocol used in the blockchain consensus stage [25], a new and efficient K-Raft consensus protocol is adopted in this scheme to make each node in the blockchain network reach a consensus. The K-Raft consensus protocol is a Raft-like consensus protocol that retains part of the logic of the Raft consensus protocol. It optimizes the leader node election and the consensus process of the Raft consensus protocol through the K-Bucket node relationship in the Kademlia protocol, and improves the node election speed and throughput.
In the process of leader node election, the internal nodes of K-bucket are maintained through the Kademlia protocol on the network layer by K-Raft dynamically. The value of can be updated through messages . The “timeout, request voting” process of Raft is converted into the “timeout, identification” process in K-Raft. When the candidate node finds that the leader node has collapsed, it will generate a random number according to the current timestamp. The timestamp ensures that the earlier the candidate node finds the leader node has collapsed, the more likely it is to be elected as the leader node. The two main points of the leader node election are the correctness and optimality of candidate nodes [26]. In order to ensure the optimality and correctness of candidate nodes, the priority is set for the replication of candidate nodes in the table during the log replication process. is a flag indicating that all candidate nodes have completed the log replication process. indicates that all candidate nodes have completed log replication, and indicates that the candidate has not completed log replication. The election of leader node is the process of obtaining the approval of the majority of nodes in the table [27]. When the leader node receives the appendix response message, more than half of the nodes, a consensus, has been reached, and the transaction is written into the blockchain by the leader node. The pseudo code of the leader node election process is shown in Algorithm 2.
| Algorithm 2: Leader Election | |
| Input: Leader crash | |
| Output: New leader and its table | |
| 1 | if then |
| 2 | |
| 3 | else |
| 4 | |
| 5 | |
| 6 | |
| 7 | |
| 8 | |
| 9 | end if |
| 10 | return |
- (3)
- After the data are uploaded and stored, the local data can be deleted by the microgrid node. When it needs the data again, it can first generate a data download request , and then send it to the edge server. The edge server responds according to the download request and returns the ciphertext. The ciphertext is decrypted by the microgrid node to obtain the required data. The specific process of data download is as follows:
- The microgrid node first calculates its file label according to the identity of the data file to be downloaded, then uses the private key to calculate the digital signature of the data file , and finally generates a download request composed of file label, digital signature, edge server identity, timestamp, and microgrid node account information and sends it to the edge server.
- The public key is used to verify the digital signature , and then the data download request submitted by the microgrid node is used to query and verify the microgrid account information on the secure storage chain by the edge server. If the digital signature, account information, edge server identity, and timestamp are all verified, then look up the hash of the ciphertext and return it to the edge server. Otherwise, an error is returned for it.
- First, the edge server uses the file label to search for the ciphertext in the cloud server, then calculates its hash value , and compares it with the ciphertext hash value returned from the secure storage chain. If they are the same, the edge server uses the ciphertext hash value to search the key ciphertext in the edge server and returns the ciphertext and the key ciphertext to the microgrid node. Otherwise, a data destruction warning is returned to the microgrid node.
- After receiving the valid information returned by the edge server, the ciphertext is decrypted to obtain the required plaintext by the microgrid node. The specific decryption process is as follows:
① First, Equation (3) is used to decrypt the key ciphertext to obtain the key :
② Then, the key is used to decrypt the ciphertext to obtain the required data plaintext.
4.2. Deletion Verification
When the microgrid node no longer needs the data stored in the cloud server, it directly sends a data deletion request to the cloud server. After the verification is passed by the cloud server, it deletes the data and generates a deletion proof, and then uploads the deletion proof to the deletion verification chain for storage. At the same time, the deletion proof is returned to the microgrid node for verification. The deletion verification process is shown in Figure 3, and the specific process is as follows:
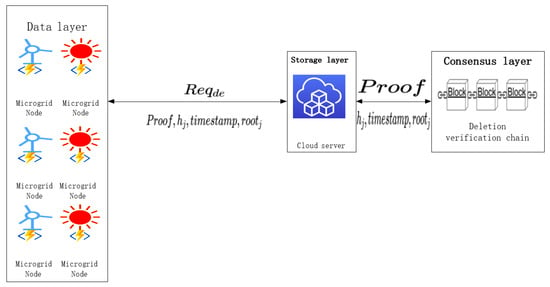
Figure 3.
Process of secure storage.
- (1)
- The microgrid node first calculates its file label according to the identity of the data file to be deleted, then uses the private key to calculate the digital signature of the data file , and finally generates a deletion request and sends it to the cloud server.
- (2)
- After receiving the data deletion request sent by the microgrid node, the cloud server parses it and uses the public key to verify the digital signature . If the digital signature, cloud server identity, and timestamp are verified, the cloud server deletes the requested data file. If not, an error will be returned for the microgrid node.
After the cloud server deletes the data file, it will first generate a deletion proof, and then return it to the microgrid node for verification. The specific process of generating the deletion proof is as follows:
- (1)
- The cloud server first uses the data file identity obtained by parsing to calculate its file label , then uses the private key to calculate the digital signature of the data file , and finally generates a deletion proof .
- (2)
- The cloud server first uses the Merkle Tree structure to hash the transaction (deletion proof ) until its Merkle Root is obtained, and then calculates the hash value of the current block , where is the hash value of the previous block and is the Merkle Root of the current block. Finally, the deletion proof, the current block hash value, the timestamp, and the Merkle Root are returned to the microgrid node for verification. If a consensus can be reached on the current block by the cloud server nodes, this block can be linked to the deletion verification chain. The structure of the deletion verification chain is shown in Figure 4.
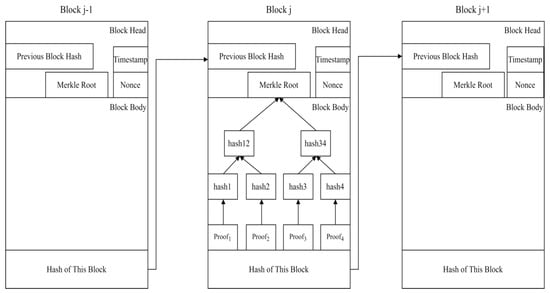 Figure 4. Structure of the deletion verification chain.
Figure 4. Structure of the deletion verification chain.
In the process of reaching consensus of each node in the verification chain, a minimalist and lightweight Streamlet consensus protocol is used in this scheme. The Streamlet follows the fault-tolerant rule of the traditional BFT protocol, that is, in a network with nodes, it can tolerate up to Byzantine nodes, which needs to meet [28]. In Streamlet, the operation of the protocol is divided into multiple synchronous block generation cycle epochs (each epoch lasts for 1 s), and each epoch is randomly assigned a leading node by the hash algorithm. Each leader node publishes a block in its own epoch for other nodes to vote on. Voting can be seen as the voter signing the block hash with their private key and broadcasting it to all other nodes. A block is considered to be a notarized block if it receives votes from more than two thirds of different nodes. A chain composed of notarized blocks is called a notary chain. An example of the consensus protocol reaching consensus is shown in Figure 5, and the specific process is as follows:
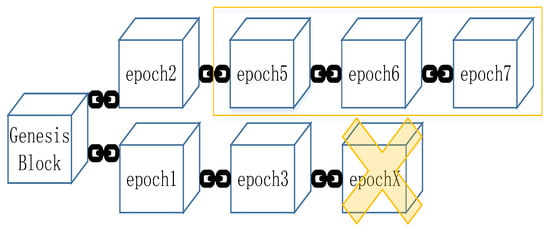
Figure 5.
Example of Streamlet consensus protocol.
① Propose Each leader node publishes new blocks based on the longest local notary chain, that is, the hash value of the previous block in the new block points to the block at the end of the local longest notary chain.
② Vote Other nodes only vote for the first block published by the current leader node, and the block must be extended from the local longest notary chain, that is, the hash value of the previous block in the block must point to the block at the end of the longest voter’s local notarization chain.
③ Confirm When a block is confirmed in the blockchain, it means that all honest nodes in the network have reached consensus on the block and will not modify the consensus result. Notarized blocks do not necessarily end up being confirmed. In a notarization chain, when there are three consecutive notarization blocks each with an epoch number, the first two blocks and all previous blocks on the same chain are confirmed. For example, in the example of Figure 5, epochs 5, 6, and 7 have successively generated three notarized blocks, so when block 7 becomes a notarized block, blocks 5 and 6 and the previous block 2 are all confirmed.
After receiving the valid information returned by the cloud server, the microgrid node can verify it. Take as an example to illustrate the specific verification process as follows:
- (1)
- The microgrid node first calculates according to the deletion proof returned by the cloud server. If , the microgrid node continues to use Equations (4)–(7) for verification until the Merkle Root is traversed.
- (2)
- The microgrid node uses Equations (8)–(11) to verify the hash value of the block.
⋯⋯
where is the hash of the latest block. Only when all verifications are successful can the microgrid nodes trust that the cloud server has actually deleted the corresponding data files according to its requirements.
5. Security Analysis
5.1. Blockchain Security
In the secure storage chain, the security of K-Raft is reflected in election security, leader node security, and state machine security.
- (1)
- For election security, the logic of log replication and its completion flags are optimized to ensure high quality keys and values for the logs in the table by the K-Raft. The election of the K-Raft leader node is randomly selected by the nodes in the table. In K-Raft, appendix messages are preserved, and the leader node’s log can be sent to other nodes through appendix messages. Therefore, the election of the leader node is secure.
- (2)
- For leader node security, the security of leader nodes is mainly reflected in two aspects, the integrity of leader nodes and the addition of appendices only to leader nodes. The election of the K-Raft leader node and log replication process ensures that logs submitted to the blockchain must appear in the leader node. Once a transaction is confirmed, it is permanently stored in the blockchain. Therefore, the leader node is secure.
- (3)
- For state machine security, by combining the usage scenarios of the blockchain, the premise of 51% of the state machine submission is preserved, and K-Raft transforms the submission state machine process into a process in which the leader node writes transactions into the blockchain. Therefore, the state machine is security.
In the deletion verification chain, the security of the Streamlet protocol can be expressed, as there are no two different blocks with the same height to be confirmed. Proof of contradictory is used to prove that the problem is not established. Assuming that there is a notarial block , there are only two possibilities, that is, or , because it is impossible for the same epoch to produce two notarial blocks. The following is a case by case discussion:
- (1)
- For, since the block is a notarized block, which means that more than 2/3 of the nodes vote for the block , it can be further inferred that more than 2/3 of the nodes already have notarized block 3 locally at the time of voting. Therefore, when the protocol runs to epoch 5, it is impossible for enough nodes to vote for block 5. This is due to the limitation of voting rules, and honest nodes only vote for blocks on the longest notarized chain. Therefore, this contradicts the assumption that block 5 is a notarized block.
- (2)
- For, since block 7 is a notarized block, which means that more than 2/3 of the nodes vote to block 7, it can be further speculated that more than 2/3 of the nodes already have certified block 6 locally when voting to block 7. Therefore, when the protocol runs to epoch , due to the restrictions of voting rules, the block cannot become a certified block, which is contrary to the assumption.
5.2. Data Security
- (1)
- Regarding an eavesdropping attack, since various requests and responses in this scheme have been processed by symmetric encryption algorithm AES, asymmetric encryption algorithm ElGamal and hash function, if a malicious attacker launches an eavesdropping attack on the communication channel and obtains various requests and responses, these requests and responses are meaningless to him because he cannot obtain the key. Therefore, an eavesdropping attack is invalid for this scheme.
- (2)
- Regarding a sybil attack, in this scheme, each microgrid node, the edge server, and the cloud server have their own unique account information or identity. Only after passing various identity authentications as honest nodes can they join the consortium chain system. Various requests will be verified in the process of system operation, and the system will respond only after passing the verification. Therefore, the scheme can effectively prevent a sybil attack.
- (3)
- Regarding a tampering attack, since the attacker cannot crack the key, if there is a malicious attacker tampering with the transaction, it will be verified when the transaction is submitted to the edge server or cloud sever. The tampered transaction cannot pass the verification, and the transaction is invalid and will be discarded by the system. Therefore, a tampering attack is invalid for this scheme.
- (4)
- Regarding a distributed denial of service (DDoS) attack, since this scheme uses the combination of a symmetric encryption algorithm and an asymmetric encryption algorithm to encrypt data and keys, it is very difficult to infect a node. In addition, the blockchain system is a distributed structure, and even if a node fails, it will not affect the normal work of other nodes [29]. Therefore, this scheme can effectively prevent a DDoS attack.
- (5)
- Regarding a replay attack, in this scheme, since each transaction is added with a timestamp, if a malicious attacker launches a replay attack by using an expired transaction, both the edge server and the cloud server can judge whether the transaction is expired by verifying the timestamp. Therefore, a replay attack is invalid for this scheme.
6. Performance Evaluation
In order to further verify the performance of the scheme, a series of experiments are designed to test the basic computing overhead, communication delay, algorithm efficiency, block generation time, and throughput of the scheme, which can be divided into five experiments. By testing the performance of this scheme in five experiments and comparing it with other schemes, the performance of this scheme can be observed in detail.
6.1. Experimental Deployment
The hardware configuration of the experimental test environment is an Intel Core i5-8250U, 2.50 GHz CPU, 8 GB memory and the Ubuntu 20.04.1 LTS operating system. In order to reduce the influence of unstable factors on the experiment, 20 measurements are carried out for each selected data sample, and then the average value is taken as the index data under the sample.
6.2. Evaluation Results
6.2.1. Basic Computing Cost
The basic operations of the scheme can be divided into four steps, which are encryption, decryption, deletion, and verification. Therefore, the time cost of the four steps can be observed by changing the size of the data file or the number of blocks , to understand the computational cost of the scheme. The comparison schemes of this experiment are selected from the blockchain-based cloud storage publicly verifiable data deletion scheme in Yang’s scheme [16], the fog-based industrial application data fine-grained access control and deletion scheme in Yu’s scheme [17], the high-efficiency data deletion scheme with attribute revocation based on attribute-based encryption in Xue’s scheme [18], and the new publicly verifiable data deletion scheme that supports efficient tracking of cloud storage in Yang’s scheme [20]. The experimental results of basic computing overhead are shown in Figure 6.
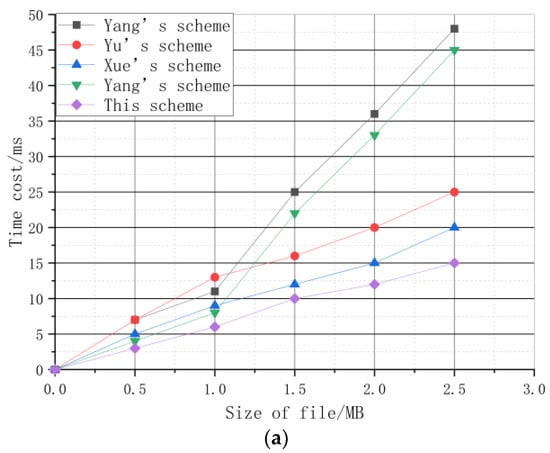
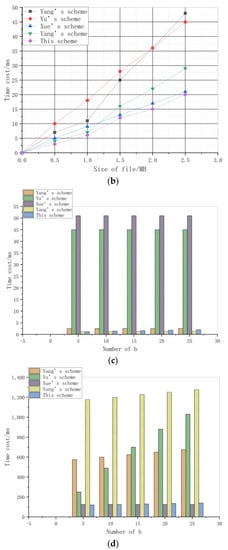
Figure 6.
Experimental results of basic computing overhead: (a) Time cost of encryption; (b) time cost of decryption; (c) time cost of deletion; (d) time cost of verification.
It can be found from Figure 6a that the encryption time of all schemes increases with an increase in data file size. Among them, when the data file size is 2 MB, the encryption time of this scheme is only 12 ms, which is the least as compared with other schemes, and it is also acceptable in practical applications.
As can be seen from the Figure 6b, similar to the encryption time, the decryption time of all schemes also increases with an increase in the size of the data file. Among these schemes, the schemes proposed in Yang’s scheme [16], Yu’s scheme [17], and Yang’s scheme [20] have faster growth rates, and the decryption time of the scheme proposed in Xue’s scheme [18] is relatively close to that of this scheme, but the overall time consumption of the latter is still less than that of the former. This is because this scheme adopts a highly efficient symmetric encryption algorithm when encrypting plaintext, and in order to ensure the security of the transmission process, an improved asymmetric encryption algorithm is used for the encryption of symmetric keys, The efficiency is greatly improved as compared with other schemes.
According to the data in Figure 6c, it can be found that the deletion time of the scheme proposed in Yu’s scheme [17] and Xue’s scheme [18] is much longer than that of other schemes, and the deletion time of the scheme proposed in Yang’s scheme [16] remains unchanged with a change in the number of deleted files, because it only needs to calculate and to verify one signature at this stage, and the deletion time of the scheme proposed in Yang’s scheme [20] increases with an increase, but the change range is small. This is because at this stage, it needs to calculate three signatures and verify one signature. In addition, it also needs to calculate hash value to update the Merkle tree. The deletion time of this scheme is similar to that of the scheme proposed in Yang’s scheme [20], but it has one more signature operation, so its efficiency is slightly lower than that of the scheme proposed in Yang’s scheme [20], but it is also within the acceptable range.
Finally, Figure 6d shows that the verification time of the schemes proposed in Yang’s scheme [16], Yu’s scheme [17], and Yang’s scheme [20] is far more than that of other schemes. The verification time of the schemes proposed in Xue’s scheme [18] remains unchanged for 125 ms no matter how the value changes. However, the verification time of this scheme is similar to the deletion time, and its verification time increases with an increase, but the change range is small. This is also because it consists of fixed and variable computing costs at this stage, The latter is mainly to calculate a hash value to reconstruct the Merkle tree. Therefore, its efficiency is not much different from that proposed in Xue’s scheme [18], which is acceptable.
6.2.2. Communication Delay
The change of communication delay is observed by changing the size of the files in the experiment. The choice of the experimental comparison scheme is the same as that of the basic computing overhead experiment. The experimental results of communication delay are shown in Figure 7.
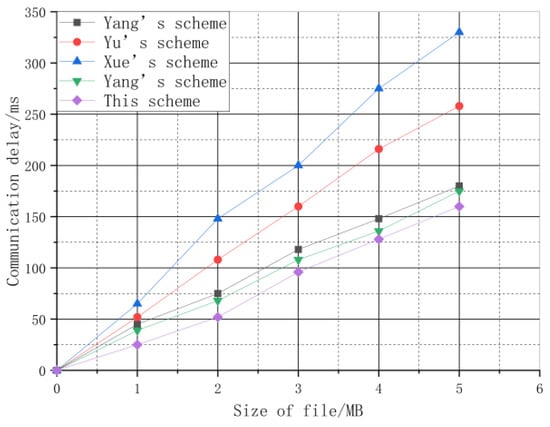
Figure 7.
Experimental results of communication delay.
The communication delay of all schemes is increased with an increase in the size of files. Where the performance of the scheme in Xue’s scheme [18] is the most unsatisfactory, the highest is over 300 ms, followed by the scheme proposed in Yu’s scheme [17]; the highest performance is over 250 ms. The performances of the schemes proposed in Yang’s scheme [16] and Yang’s scheme [20] are relatively close, but the performance of this scheme is best, the highest is only over 150 ms. As compared with other schemes, this scheme not only has fewer operations and lower computational complexity, but also edge computing is used to preprocess big data, which can greatly compress the size of data and reduce the communication delay. The traditional centralized data storage method is adopted in the scheme proposed in Xue’s scheme [18], while the scheme proposed in Yu’s scheme [17] has more advantages in processing data due to the use of fog computing. Consequently, the performance of the latter is better than that of the former. blockchain is be used to realize distributed storage of data in the scheme proposed in Yang’s scheme [16], so its performance is better than those proposed in Yu’s scheme [17] and Xue’s scheme [18].
6.2.3. Algorithm Efficiency
The experiment uses the number of iterations and the ratio of the number of iterations of the improved algorithm to the number of iterations of the traditional algorithm to measure the running efficiency of the algorithm. Since the operation efficiency is affected by the binary sequence length of the exponential of the algorithm, the efficiency of operation of the algorithm can be understood by changing the sequence length and observing the changes in the number of iterations and their ratios. The experimental results of the algorithm efficiency are shown in Figure 8.
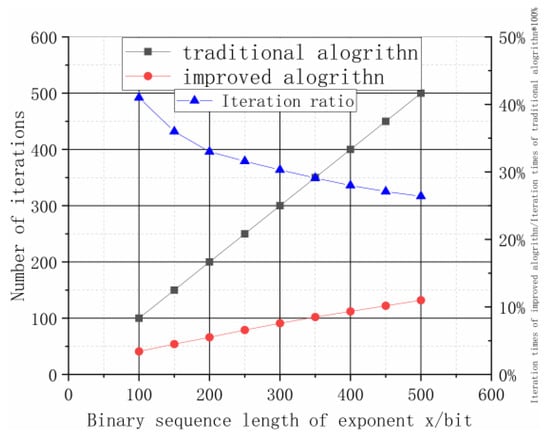
Figure 8.
Experimental results of algorithm efficiency.
When the binary sequence length of index is more than 100 bits, the iteration time curve of the traditional algorithm increases rapidly, while the iteration time curve of the improved algorithm increases slowly. The maximum ratio of the iteration times between the improved algorithm and the traditional algorithm is less than 50%. The efficiency of the improved algorithm is three times higher than that of the traditional algorithm. In addition, with an increase in sequence length, the ratio curve of iteration times shows a downward trend, and the gap between the two iteration time curves becomes larger and larger, indicating that the longer the sequence length, the better the effect of the improved algorithm, and the higher the operating efficiency as compared with the traditional algorithm.
6.2.4. Block Generation Time
In this experiment, the block size is set to 1 MB. Under this condition, by changing the number of blocks and observing the change of block generation time, the block generation speed of different schemes can be directly reflected. For the selection of comparable schemes, the data secure storage scheme based on blockchain and coding technology in edge computing in Ren’s scheme [12], the decentralized document version control scheme using Ethereum blockchain and IPFS in Nizamuddin’s scheme [13], the blockchain-based large-scale IoT data storage and protection scheme in Li’s scheme [14], and the blockchain-based energy IoT information security transmission and storage scheme in Rui’s scheme [15] are selected by the secure storage chain. The blockchain-based cloud storage public verifiable data deletion scheme in Yang’s scheme [16] and the polynomial-based modifiable blockchain structure for eliminating fraudulent transactions in Cheng’s scheme [19] are selected by the deletion verification chain. The experimental results of the block generation time are shown in Figure 9.
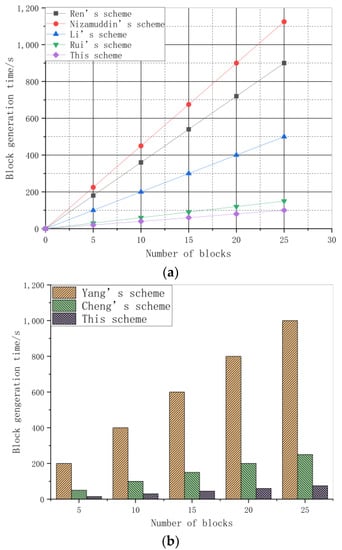
Figure 9.
Experimental results of block generation time: (a) Secure storage chain; (b) deletion verification chain.
Whether it is a secure storage chain or a deletion verification chain, the block generation time is increased with an increase in the number of blocks. This is because, when the number of nodes remains the same, the block generation time is also increased with the increasing number of packaged blocks. In the secure storage chain, the performance of the scheme in Nizamuddin’s scheme [13] is the least ideal, followed by the scheme in Ren’s scheme [12], and then the scheme in Li’s scheme [14]. The performance of the scheme in Rui’s scheme [15] is similar to this scheme, but on the whole, this scheme is performed better than that in Rui’s scheme [15]. This is because, although blockchain and IPFS are also used to realize the distributed storage of data in Nizamuddin’s scheme [13], the traditional Ethereum platform is still used to build the blockchain structure. Edge computing is introduced on the basis of traditional architecture in Ren’s scheme [12], which is more efficient in processing big data. The traditional PoW consensus protocol is improved on the basis of introducing edge computing in Li’s scheme [14], a Proof of Useful Work (PoUW) consensus protocol is introduced, which can greatly improve the data processing efficiency as compared with the traditional PoW consensus protocol. An improved PBFT consensus protocol is adopted in Rui’s scheme [15], which can greatly improve the data processing efficiency. On the basis of introducing edge computing, the K-Raft consensus protocol, a product of the integration of Kademlia protocol and Raft consensus protocol, also has a slight improvement in performance as compared with the scheme in Rui’s scheme [15]. In the deletion verification chain, the scheme in Yang’s scheme [16] performs the least ideal, followed by the scheme in Cheng’s scheme [19], and this scheme performs the best. This is because the scheme in Yang’s scheme [16] does not make any improvement on the blockchain structure, while a polynomial-based blockchain structure by using the Lagrange interpolation method is proposed in Cheng’s scheme [19], which can greatly improve the block generation speed, while a minimalist lightweight Streamlet consensus protocol is adopted in this scheme, which can simplify the process of block package and greatly improve the block generation speed.
6.2.5. Throughput
The transaction throughput of a blockchain refers to the number of transactions completed per unit time, which is one of the typical evaluation indicators of a blockchain [30]. In this experiment, the block size is set to 1 MB, and the change of throughput is observed by changing the block generation time. The selection of comparable scheme is the same as that of block generation time experiment. The experimental results of the throughput are shown in Figure 10.
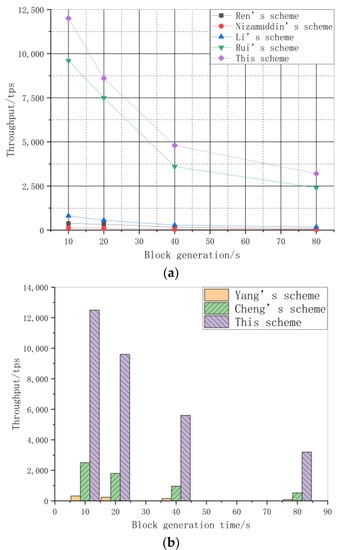
Figure 10.
Experimental results of throughput: (a) Secure storage chain; (b) deletion verification chain.
The throughput of all schemes is decreased with an increase in block generation time, because an increase in block generation time means that the number of transactions processed by the blockchain decreases at the same time. In a secure storage chain, the throughputs of the schemes in [12,13,14] basically fluctuate below 1000 tps, and the throughput of the scheme in Rui’s scheme [15] fluctuates within the interval (2000, 10,000), while the performance of this scheme is the best, and its throughput fluctuates within the interval (2500, 12,500), up to 12,500 tps. This is because the schemes in [12,13] have not changed the consensus protocol, which is the decisive factor affecting the throughput. The scheme in Li’s scheme [14] has only made some improvements on the basis of the traditional PoW consensus protocol. An improved PBFT consensus protocol is adopted in Rui’s scheme [15], and its throughput has been greatly improved. Edge computing is used to improve data processing efficiency, and also a more efficient K-Raft consensus protocol as compared with PBFT which is adopted in this scheme. In the deletion verification chain, the throughput of the scheme in Yang’s scheme [16] basically fluctuates below 1000 tps, and the throughput of the scheme in Cheng’s scheme [19] fluctuates within the interval (500, 3000). While the performance of this scheme is the best, its throughput fluctuates within the range (3000, 13,000), and the highest can be close to 13,000 tps. This is because the scheme in Yang’s scheme [16] does not make any improvement on the blockchain structure, and a polynomial-based blockchain structure is proposed by using the Lagrange interpolation method in Cheng’s scheme [19], while a minimalist lightweight Streamlet consensus protocol is adopted in this scheme, which can simplify the consensus reaching process and greatly improve the throughput.
7. Conclusions
Aiming at the problems of limited capacity of storage of traditional data storage schemes, low data processing efficiency, over reliance on trusted third parties, and inability to verify data deletion schemes, a secure storage and deletion verification scheme of microgrid data based on integrating blockchain into edge computing is proposed. The hybrid encryption method that combines symmetric encryption and asymmetric encryption are adopted to ensure the security of data transmission and storage process. At the same time, the K-Raft and Streamlet consensus protocols are used to build a secure storage chain and deletion verification chain, respectively, which can realize the distributed storage and deletion verification of data, and can provide a new idea for improving the current secure storage and deletion verification scheme of data.
Author Contributions
Conceptualization, L.Z.; methodology, L.Z.; software, C.L.; investigation, L.Z.; resources, L.Z.; data curation, C.L.; writing—original draft preparation, C.L.; writing—review and editing, L.Z., C.L., B.L. and H.F.; supervision, L.Z. and J.G.; project administration, L.Z. and J.G.; funding acquisition, L.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Key Of National Natural Science Foundation of China (grant number U21A20463) and the National Natural Science Foundation of China (grant numbers 62261023 and 72262014).
Data Availability Statement
Some or all data, models, or code generated or used during the study are available from the corresponding author by request.
Acknowledgments
The authors would like to acknowledge the East China Jiaotong University for the lab facilities and necessary technical support.
Conflicts of Interest
All authors have no known or potential competing financial interest or personal relationships that could have appeared to influence the work reported in this paper.
References
- Ali, F.S.; Bouachir, O.; Ozkasap, O.; Aloqaily, M. SynergyChain: Blockchain-Assisted Adaptive Cyber- Physical P2P Energy Trading. IEEE Trans. Ind. Inform. 2020, 17, 5769–5778. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine Blackout: Implications for False Data Injection Attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: http://www.bitcoin.org/bitcoin.pdf (accessed on 1 January 2008).
- Qi, Y.; Hossain, M.S.; Nie, J.; Li, X. Privacy-preserving blockchain-based federated learning for traffic flow prediction. Future Gener. Comput. Syst. 2020, 117, 328–337. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, J.; Zhan, J. Privacy protection for fog computing and the internet of things data based on blockchain. Clust. Comput. 2020, 24, 1331–1345. [Google Scholar] [CrossRef]
- Jiang, W.; Li, H.; Xu, G.; Wen, M.; Dong, G.; Lin, X. PTAS: Privacy-preserving thin-client authentication scheme in blockchain-based PKI. Future Gener. Comput. Syst. 2019, 96, 185–195. [Google Scholar] [CrossRef]
- Bonnah, E.; Shiguang, J. DecChain: A decentralized security approach in Edge Computing based on Blockchain. Future Gener. Comput. Syst. 2020, 113, 363–379. [Google Scholar] [CrossRef]
- Peng, S.; Hu, X.; Zhang, J.; Xie, X.; Long, C.; Tian, Z.; Jiang, H. An efficient double-layer blockchain method for vaccine production supervision. IEEE Trans. NanoBiosci. 2020, 19, 579–587. [Google Scholar] [CrossRef]
- Fu, J.S.; Liu, Y.; Chao, H.C.; Bhargava, B.K.; Zhang, Z.J. Secure data storage and searching for industrial IoT by integrating fog computing and cloud computing. IEEE Trans. Ind. Inform. 2018, 14, 4519–4528. [Google Scholar] [CrossRef]
- Sun, Z.; Han, D.; Li, D.; Wang, X.; Chang, C.-C.; Wu, Z. A blockchain-based secure storage scheme for medical information. Eur. J. Wirel. Commun. Netw. 2022, 2022, 40. [Google Scholar] [CrossRef]
- Han, H.; Wan, W.; Zhang, J.; Qin, Z.; Qiu, X.; Zhang, S.; Xia, J. A scalable double-chain storage module for blockchain. Comput. Mater. Contin. 2022, 73, 2651–2662. [Google Scholar] [CrossRef]
- Ren, Y.; Leng, Y.; Cheng, Y.; Wang, J. Secure data storage based on blockchain and coding in edge computing. Math. Biosci. Eng. 2019, 16, 1874–1892. [Google Scholar] [CrossRef] [PubMed]
- Nizamuddin, N.; Salah, K.; Azad, M.A.; Arshad, J.; Rehman, M. Decentralized document version control using ethereum blockchain and IPFS. Comput. Electr. Eng. 2019, 76, 183–197. [Google Scholar] [CrossRef]
- Li, R.; Song, T.; Mei, B.; Li, H.; Cheng, X.; Sun, L. Blockchain for large-scale internet of things data storage and protection. IEEE Trans. Serv. Comput. 2018, 12, 762–771. [Google Scholar] [CrossRef]
- Rui, H.; Huan, L.; Yang, H.; Yunhao, Z. Research on secure transmission and storage of energy IoT information based on Blockchain. Peer-to-Peer Netw. Appl. 2020, 13, 1225–1235. [Google Scholar] [CrossRef]
- Yang, C.; Chen, X.; Xiang, Y. Blockchain-based publicly verifiable data deletion scheme for cloud storage. J. Netw. Comput. Appl. 2018, 103, 185–193. [Google Scholar] [CrossRef]
- Yu, Y.; Xue, L.; Li, Y.; Du, X.; Guizani, M.; Yang, B. Assured data deletion with fine-grained access control for fog-based industrial applications. IEEE Trans. Ind. Inform. 2018, 14, 4538–4547. [Google Scholar] [CrossRef]
- Xue, L.; Yu, Y.; Li, Y.; Au, M.H.; Du, X.; Yang, B. Efficient attribute-based encryption with attribute revocation for assured data deletion. Inf. Sci. 2018, 479, 640–650. [Google Scholar] [CrossRef]
- Cheng, L.; Liu, J.; Su, C.; Liang, K.; Xu, G.; Wang, W. Polynomial-based modifiable blockchain structure for removing fraud transactions. Future Gener. Comput. Syst. 2019, 99, 154–163. [Google Scholar] [CrossRef]
- Yang, C.; Tao, X.; Chen, Q. New publicly verifiable data deletion supporting efficient tracking for cloud storage. Int. J. Netw. Secur. 2020, 22, 885–896. [Google Scholar]
- Hassija, V.; Chamola, V.; Garg, S.; Krishna, D.N.G.; Kaddoum, G.; Jayakody, D.N.K. A blockchain-based framework for lightweight data sharing and energy trading in V2G network. IEEE Trans. Veh. Technol. 2020, 69, 5799–5812. [Google Scholar] [CrossRef]
- Li, M.; Lal, C.; Conti, M.; Hu, D. LEChain: A blockchain-based lawful evidence management scheme for digital forensics. Future Gener. Comput. Syst. 2020, 115, 406–420. [Google Scholar] [CrossRef]
- Niu, Z.; Zheng, M.; Zhang, Y.; Wang, T. A new asymmetrical encryption algorithm based on semitensor compressed sensing in WBANs. IEEE Internet Things J. 2019, 7, 734–750. [Google Scholar] [CrossRef]
- Wang, P.; Li, Y.; Dong, X.; Chen, P. Secure and Traceable Copyright Management System Based on Blockchain. In Proceedings of the 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 6–9 December 2019; pp. 1243–1247. [Google Scholar]
- Gao, J.; Yu, H.; Zhu, X.; Li, X. Blockchain-Based Digital Rights Management Scheme via Multiauthority Ciphertext-Policy Attribute-Based Encryption and Proxy Re-Encryption. IEEE Syst. J. 2021, 15, 5233–5244. [Google Scholar] [CrossRef]
- Wang, E.K.; Liang, Z.; Chen, C.-M.; Kumari, S.; Khan, M.K. PoRX: A reputation incentive scheme for blockchain consensus of IIoT. Future Gener. Comput. Syst. 2019, 102, 140–151. [Google Scholar] [CrossRef]
- Huang, H.; Miao, W.; Min, G.; Tian, J.; Alamri, A. NFV and Blockchain Enabled 5G for Ultra-Reliable and Low-Latency Communications in Industry: Architecture and Performance Evaluation. IEEE Trans. Ind. Inform. 2020, 17, 5595–5604. [Google Scholar] [CrossRef]
- Gao, Y.; Chen, Y.; Hu, X.; Lin, H.; Liu, Y.; Nie, L. Blockchain based IIoT data sharing framework for SDN-enabled Pervasive Edge Computing. IEEE Trans. Ind. Inform. 2020, 17, 5041–5049. [Google Scholar] [CrossRef]
- Singh, N.; Kumar, T.; Vardhan, M. Blockchain-based e-cheque clearing framework with trust based consensus mechanism. Clust. Comput. 2020, 24, 851–865. [Google Scholar] [CrossRef]
- Yun, J.; Goh, Y.; Chung, J.-M. DQN-Based Optimization Framework for Secure Sharded Blockchain Systems. IEEE Internet Things J. 2020, 8, 708–722. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).